New ISO Standards on Vulnerability Handling and Disclosure
Also in the news, ISO standard 30111 was published recently (on Jan 21) - a standard for the Vulnerability Handling Processes. The standard was edited by Katie Moussouris, Senior Security Strategist Lead at Microsoft
The standard covers all the basics, including Vulnerability Verification steps, the Vulnerability Handling Process, and of particular interest is that it delineates where vendors should and should not be in the process.
The companion document, ISO 29147 (published in 2013) covers Vulnerability Disclosure. This one is extremely valuable both to security researchers and for any company with a software product. This standard includes guidance on buidling a framework to address vulnerabilities, including a 5 step process that guides vendors through initial receipt and verification of the vulnerability, developing a resolution, releasing the final fix and communication with customers after the fix is released
As with all ISO standards, unfortunately these are not free - both are well worth it if the standards apply to your organization. If your organization writes code, or if you sell hardware that runs code, both of these standards are a must-have.
ISO 30111 can be purchased here: http://www.iso.org/iso/catalogue_detail.htm?csnumber=53231
ISO 29147 can be purchased here: http://www.iso.org/iso/catalogue_detail.htm?csnumber=45170
===============
Rob VandenBrink
Metafore
Hello Virustotal? It's Microsoft Calling.
You might think that phone call might be unlikely, but as of this week it's built in and is likely happening right now.
I was poking around in the latest version of Sysinternals, and tripped over a new option. You can now submit any running process in memory directly to Virustotal. it's a simple right-click in the latest version of Process Explorer.
If that's not just the coolest thing! If your AV product isn't triggering on a suspect process, you can now query all the AV engines without even having to find or upload the file - - assuming that a file that matches your process even exists - if you're in the midst of a security incident a suspect process might not have a matching file.
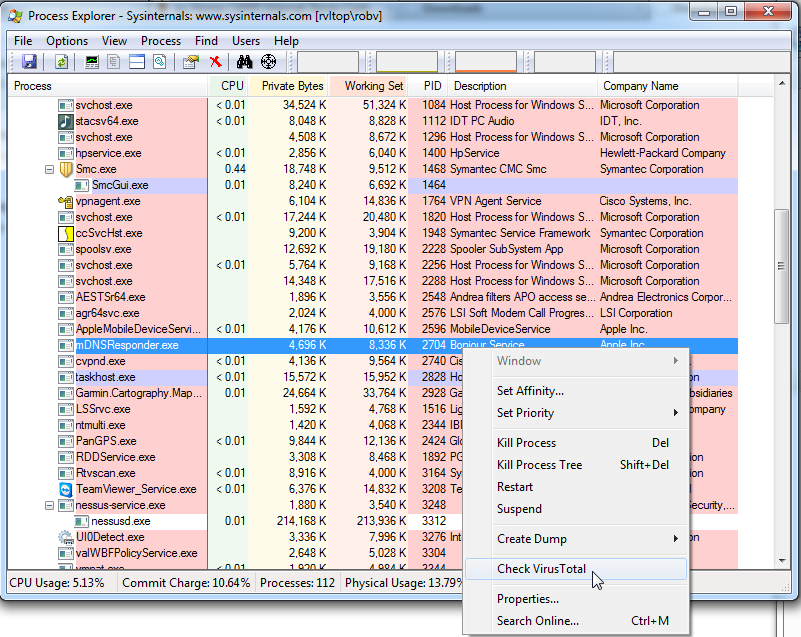
Sysinternals: http://technet.microsoft.com/en-us/sysinternals
VirusTotal: https://www.virustotal.com/
===============
Rob VandenBrink
Metafore
Microsoft Advance Notification for February 2014
Today Microsoft published the advance notification for this months security bulletins. The bulletins will be published on February 11th (coming Tuesday) [1]. Again, we will have a pretty light patch day, with only 5 bulletins, and only 2 of these bulletins are considered critical.
Noteworthy: No Internet Explorer patches and no Office Patches. We will only see Windows Patches, a patch for .Net and a "Security Software" patch.
Not part of the patch Tuesday, but still happening on the same day: Microsoft will no longer allow MD5 hashes for certificates. This may be difficult for some applications that haven't been changed over yet, even though Microsoft gave ample warning, and MD5 hashes have been shown to be badly broken for certificate signatures for a few years now. Just earlier today I ran into a brand new Axis, pretty expensive, network camera that only allows the use of MD5 hashed certificate signatures.
[1] http://technet.microsoft.com/en-us/security/bulletin/ms14-feb
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter

Comments