More Device Malware: This is why your DVR attacked my Synology Disk Station (and now with Bitcoin Miner!)
Update: Just found what looks like a bitcoin miner on the infected DVR. There are two more binaries. D72BNr, the bitcoin miner (according to the usage info based on strings) and mzkk8g, which looksl ike a simplar http agent, maybe to download additional tools easily (similar to curl/wget which isn't installed on this DVR by default). I will add these two files to https://isc.sans.edu/diaryimages/hikvision.zip shortly.
Last week, we reported that some of the hosts scanning for port 5000 are DVRs (to be more precise: Hikvision DVRs, commonly used to record video from surveillance cameras [1] ).
Today, we were able to recover the malware responsible. You can download the malware here https://isc.sans.edu/diaryimages/hikvision.zip (password: infected) .
The malware resides in /dev/cmd.so . A number of additional suspect files where located in the /dev directory which we still need to recover / analyze from the test system. The compromisse of the DVR likely happened via an exposed telnet port and a default root password (12345).
Analysis of the malware is still ongoing, and any help is appreciated (see link to malware above). Here are some initial findings:
- The malware is an ARM binary, indicating that it is targeting devices, not your typical x86 Linux server.
- The malware scans for Synology devices exposed on port 5000. The http request sent by the malware:
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
Malicious PDF sent in massive scam to Colombian users claiming to be from Credit score agency
We got reports for a massive scam sent to colombian users claiming to be from one of the two credit score agencies in Colombia. The agency is called Datacredito, affiliated to experian. The following e-mail was received:
.png)
This e-mail poses as an alert for a false negative report to the credit agency. It comes with an attached PDF with the following information:
The file does not show malicious payload when scanned by antimalware software. However, this file has a PDF structure. Ater using PDFStreamDumper for reviewing, the following interesting information appeared:
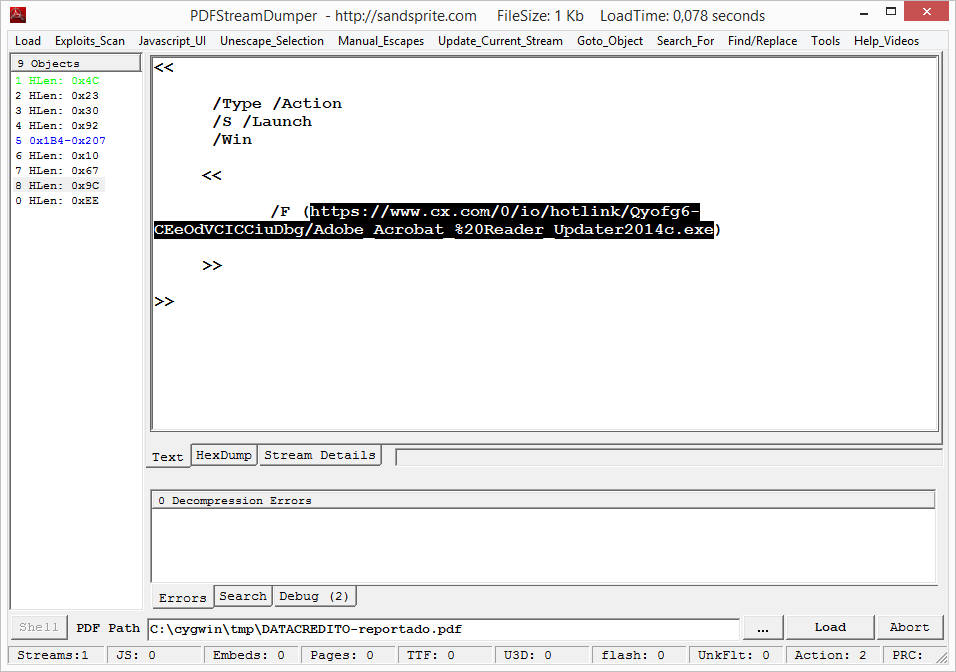
This PDF has malicious scripting, which instructs the reader to download and execute the URL shown in the previous URL. After downloading the file shown in that URL, which is live at this time, a keylogger is downloaded.
Malicious PDFs are still a problem. If you want to avoid falling into one of this scams, please remember the following:
- Have the last version of acrobat reader installed in your computer
- Do not open attachments from unknown sources
- Do not enable scripting in your acrobat reader configuration. Keep it turned off.
Manuel Humberto Santander Peláez
SANS Internet Storm Center - Handler
Twitter:@manuelsantander
Web:http://manuel.santander.name
e-mail: msantand at isc dot sans dot org
1 Comments
War of the Bots: When DVRs attack NASs
While looking at the latest honeypot data for what is happening with Synology devices, I did notice one particular agressive IP connecting to a number of our honeypot IPs. At first, I figured it may just be a new Shodan scan (got tons of them in the honeypot). But when I connected to port 443 using openssl, I saw a rather interesting SSL certificate being sent:
$ openssl s_client -connect a.b.c.d:443 CONNECTED(00000003) depth=0 C = CN, ST = ZheJiang, L = HangZhou, O = HIKVISION, OU = DVRNVR, CN = www.hikvision.com, emailAddress = menghong@hikvision.com verify error:num=18:self signed certificate verify return:1 depth=0 C = CN, ST = ZheJiang, L = HangZhou, O = HIKVISION, OU = DVRNVR, CN = www.hikvision.com, emailAddress = menghong@hikvision.com verify return:1 GET --- Certificate chain 0 s:/C=CN/ST=ZheJiang/L=HangZhou/O=HIKVISION/OU=DVRNVR/CN=www.hikvision.com/emailAddress=menghong@hikvision.com i:/C=CN/ST=ZheJiang/L=HangZhou/O=HIKVISION/OU=DVRNVR/CN=www.hikvision.com/emailAddress=menghong@hikvision.com
This certificate appears to be associated with a DVR sold in conjunction with security camera systems [1]. Usually these systems run some form of Linux, so I guess it is to expected that given a weak password, these systems get mistaken for a Linux server and exploited just like one.
Right now, if I am real lucky I may be able to get a hold of the owner of the DVR, but it looks like a Chinese residential IP so not getting my hopes up too high.
[1] http://www.hikvision.com/en/us/index.asp
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
0 Comments
Apple Credential Phishing via appleidconfirm.net
ISC user Craig Cox wrote in alerting us of a fairly sophisticated phishing campaign that is currently in progress. The website appleidconfirm.net has a seemingly realistic Apple login page that is being sent out by email.
The site even includes JavaScript code which validates your Apple ID as an email in an attempt to obtain only valid credentials.
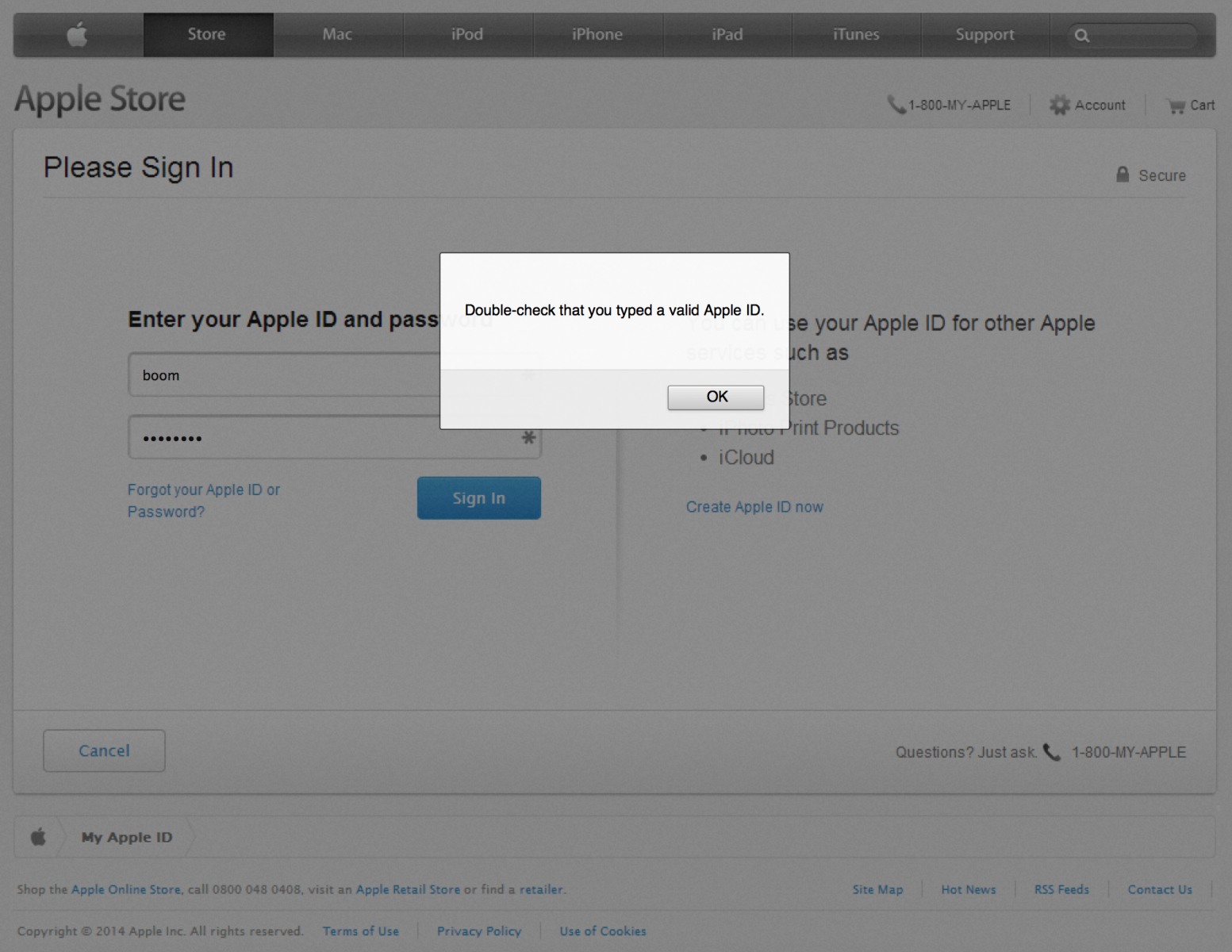
Upon submitting what it considers valid credentials, you're redirected to the /?2 page of the site which contains another form which appears to be Apple's site:
At this stage the site is collecting personal details about the account holder which may aid them in making changes to the account or stealing the victim's identity. After submitting precious personal information, it's now time to give them your credit card information:
Only after supplying a valid Visa, Mastercard, American Express or Discover card number are you forwarded to the /?3 "Success" page.
Finally, after a just a couple of seconds on this page (before you have a chance to click one of the links which are actually a screenshot image of the real Apple site without any functional links) you are redirected to the real apple.com. At this point the attacker would have obtained all the necessary information to exploit the victim, and the victim would have absolutely no idea how this happened. Clever!
Technical Analysis
We're able to observe or infer several things through a quick analysis.
First of all, we can observe that the site is running on PHP:
Set-Cookie: PHPSESSID=4b2be321acb0eac806780b7cd3ae1ba8;
In the phishing emails, they have a parameter like /e=656d61696c4076696374696d2e656d61696c appended to the URL. Thanks to insight from ISC readers, it's now clear that this is the victim's email as a tracking identifier. (Hex to ASCII)
We can also see that the site is hosted by Lycos with a domain registered just a day ago via Tucows.
Looking at the front-end of the site, we can see that the phishers didn't actually replicate the full HTML/CSS page but rather overlayed screenshots of the real apple.com with forms. This is how they manage to so accurately mimic the appearence of the target site without affording much effort into the front-end development. The background screenshot of apple.com used on their main page can be seen at http://www.appleidconfirm.net/img/main.png
Lastly, we can see that the site is not using HTTPS. This is a key differentiator from the true apple.com login page which does utilize HTTPS. Yet another reason to pay close attention to the URL bar in your browser.
Mitigation
Obviously it's not very difficult to craft a successful phishing campaign, but from a technological standpoint it's difficult to thwart them. So, what can we do? We should invest in awareness through education. That means reconsidering the amount of time and budgeting you set aside to train the less technical staff about phishing and social engineering. Informally, it may be time to sit down with that friend or family member who keeps sending you ads for weight loss because they have fallen victim to the latest phish. Knowledge is power.
Finally, when you see a phish in progress take the time to write a few abuse emails to the relevant providers. (and forward the phish to us!)
6 Comments
Mass XSSodus in PHP
In writing web applications PHP developers often find themselves repeatedly calling the htmlentities function, or the htmlspecialchars function. These will encode the special characters of a string to their HTML entities, ensuring that output can safely avoid being executed by browser parsing engines.
The problem with this is a human one. Humans do make mistakes, and even those well aware of the consequences and solutions will eventually suffer from an oversight that results in an XSS vulnerability. How can we limit the possibility of creating vulnerabilities in such a situation?
We’ve seen a very fair share of approaches to mitigating XSS in PHP but one in particular seems to fly under the radar. PHP has a couple of configuration directives in php.ini which will automagically filter input by various sanitization and/or validation flags of your choosing. So, can we make it work like htmlentities? Yes!
In your (recent) default php.ini file you will find the following:
[filter] ; http://php.net/filter.default ;filter.default = unsafe_raw ; http://php.net/filter.default-flags ;filter.default_flags =
Modify these as follows:
[filter] ; http://php.net/filter.default filter.default = full_special_chars ; http://php.net/filter.default-flags filter.default_flags = 0
This will encode all $_GET, $_POST, $_COOKIE, $_REQUEST and $_SERVER values. (The original data can be accessed through the filter_input() function.)
Example In Action
As a quick proof of concept I built a simple login form that does no sanitization or encoding. The first (Username) field is pre-filled with the data you submitted if an error occurs, such as not providing any password. To exploit the first form field, I entered "><script>alert("XSS");</script> with no password at all.
Without the php.ini configuration changes:
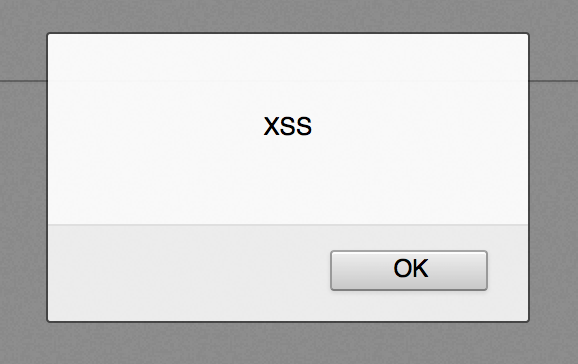
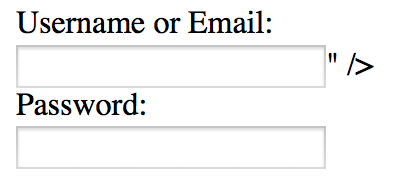
The input data is parsed by the browser as code and the JavaScript alert is displayed, thereby proving the presence of an XSS vulnerability.
Now, with the php.ini configuration changes:
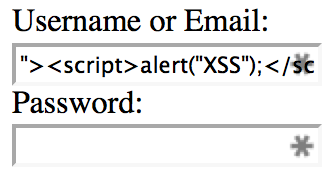
The input data is safely output into the form field as content instead of code, thereby mitigating the XSS vulnerability.
Common Questions
-
Do I still need to perform output encoding in my application?
Yes. This approach will handle a large portion of the repetitive cases, but some necessity for output encoding will remain. A simple example would be the importance of using theurlencodefunction upon outputting a URL which contains user input. -
What about JSON/JavaScript output?
Any input you place into JSON or JavaScript from PHP’s superglobals would still be encoded. -
Does this work for distributable web apps that run in shared hosting environments?
This approach may not always be feasible in shared environments due to the potentially limited access to php.ini directives. If you’re building distributable web apps which support running in shared environments, it is not safe to rely on this approach. However, if you’re working in an environment with a custom PHP back-end running on a dedicated server(s) this approach may be your best bet. -
Won’t this result in double encoding?
Yes, quite possibly. That said, double encoding is far lower risk and more easily identifiable than XSS vulnerabilities. -
How can I check that the directives are properly set before outputting anything from my application?
The following code will check that the php.ini settings are in place as expected and discontinue execution with a relevant error otherwise. It should be placed at the beginning of your application before any other code is executed.if(ini_get('filter.default')!=='full_special_chars'||ini_get('filter.default_flags')!=='0') die('Missing and/or incorrect filter.default and/or filter.default_flags directives in php.ini');
Not a Replacement for Defense in Depth
While this approach can simplify output encoding and limit the risk of developer oversight, it should not be considered an end-all solution. You may have input data sources in your application other than PHP's superglobals. You should still consider the results of a SQL query or cURL request, for example, as potentially malicious. Finally, you should continue performing penetration testing and code reviews to catch that inevitable XSS vulnerability before they do.
4 Comments
Let's Finally "Nail" This Port 5000 Traffic - Synology owners needed.
We have written a couple diaries about port 5000 traffic, and received plenty of packet captures. But we still need to get all the pieces together to see what the "end game" is with these attacks. Here is what I found so far from our honeypot:
- a lot of the port 5000 traffic is spoofed.
I do receive "SYNs" from an IP, and my honeypot responds with a SYN-ACK, but then I get a reset back with a very different TTL.
- the once that connect, send a couple different requests (a.b.c.d is the address of the honey pot)
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
6 Comments
A few updates on "The Moon" worm
It has been over a month since we saw the "Moon" worm first exploiting various Linksys routers [1]. I think it is time for a quick update to summarize some of the things we learned since then:
Much of what we found so far comes thanks to the malware analysis done by Bernado Rodriges [2]. Bernado used QEMU to run the code in a virtual environment. QEMU is as far as I know the only widely available virtualization technique that can simulate a MIPS CPU while running on an x86 host. So far, most of what I have been doing relied on telnetting to an infected router. With QEMU, Bernado got additional insight into what happened with the worm. In particular, it is now easy to dump physical memory. The worm ran on OpenWRT. I am not sure if it would be possible to install the stock Linksys firmware in QEMU. Something on my list of things to try out. I think for future reverse analysis, this would provide a more realistic target.
Infected systems will run an additional https server on a random port. The communication we observed in earlier posts is just https, using a self signed certificate. The server also provides statistics pages with summaries listing infected systems. For a screenshot, see https://twitter.com/daavidhentunen/status/441551682443300866/photo/1 .
At this point, I do still see regular hits from infected routers to my honeypot. They appear to have slowed down a bit, but I still get a number of scans a day.
[1] https://isc.sans.edu/forums/diary/Linksys+Worm+TheMoon+Summary+What+we+know+so+far/17633
[2] http://w00tsec.blogspot.com
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
0 Comments
New Microsoft Advisory: Unpatched Word Flaw used in Targeted Attacks
Microsoft today published a new security bulletin, announcing that it has seen a new Word 2010 exploit used in recent targeted attacks. The exploit uses a so far unpatched vulnerability in Word that is triggered by opening a crafted RTF document.
To prevent exploitation of the vulnerability, Microsoft released a "Fix It" that will prevent Word from opening RTF documents. [1][2]
Frequently RTF ("Rich Text Format") is used as a more portable way to exchange documents with basic formatting elements. The Fix-It may not be appropriate if you use RTF documents regularly. However, given that RTF documents are portable and can be opened by other software, it MAY be ok to just use software other then word to open the document.
This vulnerability is identified by CVE-2014-1761.
More details about the exploit can be found in Microsoft's "Security Research and Defense Blog" [3]. It points out that EMET can help block the exploit if the "Mandatory ASLR" and the "Anti-ROP" features are selected. This may be of help if you can't stop opening RTFs altogether. Word 2013 appears vulnerable, but the exploit fails due to ASLR and "just" crashes Word 2013.
The blog post also includes indicators of compromise for the particular exploit seen.
[1] https://technet.microsoft.com/en-us/security/advisory/2953095
[2] https://support.microsoft.com/kb/2953095
[3] http://blogs.technet.com/b/srd/archive/2014/03/24/security-advisory-2953095-recommendation-to-stay-protected-and-for-detections.aspx
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
1 Comments
Integrating Physical Security Sensors
I have been playing for a few years now with different network connected devices [1]. As a "security guy", a lot of this research has been about vulnerability in these devices, or what we sometimes call the "Internet of Things". Over the years, I also learned to appreciated the ability of these devices to deliver physical context to some events that I may see in my logs, and I started to add the state reported from some of these devices to my syslog collector feeding into my SIM (right now not a "full SIM, but Splunk for the most part).
Here are a couple of experiences that I found helpful:
Servers
Servers (and many desktops) do provide a number of useful sensors. For example a sensor to detect opening the case, and various temperature sensors. The temperature sensor can easily be monitored with tools like Nagios. The case sensor is a bit more tricky. Yes, it can easily be monitored (nagios again), but I find that nobody resets the sensor in the BIOS after legitimately opening the case, and to avoid tampering with this setting, this requires a BIOS password. Not too many people are willing to set BIOS passwords and rather rely on the physical security of the data center itself. A switch port can also be used to detect disconnection of a server, and the power usage of your power distribution unit (PDU) can often be polled remotely. I haven't run into a PDU yet that can set a syslog/snmp message that would alert you of power use going to zero on a device. Usually they have alerts that will tell you about high load or high temperature.
Environmental Sensors
There are a number of environmental sensors that are available outside of the server. Many AC systems can be polled remotely I have run into http APIs, some snmp and even syslog. This can alert you of an AC failure before the temperature in your server rises significantly. Some advanced systems will also provide overall "health" information but I haven't played much with that yet. Usually this information is used for remote maintenance. Of course, you can always add additional network readable sensors for temperature and humidity. There are also a number of options to detect more "catastrophic" conditions like water leaks and to automatically shut off water feeds if they are detected.
Physical Sensors
Access cards and door open/close sensors are pretty much standard in large office buildings these days. But the information isn't always easily accessible to the network security team. Being able to correlate an event with a person's presence (or absence) from an area can be important. Not just to identify the culprit, but also to provide context to an alert. For example, a work station sending excessive HTTP requests while a user isn't sitting in front of it can be an important indicator. You may be able to get signals if a screen saver is engadged or not on a system in order to monitor physical security or additionally verify if a user is using a system or not (nagios can do that easily in Linux. Not sure if there is an easy way to poll in Windows remotely if a screen saver is engadged).
My favorite example is always a hotel in Singapore that used the signal from an opening room door to dispatch an elevator to that respective floor.
Cameras
Network cameras are pretty much everywhere these days. Some come with integrated motion sensors, or can detect motion by monitoring changes to the image. Either way, many of these cameras can send a signal whenver they detect motion, and even attach images. This can suplement some of the door sensors.
Anything else you recently integrated?
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
3 Comments
How the Compromise of a User Account Lead to a Spam Incident
ISC contributor Simon transmitted the following results of their investigation to the local users of their forum highlighting how a safety lapse on a user machine resulted into some dramatic consequences. It highlights the IR steps taken by the response team to cleanup, return the mail service in operation and dealing with the aftermath of the spam campaign.
--------------------------------
Late last night we had an occurrence that raised a red alert on one of our servers indicating it might have been compromised. We received notification from the abuse department of our ISP, that our servers were transmitting spams.
We immediately shut down all e-mail services then started to analyse the log files.
We found that all spams had been sent using a particular user account on this very server, that user enjoying the privilege of an e-mail account on this server. A whole botnet was participating in "delivering" the spams for distribution by our servers.
Further analysis of log files as well as packet captures showed that there had been no occurrence prior to the first login to the user's account, no attempts to break into that account was registered. The first attempt to log into that account already used the correct password.
We changed the password of that user, effectively taking control of that account away from that user, removed more than 17,000 spams still waiting to be delivered from the server's mail transmit queue, and began to partially restart the mail services until all mail servers were operating in full again with no further anomalies.
While we are waiting for reply from that particular user, who had instantly been notified about the issue as well, we can only assume what may have happened: we believe the user's computer has been compromised and the credentials for this server as well as possibly other sites (including telebanking etc.) have been stolen. That way the spammer then could use the correct password for the correct account a short while later and started his spam campaign.
In the meantime we are continuing to work on that affair to ensure, that ISPs affected by the spam campaign get to know about the result of our analysis (the whole spam campaign was stopped within one hour), also in the attempt to limit the impact of spam protection which might blocklist our e-mail servers.
The occurrence highlights the dangers of the highly networked environment we are operating in. A user's PC being compromised is not just a local event, it affects the user's ISPs and mail service providers, the banks the user works with. A compromised PC thus provides not only headache to the owner of that PC for exposing private and confidential details to others, but also a lot of headache to other people who provide service and trust in the PCs being handled securely.
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot edu
3 Comments
Cisco AsyncOS Patch
Cisco released a patch for AsyncOS, the operating system used in it's E-Mail Security Appliance (ESA) and Security Management Appliance (SMA).
The vulnerability is exploited by an authenticated attacker uploading a crafted blocklist file. The file has to be uploaded via FTP, so this vulnerability is only exploitable if the FTP service is enabled. Once the blocklist is pared, arbitrary commands are executed.
This sounds like an OS command injection vulnerability. The parameters (assumed to be IP addresses) are likely passed as arguments to a firewall script, but if the address includes specific characters (usually ; or & ?) , additional commands can be executed.
Time to patch, but given that the attacker has to be authenticated, makes this a less severe vulnerability then other arbitrary code execution vulnerabilities.
[1] http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20140319-asyncos
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
0 Comments
Normalizing IPv6 Addresses
One of the annoyances with IPv6 addresses is that they may be abbreviated. Leading "0"s may be omitted, and groups of all ":0000:" may be replaced with "::". The key annoyance is the word "may". Some logs (for example iptables) will not abbreviate, others, like for example nginx or apache, will abbreviate, making correlating logs more difficultly.
Lately, I started using a little perl script to "normalize" my IPv6 addresses in logs. The script will insert all the missing "0"s making it easier to find a specific IP address. The script I am using:
#!/usr/bin/perluse strict;while (<> ) {my $line=$_;if ( $line=~/[0-9a-f:]+/ ) {my $old=$&;my $new=fillv6($old);$line=~ s/$old/$new/;}print $line;}sub fillv6 {my $in=shift;$in =~ s/^:/0000:/;my @parts=split(/:/,$in);my $partn=scalar @parts;if ( $partn < 7 ) {my $x= ':0000' x (9-$partn);$in =~ s/::/$x:/;$in =~ s/:://g;@parts=split(/:/,$in);}while ( my $part=each(@parts) ) {$parts[$part] = sprintf("%04s",$parts[$part]);}return join(':',@parts);}
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
3 Comments
For the Adventurous, Java 8 is out
Looks like JAVA 8 is out (thanks Rob).
What’s new: http://www.oracle.com/
Release notes: http://www.oracle.com/
Downloads: http://www.oracle.com/
Note that many of the Java 8 download links still point to 7.51
Good luck let us know how you go if you are updating right now.
M
3 Comments
Full Disclosure list shuts down
The Full Disclosure mailing list which is at times an interesting source of information, other times entertainment and sometimes a source of frustration is shutting down. John Cartwright posted a message announcing the closure on the site (http://seclists.org/fulldisclosure/2014/Mar/332).
I for one thank John and Len for the list. It is a shame to see it go. I'll miss the technical components. I won't miss the reasons for taking this decision.
M
0 Comments
Call for packets dest 5000 or source 6000
There are two events I'm interested in following up at the moment. A few reports mentioned that scans to destination port 5000 seem to be popular at the moment. (https://isc.sans.edu/port.html?port=5000). So if you have a few spare packets that would be great. In this instance I'm not looking for log records only pcaps.
Another reader mentioned scans from source port 6000 going to numerous ports on their infrastructure, but from different IP addresses. eg. IP address A scanning target 1089-1099. IP address B scanning target 1100-1110, etc. If you have log records or packets for trafic from source port 6000 to multiple ports or IP addresses in your environment I'd be interested in taking a look.
We've seen both of these previously, but certainly like to see if it is the same or something different.
Thanks
Mark H
2 Comments
Scans for FCKEditor File Manager
FCKEditor (now known as CKEditor [1]) is a popular full featured GUI editor many web sites use. For example, you frequently find it with blog systems like WordPress or as part of commenting/forum systems. As an additional feature, a filemanager can be added to allow users to upload images or other files. Sadly, while a very nice and functional plugin, this features if frequently not well secured and can be used to upload malicious files. We have seen some scans probing specifically for this file manager plugin:
HEAD /js/fckeditor/editor/filemanager/connectors/test.html HEAD /admin/FCKeditor/editor/filemanager/connectors/test.html HEAD /admin/FCKeditor/editor/fckeditor.htmlHEAD /include/fckeditor/_samples/default.html HEAD /include/fckeditor/editor/filemanager/connectors/test.htmlGET /editor/editor/filemanager/connectors/uploadtest.html HTTP/1.1GET /editor/editor/filemanager/upload/test.html HTTP/1.1GET /editor/editor/filemanager/browser/default/connectors/test.html HTTP/1.1GET /editor/editor/filemanager/connectors/test.html HTTP/1.1GET /admin/fckeditor/editor/filemanager/connectors/test.html HTTP/1.1GET /FCKeditor/editor/filemanager/upload/test.html HTTP/1.1GET /Fckeditor/editor/filemanager/browser/default/connectors/test.html HTTP/1.1GET /admin/FCKeditor/editor/filemanager/connectors/uploadtest.html HTTP/1.1GET /admin/FCKeditor/editor/filemanager/upload/test.html HTTP/1.1GET /Fckeditor/editor/filemanager/connectors/test.html HTTP/1.1GET /admin/fckeditor/editor/filemanager/browser/default/connectors/test.html HTTP/1.1
GET /FCKeditor/editor/filemanager/connectors/uploadtest.html HTTP/1.1
I am still looking for any samples of files these script attempt to upload. If you got any, please let use know.
[1] http://ckeditor.com
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
2 Comments
New Apache web server release
The Apache folks have released version 2.4.9 of their ubiquitous web server. This one fixes a couple of security vulnerabilities along with some other bug fixes, one in mod_log_config having to do with issues with truncated cookies and one in mod_dav that was a potential denial of service. Expect most of the Linux distros to apply the appropriate fixes shortly, but if you are building from source or running on a platform that won't push the updates to you, go grab the update.
References:
http://httpd.apache.org/security/vulnerabilities_24.html
http://www.apache.org/dist/httpd/CHANGES_2.4.9
---------------
Jim Clausing, GIAC GSE #26
jclausing --at-- isc [dot] sans (dot) edu
1 Comments
NTIA begins transition of Root DNS Management
The U.S. National Telecommunications and Information Administration (NTIA) has begun the final stages of privatizing the management of the Domain Name System (DNS) that powers the Internet. This transition was begun in 1997.
From the press release...
"As the first step, NTIA is asking the Internet Corporation for Assigned Names and Numbers (ICANN) to convene global stakeholders to develop a proposal to transition the current role played by NTIA in the coordination of the Internet’s domain name system (DNS). "
The NTIA, in conjunction with ICANN and Verisign, is currently responsible for managing the root zone, including the administration of the root zone file which contains the details about the top level domains (TLDs). The TLDs are the last part of a Full Qualified Domain Name (FQDN), such as .com, .gov, .mil, etc.
-- Rick Wanner - rwanner at isc dot sans dot edu - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)
0 Comments
Word Press Shenanigans? Anyone seeing strange activity today?
We are getting different activity reports (Thanks for those!) on Word Press. Beyond the ping back issue that has been happening, is anyone else seeing strange WP behavior?
Richard Porter
--- ISC Handler on Duty
Twitter: Packetalien
Blog: packetalien.com
4 Comments
Identification and authentication are hard ... finding out intention is even harder
While the drama about the lost airplane in Malaysia is still continuing, our hearts of course go out to the families of the missing. This ISC diary though is not about airplanes, or terrorism, it is rather about the related discovery that at least two passengers on the plane were using fake passports. Equally startling was the comment by Interpol that this is "common". What is the point of maintaining, for example, a no-fly list, if those listed on it anyway travel with stolen documents, and if the security checkpoint apparently fails to determine that a 19yr old doesn't look like a 40yr old, and that Italians who don't speak at least rudimentary Italian are, well, somewhat rare?
If we translate this to the virtual world, it turns into an everyday problem. How do we know that Joe using Joe's password is actually Joe, and not Jane? I probably should call them "Bob" and "Alice" to make this worthy of a scientific paper :), but the problem still stands: identification and authentication are hard, and finding out intentions is even harder. If we take from the airport physical security playbook, then it is "behavior" that makes the difference. The security checkpoint guys are (supposedly) trained to look for "clues" like nervousness, and carry-on baggage that is leaking 1,2,3-trinitroxypropane. Inevitably, there are numerous software products that claim to identify the "unusual" as well. Joe connecting from Connecticut, even though he lives in Idaho? Alert! Joe using Chrome even though he used Firefox last time? Alert! Joe typing his password faster than usual? Alert!
But like in the physical world, this kind of profiling only works well if you have a pretty homogenous and static "good guy" population, and a pretty well defined adversary. The real world, unfortunately, tends to be more diverse and complex than that. Which is why login fraud detection, just as airport security, often drowns in the "false positives", and as a result, de-tunes the sensitivity to the point where real fraud has stellar odds to just slip by. This is a fundamental issue with many security measures. Statisticians call this "base rate fallacy". If there are many many! more good guys than bad guys, finding the bad guys with a test that has a high error rate is pretty much: moot.
Checking the passports against the Interpol list of stolen passports .. wouldn't hurt though. Not doing this is akin to letting someone log in to an account that is suspended, or log in with a password that was valid two years ago.
1 Comments
Web server logs containing RS=^ ?
A SANS ISC reader sent us the following Apache log snippet earlier today
108.178.x.x - [11/Mar/2014:04:21:14 +0100] "GET /index.shtml/RK=0/RS=o_wLEbyzxJDMeXhdrhZU9KN7uD4- HTTP/1.0" 302 206
196.196.x.x - [11/Mar/2014:07:43:19 +0100] "GET /index.shtml/RS=^ADAY1N1JxWPFnnOEW3FpVC1g.n4rec- HTTP/1.0" 302 206
88.80.x.x - [11/Mar/2014:15:02:01 +0100] "GET /index.shtml/RS=^ADAw5eOsxy0br6iGm1BZPRs2wtnyAE- HTTP/1.1" 302 206
index.shtml exists on the reader's server, but the RS= / RK= stuff is bogus. The RS= looks like it could be a regular expression for a pattern match of sorts, since it is starting with an anchor "^", but that's guessing. We don't really know. Googling for the pattern shows that this sort of thing has been around for a while, but I didn't find any definite explanation about which software or toolkit these requests are attempting to exploit, if any. If you have information on what this is, please share in the comments below, or via our contact form.
4 Comments
Wordpress "Pingback" DDoS Attacks
Sucuri detected an interesting "reflective" attack using the Wordpress Pingback feature to attack web sites [1]. Unlike other reflective attacks that use UDP services like NTP and DNS, this attacks uses the Wordpress Pingback feature.
The intend of Pingback is to notify a site that you link to about the link hoping that the site you are linking to will return the favor. Some systems automate this and maintain automated lists linking back to sites that covered their article. In order to implement pingback, Wordpress implements an XML-RPC API function. This function will then send a request to the site to which you would like to send a "pingback".
With Wordpress, the Pingback is sent as a POST request to the /xmlrpc.php request. The body of the request will look like:
<methodCall>
<methodName>pingback.ping</methodName>
<params>
<param><value><string>http://victim</string></value></param>
<param><value><string>http://reflector</string></value></param>
</params>
</methodCall>
For the attack seen by Sucuri, the "victim" URL included a random parameter like "victim.com?123456=123456" to prevent caching.
The result of this request is that your Wordpress install will send a request to the victim's site. I don't think the attack will provide a significant traffic amplification, but it does obfuscate the actual source of the attack.
By default, this feature is enabled in all Wordpress installs, and isn't quite easy to turn off. Sucuri recommends to add the following API filter to Wordpress:
add_filter( ‘xmlrpc_methods’, function( $methods ) {
unset( $methods['pingback.ping'] );
return $methods;
} );
Removing xmlrpc.php is not recommended as it will breack a number of other features that will use the API.
[1] http://blog.sucuri.net/2014/03/more-than-162000-wordpress-sites-used-for-distributed-denial-of-service-attack.html
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
6 Comments
Introduction to Memory Analysis with Mandiant Redline
In a previous diary I talked about memory acqusition with Dumpit .in this diary I will talk about how to use Mandiant Redline to analysis the memory dump.[1]
Mandiant Redline:
“Redline, Mandiant’s premier free tool, provides host investigative capabilities to users to find signs of malicious activity through memory and file analysis, and the development of a threat assessment profile”.[2]
Installation:
1-Download Mandiant Redline from https://www.mandiant.com/resources/download/redline
2-Double click on Redline-1.11.msi
3-follow up the steps, then click close
Redline Usage:
To analysis a memory image :
1-Select From a Saved Memory File under Analyze Data on the home screen
2-Click Browse under Location of Saved Memory Image (for this diary I will not use an Indicators of Comporomise)
3-Click Next then OK
Depending on the size of the image and the speed of your PC, Mandiant Redline will take time to process the memory image.
4-For this example I am going to choose “I am reviewing A Full Live Response or Memory Image”
Now our Image is ready for Review:.jpg)
From the left hand side you can choose which type of Data you would like to analysis in this view it’s the “Processes”
Here you can find all the process which was running on the system when the memory image was acquired . It shows the full details about the process such as the Process ID,Path ,Arguemnts ,User name ,SID …etc .
If you would like to view the open ports on the System while the image was acquired , To view ports, click Ports under Processes on the Analysis Data window’s Host tab.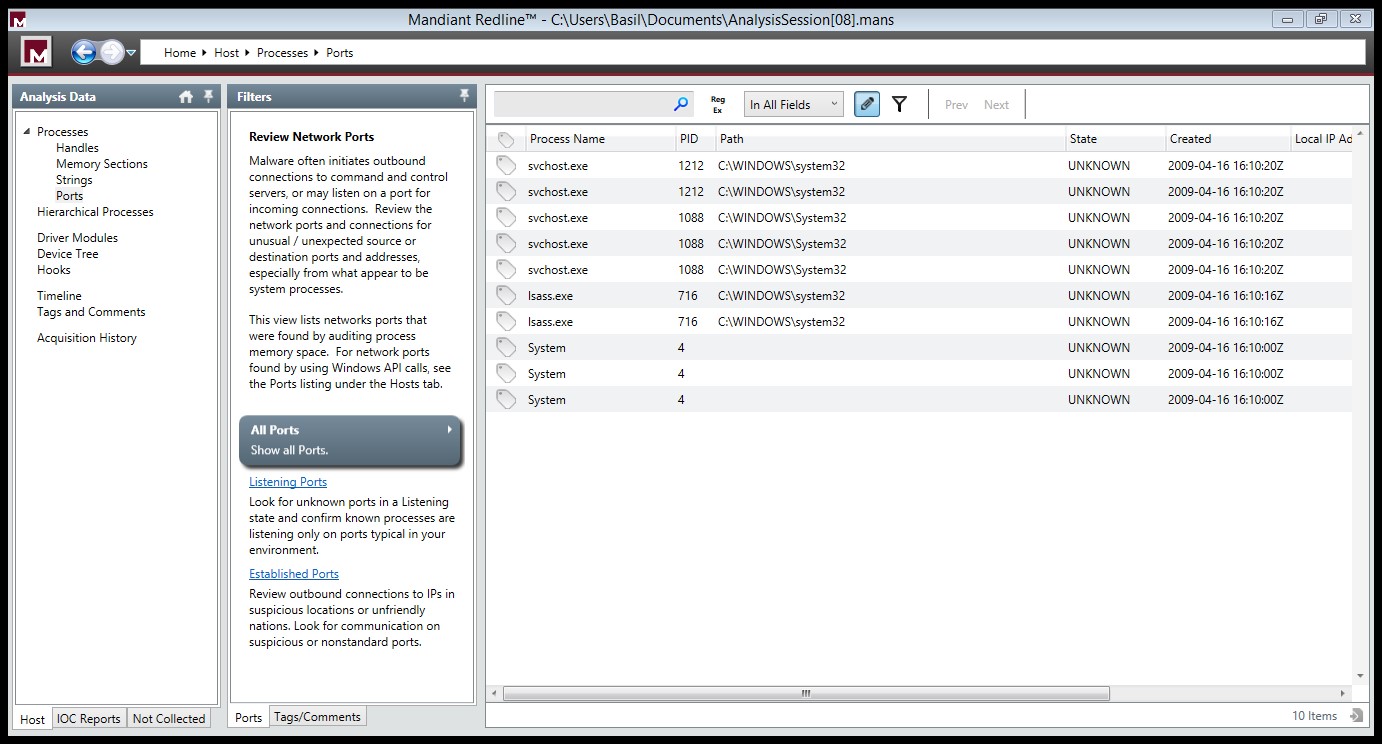
0 Comments
Microsoft Patch Tuesday March 2014
Overview of the March 2014 Microsoft patches and their status.
| # | Affected | Contra Indications - KB | Known Exploits | Microsoft rating(**) | ISC rating(*) | |
|---|---|---|---|---|---|---|
| clients | servers | |||||
| MS14-012 |
Cummulative Security Update for Internet Explorer (ReplacesMS14-010 ) |
|||||
|
Internet Explorer CVE-2014-0297 CVE-2014-0298 CVE-2014-0299 CVE-2014-0302 CVE-2014-0303 CVE-2014-0304 CVE-2014-0305 CVE-2014-0306 CVE-2014-0307 CVE-2014-0308 CVE-2014-0309 CVE-2014-0311 CVE-2014-0312 CVE-2014-0313 CVE-2014-0314 CVE-2014-0321 CVE-2014-0322 CVE-2014-0324 |
KB 2925418 | Yes! |
Severity:Critical Exploitability: 1 |
PATCH NOW! | Critical | |
| MS14-013 |
Remote Code Execution Vulnerability in Microsoft Direct Show (ReplacesMS13-056 ) |
|||||
|
Direct Show JPEG Library CVE-2014-0301 |
KB 2929961 | No. |
Severity:Critical Exploitability: 1 |
Critical | Important | |
| MS14-014 |
Vulnerability in Silverlight Could Allow Security Feature Bypass (ReplacesMS13-087 ) |
|||||
|
Silverlight CVE-2014-0319 |
KB 2932677 | No. |
Severity:Important Exploitability: 1 |
Important | Important | |
| MS14-015 |
Privilege Escalation Vulnerability in Windows Kernel-Mode Driver (ReplacesMS13-101 ) |
|||||
|
Windows Kernel-Mode Driver CVE-2014-0300 CVE-2014-0323 |
KB 2930275 | Yes. CVE-2014-0323 was public. |
Severity:Important Exploitability: 1 |
Important | Important | |
| MS14-016 |
Security Bypass Vulnerabilty in Security Account Manager Remote (SAMR) (ReplacesMS11-095 MS13-032 ) |
|||||
|
Security Account Manager Remote CVE-2014-0317 |
KB 2930275 | No. |
Severity:Important Exploitability: 1 |
Important | Important | |
We appreciate updates
US based customers can call Microsoft for free patch related support on 1-866-PCSAFETY
-
We use 4 levels:
- PATCH NOW: Typically used where we see immediate danger of exploitation. Typical environments will want to deploy these patches ASAP. Workarounds are typically not accepted by users or are not possible. This rating is often used when typical deployments make it vulnerable and exploits are being used or easy to obtain or make.
- Critical: Anything that needs little to become "interesting" for the dark side. Best approach is to test and deploy ASAP. Workarounds can give more time to test.
- Important: Things where more testing and other measures can help.
- Less Urgent: Typically we expect the impact if left unpatched to be not that big a deal in the short term. Do not forget them however.
- The difference between the client and server rating is based on how you use the affected machine. We take into account the typical client and server deployment in the usage of the machine and the common measures people typically have in place already. Measures we presume are simple best practices for servers such as not using outlook, MSIE, word etc. to do traditional office or leisure work.
- The rating is not a risk analysis as such. It is a rating of importance of the vulnerability and the perceived or even predicted threat for affected systems. The rating does not account for the number of affected systems there are. It is for an affected system in a typical worst-case role.
- Only the organization itself is in a position to do a full risk analysis involving the presence (or lack of) affected systems, the actually implemented measures, the impact on their operation and the value of the assets involved.
- All patches released by a vendor are important enough to have a close look if you use the affected systems. There is little incentive for vendors to publicize patches that do not have some form of risk to them.
(**): The exploitability rating we show is the worst of them all due to the too large number of ratings Microsoft assigns to some of the patches.
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
0 Comments
Adobe Updates: Flash Player
Adobe released a new version of Flash Player as part of today's patch Tuesday. No details are available yet. We will update this diary once the details become available. Note that this will also affect browsers like Chrome that include an embeded version of Flash.
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
1 Comments
Apple iOS 7.1
Here is detailed information on today's Apple releases - both iOS and Apple TV were updated
APPLE-SA-2014-03-10-1 iOS 7.1
iOS 7.1 is now available and addresses the following:
Backup
Available for: iPhone 4 and later,
iPod touch (5th generation) and later, iPad 2 and later
Impact: A maliciously crafted backup can alter the filesystem
Description: A symbolic link in a backup would be restored, allowing
subsequent operations during the restore to write to the rest of the
filesystem. This issue was addressed by checking for symbolic links
during the restore process.
CVE-ID
CVE-2013-5133 : evad3rs
Certificate Trust Policy
Available for: iPhone 4 and later,
iPod touch (5th generation) and later, iPad 2 and later
Impact: Root certificates have been updated
Description: Several certificates were added to or removed from the
list of system roots.
Configuration Profiles
Available for: iPhone 4 and later,
iPod touch (5th generation) and later, iPad 2 and later
Impact: Profile expiration dates were not honored
Description: Expiration dates of mobile configuration profiles were
not evaluated correctly. The issue was resolved through improved
handling of configuration profiles.
CVE-ID
CVE-2014-1267
CoreCapture
Available for: iPhone 4 and later,
iPod touch (5th generation) and later, iPad 2 and later
Impact: A malicious application can cause an unexpected system
termination
Description: A reachable assertion issue existed in CoreCapture's
handling of IOKit API calls. The issue was addressed through
additional validation of input from IOKit.
CVE-ID
CVE-2014-1271 : Filippo Bigarella
Crash Reporting
Available for: iPhone 4 and later,
iPod touch (5th generation) and later, iPad 2 and later
Impact: A local user may be able to change permissions on arbitrary
files
Description: CrashHouseKeeping followed symbolic links while
changing permissions on files. This issue was addressed by not
following symbolic links when changing permissions on files.
CVE-ID
CVE-2014-1272 : evad3rs
dyld
Available for: iPhone 4 and later,
iPod touch (5th generation) and later, iPad 2 and later
Impact: Code signing requirements may be bypassed
Description: Text relocation instructions in dynamic libraries may
be loaded by dyld without code signature validation. This issue was
addressed by ignoring text relocation instructions.
CVE-ID
CVE-2014-1273 : evad3rs
FaceTime
Available for: iPhone 4 and later,
iPod touch (5th generation) and later, iPad 2 and later
Impact: A person with physical access to the device may be able to
access FaceTime contacts from the lock screen
Description: FaceTime contacts on a locked device could be exposed
by making a failed FaceTime call from the lock screen. This issue was
addressed through improved handling of FaceTime calls.
CVE-ID
CVE-2014-1274
ImageIO
Available for: iPhone 4 and later,
iPod touch (5th generation) and later, iPad 2 and later
Impact: Viewing a maliciously crafted PDF file may lead to an
unexpected application termination or arbitrary code execution
Description: A buffer overflow existed in the handling of JPEG2000
images in PDF files. This issue was addressed through improved bounds
checking.
CVE-ID
CVE-2014-1275 : Felix Groebert of the Google Security Team
ImageIO
Available for: iPhone 4 and later,
iPod touch (5th generation) and later, iPad 2 and later
Impact: Viewing a maliciously crafted TIFF file may lead to an
unexpected application termination or arbitrary code execution
Description: A buffer overflow existed in libtiff's handling of TIFF
images. This issue was addressed through additional validation of
TIFF images.
CVE-ID
CVE-2012-2088
ImageIO
Available for: iPhone 4 and later,
iPod touch (5th generation) and later, iPad 2 and later
Impact: Viewing a maliciously crafted JPEG file may lead to the
disclosure of memory contents
Description: An uninitialized memory access issue existed in
libjpeg's handling of JPEG markers, resulting in the disclosure of
memory contents. This issue was addressed through additional
validation of JPEG files.
CVE-ID
CVE-2013-6629 : Michal Zalewski
IOKit HID Event
Available for: iPhone 4 and later,
iPod touch (5th generation) and later, iPad 2 and later
Impact: A malicious application may monitor on user actions in other
apps
Description: An interface in IOKit framework allowed malicious apps
to monitor on user actions in other apps. This issue was addressed
through improved access control policies in the framework.
CVE-ID
CVE-2014-1276 : Min Zheng, Hui Xue, and Dr. Tao (Lenx) Wei of FireEye
iTunes Store
Available for: iPhone 4 and later,
iPod touch (5th generation) and later, iPad 2 and later
Impact: A man-in-the-middle attacker may entice a user into
downloading a malicious app via Enterprise App Download
Description: An attacker with a privileged network position could
spoof network communications to entice a user into downloading a
malicious app. This issue was mitigated by using SSL and prompting
the user during URL redirects.
CVE-ID
CVE-2014-1277 : Stefan Esser
Kernel
Available for: iPhone 4 and later,
iPod touch (5th generation) and later, iPad 2 and later
Impact: A local user may be able to cause an unexpected system
termination or arbitrary code execution in the kernel
Description: An out of bounds memory access issue existed in the ARM
ptmx_get_ioctl function. This issue was addressed through improved
bounds checking.
CVE-ID
CVE-2014-1278 : evad3rs
Office Viewer
Available for: iPhone 4 and later,
iPod touch (5th generation) and later, iPad 2 and later
Impact: Opening a maliciously crafted Microsoft Word document may
lead to an unexpected application termination or arbitrary code
execution
Description: A double free issue existed in the handling of
Microsoft Word documents. This issue was addressed through improved
memory management.
CVE-ID
CVE-2014-1252 : Felix Groebert of the Google Security Team
Photos Backend
Available for: iPhone 4 and later,
iPod touch (5th generation) and later, iPad 2 and later
Impact: Deleted images may still appear in the Photos app underneath
transparent images
Description: Deleting an image from the asset library did not delete
cached versions of the image. This issue was addressed through
improved cache management.
CVE-ID
CVE-2014-1281 : Walter Hoelblinger of Hoelblinger.com, Morgan Adams,
Tom Pennington
Profiles
Available for: iPhone 4 and later,
iPod touch (5th generation) and later, iPad 2 and later
Impact: A configuration profile may be hidden from the user
Description: A configuration profile with a long name could be
loaded onto the device but was not displayed in the profile UI. The
issue was addressed through improved handling of profile names.
CVE-ID
CVE-2014-1282 : Assaf Hefetz, Yair Amit and Adi Sharabani of Skycure
Safari
Available for: iPhone 4 and later,
iPod touch (5th generation) and later, iPad 2 and later
Impact: User credentials may be disclosed to an unexpected site via
autofill
Description: Safari may have autofilled user names and passwords
into a subframe from a different domain than the main frame. This
issue was addressed through improved origin tracking.
CVE-ID
CVE-2013-5227 : Niklas Malmgren of Klarna AB
Settings - Accounts
Available for: iPhone 4 and later,
iPod touch (5th generation) and later, iPad 2 and later
Impact: A person with physical access to the device may be able to
disable Find My iPhone without entering an iCloud password
Description: A state management issue existed in the handling of the
Find My iPhone state. This issue was addressed through improved
handling of Find My iPhone state.
CVE-ID
CVE-2014-1284
Springboard
Available for: iPhone 4 and later,
iPod touch (5th generation) and later, iPad 2 and later
Impact: A person with physical access to the device may be able to
see the home screen of the device even if the device has not been
activated
Description: An unexpected application termination during activation
could cause the phone to show the home screen. The issue was
addressed through improved error handling during activation.
CVE-ID
CVE-2014-1285 : Roboboi99
SpringBoard Lock Screen
Available for: iPhone 4 and later,
iPod touch (5th generation) and later, iPad 2 and later
Impact: A remote attacker may be able to cause the lock screen to
become unresponsive
Description: A state management issue existed in the lock screen.
This issue was addressed through improved state management.
CVE-ID
CVE-2014-1286 : Bogdan Alecu of M-sec.net
TelephonyUI Framework
Available for: iPhone 4 and later,
iPod touch (5th generation) and later, iPad 2 and later
Impact: A webpage could trigger a FaceTime audio call without user
interaction
Description: Safari did not consult the user before launching
facetime-audio:// URLs. This issue was addressed with the addition of
a confirmation prompt.
CVE-ID
CVE-2013-6835 : Guillaume Ross
USB Host
Available for: iPhone 4 and later,
iPod touch (5th generation) and later, iPad 2 and later
Impact: A person with physical access to the device may be able to
cause arbitrary code execution in kernel mode
Description: A memory corruption issue existed in the handling of
USB messages. This issue was addressed through additional validation
of USB messages.
CVE-ID
CVE-2014-1287 : Andy Davis of NCC Group
Video Driver
Available for: iPhone 4 and later,
iPod touch (5th generation) and later, iPad 2 and later
Impact: Playing a maliciously crafted video could lead to the device
becoming unresponsive
Description: A null dereference issue existed in the handling of
MPEG-4 encoded files. This issue was addressed through improved
memory handling.
CVE-ID
CVE-2014-1280 : rg0rd
WebKit
Available for: iPhone 4 and later,
iPod touch (5th generation) and later, iPad 2 and later
Impact: Visiting a maliciously crafted website may lead to an
unexpected application termination or arbitrary code execution
Description: Multiple memory corruption issues existed in WebKit.
These issues were addressed through improved memory handling.
CVE-ID
CVE-2013-2909 : Atte Kettunen of OUSPG
CVE-2013-2926 : cloudfuzzer
CVE-2013-2928 : Google Chrome Security Team
CVE-2013-5196 : Google Chrome Security Team
CVE-2013-5197 : Google Chrome Security Team
CVE-2013-5198 : Apple
CVE-2013-5199 : Apple
CVE-2013-5225 : Google Chrome Security Team
CVE-2013-5228 : Keen Team (@K33nTeam) working with HP's Zero Day
Initiative
CVE-2013-6625 : cloudfuzzer
CVE-2013-6635 : cloudfuzzer
CVE-2014-1269 : Apple
CVE-2014-1270 : Apple
CVE-2014-1289 : Apple
CVE-2014-1290 : ant4g0nist (SegFault) working with HP's Zero Day
Initiative, Google Chrome Security Team
CVE-2014-1291 : Google Chrome Security Team
CVE-2014-1292 : Google Chrome Security Team
CVE-2014-1293 : Google Chrome Security Team
CVE-2014-1294 : Google Chrome Security Team
Information will also be posted to the Apple Security Updates
web site: http://support.apple.com/kb/HT1222
0 Comments
Sysinternals Process Explorer v16.02, Process Monitor v3.1, PSExec v2.1 and Sigcheck v2.03 update
Microsoft Sysinterals has updates Process Explorer v16.02, Process Monitor v3.1, PSExec v2.1, Sigcheck v2.03 :
Process Explorer v16.02: This minor update adds a refresh button to the thread’s stack dialog and ensures that the Virus Total terms of agreement dialog box remains above the main Process Explorer window.
Process Monitor v.3.1: This release adds registry create file disposition (create vs open) and a new switch, /saveapplyfilter, which has Process Monitor apply the current filter to the output file as it saves it.
PSExec v2.1: This update to PsExec, a command-line utility that enables you to execute programs on remote systems without preinstalling an agent, encrypts all communication between local and remote systems, including the transmission of command information such as the user name and password under which the remote program executes.
Sigcheck v2.03: This version corrects a bug that caused the output of the –u switch to include signed files, and fixes several other minor bugs.
0 Comments
Microsoft March Patch Pre-Announcement
Microsoft released its pre-announcement for the upcoming patch Tuesday. The summary indicates a total of 5 bulletins, 2 are critical with remote code execution and 3 Important with a mix of security feature bypass and elevation of privileges. The announcement is available here.
[1] http://technet.microsoft.com/en-us/security/bulletin/ms14-mar
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot edu
5 Comments
PHP 5.4.26 and 5.5.10 available. Several Security Fixes @ : http://www.php.net/downloads.php
PHP 5.4.26 and 5.5.10 available. Several Security Fixes @ : http://www.php.net/downloads.php
--
Tom Webb
0 Comments
Linux Memory Dump with Rekall
Memory dumping for incident response is nothing new, but ever since they locked down access to direct memory (/dev/mem) on Linux, I’ve had bad experiences dumping memory. I usually end up crashing the server about 60 percent of the time while collecting data with Fmem.
A new version of Linux memory dumping utility rekall (previous called Winpmem) has recently came out. I’ve been testing it on the latest versions of Ubuntu and Redhat EL 5 and have not run into any issues with collection.
If you are fortunate enough to have an environment where you have groups of servers with the same patch levels, you should run the following steps on a non-compromised server. Additionally, if the compromised system is a VM, you can clone it and perform these actions on the clone. Make sure you collect all other volatile data (MACtimes, LSOF, PS ect..) before you dump memory as this may still cause instability to the system and you do not want to lose this data.
Preparing for collection
Install Linux Kernel Headers
Ubuntu
>sudo apt-get install linux-headers-server zip
CentOS/Redhat
>yum install kernel-headers gcc
Download and Compile rekall
When you run the makefile, it will automatically create part of the profile for the server. This will need to be copied off the server for analysis.
>wget http://downloads.rekall.googlecode.com/git/Linux/linux_pmem_1.0RC1.tgz
>tar -zxvf linux_pmem_1.0RC1.tgz
>cd linux
>make
Note:For Redhat/CentOS systems you will need to adjust the Makefile KHEADER variable.
Copy this file to your Volatility analysis machine under your volatility directory /plugins/overlays/linux/.
Load the Kernel Driver
>sudo insmod pmem.ko
>sudo lsmod |grep pmem
pmem 12680 0
Collect Memory
Now that the drive is loaded, a new device is accessible /dev/pmem. We want to copy the memory to an external device/share.
#Items in {} need to be changed per incident to be useful for analysis
>dcfldd if=/dev/pmem bs=512 conv=noerror,sync of=/{USBDRIVE}/ mount/{servername.date}.memory.dd hash=md5,sha256 hashlog=/{USBDRIVE}/{servername.date}.memory.dd-hash.log
Unload driver
>sudo rmmod pmem.ko
Analysis using Rekall
Now that collection is completed, we need to be able to examine the memory dump. Copy the memory image to your analysis workstation.
Install Rekall
>sudo apt-get install python-pip python-dev
>sudo pip install rekall
Build Rekall Profile
We now need to create a profile that will work with Rekall. Convert the file that was copied from the server and name it something useful for future analysis.
>rekal.py convert_profile 3.5.0-45-generic.zip Ubuntu3.5.0-45-generic.zip
>rekal.py --profile ./Ubuntu3.5.0-45-generic.zip -f /media/mem.dd pslist
To enter the interactive shell, you do not add a plugin on the commandline
>rekal.py --profile ./Ubuntu3.5.0-45-generic.zip -f /media/mem.dd
To list the available plugins, use the interactive shell:
>rekal.py info[tab][tab]
plugins.arp plugins.check_idt plugins.convert_profile plugins.dwarfparser plugins.info plugins.lsof plugins.null plugins.psaux plugins.vmscan
plugins.banner plugins.check_modules plugins.cpuinfo plugins.fetch_pdb
…..
To get more info about a specific plugin use a ? after plugin name
mem 12:38:31>plugins.pslist?
Some of the more useful plugins are:
-
plugins.bash -searches for bash history
-
plugins.check_modules- List loaded modules
-
plugins.dmesg - Gathers dmesg buffer
-
plugins.lsof
-
plugins.netstat
-
plugins.pslist
Optional (If you want to use Volatility for analysis)
I haven’t spent much time on this, but Volatility will not be able to use the rekall default profile. You also have to do the steps below to read the memory dump with Volatility. I’m guessing only a small change in the file is needed, but I have dug any deeper at this time.
>sudo apt-get install dwarfdump
>wget https://volatility.googlecode.com/files/volatility-2.3.1.tar.gz
>tar -zxvf volatility-2.3.1.tar.gz
>cd volatility-2.3.1/tools/linux
>make
>zip Ubuntu{Kernel ver}.zip ./module.dwarf /boot/System.map-`uname -r`
For more information on Rekall
http://docs.rekall.googlecode.com/git/tutorial.html
For more info on Volatility Linux analysis
https://code.google.com/p/volatility/wiki/LinuxMemoryForensics
--
Tom Webb
1 Comments
Port 5000 traffic and snort signature
ISC Reader James Lay has captured the mysterious port 5000 traffic and provided us with a copy of the packets and a snort signature. Thanks James! Your awesome!
The traffic is scanning TCP port 5000. After establishing a connection it sends "GET /webman/info.cgi?host='"
This appears to be a scan for Synology DiskStation Manager installations that are vulnerable to a remote code exection exploit published in October 2013. There is currently a metasploit module available for the vulnerability.
Thanks to James for the following snort signature.
alert tcp $EXTERNAL_NET any -> $HOME_NET 5000 (msg:"SERVER-WEBAPP Synology DiskStation Manager Reflected XSS attempt over UPnP"; flow:to_server,established; content:"/webman/info.cgi|3f|host="; fast_pattern:only; http_uri; metadata:policy balanced-ips drop, policy connectivity-ips drop, policy security-ips drop, reference:url,www.scip.ch/en/?
Follow me on Twitter: @markbaggett
http://www.sans.org/event/northern-virginia-2014/course/python-for-pen-testers
http://www.sans.org/event/sansfire-2014/course/python-for-pen-testers
There are a couple of chances to sign up for SANS Python programming course. The course starts from the very beginning, assuming you don't know anything about programming or Python. The course is self paced learning and we cover the essentials before we start building tools you can use in your next security engagement. You will love it!! Join me for Python for Penetration testers in Reston VA March 17-21 or at SANSFire in Baltimore June 23-27.
2 Comments
Gems in the ISC Diary Comments
Thanks for reading the ISC Diary! I hope you find useful information in the diary posts. I, and the other handlers, work hard to try and bring you the latest news as it develops, as well as point out interesting new research that affects our industry and our ability to protect our networks. BUT don’t stop with the diary. Quite often the MOST interesting part of the article is in the comments from the readers. Consider the following:
About a year ago I did a post entitled “What can you do with funky directory names?” https://isc.sans.edu/forums/diary/Challenge+What+can+you+do+with+funky+directory+names/12958
The post is about creating a “.. “ (Dot Dot Space) directory. You can even create a funky directory name that will cause windows to generate an error dialog message and go into an error condition. This is COOL STUFF right? Well, yeah but not nearly as interesting as the mostly overlooked last comment on the page. An anonymous ISC reader posted this comment:
“It's also easy to use similar file name tricks to make your malicious binary appear to be Microsoft signed. Name your malware file "svchost.exe " (note trailing space) and put it in the same folder as the legitimate file. Attempted reads of your malicious file will "miss" your file and instead hit the legitimate (and signed) binary. (This is because win32 will auto-remove the trailing space.)
The nice thing about CreateProcess is that it launches the malicious process just fine.”
What does this mean? Well, if you create a executable on the hard drive that ends with a SPACE and then execute it some interesting things happen. Applications such as Microsoft Sigcheck, Mandiant Redline, Process hacker and other tools that will check the digital signatures of the processes in the process list check the incorrect file. The malware is “svchost.exe “. But when these tools turn to the hard drive to read the executable digital signature the underlying API trims the trailing space and they read the signature on the real “svchost.exe”. The result is that those security tools find a legitimate digital signature and incorrectly believe the file “svchost.exe “ has been digitally signed by Microsoft.
Matt Graeber (@mattifestation) did a write up on his testing of the issue here http://www.exploit-monday.com/2013/02/WindowsFileConfusion.html
I have found this technique to be useful for fooling Non-Microsoft tools that rely on digital signatures. So don't stop with the article! Read the comments from our brilliant readers. Please TEST your HIPS, Whitelisting applications, Forensics tools and other digital signature based tools using the process outline by Matt Graeber. Is it vulnerable? Post a comment (responsible disclosure is encouraged) and other brilliant insights in the comments!
Follow me on Twitter: @markbaggett
There are a couple of chances to sign up for SANS Python programming course. The course starts from the very beginning, assuming you don't know anything about programming or Python. The course is self paced learning and we cover the essentials before we start building tools you can use in your next security engagement. You will love it!! Join me for Python for Penetration testers in Reston VA March 17-21 or at SANSFire in Baltimore June 23-27.
http://www.sans.org/event/northern-virginia-2014/course/python-for-pen-testers
http://www.sans.org/event/sansfire-2014/course/python-for-pen-testers
0 Comments
TCP/5000 - The OTHER UPNP Port
We've all read a lot about the scans and exploits of UPNP (Universal Plug N Play), on UDP port 1900. Jens, one of our readers, pinged us this morning with a question about an uptick he was seeing in TCP/5000, which is also listed as UPNP - who knew? (not me, that's who!)
After a quick check, I'm seeing an uptick in attack activity on TCP/5000 starting in mid-February, both in our dshield database and on various customer firewalls. Our reader was seeing his attacks come from an IP allocated to China, but I'm seeing more attacks sourced from the US.
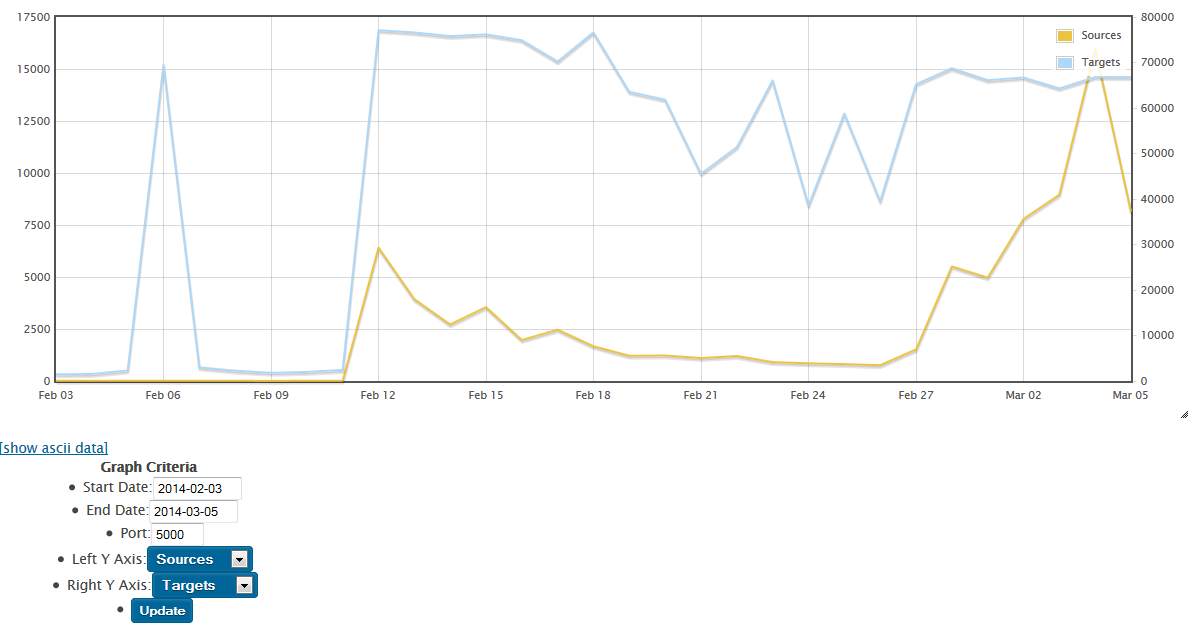
Does anyone have any of these attack packets captured, preferably more than just SYN packets?
Or if anyone has a sample of the attack software or any malware involved, we'd of course love a sample of that as well !
===============
Rob VandenBrink
Metafore
3 Comments
Mitigation Fail for Gas Pump Skimmers
In late January we all heard about bluetooth enabled credit card skimmers on gas pumps. Since that story broke, I've been seeing some attempts at reassuring the public on this issue - I'm seeing pumps at multiple chains having their card readers taped and initialed.

I suppose they figure crooks don't have red tape, or pens. This really is more to reassure consumers, to say "yes, we do check these once in a while to make sure that your card isn't being skimmed". Though that assumes the person checking can tell a reader cover from a skimmer.
I was surprised also to find that this "breaking story" on skimmers which hit the news in January 2014 was first posted by Brian Krebbs way back in 2010 -
http://krebsonsecurity.com/2010/07/skimmers-siphoning-card-data-at-the-pump/
http://krebsonsecurity.com/all-about-skimmers/
... but by the time my brain caught up with who's page I found this on, I wasn't surprised at all.
The main protection we have against skimmers is the moral fortitude of the attendant working at the station. We're depending on that person doing the right thing when faced with a choice between a potentially very large bribe. Skimmer operations can easily net tens of thousands per week, or millions in this recent case https://krebsonsecurity.com/2014/01/gang-rigged-pumps-with-bluetooth-skimmers/. So the risk / reward proposition is a large bribe, often in the tens-of-thousands range, against being aprehended and charged/convicted if the operation is caught and apprehended before they shut down and move on to the next set of target gas stations.
Please, weigh in using our comment form. I'd be really interested if our readers might have solutions or preventitive measures that will work better than the red tape I described in this story!
==============
Rob VandenBrink
Metafore
7 Comments
Triple Handshake Cookie Cutter
Researches have released a paper describing several vulnerabilities in TLS (Transport Layer Security). Some of the attacks have been known for a while, but the paper combines and explains them nicely, and also adds a couple of really clever new ideas. The tricks rely on cutting sessions off and re-starting them in a way that client and server end up with a different (security) state. The full research is available here https://secure-resumption.com/. The good news is that (a) the main impact is apparently limited to connections that use client-side certificates, which is rare, and (b) the researchers have informed the browser vendors early on, and some browsers and TLS libraries are already patched.
2 Comments
XPired!
Yes, Windows XP is about to Xpire. This sunset has been a while in the making, and has even been paused so that the world could admire it a while longer. But now, it really is upon us, on April 8, the earth rotation will stop for a second or three, and then move on.
If you don't know whether you are running Windows XP, you are probably not reading SANS ISC, but for the off chance that you are, Microsoft now have a cute site http://AmIRunningXP.com to tell you. I wonder how many Mac users connect to that site, just to make sure :).
If you are still running XP anywhere, the current MSFT Blog states that users of XP who have "auto-update" turned on will see a *Warning* come March 8. So ... expect grandma to call and ask about the weird pop-up. It was anyway overdue that you talked to her. Kudos to Microsoft for keeping us connected with our family!
Long story short: If you are still on XP, get off it. The mentioned blog is now even offering migration tools, though that "free" offer is somewhat of a trojan: If you want to move applications in addition to your data, it comes with a 23$ price tag. But why anyone would opt to "migrate" applications rather than go for a clean re-install is anyway beyond me .. as is using a "migration tool" black-box without knowing what is actually being migrated.
Here's my XP migration 101:
- Determine if your box can run Windows 7 (enough muscle and memory). Yes, I wrote Windows 7. Who wants Windows 8, anyway?
- If no, buy a new computer. Not necessarily a PC. Then go to step 8.
- If yes, get yourself a new Hard Drive that fits, and a USB drive enclosure for the disk that is currently in the box.
- You'll need to buy a new OS. It doesn't come for free. You might find out that you have to buy Windows 8 after all, because Windows 7 supply is artificially shortened. Well, you had it coming. Life punishes he who is late. What were you waiting for? If the price tag of disk+enclosure+OS turns out bigger than buying a new computer, go to step 2.
- Install the new HD, and the new OS onto it.
- Boot the new OS. It probably won't bluescreen. Reinstall only the ~five applications that you remember using in the past two weeks or so.
- Attach the old HD via USB
- Manually copy whatever you still need of your data over. Be skimpy, you can always go back to the original disk if something vital is missing.
- Enjoy, sort of.
9 Comments
Ongoing Data breach in Chicago Area Taxis
Customers continue to have credit card and banking information stolen from taxi services in the Chicago area. Customers of serveral cab services including American United, Checker, Yellow, and Blue Diamond have fallen victim to data theft over the last several weeks. First American Bank is now advising customers to pay cash for taxi services in the area. For more details check out Brian Krebs story.
http://krebsonsecurity.com/2014/03/illinois-bank-use-cash-for-chicago-taxis/
Thanks to ISC reader Sean Thomas for the heads up.
0 Comments
A buffer overflow in a "Type safe" Language?
Type Safe Languages and Buffer Overflows
There are those of us that do most of our software development in “Type Safe” languages such as Python, Ruby and .NET. Sometimes we smuggly look down upon languages such as C, C++ and Assembly that are not type-safe and do not provide memory protection. You see, type-safe programming languages are "immune" to pesky problems such as buffer-offerflows.
Lets compare the source code of simple C and Python program that assign and print a string. First here is the Python source code.
>>> mystring="This is my string"
>>> print mystring
This is my string
You can see that with Python you don’t have to declare a variable type. You don’t have to specify how big your string will be. All you do is assign a string to your variable and the Python language takes care of the rest for you. Now lets take a look at C version of that code.
char mystring[20]=“This is my string”;
printf(“%s”, mystring);
With C the first line tells the compiler that the "mystring" variable will hold 20 characters. The next line will assign the mystring variable the value “This is my string”. The programmer is responsible for defining both what the variable will store and what the size of variable in memory will be. If the programmer makes a mistake and only allocates 20 bytes of memory then tries to store 30 bytes a buffer overflow condition exists.
Since the underlying Python language takes care of all of the memory management and variable typing for you, it is "immune" to these type of problems. So type use type-safe languages and everything will be fine. Right?
Last week an exploit was posted to pastebin.com that exploited a buffer overflow condition in Pythons socket.recvfrom_into() function. The function was introduced in Python 2.5 and is still vulnerable in Python 3. Every Python program out there that uses that function is potentially vulnerable to remote exploitation. And the exploit for this vulnerabilty is being ditributed in the wild. But how can this be? It is a type safe language!
All type safe languages do offer some protection against memory manipluation attacks, but eventually they all these languages make calls to native libraries. So while software developers in type-safe languages are usually less likely to develop code vulnerable to buffer overflows this exploit serves as a potent reminder than all languages are vulnerable to exploitation. Security professional should always rely on defense in depth.
The vulnerability has been patched in the latest version of the 3.3.4 Python interpreter. Update your interpreter soon. Verions 2.7 interpreters are a little more complicated. The lastest interpreter is 2.7.6 and it doesn’t contain the patch for Issue #20246. The patch is available on the website, but is not compiled into the lastest build yet. In this case prevention isn’t possible so detection and monitoring is essential. Keep an eye on the Python website and watch for the latest updates.
There are a couple of chances to sign up for SANS Python programming course. Join me for Python for Penetration testers in Reston VA March 17-21 or at SANSFire in Baltimore June 23-27.
Python bug report: http://bugs.python.org/issue20246
http://www.sans.org/event/northern-virginia-2014/course/python-for-pen-testers
http://www.sans.org/event/sansfire-2014/course/python-for-pen-testers
4 Comments
Sunday Reading
Time to catch up with that security reading now that your favourite team is second in the league, so lets see what we can do to bring us all up to speed ready for what Monday will bring, so in no particular order:
Data breach, after data breach it would appear as 2014 is turning into the year of the use of "sophisticated techniques" to breach online security.
Securing online applications via a mechanism which is susceptible to a brute force is not a good idea!
Digging through our mail brings a gem. Nigeria Scams are still coming in, I do love todays which is from:
Steve Hall
ISC Handler
www.tarkie.net
2 Comments
Symantec goes yellow
Big Yell'eh has raised its ThreatCon to Yellow - "Medium : Increased alertness" due to increased activity exploiting CVE-2014-0322 which is referenced in Microsoft KB reference 2934088
If you cannot apply the FixIt, best look at the mitigating factors, or wait (and monitor, react, and fix) until the patch comes out to mitigate this vulnerability.
Steve Hall
ISC Handler
www.tarkie.net
0 Comments
How not to code your mobile app
- Credit card numbers stored locally (not quite in line with PCI DSS)
- Connections to "weird" locations (i.e. connections to sites that do not seem to have a connection to the main application)
- Unpinned SSL connections (therefore easily susceptible to MITM)
- "secret" urls on the mobile site which can be accessed outside of the mobile application and used for data-mining.
4 Comments

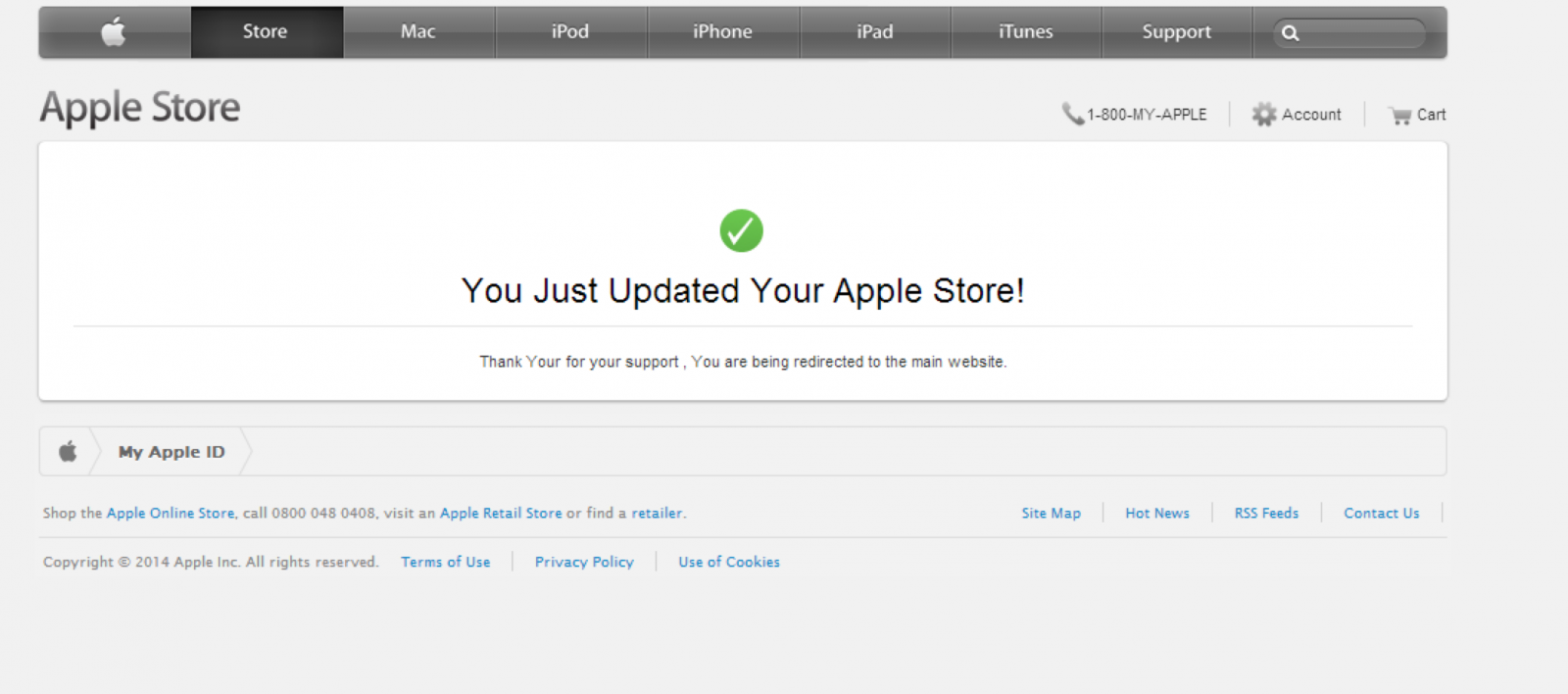


6 Comments