Malspam pushes GuLoader for Remcos RAT
Introduction
Malicious spam (malspam) pushing GuLoader malware has been around for over a year now. GuLoader is a file downloader first observed in December 2019, and it has been used to distribute a wide variety of malware, especially malware based on remote administration tools (RATs). I wrote a blog last year examining malspam using GuLoader for Netwire RAT. And GuLoader activity has continued since then.
Today's diary reviews a case of malspam pushing GuLoader for Remcos RAT on Tuesday 2021-02-23.
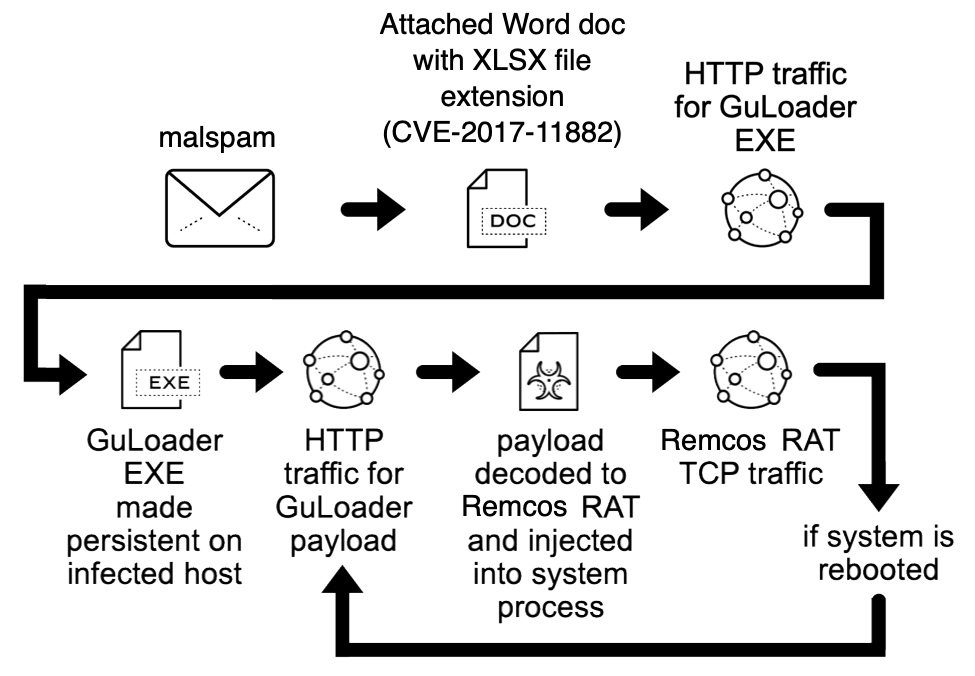
Shown above: Flow chart for the Remcos RAT infection reviewed in today's diary.
The malspam
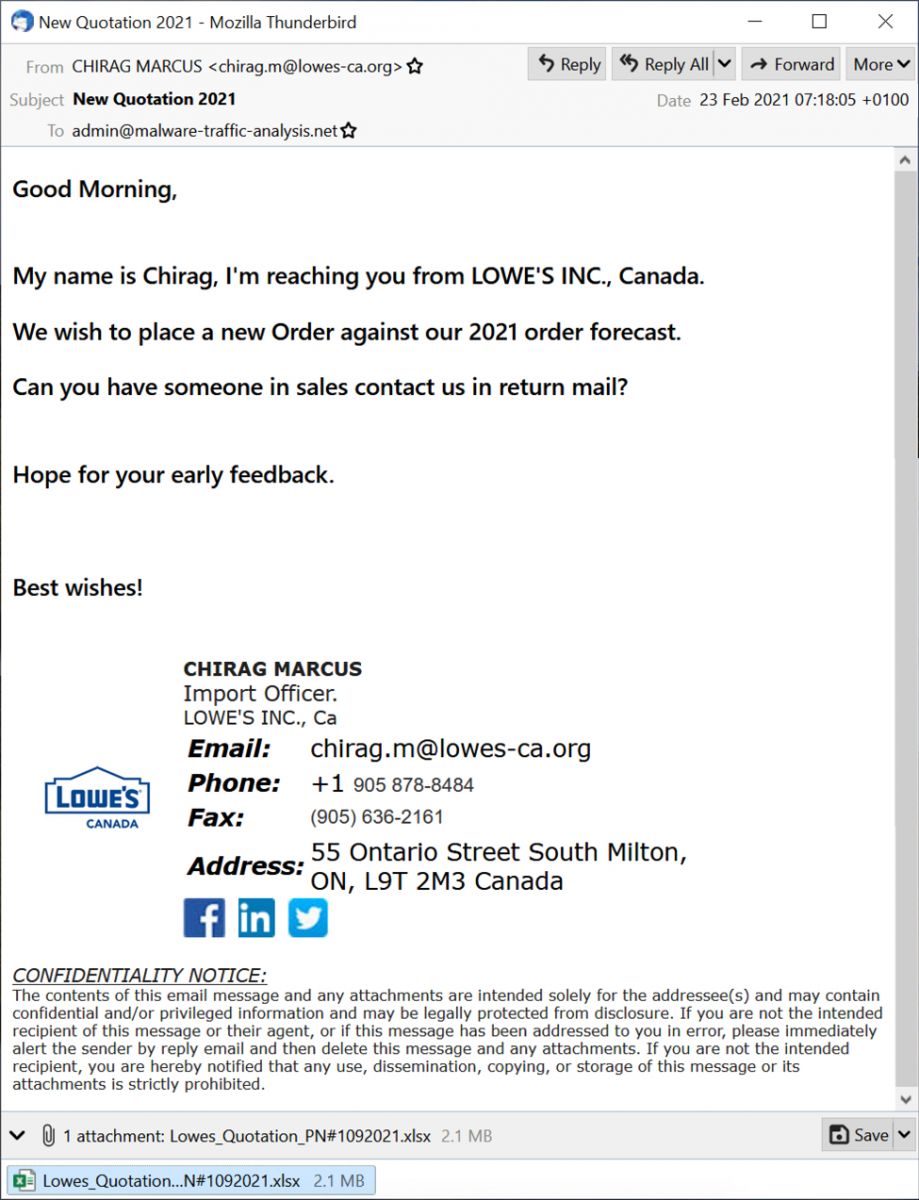
Shown above: Screenshot of the malspam.
The malspam is supposedly from someone in Lowes from Canada. Below are some email headers associated with this message.
Date: 23 Feb 2021 07:18:05 +0100
From: CHIRAG MARCUS <chirag.m@lowes-ca.org>
Subject: New Quotation 2021
Message-ID: <20210223071804.247143D567E6DCFA@lowes-ca.org>
As noted above, the sender is supposedly from lowes-ca.org, but this site is not associated with Lowes. That domain has an open directory for its web server, and it seems like it's being used for malicious purposes.
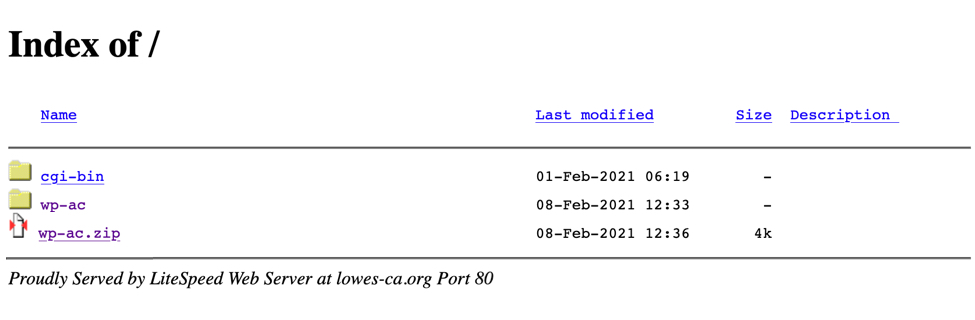
Shown above: Lowes-ca.org when viewed in a web browser.
The attachment
I opened the attachment in my lab, but I was on a Windows 10 host running a recent version of Microsoft Office. Initially, I didn't realize this was a document with an exploit targeting CVE-2017-11882. I had to switch to an older Windows 7 host to get an infection.
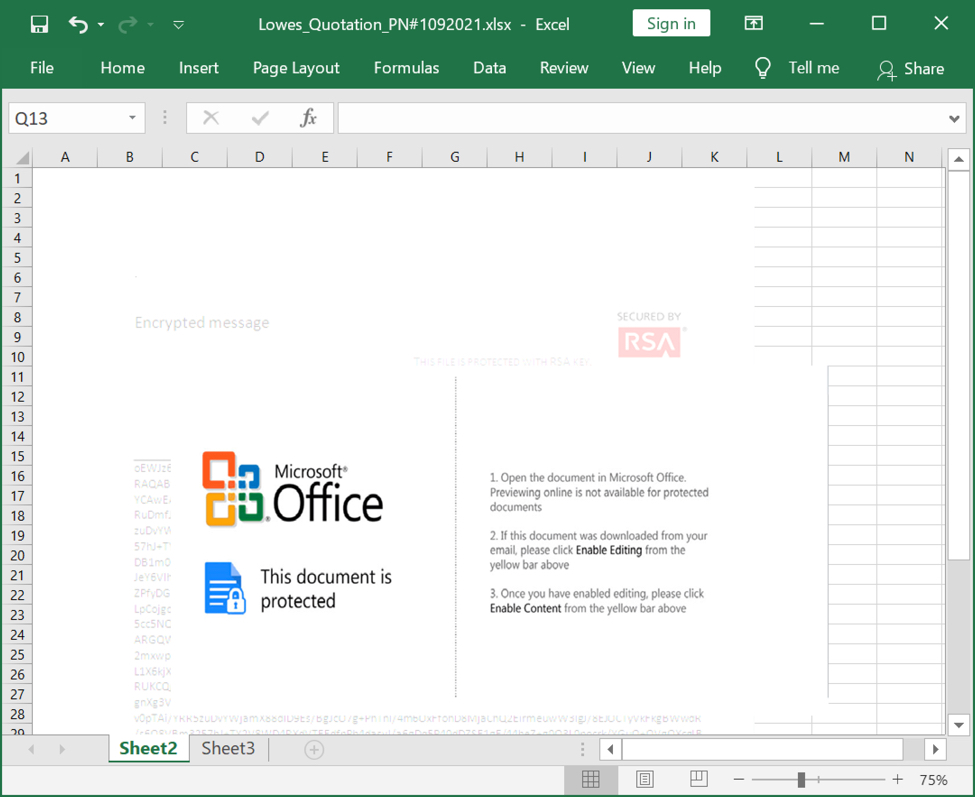
Shown above: Screenshot of the attachment opened in Excel.
The infection traffic
Infection traffic was typical for what I've seen with previous GuLoader infections for some sort of RAT-based malware. In this case, the infected Windows host was unable to establish a TCP connection with the server used by this sample for Remcos RAT.
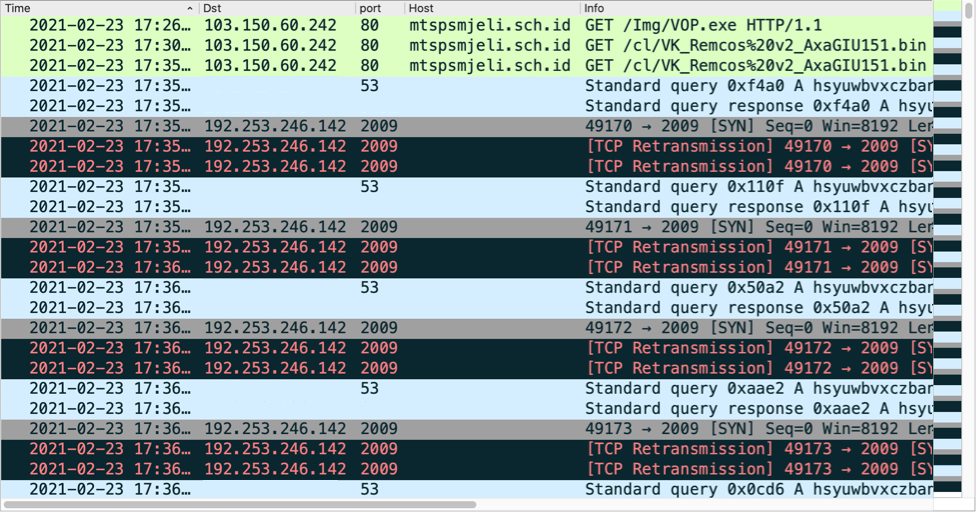
Shown above: Traffic from the infection filtered in Wireshark.
Forensics on the infected Windows host
The infected Windows host had GuLoader persistent on the infected host using a registry update. When rebooted, the GuLoader sample again retrieved the encoded binary for Remcos RAT.
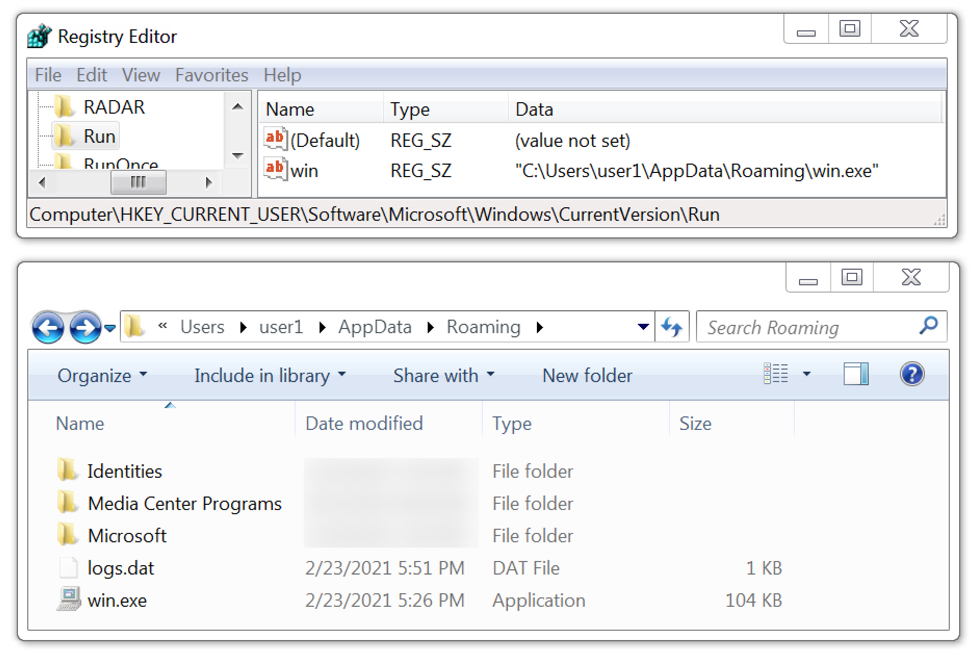
Shown above: GuLoader for Remcos RAT persistent on the infected Windows host.
Indicators of Compromise (IOCs)
Associated malware:
SHA256 hash: 21c4c697c6cba3d1d7f5ae5d768bf0c1d716eccc4479b338f2cf1336cf06b8ad
- File size: 2,231,808 bytes
- File name: Lowes_Quotation_PN#1092021.xlsx
- File description: Email attachment, Word doc with exploit for CVE-2017-11882
SHA256 hash: 6141efb6f1598e2205806c5a788e61c489440dfc942984ee1688bb68ad0f18df
- File size: 106,496 bytes
- File location: hxxp://mtspsmjeli.sch[.]id/Img/VOP.exe
- File location: C:\Users\[username]\AppData\Roaming\win.exe
- File description: Windows EXE, GUI Loader for Remcos RAT
Infection traffic:
GuLoader EXE retrieved through CVE-2017-11882 exploit:
- 103.150.60[.]242 port 80 - mtspsmjeli.sch[.]id - GET /Img/VOP.exe
GuLoader retrieves encoded data for Remcos RAT:
- 103.150.60[.]242 port 80 - mtspsmjeli.sch[.]id - GET /cl/VK_Remcos%20v2_AxaGIU151.bin
Remcos RAT post-infection traffic:
- 192.253.246[.]142 port 2009 - hsyuwbvxczbansmloiujdhsbnbcgywqauaghxvz.ydns[.]eu - attempted TCP connections
Final words
We continue to see new malware samples using exploits based on CVE-2017-11882 in the wild. This vulnerability is over 3 years old, and exploits targeting it are not effective against the most recent versions of Microsoft Windows and Office. The only reason we continue to see these new samples is because distributing exploits based on CVE-2017-11882 remains profitable. That means a substantial number of people still use outdated versions of Microsoft Office and/or Windows that are not properly patched or updated.
GuLoader has been a relatively a constant presence in our threat landscape since it was discovered in December 2019, so I expect we'll also continue to see new samples for various RAT-based malware in the weeks and months ahead.
---
Brad Duncan
brad [at] malware-traffic-analysis.net

Comments
People "use outdated versions of Microsoft Office and/or Windows that are not properly patched or updated" because (1) Microsoft put bugs in them in the first place and (2) Microsoft stopped supporting them. To use supported versions of Microsoft software generally (3) has an added monetary cost and (4) there are still bugs. In addition, (5) most new Microsoft software doesn't work like the old Microsoft software. This started when (6) Microsoft invented the "ribbon" and started "ribbonizing" things and (7) in Windows 10 even invalidated their own Microsoft software (examples: the wonderful and extremely useful MS-Office Shortcut Bar no longer works; Briefcase, which could be patched to work, can no longer even be patched to work; I had to change a Briefcase-based "app" to use ROBOCOPY so I could use it on a Windows 10 PC; note that Windows tells you XCOPY is deprecated and to switch to ROBOCOPY, so I broke down and learned ROBOCOPY; I also personally like and use Windows Sidebar, which still works in Windows 10, but I don't know for how long).
All companies work like this now. Apps are constantly updated. So it's not just Microsoft. But Microsoft makes it a habit of making incompatible changes. In Windows 10 I can't even make my desktop, windows, etc. even LOOK like Windows has looked for years. So I have to learn new visual cues, etc. I LIKED THE OLD LOOK, and cannot adjust it like in earlier versions of Windows! But, again, it's not just Microsoft. I read SANS NewsBites and browse SANS ISC, and there is never a shortage of "new and improved" apps that ultimately have bugs in them both in the logic of its function and the security of its use. It's an infinite loop. I don't know what to do to fix it (although I see recommendations in the various forums), but what ever really gets done? And if you happen to find something that works and you like it, sooner or later it will be decommitted or broken. The only way to get the functionality back that you want is to..."use outdated versions of [software]." My PCs are my tools, and I want them to work reliably well. And I don't want to have to "adapt" to every whim of every developer (who are in large part motivated by remuneration, i.e., money from me et al.). Stable functionality is all I want, and we just don't get that. Everything is in a state of flux unless you..."use outdated versions of [software]."
Anonymous
Feb 26th 2021
3 years ago