PNG Analysis
I updated my tool pngdump.py to deal with all the different samples tagged with PNG on MalwareBazaar.
The analysis results of a normal PNG file looks like this:
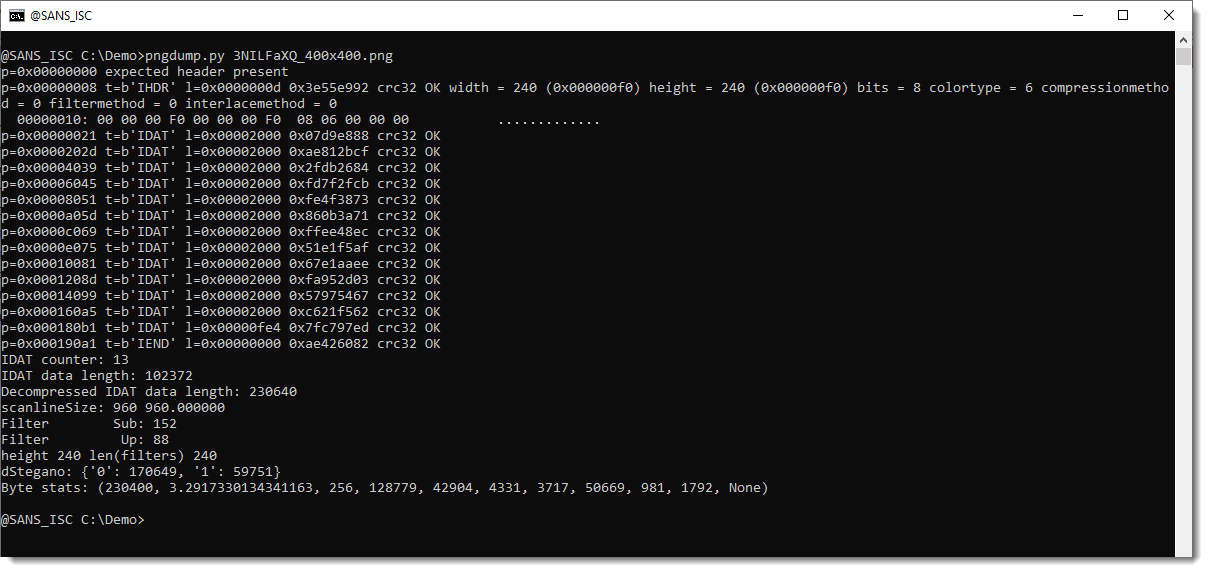
But I also had samples that were not valid PNG files: The data of the IDAT chunk(s) was not ZLIB compressed. Notice the decompression error:
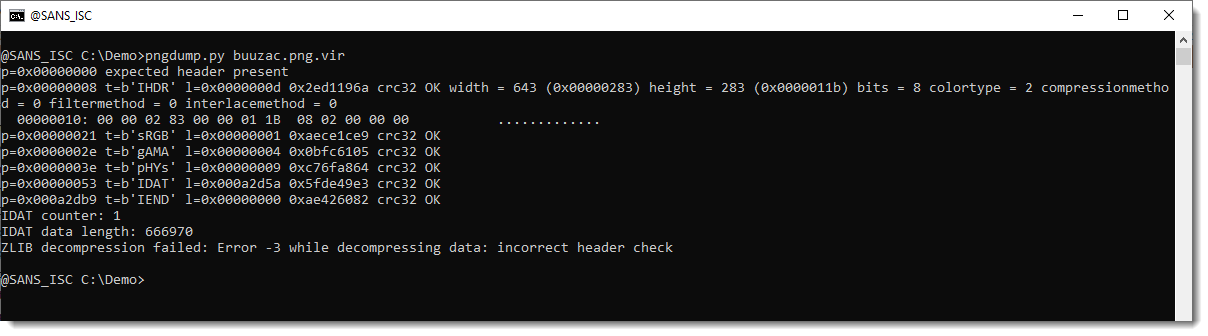
According to MalwareBazaar's info for these files, they were PNG files with an encrypted IcedID payload.
So I set out to write a small script that would help me detect PNG files carrying an IcedID payload.
There are a couple of decryptors online, like this one and this one. The payload is RC4 encrypted, and the RC4 key is in front of the payload (8 bytes long). One decryptor extracted the key from position 0 in the chunk data, another from position 5.
Decrypting this payload is not difficult, thus I wrote a small script for my translate.py tool. It has 2 functions: Check and Decrypt.
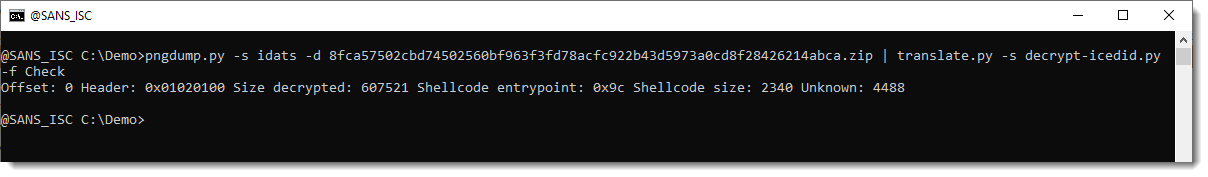
I use Check to validate that the PNG I'm analyzing, is an IcedID payload:
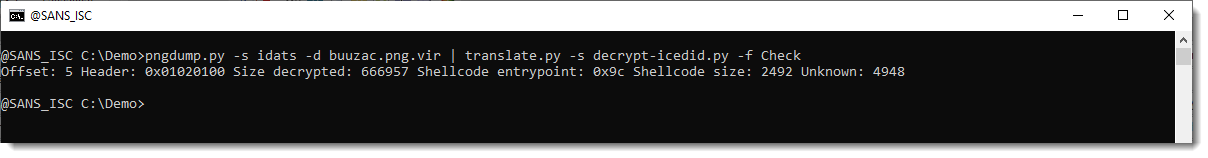
The key is found at offset 5, and the header and other metadata indicate that this is indeed IncedID.
If you want the decrypted payload, use function Decrypt, for example like this:
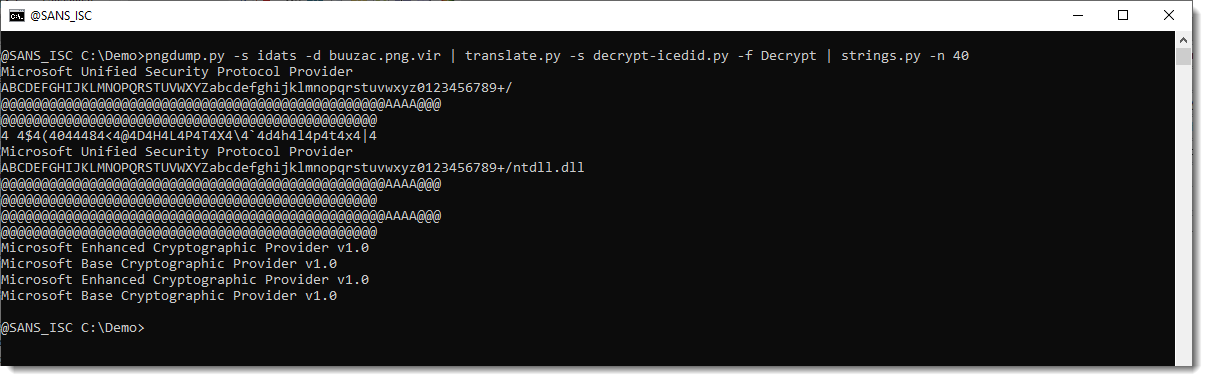
Here is another example with offset 0:
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com


Comments