New Variant of Crypto Confidence Scam
In February, we had a few diaries about crypto wallet scams. We saw these scams use YouTube comments, but they happened via other platforms and messaging systems, not just YouTube [1]. The scam was a bit convoluted: The scammer posted the secret key to their crypto wallet. Usually, this would put their crypto wallet at risk of being emptied. But the wallet they used came with a twist: A second key was required. The scammer counted on the victim paying the transaction fee, which the scammer would receive, before attempting to withdraw the funds.
This is a classic "confidence scheme" or "advance fee" scheme. The victim believes they are scamming the attacker out of their money. Instead, they are being robbed. These types of scams are amazingly successful in real life and online. They rely on greedy victims attempting to get something for free (or cheap).
I recently started seeing a new variation of this scam, this time mostly via X direct messages:
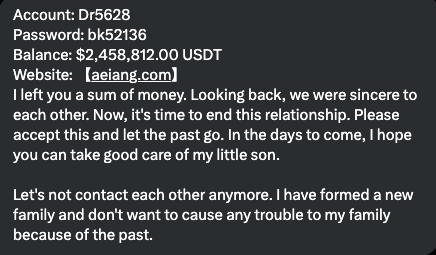
Just like before, the attacker is offering access to their crypto account. The victim is enticed to log in to the account, and there is indeed a substantial amount in this account:
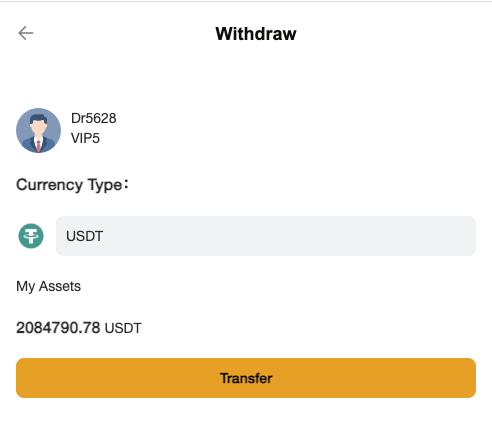
Next, I, of course, want to transfer the money! But this is where the problem starts. To transfer any money from the wallet, I must provide a "KEY." I do not have that key :(. But there is a solution! I could register an account!
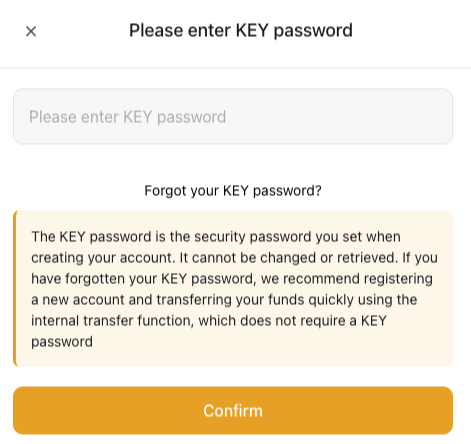
I went to register an account and now attempted to "transfer" the tokens instead of "withdrawing" them. This is where the next snag hits: You must be a "VIP" member of the site, which isn't cheap!
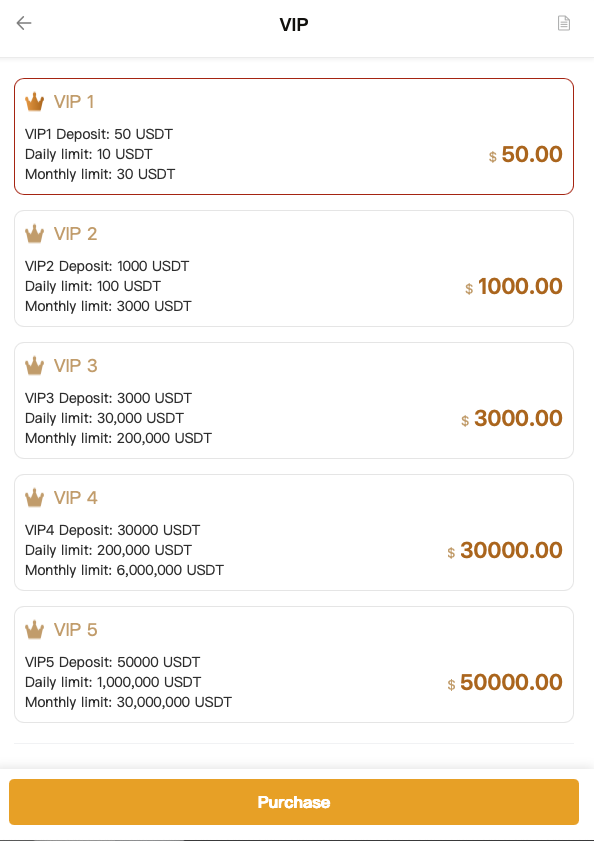
The minimum fee of $50 was more than I wanted to throw away on an obvious scam.
I suspect that, in this case, whoever runs this site (aeiang.com) is the one receiving the money. Overall, I find these scams quite over-complicated. But maybe all this filters victims for those who are greedy enough to fall for this scam. The website does not state who is behind it and uses a generic GMail address for customer support (bitkit998@gmail.com).
[1] https://isc.sans.edu/diary/Crypto+Wallet+Scam/31646
[2] https://isc.sans.edu/diary/Crypto+Wallet+Scam+Not+For+Free/31666
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|



Comments