MS12-020 RDP vulnerabilities: Patch, Mitigate, Detect
As a follow up to the fact the we've raised the INFOCON level to yellow for MS12-020, a step not taken lightly, it was suggested that we offer a few simple things folks can do to ensure that they're patched appropriately, as well as employ possible mitigations and detection.
INFOCON Yellow - Microsoft RDP - MS12-020
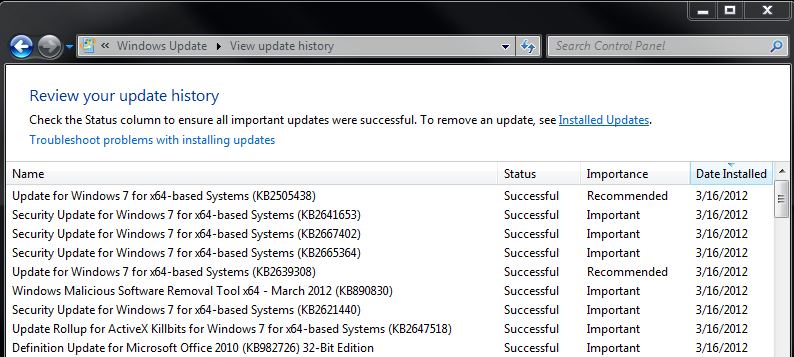
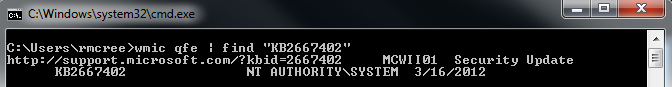
As we feared the MS12-020 bulletin from last black Tuesday caused a race for finding an exploit.
The last few evolutions in that process cause our worries to increase significantly. In order to help raise awareness and call administrators to action, we're raising our INFOCON to YELLOW for 24 hours.
Some history:
- Luigi Auriemma found a problem on May 16th, 2011.
- Microsoft was warned on August 24th, 2011 working with TippingPoint's Zero Day Initiative
- Microsoft released bulletin MS12-020 on March 13th, 2012, crediting "Luigi Auriemma, working with TippingPoint's Zero Day Initiative, for reporting an issue described in MS12-020"
- Luigi Auriemma released his work on March 16th, 2012
Luigi wrote today: "now that my proof-of-concept is out (yeah rdpclient.exe is the poc written by Microsoft in November 2011 using the example packet I sent to ZDI) I have decided to release my original advisory and proof-of-concept packet written the 16 May 2011... full-disclosure as usual :)" and he released his analysis and exploit of the vulnerability.
This is expected to speed up the efforts of the bad guys significantly and gives those having exposed RDP services very little time to fix before it will get exploited somehow.
The clock is ticking, please consider:
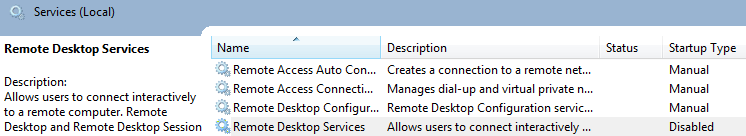
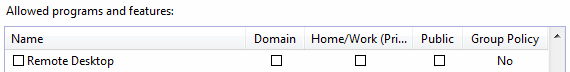
- block off RDP from all sources but those you absolutely need
- install the Microsoft patch
--
Swa Frantzen -- Section 66
VMware New and Updated Security Advisories
VMware issued the following security advisories:
VMware View privilege escalation and cross-site scripting (VMSA-2012-0004) [1] and VMware vCenter Server, Orchestrator, Update Manager, vShield, vSphere Client, ESXi and ESX address several security issues (VMSA-2012-0005) [2].
[1] http://www.vmware.com/security/advisories/VMSA-2012-0004.html
[2] http://www.vmware.com/security/advisories/VMSA-2012-0005.html
The following advisory has been updated:
VMware ESXi and ESX updates to third party library and ESX Service Console address several security issues (VMSA-2012-0001.1) [3]
[3] http://www.vmware.com/security/advisories/VMSA-2012-0001.html
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot edu

Comments