A recent example of wire transfer fraud
Introduction
Do you know about any attempts of wire transfer fraud in your organization? They often start with phishing emails. These emails are used to trick an employee into wiring money to bank accounts established by the criminal. It's an old scam, but 2015 apparently saw a resurgence in wire transfer fraud [1]. Last August, we saw reports that thieves stole $46.7 million from Ubiquity using this method [2]. Since then, at least one organization has shared its experience as the target of an (unsuccessful) attempt at wire transfer fraud [3].
During the first full week of 2016, I ran across such an attempt and thought I'd share.
Chain of events
In most cases I've seen, the general sequence of events runs as follows:
- Criminal sends an email with a spoofed sending address to one or more targeted recipients.
- A recipient replies to the Reply-To: address in the email headers.
- Criminal continues the conversation and asks for a wire transfer.
The actor may spoof an executive from your organization, a business partner, or a customer. If the actor is successful, someone in your organization will do the wire transfer It may take a while before people know they've been tricked. In Ubiquity's case, the criminals managed to steal millions of dollars before the company realized it [2].
Ubiquity is not unique in this regard. According to the FBI, between October 2013 and August 2015, thieves stole nearly $750 million from more than 7,000 companies in the US using such scams [4].
How does a criminal decide who to target in your organization? If your company has a website with biographies of your leadership, it's fairly easy to figure out who might be able to authorize a wire transfer.
Example from Monday 2016-01-04
In this example, 17 emails were sent in two waves. The first wave went to the first two individuals, and the second wave happened almost 6 hours later and went to the last two individuals. The criminal didn't have the email addresses of the actual recipients, so multiple messages were sent using different recipient emails. We saw [firstname.lastname]@[company].com, [first initial + lastname]@[company].com, and variations on the domain, like [company].com.de or [company].com.br for those recipients not located in the United States. A list follows:
- 16:32:27 UTC - Subj: Please get back to me on this - From: [redacted] - To: [1st recipient]
- 16:32:32 UTC - Subj: Please get back to me on this - From: [redacted] - To: [2d recipient]
- 22:17:02 UTC - Subj: Please get back to me on this - From: [redacted] - To: [3d recipient]
- 22:17:02 UTC - Subj: Please get back to me on this - From: [redacted] - To: [4th recipient]
- 22:17:23 UTC - Subj: Please get back to me on this - From: [redacted] - To: [3d recipient]
- 22:18:27 UTC - Subj: Please get back to me on this - From: [redacted] - To: [3d recipient]
- 22:18:27 UTC - Subj: Please get back to me on this - From: [redacted] - To: [4th recipient]
- 22:18:45 UTC - Subj: Please get back to me on this - From: [redacted] - To: [4th recipient]
- 22:18:45 UTC - Subj: Please get back to me on this - From: [redacted] - To: [3d recipient]
- 22:18:46 UTC - Subj: Please get back to me on this - From: [redacted] - To: [3d recipient]
- 22:18:46 UTC - Subj: Please get back to me on this - From: [redacted] - To: [4th recipient]
- 22:21:25 UTC - Subj: Please get back to me on this - From: [redacted] - To: [4th recipient]
- 22:21:25 UTC - Subj: Please get back to me on this - From: [redacted] - To: [4th recipient]
- 22:21:46 UTC - Subj: Please get back to me on this - From: [redacted] - To: [3d recipient]
- 22:22:49 UTC - Subj: Please get back to me on this - From: [redacted] - To: [3d recipient]
- 22:23:08 UTC - Subj: Please get back to me on this - From: [redacted] - To: [4th recipient]
- 22:23:08 UTC - Subj: Please get back to me on this - From: [redacted] - To: [3d recipient]
An example of these emails follows:
Date: Mon, 4 Jan 2016 22:18:08 GMT
From: [spoofed executive's email address]
To: [each of the targeted recipients]
Subject: Please get back to me on this
Do you have a moment? I am tied up in a meeting and there is something i need you to take care of.
We have a pending invoice from our Vendor. I have asked them to email me a copy of the invoice and i will appreciate it if you can handle it before the close of banking transactions for today.
I cant take calls now so an email will be fine.
Sent from my iPhone
Tracing the source of these emails
Reviewing the email headers, it appears this email came from a virtual private server (VPS) on an IP administered by myhosting.com (a hosting provider). From what I understand, almost everything in the email headers can be spoofed. The only certain information is the IP address listed in the "Received" line for your email server.
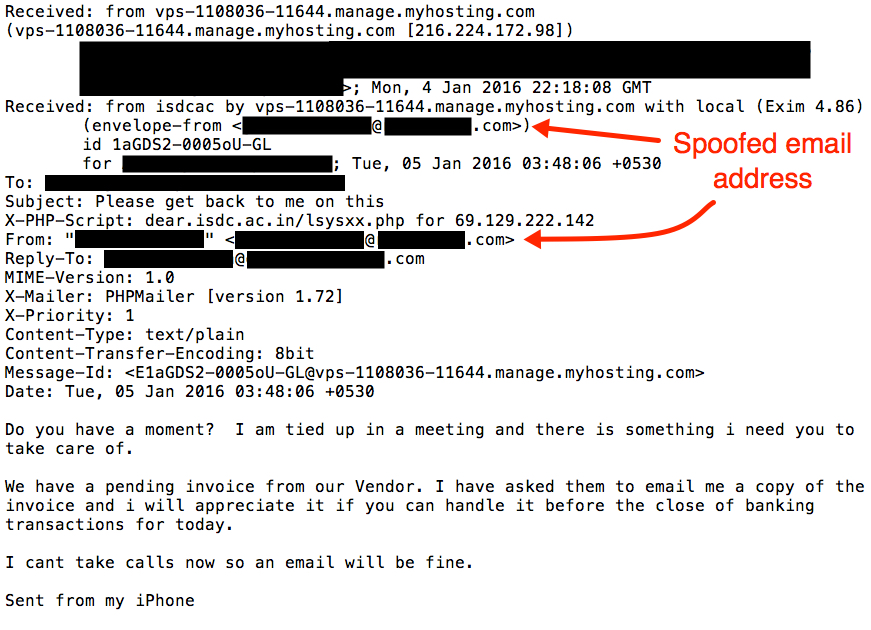
Shown above: An example of the message with some of the email header lines.
If we can believe some of the other email header lines, these messages were sent using PHPMailer.
Final words
This diary shows an example of attempted wire transfer fraud seen during the first week of 2016. It isn't the most sophisticated attempt I've looked into; however, this type of activity seems increasingly more common.
Although technical methods can ;combat these types of scams, the best defense is user education. Make sure people with authority for wire transfers know to what expect.
Do you have a wire fraud transfer story? Feel free to share in the comments!
---
Brad Duncan
Security Researcher at http://www.rackspace.comRackspace
Blog: www.malware-traffic-analysis.net - Twitter: @malware_traffic
References:
[1] https://www.dlapiper.com/en/us/insights/publications/2015/08/wire-transfer-phishing-an-old-scam-returns/
[2] http://krebsonsecurity.com/2015/08/tech-firm-ubiquiti-suffers-46m-cyberheist/
[3] http://fortune.com/2015/10/13/ceo-wire-transfer-scam/
[4] http://krebsonsecurity.com/2015/08/fbi-1-2b-lost-to-business-email-scams/



Comments