Sigcheck and VirusTotal
Continuing my diary entries on Sysinternals tools with VirusTotal support, I'm taking a look at sigcheck.
Sigcheck is a command-line utility to check the digital signature of files like PE files (EXEs).
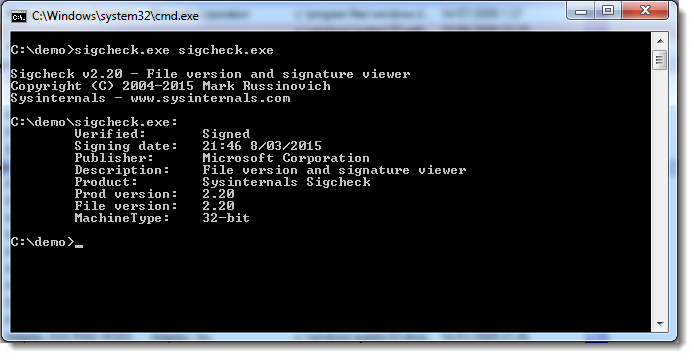
Sigcheck also supports VirusTotal searches. When you use option -v, the hash of the file will be submitted to VirusTotal. The first time you run it, you'll have to accept VirusTotal's terms (or use option -vt to accept and avoid the prompt):
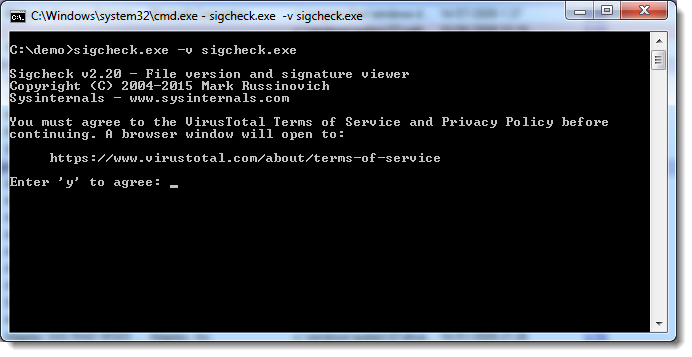
You'll get the score and a link to the report for the checked file.
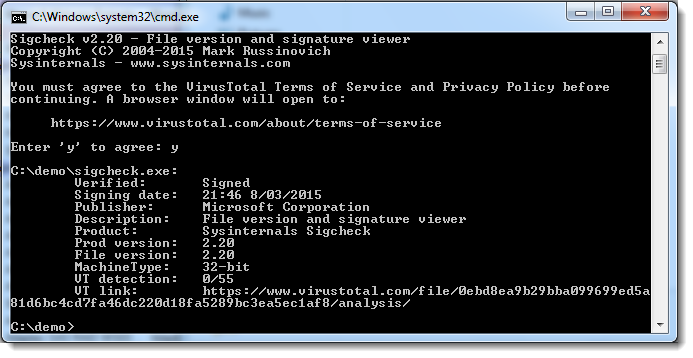
If a hash is not present in VirusTotal's database, the file will not be submitted, unless you use option -vs:
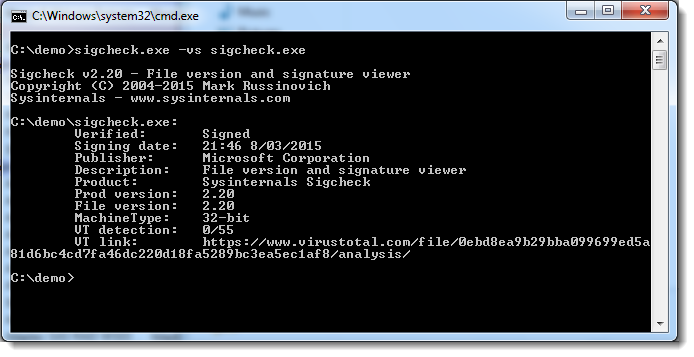
You can scan a complete disk with option -s and specifying the root folder of the disk (e.g. c:\), and you can produce a CSV report with option -c:
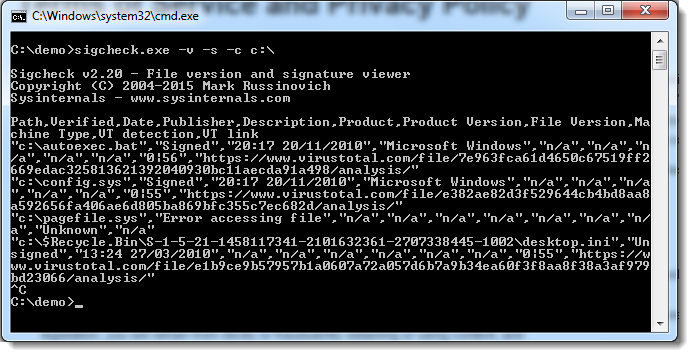
As can be seen from this last screenshot, files without digital signature are also checked with VirusTotal.
Sysinternals: http://technet.microsoft.com/en-us/sysinternals
VirusTotal: https://www.virustotal.com/
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
Autoruns and VirusTotal
Continuing my diary entries on Sysinternals tools with VirusTotal support, I'm taking a look at autoruns.
Autoruns is another fine Sysinternals tool that comes with VirusTotal integration. If you are not familiar with autoruns, it scans all auto-starting locations in Windows and provides a comprehensive report. This gives you an overview of all programs that start automatically on the scanned Windows machine.
When you start autoruns it will start scanning the Windows machine. Wait for the scan to terminate, or abort it with the Escape key.
Go to the scan options:
And enable "Check VirusTotal.com":
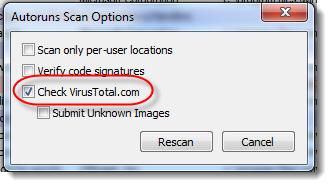
With this option, autoruns will only submit hashes to VirusTotal. If a file is not known by VirusTotal, you won't have a score. But if you enable "Submit Unknown Images" too, then autoruns will submit (upload) files that are not in VirusTotal's database, and you will have a score after VirusTotal finishes scanning the file (this takes a couple of minutes).
You have to agree to VirusTotal's terms of use to enable this feature:
Hashes will be submitted:
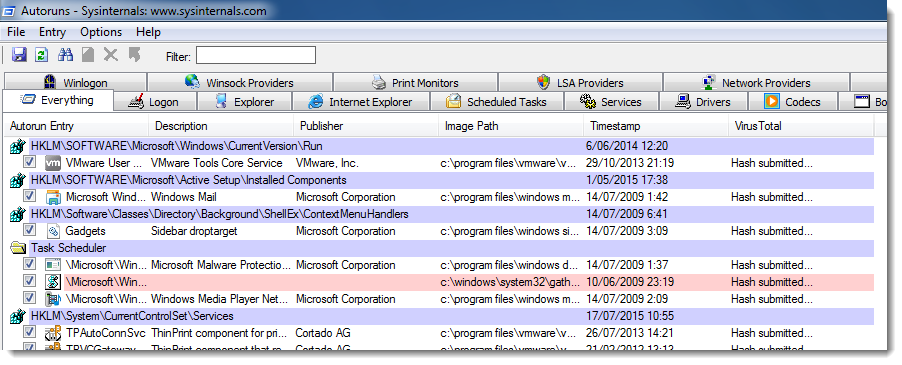
And soon you'll have the VirusTotal scores for known entries:
.png)
Sysinternals: http://technet.microsoft.com/en-us/sysinternals
VirusTotal: https://www.virustotal.com/
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
Process Explorer and VirusTotal
About a year ago, Rob had a diary entry about checking a file from Process Explorer with VirusTotal.
Did you know you can have all EXEs of running processes scanned with VirusTotal?
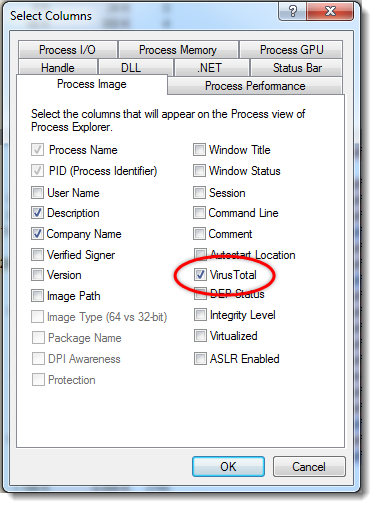
In Process Explorer, add column VirusTotal:
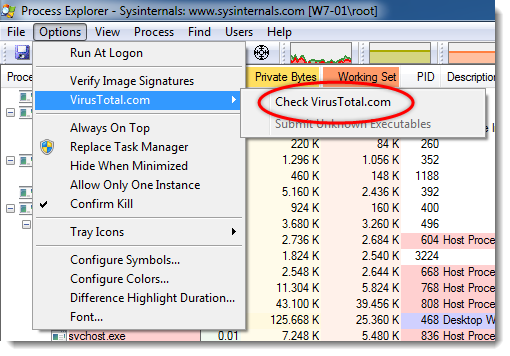
Enable VirusTotal checks:
And accept the VirusTotal terms:
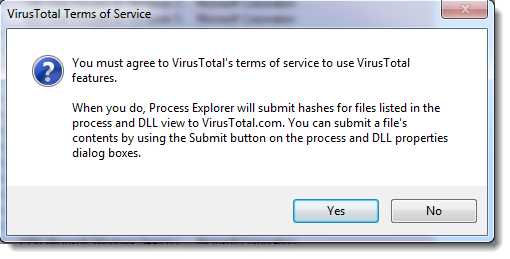
(update: as you can see, by default Process Explorer only submits hashes to VirusTotal, not files, unless you explicitly instruct it to submit a file).
And now you can see the VirusTotal scores:
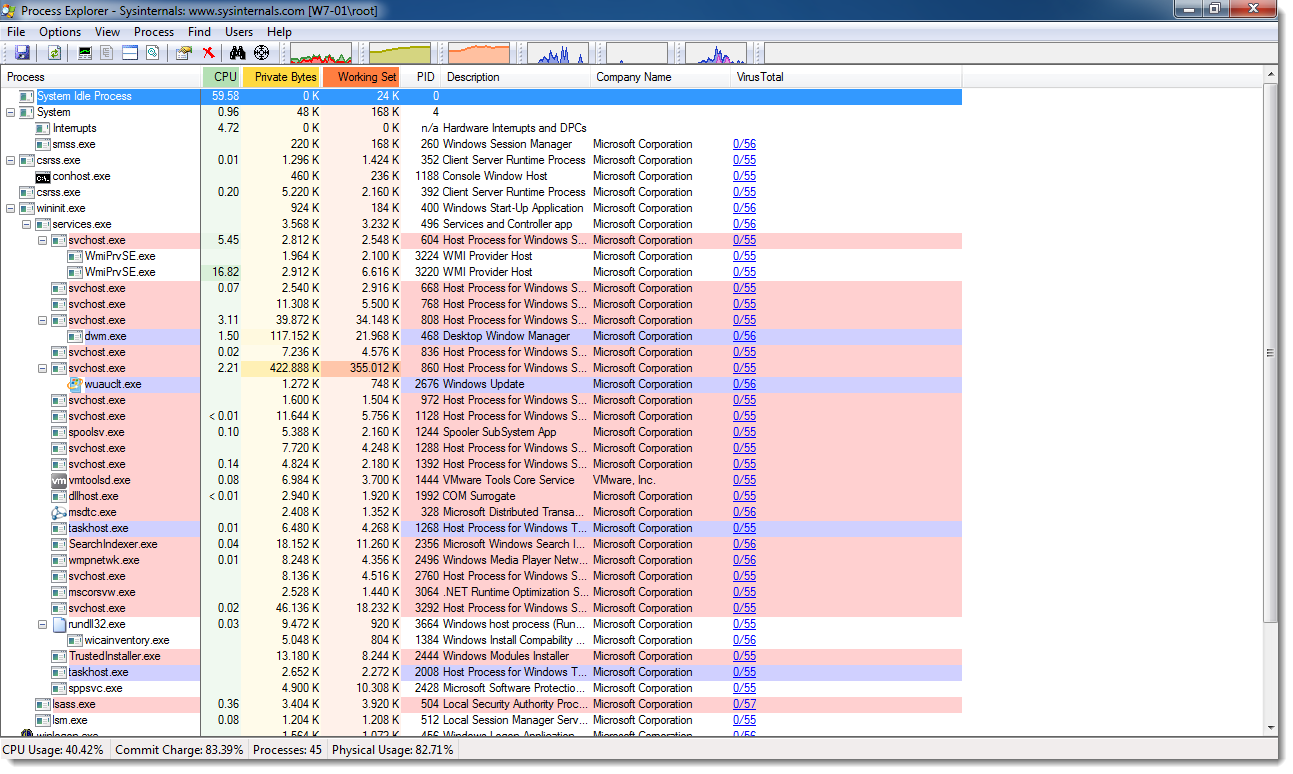
Process Explorer is not the only Sysinternals tool that comes with VirusTotal support. I'll showcase more tools in upcoming diary entries.
Sysinternals: http://technet.microsoft.com/en-us/sysinternals
VirusTotal: https://www.virustotal.com/
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com


Comments