Apple DDOS? Nope, just the update coming down!
The amount of press that Apples IOS 7 update has gotten today has had an unintended consequence - everyone seems to be pulling it down the instant they see that it's available.
This is triggering IPS Sensors and causing real DOS conditions due to the traffic involved - an unintended "apple - zooka"
<<updated content follows>>
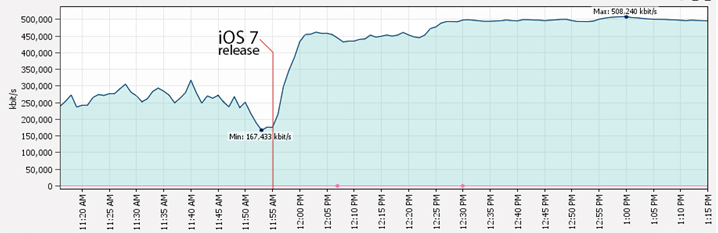
Our readers are reporting up to a doubling of wireless traffic, and similar increases on overall internet bandwidth usage! The chart below shows the impact on a wireless network in a education setting (thanks again to John and Eric for this!). That's more Apple-y goodness than we bargained for today !
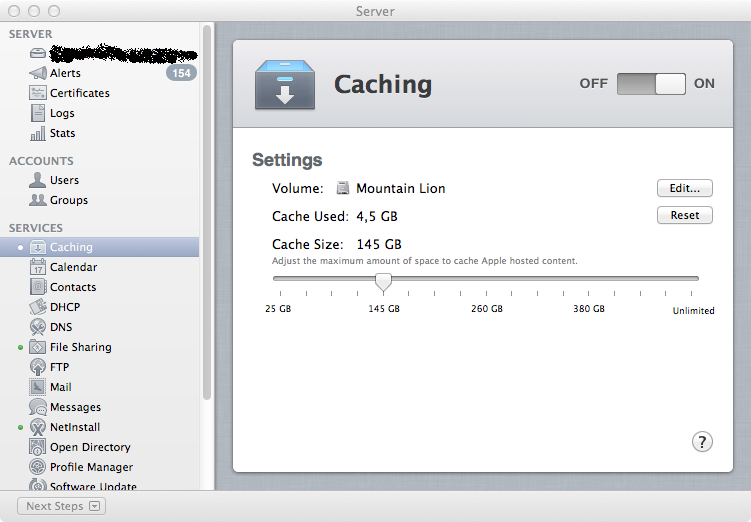
Swa, one of our handlers, indicates that this can be easily resolved for a corporate network by enabling the Apple Caching Service and/or Software Update Server on a single OSX Server in the network, which serves as the update "broker" for all clients on the netowrk. (thanks for the screenshot Swa). The Caching Server will serve up all Apple content (including updates), while the Update Server will only server up Updates.
I'm not sure how these services interact with the Service Discovery features in mDNS - if anyone has details on this we'd appreciate your insight in the comments field for this story!
The basics of setting up your Caching Server can be found in the "Mac Management Basics" guide, found here ==> http://training.apple.com/pdf/Mac_Management_Basics_10.8.pdf
Generally, just enabling the Caching Server is enough, but advanced settings for the caching server can be found here ==> http://support.apple.com/kb/HT5590
===============
Rob VandenBrink
Metafore
More Goodies in the Apple Security Update Basket!
APPLE-SA-2013-09-18-3
An OSX update that fixes a situation where the hostname in a certificate is not checked against the actual hostname. This vulnerability means that anyone with a valid certificate can impersonate any host - lots of attack applications in this, when combined with MITM or DNS hijack attacks
APPLE-SA-2013-09-18-2
An absolute TON of updates for IOS, which should be no surprise in a new version. The highlights include updates to the Root Certificates, fixes for code exploit issues from malicious PDF and Movie files, and a bypass for the password retry limit, allowing a malicious app to brute force the device unlock code.
Also some fun fixes for several cross site scripting issues within Webkit (which is the provider for browser functions in IOS)
Attack vectors for these include buffer overflows, misses on bounds checking and some fun kernel mode attacks!
As always, watch for the full details on Apple's Security Update Page, found here ==> http://support.apple.com/kb/HT1222
===============
Rob VandenBrink
Metafore
Cisco DCNM Update Released
We continue to see web applications deployed to manage datacenter functions. And I'm sorry to say, we continue to see security issues in these applications - some of them so simple a quick run-through with Burp or ZAP would red-flag them.
In that theme, today Cisco posts updates to DCNM (Cisco Prime Data Center Network Manager). The issues resolved are not so simple as I describe above (they are more complex than a simple scan to detect or exploit), but they do involve remote command execution and authentication bypass - two things most folks should have problems with in a Data Center Network Manager.
The advisory is here ==> http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20130918-dcnm
As per usual, a valid service contract is required to obtain the update. My clients do have Cisco contracts, but I'm not sure how thrilled I am that you need to pay maintenance to fix security issues so fundamental.
===============
Rob VandenBrink
Metafore
Apple IOS 7 - Brace for Impact!
Apple IOS 7 is available today (just posted in fact). While the major push for this is support for the new iPhone platforms, we can expect functional and security changes that will affect all ios platforms, among them:
- per app licensing
- per app vpn settings
- per app encryption keys
- single signon (What could possibly go wrong with this?! )
- and better MDM (Mobile Device Management) functions - expect upgrades for your corporate MDM platforms sometime real soon, and expect that management will want these applied ASAP!
- More on these features here - http://www.apple.com/ios/business/
I'm sure several of these new features are worth a story all on their own - stay tuned!
We've all seen the flurry of app updates over the past few weeks, as everyone gets their app ready for the new OS. Before updating, you should check to see that all of your apps will support the new operating system. For instance, I still use Stanza as a reader app for my fiction library. Since it was officially moved to unsupported status by Amazon, I think it's smart for me to (finally) change readers before I upgrade.
This update comes at an interesting time for a couple of my clients. Since going to a BYOD model, they now have thousands of i-devices ontheir networks, unmanaged and for the mostly owned by their users (or their visitors). Ibn most organizations, at just under 1GB the bandwidth overhead of for this update shouldn't be an issue, but one client in my list is in that "thousands of Apple devices" list and is also on my "bandwidth constrained" list. I can see this update affecting their business applications, both by stressing their already maxed out WAN and also by adding to their already over-capacity internet uplink. We're changing their QOS to de-prioritize "all things Apple" for today. Once we can characterize what this update looks like on the network, we'll make the ACL more specific to just deprioritize the update traffic. Now that the update is posted, I'll be firing up TCPDUMP and doing just that !
===============
Rob VandenBrink
Metafore

Comments