DNS servers hijacked in the Netherlands
Information leakage through cloud file storage services
Last Updated: 2013-08-08 02:01:13 UTC
by Manuel Humberto Santander Pelaez (Version: 1)
Cloud services are here to stay. This poses a big challenge for information security professionals, because we cannot longer restrict mobility and thus we need to implement controls to ensure that mobility services does not pose a threat to any information security asset of the company.
Bad guys tend to steal critical information from the company and takes it out using e-mails, chat file transfers and could file storage services. The first two are being monitored in most companies, but not all companies have the technical controls available to regulate usage on the third one. There are two big services here: Skydrive and Dropbox. Skydrive does not announce to the network and so the only way to detect it is to monitor outgoing traffic for the file transfer protocol used, which is MS-FSSHTTP (File Synchronization via SOAP over HTTP Protocol). For example, if anyone is saving a file to http://Example/Shared%20Documents/test1.docx, the request sent would be:
<s:Envelope xmlns:s="http://schemas.xmlsoap.org/soap/envelope/">
<s:Body>
<RequestVersion Version="2" MinorVersion="0"
xmlns="http://schemas.microsoft.com/sharepoint/soap/"/>
<RequestCollection CorrelationId="{83E78EC0-5BAE-4BC2-9517-E2747382569B}"
xmlns="http://schemas.microsoft.com/sharepoint/soap/">
<Request Url="http://Example/Shared%20Documents/test1.docx" RequestToken="1">
<SubRequest Type="Coauth" SubRequestToken="1">
<SubRequestData CoauthRequestType="RefreshCoauthoring"
SchemaLockID=" 29358EC1-E813-4793-8E70-ED0344E7B73C"
ClientID="{BE07F85A-0CD1-4862-BDFC-F6CC3C8588A4}" Timeout="3600"/>
</SubRequest>
<SubRequest Type="SchemaLock" SubRequestToken="2" DependsOn="1"
DependencyType="OnNotSupported">
<SubRequestData SchemaLockRequestType="RefreshLock"
SchemaLockID=" 29358EC1-E813-4793-8E70-ED0344E7B73C"
ClientID="{BE07F85A-0CD1-4862-BDFC-F6CC3C8588A4}" Timeout="3600"/>
</SubRequest>
<SubRequest Type="Cell" SubRequestToken="3" DependsOn="2"
DependencyType="OnSuccessOrNotSupported">
<SubRequestData Coalesce="true" CoauthVersioning="true"
BypassLockID="29358EC1-E813-4793-8E70-ED0344E7B73C"
SchemaLockID="29358EC1-E813-4793-8E70-ED0344E7B73C" BinaryDataSize="17485">
<i:Include xmlns:i="http://www.w3.org/2004/08/xop/include"
href="cid:b2c67b53-be27-4370-b214-6be0a48da399-0@tempuri.org"/>
</SubRequestData>
</SubRequest>
</Request>
</RequestCollection>
</s:Body>
</s:Envelope>
And the response would be:
<s:Envelope xmlns:s="http://schemas.xmlsoap.org/soap/envelope/">
<s:Body>
<ResponseVersion Version="2" MinorVersion="0"
xmlns="http://schemas.microsoft.com/sharepoint/soap/"/>
<ResponseCollection WebUrl="http://Example"
xmlns="http://schemas.microsoft.com/sharepoint/soap/">
<Response Url="http://Example/Shared%20Documents/test1.docx"
RequestToken="1" HealthScore="0">
<SubResponse SubRequestToken="1" ErrorCode="Success" HResult="0">
<SubResponseData LockType="SchemaLock" CoauthStatus="Alone"/>
</SubResponse>
91
<SubResponse SubRequestToken="2"
ErrorCode="DependentOnlyOnNotSupportedRequestGetSupported"
HResult="2147500037">
<SubResponseData/>
</SubResponse>
1dd
<SubResponse SubRequestToken="3" ErrorCode="Success" HResult="0">
<SubResponseData Etag=""{600CE272-068F-4BD7-A1FB-4AC10C54386C},2""
CoalesceHResult="0" ContainsHotboxData="False">DAALAJ3PKfM5lAabFgMCAAAOAgYAAwsAhAAmAiAA9jV
6MmEHFESWhlHpAGZ6TaQAeCRNZ9PslLQ+v5Vxq4ReeFt+AMF4JLKYLBNrS8FAlXGrhF54W
34At1ETASYCIAATHwkQgsj7QJiGZTP5NMIdbAFwLQz5C0E3b9GZRKbDJyMu3KcRCTMAAAC1
EwEmAiAADul2OjKADE253fPGUClDPkwBICYMspgsE2tLwUCVcauEXnhbfrcApRMBQQcBiwE=</SubResponseData>
</SubResponse>
36
</Response>
</ResponseCollection>
</s:Body>
</s:Envelope>
The following table resumes all possible subrequest operations and their descriptions.
|
Operation |
Description |
|---|---|
|
Cell subrequest |
Retrieves or uploads a file’s binary contents or a file’s metadata contents. |
|
Coauth subrequest |
Gets a shared lock on a coauthorable file that allows for all clients with the same schema lock identifier to share the lock. The protocol server also keeps tracks of the clients sharing the lock on a file at any instant of time. |
|
SchemaLock subrequest |
Gets a shared lock on a coauthorable file that allows all clients with the same schema lock identifier to share the lock. |
|
ExclusiveLock subrequest |
Gets an exclusive lock on the file, which ensures only one client edits the file at an instant in time. |
|
WhoAmI subrequest |
Retrieves the client's friendly name and other client-specific information for a client with a unique client identifier. |
|
ServerTime subrequest |
Retrieves the server time. |
|
Editors Table subrequest |
Adds the client to the editors table, which is accessible to all clients editing or reading a document. |
|
GetDocMetaInfo subrequest |
Retrieves various properties for the file and the parent folder as a series of string pairs. |
|
GetVersions subrequest |
Sends back information about the previous versions of a file. |
This protocol can be easily detected and tracked using IPS signatures or, if you have a layer 7 firewall, you can use their functionality to detect this protocol application and stop it. Checkpoint can do it with its software blade for 5052 applications as of today.
Dropbox can be easily detected on the network. It sends every 30 seconds a packet announcing the client for possible LAN Sync operations. Those packets are like the following one:
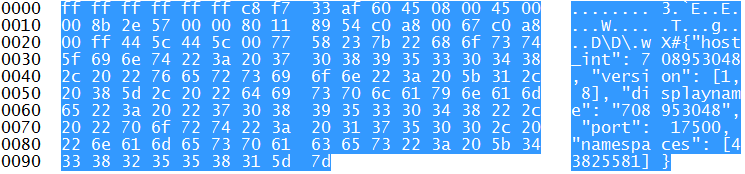
If you want to detect those packets, you can use wireshark and look for them using the filter udp.port==17500 or performing the following command using nmap:
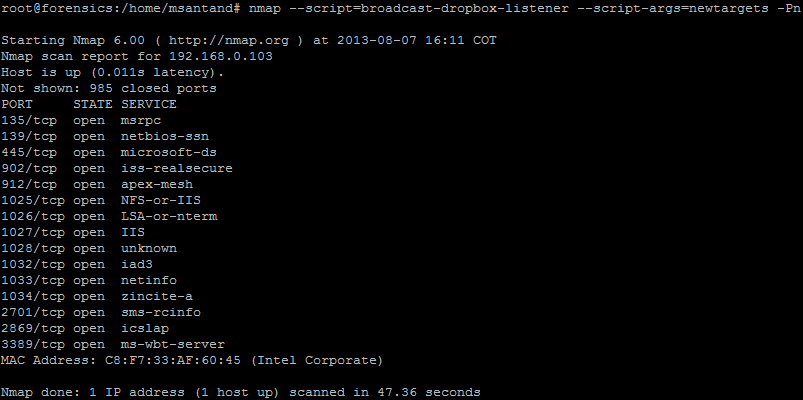
This command performs portscan to all the IP address where the Dropbox listener was detected. The nmap script shown in the last figure has the following options:
- --script=broadcast-dropbox-listener: This nmap scripts listen for the Dropbox LAN Sync protocol broadcast packet sent every 30 second on the LAN.
- --script-args=newtargets: This option tells nmap to add the detected IP as a target to perform a scan.
- -Pn: Treat all hosts as online without performing host discovery.
How can we provide this kind of services to our users without having their mobility ability affected? Skydrive Pro can be used with Sharepoint Online or local Sharepoint Server 2013. If you don't have servers inside, you can use Dropbox for business, which is now able to integrate with your local active directory.
Manuel Humberto Santander Peláez
SANS Internet Storm Center - Handler
Twitter:@manuelsantander
Web:http://manuel.santander.name
e-mail: msantand at isc dot sans dot org
Firefox 23 and Mixed Active Content
One of the security relevant features that arrived in the latest version of Firefox was the blocking of mixed active content. In the past, you may have seen popups warnings in your browser alerting you of "mixed content". This refers to pages that mix and match SSL and non SSL content. While this is not a good idea even for passive content like images, the real problem is active content like script. For example, a page may download javascript via HTTP but include it in an HTTPS page. The javascript could now be manipulated by someone playing man in the middle. The modified javascript can then in turn alter the HTML page that loaded it. After all we are using the HTML to load the javascript, so we will not have any "origin" issues.
Firefox 23 refined how it deals with "mixed ACTIVE content". If an HTML page that was loaded via HTTPS includes active content, like javascript, via HTTP, then Firefox will block the execution of the active content.
I setup a quick test page to allow you to compare browsers. The first page https://isc.sans.edu/mixed.html just includes two images. One is loaded via https and one via http. The second page, https://isc.sans.edu/mixed2.html does include some javascript as well. If the javascript executes, then you should see the string "The javascript executed" under the respective lock image.
For more details, see Mozilla's page about this feature:
https://blog.mozilla.org/tanvi/2013/04/10/mixed-content-blocking-enabled-in-firefox-23/
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter

Comments