Why is your Mac all for sudden using Bing as a search engine?
Even as a Mac user, you may have heard about Bing, at least you may have seen it demonstrated in commercials [1]. But if your default search engine on your Mac is all for sudden switched to Bing, this may be due to another piece of legacy software that some Mac users may have a hard time living without : Microsoft's Internet Explorer. So why not just search ("google") if there is a version for OSX:
Sure enough, there is a FREE! Internet Explorer for Mac available. Lets download it, and see what happens.
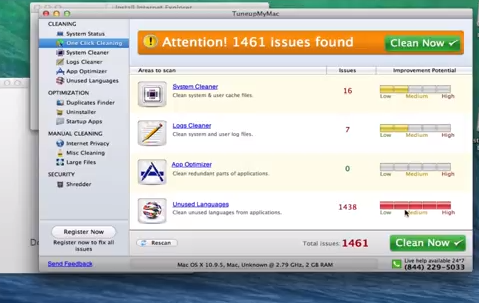
As it turns out, the page that you are going to download (the usual .dmg file) is signed by a valid Apple developer signature. It will install fine with Maverick's default "gate keeper" setting. Upon installation, it offers a couple additional free product. A "Shopping and Search Helper" as well as some software that will clean your Mac and make it run faster and safer.
In some ways, I have to say I admire how honest the search optimizer is in its EULA. The software will (the original uses all upper case for this section, like shown below):
.. RESET YOUR HOME PAGE AND/OR DEFAULT SEARCH FOR INTERNET EXPLORER, FIREFOX AND CHROME TO TROVI SEARCH...
... BLOCK AND NOTIFY YOU OF ATTEMPTS BY OTHER SOFTWARE TO CHANGE YOUR SELECTED HOME PAGE AND/OR DEFAULT SEARCH...
The Trovi privacy policy is similarly explicit, and not hiding must. The software will collect among other items [2]:
- IP Address and device identifiers like UDID
- web pages you visit and the content you see, access and utilize...
- interactions on social networks
- registration information you provide like name, address, e-mail, phone number, gender birthday
In the end, you end up with a bunch of adware, and , an actual legit version of Internet Explorer 5, which used to run on Mac OS, but doesn't really run on OS X Mavericks.
For a full walk through see this YouTube video: https://www.youtube.com/watch?v=bVwyxaYJgKY
In short: I don't think this software does anything illegal. It clearly advertises what it does. If you feel otherwise, you can file a complaint with courts in Cyprus where the company is located.
[1] https://www.youtube.com/user/bing
�??[2] http://info.trovi.com/Privacy
CSAM: My Storage Array SSHs Outbound!
Kuddos to Matthew for paying attention to egress traffic. We keep emphasizing how important it is to make sure no systems talk "outbound" without permission. Just this last week, various Shellshock exploits did just that: Turn devices into IRC clients or downloading additional tools via HTTP, or just reporting success via a simple ping.
So no surprise that Matthew wrote us: "... the first time I saw the storage array SSH to the internet I about fainted. ..."
I would be surprised too! And turns out that isn't the only person that experienced this. Mark noted:
"Had the seem freak moment when I saw it happen. The SAN happily communicating to an outside entity. Though the company had been well and truly hosed."
Luckily, before going too far down the incident handling road, Matthew realized that this was a false positive. The storage array in question called "back home" to the vendor to report on its status. The purpose of this communication is to report failed disks or other critical events that may trigger a service call. Vendors will agree to turn off this feature, but then of course it is up to you to recognize faulty disks.
Got anything like that? Let us know. (if possible with log snippet / packet capture or other show-and-tells)
Cyber Security Awareness Month 2014: Scary False Positives
To "celebrate" cyber security awareness month, we decided to focus on "scary false positives" during October. If you have any to share, please let us know. What we are looking for is preferably a lot entry, or another "indicator" that led you to believe that your system was compromised, but in the end turned out to be a false positive.
Please e-mail your stories to handlers-at-isc.sans.edu or use out Contact form.


Comments