Linux Trojan - Xorddos with Filename eyshcjdmzg
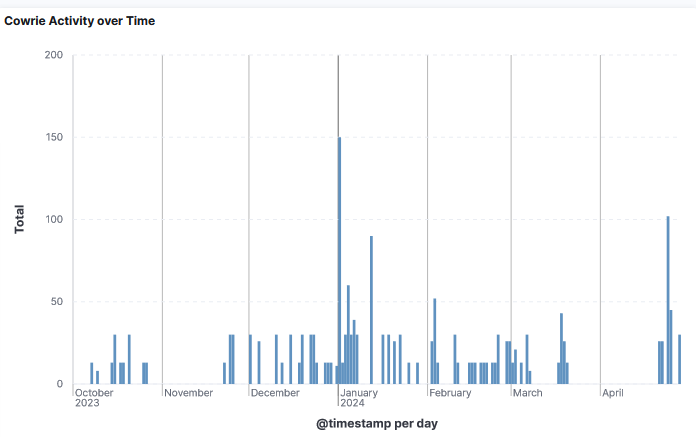
I reviewed a filename I see regularly uploaded to my DShield sensor eyshcjdmzg that have been seeing since the 1 October 2023 which has multiple hashes and has been labeled as trojan.xorddos/ddos. These various files have only been uploaded to my DShield sensor by IP 218.92.0.60. Here is the timeline of the activity since 1 October 2023.
According to VirusTotal the oldest file submission is b39633ff1928c7f548c6a27ef4265cfd2c380230896b85f432ff15c7c819032c [1] last submitted in Aug 2019 and was uploaded to the DShield sensor only once on the 7 March 2024.
This file can be detected with ET MALWARE DDoS.XOR Checkin via HTTP at Proofpoint Emerging Threats Open.
Sandbox Analysis
I submitted file ea40ecec0b30982fbb1662e67f97f0e9d6f43d2d587f2f588525fae683abea73 to a few sandbox including AssemblyLine [7] to get any and all indicators that were part of this sample:
Other indicators appear to include a config file [5] that is used for C2 communications. I compared my results against other online sandbox [8][9] and there isn't much that has changed in the most active sample [1].
Indicators - Hashes
ea40ecec0b30982fbb1662e67f97f0e9d6f43d2d587f2f588525fae683abea73 - 65
cd9bc23360e5ca8136b2d9e6ef5ed503d2a49dd2195a3988ed93b119a04ed3a9 - 2
98e53e2d11d0aee17be3fe4fa3a0159adef6ea109f01754b345f7567c92ebebb - 1
b39633ff1928c7f548c6a27ef4265cfd2c380230896b85f432ff15c7c819032c - 1
ecc33502fa7b65dd56cb3e1b6d3bb2c0f615557c24b032e99b8acd40488fad7c - 1
b4a86fdf08279318c93a9dd6c61ceafc9ca6e9ca19de76c69772d1c3c89f72a8 - lib.xlsx
b4a86fdf08279318c93a9dd6c61ceafc9ca6e9ca19de76c69772d1c3c89f72a8 - lib.xlsxpi.enoan2107[.]com:112
Indicator - IP
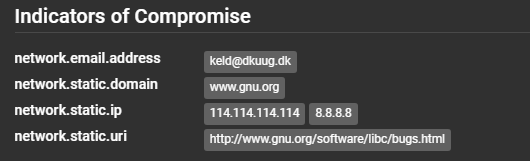
218.92.0.60
114.114.114.114
Indicator - Domain
qq[.]com/lib.asp
qq[.]com/lib.xlsx
qq[.]com/lib.xlsxpi.enoan2107.com:112
Indicator - Email
keld@dkuug.dk
[1] https://www.virustotal.com/gui/file/ea40ecec0b30982fbb1662e67f97f0e9d6f43d2d587f2f588525fae683abea73
[2] https://www.virustotal.com/gui/file/cd9bc23360e5ca8136b2d9e6ef5ed503d2a49dd2195a3988ed93b119a04ed3a9
[3] https://www.virustotal.com/gui/file/98e53e2d11d0aee17be3fe4fa3a0159adef6ea109f01754b345f7567c92ebebb
[3] https://www.virustotal.com/gui/file/b39633ff1928c7f548c6a27ef4265cfd2c380230896b85f432ff15c7c819032c
[4] https://www.virustotal.com/gui/file/ecc33502fa7b65dd56cb3e1b6d3bb2c0f615557c24b032e99b8acd40488fad7c
[5] https://www.virustotal.com/gui/file/b4a86fdf08279318c93a9dd6c61ceafc9ca6e9ca19de76c69772d1c3c89f72a8
[6] https://isc.sans.edu/ipinfo/218.92.0.60
[7] https://cybercentrecanada.github.io/assemblyline4_docs/
[8] https://www.hybrid-analysis.com/sample/ea40ecec0b30982fbb1662e67f97f0e9d6f43d2d587f2f588525fae683abea73/6542ca0426609dce5c06aef5
[9] https://www.hybrid-analysis.com/sample/f0e4649181ee9917f38233a1d7b6cbb98c9f7b484326f80c1bebc1fa3aef0645/65c332e1c38ced89350a1e94
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
D-Link NAS Device Backdoor Abused
End of March, NetworkSecurityFish disclosed a vulnerability in various D-Link NAS devices [1]. The vulnerability allows access to the device using the user "messagebus" without credentials. The sample URL used by the PoC was:
GET /cgi-bin/nas_sharing.cgi?user=messagebus&passwd=&cmd=15&system=<BASE64_ENCODED_COMMAND_TO_BE_EXECUTED>
In addition to not requiring a password, the URL also accepts arbitrary system commands, which must be base64 encoded. Initial exploit attempts were detected as soon as April 8th. The vulnerability is particularly dangerous as some affected devices are no longer supported by DLink, and no patch is expected to be released. DLink instead advised to replace affected devices [2]. I have not been able to find an associated CVE number.
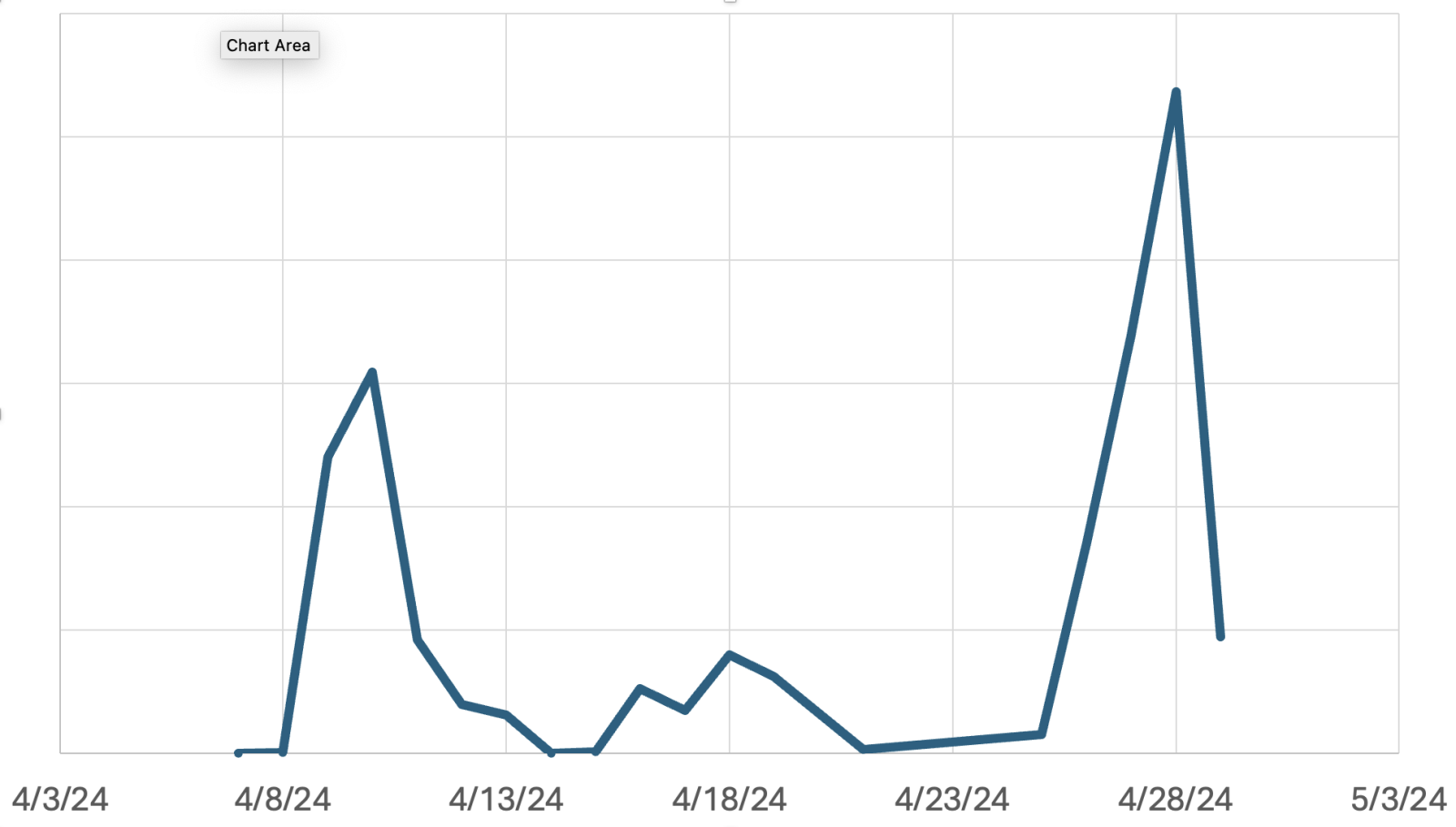
After the initial exploit attempts at the beginning of the month, we now see a new distinct set of exploit attempts, some of which use different URLs to attack vulnerable systems. It appears that nas_sharing.cgi is not the only endpoint that can be used to take advantage of the passwordless "messagebus" account.
So far, we do see these three different URLs
/.most/orospucoc.cgi
/cgi-bin/nas_sharing.cgi
/cgi-bin/orospucoc.cgi
It is not clear if "orospucoc.cgi" is a distinct different vulnerability. But it appears more like another endpoint allowing for command execution, just like the original "nas_sharing.cgi" endpoint. I found no documentation mentioning the "orospucoc.cgi" endpoint. If anybody has an affected D-Link NAS device, let me know if this endpoint exists. In particular, "/.most/orospucoc.cgi" is odd. This URL starts showing up in our logs on April 17th. The term "orospucoc" in Turkish translates to the English "bitch", which could indicate that this is not an actual vulnerable URL, but maybe a backdoor left behind by earlier attacks. The use of the directory ".most" and the payload "echo most" may point to a backdoor rather than a valid binary shipped with the device's firmware.
Any feedback from DLink NAS users is appreciated.
The most common command executed is "uname -m" which is likely used to identify vulnerable devices. Other commands include:
echo @hackerlor0510
echo most
[1] https://github.com/netsecfish/dlink
[2] https://supportannouncement.us.dlink.com/security/publication.aspx?name=SAP10383
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|

Comments