Take Downs and the Rest of Us: Do they matter?
Last week, the US Department of Justice published a press release entitled "Justice Department Conducts Court-Authorized Disruption of Botnet Controlled by the Russian Federation’s Main Intelligence Directorate of the General Staff (GRU)" [1]. The disruption targeted a botnet built using the "Moobot" malware. According to the press release, this particular botnet focused on routers made by Ubiquity, using well-known default credentials.
Why do nation-state actors go after "simple" home devices? Usually, these attacks are associated with simple "vandel ware" like Mirai and similar bots. Often, a Miner may be deployed as part of the attack. But even for more sophisticated attackers, these devices are attractive:
- They may provide access to more interesting networks. The Ubiquity Edge router attacked by this Moobot variant is often used as a perimeter device for smaller remote networks. This may provide access to a remote site of a power network or industrial equipment deployed remotely. Disabling this equipment may cause significant cost if a technician must visit the remote site.
- Due to the enormous scan volume for these default credentials, the attacker can hide in the noise created by vandals and miners. The attack tools are essentially identical. Even if the attack is discovered, it is likely considered a "nuisance attack" and not attributed to a particular actor. For a sophisticated attacker, winning with a simple default password is far preferred over winning using a zero-day vulnerability. Each time a vulnerability is exploited, the attacker risks being discovered, and the zero-day vulnerability may be fixed.
- "Innocent" home devices make a great attack platform. Some networks will, for example, block access from certain countries or specific hosting providers. Having access to a diverse set of commodity devices in different networks is a great asset to building up an attack infrastructure of proxies to obfuscate the source of the attack.
This is also not the first time a nation-state attacker was caught using routers to build an attack infrastructure. For example, in 2018, Kaspersky published a report of the "Slingshot APT" taking advantage of vulnerabilities in Mikrotik routers [2]. This threat has been active since 2012, according to Kaspersky.
But let's go back to the last takedown: Did it matter? All indications provided by the Department of Justice are that the botnet was dismantled. The press release stated that affected routers were secured by applying firewall rules to block access to the device. Likely this meant a firewall rule blocking port 22. It needs to be clarified if the rule was applied in a way that would survive a reboot.
The default username and password the affected devices use is "ubnt". Using our honeypot data, we can easily check how popular scans are for this username and password combination. The username and password combination ubnt/ubnt has been in the top 10 password combinations for 22 days this year (out of 55 days total). Ubiquity equipment is a popular target. In addition to the Edge Routers targeted by the takedown, this password combination is used for other Ubiquity equipment like cameras and switches.
A quick look at the number of sources scanning for this username and password combination does not show a significant drop
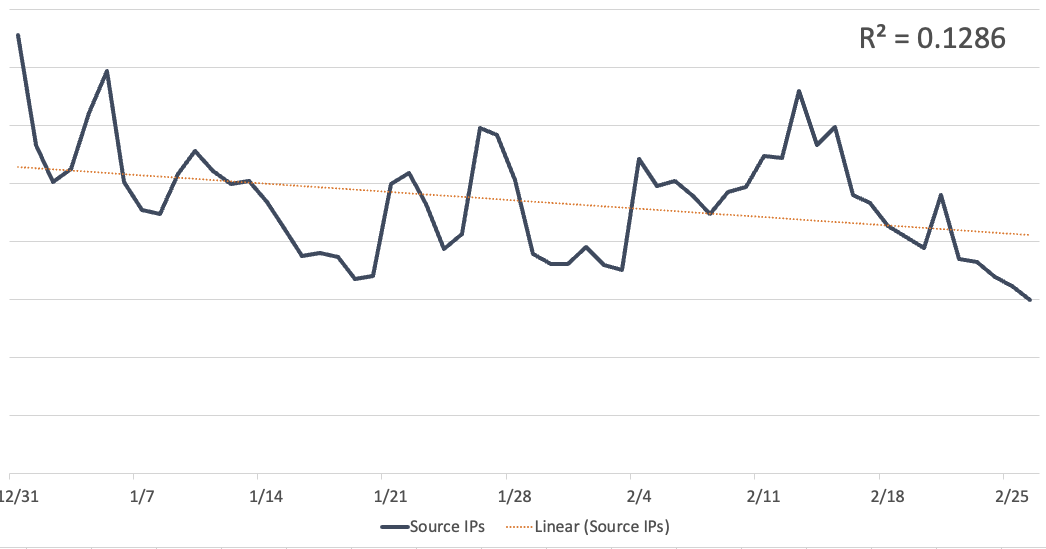
I did a linear regression that showed a slight drop, but the data was too noisy to support the correlation.
The number of reports shows an interesting peak at around January 26th. This peak can be attributed to a single source IP address: %%34.18.78.72%%. The IP address is part of Google's cloud. Other than the timing, there is no evidence that this address is related to the botnet.
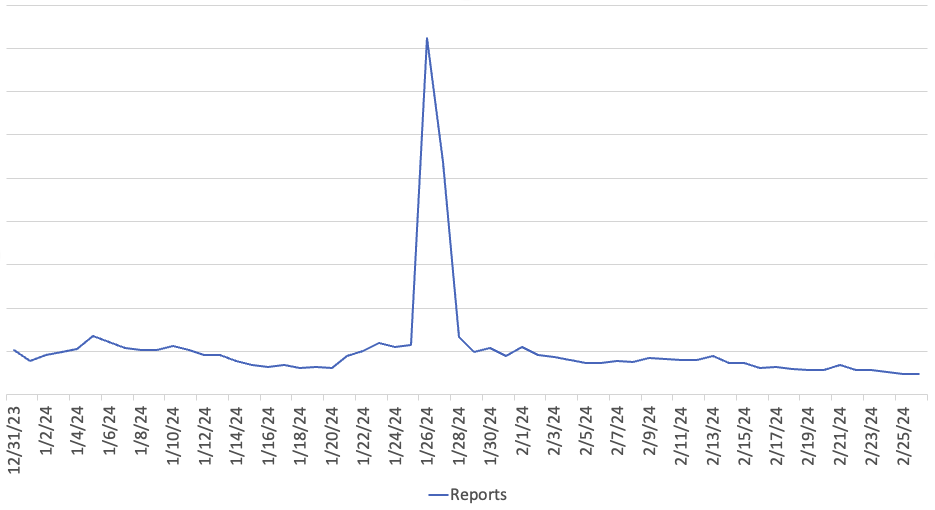
Without the peak, a small drop in reports may be visible over the last few months.
So what does this all mean?
The drop in scans for "ubnt"/"ubnt" may be due to the takedown, but the drop is insignificant, and there is no strong enough correlation to suggest the takedown causes it. Attackers still use default passwords. We do see many more attempts for "vyos" and "345gs5662d34" are more popular than "ubnt". Takedowns will be able to reduce specific threats, but in the end, they will not protect us from negligent vendors shipping equipment with default usernames and passwords. Until then, these devices will remain the "mosquitoes of the internet." Ubiquitous, small and deadly.
[1] https://www.justice.gov/opa/pr/justice-department-conducts-court-authorized-disruption-botnet-controlled-russian
[2] https://s3-eu-west-1.amazonaws.com/khub-media/wp-content/uploads/sites/43/2018/03/09133534/The-Slingshot-APT_report_ENG_final.pdf
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|


Comments