Phishing Page Branded with Your Corporate Website
Here is another perfect example that shows how attackers abuse free services...
Phishing campaigns are often combined with a layer of social engineering to make the victim more confident to click on a link or to open the attacked file. I spotted an interesting phishing email redirecting you to a classic login page.
The page asks you to provide your credentials to “unlock” access to a PDF document, but the attacker implemented a nice trick. The background of the fake login page is… a screenshot of your corporate website!
Here is an example with my own company:
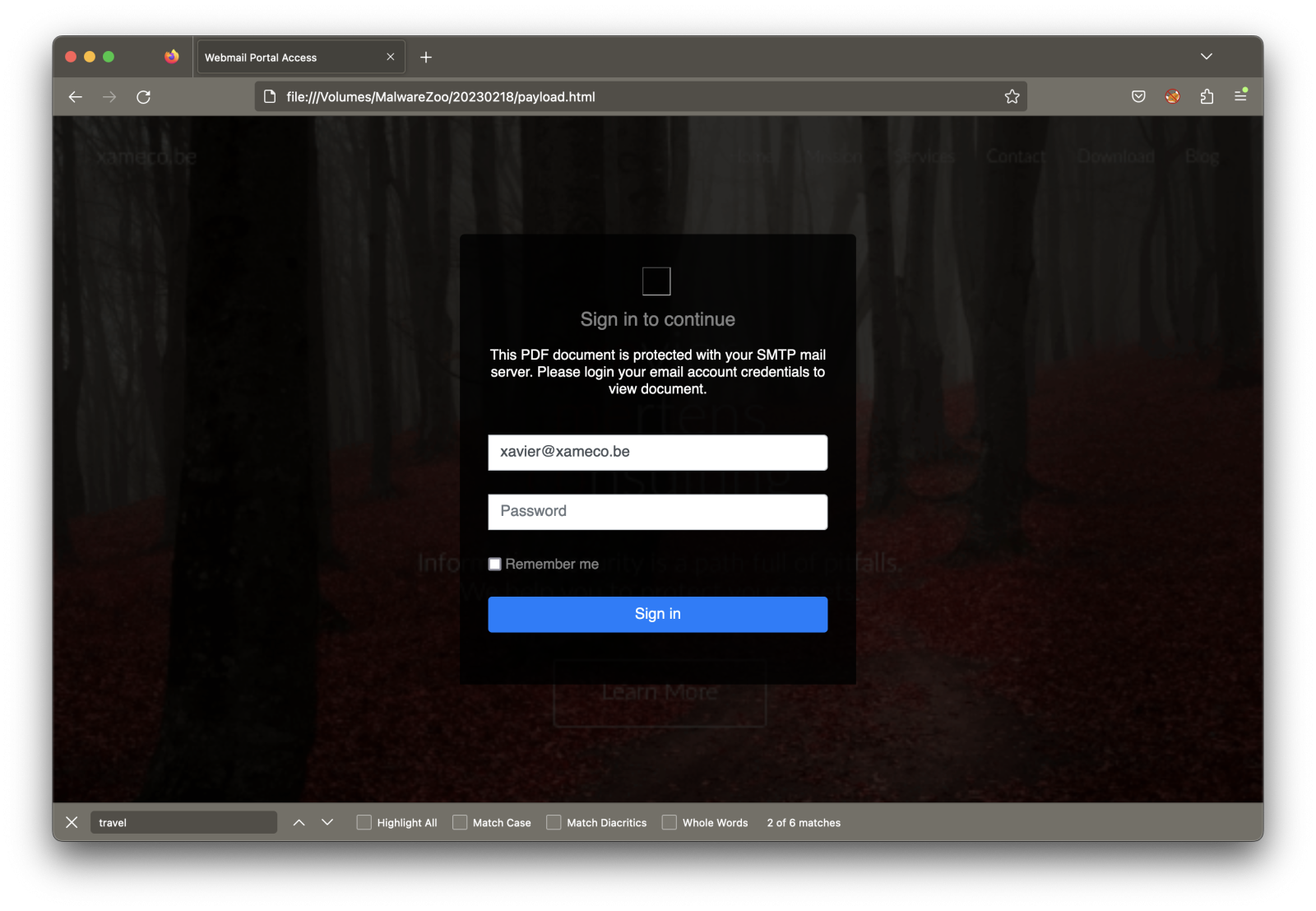
I changed the targeted email address, and here is an example with the sans.org website:
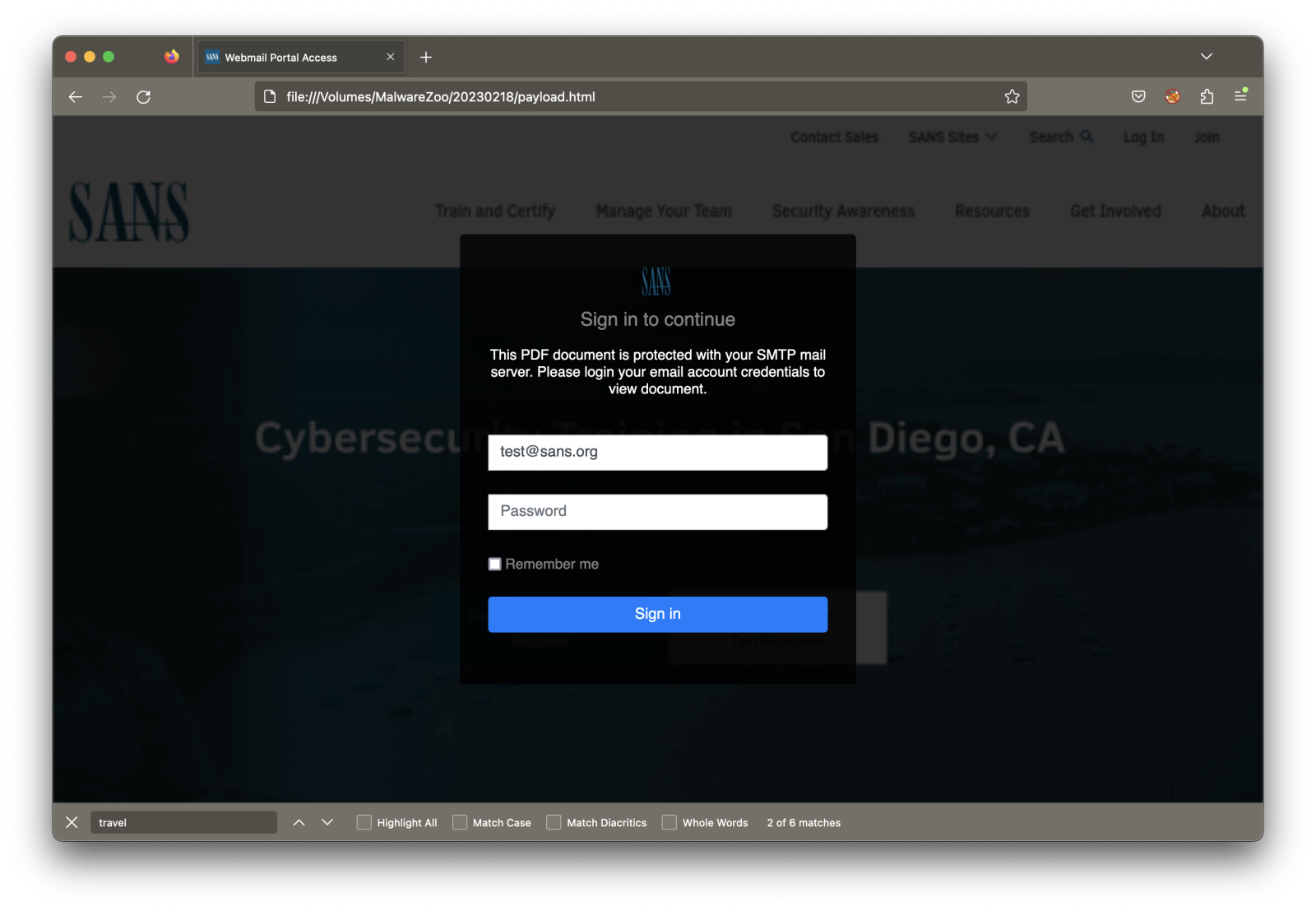
I deobfuscated the JavaScript, and here is how they implemented this:
<script>
let emailzz = "test@sans.org";
function jpgvbqitfwqpnhjgqktfqwpwoufrhtbrkktpjfizjuqjvxjjkperhumw(fscigkwyepzcytekcylktcjcpcurjwwebroblbnfyewnlqtqzgtwaa)
{
return fscigkwyepzcytekcylktcjcpcurjwwebroblbnfyewnlqtqzgtwaa.split("").reverse().join("");
}
var dtisejcxzuvjbshjmgaewqkxryjqdxcqfykqczkhbwtdmytbtwgliiqerzem=document.write(atob(...)));
</script>
This function decodes a stream of Base64 data that has been reserved. Pretty simple obfuscation. To make the script more difficult to read, this technique has been implemented ten (yes, you read properly) times! I wrote a CyberCheck recipe to decode it:
Label('Loop0')
Regular_expression('User defined','[a-zA-Z0-9+=]{200,}',true,true,false,false,false,false,'List matches')
Reverse('Character')
From_Base64('A-Za-z0-9+/=',true)
Conditional_Jump('[a-zA-Z0-9+=]{200,}',false,'Loop0',8)
Regular_expression('User defined','[a-zA-Z0-9+=]{200,}',true,true,false,false,false,false,'List matches')
From_Base64('A-Za-z0-9+/=',true)
By the way, this is a good example to demonstrate how CyberChef recipes may contain conditional jumps and label to implement loops! Pretty handy in this case.
Now, here is the interesting piece of code found in the deobfuscated script:
<script>
const emailarr = emailzz.split("@");
let webzz = emailarr["1"];
const webzzarr = webzz.split(".");
let webnamezz = webzzarr["0"]
let googlezz = "https://www.google.com/s2/favicons?domain="+webzz;
let weblogozz = "https://logo.clearbit.com/"+webzz;
var bkimage = "url('https://image.thum.io/get/https://www."+webzz;"')"
</script>
...
<script>
document.body.style.backgroundImage = bkimage;
</script>
The variable 'emailzz' has been defined in the original HTML page (see above), and the domain is extracted. How the attacker gets the background?
It’s a free service provided by thum.io[1], the free website screenshot generator:
hxxps://image[.]thum[.]io/get/https://www."+webzz;
The same domain name is also used to fetch interesting data:
- The company logo is fetched via hxxps://logo[.]clearbit[.]com/<domain>
- The favicon is fetched via hxxps://www[.]google[.]com/s2/favicons?domain=<domain>
These graphical elements help to build the fake page that looks familiar to potential victims!
[1] https://thum.io/
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Online | Greenwich Mean Time | Oct 27th - Oct 31st 2025 |


Comments
I reached out to Clearbit after reading about their logo service, but only were only offered to have my own domain names/logos disallowed. I did my best to convince them their Logo API service, though "neat"/"cool" was being and would continue to be abused by malicious actors.
I did not get the impression they were interested in changing their services, so I've settled on adding them to our domain RBLs.
Joel
Feb 21st 2023
2 years ago
J0xA0
Feb 24th 2023
2 years ago