Microsoft February Patch Tuesday Advance Notification
Looks like next tuesday will be a busy patch tuesday. Expect 11 bulletins fixing 57 vulnerabilities. Most of the bulletins affect Windows, but we also got one for Office, two affecting Internet Explorer and one affecting server software. It is a bit odd to see two bulletins affecting Itnernet Explorere instead of just one "roll up patch". 5 of the bulletins are ratesd critical.
Also note that Microsoft released an update for the Flash Player for Internet Explorer 10 today, in sync with Adobe's update for flash player [2].
[1] http://technet.microsoft.com/en-us/security/bulletin/ms13-feb
[2] http://technet.microsoft.com/en-us/security/advisory/2755801
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
Is it Spam or Is it Malware?
The Friend
Does anyone have a friend that regularly still sends you crap via email that usually includes a link or some pic's? We are all IT security professionals here and know the preacher's drill on this topic. Really, we do not like wasting our time on the junk that is sent to us. Delete, Delete, Delete.
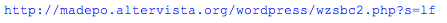
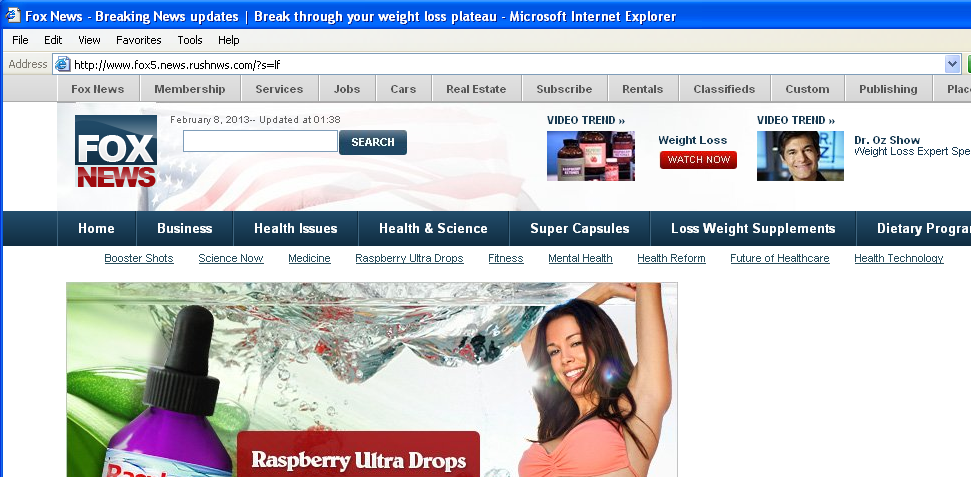
Now. We Need To Know
Did we just infect our system?
We need to know. It is time to act fast. Get to a shell and pull that page down with a text browser ala wget or curl. It is possible for this page to disappear quickly. This sample was sent in by a reader who acted fast. By the time I got around to verifying some things on this sample, the below pasted code was gone.
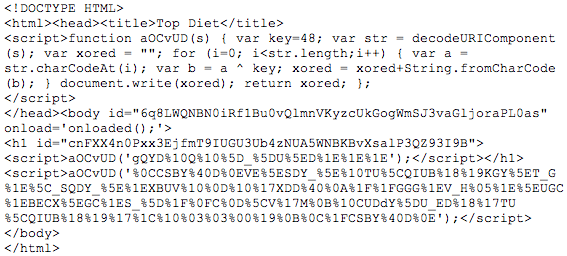
The Lazy Liston
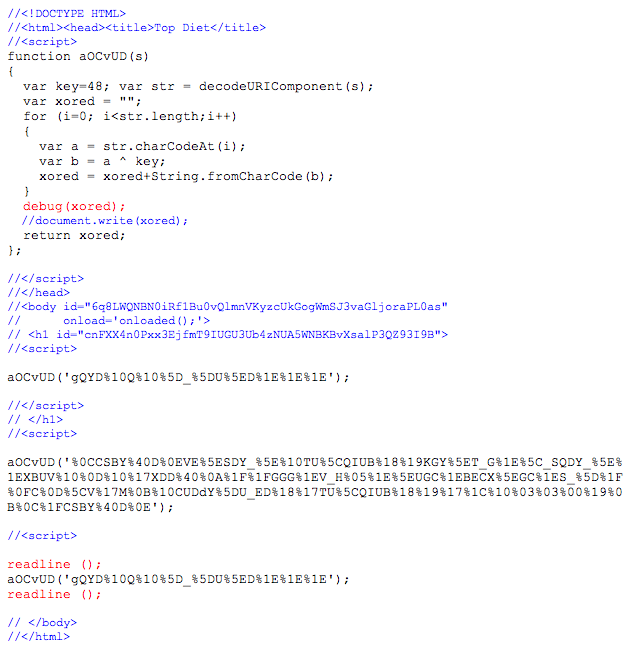
I used jsc to help me out with the prepared script above. jsc is a command line utility that allows you to run javascript interactively. I inserted a debug and a couple of readline statements to assist. The readline allows me to pause the script to view the output. Pressing enter continues it.
Below is a snapshot of the jsc run of script.js. I pasted and circled the obfuscated strings and the decoded pieces. Note the url listed matches the browser shot up above.
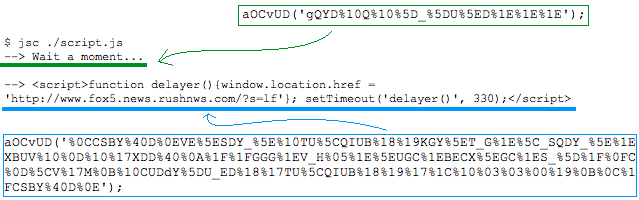
In summary, my diagnosis of the original email and sample with the clickable link, is it is only a spoofed email and intended to be spam. I humbly encourage all to offer any feedback to counter my assessment or offer any added value to it. Many thanks to Lode V. for sending it in!
-Kevin
--
ISC Handler on Duty

Comments