Malicious Or Not? You decide...
On of the hardest tasks in security, and probably fundamentally an impossible task is to figure out if something is not malicious. Even the code you wrote yourself, once it exceeds a certain complexity, could include backdoors that you as the author missed. They may come in the form of vulnerabilities, or maybe it was bad advice that you followed (ever copied code from Stackoverflow?). Never mind malicious libraries or compilers.
Earlier today, a reader sent me a file asking just that question. Carlos received an anti-malware warning flagging a file as malicious. According to Virustotal, ESET-NOD32 flags it as "a variant of Win32/KingSoft.D potentially unwanted". This is a pretty weak signature. Virustotal also stated that the file is "Probably harmless" and that "There are strong indicators suggesting that this file is safe to use."
Next, I uploaded it to hybrid-analysis. Hybrid-Analysis returned the following risk assessment:
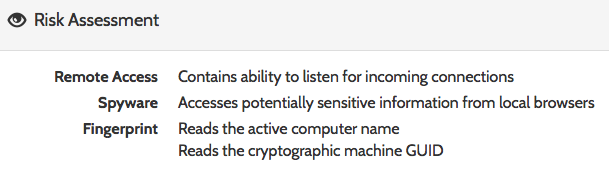
This looks quite a bit more malicious.
Some additional Google searches revealed that the file is likely part of "WPS Office," a free Chinese office suite that appears to be included for free with some HP Laptops.
My advice to Carlos was that the file is likely not malicious, but as long as he doesn't need WPS Office, he is probably better off deleting it to save some disk space. In short: bloatware.
What would your advice be? Here are the links to the results from Hybrid Analysis and Virustotal:
https://www.hybrid-analysis.com/sample/e3d74b6eb7f941125c35ae0ab2c5bd8d7116e6794f38b3879bddeb4b1570a433?environmentId=100
https://virustotal.com/en/file/e3d74b6eb7f941125c35ae0ab2c5bd8d7116e6794f38b3879bddeb4b1570a433/analysis/
What Are These Odd POP3 (Port 110/tcp) Scans About?
I am seeing a steady trickle of scans for port 110 against my honeypot. Initially, I believed that the goal was brute forcing e-mail passwords. But instead, when setting up a quick netcat listener, I am seeing binary content without any obvious purpose. Various POP3 daemons have had vulnerabilities in the past, so maybe there is a way this is exploited? Or someone looking for backdoors that happen to listen on port 110 to disguise themselves. Can anybody help out with any ideas what this is about?
Here is a typical payload:
00000000 16 03 01 01 22 01 00 01 1e 03 03 a2 33 18 56 3f ...."... ....3.V?
00000010 b9 9a 05 1c 33 24 0c 83 03 bf 62 29 a6 37 22 da ....3$.. ..b).7".
00000020 33 e2 ac 9c 3c 44 28 bd 4d 8b d8 00 00 88 c0 30 3...<D(. M......0
00000030 c0 2c c0 28 c0 24 c0 14 c0 0a 00 a3 00 9f 00 6b .,.(.$.. .......k
00000040 00 6a 00 39 00 38 00 88 00 87 c0 32 c0 2e c0 2a .j.9.8.. ...2...*
00000050 c0 26 c0 0f c0 05 00 9d 00 3d 00 35 00 84 c0 12 .&...... .=.5....
00000060 c0 08 00 16 00 13 c0 0d c0 03 00 0a c0 2f c0 2b ........ ...../.+
00000070 c0 27 c0 23 c0 13 c0 09 00 a2 00 9e 00 67 00 40 .'.#.... .....g.@
00000080 00 33 00 32 00 9a 00 99 00 45 00 44 c0 31 c0 2d .3.2.... .E.D.1.-
00000090 c0 29 c0 25 c0 0e c0 04 00 9c 00 3c 00 2f 00 96 .).%.... ...<./..
000000A0 00 41 c0 11 c0 07 c0 0c c0 02 00 05 00 04 00 15 .A...... ........
000000B0 00 12 00 09 00 ff 01 00 00 6d 00 0b 00 04 03 00 ........ .m......
000000C0 01 02 00 0a 00 34 00 32 00 0e 00 0d 00 19 00 0b .....4.2 ........
000000D0 00 0c 00 18 00 09 00 0a 00 16 00 17 00 08 00 06 ........ ........
000000E0 00 07 00 14 00 15 00 04 00 05 00 12 00 13 00 01 ........ ........
000000F0 00 02 00 03 00 0f 00 10 00 11 00 23 00 00 00 0d ........ ...#....
00000100 00 20 00 1e 06 01 06 02 06 03 05 01 05 02 05 03 . ...... ........
00000110 04 01 04 02 04 03 03 01 03 02 03 03 02 01 02 02 ........ ........
00000120 02 03 00 0f 00 01 01 .......
UPDATE
ok.. this was a bit too easy. After a bit of staring at the payload, it looked familiar. Turns out that this is an SSL Client hello (the 0x16 0x03 0x01 preamble gave it away). So now back to giving the attacker an SSL-enabled server to play with.

Comments