Spot the Phish: Verizon Wireless
We have seen a couple of reports recently of pretty well done Verizon Wireless phishing attempts. At this point, I haven't gotten one with the target site still up, so they may try to install malware instead of just asking for Verizon credentials.
update: Paul just wrote in that he caught some of the links still active, and indeed they are trying to install malware and don't ask for credentials. And fellow handler Pedro notes that the malware is a blackhole exploit kit that will try to install Zeus.
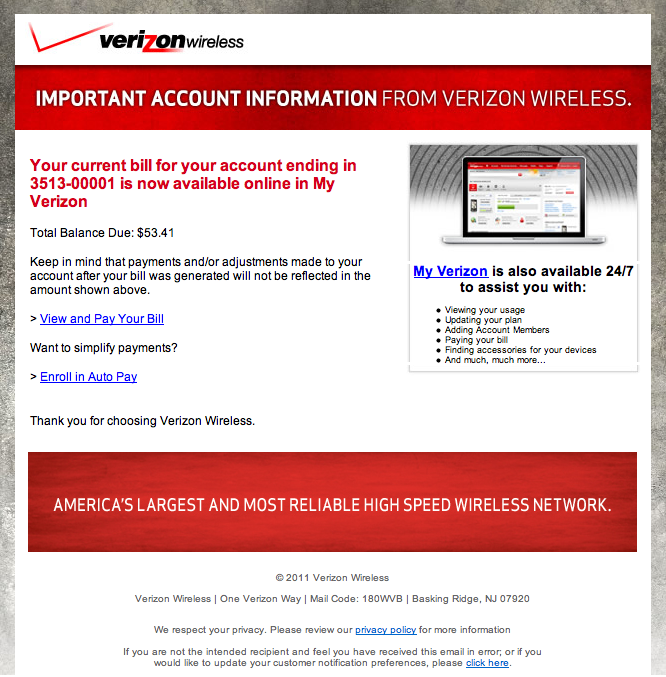
See if you can spot the fake one. The answer is below the images (click to open image in new window at full resolution)
The left one is the fake. The only give away is that the fake e-mail doesn't include the partial account number, and typically indicates a large bill > $1,000 (at least large for me). I assume the large amount is supposed to cause panic clicking.
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
VMWare Security Advisories
VMWare Released a new security advisory (VMSA-2012-0011) for its products [1]. The advisory covers pretty much all of VMWare's virtualization platforms (Player, Workstation, Fusions, ESX and ESXi).
The in my opinion most severe vulnerability out of the two described would allow an attacker to execute code on the remote host, which could be used to "break out" of the guest. However, this issue requires that the attacker is able to load checkpoint files on the guest, which in turn requires the attacker to have full control of the guest, a typical requirement for VMWare escape.
The second vulnerability can lead to a denial of service. An attacker can crash the virtual machine by manipulating traffic to remote devices like keyboards or disks attached to the virtual machine.
I would not consider either one of these as "super critical", but in particular the first issue should be patched soon.
[1] http://www.vmware.com/security/advisories/VMSA-2012-0011.html
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter



Comments