ADS & Python Tools
Ehsaan Mavani talks about Alternate Data Streams (ADS) in diary entry "Alternate Data Streams ? Adversary Defense Evasion and Detection [Guest Diary]".
I'm taking this as an opportunity to remind you that Python tools on Windows and an NTFS disk, can access alternate data streams.
Like my tool cut-bytes.py, here I use it to show the content of the Mark-of-the-Web stored inside the Zone.Identifier ADS:
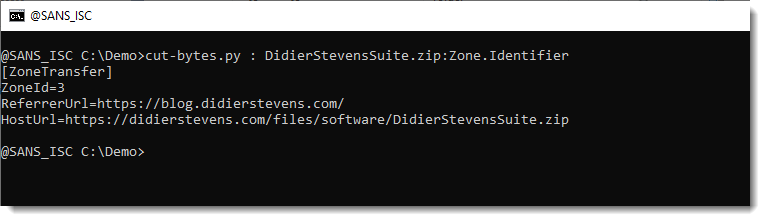
You just need to type a colon (:) followed by the ADS name after the filename.
I didn't have to code this in Python for Windows, it's default behavior.
I did code ADS features in my FileScanner tool. It's not written in Python, but in C for Windows, and I coded features to enumerate and scan alternate data streams.
If you give it a file to scan, it will scan the file content, and also the content of all of its alternate data streams. Like with this download with a MotW:
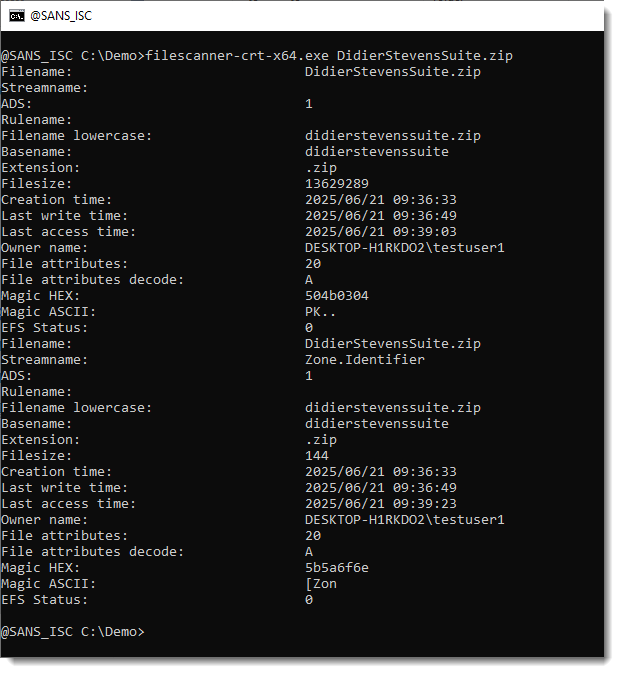
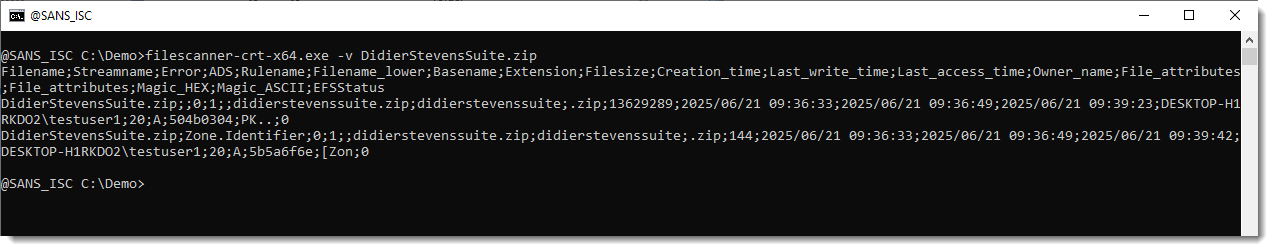
And if you give it a folder or a drive to scan, it will also enumerate and scan all alternate data streams.
Didier Stevens
Senior handler
blog.DidierStevens.com


Comments