Qakbot (Qbot) activity, obama271 distribution tag
Introduction
Qakbot using the obama-series distribution tag has been active this week on Tuesday 2023-06-20 (obama269), Wednesday 2023-06-21 (obama270), and Thursday 2023-06-22 (obama271). Today's diary provides indicators from an infection and some samples collected today from the obama271 wave on Thursday 2023-06-22.
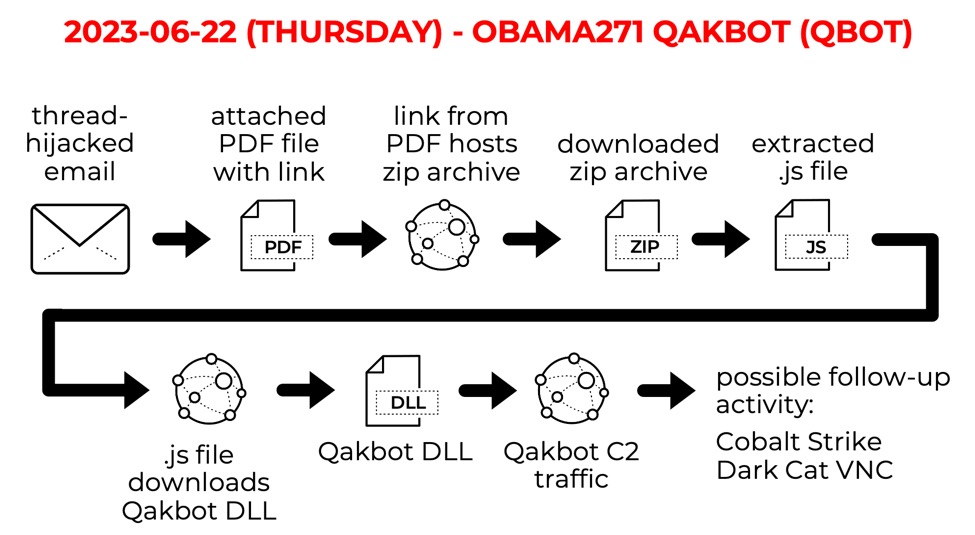
Shown above: Flow chart for today's obama271 Qakbot infection.
Initial Infection Traffic
The initial infection started with an HTTP URL ending in .gif that returned a zip archive. After extracting a .js file from the downloaded zip and running it, we see HTTPS traffic with the domain that returned our Qakbot DLL. Qakbot C2 traffic includes HTTPS requests to legitimate domains like oracle.com as noted below. Finally, we saw Qakbot HTTPS C2 traffic on 142.154.58[.]207 almost eight minutes after the Qakbot DLL was retrieved.
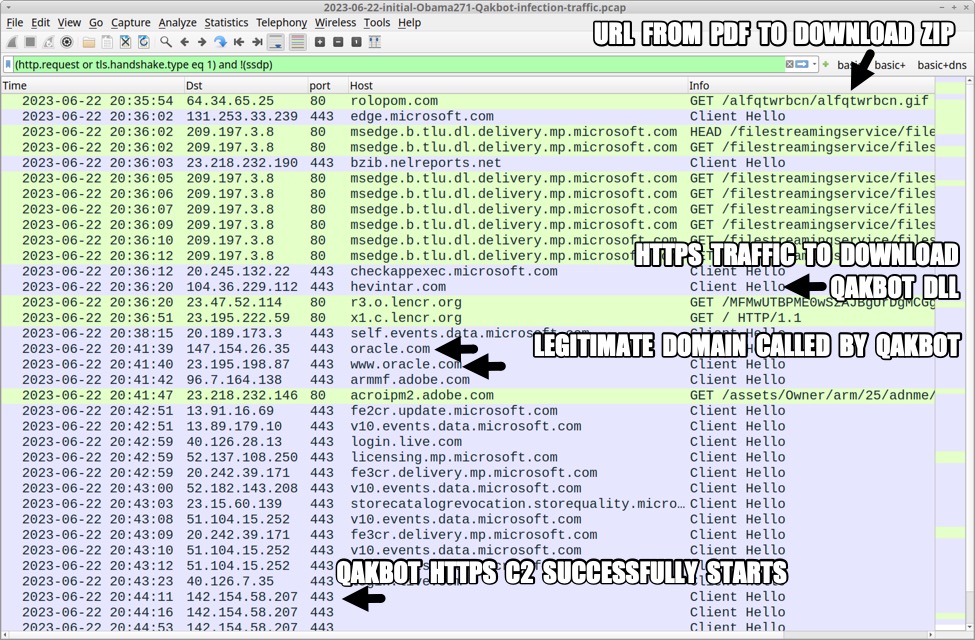
Shown above: Traffic from the infection filtered in Wireshark.
Indicators of compromise (IOCs)
2023-06-22 (THURSDAY): OBAMA271 QAKBOT (QBOT) ACTIVITY
INFECTION CHAIN:
email --> PDF attachment --> link from PDF --> downloaded zip --> extracted .js --> retrieves/runs Qakbot DLL
SIX EXAMPLES OF PDF ATTACHMENTS:
272ce466b3a6170c010806f207e3f69cb732c6d56d219e48c24f954378a044fb BSN-1123674130.pdf
06f3fc2a37fcc5785fcf482ff01f83e461be4ad55aa20abbbc6dbf3239a1eabd BSN-1606206602.pdf
c95a5ce6a5826df5ac6589a87faf3c67ff42f44dd4474c27a3eac13580329423 BSN-2057567741.pdf
dc8150390742b6d5c7a1c2d8c1f7291181382f1fa03dccb6cabd7e669e28640d BSN-235750987.pdf
622b1ca18203ea6203845df514442370f547bfd5fa9ca3efd8b947ad37ad37ef BSN-689895792.pdf
e032d480889727fb3fa5632084b4ce846b9a25fb855d1897977d0e155a472e2b BSN-773800054.pdf
LINKS FROM ATTACHED PDF FILES:
hxxps://brotherocean[.]com/bebarwlxbs/bebarwlxbs.gif
hxxp://garagedoorportsmouthnh[.]com/xnozmxusda/xnozmxusda.gif
hxxps://janakagroup[.]lk/dfvurstvvb/dfvurstvvb.gif
hxxp://pn-jayapura[.]go[.]id/rwhdnuavuo/rwhdnuavuo.gif
hxxp://rolopom[.]com/alfqtwrbcn/alfqtwrbcn.gif
hxxp://treegeyecare[.]com/ypsormkzyz/ypsormkzyz.gif
FILES USED FOR AN INFECTION RUN:
SHA256 hash: d32e1cc5c161ae0fd8ae6c11cb6df5bce79690d1c533b4a5b9140ed8cb005f21
File size: 79,478 bytes
Downloaded from: hxxp://rolopom[.]com/alfqtwrbcn/alfqtwrbcn.gif
File name: BSN-1226578580.zip
File description: Zip archive downloaded from link in PDF attachment
SHA256 hash: c465f039b08c3320fdce5f63992b5363b96c21d6e3b1da1df1e38caf65482caa
File size: 350,611 bytes
File name: BSN-1226578580.js
File description: JS file extracted from the above zip archive
URLS GENERATED BY THE ABOVE .JS FOR QAKBOT DLL:
hxxp://hevintar[.]com/0.38107541532568295.dat
hxxp://cehazik[.]com/0.8841605299322328.dat
hxxp://cosiruk[.]com/0.2959007454371704.dat
hxxp://swofacin[.]com/0.6385317941125832.dat
hxxp://tytrhel[.]com/0.8364758034624875.dat
hxxp://cgpersa[.]com/0.9934429799425988.dat
QAKBOT DLL SEEN DURING THE INFECTION RUN:
SHA256 hash: 98bf24844d138dfd50188f3325f13ea3a1cde4d650900ae1d6820a2b1d4a59fd
File size: 1,405,439 bytes
Downloaded from: hxxp://hevintar[.]com/0.38107541532568295.dat
File location: C:\VPNStors\Krosters\Spote.OCCXX
Run method: rundll32.exe [file name],zertc
Final Words
A pcap of the infection traffic, along the the associated malware and artifacts can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
Apple Patches Exploited Vulnerabilities in iOS/iPadOS, macOS, watchOS and Safari
Apple released iOS, macOS, and watchOS updates, patching three vulnerabilities already being exploited. Two vulnerabilities affect WebKit, leading to a Safari patch for older operating systems.
The two WebKit issues (CVE-2023-32439 and CVE-2023-32435) can be used to execute arbitrary code as a user visits a malicious web page. The third vulnerability, CVE-2023-32434, can be used to elevate privileges after the initial code execution.
See below for affected operating systems. Apple does not provide CVSS scores, so we asked ChatGPT to fill them in.
| Safari 16.5.1 | iOS 16.5.1 and iPadOS 16.5.1 | iOS 15.7.7 and iPadOS 15.7.7 | macOS Ventura 13.4.1 | macOS Monterey 12.6.7 | macOS Big Sur 11.7.8 | watchOS 9.5.2 | watchOS 8.8.1 |
|---|---|---|---|---|---|---|---|
| CVE-2023-32439 [critical] ChatGPT-CVSS: CVSS score: 9.8 (Critical) *** EXPLOITED *** WebKit A type confusion issue was addressed with improved checks. Processing maliciously crafted web content may lead to arbitrary code execution. Apple is aware of a report that this issue may have been actively exploited. |
|||||||
| x | x | x | x | ||||
| CVE-2023-32434 [important] ChatGPT-CVSS: 8.8 *** EXPLOITED *** Kernel An integer overflow was addressed with improved input validation. An app may be able to execute arbitrary code with kernel privileges. Apple is aware of a report that this issue may have been actively exploited against versions of iOS released before iOS 15.7. |
|||||||
| x | x | x | x | x | x | x | |
| CVE-2023-32435 [critical] ChatGPT-CVSS: 7.8 *** EXPLOITED *** WebKit A memory corruption issue was addressed with improved state management. Processing web content may lead to arbitrary code execution. Apple is aware of a report that this issue may have been actively exploited against versions of iOS released before iOS 15.7. |
|||||||
| x | |||||||
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|

Comments