Is this a pentest?
Sometimes, when I'm analyzing malware, I think: this is probably part of a penetration test.
For example, until about a year ago, when I would analyze a malicious Office document with shellcode, there was a very high probability it was created by a penetration tester.
And it has happened too, that readers have submitted malware to the Internet Storm Center that turns out to be created for a penetration test. We inform them about this, and sometimes they will confirm later that it was indeed a pentest.
Just because it's a penetration test, doesn't mean that I'm halting my analysis. Depending on the context, I will take appropriate action. It has happened for example, that I obtained from the maldoc the domain name registered by the pentesters. In stead of blocklisting that domain, I would monitor it closely.
Have you uncovered a pentest? What did you do? Please post a comment.
Recently in my Twitter feed, I found a document with macros created to raise awareness.
It is not that difficult to analyze with oledump:
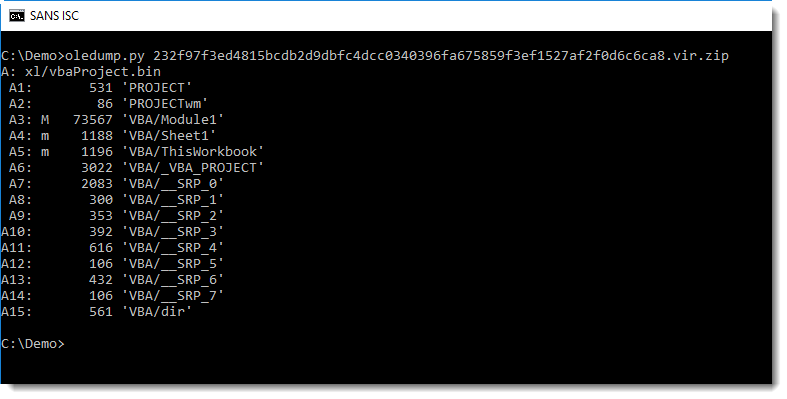
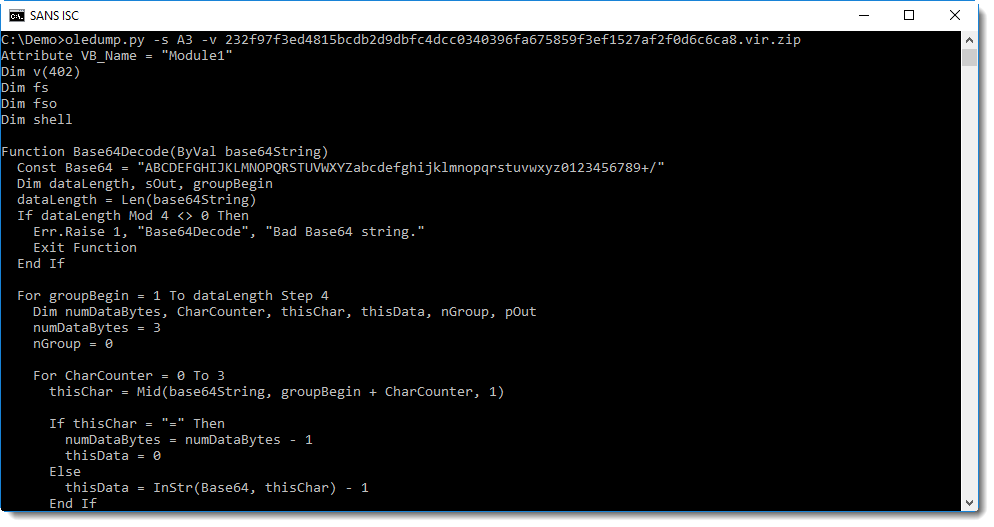
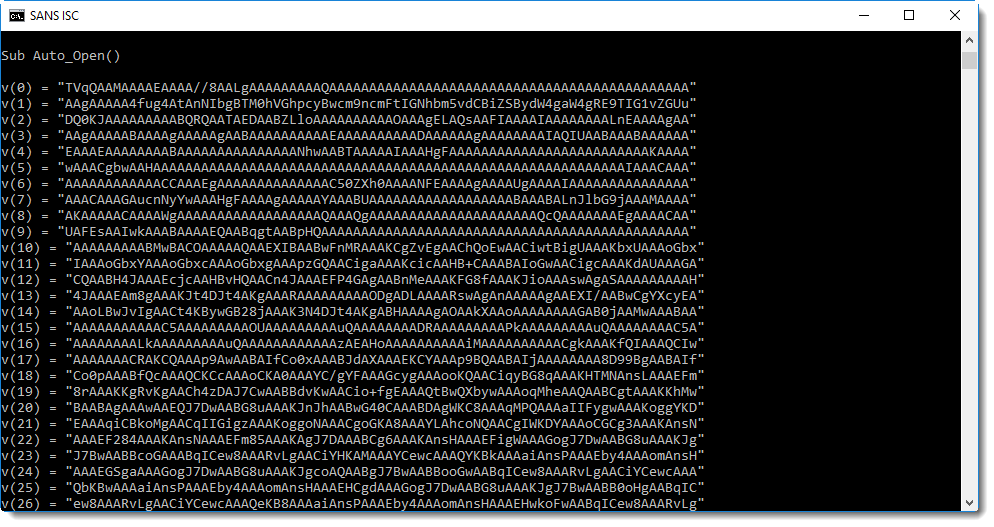
Yes, that's BASE64 that starts with TVqQ..., a strong indication that this is a Windows executable (MZ...).
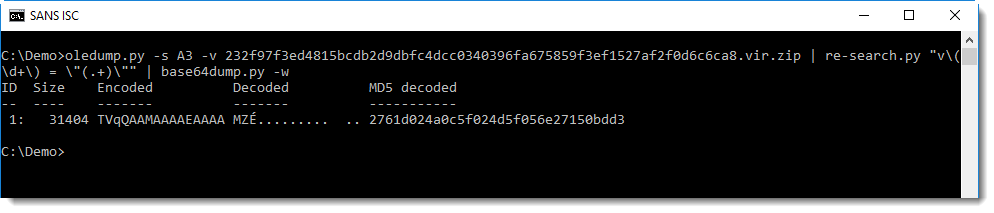
And it is indeed a Windows executable. It is a 32-bit .NET executable with name CERT_Lock:
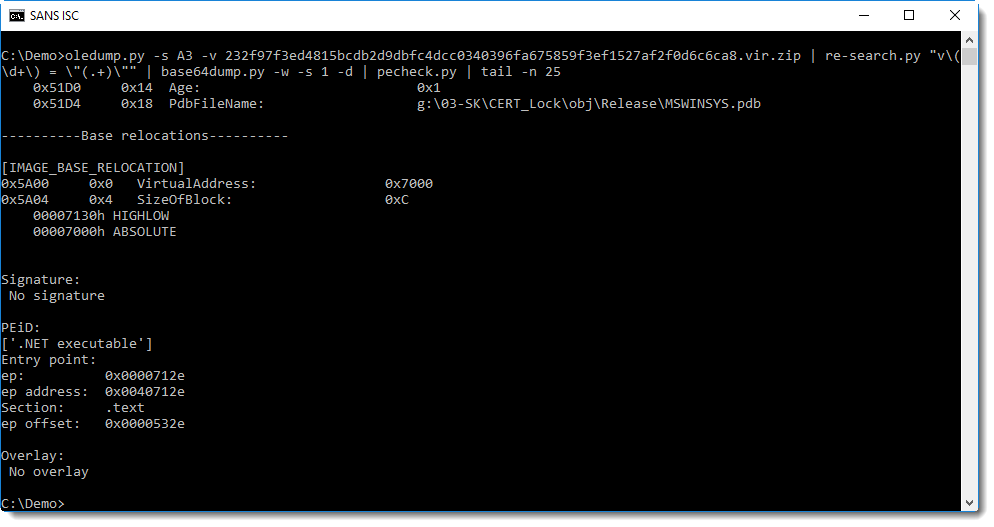
This .NET program will lock the computer screen for a couple of minutes and display phishing awareness messages in Slovak.
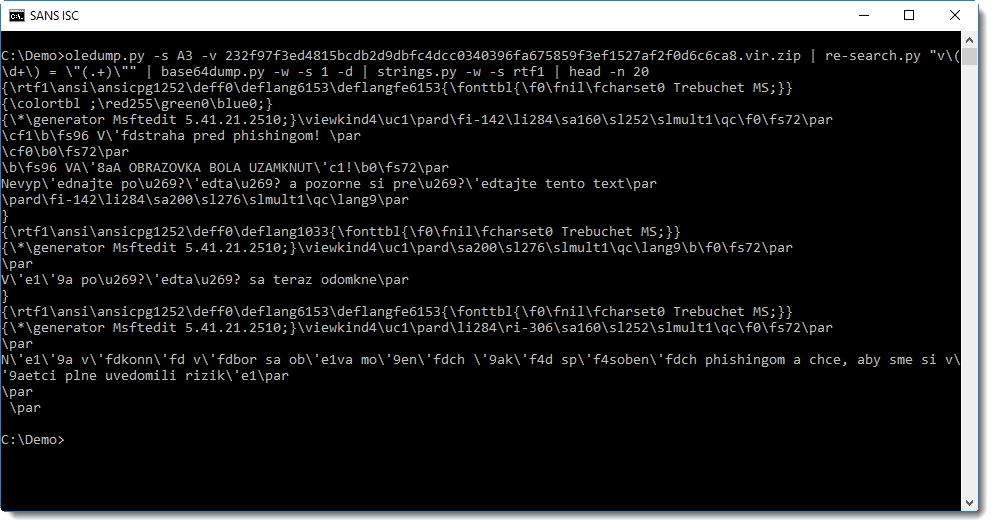
I think this was created for users that did not score high in awareness training quizes. Did you ever have to take such strong measures to raise awareness?
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com



Comments