Vulnerabilities on the Rise?
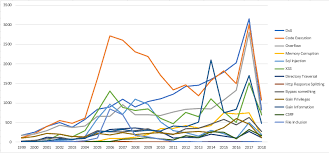
Lately, stories of stolen data, compromised systems, and vulnerabilities that send us scrambling to patch, headline the news. It seems that we have been taking two steps forward and one step back when it comes to fighting the battle to protect our systems and networks. Exactly how bad is it and what does the future hold? I am a big fan of metrics, so I did some digging on the data that exists and what it can tell us. I started with looking at CVEs and what that trend looks like over time. I used the CVE data from a site I like called cvedetails.com. All data here comes from the National Vulnerability Database (NVD). How bad has it become and what is the focus of the bad guys? Here is a chart I made of all the CVEs since 1999:
As you can see, there has been a steady increase in vulnerabilities discovered over the years. In 2017, it seems there was a large rise in several of the categories. It's not surprising that the areas of interest are DoS, Code Execution and buffer overflows. Categories of Gain Information and Cross Site Scripting (XSS) were also areas with an uptick in 2017.
What does that mean for those of us focused on defending the networks? Well, if you're a pessimist, you probably should unplug your network and hide. I believe we see more CVEs because every year there are more cyber-savvy people that understand computers and networking. They know how to find the vulnerabilities and its become lucrative for them. I'd like to think responsible disclosure drove most of these, but sadly these vulnerabilities could have been used against us before they were found and reported. I could not find a way to determine how many of them had exploits in the wild when they were released. If you know of a way to pull this data (without manually going through each of them), please let us know.
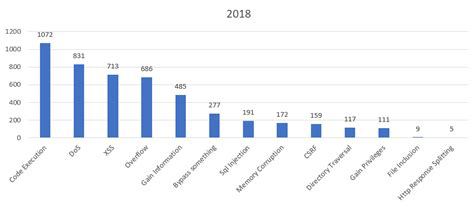
So what does the future hold for 2018? Its hard to say at this point, but here is some interesting data. This chart with just the CVEs so far for 2018:
Looking at code execution, we are just starting May and already we are almost half way to what we saw in 2017 for vulnerabilities that have been found and disclosed! Keep in mind, there is no way to estimate those out there that have not been made public or are currently in use. Are the CVEs representative of the tip of the iceberg or do they represent the vast majority of the vulnerabilities discovered? Regardless, it becomes increasingly obvious, by the number of growing vulnerabilities found and disclosed each year, that you cannot slack off when it comes to monitoring your infrastructure. With the increase in technology running everything, the complexity of today's networks and systems, and the rise of a generation that has only known a world run by technology, the attack surface and the knowledge to exploit it will present unprecedented challenges to those charged with defending!


Comments
Maybe a metric of the number of products with reported vulnerabilities?
I suspect there may be correlation involving the number of vendors or products involved in vulnerability reporting compared to the raw number of vulnerabilities reported.
In other words... More engagement by the community of vendors and researchers can directly impact the number of reported vulnerabilities. Of course, more software products in the market could also contribute to the rise in numbers per year.
Similar to incident reporting.
I worked in an organization where I had to build a security program from scratch. The year prior, the "outgoing" security officer had zero reports of security incidents. When I took over, incident reporting that first year indicated about 40 reported incidents. The subsequent years, those numbers doubled as the security program (including employee awareness and technical sensors) matured and became more relevant in operations. Basically, the number of sources for reporting increased as the program matured.
I suspect vulnerability reporting to the NVD may still be going through a similar evolutionary process.
Anonymous
May 8th 2018
7 years ago