Rich Quick Make Money!
Based on reader reports (thanks Fred!) it looks like some carefully crafted spam is making its way past filters at the moment. The spams have content like
To all of my friends who didn't have the a moment to watch me on the channel-20 news last Tuesday talking about my blog, and financial accomplishments. I'm forwarding you the News Article, so you can read the whole story on how I became financially independent and wealthy. hxxp://r,turn,com/r/formclick/id/Ln5c6GsFyTbGgAsAbQABAA/url/%68%74%74%70%3a%2f\%6a%2e%6d%70/TSQHMO?djyna
I'm using hxxp and , instead of . to keep the domains from becoming clickable .. and to hopefully keep your spam/virus filter from panicking belatedly over this ISC diary instead of over the real spam earlier :)
We first expected some sort of Fake AV malware campaign, but it looks like the site "only" pushes the latest work-at-home-get-rich-quick scam. At least for the moment. Looking at the URL closely, here's what's going down: r,turn,com has an open redirect. The bad guys use this as a trampoline to bounce whoever clicks on the link to the next stage.
"%68%74%74%70%3a%2f\%6a%2e%6d%70" is really only hexadecimally encoded ASCII, and translates to "hxxp:/\j,mp", so the next stage is hxxp://j,mp/TSQHMO?djyna.
There, we get a redirect to hxxp://wallyplanet,info/fizo.htm?33722, where we get a file that contains window.location = "hxxp://bit,ly/Vn3lWj". Which redirects to hxxp://picklecook,us/fizo2.htm, where we get a file that contains window.location = "hxxp://CNBC-20NEWS,NET/momstory294b.htm", where we finally get the sob story and the get-rich-quick scam.
I doubt the spam filters follow this mess all the way, hence the URL reputation score in the spam filters apparently got tricked, and let the email through.
Comodo DNS hiccup on usertrust.com
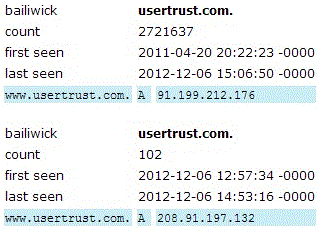
We received a report from a reader (thanks Marco!) that earlier today, "usertrust.com", a domain used by Comodo CA, apparently was pointing elsewhere for a while. From information captured by passive DNS sensors, it indeed looks like the NS records were changed to "ns1.pendingrenewaldeletion.com" and the A records were changed to point to 208.91.197.132, both indicative of a domain that has been "parked" by Network Solutions. Two hours later, the DNS records were updated again, and pointed back to Comodo. Given that the registration record on Network Solutions' WHOIS shows a renewal date of December 5 for the usertrust.com domain, it is probably fair to assume that "something" went wrong in the renewal.
Fake tech support calls - revisited
Back when this scam started to become "popular", the caller usually claimed to be from Microsoft or any other large well known techie company, and tried to talk the person answering into running some commands or programs on the PC "in order to fix a critical problem". But the latest twist of this scam seems to get more targeted: We have had two reports of fake tech support calls where the caller claimed to be representing the firm to which the called company had in fact outsourced its IT Support.
This isn't really rocket science on the attackers' part - some basic internet searches will give them lots of press releases and marketing blah where service providers tout their success in winning over a big support contract for company XYZ. I tried a search on my own based on one of the samples, and even found job postings where the service provider was explicitly looking for techies to work on the XYZ account. Next, I went on a LinkedIn search to find techies working for the service provider, and filtered to discover if any were connected to anyone at company XYZ. Not surprisingly, there were quite a few. Stuff like this is a gold mine for phishers, social engineering, and fake tech support scammers.
There is little point though in trying to keep the Internet free from such information. Company XYZ might have been able to control what the marketing people of the service provider write about their "reference customer", but they can't really control who is connected to whom on social networks.
In terms of countermeasures, as a service provider, make sure you have an established way how your staff identifies itself to your customer. As a company with outsourced services, make sure there is a well defined conduit how the service provider interacts with your employees, that your employees are aware of this, and that there is a defined mechanism (known call back number, etc) in place to verify a call if your employees have any doubt.
Please report fake tech support calls on https://isc.sans.edu/reportfakecall.html
How to identify if you are behind a "Transparent Proxy"
Traveling a lot? You may still be one of the unlucky few who not only connects to hotel networks regulary, but doesn't have easy access to a VPN to bypass all the nastyness they introduce. In addition, even some "normal" ISPs do introduce a feature called "transparent proxy" to manage traffic. Transparent proxies are nice in that they are easy to setup up and invisible ("transparent") to the user. However, the browser isn't aware of them, and as a result the transparent proxy even if configured non-malicious can still cause confusion bout the same origin policy browser depend on to isolate web sites from each other.
A transperent proxy works in conjunction with a firewall. The firewall will route traffic to the proxy, but changing the desitination IP address of the packet to the proxy's IP address. The proxy now relies on the "Host" header to identify the target site. As a result, the relationship between IP address and host name that the client established is lost.
There is a pretty simple test to figure out if you are behind a simple transparent proxy: Telnet to a "random" IP address (e.g. 192.0.2.1) on port 80. Then, copy/past a simple HTTP request, that includes the host header (the part you type is shown in bold font:
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter

Comments