RTF files for Hancitor utilize exploit for CVE-2017-11882
Introduction
Malicious spam (malspam) pushing Hancitor malware (also known as Chanitor or Tordal) has been somewhat quiet since its last wave of 2017 on December 21st. During the holidays, Hancitor took a break. And in the first three weeks of 2018, I only saw one wave of Hancitor malspam that occurred on Wednesday 2018-01-10.
But on Tuesday 2018-01-23, we saw a new wave of Hancitor malspam. This time, links in the emails returned an RTF file that exploits CVE-2017-11882.
As usual, these waves of malspam are most often caught by spam filters, so few people will actually see the messages. And best security practices can easily prevent these infections from happening.
But we continue to see this malspam, so today's diary examines the infection traffic in my lab environment.
Chain of events
Operational characteristics of this campaign haven't changed much during the past few months. This campaign sends out waves of malspam using a different themed template each day it's active. Tuesday's theme spoofed eFax messages. Hancitor malspam has used variations on this eFax theme several times before.
Each email has a link to download a fake document. The result is most often a Microsoft Word document that has macros to run Hancitor. Once activated, Hancitor then downloads two or three additional items of malware. The additional malware is usually Pony, Evil Pony, and Zeus Panda Banker. Pony and Evil Pony stay resident in the infected host's memory (they're both file-less); however, I can always grab a copy of Zeus Panda Banker that's been saved to disk.

Shown above: A very simplified flow chart for Tuesday's infection chain.
Starting on 2017-11-21, I saw examples of the IcedID banking Trojan instead of Zeus Panda Banker on infected hosts in my lab environment. Further waves of Hancitor malspam switched back and forth between IcedID and Zeus Panda Banker. However, 2017-12-13 was the last time I saw IcedID banking Trojan during Hancitor infection traffic. It's consistently been Zeus Panda Banker since 2017-12-18.
At times, post-infection traffic will show another item of follow-up malware. In this diary's example, I also saw spambot malware. The malware caused my infected lab host to send out more Hancitor malspam. At least it tried to. The few successful SMTP connections from my infected host were flagged by the receiving mail servers, and no spam was actually sent.
In October 2017, we briefly saw Hancitor malspam utilizing Microsoft Word documents with the DDE attack technique. But after 10 days, it had gone back to using Word macros. I predict that, after trying out these RTF files, Hancitor malspam will go back to regular Word document macros in the near future.
CVE-2017-11882
The CVE-2017-11882 vulnerability was patched by Microsoft in November 2017. Since then, I've documented RTF files exploiting this vulnerability from malspam pushing malware like Loki-Bot and Formbook. By now, exploits for this vulnerability are old news, and more than 1,000 samples have been submitted to VirusTotal since November 2017.
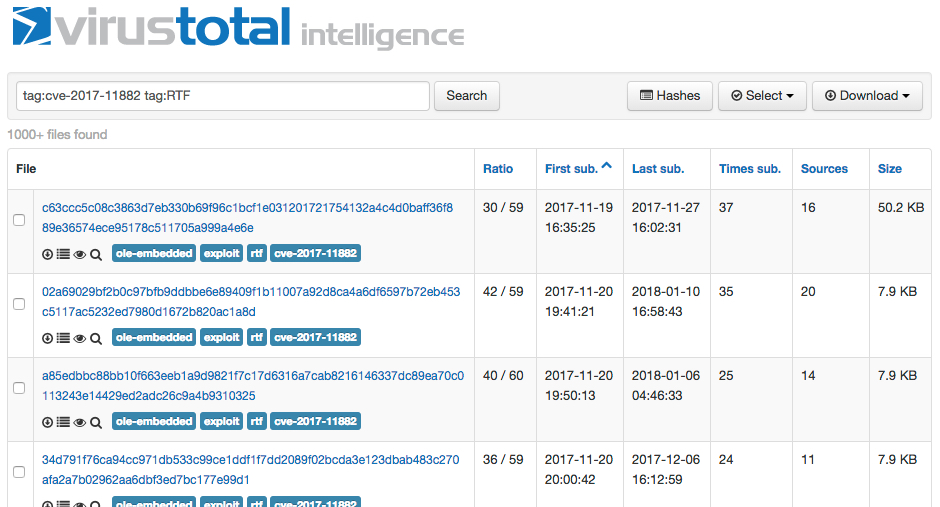
Shown above: VirusTotal stopped counting after 1,000.
Tuesday's wave of malspam
Below is a screenshot from an example of Hancitor malspam on Tuesday 2018-01-23.
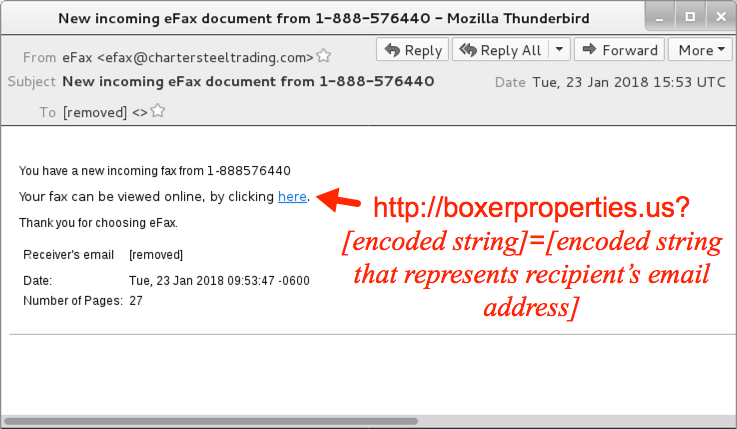
Shown above: Hancitor malspam example.
Prior to December 2017, URLs in the malspam's message text included base64 encoded strings representing the recipient's email address. Sometimes, they were just plain text. However, since early December 2017, URLs in the message text have been using a custom encoding that I haven't figured out yet.
The email link returned an RTF file disguised as a Word document using the .doc file extension.
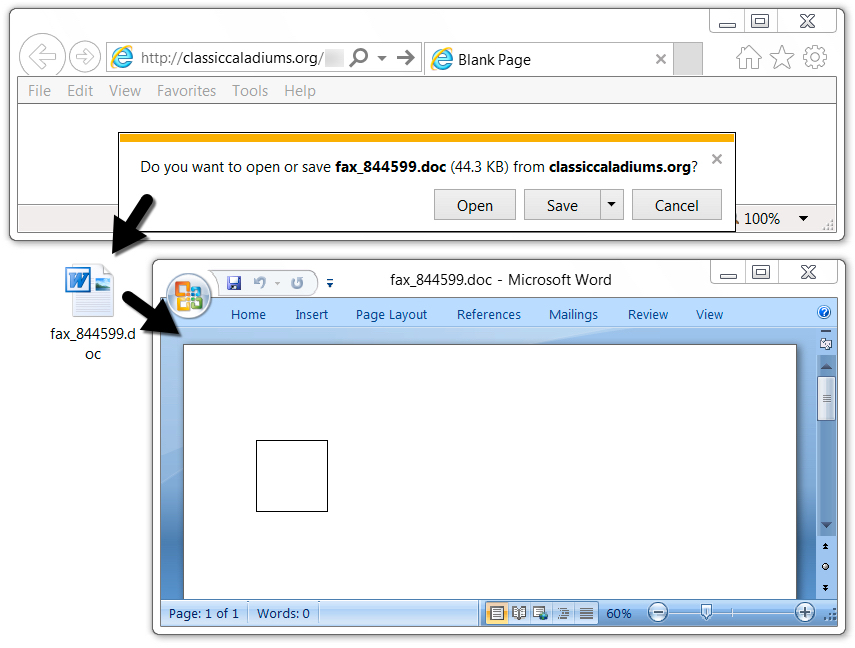
Shown above: Downloading Tuesday's Hancitor RTF document.
Network traffic
I opened the RTF file using Microsoft Word on a vulnerable Windows 7 host, and it automatically retrieved the Hancitor binary and started the infection process. The Hancitor binary was encoded as a base64 string in script returned from ofthi.com. See the image below for details.
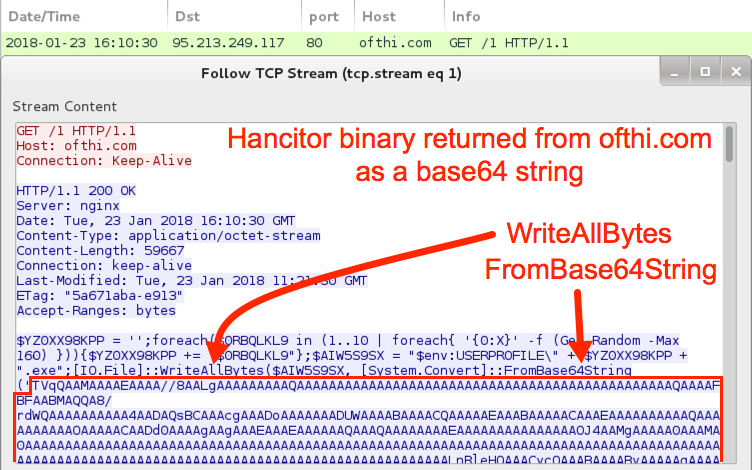
Shown above: Opening the RTF in Word caused this HTTP request.
Otherwise, traffic looked very similar to Hancitor infections I've documented numerous times in recent months.
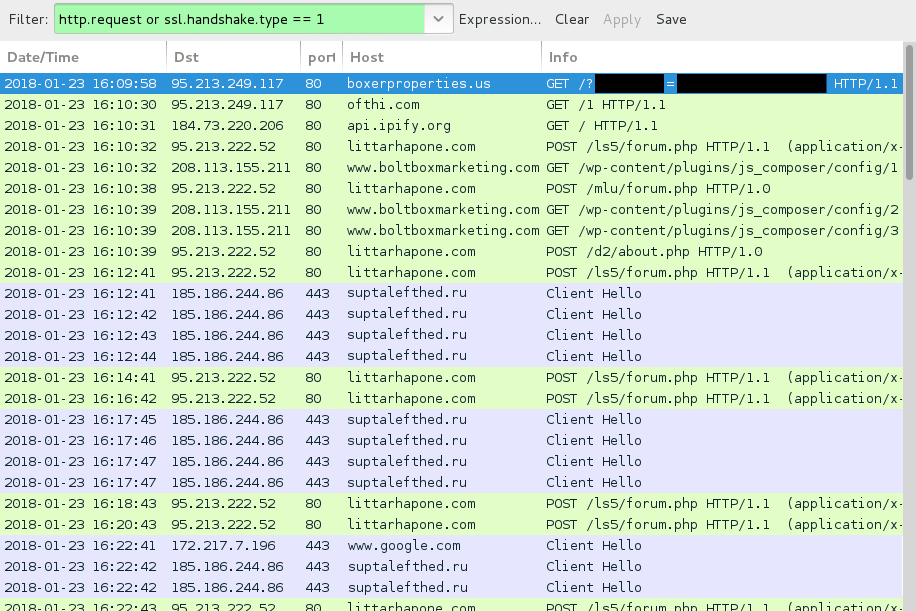
Shown above: Hancitor infection traffic filtered in Wireshark.
As I mentioned earlier, in this infection, I saw another item of malware sent to my infected lab host. It was spambot malware based on the Send-Safe bulk mailer. After this malware came across, my infected host generated indicators for Send-Safe, and I saw plenty of attempts at SMTP.

Shown above: Send-Safe based spambot malware sent during the post-infection traffic.
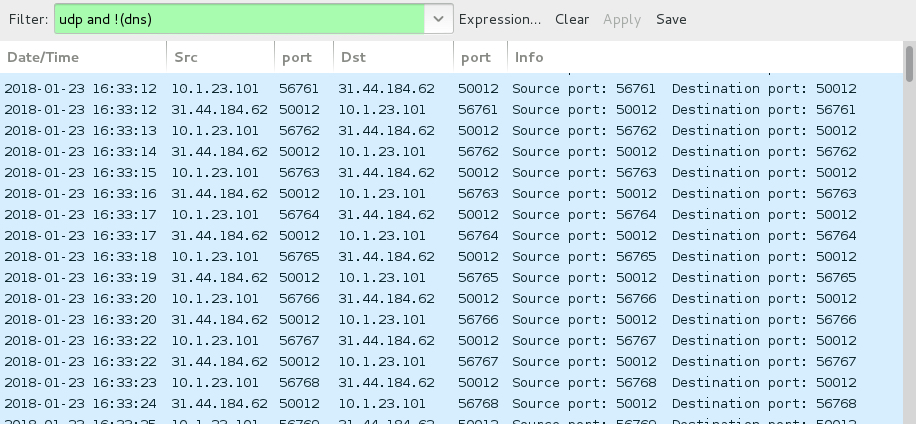
Shown above: Send-Safe Enterprise Mailer UDP beacon traffic over port 50012.
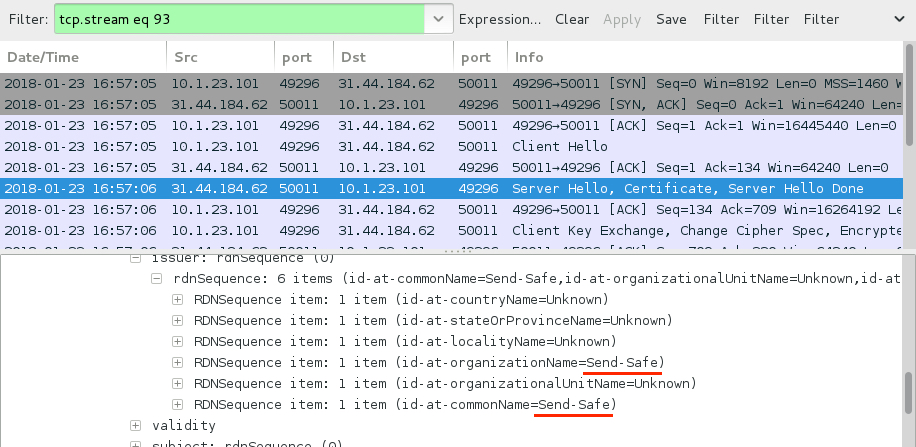
Shown above: Send-Safe SSL traffic over TCP port 50011.

Shown above: Some of the many email-related DNS queries and SMTP attempts over TCP port 25.
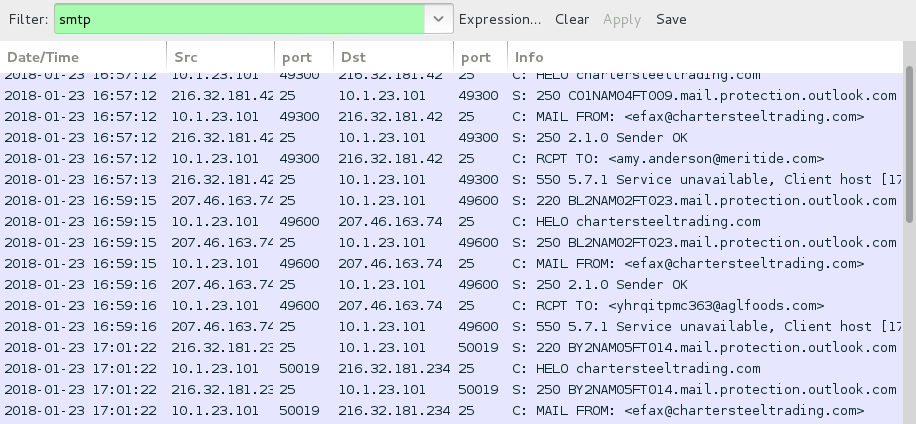
Shown above: SMTP traffic from my infected lab host. No actual emails were sent.

Shown above: Some alerts seen in Security Onion on Sguil using Suricata and the EmergingThreats Pro (ETPRO) ruleset.

Shown above: Some alerts seen in Snort 2.9.11.1 focusing on CVE-2017-11882 using the Snort subscriber ruleset.
Forensics on the infected host
I checked my infected Windows host to see what artifacts remained after the computer had been infected for a while. I found Zeus Panda Banker in its usual location, and the Send-Safe spambot malware EXE was in a folder under the user's AppData\Local\Temp directory.

Shown above: Zeus Panda Banker persistent on the infected Windows host.
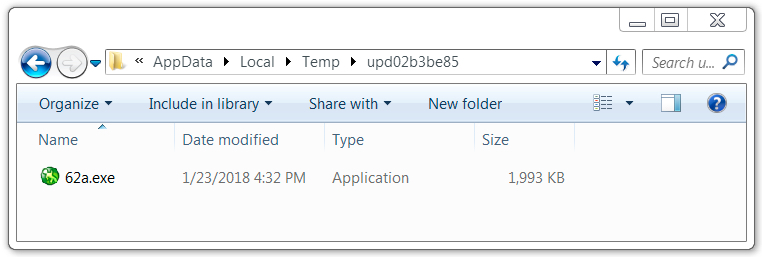
Shown above: Send-Safe spambot malware on the infected Windows host.
Indicators
I collected 30 emails from Tuesday's wave of malspam. The malspam spoofed chartersteeltrading.com as a sender, but that company is not involved with this malspam at all. Details on these emails follow.
- Date/Time: Tuesday 2018-01-23 as early as 15:27 UTC through at least 19:26 UTC
- Sending email address (spoofed): "eFax" <efax@chartersteeltrading.com>
IP addresses for the sending hosts (hostname spoofed):
- Received: from chartersteeltrading.com ([24.172.35.186])
- Received: from chartersteeltrading.com ([24.209.225.196])
- Received: from chartersteeltrading.com ([24.229.13.112])
- Received: from chartersteeltrading.com ([24.240.249.177])
- Received: from chartersteeltrading.com ([50.243.250.42])
- Received: from chartersteeltrading.com ([65.119.133.234])
- Received: from ([67.185.30.14])
- Received: from chartersteeltrading.com ([69.168.10.171])
- Received: from chartersteeltrading.com ([69.68.213.2])
- Received: from chartersteeltrading.com ([69.85.138.250])
- Received: from chartersteeltrading.com ([72.87.95.7])
- Received: from chartersteeltrading.com ([73.139.187.123])
- Received: from chartersteeltrading.com ([73.204.111.182])
- Received: from chartersteeltrading.com ([74.193.124.128])
- Received: from chartersteeltrading.com ([74.205.144.158])
- Received: from chartersteeltrading.com ([89.105.112.225])
- Received: from chartersteeltrading.com ([96.33.255.179])
- Received: from chartersteeltrading.com ([96.93.239.202])
- Received: from chartersteeltrading.com ([97.64.237.178])
- Received: from chartersteeltrading.com ([97.88.126.215])
- Received: from chartersteeltrading.com ([162.212.89.158])
- Received: from chartersteeltrading.com ([170.82.209.179])
- Received: from chartersteeltrading.com ([174.50.105.120])
- Received: from chartersteeltrading.com ([174.50.253.185])
- Received: from chartersteeltrading.com ([172.116.233.29])
- Received: from chartersteeltrading.com ([174.140.111.81])
- Received: from chartersteeltrading.com ([184.69.39.44])
- Received: from chartersteeltrading.com ([204.98.126.34])
- Received: from chartersteeltrading.com ([205.207.125.4])
- Received: from chartersteeltrading.com ([216.174.116.246])
Subject lines:
- Subject: New incoming eFax document from 1-888-054543
- Subject: New incoming eFax document from 1-888-054867
- Subject: New incoming eFax document from 1-888-058404
- Subject: New incoming eFax document from 1-888-065263
- Subject: New incoming eFax document from 1-888-082230
- Subject: New incoming eFax document from 1-888-104320
- Subject: New incoming eFax document from 1-888-125841
- Subject: New incoming eFax document from 1-888-133424
- Subject: New incoming eFax document from 1-888-151448
- Subject: New incoming eFax document from 1-888-158888
- Subject: New incoming eFax document from 1-888-174616
- Subject: New incoming eFax document from 1-888-200502
- Subject: New incoming eFax document from 1-888-243674
- Subject: New incoming eFax document from 1-888-282052
- Subject: New incoming eFax document from 1-888-315617
- Subject: New incoming eFax document from 1-888-484137
- Subject: New incoming eFax document from 1-888-567328
- Subject: New incoming eFax document from 1-888-570874
- Subject: New incoming eFax document from 1-888-576440
- Subject: New incoming eFax document from 1-888-577320
- Subject: New incoming eFax document from 1-888-607645
- Subject: New incoming eFax document from 1-888-662207
- Subject: New incoming eFax document from 1-888-701147
- Subject: New incoming eFax document from 1-888-704704
- Subject: New incoming eFax document from 1-888-724271
- Subject: New incoming eFax document from 1-888-733843
- Subject: New incoming eFax document from 1-888-828665
- Subject: New incoming eFax document from 1-888-855238
- Subject: New incoming eFax document from 1-888-877866
- Subject: New incoming eFax document from 1-888-886210
Links from the emails:
- boxerproperties.biz - GET /?[info redacted]=[info redacted]
- boxerproperties.info - GET /?[info redacted]=[info redacted]
- boxerproperties.org - GET /?[info redacted]=[info redacted]
- boxerproperties.us - GET /?[info redacted]=[info redacted]
- carolinecollective.cc - GET /?[info redacted]=[info redacted]
- classiccaladiums.info - GET /?[info redacted]=[info redacted]
- classiccaladiums.org - GET /?[info redacted]=[info redacted]
- classiccaladiumsllc.org - GET /?[info redacted]=[info redacted]
- eastlandmallcharlotte.com - GET /?[info redacted]=[info redacted]
- long-island-office-space.com - GET /?[info redacted]=[info redacted]
- subleaseofficehouston.com - GET /?[info redacted]=[info redacted]
- tabconstructioninc.com - GET /?[info redacted]=[info redacted]
- tabrrinc.com - GET /?[info redacted]=[info redacted]
- tabrs.com - GET /?[info redacted]=[info redacted]
- thesublease.com - GET /?[info redacted]=[info redacted]
URL to retrieve the Hancitor binary that returned script with a base64 string:
- 95.213.249.117 port 80 - ofthi.com - GET /1
Post-infection traffic from my infected lab host:
- api.ipify.org - GET / (IP address check by the infected host, not inherently malicious)
- 95.213.222.52 port 80 - littarhapone.com - POST /ls5/forum.php
- 95.213.222.52 port 80 - littarhapone.com - POST /mlu/forum.php
- 95.213.222.52 port 80 - littarhapone.com - POST /d2/about.php
- 208.113.155.211 port 80 - www.boltboxmarketing.com - GET /wp-content/plugins/js_composer/config/1
- 208.113.155.211 port 80 - www.boltboxmarketing.com - GET /wp-content/plugins/js_composer/config/2
- 208.113.155.211 port 80 - www.boltboxmarketing.com - GET /wp-content/plugins/js_composer/config/3
- 185.186.244.86 port 443 - suptalefthed.ru - HTTPS/SSL/TLS traffic from Zeus Panda Banker
- 27.124.124.97 port 80 - yoyostudy.com.au - GET /62a.exe (Send-Safe spambot malware)
- 31.44.184.62 port 50011 - Send-Safe SSL traffic
- 31.44.184.62 port 50012 - Send-Safe Enterprise Mailer UDP beacon traffic
Associated malware:
SHA256 hash: 6dcbf652b96a7aea16d0c2e72186173d9345f722c9592e62820bcfe477b2b297
- File size: 45,375 bytes
- File name: fax_518506.doc
- File description: From link in email text - RTF file with exploit for CVE-2017-11882
SHA256 hash: 2c506742267dd9d41dc62f2614f6306458da185230fb46cb467c98a8f48317a4
- File size: 44,544 bytes
- File location: hxxp://ofthi.com/1 (base64 string portion of the script)
- File description: Hancitor binary decoded from base64 string in script returned by ofthi.com
SHA256 hash: 8418887655f69ab5a61915bad2af633462760b128d38f53911da020d70e4862e
- File size: 159,744 bytes
- File location: C:\Users\[username]\AppData\Roaming\[existing directory path]\[random file name].exe
- File description: Zeus Panda Banker
SHA256 hash: 42b02d621696ec33e9140fedcf8b48695059595f9469dbf28daf4667ac0d214f
- File size: 2,040,320 bytes
- File location: hxxp://yoyostudy.com.au/62a.exe
- File location: C:\Users\[username]\AppData\Local\Temp\upd02b3be85\62a.exe
- File description: Follow-up malware (Spambot malware based on Send-Safe)
Block list
As always, indicators are not a block list. If anyone's inclined to web traffic, I suggest the following domains and URLs. Keep in mind many of these may have been taken off-line by the time you read this.
boxerproperties.info
boxerproperties.org
boxerproperties.us
carolinecollective.cc
classiccaladiums.info
classiccaladiums.org
classiccaladiumsllc.org
eastlandmallcharlotte.com
long-island-office-space.com
subleaseofficehouston.com
tabconstructioninc.com
tabrrinc.com
tabrs.com
thesublease.com
ofthi.com
hxxp://www.boltboxmarketing.com/wp-content/plugins/js_composer/config/1
hxxp://www.boltboxmarketing.com/wp-content/plugins/js_composer/config/2
hxxp://www.boltboxmarketing.com/wp-content/plugins/js_composer/config/3
littarhapone.com
suptalefthed.ru
hxxp://yoyostudy.com.au/62a.exe
Final words
As always, the standard disclaimer applies: Hancitor is really no more dangerous than other types of malspam we see on a daily basis. This malware is for Windows systems, but Windows 10 hosts seem well-protected against this threat. Even with the switch to RTF files exploiting CVE-2017-11882, I don't think this campaign is much more of a threat now than it was before. Why? Because spam filters seem to detect and block this malspam fairly easily.
The detection rate on the RTF files is a bit lower than I've seen before on previous Hancitor-related Word documents. Today's RTF sample was 12 of 57 when I checked VirusTotal on 2018-01-24 at 00:32 UTC. However, most of the infrastructure on these campaigns is quickly detected, and the associated hosting providers usually take most of it off-line within hours of discovery.
As always, properly-administered Windows hosts are unlikely to get infected. For older versions of Windows, system administrators and the technically inclined can implement best practices like Software Restriction Policies (SRP) or AppLocker to prevent these types of infections.
Pcap and malware samples for today's diary can be found here.
Finally, thanks to the security professionals on Twitter who share indicators and discuss these waves of malspam in near-real-time. Here is a Twitter search to help you find more information and indicators for recent Hancitor activity.
---
Brad Duncan
brad [at] malware-traffic-analysis.net



Comments
Anonymous
Jan 25th 2018
7 years ago