New tool: mac-robber.py
On a recent forensic investigation where we couldn't take the Linux system down to image the disks, I was forced to do live response. Fortunately, I was able to get a memory image, but I also wanted a filesystem timeline. I first went to my old friend fls from The SleuthKit (TSK), but for some reason, it failed. So, I tried mac-robber (also from TSK) and it, too, failed. Not one to give up easily, I decided to write my own version of mac-robber in Python. Like the TSK mac-robber, it outputs the data in body file format (so that it can be fed into mactime or elasticsearch). Like the TSK version, by default, it does not hash the files (so it doesn't modify access times), so the "MD5" column defaults to 0. In this case, though, I had reason to believe that there might be multiple copies of some potential malware scattered around the filesystem, so I really wanted to grab hashes, too. So I included the capability in the tool (in my next diary, I'll explain the trick I used to grab hashes without modifying access times). A couple of other notes on the tool. It only hashes "regular" files, it doesn't attempt to hash soft-links, block or character device files, pipes, or sockets. It also skips /proc/kcore which to os.stat() looks like a regular file, but on my dev box is 128TB (a little more than I want to hash). At the moment, it uses MD5 as the hash because that is what fls uses, but I could easily be talked into substituting SHA256 (or SHA3 of whatever length, though in Python -m switch behaves just like the corresponding switch in fls and allows you to prefix the path with a system name or drive letter. The -r switch allows you to remove a prefix (for example, when the directory in question has been mounted on /mnt, but you want your report to show the actual path on the system in question). The -x option actually needs more work, at present, it isn't as flexible as I'd like, but if you want to skip a specific directory or file you can.
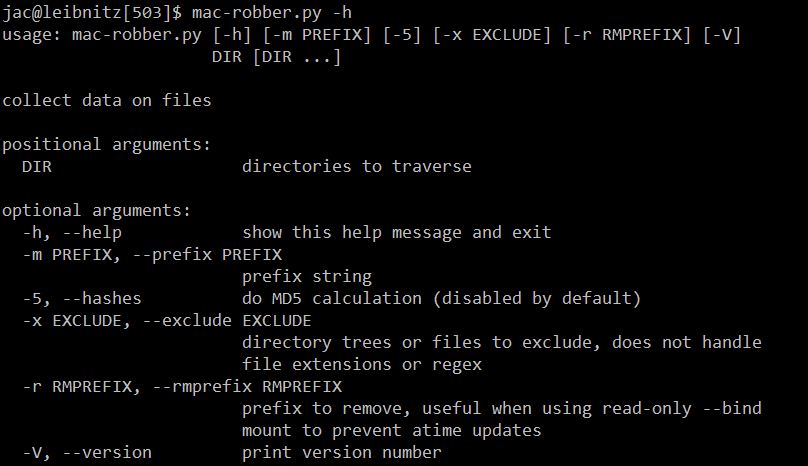
The tool can be downloaded from my docker-forensics github and is distributed under the BSD 3-clause license. I hope you find it useful. If you have any questions, comments, suggestions, or bug fixes, please let me know via the comments here, our contact form, or create an issue (or pull request) on github.
References:
[1] https://github.com/att/docker-forensics/blob/master/mac-robber.py
---------------
Jim Clausing, GIAC GSE #26
jclausing --at-- isc [dot] sans (dot) edu
Upcoming Courses Taught By Jim Clausing
| Type | Course / Location | Date |
|---|---|---|
 Community SANS |
Community SANS Ottawa FOR610 Ottawa, ON |
Dec 4, 2017 - Dec 9, 2017 |


Comments