Keeping the RATs out: the trap is sprung - Part 3
As we bring out three part series on RAT tools suffered upon our friends at Hazrat Supply we must visit the centerpiece of it all. The big dog in this fight is indeed the bybtt.cc3 file (Jake suspected this), Backdoor:Win32/Zegost.B. The file is unquestionably a PEDLL but renamed a .cc3 to hide on system like a CueCards Professional database file.
Based on the TrendMicro writeup on this family, the backdoor drops four files, including %Program Files%\%SESSIONNAME%\{random characters}.cc3
This indicates that bybtt.cc3 is one of the dropped files rather than the source file.
Per the Microsoft writeup for Backdoor:Win32/Zegost.B, once installed, it attaches its code to the legitimate Windows process, svchost.exe.
This is therefore likely the svchost.exe (MD5 20a6310b50d31b3da823ed00276e8a50) that Jake sent us. It's all coming together.
The Microsoft writeup also states that after connecting to the C2 server it receives commands to copy, execute, download, and delete files, gather information from the RAS phonebook, and capture screenshots. I'll confirm each of these steps from strings or a specific tool.
Unfortunately, bybtt.cc3 wouldn't run easily in my sandbox (it's a PEDLL and yes, I know it can be done but there's only so much time in the day) but I learned or confirmed everything I needed to create IOCs for you.
First, this sample connects to ip.sousf8.com and while its registered to Peng Peng (um, yeah) the server is actually in the US.
What I really didn't like is that searches for sousf8.com prove that its been embedded as Louis Vitton forum SPAM and other evil crap that point to hxxp://fz.sousf8.com. Do not freaking go there please.
This domain points to 142.4.120.9. Jake reported to us, based on network connections and NetFlow analysis that he had RDP (TCP 3389) connections to 142.4.120.8 using mylcx.exe which we've already discussed. What what!? Oh, boy. So again, these server are in San Jose, CA but they're registered to vpsbus in...wait for it...please hold...prepareth thy shocked face...Jinjiang, in the province of Fujian, in the country of...China.
The three domains hosted on 142.4.120.9 are 9uufu.com, sousf8.com, taobaofu.com.
The ASN for these IPs belong to PEG TECH INC, a notorious spammer.
According to Wepawet, who says that fz.sousf8.com is benign, that flow includes a redirect from hxxp://cnzz.mmstat.com to hxxp://pcookie.cnzz.com. Again, please don't. Both are immediately associated with Troj/Clicker-GL (more crap adware).
There are all kinds of malicious attributes in the bybtt.cc3 file too, in addition to all the IOC fodder above.
According to HookAnalyser, there's a ton of what looks like NOP padding in this sample.
[!] Found 373 traces of NOP instructions (a potential shellcode - Suspicious)
[-] At the offset 00001109, found: '\x90\x90\x90\x90\x90\x90\x90'
And it notes the fact that:
[!] Executable is Debug aware
[!] Executable could spawn a new process
[!] Executable can enemurate processes
[!] Executable could hook to other processes
[!] Executable is potentially anti-debug aware
Yep.
Strings confirms the RAS phonebook reference from above, not two lines removed from the hostile domain:
Microsoft\Network\Connections\pbk\rasphone.pbk
%USERPROFILE%\Application Data\Microsoft\Network\Connections\pbk\rasphone.pbk
Global\b%d_%dj
+@22220Sdag892+
ip.sousf8.com
References to GDI32.dll and CreateCompatibleBitmap are indicative of the screencapture attribute, and there are way too many elements to its capability to "copy, execute, download, and delete files" to spell each out but Figure 1, created using PeStudio helps confirm.
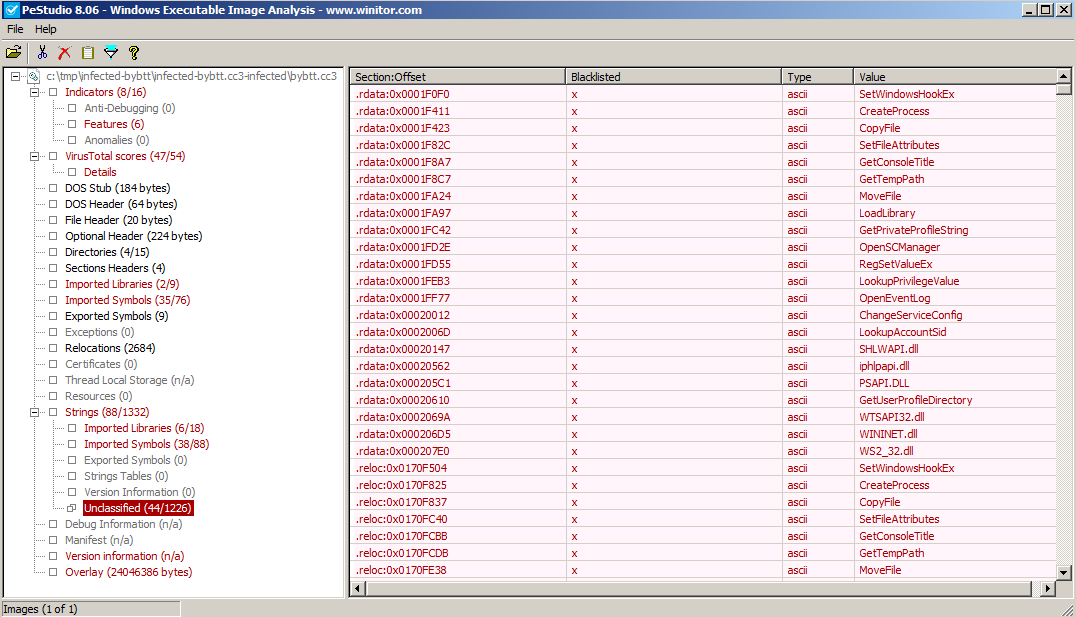
Figure 1
What a swirling vortex of nastiness. There are so many rabbit holes to go down here, but I promised you IOCs.
I'm not going to go for file name or size or hashes, because they won't match. I'm working from one of the dropped files and as we've seen there's much randomization.
But we know for sure the related domain names, IPs, and we know thanks to Jake who teased a lot of this from the running server during his IR process, that it creates specific registry keys (PeStudio confirmed as did strings). Figure 2 is the IOC build.
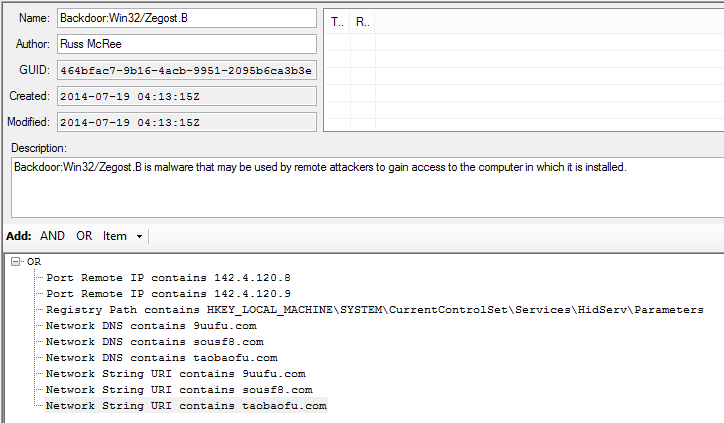
Figure 2
Its cool to match the great work Jake did during IR with static analysis and turn it into what is hopefully actionable intelligence for you, dear reader.
I've posted the IOC XML files for you:
- http://holisticinfosec.org/iocs/464bfac7-9b16-4acb-9951-2095b6ca3b3e.ioc
- http://holisticinfosec.org/iocs/7d540cb4-5a52-46e4-9465-081e6735cb3d.ioc
- http://holisticinfosec.org/iocs/dea382df-9592-4528-b9e5-fef136e30805.ioc
Remember that IOCs change quickly and that another very related sample may exhibit entirely different indicators. So don't treat these as a panacea, but do use them as reference for your hunt and detect missions. Please feel free to enhance, optimize, tune, improve, criticize, and assassinate the character of the IOCs; they're always a work in progress, I won't be hurt.
Good luck and let us know how it goes!
Cheers.


Comments
Anonymous
Jul 19th 2014
1 decade ago
Anonymous
Jul 19th 2014
1 decade ago
Anonymous
Jul 21st 2014
1 decade ago
(Maybe this is out of scope of the current blog post. But I think this is important)
Anonymous
Jul 22nd 2014
1 decade ago
Almost won Forensics article of the year even: https://forensic4cast.com/forensic-4cast-awards/2014-results/ :-)
Anonymous
Jul 27th 2014
1 decade ago