Email Spam with Attachment Modiloader
This week (2023-06-21) I found 2 emails attachment in quarantine that had different text with the same attachment. The first one had an Office 365 indicating the admin had setup a custom rule to block the message and could not be delivered to the recipients and what to do to fix it.
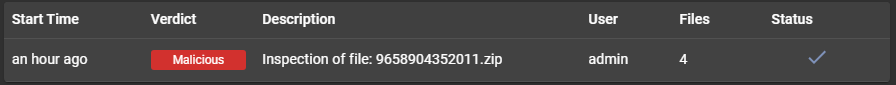
This attachment is well detected by multiple AV vendor as trojan downloader. I used AssemblyLine [1] for to analyse this zip file (9658904352011.zip) [2] and recovered a long list of indicators from the analysis. Brad [3] published a similar diary with Modiloader last month.
AssemblyLine classifies the indicators as informative, suspicious, malicious during the analysis.
Emerging Threat Signature
ET MALWARE FormBook CnC Checkin (GET)
Indicators of Compromised - Malicious
atlas-management.tech
94.73.149.144
Indicators of Compromised - Suspicious
www.7523615.com
www.espiaocelular.foundation
www.harrisonfanilyvets.co.uk
www.realt39.ru
www.ufalive.ru
45.33.2.79
45.79.19.196
96.126.123.244
209.197.3.8
SHA256 Hashes
38b0084c5d02a04696027b5f58eaf6f528af5ba303f67f8cdf2d193a267beda8
fe9f53f107e573b8ab26e52e4f894d5f157b57e81a828ff4e530c3741c0006d5
SSDEEP
24:hYIJAC8kMxMg8p0MlgAtHQTVC94yXzeUt2:OPxMvpflmVC946aUc
12288:mJJqvi0qOhfCAUBBzjjSphHrqFDq++ByPcwie8EWnLI4jREohPXYKC:mJshqECZ3njSnHrqFgwdePL/VE8fDC
[1] https://isc.sans.edu/diary/Assemblyline+as+a+Malware+Analysis+Sandbox/29510
[2] https://www.virustotal.com/gui/file/38b0084c5d02a04696027b5f58eaf6f528af5ba303f67f8cdf2d193a267beda8
[3] https://isc.sans.edu/diary/Malspam+pushes+ModiLoader+DBatLoader+infection+for+Remcos+RAT/29896
[4] https://community.emergingthreats.net/
[5] https://tria.ge/s/family:modiloader
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
.png)


Comments