Buffer overflows found in libpcap and tcpdump
It is always a bit worrisome when vulnerabilities are found in our favorite tools, but our tools are software like any other software and can have bugs, too. One of the feeds I have in my RSS reader is NIST National Vulnerability Database (NVD) feed. Earlier today, I noticed a bunch of CVEs show up there for libpcap and tcpdump. I hadn't noticed any major announcements of new versions or any automatic updates of those tools on any of my linux boxes, so I decided to head straight to the source, www.tcpdump.org. It turns out, there were new versions of both libpcap (new version is 1.9.1) and tcpdump (version 4.9.3) released on Monday. And, there under latest releases, it notes that this release "addresses a large number of vulnerabilities." It should also be noted, this is the first release in over 2 years. Quite of few of the vulnerabilities have CVEs dating from 2018. In all, this update addresses 33 CVEs. Hopefully, the major linux distros will roll out updates over the next few days or weeks. I haven't seen any indication that folks have tried to craft traffic to exploit any of these vulnerabilities, but that is always a concern when a tool like tcpdump or wireshark or the like has buffer overflows in their protocol parsers/decoders/dissectors. So, if you use tcpdump and/or any libpcap-based tools in your toolbox for network monitoring or network forensics, be on the lookout for updates from your linux distro or tool vendor or just go ahead and build your own copy from source.
---------------
Jim Clausing, GIAC GSE #26
jclausing --at-- isc [dot] sans (dot) edu
"Lost_Files" Ransomware
Are good old malware still used by attackers today? Probably not running the original code but malware developers are… developers! They don’t reinvent the wheel and re-use code published here and there. I spotted a ransomware which looked like an old one.
The following email landed in my mailbox:
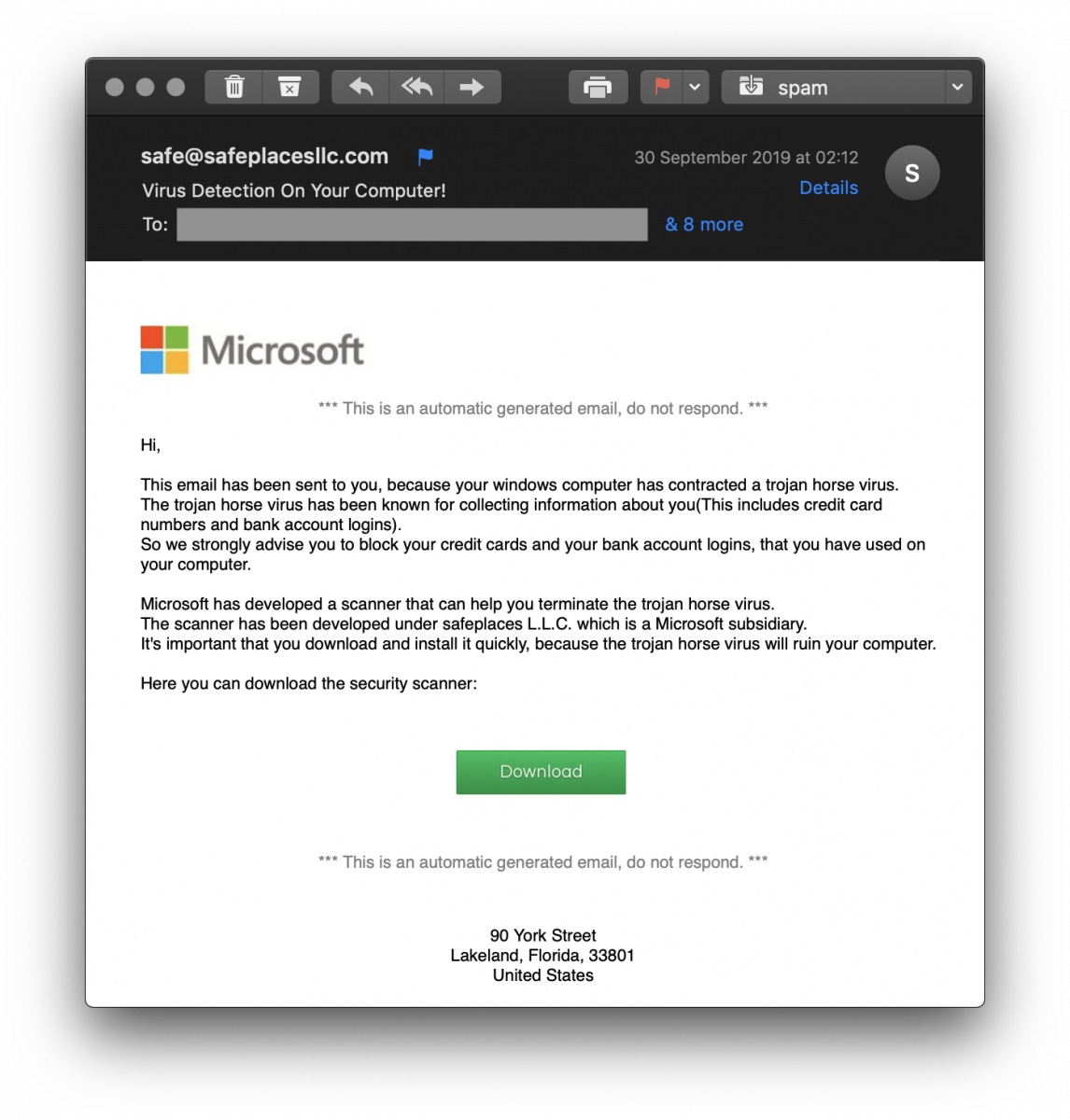
Not very well designed, the sender email address is even not spoofed but it made me curious. The delivered message is always the same: to make the victim scary and lure it to click on a link. The “Download” button hides the following URL:
hxxp://104[.]168[.]159[.]201/WSS.zip
Let’s visit the URL and grab a copy of the WSS.zip archive (SHA256:02629729329cde8d1892afa1d412a75cfcc338826c0b5087a2ef3182b5a1af85). It’s indeed a valid archive:
$ unzip -t WSS.zip
Archive: WSS.zip
testing: Windows Security Scanner/ OK
testing: Windows Security Scanner/desktop.ini OK
testing: Windows Security Scanner/Resources/ OK
testing: Windows Security Scanner/Resources/32BitRun.exe OK
testing: Windows Security Scanner/Resources/Installer_exe.exe OK
testing: Windows Security Scanner/Resources/SecurityUpdater.exe.exe OK
testing: Windows Security Scanner/Resources/ShortCutVBS.vbs OK
testing: Windows Security Scanner/Resources/Temp_Test.tester OK
testing: Windows Security Scanner/Resources/Windows.LNK OK
testing: Windows Security Scanner/Windows Security Scanner.exe OK
No errors detected in compressed data of WSS.zip.
Strings found in the “Windows Security Scanner.exe” PE file reveal immediately the type of malware:
Attention!!! First of all we are terribly sorry to have encrypted your data. Because we are human too and we feel some guilt encrypting your data. We offer that we can help you decrypt it again for a small amount of Bitcoins(BTC). The amount that we need from you is 500 USD that you will transfer to our BTC account. To Get your unique tool to decrypt your files, your need to push the button below and your BTC payment address will show, transfer 500 USD in BTC to that address. After you have transfered the BTC you are going to send an email to our email address(Our email will also get displayed when pushed the button). Where you provide your BTC address of the wallet that you used to send our BTC(If you have other comments, you are welcome to say it)[Also remerber to check your spam inbox for when we send your decryption tool]. We will check it, if you have sent the BTC, you will get your decryption tool. Everything from family memories to the hard work of yours, will be washed down the toilet and it will never return. So it's strongly advised that you start paying us for helping you to decrypt it. In the case that you are a little older and don't know much about all the computer stuff then you can ask your children or grandchildren. PLEASE Look below for additional information. Needing help to get your BTC? Some resources to get started with BTC: https://coinsutra.com/buy-bitcoin-uk/ https://cryptocurrencytutors.com/getting-started-with-bitcoin/ https://blokt.com/guides/10-best-bitcoin-cryptocurrency-exchanges-2019-proven-safe-exchanges Keep in mind! When you buy BTC you should buy slightly more than 500 USD, just in case the price drops. Also you need it as sending fees which varies at times. So it's recommended to buy 510 USD worth of BTC from one of the exchanges. Then again we are sorry for what happened to you, hope you will have better luck next time! :-)
or
Hi, This is Lost_Files Ransomware, Pay us 500 USD to get our decryption software. So that you can get your files back. The payment is going to be paid in Bitcoin(BTC). For more information about this please click the same EXE file you clicked when you lost all your files. There will be detailed instruction there. The email is: Lost_Files_Ransom@secmail.pro Transfer BTC to this address: 13nRGetwvc7UZF8P5KM9bWqHGK6tMk7wyf
Executed alone, the main binary does not work without the files in the Resources directory. They are also referenced in the code:
\Resources\ \Resources\Temp_Test.tester \Resources\Windows.LNK") \Resources\\ShortCutVBS.vbs
Its SHA256 is df693cc9d9e89e1db2a8edeaf2e77723e853f363da510a15ade9be79df96dc5e and its compilation time is Sun Sep 29 15:27:35 2019. The current VT score is 30/58[1]. Identified by some AV as “Hidden Tear”. This ransomware is pretty old and has been open-sourced on GitHub a few years ago[2].
Let’s execute it in a sandbox:
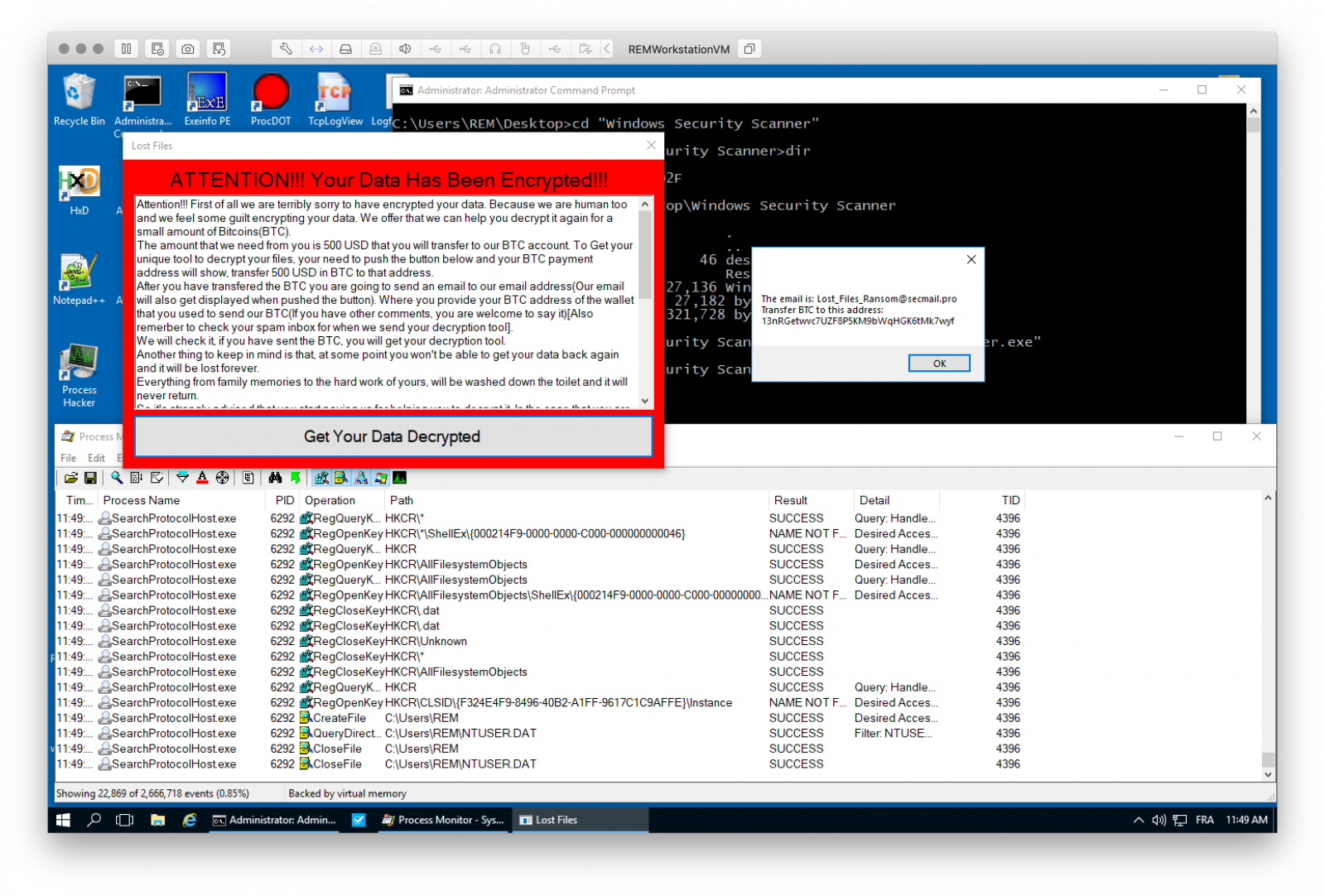
Encrypted files are the following (extracted from the binary):
.xxx .sdf .txt .doc .docx .xls .pdf .zip .rar .css .xlsx
.ppt .pptx .odt .jpg .bmp .png .csv .sql .mdb .php.asp
.aspx .html .xml .psd .bat .mp3 .mp4 .wav .wma.avi .mkv
.mpeg .wmv .mov .jpeg .ogg.TXT .DOC .DOCX .XLS .PDF
.ZIP .RAR .CSS .XLSX .PPT .PPTX .ODT .JPG .BMP.CSV
.SQL .MDB .PHP .ASP .ASPX .HTML .XML .PSD .BAT
.MP3 .MP4 .WAV .WMA .AVI .MKV .MPEG .WMV .MOV
.OGG .JPEG
Once processed, files are renamed with the extension '.Lost_Files_Encrypt'. Apparently, the ransomware started to scan for SMB services (TCP/445) on random IP addresses after the initial infection. Probably trying to infect host vulnerable to EternalBlue.
I did not find relevant online information about this ransomware. I'll have a look deeper at the binaries. Did you have something interesting to share about this threat? Please do!
[1] https://www.virustotal.com/gui/file/df693cc9d9e89e1db2a8edeaf2e77723e853f363da510a15ade9be79df96dc5e/detection
[2] https://github.com/goliate/hidden-tear
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key


Comments