Oracle Patches (Jan2011 CPU)
Today, Oracle will release its quarterly patch bundle ("Jan2011 CPU"). The pre-announcement is already out, and it promises quite some "entertainment" for DBAs and Middleware Admins for the next couple weeks. One thing that certainly stands out from the list is the vulnerability in Oracle Audit Vault with a CVSS score of 10.0, apparently remotely exploitable without authentication. Always disappointing when a so-called security component makes the system actually more vulnerable.
We'll update this diary later, once the full information becomes available.
Update 2105 UTC: The full advisory is now out, see www.oracle.com/technetwork/topics/security/cpujan2011-194091.html. In addition to the already mentioned Audit Vault vulnerability, other notable problems include vulnerabilities in Oracle Fusion Middleware, a remotely exploitable hole in Sun Solaris CDE Calendar Manager Service, and also a serious problem in the PowerPoint parser for OpenOffice.
Given the long list, it stands to hope that Oracle took the time to properly check the patches for compatibility with each other, as well as with their other product lines.
Yet another rogue anti-virus
Remember four years ago when the "Fake Codec" scam managed to infect even large corporations? The bad guys still try this approach every now and then, but their most successful "invention" to date is clearly the fake anti-virus. We've been covering it repeatedly for the past two, three years now, and still is going strong. If an attack vector stays the same for years, it can only mean one thing: It is netting the bad guys enough money that they don't feel the urge to innovate.
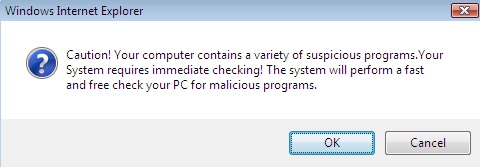
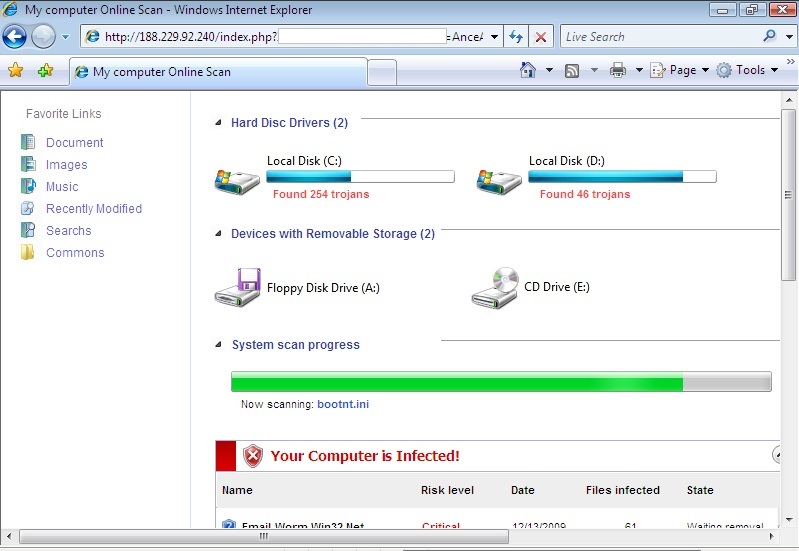
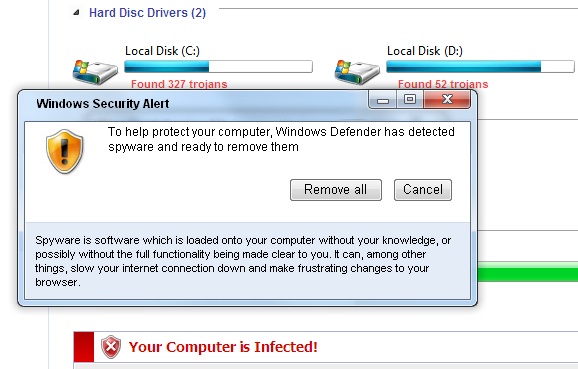
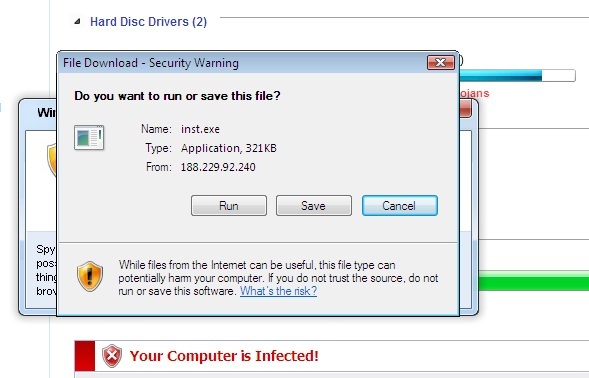
The following popped up earlier today when some readers surfed to a perfectly OK web site that had apparently been hacked and "amended". The site that seems to start the dive down the FakeAV rabbit hole at the moment is (dontclick!) baullka-dot-com/red.php . The goodies then come from 91.216.122.x which is known to provide unsolicited anti-virus "help". Another netblock involved - 188.229.88.x and 188.229.92.x - seems to be a recent addition to the FakeAV universe.
I'm including a couple screenshots below, it never hurts to know what the current incarnation of FakeAV looks like ... *especially* since their current EXE registers with a mere 6/43 on the Virustotal scale.
Stay safe!


Comments