Massive wave of ransomware ongoing
For an updated summary, see: WannaCry/WannaCrypt Ransomware Summary
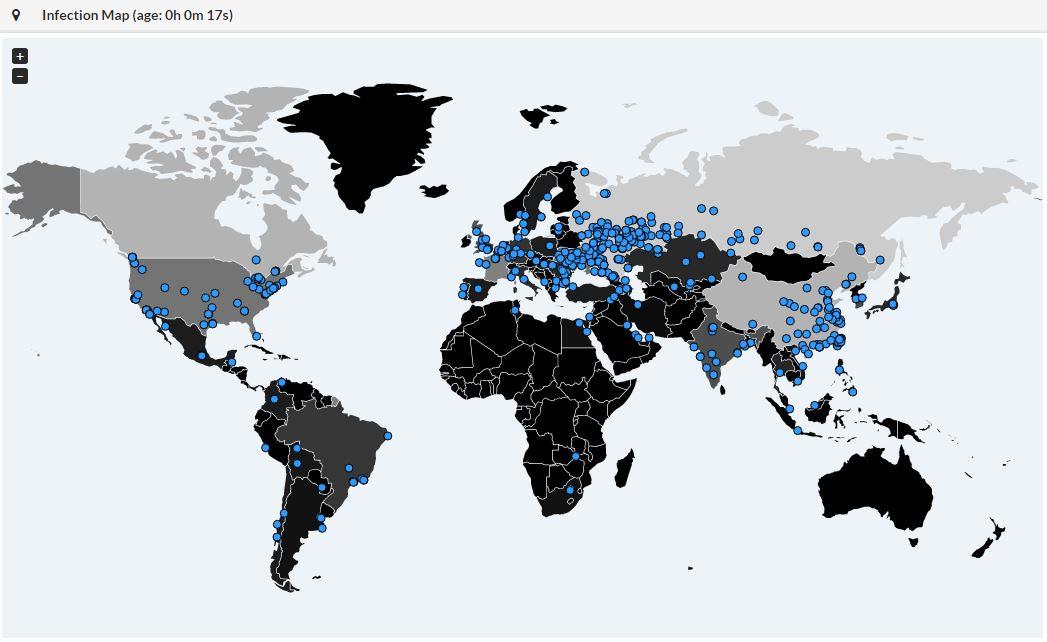
For a few hours, bad news are spreading quickly about a massive wave of infections by a new ransomware called "WannaCry". We are still trying to collect more information about it. It seems that 45K attacks were detected from 74 differents countries:
Big targets have been telecom operators (ex: Telefonica in Spain) and hospitals in UK. Once the malware has infected a computer, it spreads across the network looking for new victims using the SMB protocol.
The ransomware uses the Microsoft vulnerability MS17-10[1]. (This vulnerability was used by ETERNALBLUE[2])
Here are some IOC's that we already collected:
SHA256:
- 09a46b3e1be080745a6d8d88d6b5bd351b1c7586ae0dc94d0c238ee36421cafa
- 24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c
- 2584e1521065e45ec3c17767c065429038fc6291c091097ea8b22c8a502c41dd
- 2ca2d550e603d74dedda03156023135b38da3630cb014e3d00b1263358c5f00d
- 4a468603fdcb7a2eb5770705898cf9ef37aade532a7964642ecd705a74794b79
SHA1:
- 45356a9dd616ed7161a3b9192e2f318d0ab5ad10
- 51e4307093f8ca8854359c0ac882ddca427a813c
MD5:
- 509c41ec97bb81b0567b059aa2f50fe8
- 7bf2b57f2a205768755c07f238fb32cc
- 7f7ccaa16fb15eb1c7399d422f8363e8
File extension: .wncry
Ransomware notification: @Please_Read_Me@.txt
Emerging threats has an IDS rule that catches the ransomware activity: (ID: 2024218)
alert tcp $HOME_NET 445 -> any any (msg:"ET EXPLOIT Possible ETERNALBLUE MS17-010 Echo Response"; flow:from_server,established; content:"|00 00 00 31 ff|SMB|2b 00 00 00 00 98 07 c0|"; depth:16; fast_pattern; content:"|4a 6c 4a 6d 49 68 43 6c 42 73 72 00|"; distance:0; flowbits:isset,ETPRO.ETERNALBLUE; classtype:trojan-activity; sid:2024218; rev:2;)
Until now, the best protection is of course to patch your systems as soon as possible and keep your users aware of the new ransomware campaign to preven them to open suspicious emails/files.
[1] https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
[2] https://isc.sans.edu/forums/diary/ETERNALBLUE+Windows+SMBv1+Exploit+Patched/22304/
We will update this diary with more information if available.
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
When Bad Guys are Pwning Bad Guys...
A few months ago, I wrote a diary about webshells[1] and the numerous interesting features they offer. They’re plenty of web shells available, there are easy to find and install. They are usually delivered as one big obfuscated (read: Base64, ROT13 encoded and gzip'd) PHP file that can be simply dropped on a compromised computer. Some of them are looking nice and professional like the RC-Shell:
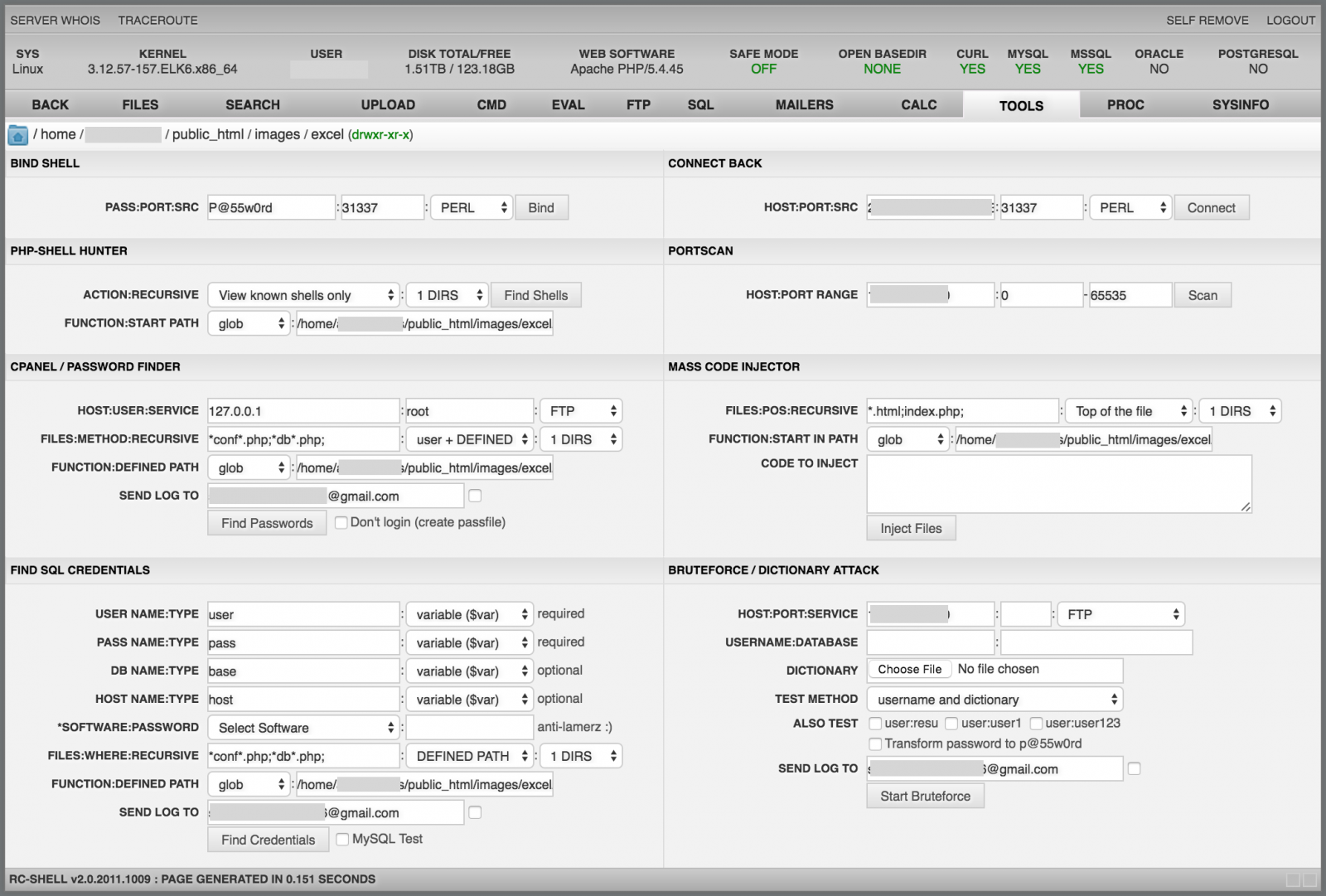
I’m pretty sure that some people are using web shells as a remote administration tool. Is it really a good idea? Not sure… When we install a software on our computer, one of the recommendations is to check the hash of the files/archives with the one provided by the developer to be sure that the software has not been altered by any means. It could be a good idea to make the same with web shells!
While preparing a presentation about web shells and testing some of them in a lab, I found a specific version of the RC-Shell (v2.0.2011.0827) that started to generate suspicious traffic. Almost at the same time, I was contacted by one of our readers that reported to me the same behaviour. He did some analysis on his side and the conclusion was that the web shell was backdoored! The PHP code contains an array of Base64 encoded images which are icons used to identify the file types. In the backdoored version, the "unknown" file has been replaced by a rogue one.
$images = array(
"small_unk" => "iVBORw0KGgoAAAANSU ...",
"unknown" => "iVBORw0KGgoAAAANSU ..."
);
MD5 (unknown.png) = 1470521de78ef3d0795f83ea7af7c6ad
If you have a look at the picture metadata, you will see that the 'unknown' one contains a very long and obfuscated comment (TweakPNG[2] is a very nice tool to play with PNG images metadata):
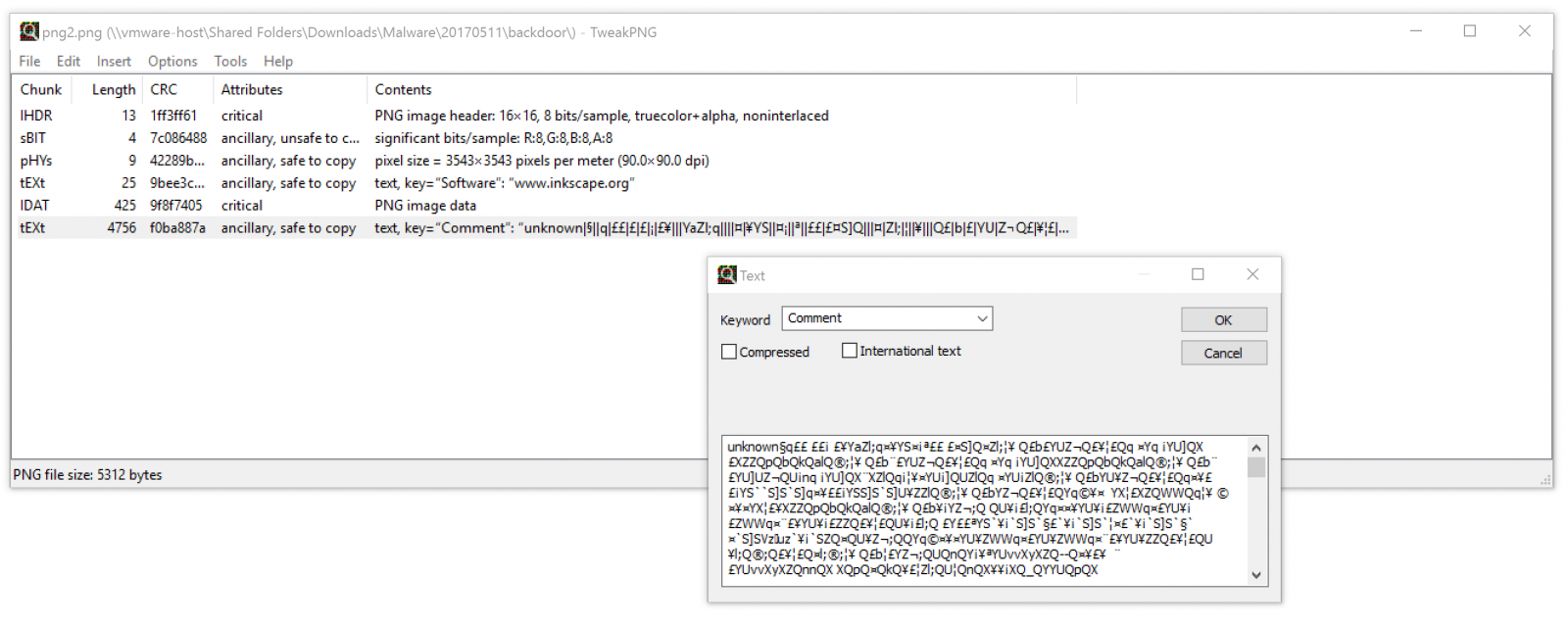
Multiple functions have been added to the web shell to deploy the backdoor. Once data decoded, they are passed to a create_function():
function z8t($i, $o)//run backdoor
{
$r = @create_function('$o', 'return @' . z7v($o, 0) . '($o);');
return $r($i);
}
Note: I found different versions of the web shell with different function names.
The decoding of the PNG image comment and the installation of the backdoor is available here[3]. The code of the backdoor is located here[4]. Basically, it collects juicy information (local PHP variables and details about the web shell and phone home via two channels:
- SMTP is used to drop an email to peterlegere51@yahoo[.]com
- HTTP is used to post the same data to hxxp://peterlegere.byethost2[.]com/news/index.php
Here is an example of an email sent to the email address:
To: peterlegere51@yahoo.com Subject: Linux|http://shiva/lab/VW4Zy8Yg.php? X-PHP-Originating-Script: 1000:VW4Zy8Yg.php(830) : runtime-created function(1) : eval()'d code Message-Id: <20170509202418.BE96124112C@shiva> Date: Tue, 9 May 2017 22:24:18 +0200 (CEST) From: www-data@xxxxxx.rootshell.be (www-data) URL=http://shiva/lab/VW4Zy8Yg.php? version=2.0.2011.0827 auth use_auth=0 auth md5_user=098f6bcd4621d373cade4e832627b4f6 auth md5_pass=098f6bcd4621d373cade4e832627b4f6 default_vars language=en default_vars email=q_q_x_x@yahoo.com default_vars default_sort=0a default_vars default_act=tools default_vars bind_port=31337 default_vars bind_pass=xxxxxx default_vars backcon_port=31337 default_vars sql_host=localhost default_vars sql_user=root default_vars sql_db=mysql default_vars sql_table=users default_vars ftp_user=anonymous default_vars ftp_pass=anonymous@ftp.com default_vars downloada=Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; Trident/4.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR SERVER_NAME=xxxxxx SERVER_ADDR=192.168.254.8 SERVER_PORT=80 HTTP_REFERER=http://shiva/lab/ PHP_SELF=/lab/VW4Zy8Yg.php REQUEST_URI=/lab/VW4Zy8Yg.php SCRIPT_NAME=/lab/VW4Zy8Yg.php SCRIPT_FILENAME=/var/www/lab/VW4Zy8Yg.php REMOTE_ADDR=192.168.254.11
So, be warned when you download and use tools from unknown or unreliable sources. Even underground tools can be backdoored!
[1] https://isc.sans.edu/forums/diary/The+Power+of+Web+Shells/21257
[2] http://entropymine.com/jason/tweakpng/
[3] https://gist.github.com/anonymous/319ef7124affebec67ebc56bc83cbe87
[4] https://pastebin.com/bgj7aH9u
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key



Comments