Ransomware & Entropy: Your Turn -> Solution
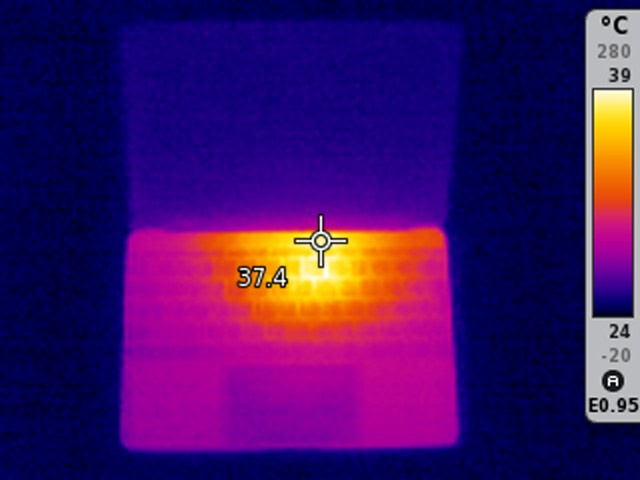
This is the image you can recover from the ransomed file I published in my last diary entry.
Let's use byte-stats to check the entropy of the ransomed file:
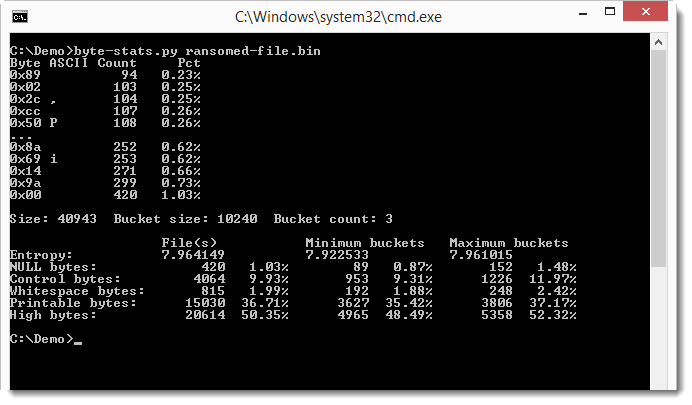
We don't see much difference between the overal entropy and the entropy of the buckets, but that's because it's a small file. Notice that only 3 buckets were used. The file is only 36KB, so let's use a smaller bucket size: 1024 bytes.
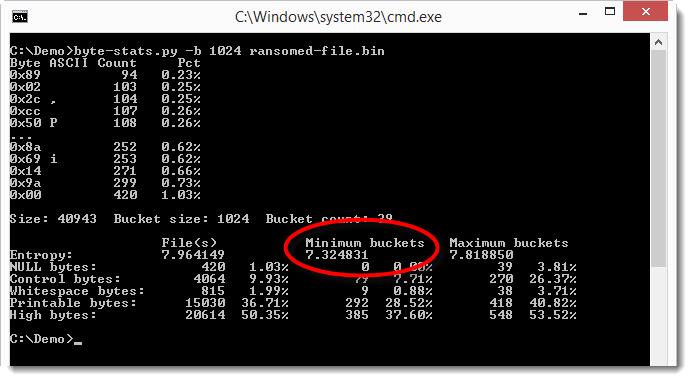
The smallest value for the entropy is 7.32... So we have something in this file that is not encrypted/compressed. Let's try to locate this:
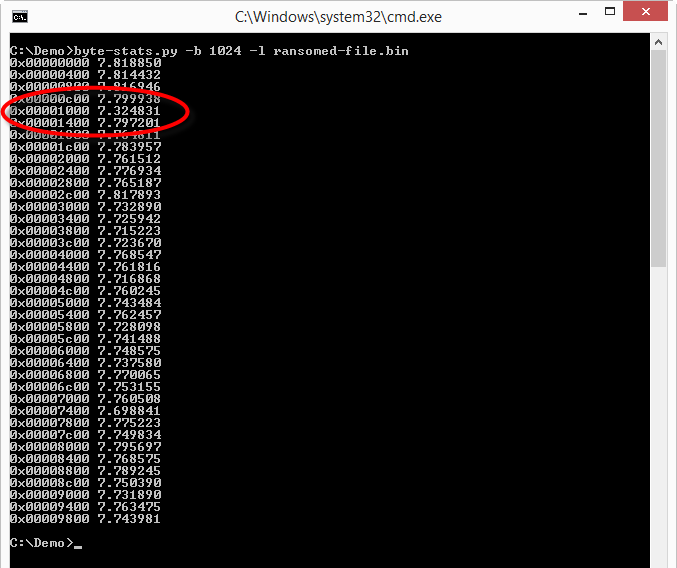
The lower entropy appears to be around position 0x1000. Let's take a look:
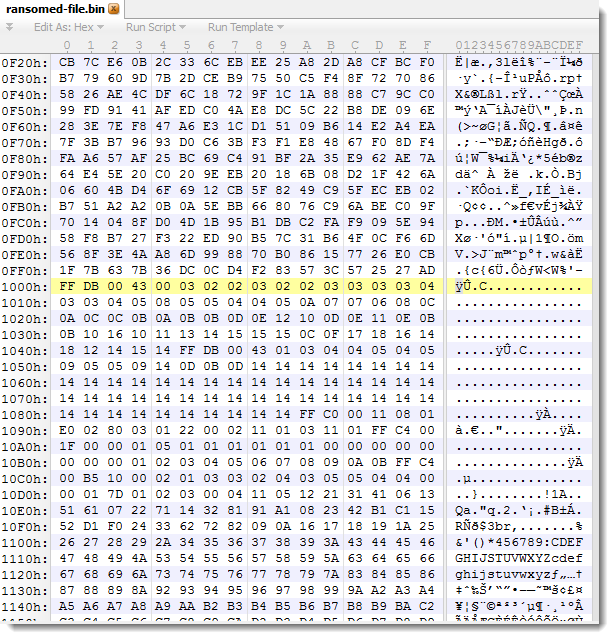
Bytes before 0x1000 look random, while we see some patterns appearing after 0x1000.
FFDB is the JPEG marker for quantization tables. This should be preceded by a JPEG header, like this one: \xFF\xD8\xFF\xE0\x00\x10\x4A\x46\x49\x46\x00\x01\x01\x01\x00\x48\x00\x48\x00\x00
To recover the image, just create a new file with this JPEG header and append all bytes from the ransomed file starting at the FFDB marker (position 0x1000).
What is this image? It's a thermal image of my MacBook 12" with the processor running "hot". The processor is located where you see the yellow/orange spot. The color indicates it's around 39°C. That's around 312°K and 102°F.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
IT Security consultant at Contraste Europe.


Comments