Who Develops Code for IT Support Scareware Websites?
When investigating a website used as part of an IT support scam, I came across a web page that attempted to fool the visitor into thinking that the person’s system was infected. The goal was to persuade the potential victim to call a "Microsoft Certified Live Technician" at the designated phone number " for assistance on how to remove malicious pop-ups."
The scareware page resided at 247tech.help (don't go there). It looked like this:
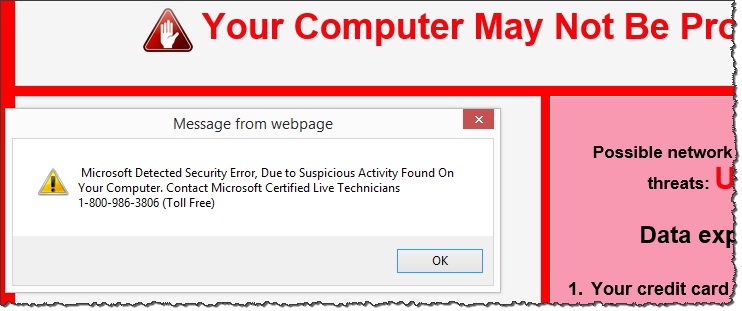
The source code of this scammy page, which you can see on Pastebin, included the following HTML comment:
Mirrored from clients.worldnetconsultants.com/Lander3/ by HTTrack Website Copier/3.x [XR&CO'2014], Thu, 08 Jan 2015 03:52:17 GMT
Such comments are automatically added using the non-malicious website-mirroring tool HTTrack Website Copier. This comment offered a pointer to the origin of the page's code.
The Lander3 page was available on the clients.worldnetconsultants.com server as of this writing. It showed a web page that was almost identical to the one captured above, except it lacked a pop-up and specified a different "tech support" phone number: (855) 662-9616. Also, it contained pointers to YourTechSupport.org and YourTechSupport.com (don't go there), who may have been the client that paid to develop this code. You can see Lander3 source code on Pastebin.
The clients.worldnetconsultants.com server contained a publicly-accessible listing of other projects, which included other variations on landing pages for YourTechSupport.org, inviting people to get a "free secure diagnostic session" (lander1 screenshot), "detect, diagnose and troubleshoot all spyware problems" (lander2 screenshot), perform a "security check" (lander4 screenshot), etc.
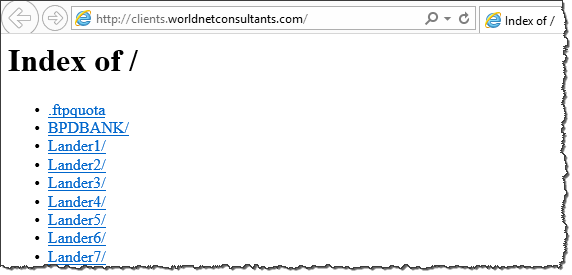
The server also contained code for other websites, which seemed to be associated with legitimate, less shady companies.
By performing some Google searches, I came across pop3.yourtechsupport.org (don't go there), which was live at the time of this writing. Its look-and-feel matched the lander1 screenshot.
Google also pointed me to yourtechsupport.org/L3 (don't go there). Its look-and-feel matched that of 247tech.help, which I mentioned in the beginning of this article. It included a pop-up, thought its text was different from what 247tech.help used, which stated:
"YOUR COMPUTER MAY NOT BE PROTECTED FROM ADWARE / SPYWARE
Call 844-325-8014 immediately for assistance on how to remove potential spyware. The call is toll-free."
I captured a screenshot of that page for those who wish to see it in its full glory.
The site www.worldnetconsultants.com describes Worldnet Consultants Inc. The company positions itself as "a leading web design company in USA for offshore web design, offshore web development," etc. The site lists office addresses in Forest Hills, NY and Gurgaon, India. This company appears to have developed the code used by yourtechsupport.org and 247tech.help. I saw no indications that the software development firm is malicious—however, they don't seem to be particularly selective about their clientele.
If this topic interests you, you might also like these articles of mine:
- The Manipulative Nature and Mechanics of Visitor Survey Scams
- How Victims Are Redirected to IT Support Scareware Sites
- Conversation With a Tech Support Scammer
-- Lenny Zeltser
Lenny Zeltser focuses on safeguarding customers' IT operations at NCR Corp. He also teaches how to analyze malware at SANS Institute. Lenny is active on Twitter and Google+. He also writes a security blog.
How Victims Are Redirected to IT Support Scareware Sites
In the classic version of tech support scams, the fake technician initiated an unsolicited phone call to the victim. Now the awareness for this scheme has increased, scammers shifted tactics. Their latest approaches involve convincing the potential victim to be the one calling the impostor. I've seen this accomplished in two ways:
- Scammers use bots to respond to Twitter users who mention PC problems or malware. The bots search for the appropriate keyboards and send messages that include a phone number of a tech support firm. I described this approach when exploring how scammers prescreen potential victims.
- Scammers set up scareware websites that are designed to fool people into thinking their PC is infected, compelling visitors to call the fake tech support organization. Johannes Ullrich described a typo squatting variation of this technique in an earlier diary. Let’s take a look a domain redirection variation of this scam below.
In the following example, the victim visited a link that was once associated with a legitimate website: 25yearsofprogramming.com. The owner of the domain appears to have allowed its registration to expire in early 2014. At that point, the domain was transferred to Name Management Group, according to DomainTools Whois records. The record was assigned DNS servers under the domains cashparking.com, hastydns.com, dsredirection.com and eventually brainydns.com.
Name Management Group seems to own over 13,000 domains (according to DomainTools Whois records), including numerous domains that DomainTools classifies as malicious, such as 0357al.com, 18aol.com, 520host.com, 60dayworkout.us, 61kt.com, 7x24sex.net, 9tmedia.com, adobecrobat.info, adultfantasynetwork.com, allappsforpc.com, apkcracks.net, etc. (Don't visit these domains.)
Landing on the Fake Malware Warning Site
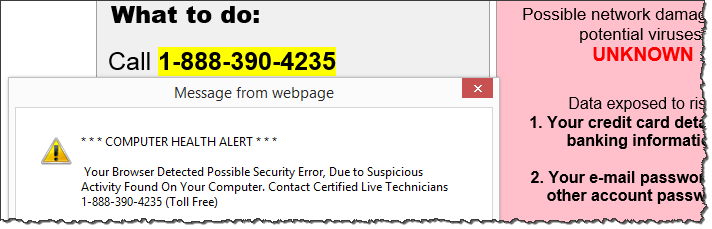
Visiting the once-legitimate URL a few days ago landed the victim on a scammy scareware page, designed to persuade the person to contact "Microsoft Certified Live Technicians" at the specified toll-free phone number. The site employed social engineering techniques employed by rogue antivirus tools. Such schemes present victims with fake virus warnings, designed to scare people into submission.
The site in our example also played an auditory message, exclaiming:
"This is a Windows system warning! This is a Windows system warning! If you are hearing this warning message, the security of your Windows system has been compromised. Your Windows computer and data might be at risk because of adwares, spywares and malicious pop-ups! Your bank details, credit card information, email accounts, Facebook account, private photos and other sensitive files may be compromised. Please call the number mentioned now to resolve this issue."
To see and hear what the victim experienced, play the video clip below or watch it on YouTube.
Here are the redirection steps that brought the victim to the scareware site mentioned above:
http ://25yearsofprogramming.com/blog/2010/20100315.htm -> https ://p2.dntrax.com/tr?id=f2d252736d65832f11811ad8cb43ceff00313e75.r -> http ://247tech.help/crt/us_seg0303/m1/us_windos_3806/index.html
You can see the source code to the final page on Pasebin, if you're interested. According to the code, it was mirrored from clients.worldnetconsultants.com/Lander3 using the free non-malicious tool HTTrack Website Copier on 08 Jan 2015. (More on this interesting tidbit in my diary
Who Develops Code for IT Support Scareware Websites?)
If you visited the top page of the 247tech.help website (don't go there), you would see a friendly, professional-looking page, gently inviting the visitor to "Call Now for Instant Support" by dialing 844-878-2550. Please don't call that number; however, if you'd like to hear a details account of what people experience when they do call, read my article Conversation With a Tech Support Scammer.
The nature of this page is in stark contrast to the scareware warnings-filled trap shown above, which redirection victims encountered.
Other Redirection Possibilities
The website hosting 25yearsofprogramming.com at the time of this writing redirects visitors to various places, perhaps randomly, perhaps based on the person’s geography or browser details. I encountered two other redirection flows that led to scareware websites set up for IT support scams.
One redirection flow employed p2.dntrax.com, as the example above, but took the victim to alert.windows.com.computers-supports.com (don't go there):
http ://25yearsofprogramming.com/blog/2010/20100315.htm -> https://p2.dntrax.com/tr?id=f2d252736d65832f11811ad8cb43ceff00313e75.r -> http ://alert.windows.com.computers-supports.com/index-1.html?isp=Time%20Warner%20Cable&browser=Internet%20Explorer&browserversion=Internet%20Explorer%2011&ip= 108.61.226.4&os=Windows&osversion=Windows%208.1
The resulting site is a bit more sophisticated than the one in the previous example, because it uses JavaScript to customize the web page to include the victim's ISP, browser name, IP address and Windows version. For instance:
document.write(getURLParameter('ip'))
You can see the source code of that page on Pastebin. Here's the screenshot of what the victim saw; in this example, the website didn't receive the victim's IP and other details and therefore didn't display this info:
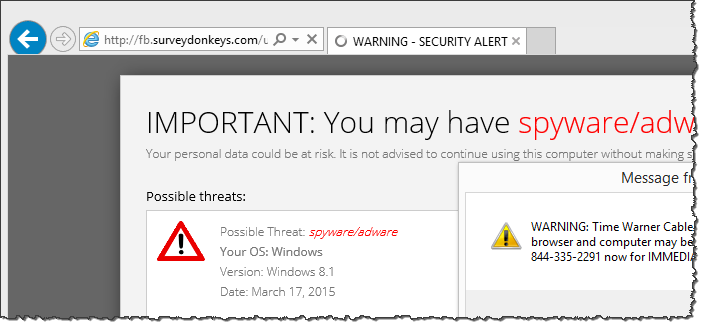
Sometimes the victim was redirected using a longer trail to a different IT support scareware site (don't go there):
http ://25yearsofprogramming.com/blog/2010/20100315.htm -> http ://xml.revenuehits.com/click?i=cEuxzuX2fpc_0 -> http ://zh.zeroredirect1.com/zcvisitor/fddce3a1-ccbb-11e4-ab5a-0a92e2e12617 -> http ://claimyourfree.com/promo/base.php?c=734&key=0cdc58908ab3a694320034e391aa520a&target=oscar-vox-zKU0jhQu -> http ://fb.surveydonkeys.com/us/index.php?target=oscar-vox-zKU0jhQu -> http ://ajax.surveydonkeys.com/imp/g38a0n?data=eyJicm93c2VyX3R6X29mZnNldCI6LTI0MCwiY2IiOjEwNTExNSwibHBfcmVmIjoiIiwibHBfdXJsIjoiaHR0cDovL2ZiLnN1cnZleWRvbmtleXMuY29tL3VzL2luZGV4LnBocD90YXJnZXQ9b3NjYXItdm94LXpLVTBqaFF1In0= -> http ://securedgo.com/d3ed9240-61de-48c1-9a7b-b10dbafaa7d2 -> http ://fb.surveydonkeys.com/us/windowswarning.php?os=Windows&osversion=Windows%208.1&isp=Time%20Warner%20Cable&browser=Internet%20Explorer&voluumdata=vid..00000003-ee55-4287-8000-000000000000__vpid..48799800-ccb6-11e4-8c70-feaa7355a29a__caid..d3ed9240-61de-48c1-9a7b-b10dbafaa7d2__lid..5e47c857-460b-4d05-b92e-e24c030f0933__rt..R__oid1..b74614e1-7a0b-40bb-8bd5-66fbfc48a121
The redirection chain and the source code (you can see it on Pastebin) of the resulting site, as well as its look-and-feel were different from the examples above:
The design of this page matches closely the site Johannes Ullrich described in the typo squatting variation of this scenario on December 15. The latest page employed the sound file gp-msg.mp3 to scare visitors. VirusTotal has a record of this file, which was first uploaded to VirusTotal on December 11, 2014.
Who is Redirecting, Why and How?
We seem to be dealing with two different redirection engines and companies: p2.dntrax.com and xml.revenuehits.com after the initial 25yearsofprogramming.com redirect.
The domain dnstrax.com was registered by Team Internet AG, which is associated with over 44,000 domains, including several that DomainTools classifies as malicious: anonse24.de, natursteindichtstoff.de, seospecialists.de, etc. The domain revenuehits.com is registered to MYADWISE LTD, which is associated with about 50 domains.
The companies behind these servers, as well as the firm presently controlling 25yearsofprogramming.com are probably receiving referral fees for their roles in the redirection scheme.
There's much to explore regarding the domain names, systems and companies involved in the schemes outlined above. If you have additional information about these entities, or would like to contribute towards this analysis, please leave a comment. If you decide to explore any of these systems, do so from an isolated laboratory environment.
Also, if you encounter a tech support scam, please register it with our database of such incidents.
-- Lenny Zeltser
Lenny Zeltser focuses on safeguarding customers' IT operations at NCR Corp. He also teaches how to analyze malware at SANS Institute. Lenny is active on Twitter and Google+. He also writes a security blog.




Comments