Decoding the Patterns: Analyzing DShield Honeypot Activity [Guest Diary]
[This is a Guest Diary by Alex Rodriguez, an ISC intern as part of the SANS.edu BACS program]
Honeypots can be an effective means of discovering the variety of ways hackers target vulnerable systems on the Internet. The first thing you may ask yourself is, “What is a honeypot?” In short, it is a magnificent tool that can be attached to your home router and is designed to lure potential hackers into attacking it by pretending to be a vulnerable system. As part of my internship with the SANS Internet Storm Center, I have had the pleasure of setting up a honeypot and monitoring activity to assist me in identifying some of the trends hackers use to target vulnerable systems.
Monitoring activity on a honeypot usually entailed reviewing logs, which in my case meant combing through JSON-formatted, SSH and Web logs looking for activity that piqued my interest. According to my SSH logs, the honeypot captured 26171 IP addresses, 48548 Source Ports, 13201 Usernames, and 43794 Passwords between July 30, 2023, and October 30, 2023. Listed below are the Top 10 IPs, Ports, Usernames, and Passwords captured during the four-month period:
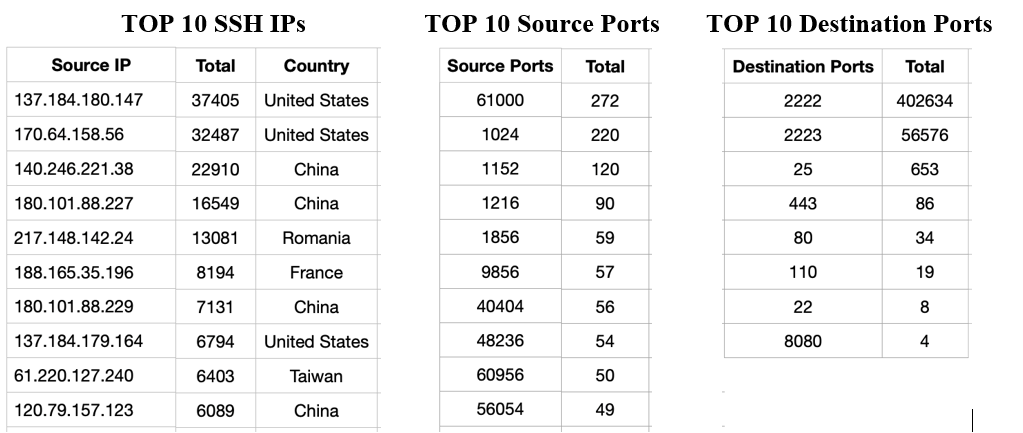
Although Port 1024 is within the user server range, Trojan activity has been associated with Port 1024 as indicated by the SANS Internet Storm Center:
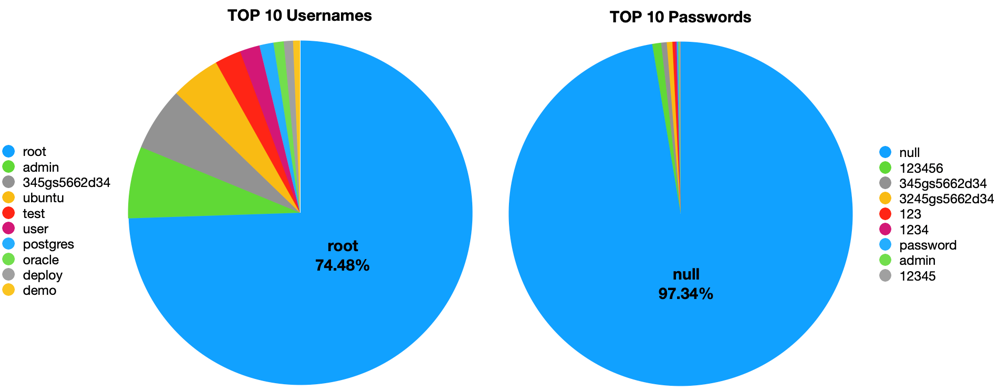

What is interesting about this login data is that the ratio between successful and failed logins is vastly different despite the total number of username and password combinations that were utilized. On the other hand, a change in simple password or default password usage would increase this disparity even more.
Commands Captured by Honeypot
During the same period, 27096 commands were captured on the honeypot. Listed below are the Top 10 commands seen during the period:
Top 10 Commands
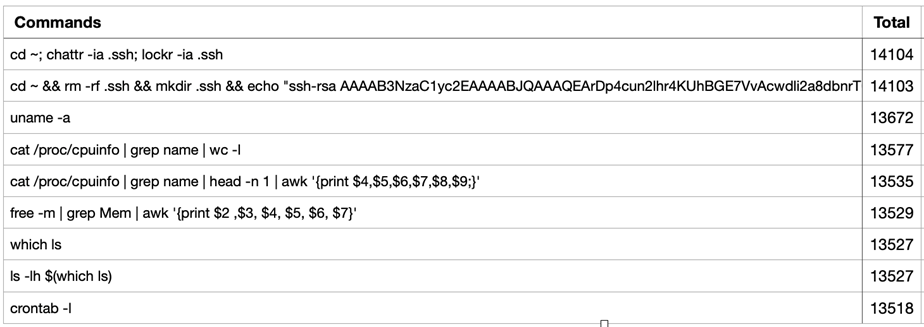
The most interesting commands listed above are the first two, as they are normally used together to help maintain system access once a system is compromised. The first command upon execution removes any attribute that would prevent overwriting the .ssh hidden file. The next command would effectively add an attacker’s own SSH public key to .ssh in authorized_keys, to maintain access:
cd ~ && rm -rf .ssh && mkdir .ssh && echo "ssh-rsa AAAAB3NzaC1yc2EAAAABJQAAAQEArDp4cun2lhr4KUhBGE7VvAcwdli2a8dbnrTOrbMz1+5O73fcBOx8NVbUT0bUanUV9tJ2/9p7+vD0EpZ3Tz/+0kX34uAx1RV/75GVOmNx+9EuWOnvNoaJe0QXxziIg9eLBHpgLMuakb5+BgTFB+rKJAw9u9FSTDengvS8hX1kNFS4Mjux0hJOK8rvcEmPecjdySYMb66nylAKGwCEE6WEQHmd1mUPgHwGQ0hWCwsQk13yCGPK5w6hYp5zYkFnvlC8hGmd4Ww+u97k6pfTGTUbJk14ujvcD9iUKQTTWYYjIIu5PmUux5bsZ0R4WFwdIe6+i6rBLAsPKgAySVKPRK+oRw== mdrfckr">>.ssh/authorized_keys && chmod -R go= ~/.ssh && cd ~
This command has been directly associated to the Outlaw Hacker Group by TrendMicro in 2018. Additional information concerning its usage and association with a Crypto-Botnet can be found by navigating to this site [1].
Uploaded Honeypot Files
Uploaded honeypot files are files uploaded to a honeypot by threat actors. These files can contain malware, exploits, backdoors, or other malicious content that can be analyzed to gain insights into the attacker's methods and intentions. During the four-month period, 8 binaries, a Bash shell script, and an empty file with the following SHA256 hash values were uploaded to the honeypot:
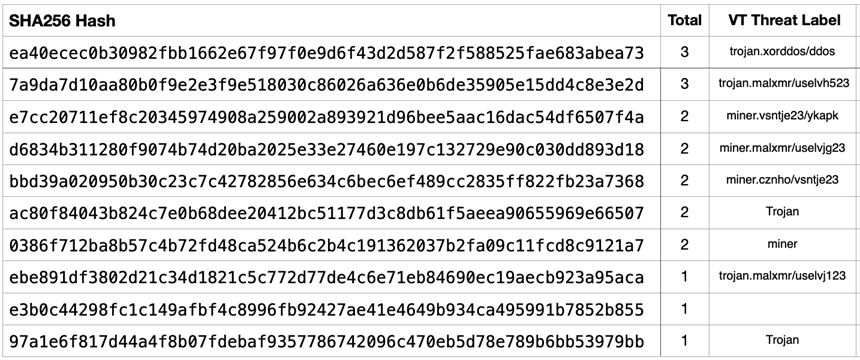
According to VirusTotal, 9 of the hashes listed above are all indicators of compromise, which consist of various Trojan and Miner families as well as a Bash shell script. The empty file with no threat label as indicated above is an empty file with zero bytes. In addition, this file has been categorized as stealer malware based on two Dynamic Analysis Sandbox Detections [3]. It seems interesting that even amongst the VirusTotal community there seems to be some debate as to whether this file is a threat. There is still not enough known about this file.
On the other hand, the XorDDoS Trojan listed above is well known and was first discovered by a white hat malware research group, MalwareMustDie [4]. The Trojan uses an XOR encryption key to encrypt all the data related to its execution. This Trojan is interesting as it has rootkit capabilities that infect Linux devices, transform them into zombies and subsequently controlled by attackers to execute malicious tasks remotely, including a DDoS attack.
In conclusion, honeypots provide a wealth of information that would be useful to cybersecurity professionals as they help identify both old and new emerging threats being used against systems on the Internet. While exploits will forever haunt our systems exposed to the Internet, simple configuration adjustments and continual patching of systems; as well as utilizing password complexity best practices could assist in thwarting successful attacks.
[1] https://yoroi.company/research/outlaw-is-back-a-new-crypto-botnet-targets-european-organizations/
[2] https://isc.sans.edu/diary/DShield+Honeypot+Activity+for+May+2023/29932
[3] https://www.virustotal.com/gui/file/e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855/detection
[4] https://blog.malwaremustdie.org/2015/09/mmd-0042-2015-polymorphic-in-elf.html
[5] https://www.sans.edu/cyber-security-programs/bachelors-degree/
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu

Comments